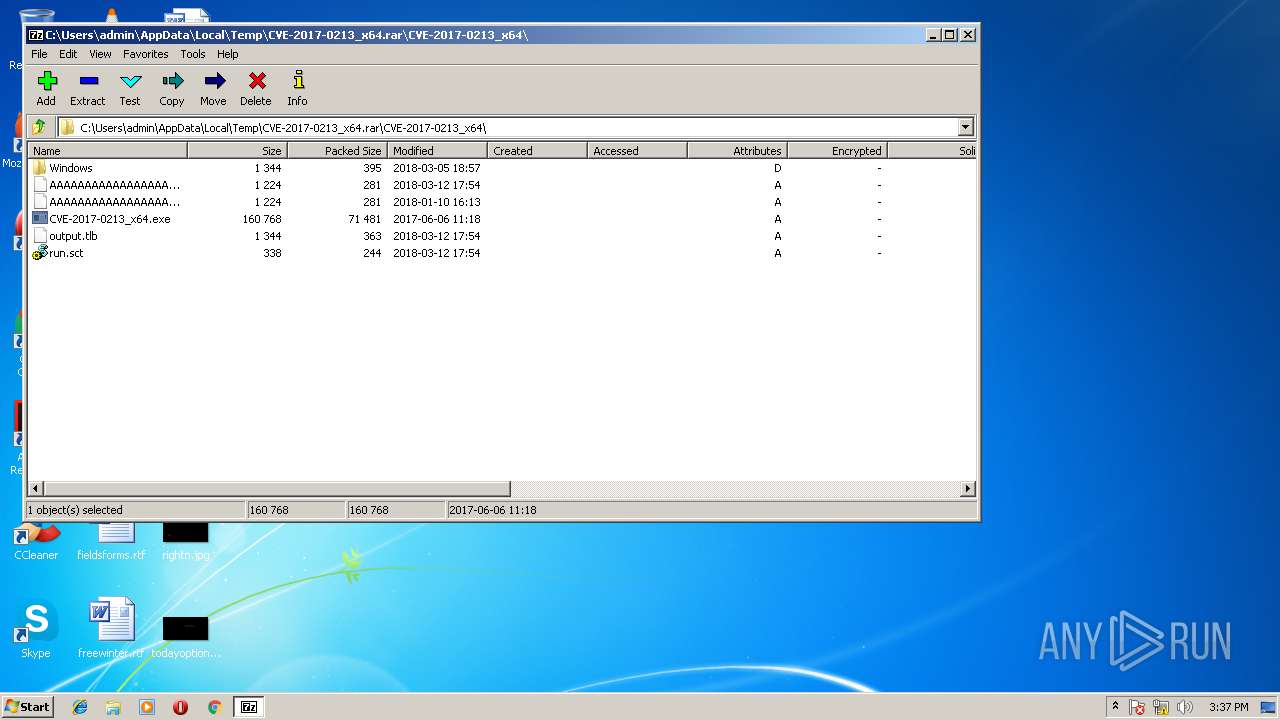
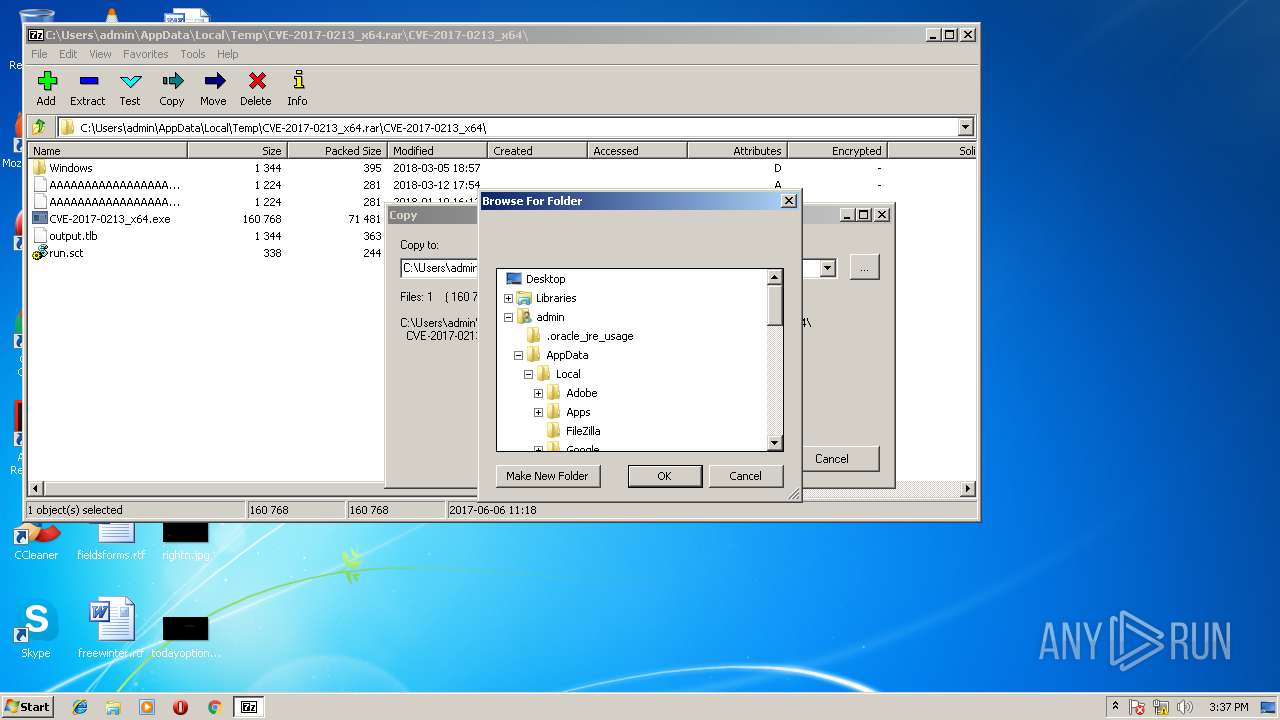
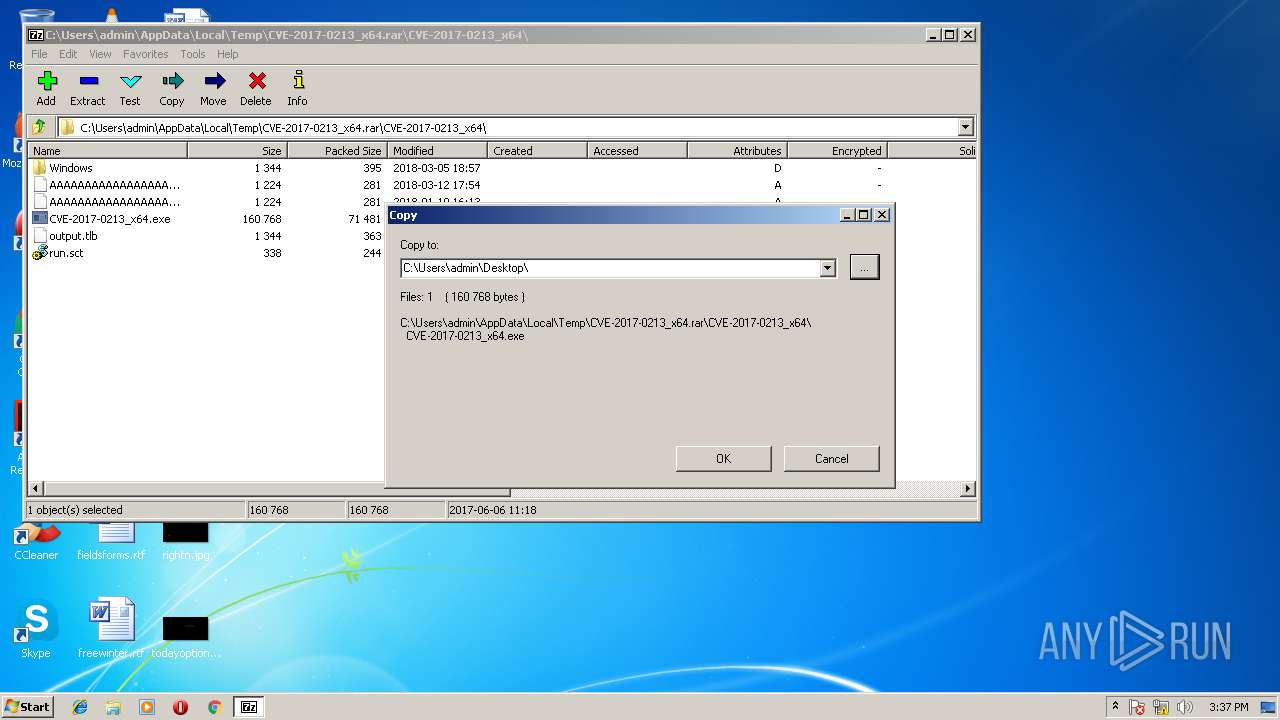
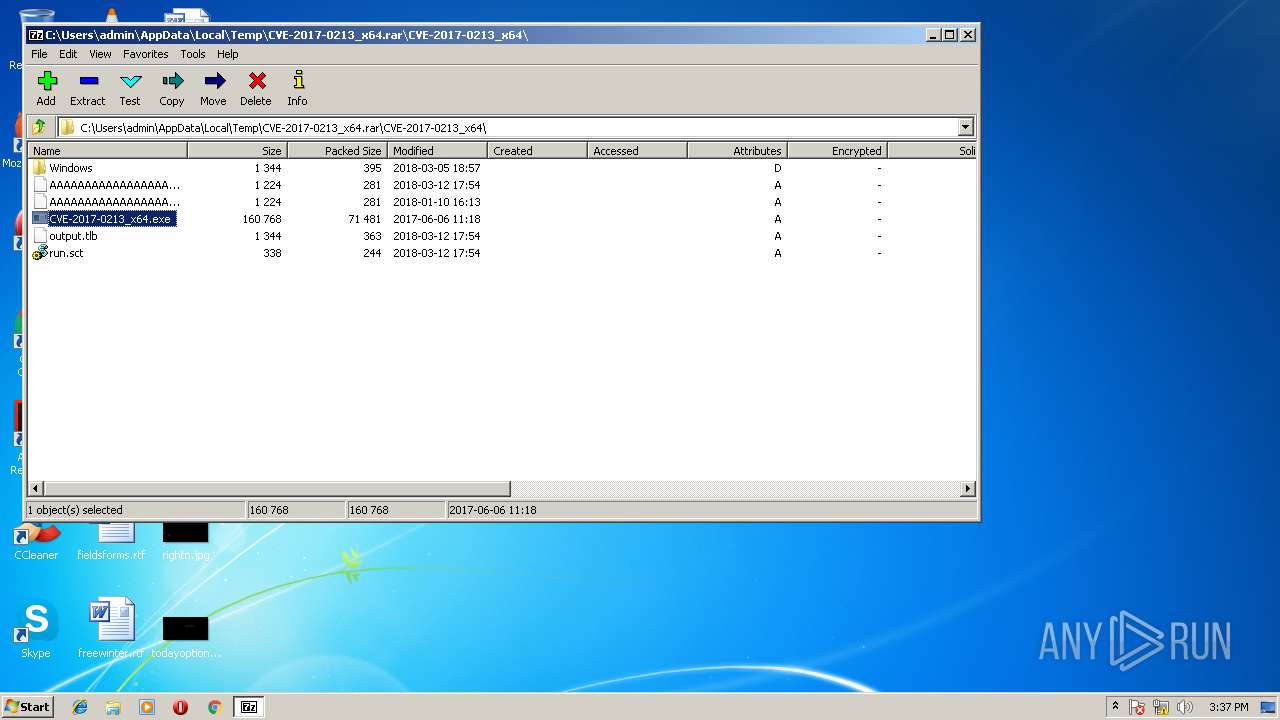
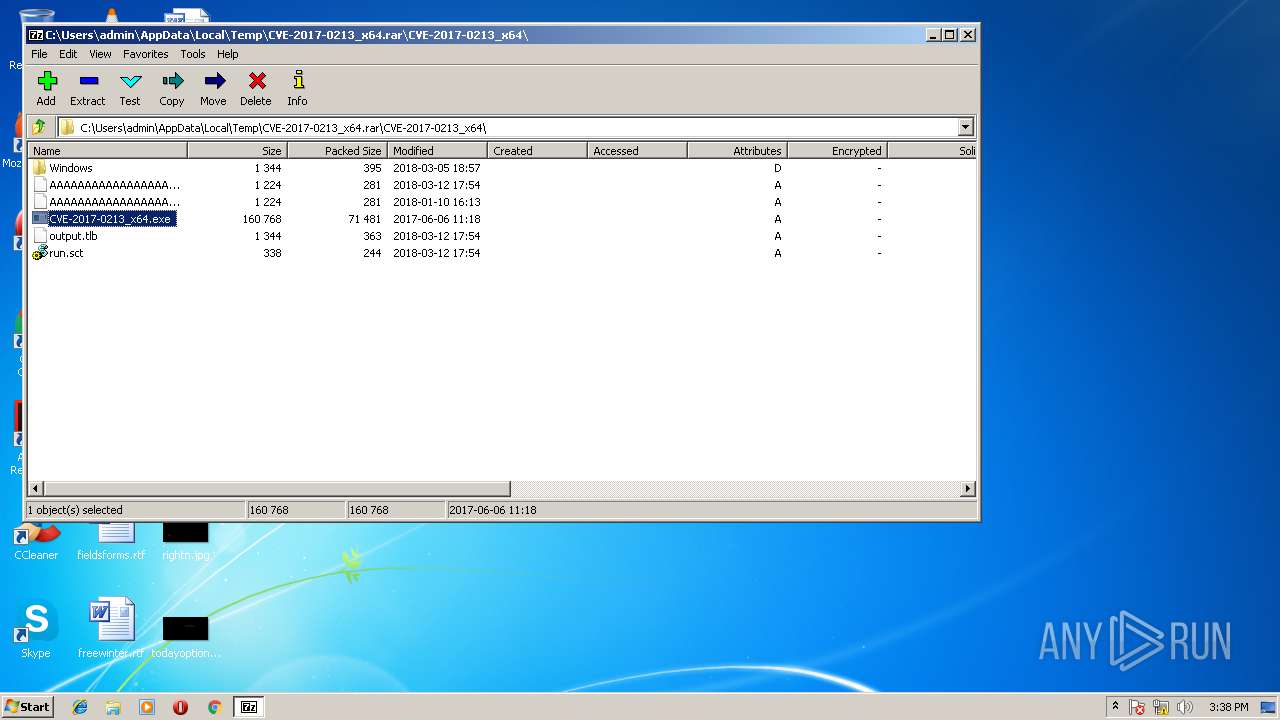
| File name: | CVE-2017-0213_x64.rar |
| Full analysis: | https://app.any.run/tasks/634ab27e-4f0a-443f-ab62-41f7f5dcf2eb |
| Verdict: | No threats detected |
| Analysis date: | May 28, 2018, 14:37:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 45A1B9366889E2625A7B14625A957B11 |
| SHA1: | 613126E085534645B474C03B7E5FDE8C3F7BBF06 |
| SHA256: | C87A3F5A1FD5A6B30409A750EC1D5E4DB4423DFF3B7B03A054FF8C020B385D6D |
| SSDEEP: | 1536:F4NcwS0iaLWzGBJQ2fLVQKCmzNzHBhAUAwUeyTlCwRh6i:F4+haLVTvfxfDzbDU15HZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 7zFM.exe (PID: 3232)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 382 |
|---|---|
| UncompressedSize: | 1224 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:01:10 16:13:28 |
| PackingMethod: | Normal |
| ArchivedFileName: | CVE-2017-0213_x64\AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA |
Total processes
34
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3232 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\CVE-2017-0213_x64.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
Total events
461
Read events
433
Write events
28
Delete events
0
Modification events
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | CopyHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000000 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\93\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (3232) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | CopyHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000000 | |||
Executable files
4
Suspicious files
0
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
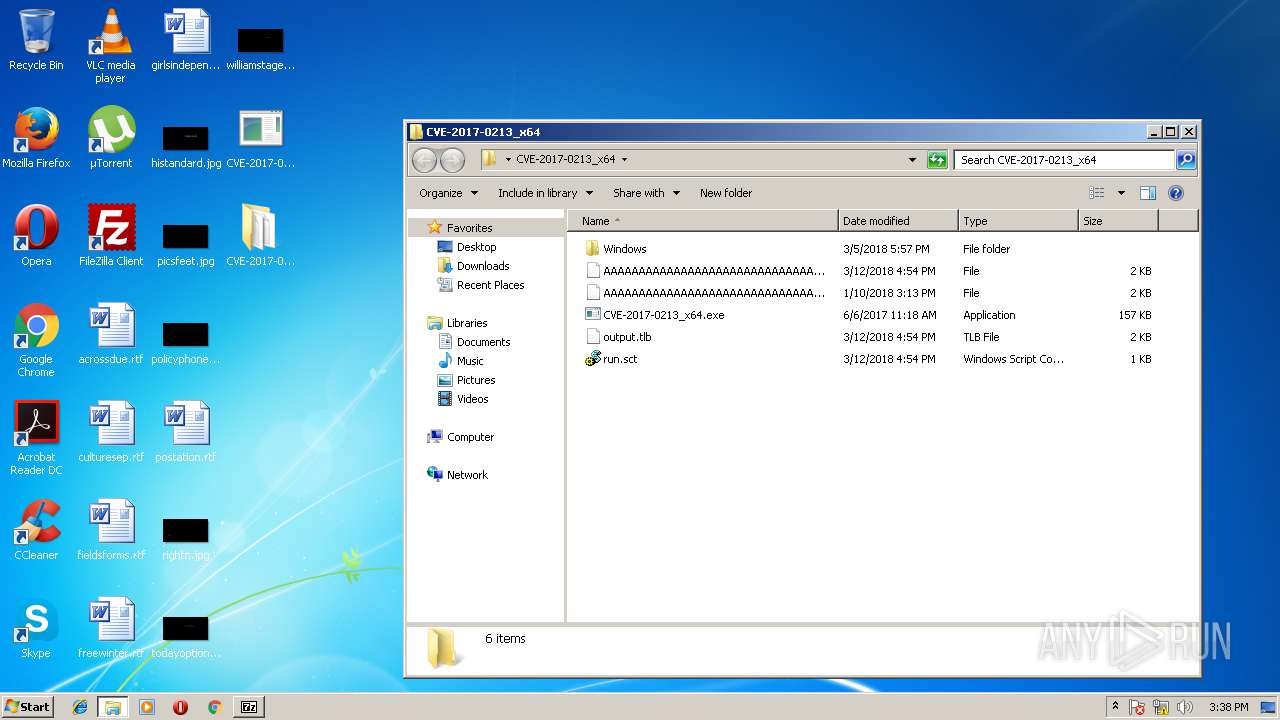
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\output.tlb | tlb | |
MD5:— | SHA256:— | |||
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\run.sct | xml | |
MD5:— | SHA256:— | |||
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\Windows\System32\tapi3.dll | tlb | |
MD5:— | SHA256:— | |||
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA | tlb | |
MD5:— | SHA256:— | |||
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA | tlb | |
MD5:— | SHA256:— | |||
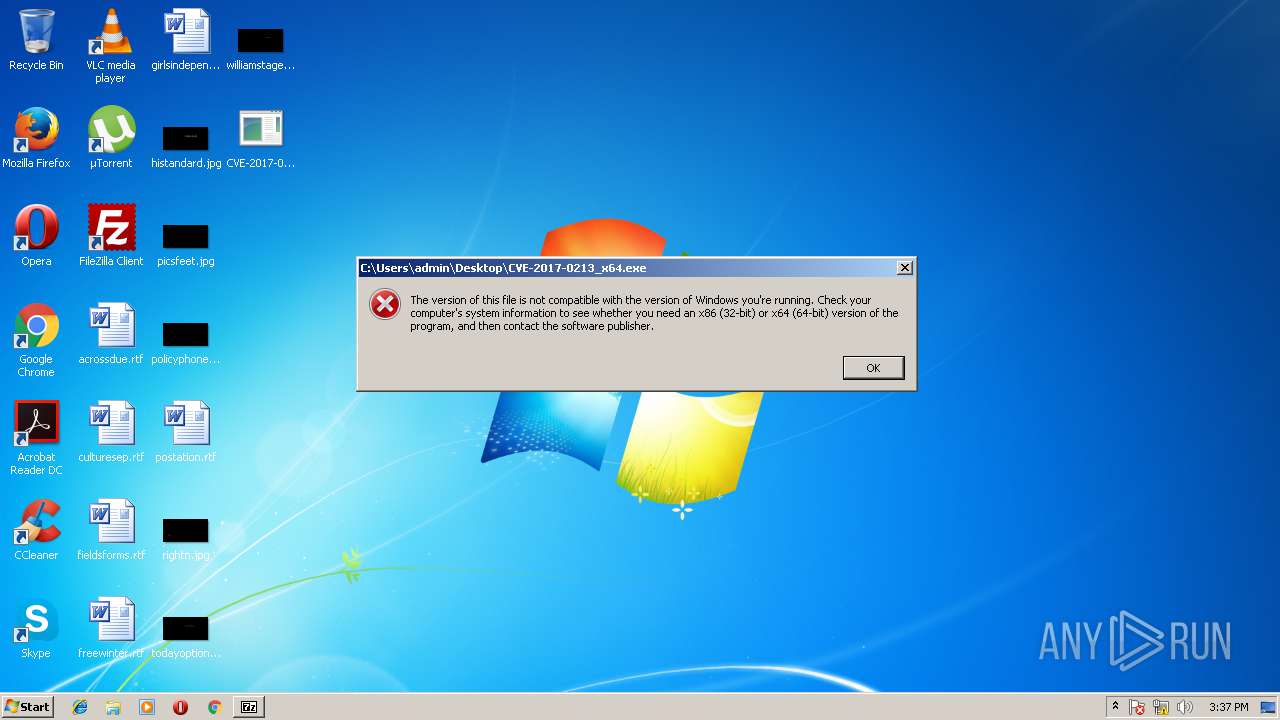
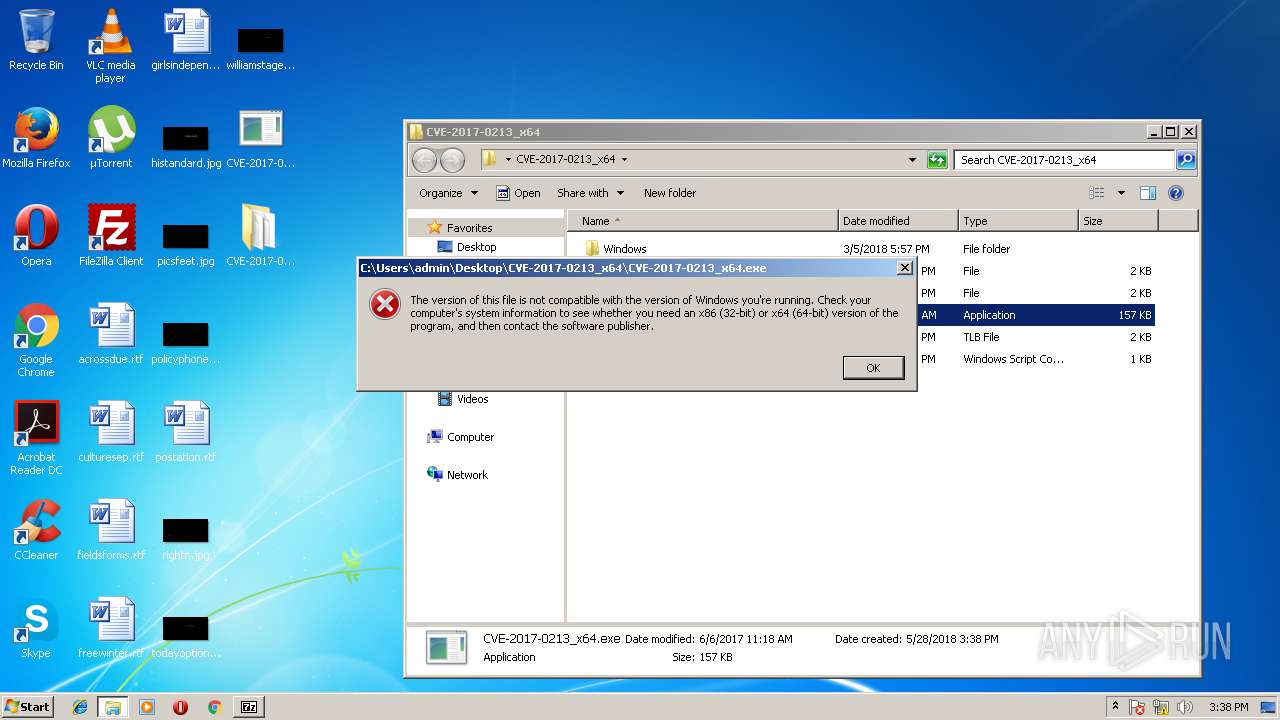
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64\CVE-2017-0213_x64.exe | executable | |
MD5:25E62EF07AA497FF4B13549BC6639E19 | SHA256:AAC0C5AD612FB9A0AC3B4BBFD71B8931FC762F8E11FDF3FFB33EF22076F9C4BC | |||
| 3232 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zO0AC00314\CVE-2017-0213_x64.exe | executable | |
MD5:25E62EF07AA497FF4B13549BC6639E19 | SHA256:AAC0C5AD612FB9A0AC3B4BBFD71B8931FC762F8E11FDF3FFB33EF22076F9C4BC | |||
| 3232 | 7zFM.exe | C:\Users\admin\Desktop\CVE-2017-0213_x64.exe | executable | |
MD5:25E62EF07AA497FF4B13549BC6639E19 | SHA256:AAC0C5AD612FB9A0AC3B4BBFD71B8931FC762F8E11FDF3FFB33EF22076F9C4BC | |||
| 3232 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\CVE-2017-0213_x64.exe | executable | |
MD5:25E62EF07AA497FF4B13549BC6639E19 | SHA256:AAC0C5AD612FB9A0AC3B4BBFD71B8931FC762F8E11FDF3FFB33EF22076F9C4BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report