| URL: | https://urldefense.proofpoint.com/v2/url?u=https-3A__url.avanan.click_v2_r01_-5F-5F-5Fhttps-3A__uebr-2Dfbo.org-5F-5F-5F.YXAzOmNvbndlbGx0aXRsZTphOm86OTIzYzUwNmY0MjRiMWE1OTllNDc0NjYxOTNhMWYxYzE6NzowMDdkOjg1NjBkMGIzYjE3Mjc1MTgzYmFjNGI3Y2ZjZjgyODM1ODU3MjEyMWZjOWRmMDA4ZWU1M2QyMTMxOWRiYWNhMTI6aDpUOk4&d=DwMFAg&c=euGZstcaTDllvimEN8b7jXrwqOf-v5A_CdpgnVfiiMM&r=h-plCunweB9tvRvqFR4dd8rqcR8Dk4yQXgYKAmMl-wFNZHGUfYrQEHr1kukPyRMp&m=vE4hrPtS_Sdq8Jc4V0HGVcRLL2qoU5WHvT_IRvZ8UuXr0Z0kgs9GURlZjpqTrZM4&s=fLtKGmNVGLYa9uANNx-0tgCdKkWfmqyKFDFzT5CK93w&e= |
| Full analysis: | https://app.any.run/tasks/fdcd9977-ec52-464a-914b-c78f9760cc47 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 19:05:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4DA1A3AF54C6A12C8987735E465ECB07 |
| SHA1: | 5163F99BCC98D565E89E471AC6F8E18D0334BA10 |
| SHA256: | C87269E45A38DB71C55C87EC9F446965776E42A3CF2745249E2E0BEC124081D5 |
| SSDEEP: | 12:2UHP1fgYBcYKxYAruznmyhMM7vT5GLwWebwIk2gnW41Y:2ctYYD9AruzmR2T5GtkwI/GTS |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4792)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
145
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
7
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State~RF2c50e8.TMP | binary | |
MD5:2A21453795942FD88CBB06714604B9FD | SHA256:5DFE0384325B556EE4B8668E502312B9BA6ADC298CD9213DDFA528CB959ADC06 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\0fcf84a6-f377-453a-baac-86a9c44e72c3.tmp | binary | |
MD5:D1ACCD710499D082D9868A806EE16A74 | SHA256:296B66123F54F2DAC69BC98740E058C03C10F9E7B2FF29F9B9637F6D8E1773FB | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity~RF2b5998.TMP | binary | |
MD5:15D26FA4E16467BE658F42074AC0DBAA | SHA256:D287407BD901A32E3F38F4392984507184D596C3694FAA69DD0B2E68F9F3A8FE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State | binary | |
MD5:1F284BAD53B9FE9021283C75C6A5867E | SHA256:B52A074E1CB621352C5D550509361B0BFB6B736298BF699D7011577DCB87EC92 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\2970af90-5ce2-48da-8b32-b50a6095934d.tmp | binary | |
MD5:1F284BAD53B9FE9021283C75C6A5867E | SHA256:B52A074E1CB621352C5D550509361B0BFB6B736298BF699D7011577DCB87EC92 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity | binary | |
MD5:D1ACCD710499D082D9868A806EE16A74 | SHA256:296B66123F54F2DAC69BC98740E058C03C10F9E7B2FF29F9B9637F6D8E1773FB | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000ba | tss | |
MD5:22EE8D6641B5322770CDE9BD6DB99EE7 | SHA256:BCEE69FA3B0A6D7C425DE90AEBB56EB5EC73864B90EA868A5D6D63867920E550 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
55
DNS requests
35
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 108.138.7.53:443 | https://url.avanan.click/v2/r01/___https://uebr-fbo.org___.YXAzOmNvbndlbGx0aXRsZTphOm86OTIzYzUwNmY0MjRiMWE1OTllNDc0NjYxOTNhMWYxYzE6NzowMDdkOjg1NjBkMGIzYjE3Mjc1MTgzYmFjNGI3Y2ZjZjgyODM1ODU3MjEyMWZjOWRmMDA4ZWU1M2QyMTMxOWRiYWNhMTI6aDpUOk4 | unknown | — | — | — |
— | — | HEAD | 200 | 23.218.208.109:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
— | — | GET | 302 | 52.71.28.102:443 | https://urldefense.proofpoint.com/v2/url?u=https-3A__url.avanan.click_v2_r01_-5F-5F-5Fhttps-3A__uebr-2Dfbo.org-5F-5F-5F.YXAzOmNvbndlbGx0aXRsZTphOm86OTIzYzUwNmY0MjRiMWE1OTllNDc0NjYxOTNhMWYxYzE6NzowMDdkOjg1NjBkMGIzYjE3Mjc1MTgzYmFjNGI3Y2ZjZjgyODM1ODU3MjEyMWZjOWRmMDA4ZWU1M2QyMTMxOWRiYWNhMTI6aDpUOk4&d=DwMFAg&c=euGZstcaTDllvimEN8b7jXrwqOf-v5A_CdpgnVfiiMM&r=h-plCunweB9tvRvqFR4dd8rqcR8Dk4yQXgYKAmMl-wFNZHGUfYrQEHr1kukPyRMp&m=vE4hrPtS_Sdq8Jc4V0HGVcRLL2qoU5WHvT_IRvZ8UuXr0Z0kgs9GURlZjpqTrZM4&s=fLtKGmNVGLYa9uANNx-0tgCdKkWfmqyKFDFzT5CK93w&e= | unknown | — | — | — |
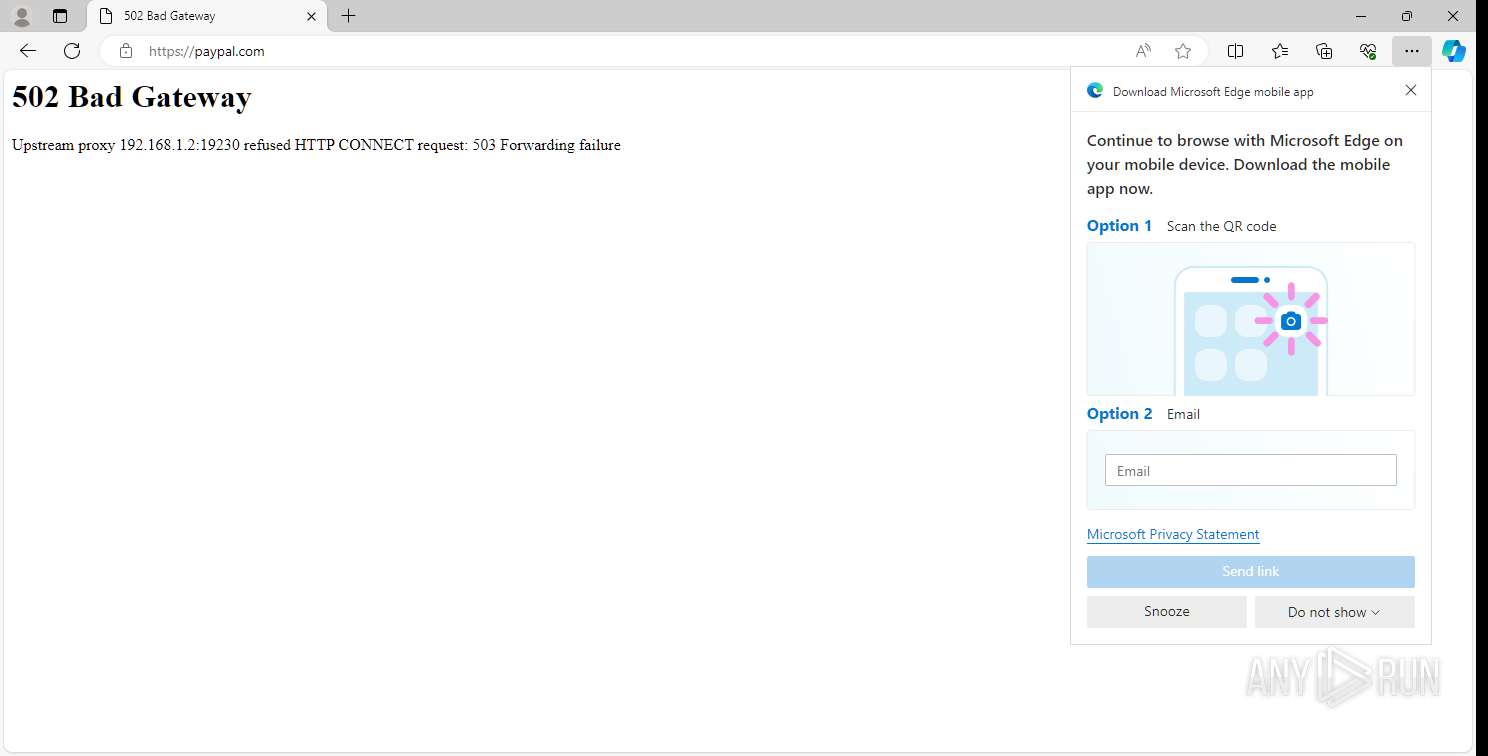
— | — | GET | — | 151.101.129.21:443 | https://paypal.com/ | unknown | — | — | — |
2856 | svchost.exe | GET | 200 | 23.37.202.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 303 | 151.101.193.21:443 | https://ungasanbaliresort.com/ | unknown | — | — | — |
— | — | GET | — | 151.101.193.21:443 | https://paypal.com/favicon.ico | unknown | — | — | — |
4304 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4016 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4844 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.251:5353 | — | — | — | unknown |
4844 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4304 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4792 | msedge.exe | 51.11.192.48:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4016 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4792 | msedge.exe | 52.204.90.22:443 | urldefense.proofpoint.com | AMAZON-AES | US | whitelisted |
4792 | msedge.exe | 18.245.46.85:443 | url.avanan.click | — | US | suspicious |
2740 | svchost.exe | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
4304 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urldefense.proofpoint.com |
| whitelisted |
url.avanan.click |
| unknown |
fs.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
uebr-fbo.org |
| unknown |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ungasanbaliresort.com |
| unknown |
paypal.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Suspected Redirection Domain ( .avanan .click) |
— | — | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Suspected Redirection Domain ( .avanan .click) |