| File name: | 33f612338b6b5e6b4fe8cbb17208795c |
| Full analysis: | https://app.any.run/tasks/cb587d5a-c53c-4f57-93ab-06675e8c6e76 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 05:48:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 33F612338B6B5E6B4FE8CBB17208795C |
| SHA1: | 66535700BBCE7F90D2ADD7C504BC0E0523D4D71D |
| SHA256: | C860BF644BD5E3D6F4CAE67848C4FC769184AE652FCB41CAC670042B185D217A |
| SSDEEP: | 196608:2SdJhhiIbZg4T4hac7p6eDcGRYTOzBVUuuB1z5:2SdJhVbehacQeHt1VUuur |
MALICIOUS
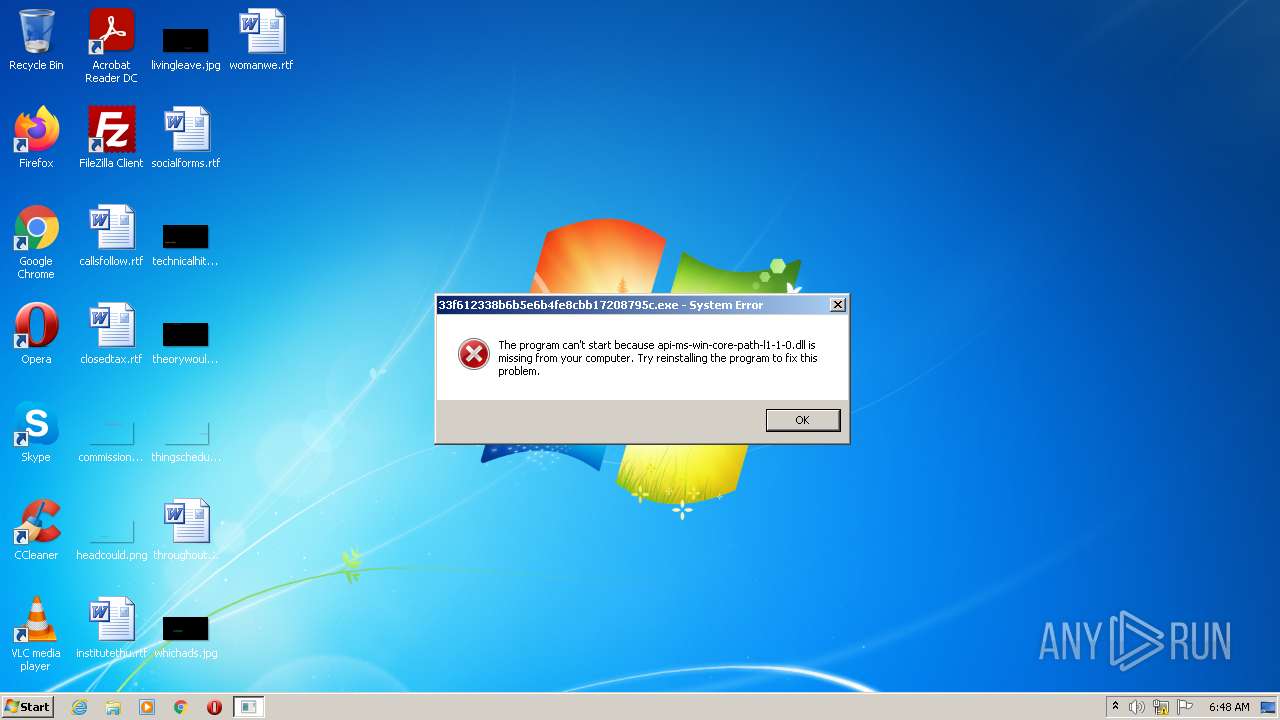
Loads dropped or rewritten executable
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 4076)
Drops executable file immediately after starts
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
SUSPICIOUS
Checks supported languages
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 4076)
Reads the computer name
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
Application launched itself
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
Executable content was dropped or overwritten
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
Drops a file with a compile date too recent
- 33f612338b6b5e6b4fe8cbb17208795c.exe (PID: 3112)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x997c |
| UninitializedDataSize: | - |
| InitializedDataSize: | 65536 |
| CodeSize: | 136192 |
| LinkerVersion: | 14.29 |
| PEType: | PE32 |
| TimeStamp: | 2022:02:03 19:33:28+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Feb-2022 18:33:28 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 03-Feb-2022 18:33:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00021248 | 0x00021400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.63065 |
.rdata | 0x00023000 | 0x0000CEA8 | 0x0000D000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.9738 |
.data | 0x00030000 | 0x0000F874 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.67626 |
.rsrc | 0x00040000 | 0x00000628 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.5651 |
.reloc | 0x00041000 | 0x00001AFC | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.57465 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.39841 | 1487 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
USER32.dll |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3112 | "C:\Users\admin\AppData\Local\Temp\33f612338b6b5e6b4fe8cbb17208795c.exe" | C:\Users\admin\AppData\Local\Temp\33f612338b6b5e6b4fe8cbb17208795c.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\33f612338b6b5e6b4fe8cbb17208795c.exe" | C:\Users\admin\AppData\Local\Temp\33f612338b6b5e6b4fe8cbb17208795c.exe | — | 33f612338b6b5e6b4fe8cbb17208795c.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
23
Read events
23
Write events
0
Delete events
0
Modification events
Executable files
59
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
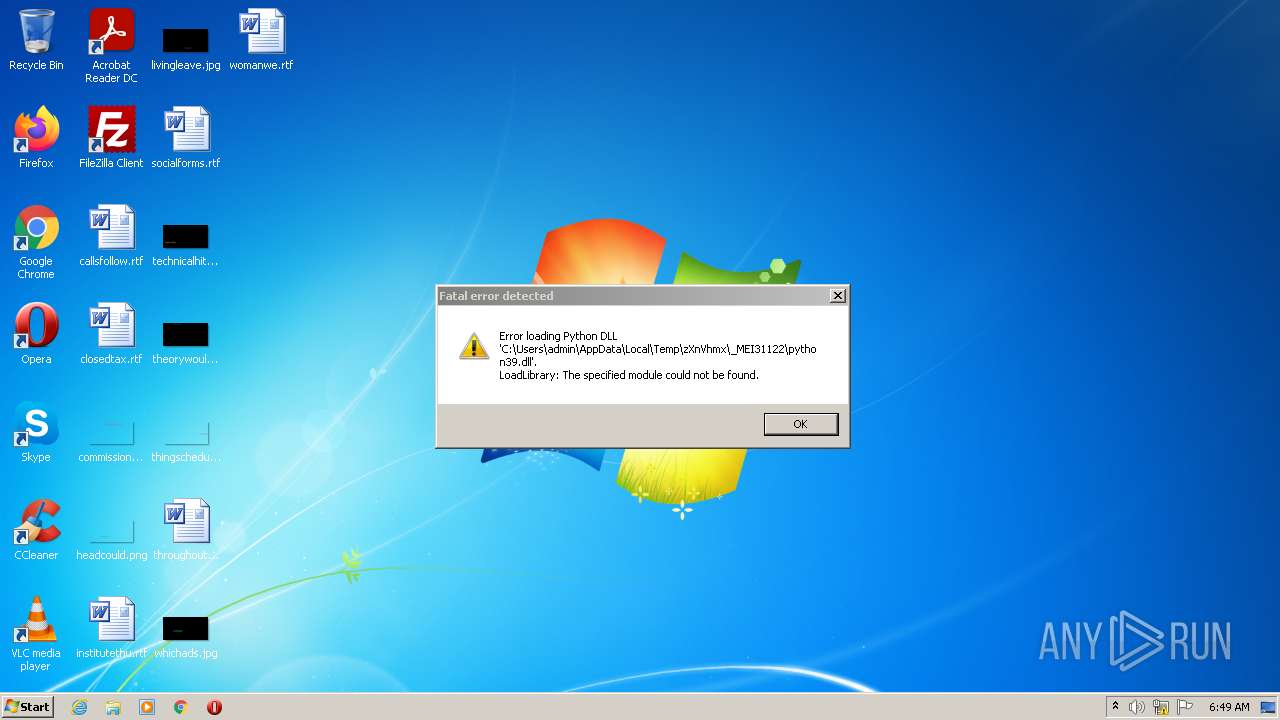
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_chacha20.pyd | executable | |
MD5:9080BBDFBB107205F904A64024EE678C | SHA256:3A750E1FE1BF019DF2252CD35267AC9D850913AA43F516306566ED1E31E1D5E8 | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:9C2390A49AC79BC05AEBB1D5D0A27FE1 | SHA256:9F718EE1D43471811D0007164F0A84578666D1DA0F6B261B86C5DFA826A3132C | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:DDBD242C046E6F339ADCEC3B26660006 | SHA256:F34CE0DFA4B81F566B51B3CB384AD21B0F81C36069C045287807278F4DFD76FA | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:FFAAE5A56CCD4FF6869CF16A36532CF5 | SHA256:79213B7E9F85931B424C818CCECDF9B06CF6ABDF091AC0DE3E3E5751145193B2 | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_cast.pyd | executable | |
MD5:984ACC820ABD67C29A2EA9767A4C277D | SHA256:E9ACFDF6557E2D7E75AFB39F209C4D6D86B36D0CBD816EEF0F4FEC0D5EBD9C35 | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Hash\_BLAKE2b.pyd | executable | |
MD5:48314EE0BEB7C48CEFA840C1F6C51E42 | SHA256:402E89A84C7C5C613FA34E0127D000E9D8FF2CC948DD9933024CD7C9036FAC75 | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_ecb.pyd | executable | |
MD5:C7FE7CAE847D9CC7FFB20FF218A5E0B9 | SHA256:4C30627081EF86F23C3292D28EA8BEAE9D32F63E4664E6799924032BA584BA72 | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:71BC71BDB08D3C606DE5706E1B8F3649 | SHA256:D7D805C3B04A8E06B229798D942B59C6C35417CD287BC6F5570E65231D7708FA | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_ctr.pyd | executable | |
MD5:D01B5C0CEDAE84707903F9660AAE2F31 | SHA256:D08CAAD9EEAE42266FBA08936450462A69DB4B96365D792E3529C1AA7FF6DB6D | |||
| 3112 | 33f612338b6b5e6b4fe8cbb17208795c.exe | C:\Users\admin\AppData\Local\Temp\zXnVhmx\_MEI31122\Crypto\Cipher\_raw_ofb.pyd | executable | |
MD5:CAAB7CA0A1BC6554C275300C18C3047B | SHA256:701CBDE9CE6FB828C46A19202AE63674670A61C9A4381BC49017CFB3CE1CED81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report