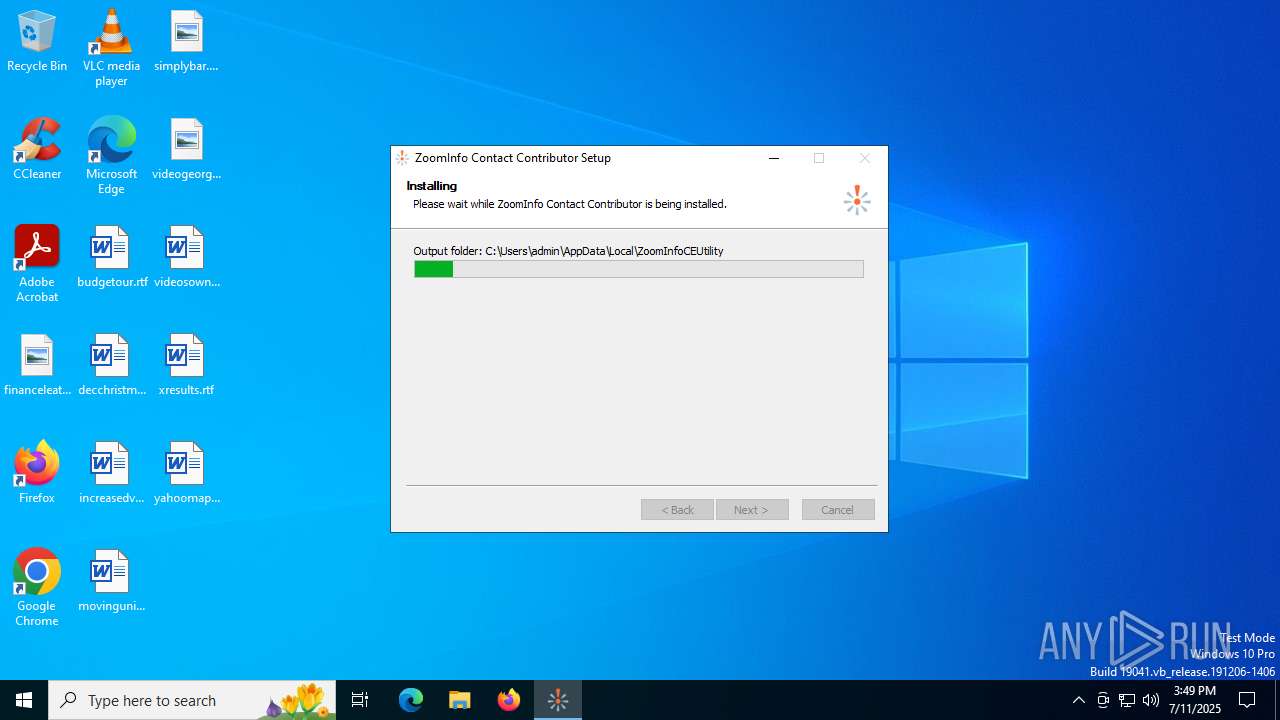
| File name: | ZoomInfoContactContributor.exe |
| Full analysis: | https://app.any.run/tasks/0268c1d7-5d42-413e-a9c1-04f8f50cee18 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2025, 15:49:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | AE1FB4C3B379E640253FA579E92AA5D7 |
| SHA1: | 2966DD1B611714D3DA70A79F9E8841A269D83419 |
| SHA256: | C8559B78AB19206C0275D6570945C31A4B36AB696865E495F92305508297A364 |
| SSDEEP: | 12288:kk52OxotZC6Pl+Zva9999qgyZW+fP2/yEion:k8XbfPmyEion |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
- powershell.exe (PID: 4820)
Changes powershell execution policy (Bypass)
- ZoomInfoContactContributor.exe (PID: 2848)
Bypass execution policy to execute commands
- powershell.exe (PID: 3556)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
The process creates files with name similar to system file names
- ZoomInfoContactContributor.exe (PID: 2848)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
Malware-specific behavior (creating "System.dll" in Temp)
- ZoomInfoContactContributor.exe (PID: 2848)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
The process bypasses the loading of PowerShell profile settings
- ZoomInfoContactContributor.exe (PID: 2848)
Executable content was dropped or overwritten
- ZoomInfoContactContributor.exe (PID: 2848)
- powershell.exe (PID: 4820)
Starts POWERSHELL.EXE for commands execution
- ZoomInfoContactContributor.exe (PID: 2848)
There is functionality for taking screenshot (YARA)
- ZoomInfoContactContributor.exe (PID: 2848)
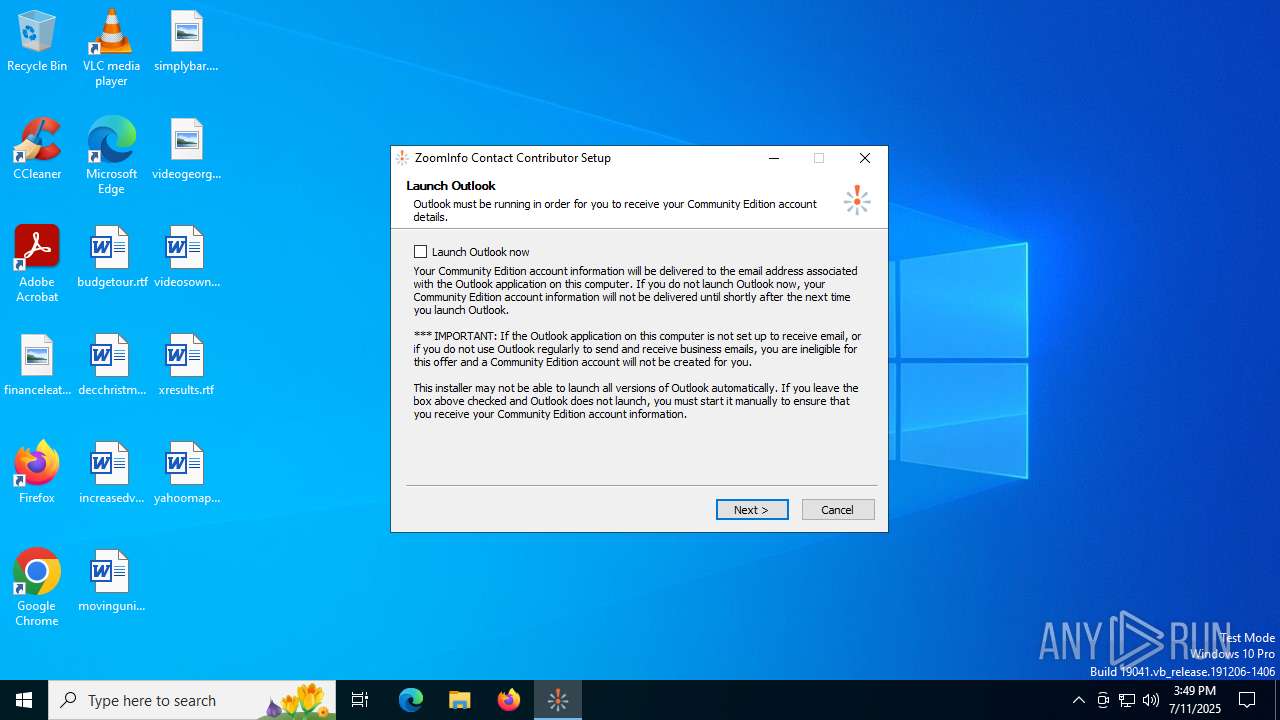
Reads Microsoft Outlook installation path
- ZoomInfoContactContributor.exe (PID: 2848)
Reads security settings of Internet Explorer
- ZoomInfoContactContributor.exe (PID: 2848)
The process hide an interactive prompt from the user
- ZoomInfoContactContributor.exe (PID: 2848)
Process drops python dynamic module
- powershell.exe (PID: 4820)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 4820)
The process drops C-runtime libraries
- powershell.exe (PID: 4820)
Process drops legitimate windows executable
- powershell.exe (PID: 4820)
INFO
Create files in a temporary directory
- ZoomInfoContactContributor.exe (PID: 2848)
Checks supported languages
- ZoomInfoContactContributor.exe (PID: 2848)
The sample compiled with english language support
- ZoomInfoContactContributor.exe (PID: 2848)
- powershell.exe (PID: 4820)
Disables trace logs
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
Reads Microsoft Office registry keys
- ZoomInfoContactContributor.exe (PID: 2848)
Checks proxy server information
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3556)
- slui.exe (PID: 2524)
Reads the computer name
- ZoomInfoContactContributor.exe (PID: 2848)
Process checks computer location settings
- ZoomInfoContactContributor.exe (PID: 2848)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4820)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4820)
Reads the software policy settings
- slui.exe (PID: 2524)
Reads Internet Explorer settings
- OUTLOOK.EXE (PID: 1080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.62 |
| ProductVersionNumber: | 2.0.0.62 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | - |
| FileVersion: | 62 |
| LegalCopyright: | (c) Zoom Information, Inc. |
| ProductName: | ZoomInfo Contact Contributor |
| ProductVersion: | 62 |
Total processes
149
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | ZoomInfoContactContributor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\ZoomInfoContactContributor.exe" | C:\Users\admin\AppData\Local\Temp\ZoomInfoContactContributor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 62 Modules
| |||||||||||||||
| 3556 | powershell -NoProfile -NonInteractive -WindowStyle Hidden -ExecutionPolicy Bypass -Command "$ProgressPreference = \"SilentlyContinue\"; [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri \"https://swapper-prd.zi-ext.com/client/download2?client_version=62&client_id={F78CDFA0-F5D7-470A-A54A-8C3A75BC110A}&outlook_bitness=64&reachout=true&appid=3\" -OutFile \"C:\Users\admin\AppData\Local\ZoomInfoCEUtility\ZoomInfo_CE.zip\" -UseBasicParsing" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | ZoomInfoContactContributor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | powershell -WindowStyle Hidden -Command "$ProgressPreference = \"SilentlyContinue\"; [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; try { Invoke-WebRequest -Uri \"https://swapper-prd.zi-ext.com/client/installopen?client_id={F78CDFA0-F5D7-470A-A54A-8C3A75BC110A}\" -OutFile \"installer_opened.txt\" -UseBasicParsing } catch { }" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | ZoomInfoContactContributor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | powershell -WindowStyle Hidden -Command "Expand-Archive -Path \"C:\Users\admin\AppData\Local\ZoomInfoCEUtility\ZoomInfo_CE.zip\" -DestinationPath \"C:\Users\admin\AppData\Local\ZoomInfoCEUtility\" -Force" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | ZoomInfoContactContributor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 376
Read events
23 948
Write events
370
Delete events
58
Modification events
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4192) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
226
Suspicious files
13
Text files
991
Unknown types
601
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1080 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p2g5izej.ddg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2848 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsd49BC.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5is5regc.xob.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3556 | powershell.exe | C:\Users\admin\AppData\Local\ZoomInfoCEUtility\ZoomInfo_CE.zip | — | |
MD5:— | SHA256:— | |||
| 2848 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsd49BC.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 1080 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\245B182F-F6AA-4AAA-8B04-A3B6FFE70A01 | xml | |
MD5:5D7C0668CDD49D24737F7C81FE4ED1F4 | SHA256:8A3CD4DC2918A2BE4CFB8BD760C9DFBA7A72338C9B22808249124DA711429852 | |||
| 3556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4vhtpvof.dfl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2848 | ZoomInfoContactContributor.exe | C:\Users\admin\AppData\Local\Temp\nsd49BC.tmp\nsExec.dll | executable | |
MD5:11092C1D3FBB449A60695C44F9F3D183 | SHA256:2CD3A2D4053954DB1196E2526545C36DFC138C6DE9B81F6264632F3132843C77 | |||
| 4192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\installer_opened.txt | binary | |
MD5:C4EA5C8E83D004E952237863EF3DDB68 | SHA256:53E43D3C8F93433F61AE2EA3A13E4376BF54BEC26EC94BE79E3ECDBEFB3CA293 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
38
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6780 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6780 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1080 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1080 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6376 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4192 | powershell.exe | 172.64.149.108:443 | swapper-prd.zi-ext.com | CLOUDFLARENET | US | unknown |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7020 | svchost.exe | 40.126.28.12:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
swapper-prd.zi-ext.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |