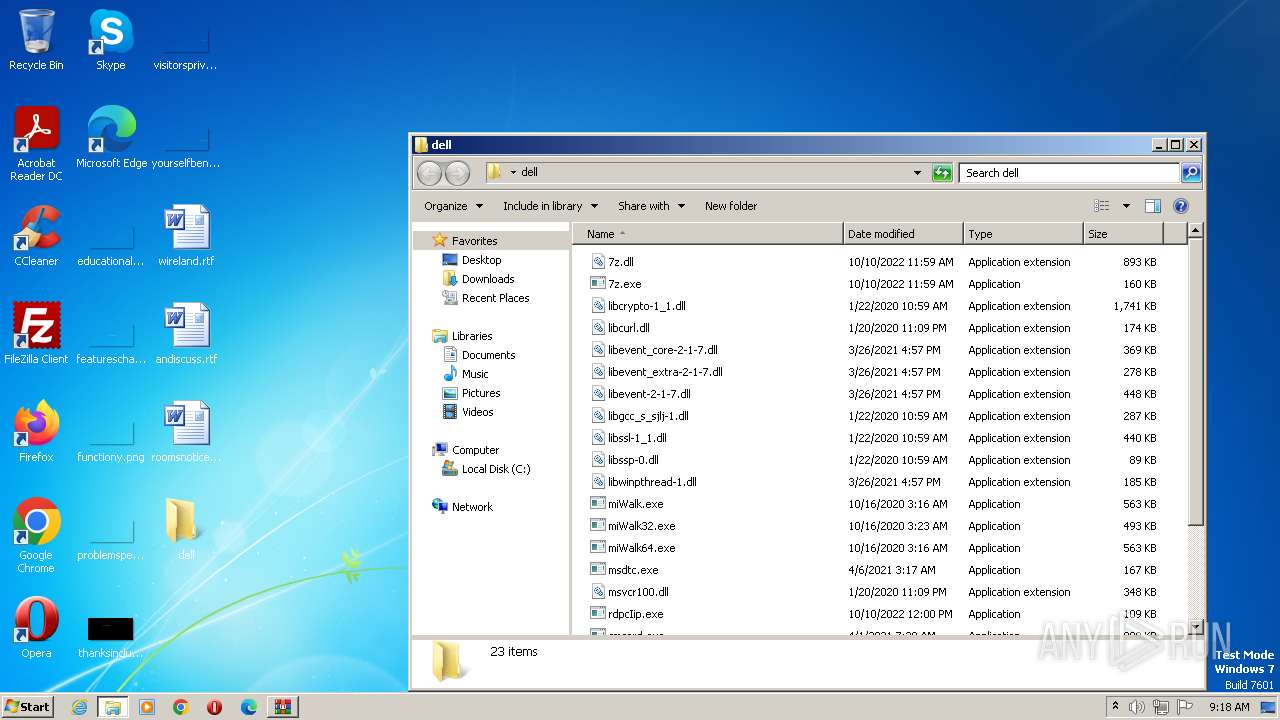
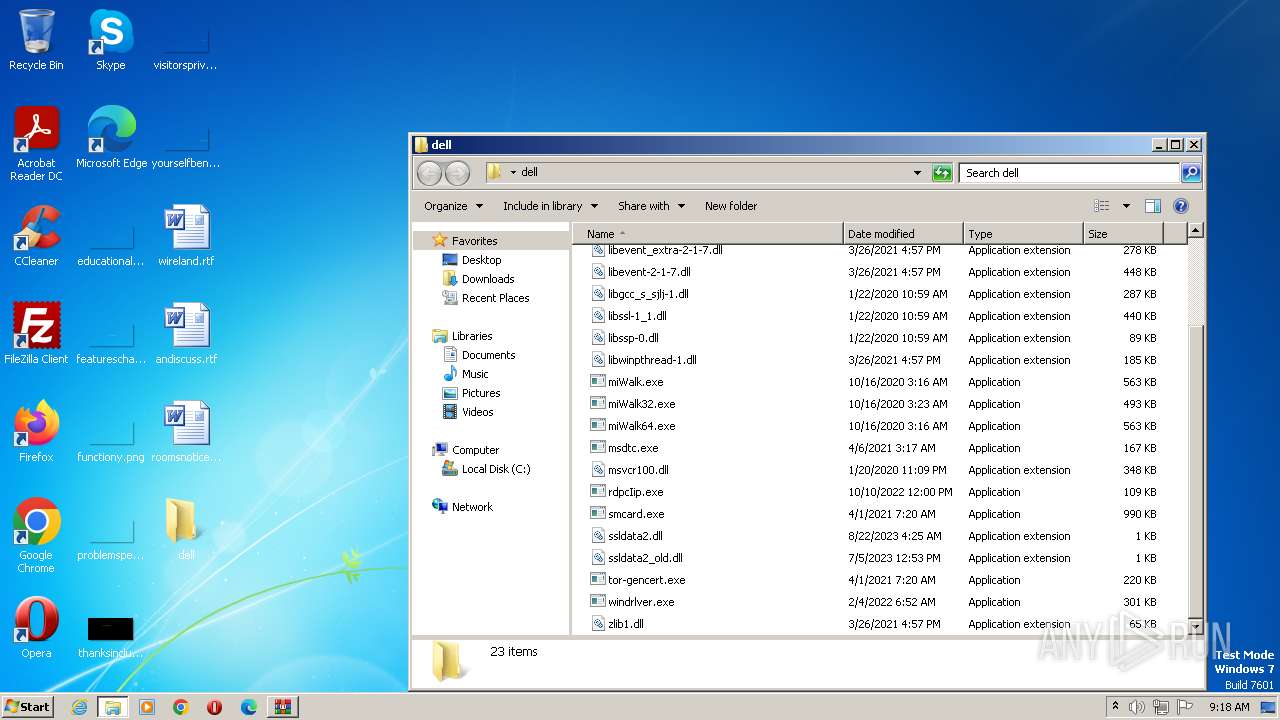
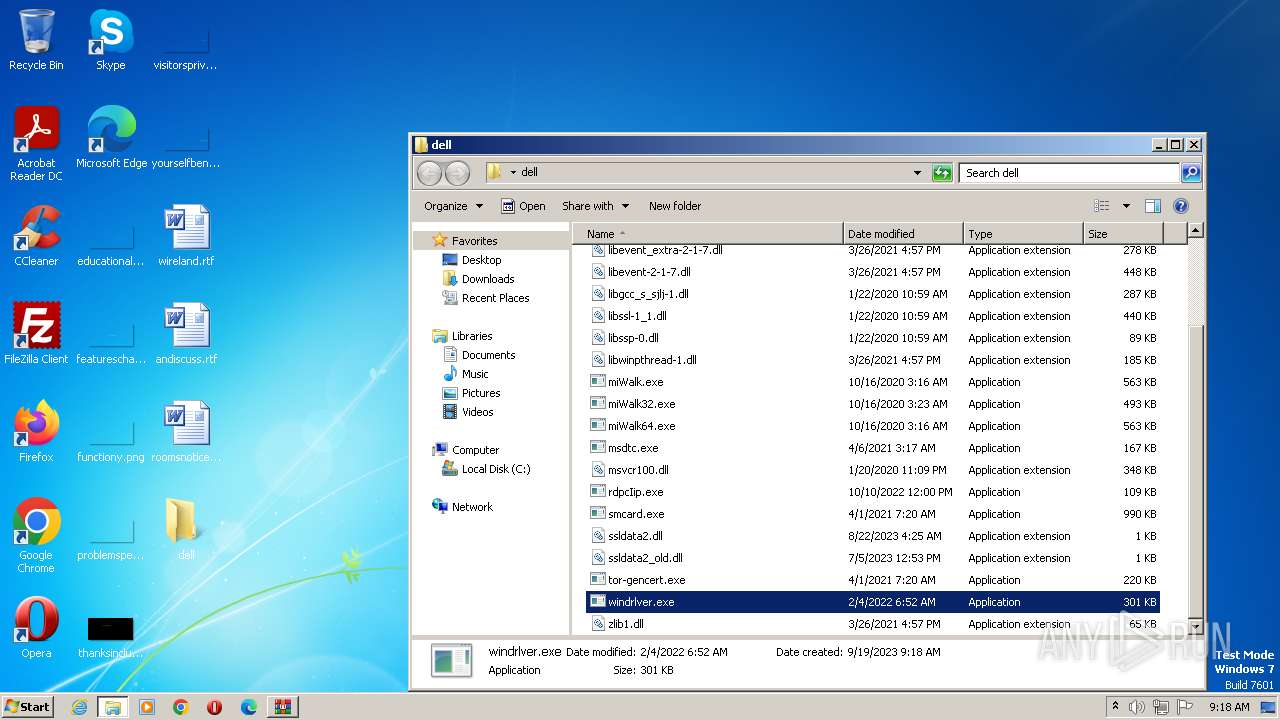
| File name: | dell (1).7z |
| Full analysis: | https://app.any.run/tasks/ee257e33-718a-4fa9-8f17-9b7c24f8787d |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2023, 08:17:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 35DB9791B9149BF6780CF6DEE5DEE5AD |
| SHA1: | BD336134A4263A9A97C612094D95AF77C72FF7C6 |
| SHA256: | C852688F4D268FB0235CA086B29D87AB680CFBE8E3A0468959656D44DF17B6ED |
| SSDEEP: | 196608:ai+Zc47p+x94LVjZvSJAJbnvi/uRrOGaY5iAFNj81UK:ai+ZZ9+x9BJAJbvNRrp5zDK |
MALICIOUS
Application was dropped or rewritten from another process
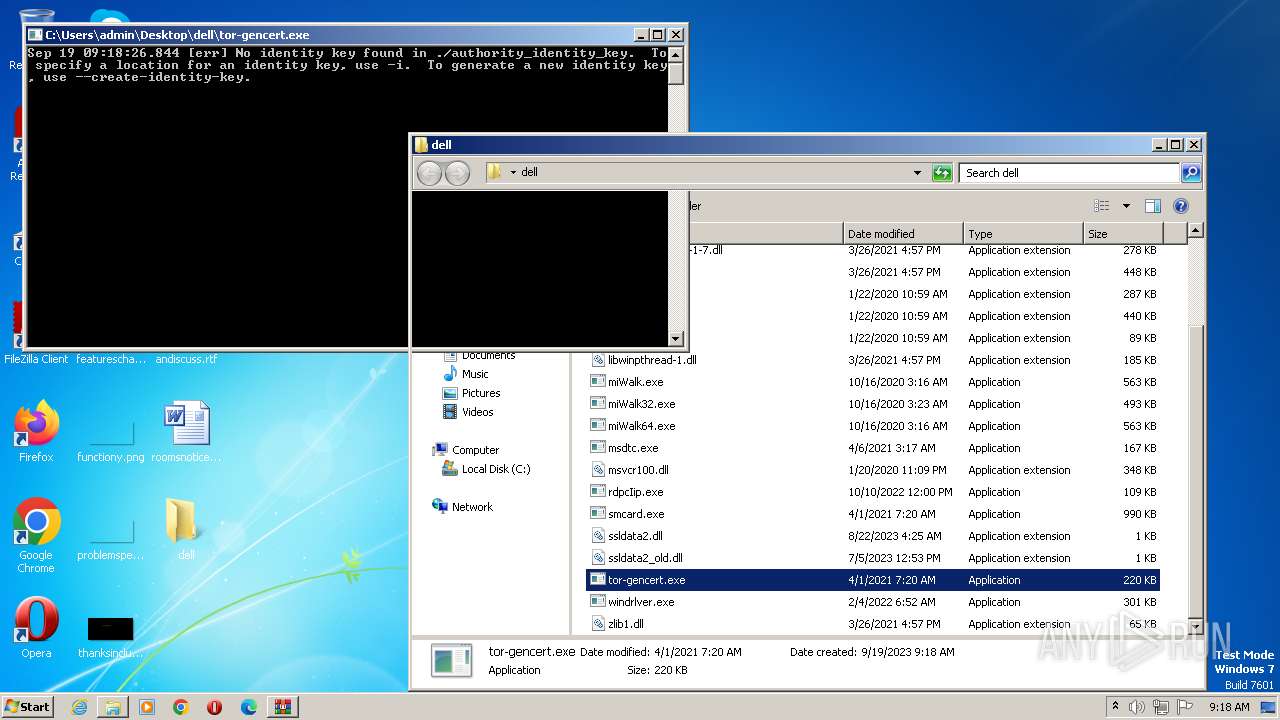
- tor-gencert.exe (PID: 648)
- windrlver.exe (PID: 2672)
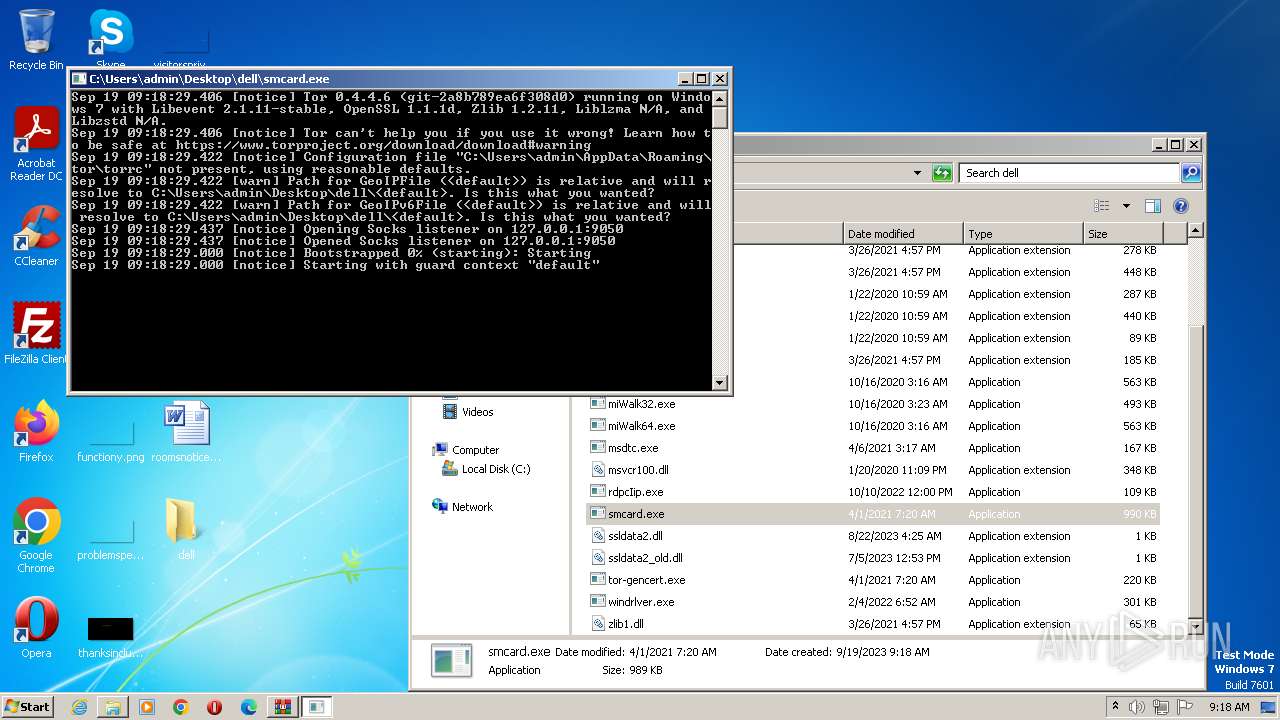
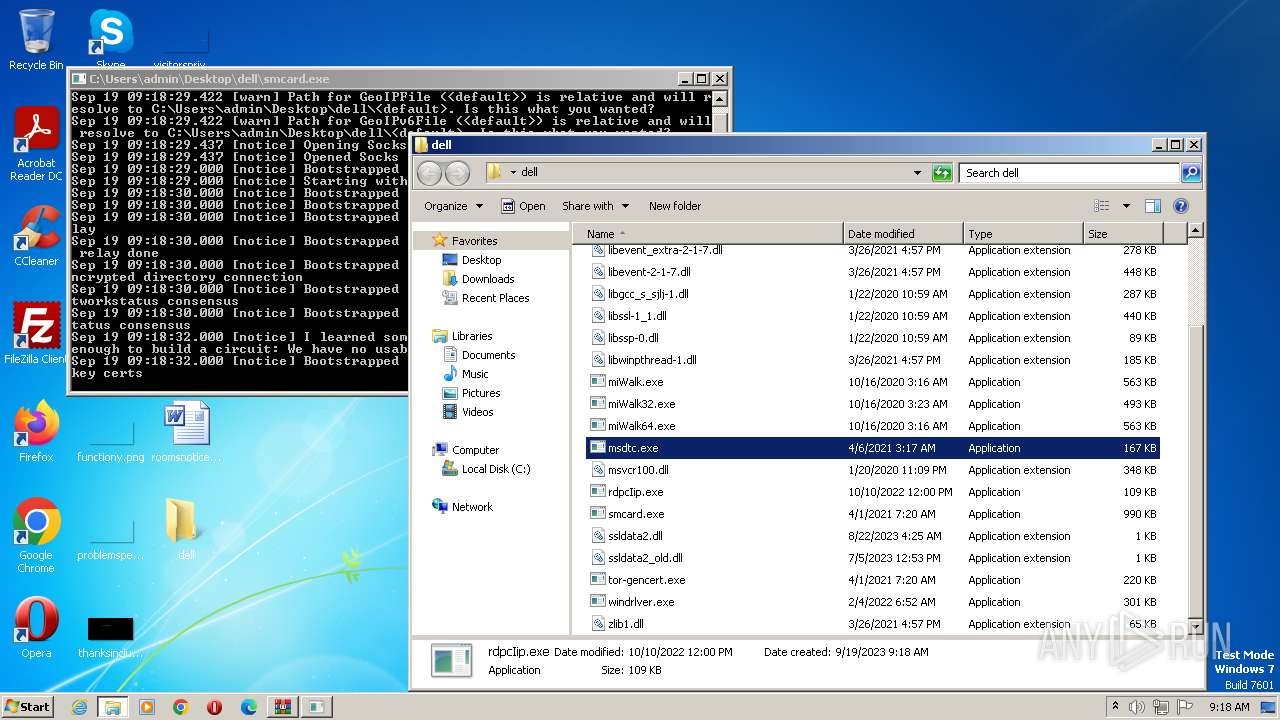
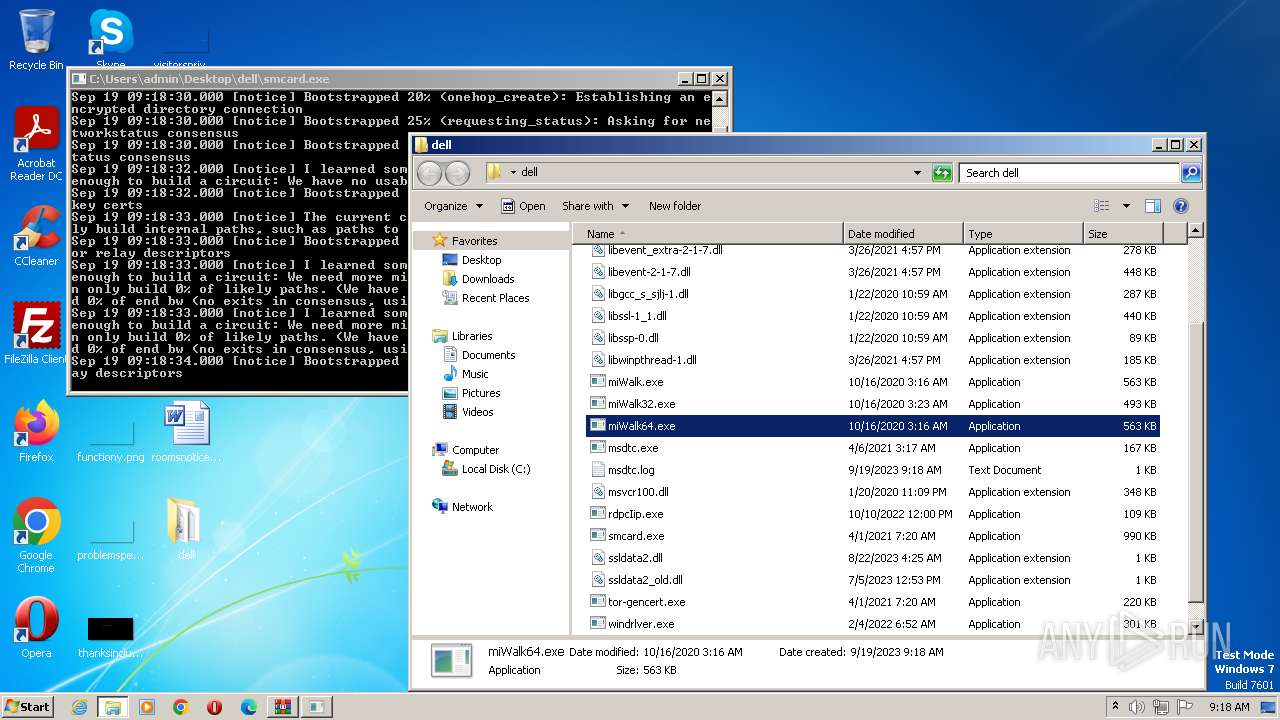
- smcard.exe (PID: 3196)
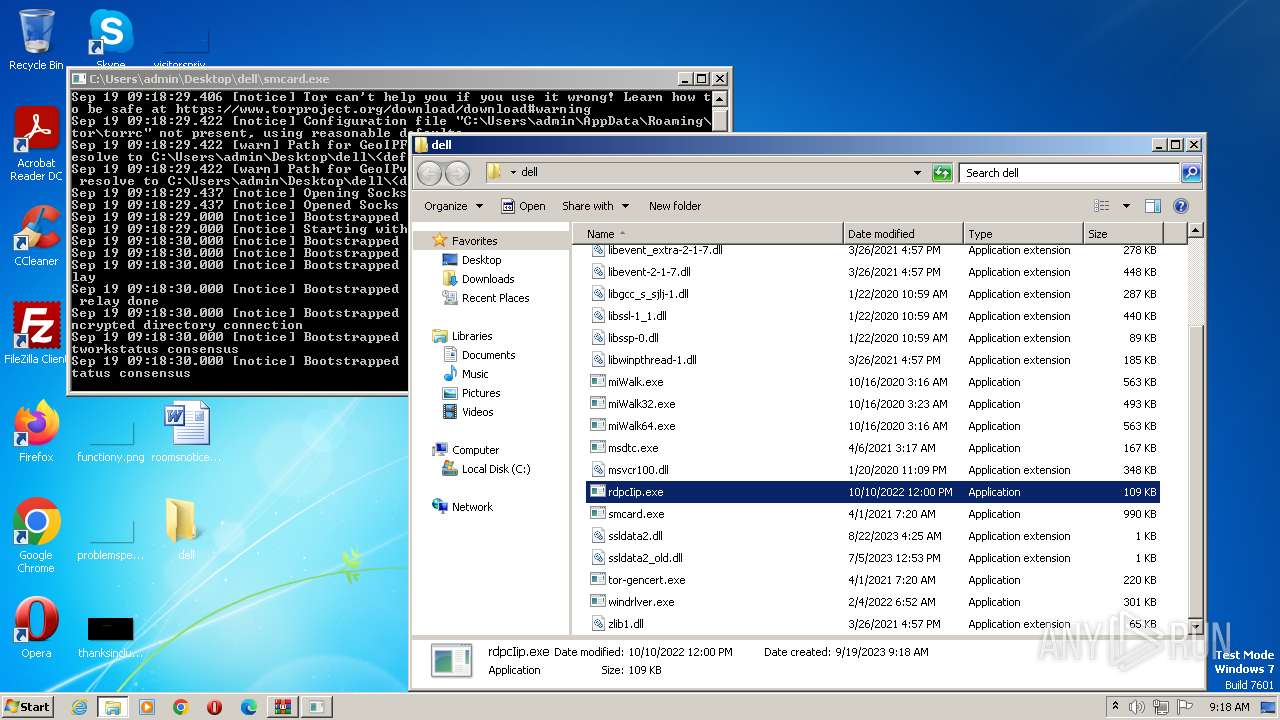
- rdpcIip.exe (PID: 3560)
- msdtc.exe (PID: 1036)
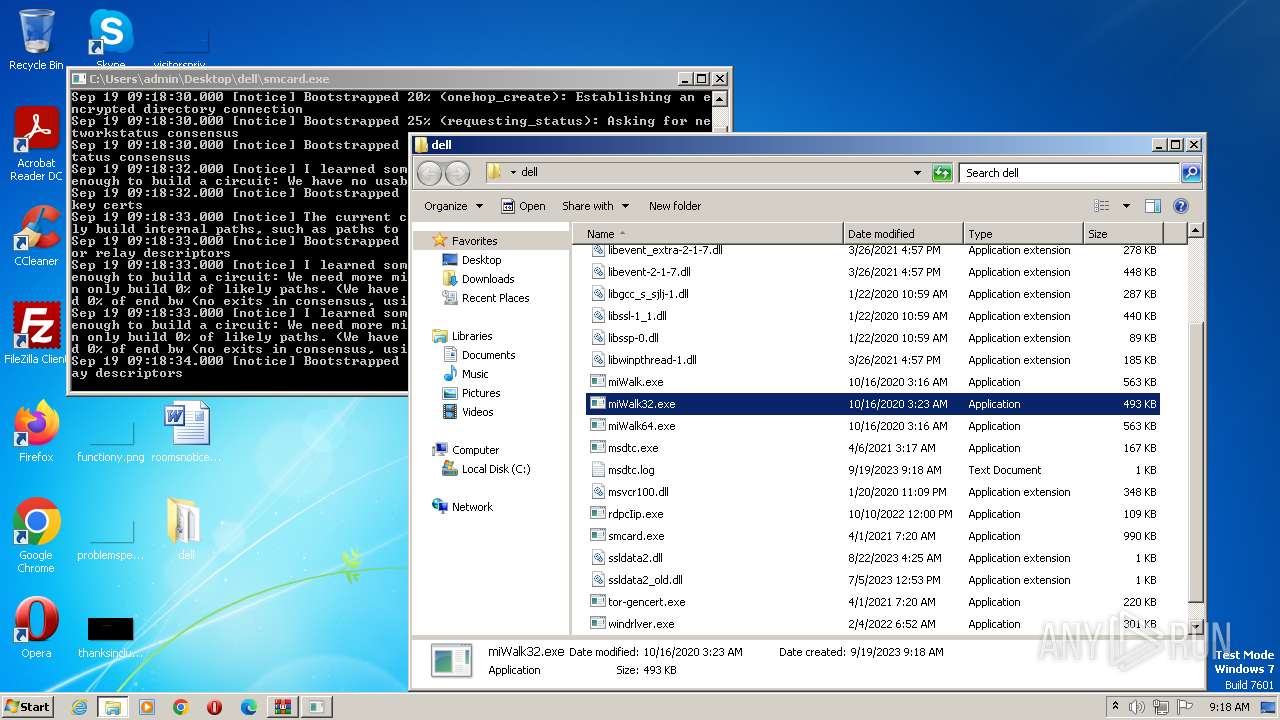
- miWalk32.exe (PID: 3472)
Loads dropped or rewritten executable
- tor-gencert.exe (PID: 648)
- windrlver.exe (PID: 2672)
- smcard.exe (PID: 3196)
- msdtc.exe (PID: 1036)
SUSPICIOUS
Reads the Internet Settings
- rdpcIip.exe (PID: 3560)
Starts CMD.EXE for commands execution
- rdpcIip.exe (PID: 3560)
Connects to unusual port
- smcard.exe (PID: 3196)
INFO
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 3556)
Manual execution by a user
- tor-gencert.exe (PID: 648)
- windrlver.exe (PID: 2672)
- smcard.exe (PID: 3196)
- rdpcIip.exe (PID: 3560)
- miWalk32.exe (PID: 3472)
- msdtc.exe (PID: 1036)
Checks supported languages
- tor-gencert.exe (PID: 648)
- windrlver.exe (PID: 2672)
- smcard.exe (PID: 3196)
- rdpcIip.exe (PID: 3560)
- msdtc.exe (PID: 1036)
- miWalk32.exe (PID: 3472)
Reads the machine GUID from the registry
- windrlver.exe (PID: 2672)
- tor-gencert.exe (PID: 648)
- smcard.exe (PID: 3196)
Reads the computer name
- smcard.exe (PID: 3196)
- rdpcIip.exe (PID: 3560)
- miWalk32.exe (PID: 3472)
Creates files or folders in the user directory
- smcard.exe (PID: 3196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
49
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | "C:\Users\admin\Desktop\dell\tor-gencert.exe" | C:\Users\admin\Desktop\dell\tor-gencert.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Desktop\dell\msdtc.exe" | C:\Users\admin\Desktop\dell\msdtc.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2556 | "C:\Windows\System32\cmd.exe" /c del *.cpass | C:\Windows\System32\cmd.exe | — | rdpcIip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\Desktop\dell\windrlver.exe" | C:\Users\admin\Desktop\dell\windrlver.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3020 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3196 | "C:\Users\admin\Desktop\dell\smcard.exe" | C:\Users\admin\Desktop\dell\smcard.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3472 | "C:\Users\admin\Desktop\dell\miWalk32.exe" | C:\Users\admin\Desktop\dell\miWalk32.exe | — | explorer.exe | |||||||||||
User: admin Company: mshlp Integrity Level: MEDIUM Description: mshlp Exit code: 1 Version: 2.2.0.0 Modules
| |||||||||||||||
| 3556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\dell (1).7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\Desktop\dell\rdpcIip.exe" | C:\Users\admin\Desktop\dell\rdpcIip.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 434
Read events
2 416
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3560) rdpcIip.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3560) rdpcIip.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
21
Suspicious files
0
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\smcard.exe | executable | |
MD5:8A5D86EB9B19DDBDED8F840B3FACBAB4 | SHA256:01BEE3BB01F34F8DA926C6B83980958166F1B10D00A923DEB87361E9F34BCD83 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libgcc_s_sjlj-1.dll | executable | |
MD5:CD24A7E27E916278546D33F8F4DB7065 | SHA256:63269FBA5E803500DC74ED82FA72B50C7EFA3948633ECE46D354544E37058E0F | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\tor-gencert.exe | executable | |
MD5:D50694D78CB253926050DDE4A4CB7A8F | SHA256:AABDA820ED8EB8FC6A4769AE709571FBB35EAB43EBFBFD7BA6124B585EF59887 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libcurl.dll | executable | |
MD5:AD0000A640B415FB8C5BB298AA2A8696 | SHA256:4BA5D21777A68DDF0F058EE9840D77A7CCCB460D634EAFB11F2EFDF62AA85FB2 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libcrypto-1_1.dll | executable | |
MD5:C7D6ED5ADBCA175D25A4103AB7CA7884 | SHA256:ADCA39F496EFD541BD706B26CFBC969F43EBC44581F2B69BF140CC666E281CA3 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libevent-2-1-7.dll | executable | |
MD5:2B5333E76FC922FA088B493BBD4B47EF | SHA256:73EC8F2A728E7BB5915BC2FC57495483C00B9C86518EF3DDD5E0004141D3C986 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libssp-0.dll | executable | |
MD5:4F01A1B4F7EFEC9543B2E6E789601D96 | SHA256:2E8F53DCA79A15621E842D121F759B8D9FE022F8BEC0DC3D09F5FA8115E2B192 | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\libevent_core-2-1-7.dll | executable | |
MD5:E9D55170C627C99F7508CAF44E95B03C | SHA256:76E9F4E8CD606D986A146A09D9219BE8D53C0504C11027DFBCA66BE6CB7408BB | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\rdpcIip.exe | executable | |
MD5:9F86955494146873A73F9DF05BFB3D01 | SHA256:3B0285D601232DDEE79A28F3923462F3E4F8C6CEDB809377ED0DA07BA06B651E | |||
| 3556 | WinRAR.exe | C:\Users\admin\Desktop\dell\7z.dll | executable | |
MD5:04AD4B80880B32C94BE8D0886482C774 | SHA256:A1E1D1F0FFF4FCCCFBDFA313F3BDFEA4D3DFE2C2D9174A615BBC39A0A6929338 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
0
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3196 | smcard.exe | 138.201.250.33:9011 | — | Hetzner Online GmbH | DE | unknown |
3196 | smcard.exe | 104.243.38.65:9200 | — | RELIABLESITE | US | unknown |
3196 | smcard.exe | 185.241.208.105:9000 | — | Meverywhere sp. z o.o. | NL | unknown |
3196 | smcard.exe | 65.21.94.13:9001 | — | Hetzner Online GmbH | FI | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3196 | smcard.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 285 |
3196 | smcard.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
3196 | smcard.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 403 |
3196 | smcard.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 868 |
3196 | smcard.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 243 |