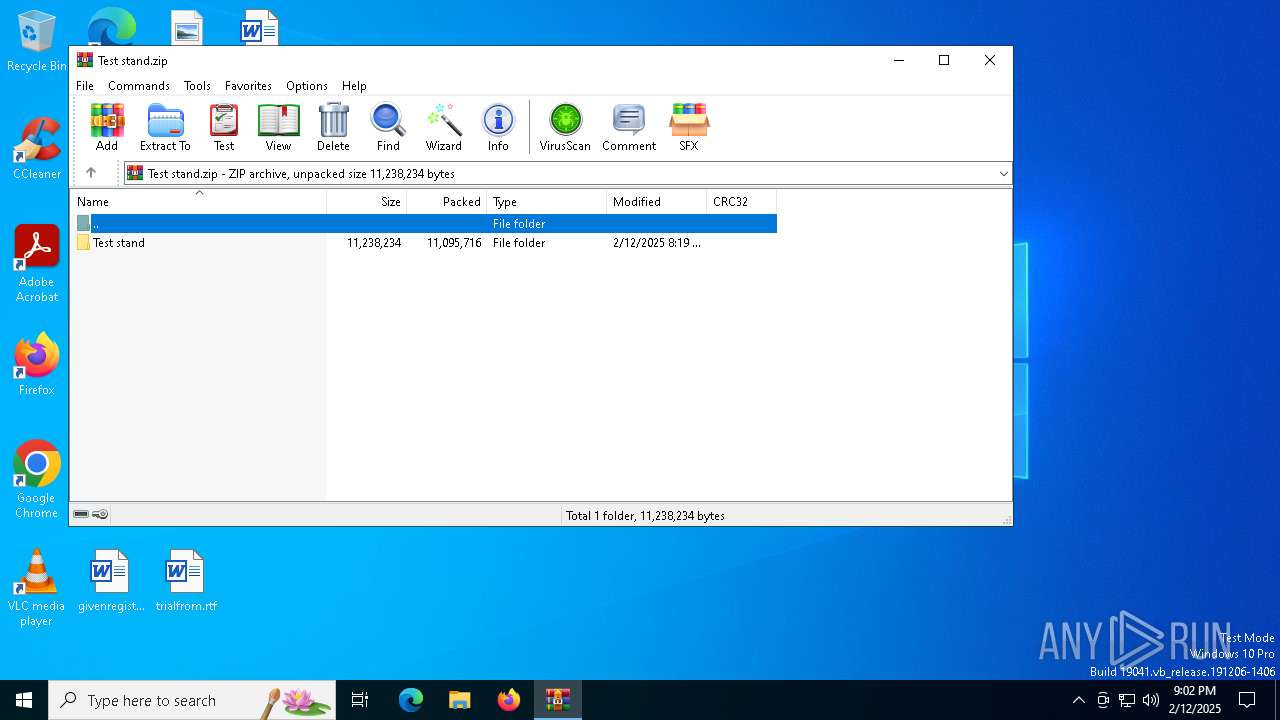
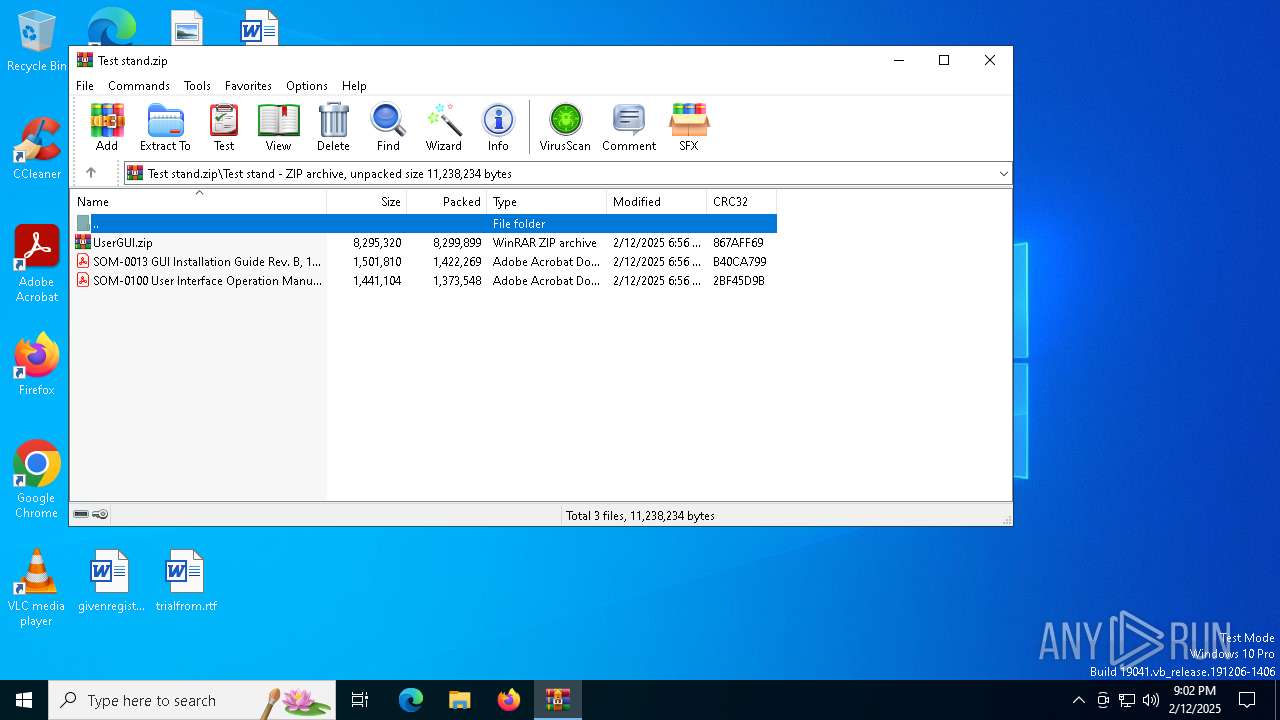
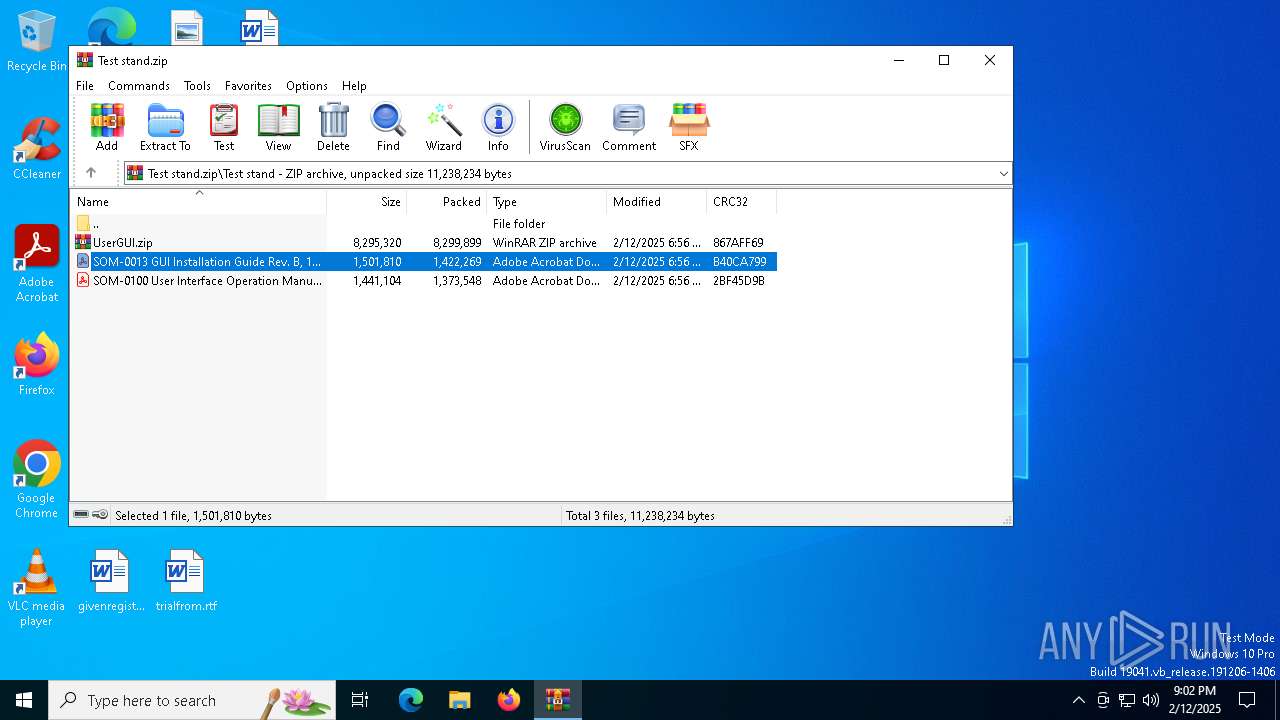
| File name: | Test stand.zip |
| Full analysis: | https://app.any.run/tasks/36aca296-930a-4ad2-982a-96224b9d76e0 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 21:02:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | A07A559973285F2AD43C702C8ADBE145 |
| SHA1: | 1782DDE5A1F59F2E94C4888AFFB8F04A12ED57E8 |
| SHA256: | C84AE33C14D83F2B7A21173265515EEE8407092D6B3D08482D7D50D182F5C000 |
| SSDEEP: | 98304:Hrgpqk/ntNgv5GJxxr1sir/L2MX8PSZkjArQ+T6S/TmeF+rD2+MTbQO0OQAIajif:uGn4bFtu9ef08IDdMMqhKlF8d/c |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6284)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6284)
- WinRAR.exe (PID: 3420)
- UserGUI.exe (PID: 5032)
Application launched itself
- WinRAR.exe (PID: 6284)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6284)
Reads the computer name
- UserGUI.exe (PID: 5032)
Application launched itself
- Acrobat.exe (PID: 6684)
Reads the machine GUID from the registry
- UserGUI.exe (PID: 5032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3420)
Checks supported languages
- UserGUI.exe (PID: 5032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:12 15:19:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Test stand/ |
Total processes
129
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
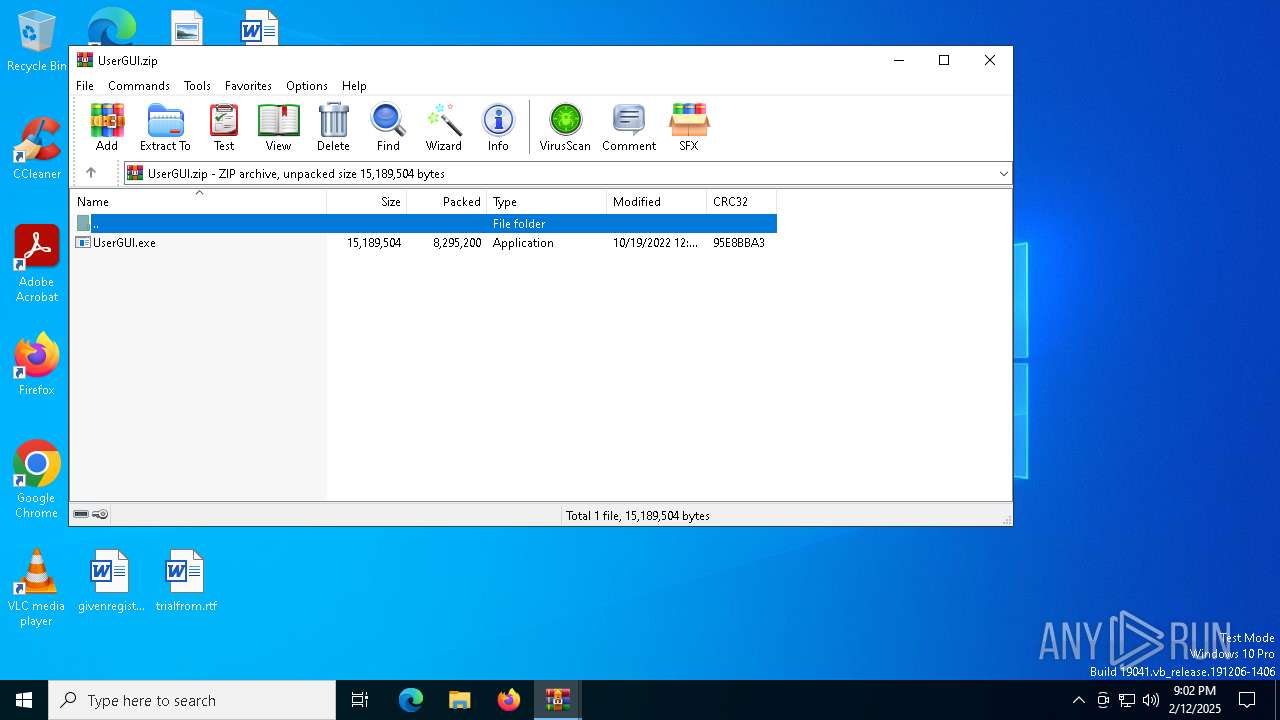
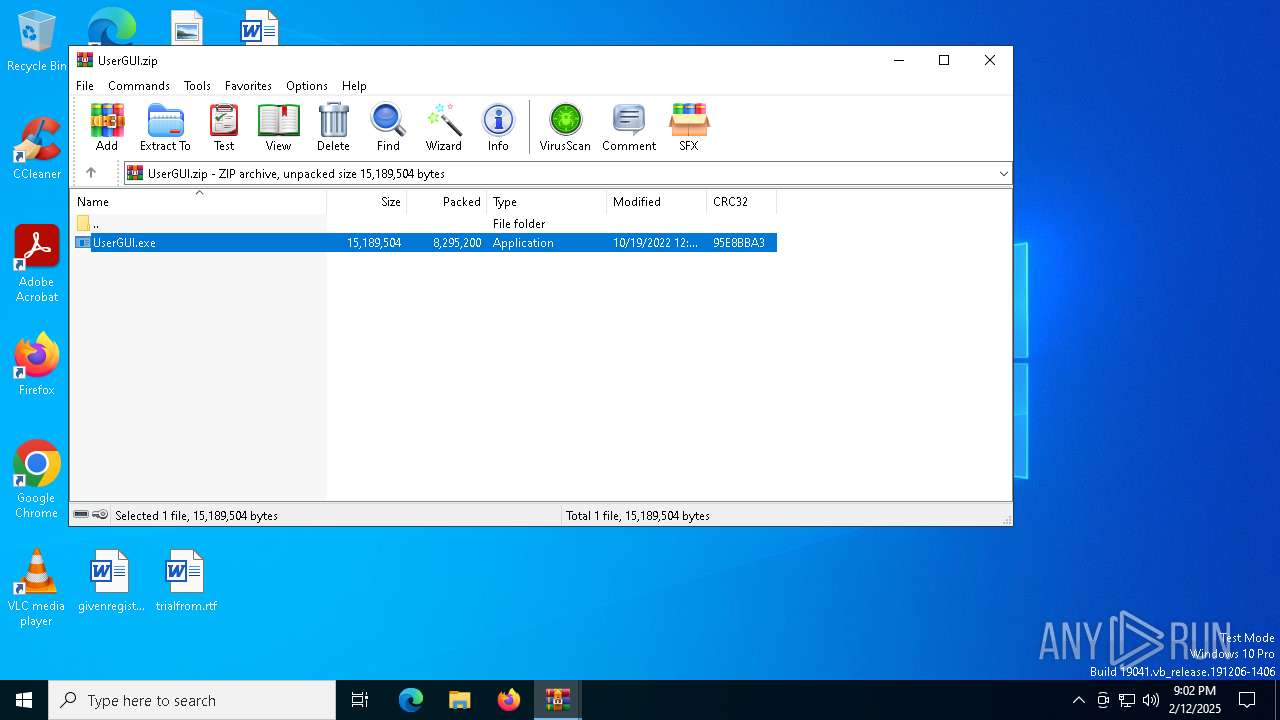
| 3420 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa6284.47620\UserGUI.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
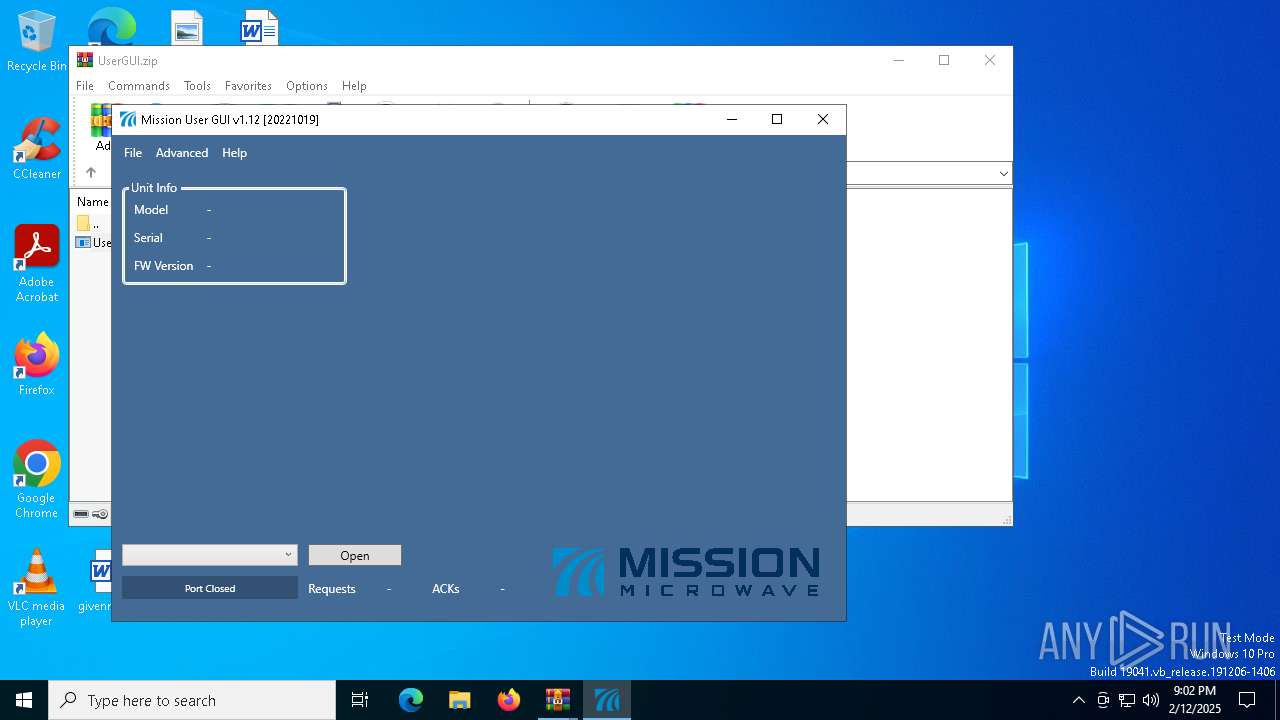
| 5032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3420.47892\UserGUI.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3420.47892\UserGUI.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Mission Microwave Integrity Level: MEDIUM Description: CustomerGUI Version: 1.0.0.0 Modules
| |||||||||||||||
| 6284 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Test stand.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6684 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6284.47025\SOM-0013 GUI Installation Guide Rev. B, 11-01-19.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 6780 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Temp\Rar$DIa6284.47025\SOM-0013 GUI Installation Guide Rev. B, 11-01-19.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
7 324
Read events
7 169
Write events
147
Delete events
8
Modification events
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Test stand.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
| (PID) Process: | (6684) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
Executable files
1
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6284.47025\SOM-0013 GUI Installation Guide Rev. B, 11-01-19.pdf | ||
MD5:71CB12492627172D936A9EE079114F51 | SHA256:CA58B033A60F95B1E83536C60EDD3ECEFED262EFF67080333A7B2927330E84A0 | |||
| 6284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6284.47620\UserGUI.zip | compressed | |
MD5:E0651D14D5B8F9B79578D3A082749800 | SHA256:05FF7E1FA0A84F896655F1A323D89658AD6AB57D34C480821EE2DF7FB925A969 | |||
| 6780 | Acrobat.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\ES_session_store | binary | |
MD5:A036990E2ACA54320B3E9EB3AE28F57F | SHA256:590DFE02709F48F0BA266CF006F527CEC4DE8B5D0B8BAA23E9A0A672B4936FD1 | |||
| 6780 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 6780 | Acrobat.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\ES_session_storei | binary | |
MD5:85BFE10CFC63D8E2880F7CBF3BAC8D2B | SHA256:32D02B57E2FDE7E7CDDD755DDA1B6C2DFEABDB09F6AE5D1B697F3810431CD9AB | |||
| 6780 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\IconCacheAcro65536.dat | binary | |
MD5:0210A04218BE6224CA993ACAE76B8B0D | SHA256:24D2B8642FBA0DD37F03234C32C379A2AC25584F57D4478497D02436EBADE70B | |||
| 3420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3420.47892\UserGUI.exe | executable | |
MD5:8A83520FB0DE61E2539E358B04FA5AB7 | SHA256:DD3A550468E781A33388BFCEDF7C78FEF1B678C25F60F3758DBEEF383B9DEA60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 62.115.252.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 62.115.252.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.85.144.229:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.85.144.229:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 184.85.144.229:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 184.85.144.229:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.42.70.18:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2220 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 80.239.137.138:443 | www.bing.com | Telia Company AB | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 62.115.252.162:80 | crl.microsoft.com | Telia Company AB | ES | whitelisted |
— | — | 184.85.144.229:80 | www.microsoft.com | AKAMAI-AS | FI | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 23.42.70.18:80 | ocsp.digicert.com | AKAMAI-AS | JP | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |