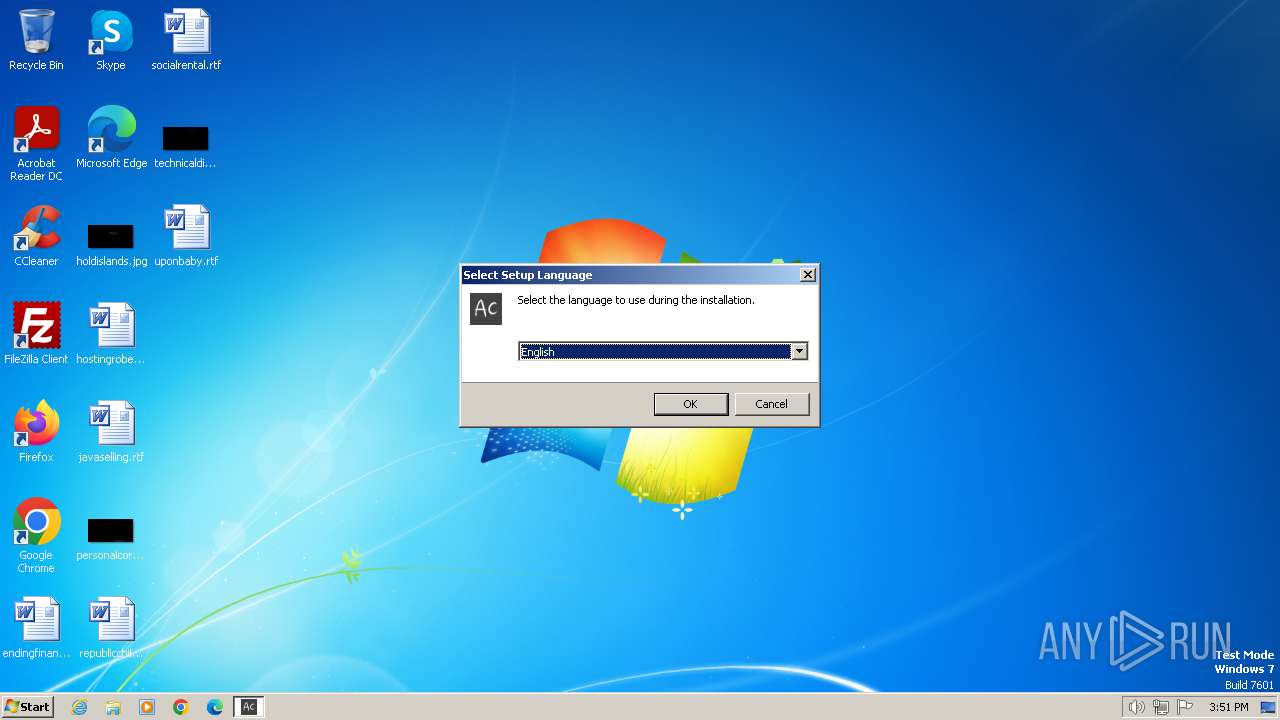
| File name: | ac-11_30.exe |
| Full analysis: | https://app.any.run/tasks/24ed1356-dfc2-4ca1-b6ef-afc3647d0ab6 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2024, 15:50:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FDACA0B08450AA333665BE8E76453999 |
| SHA1: | 1B5991E4957E6CABBC98E7462C5198F624A0E69B |
| SHA256: | C84A505D381A2B6959CBC488948B315D797E73F84C7D40474395F04950F1334A |
| SSDEEP: | 98304:3+cD4dn/BU9AOdS85aSMQZr+05+IHt30/V1SA4gnxkaM/oAkoXFbWAU27VYZcXEa:/K2sW72h545 |
MALICIOUS
Drops the executable file immediately after the start
- ac-11_30.tmp (PID: 532)
- ac-11_30.exe (PID: 548)
- ac-11_30.exe (PID: 2036)
Registers / Runs the DLL via REGSVR32.EXE
- ac-11_30.tmp (PID: 532)
SUSPICIOUS
Executable content was dropped or overwritten
- ac-11_30.tmp (PID: 532)
- ac-11_30.exe (PID: 2036)
- ac-11_30.exe (PID: 548)
Reads the Windows owner or organization settings
- ac-11_30.tmp (PID: 532)
INFO
Checks supported languages
- ac-11_30.tmp (PID: 532)
- ac-11_30.tmp (PID: 1404)
- ac-11_30.exe (PID: 548)
- ac-11_30.exe (PID: 2036)
- acmain.exe (PID: 1496)
Create files in a temporary directory
- ac-11_30.exe (PID: 548)
- ac-11_30.exe (PID: 2036)
- ac-11_30.tmp (PID: 532)
Reads the computer name
- ac-11_30.tmp (PID: 532)
- ac-11_30.tmp (PID: 1404)
Creates files in the program directory
- ac-11_30.tmp (PID: 532)
Manual execution by a user
- acmain.exe (PID: 1496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1130.2023.10.14 |
| ProductVersionNumber: | 1130.2023.10.14 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Romain Petges |
| FileDescription: | Attribute Changer Installer for 32/64 bit Windows |
| FileVersion: | 1130.2023.10.14 |
| LegalCopyright: | Copyright 1999 - 2023 Romain Petges |
| OriginalFileName: | |
| ProductName: | Attribute Changer |
| ProductVersion: | 11.30 |
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\AppData\Local\Temp\is-H3CES.tmp\ac-11_30.tmp" /SL5="$501AC,4434317,800256,C:\Users\admin\AppData\Local\Temp\ac-11_30.exe" /SPAWNWND=$501B2 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\is-H3CES.tmp\ac-11_30.tmp | ac-11_30.exe | ||||||||||||
User: admin Company: Romain Petges Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\ac-11_30.exe" /SPAWNWND=$501B2 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\ac-11_30.exe | ac-11_30.tmp | ||||||||||||
User: admin Company: Romain Petges Integrity Level: HIGH Description: Attribute Changer Installer for 32/64 bit Windows Exit code: 0 Version: 1130.2023.10.14 Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\AppData\Local\Temp\is-TAAKU.tmp\ac-11_30.tmp" /SL5="$301AA,4434317,800256,C:\Users\admin\AppData\Local\Temp\ac-11_30.exe" | C:\Users\admin\AppData\Local\Temp\is-TAAKU.tmp\ac-11_30.tmp | — | ac-11_30.exe | |||||||||||
User: admin Company: Romain Petges Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Attribute Changer\acmain.exe" | C:\Program Files\Attribute Changer\acmain.exe | — | explorer.exe | |||||||||||
User: admin Company: Romain Petges Integrity Level: MEDIUM Description: Attribute Changer Exit code: 0 Version: 1130.2023.10.14 Modules
| |||||||||||||||
| 1632 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\Attribute Changer\acshell.dll" | C:\Windows\System32\regsvr32.exe | — | ac-11_30.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Local\Temp\ac-11_30.exe" | C:\Users\admin\AppData\Local\Temp\ac-11_30.exe | explorer.exe | ||||||||||||
User: admin Company: Romain Petges Integrity Level: MEDIUM Description: Attribute Changer Installer for 32/64 bit Windows Exit code: 0 Version: 1130.2023.10.14 Modules
| |||||||||||||||
Total events
1 385
Read events
1 385
Write events
0
Delete events
0
Modification events
Executable files
8
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | ac-11_30.exe | C:\Users\admin\AppData\Local\Temp\is-TAAKU.tmp\ac-11_30.tmp | executable | |
MD5:DD55A747F5A14AEF9181095092BFDCF8 | SHA256:1C610132C3735B4FFF0CE7EC39BFF0085AF3F2B1103366819437951B592E5245 | |||
| 548 | ac-11_30.exe | C:\Users\admin\AppData\Local\Temp\is-H3CES.tmp\ac-11_30.tmp | executable | |
MD5:DD55A747F5A14AEF9181095092BFDCF8 | SHA256:1C610132C3735B4FFF0CE7EC39BFF0085AF3F2B1103366819437951B592E5245 | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\acmain.exe | executable | |
MD5:F410671213B4F486058574997182CA5C | SHA256:C03DC800F40E8E66B9F620AC53DCA693B5B5CF551C2F4808A7F3CF952D9FDBAB | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\is-J2RKU.tmp | executable | |
MD5:F410671213B4F486058574997182CA5C | SHA256:C03DC800F40E8E66B9F620AC53DCA693B5B5CF551C2F4808A7F3CF952D9FDBAB | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\unins000.exe | executable | |
MD5:988E15050EFF81FBF20879A6FBC84F9E | SHA256:1EC4F3C740722E1768252D310B38A68CBF5F5DD3F5BC2246E52256FE09148F16 | |||
| 532 | ac-11_30.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Attribute Changer\Attribute Changer.lnk | binary | |
MD5:0E2E2FE653D9EB5E023CA4AB7071E86B | SHA256:C94F234BCECACA8801B5CF6EEF3706D0CCCF683CE3F28A8FE8B578B0C251601E | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\is-HVGTE.tmp | executable | |
MD5:77D5E6700743CC1C7899B229F594B00C | SHA256:2E64F14957FEAB63EA0F8D300885B5BD9EF4110D099CED93197536BD46AAF01C | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\is-31I7Q.tmp | ||
MD5:E8966B9D36E2B488E738A2D04CE44715 | SHA256:2EDDE26D6CBD9688353B559788C3856A76622AE377F687ECD75A25264A05A9CD | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\ac.pdf | ||
MD5:E8966B9D36E2B488E738A2D04CE44715 | SHA256:2EDDE26D6CBD9688353B559788C3856A76622AE377F687ECD75A25264A05A9CD | |||
| 532 | ac-11_30.tmp | C:\Program Files\Attribute Changer\unins000.dat | binary | |
MD5:E9D03690CFBAFA2A80E9BF91966A01ED | SHA256:4D84EB3AF861A4C43D2167A3FAB92AF9A6B826D767F4CD2DB25F1A46D6097A4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |