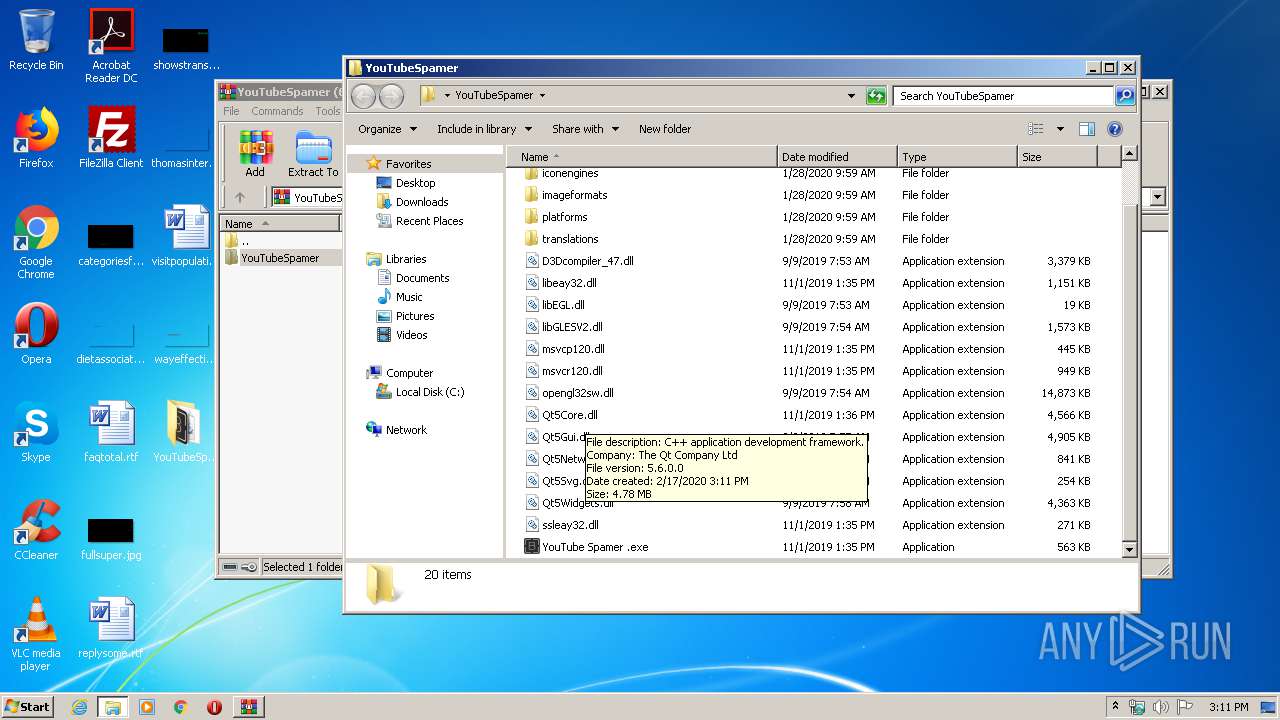
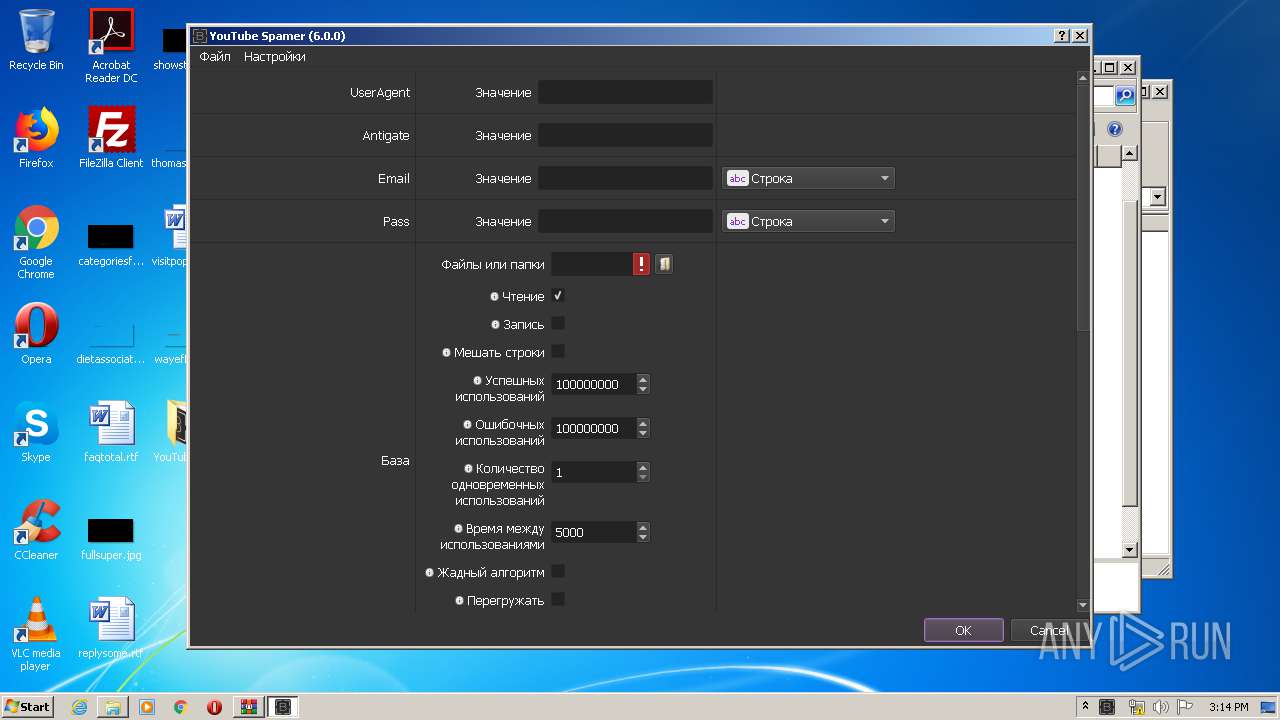
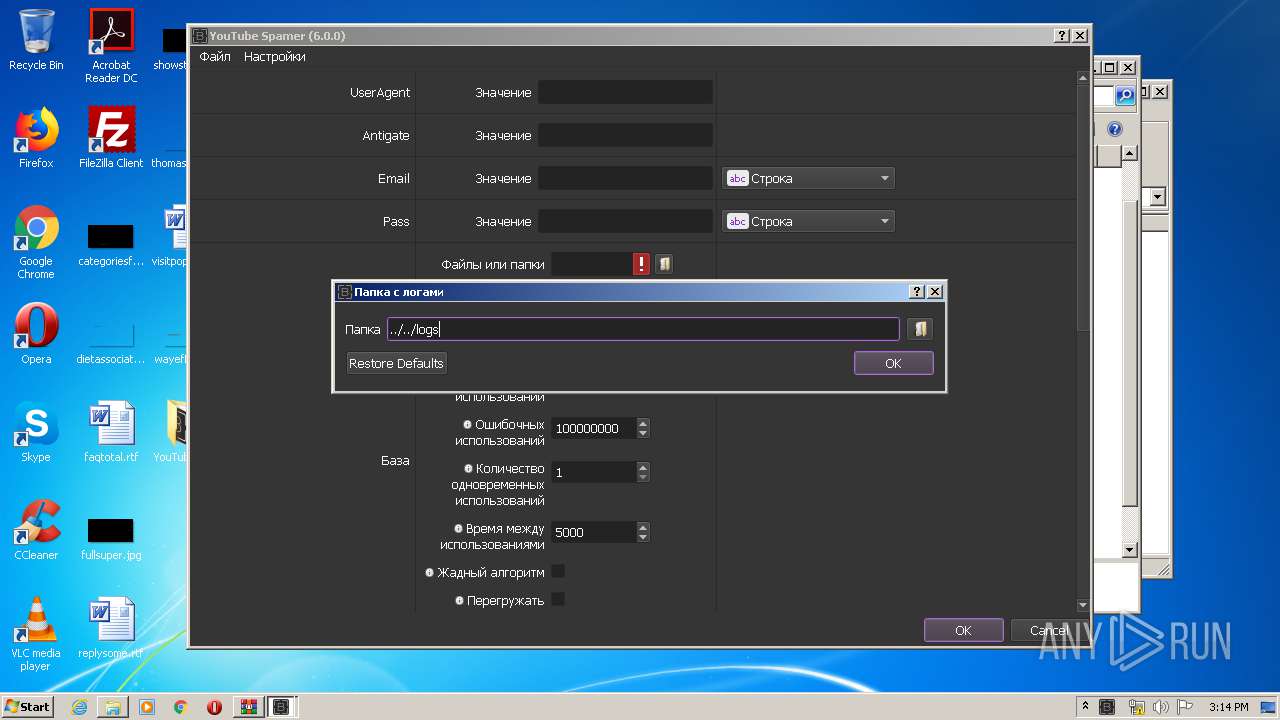
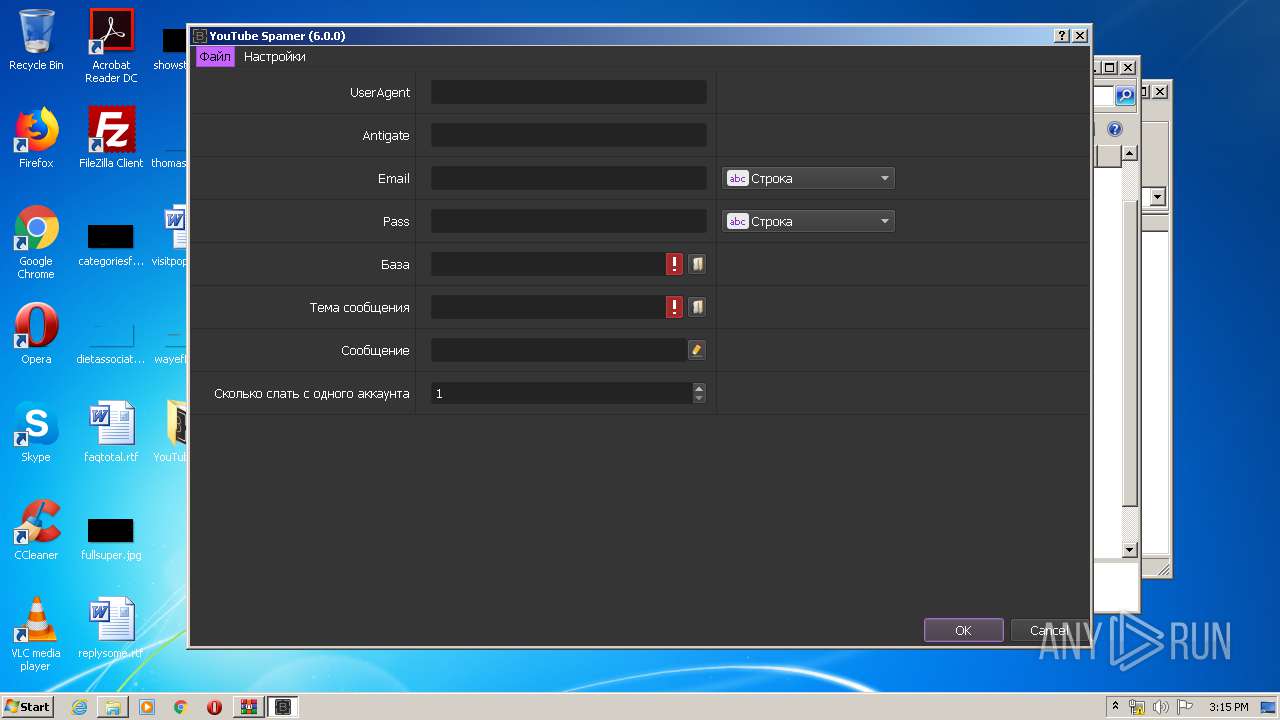
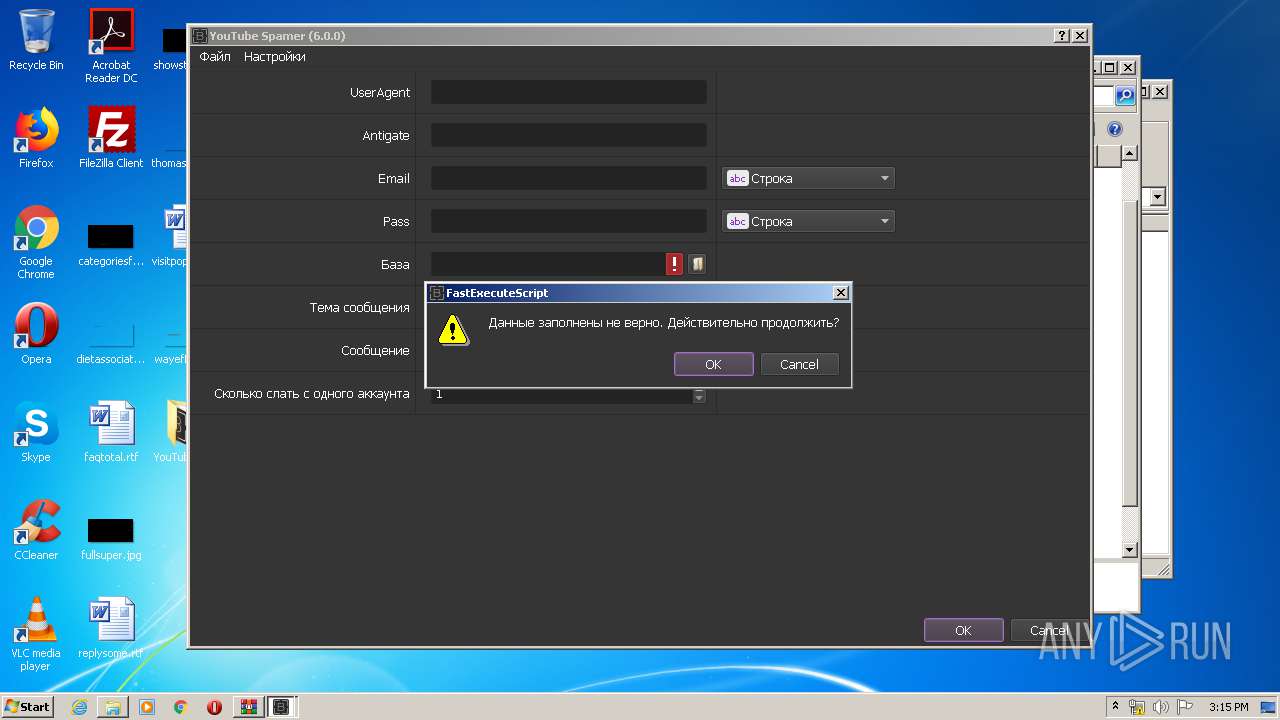
| File name: | YouTubeSpamer (6).rar |
| Full analysis: | https://app.any.run/tasks/076fa19a-b6cf-4f82-abd3-a0f98ee9b6fc |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2020, 15:10:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FCC85A67D39CB1207F04514A208E18A5 |
| SHA1: | 7FEDE22FA52A3AEABB703937AAA1502E74F4D2D5 |
| SHA256: | C846DC5262AC67CFEF11DB41C6105F1B6B076138BCACDF78BD6AD25617D0909C |
| SSDEEP: | 393216:76EhpdqxloSSM5jT8lCfAsavKF+BTThKglD1Bb1szC+:WEhGxlnSojolCZ2TThKglfhm |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
- explorer.exe (PID: 372)
- YouTube Spamer .exe (PID: 2880)
- FastExecuteScript.exe (PID: 2240)
- SearchProtocolHost.exe (PID: 1556)
- Worker.exe (PID: 2068)
- Worker.exe (PID: 3088)
- Worker.exe (PID: 3276)
- Worker.exe (PID: 2128)
Application was dropped or rewritten from another process
- YouTube Spamer .exe (PID: 2880)
- FastExecuteScript.exe (PID: 2240)
- Worker.exe (PID: 3276)
- Worker.exe (PID: 2068)
- Worker.exe (PID: 3088)
- Worker.exe (PID: 2128)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3828)
- YouTube Spamer .exe (PID: 2880)
Application launched itself
- Worker.exe (PID: 2068)
Creates files in the user directory
- explorer.exe (PID: 372)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3828)
- YouTube Spamer .exe (PID: 2880)
Reads settings of System Certificates
- YouTube Spamer .exe (PID: 2880)
Reads the hosts file
- Worker.exe (PID: 2068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
47
Monitored processes
10
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | .\Worker\Worker.exe ru --UseFlash 0 --ProxyTunneling 1 --SkipFrames 1 --unique-process-id=fCrhOolt --Profile prof/ev1XEoFN --Extensions "" rkkxevcoqo none 2240 | C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe | FastExecuteScript.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe" --type=gpu-process --disable-gpu-sandbox --no-sandbox --log-file="C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\debug.log" --log-severity=disable --lang=en-US --parent-process-id=2068 --unique-process-id=fCrhOolt --gpu-preferences=KAAAAAAAAACAA4BAAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --use-gl=swiftshader-webgl --log-file="C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\debug.log" --log-severity=disable --lang=en-US --parent-process-id=2068 --unique-process-id=fCrhOolt --service-request-channel-token=13918685148648314337 --mojo-platform-channel-handle=2028 /prefetch:2 | C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe | — | Worker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2240 | appslocal\e3b0c442\SID9957e8f4\engine\FastExecuteScript.exe | C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\FastExecuteScript.exe | — | YouTube Spamer .exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2880 | "C:\Users\admin\Desktop\YouTubeSpamer\YouTube Spamer .exe" | C:\Users\admin\Desktop\YouTubeSpamer\YouTube Spamer .exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3088 | "C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe" --type=renderer --no-sandbox --disable-gpu-compositing --service-pipe-token=7558175544363531900 --lang=en-US --log-file="C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\debug.log" --log-severity=disable --parent-process-id=2068 --unique-process-id=fCrhOolt --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7558175544363531900 --renderer-client-id=2 --mojo-platform-channel-handle=1248 /prefetch:1 | C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe | — | Worker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe" --type=gpu-process --no-sandbox --log-file="C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\debug.log" --log-severity=disable --lang=en-US --parent-process-id=2068 --unique-process-id=fCrhOolt --gpu-preferences=KAAAAAAAAACAA4BAAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --use-gl=swiftshader-webgl --log-file="C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\debug.log" --log-severity=disable --lang=en-US --parent-process-id=2068 --unique-process-id=fCrhOolt --service-request-channel-token=13677222192036164990 --mojo-platform-channel-handle=1216 /prefetch:2 | C:\Users\admin\Desktop\YouTubeSpamer\appslocal\e3b0c442\SID9957e8f4\engine\Worker\Worker.exe | — | Worker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3548 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\YouTubeSpamer (6).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
4 662
Read events
4 450
Write events
210
Delete events
2
Modification events
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\YouTubeSpamer (6).rar | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
184
Suspicious files
43
Text files
814
Unknown types
232
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\iconengines\qsvgicon.dll | executable | |
MD5:90BB882A4B5E3427F328259530AA1B3B | SHA256:B2B420AA1805D8B5DC15CCB74DD664D10BD6BA422743F5043A557A701C8A1778 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\D3Dcompiler_47.dll | executable | |
MD5:E6945CCEEFC0A122833576A5FC5F88F4 | SHA256:FB8D0049F5DD5858C3B1DA4836FB4B77D97B72D67AD951EDB48F1A3E087EC2B1 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\bearer\qgenericbearer.dll | executable | |
MD5:DBA35D31C2B6797C8A4D38AE27D68E6E | SHA256:086D6BA24F34A269856C4E0159A860657590D05AABB2530247E685543B34C52F | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\data\project.xml | xml | |
MD5:EC83791BEA128F390C57B15823213641 | SHA256:9957E8F4587E83BDCC6B84715E9CFECBA036FEA0055A4AB19105C2DA4992BF22 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\imageformats\qwbmp.dll | executable | |
MD5:131A58669BE7B3850C46D8E841DA5D4E | SHA256:043F3ACF1DC4F4780721DF106046C597262D7344C4B4894E0BE55858B9FAD00E | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\imageformats\qtga.dll | executable | |
MD5:D0604A5F13B32A08D5FA5BD887F869A6 | SHA256:2B6444D2A8146A066109CA19618CEEE98444127A5B422C14635AB837887E55BF | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\imageformats\qdds.dll | executable | |
MD5:3FDB8D8407CCCFAA0290036CC0107906 | SHA256:3A71A119EEABCE867B57636070ADEB057443A6EC262BE1360F344CB3905545DB | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\imageformats\qicns.dll | executable | |
MD5:52C6978203CA20BEEAD6E8872E80D39F | SHA256:E665F3519309BAE42E0E62F459ECC511701DDDDF94599EBFD213D0A71775C462 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\imageformats\qsvg.dll | executable | |
MD5:2831B334B8EDF842CE273B3DD0ACE1F8 | SHA256:6BAE9AF6A7790FBDEE87B7EFA53D31D8AFF0AB49BDAAEFD3FB87A8CC7D4E8A90 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.28937\YouTubeSpamer\bearer\qnativewifibearer.dll | executable | |
MD5:A8BCA50F7966F578B127D1E24FC2430F | SHA256:C209D080A62F5E67DDC01A3AE6B4F9B103FAF4104C93B7DBB5FFA8D548BF0CD5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2880 | YouTube Spamer .exe | 146.185.145.186:443 | bablosoft.com | Digital Ocean, Inc. | NL | suspicious |
2068 | Worker.exe | 216.58.207.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2068 | Worker.exe | 172.217.23.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2068 | Worker.exe | 172.217.22.37:443 | mail.google.com | Google Inc. | US | whitelisted |
2068 | Worker.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bablosoft.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
mail.google.com |
| shared |