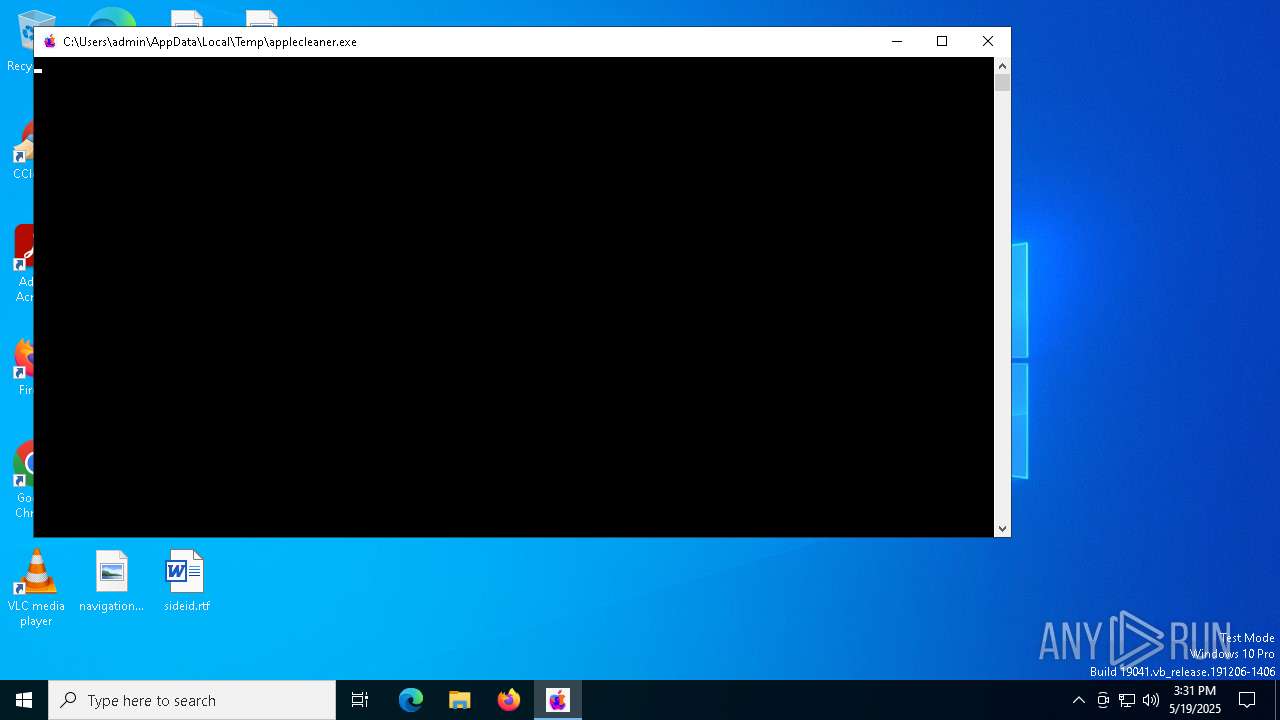
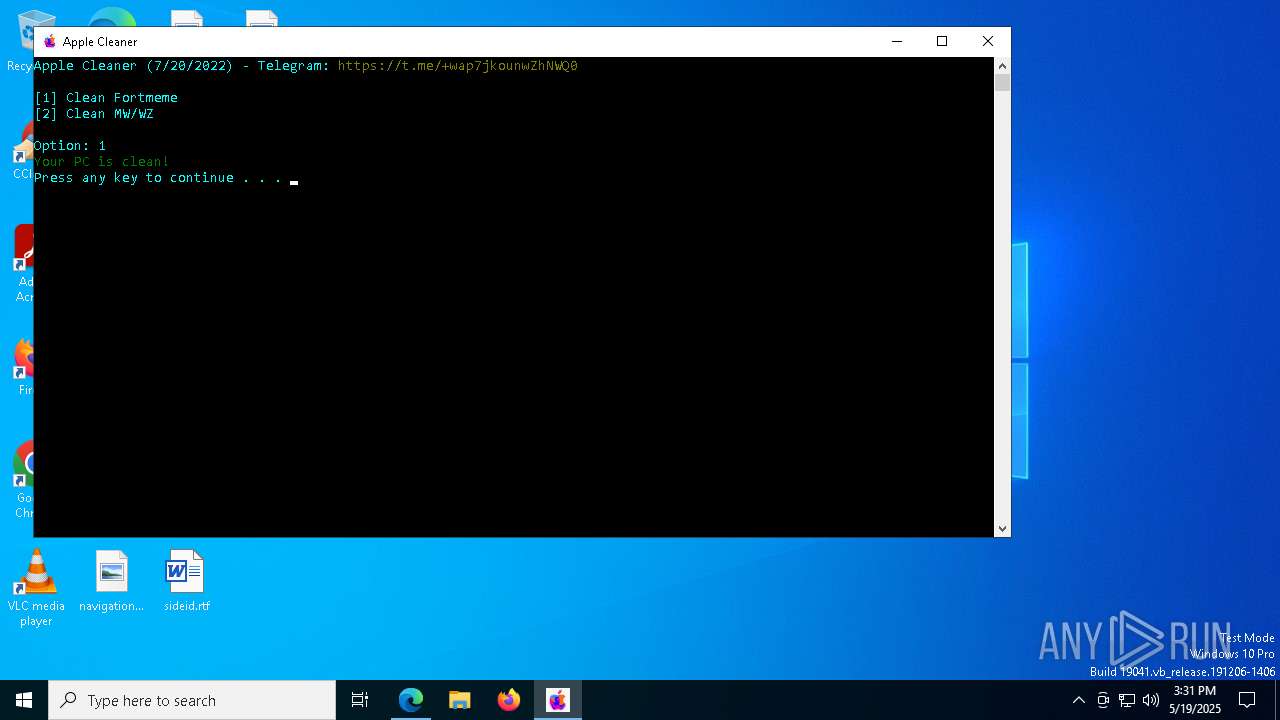
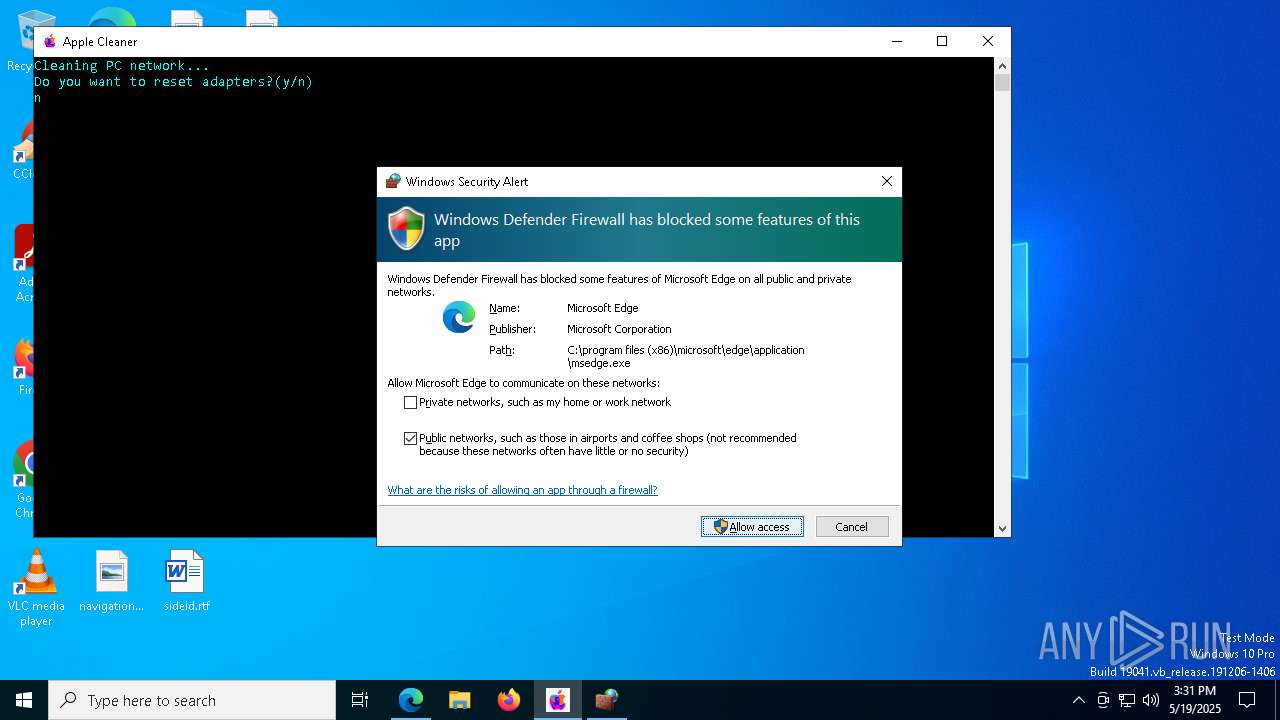
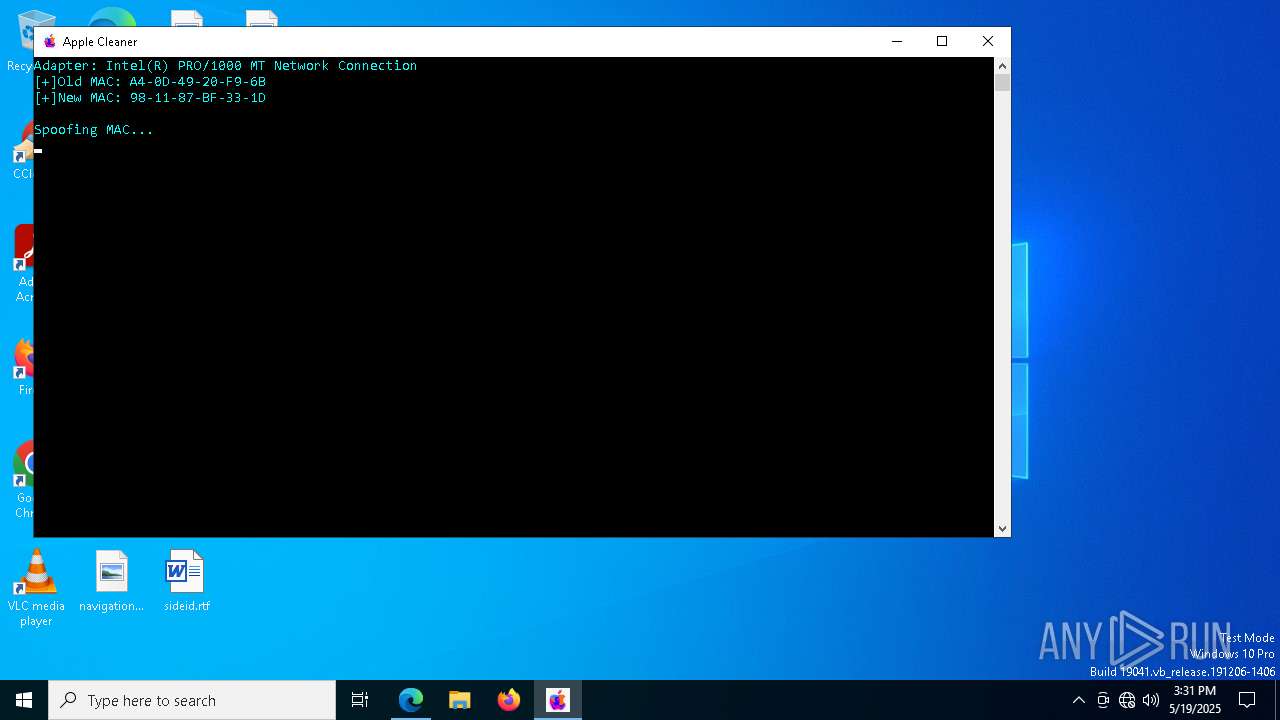
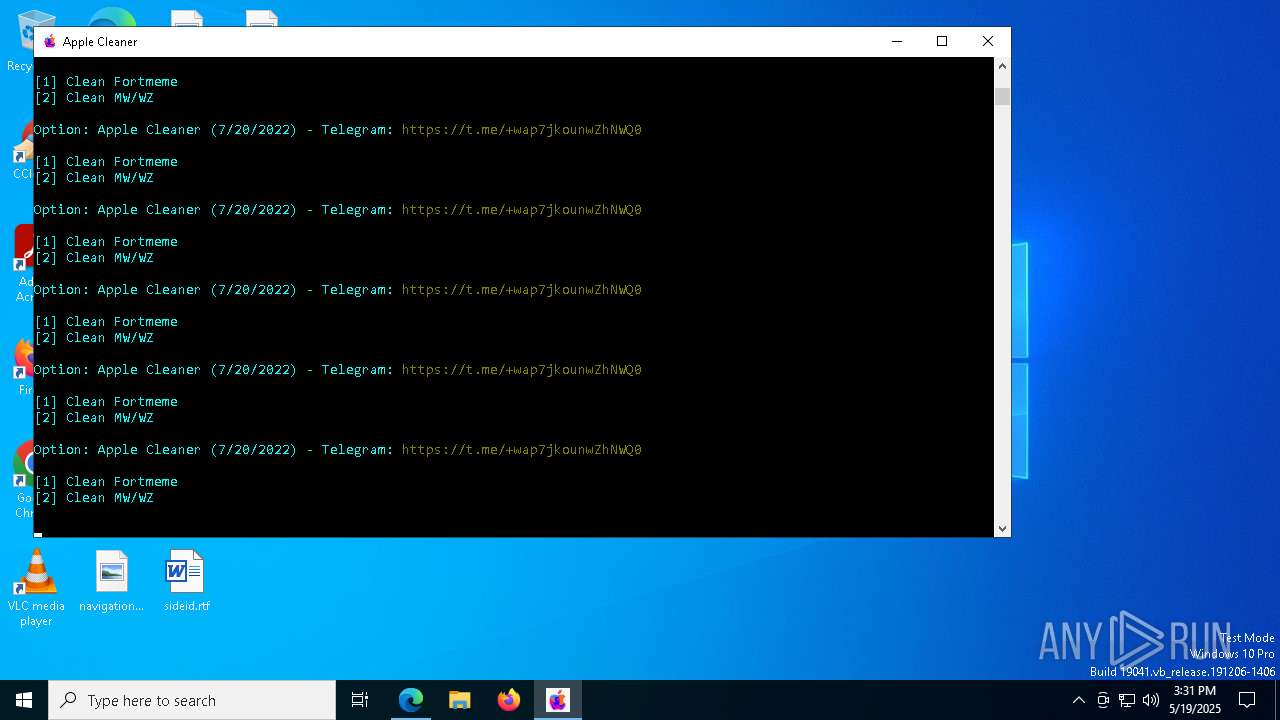
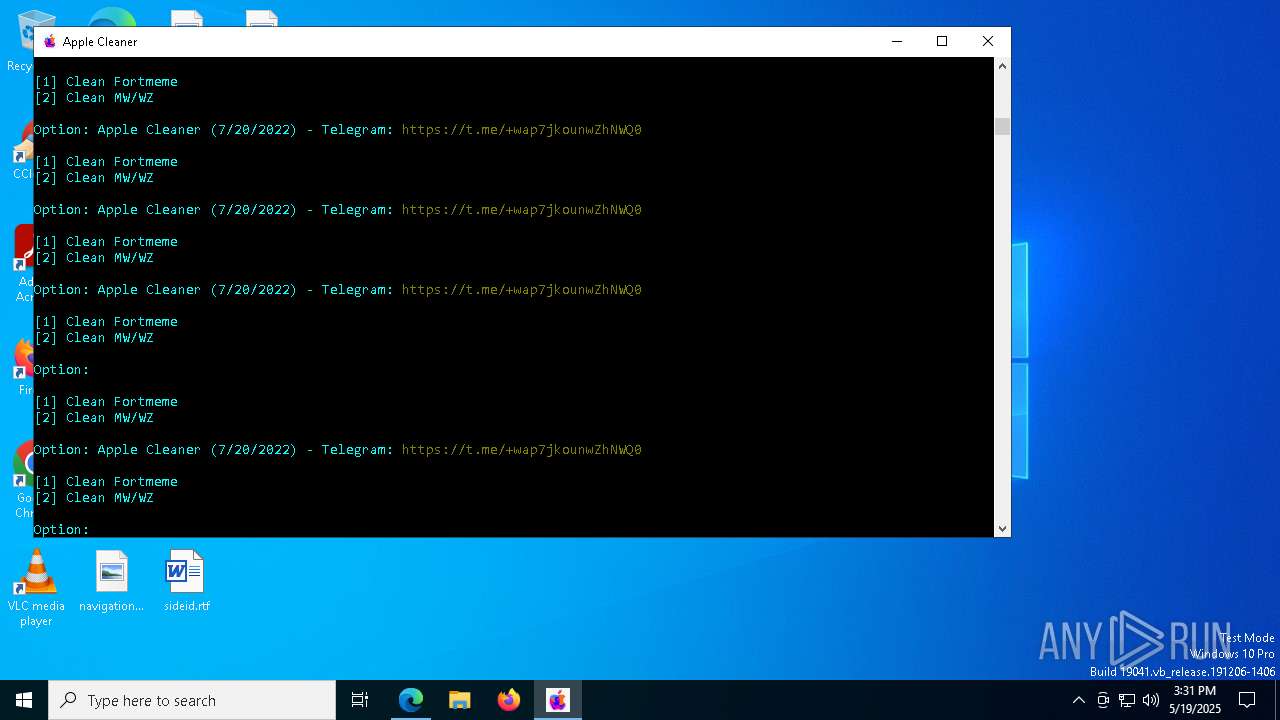
| File name: | applecleaner.exe |
| Full analysis: | https://app.any.run/tasks/292a1a6f-319e-4b89-961a-f13440054003 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 15:31:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 12 sections |
| MD5: | BA268B881BCCD2784FE98289EEC8AD72 |
| SHA1: | 0C4E7F1473FB7AB22427480C3D784B6E0E404956 |
| SHA256: | C83921C8DDA800EF24EBE873EC175617110DC9DEB2629D1107F219CA30CAECE3 |
| SSDEEP: | 49152:98jzvhuGMsOTenal2tV594MzhJD3TMgwQiPRxksa2EQUFO0JIbn6/ubWYY725hXQ:9QFXlbnal2XDhZRwRVsE0JDoWYJPXLk |
MALICIOUS
Changes the autorun value in the registry
- netsh.exe (PID: 9212)
- applecleaner.exe (PID: 7224)
Scans artifacts that could help determine the target
- applecleaner.exe (PID: 7224)
SUSPICIOUS
Hides command output
- cmd.exe (PID: 7296)
- cmd.exe (PID: 7416)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 9196)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 4652)
- cmd.exe (PID: 920)
- cmd.exe (PID: 8272)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 8524)
- cmd.exe (PID: 8700)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 8756)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 8924)
- cmd.exe (PID: 8780)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 7532)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 8576)
Reads the BIOS version
- applecleaner.exe (PID: 7224)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7296)
- cmd.exe (PID: 7416)
- cmd.exe (PID: 7472)
Starts CMD.EXE for commands execution
- applecleaner.exe (PID: 7224)
Detected use of alternative data streams (AltDS)
- applecleaner.exe (PID: 7224)
Reads the Windows owner or organization settings
- applecleaner.exe (PID: 7224)
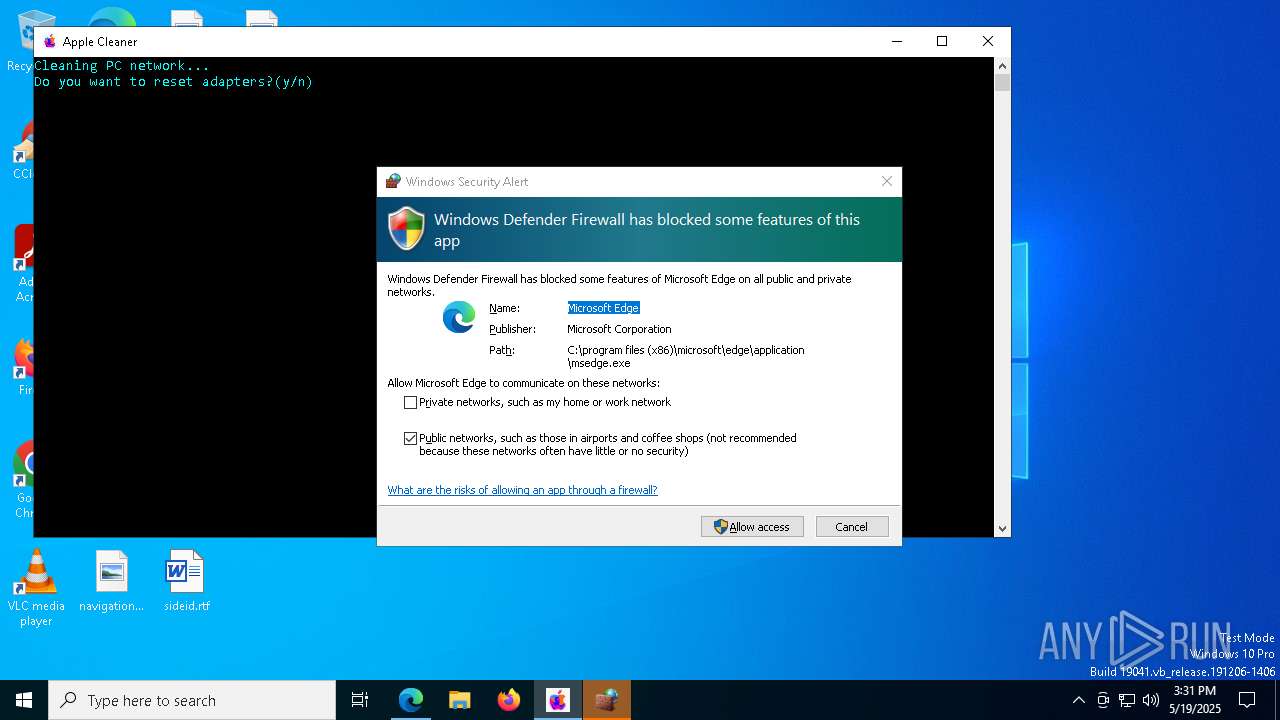
Suspicious use of NETSH.EXE
- cmd.exe (PID: 9196)
- cmd.exe (PID: 920)
- cmd.exe (PID: 4652)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 8272)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 2268)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 5400)
- cmd.exe (PID: 6576)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 8524)
Process uses NBTSTAT to discover network configuration
- cmd.exe (PID: 8700)
Process uses ARP to discover network configuration
- cmd.exe (PID: 8708)
Uses WMIC.EXE
- cmd.exe (PID: 8924)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 7532)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 5400)
INFO
Checks supported languages
- applecleaner.exe (PID: 7224)
- identity_helper.exe (PID: 8600)
Process checks whether UAC notifications are on
- applecleaner.exe (PID: 7224)
Application launched itself
- msedge.exe (PID: 8000)
- msedge.exe (PID: 5780)
Reads the machine GUID from the registry
- applecleaner.exe (PID: 7224)
Reads Windows Product ID
- applecleaner.exe (PID: 7224)
Reads the computer name
- applecleaner.exe (PID: 7224)
- identity_helper.exe (PID: 8600)
Reads Environment values
- identity_helper.exe (PID: 8600)
- applecleaner.exe (PID: 7224)
Themida protector has been detected
- applecleaner.exe (PID: 7224)
Disables trace logs
- netsh.exe (PID: 8060)
- netsh.exe (PID: 7660)
- netsh.exe (PID: 7420)
- netsh.exe (PID: 2240)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8884)
- WMIC.exe (PID: 9040)
- WMIC.exe (PID: 9168)
- WMIC.exe (PID: 7832)
- WMIC.exe (PID: 2268)
- WMIC.exe (PID: 2040)
Manual execution by a user
- msedge.exe (PID: 5780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:07:20 21:22:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.31 |
| CodeSize: | 146432 |
| InitializedDataSize: | 101376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5fa0b0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
241
Monitored processes
105
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | C:\WINDOWS\system32\cmd.exe /c NETSH INTERFACE IPV4 RESET >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2192 --field-trial-handle=2332,i,6982318537684753025,3153679744867941231,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ac,0x2b0,0x2b4,0x2a8,0x2a0,0x7ffc89985fd8,0x7ffc89985fe4,0x7ffc89985ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1676 | "C:\Users\admin\AppData\Local\Temp\applecleaner.exe" | C:\Users\admin\AppData\Local\Temp\applecleaner.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1912 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7584 --field-trial-handle=2332,i,6982318537684753025,3153679744867941231,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2040 | wmic path Win32_PNPEntity where "caption like '%bluetooth%' AND DeviceID like 'USB\\%'" call disable | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | NETSH INT RESET ALL | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\system32\cmd.exe /c NETSH INT RESET ALL >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | WMIC PATH WIN32_NETWORKADAPTER WHERE PHYSICALADAPTER=TRUE CALL ENABLE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\system32\cmd.exe /c WMIC PATH WIN32_NETWORKADAPTER WHERE PHYSICALADAPTER=TRUE CALL ENABLE >nul 2>&1 | C:\Windows\System32\cmd.exe | — | applecleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 021
Read events
11 468
Write events
403
Delete events
150
Modification events
| (PID) Process: | (8000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (8000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (8000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7960) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7960) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7960) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7960) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7224) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography |
| Operation: | write | Name: | MachineGuid |
Value: d2f0ff8c-97b3-cf12-013c-35efce83a0f7 | |||
| (PID) Process: | (7224) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | InstallTime |
Value: A13300008D660000 | |||
| (PID) Process: | (7224) applecleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | InstallDate |
Value: F02B000005180000 | |||
Executable files
10
Suspicious files
223
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10d757.TMP | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10d766.TMP | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:2D0657D50CB7EAE55511281640A49D21 | SHA256:06E35B56A2AEFF1F77AC5DC93A6D5DD1961EF50876D932854979CDE8A7DFFF37 | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10d795.TMP | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:798EBA8558D3655BC5D2B61984B3BF12 | SHA256:04EB76D36567C4FD801C5583AA34A18A081D9030BAE3034D8F81D419A797221D | |||
| 8000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:3EB0134C4F836E10B6981F95ABB399C5 | SHA256:2BC73227BA745CB5B677107F673A573A4CC737BE576C5B515F3DD820D1988AD5 | |||
| 5780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\7d8fbc8e-1947-4adc-a2f6-e3177cd1368d.tmp | binary | |
MD5:2D0657D50CB7EAE55511281640A49D21 | SHA256:06E35B56A2AEFF1F77AC5DC93A6D5DD1961EF50876D932854979CDE8A7DFFF37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
44
DNS requests
38
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
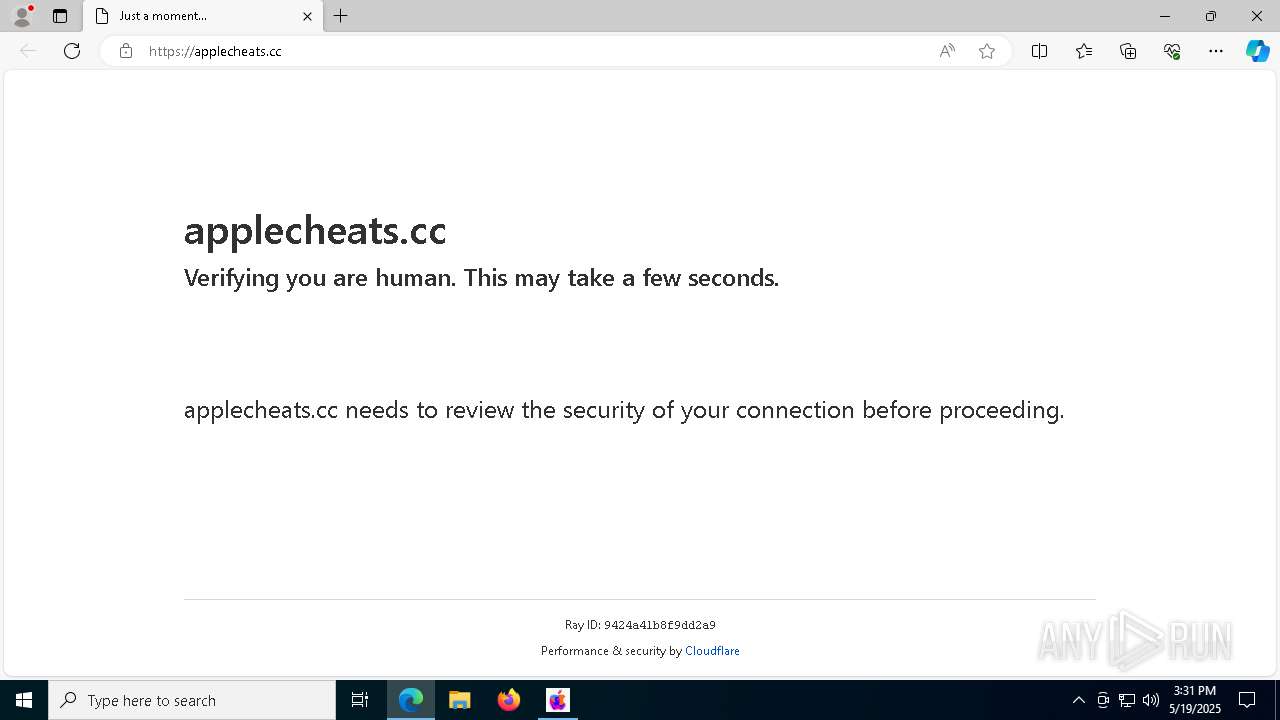
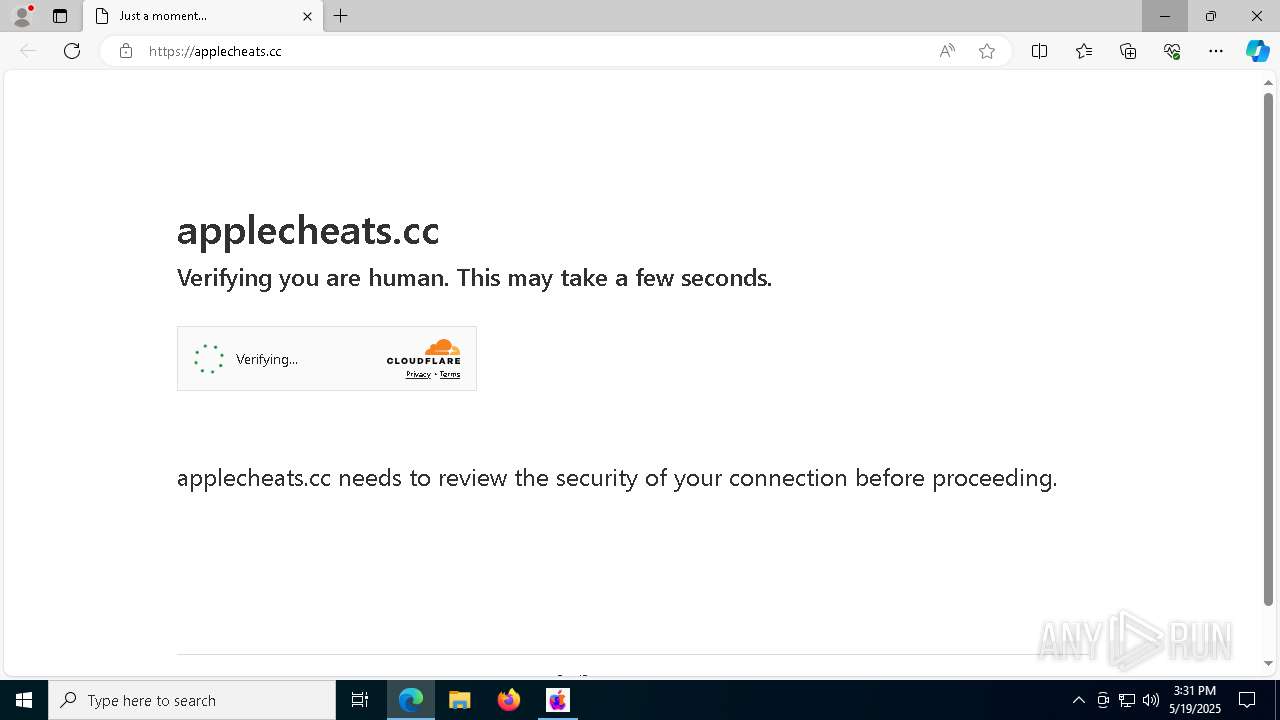
5640 | msedge.exe | 104.21.32.1:443 | applecheats.cc | — | — | unknown |
5640 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
applecheats.cc |
| unknown |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5640 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
5640 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
5640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |