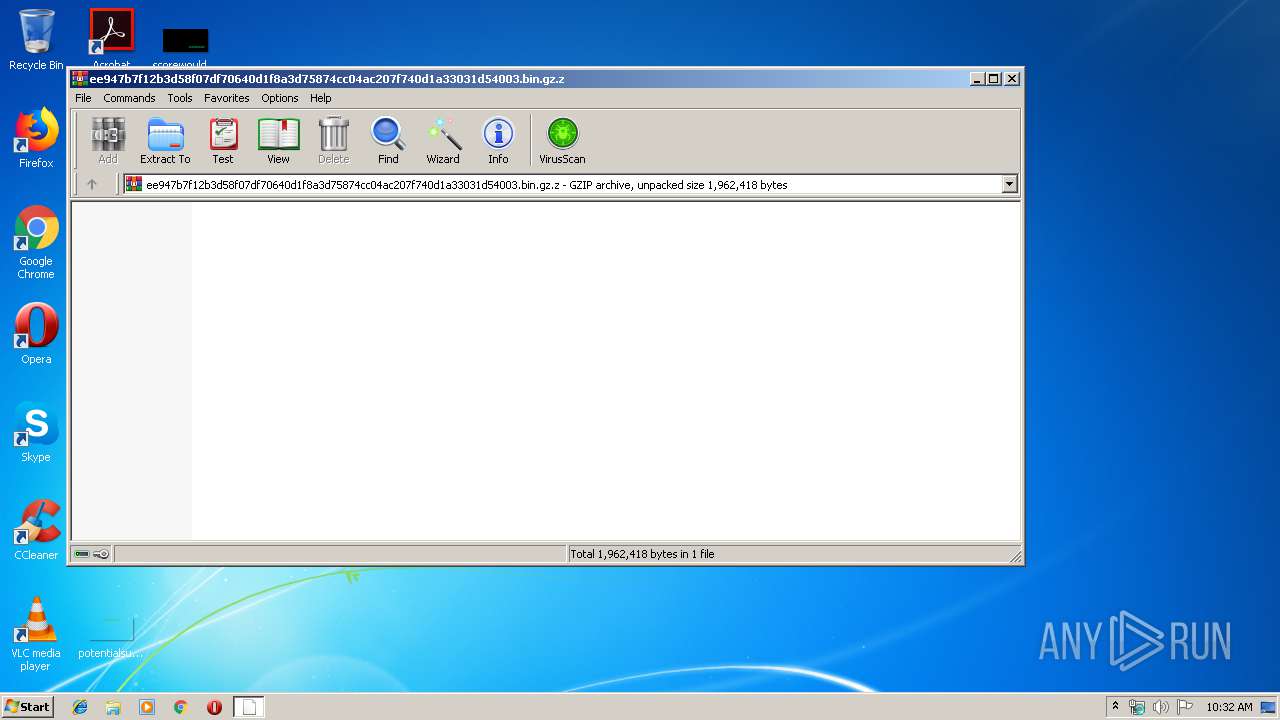
| File name: | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.gz |
| Full analysis: | https://app.any.run/tasks/205351f1-ecc3-4a9a-8636-18c2e49039ef |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 09:31:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, max compression, from Unix |
| MD5: | 160A83C561A5E893D55122993678FC72 |
| SHA1: | E9C61D00C7BF4E51B074873F6DA7B356E4D5FE2C |
| SHA256: | C80D5DA53E8DD0022B44B735F0C09BE5E624B991621A39236A84F333DC70F300 |
| SSDEEP: | 49152:GWufxo7Fn/RYgGr3Dd+Cm0qoahNYixEjk+E:GWu5WF/0bENYixqVE |
MALICIOUS
Application was dropped or rewritten from another process
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2684)
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2888)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2576)
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2888)
SUSPICIOUS
Executable content was dropped or overwritten
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2888)
INFO
Manual execution by user
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2684)
- ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | Maximum Compression |
| OperatingSystem: | Unix |
Total processes
46
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2576 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe8_ Global\UsGthrCtrlFltPipeMssGthrPipe8 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe" | C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe" | C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.gz.z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
406
Read events
398
Write events
8
Delete events
0
Modification events
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.gz.z | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
7
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3088.43591\ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.gz | — | |
MD5:— | SHA256:— | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\Desktop\7z.dll | executable | |
MD5:CA41D56630191E61565A343C59695CA1 | SHA256:6C80E3F49FCF561E6A0B52F9B4C81D1D07B22085F7864EE4CFD30DD10F6B3B12 | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\infinst.x64.exe | executable | |
MD5:— | SHA256:— | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools.7z | compressed | |
MD5:— | SHA256:— | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\data.7z | compressed | |
MD5:— | SHA256:— | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\infinst.exe | executable | |
MD5:— | SHA256:— | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\win7-10\x64\devcon.exe | executable | |
MD5:530DEDEFF00322BE5F5A0FBF341DB2CA | SHA256:97CFF42F8C0FE4FBDF991273159516BF78090625A933C3983EBD6F62284E329A | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\winxp\x64\devcon.exe | executable | |
MD5:3904D0698962E09DA946046020CBCB17 | SHA256:A51E25ACC489948B31B1384E1DC29518D19B421D6BC0CED90587128899275289 | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\winxp\x86\devcon.exe | executable | |
MD5:C4B470269324517EE838789C7CF5E606 | SHA256:5F9B898315AD8192E87E21A499FD87D31B886513BB39D368476174AAA89A2BF9 | |||
| 2888 | ee947b7f12b3d58f07df70640d1f8a3d75874cc04ac207f740d1a33031d54003.bin.exe | C:\Users\admin\AppData\Local\Temp\DevID\tools\win7-10\x86\devcon.exe | executable | |
MD5:B141565B508C89FE8DC30B009EC2EFDA | SHA256:B6736028D4957A1DC385A3BE3C59F2578CF4F5E57E6976EE6EE705E407AB811F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report