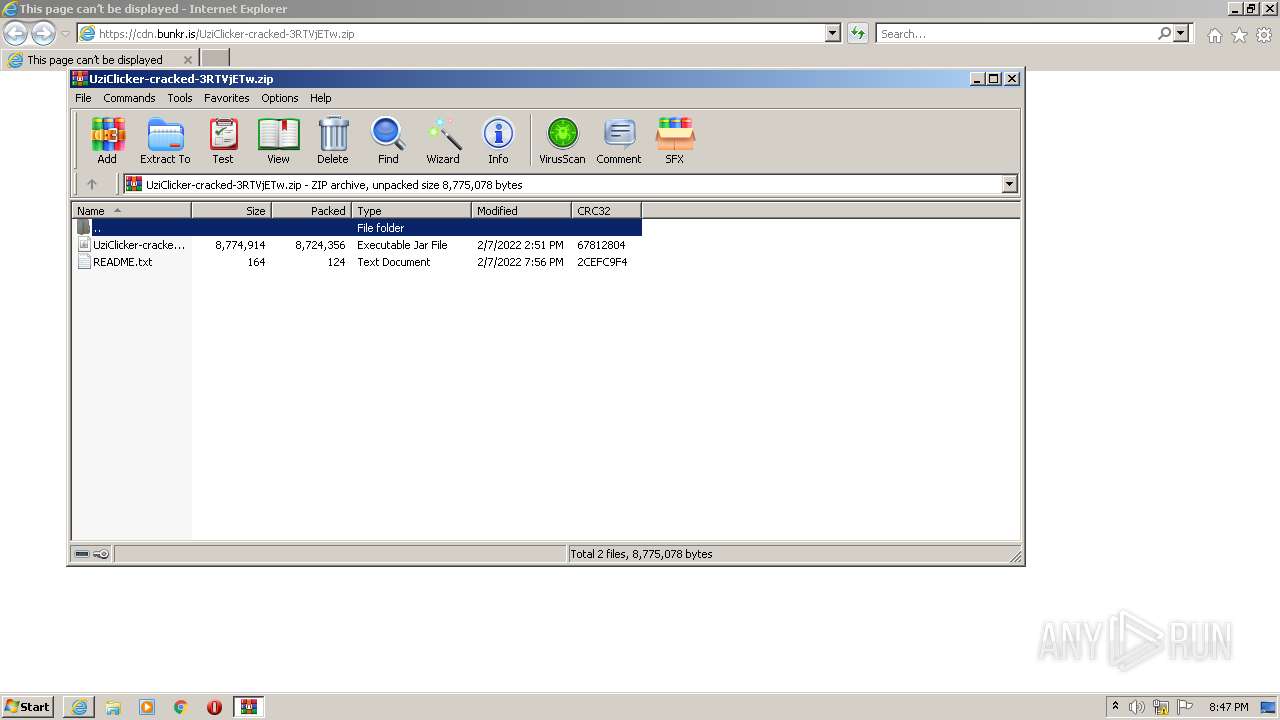
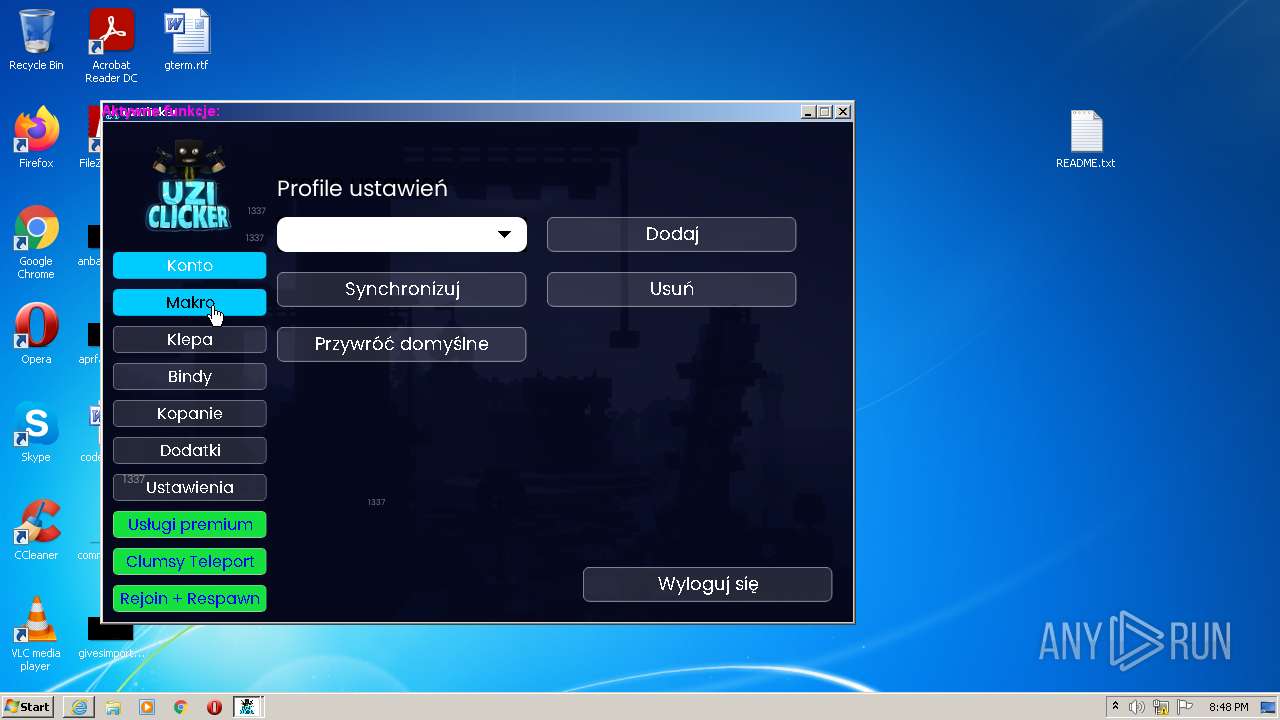
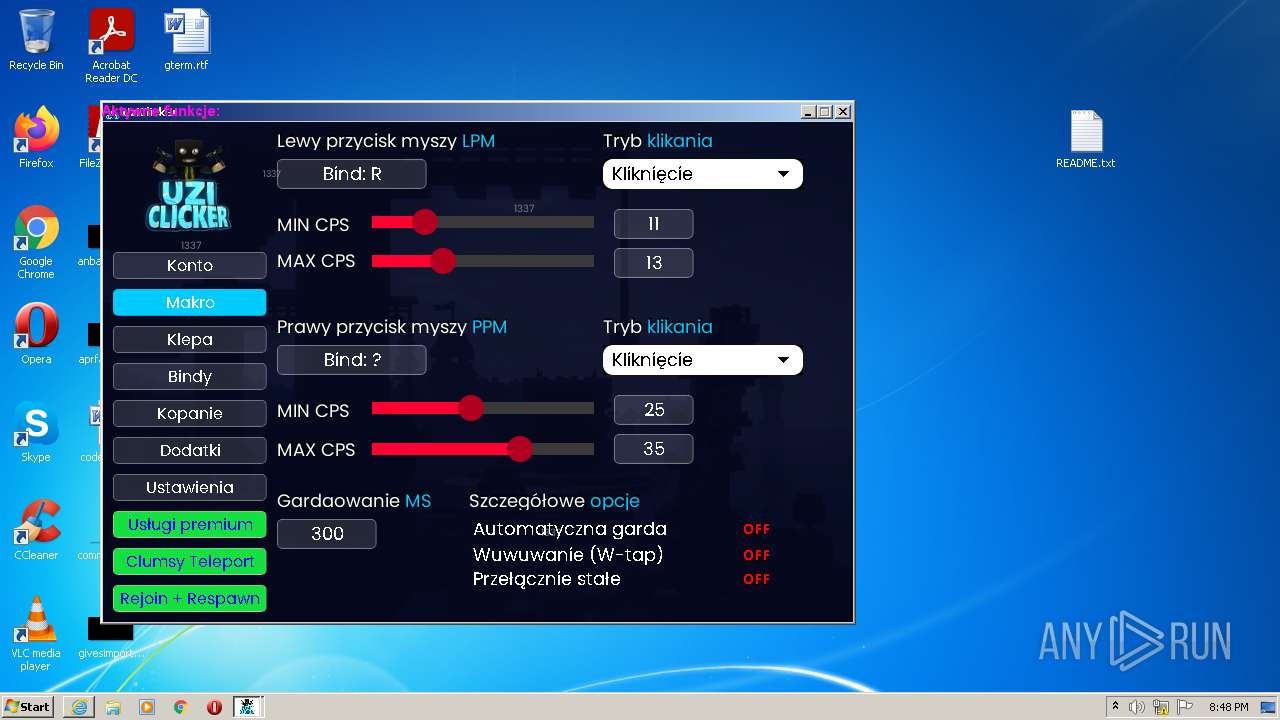
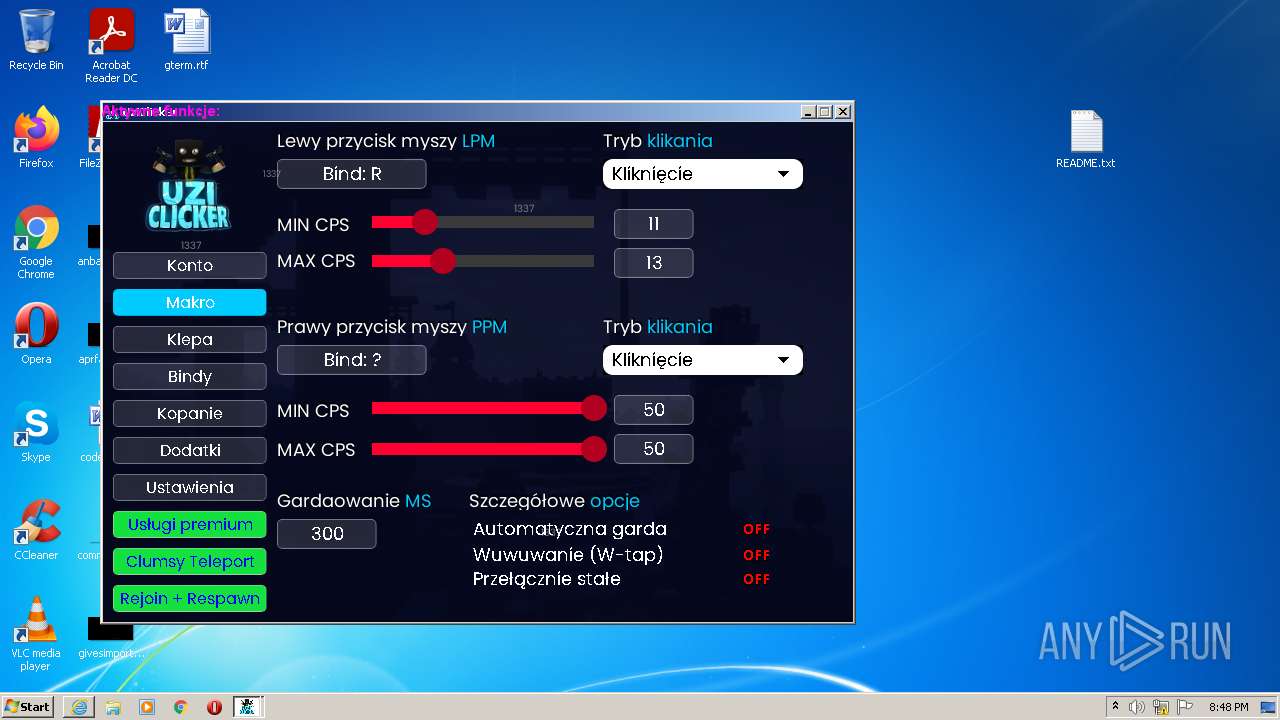
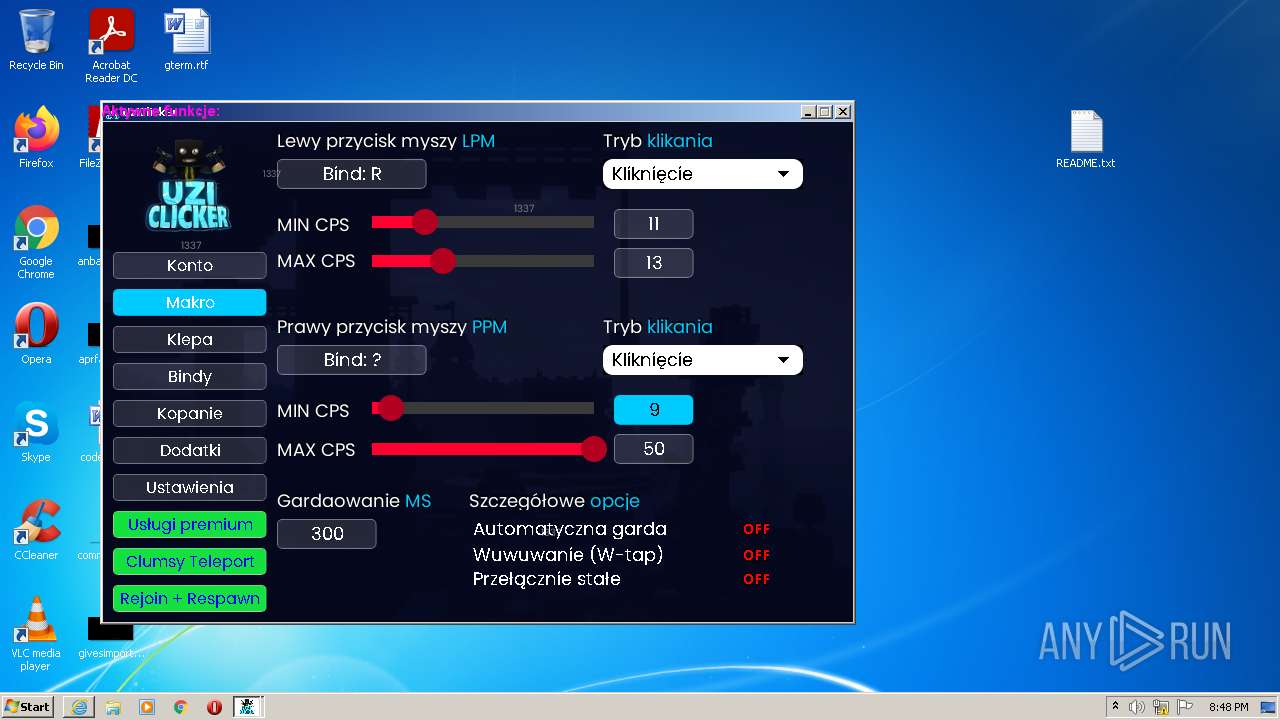
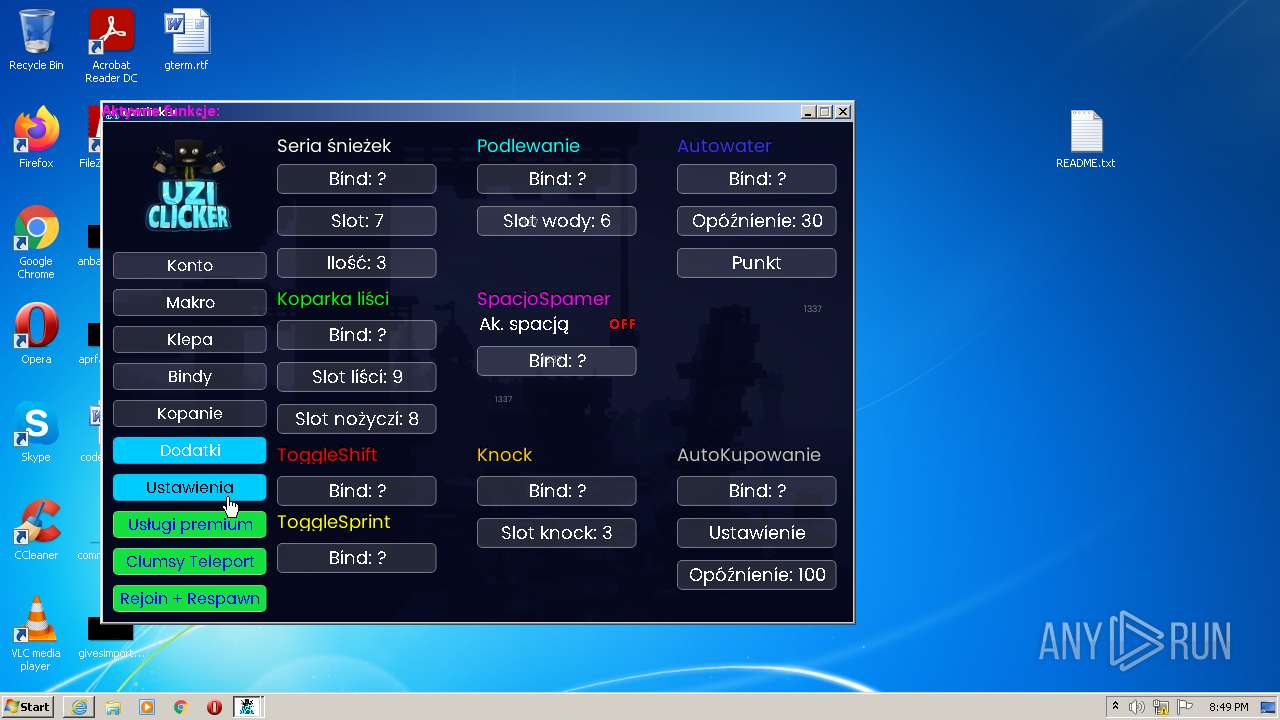
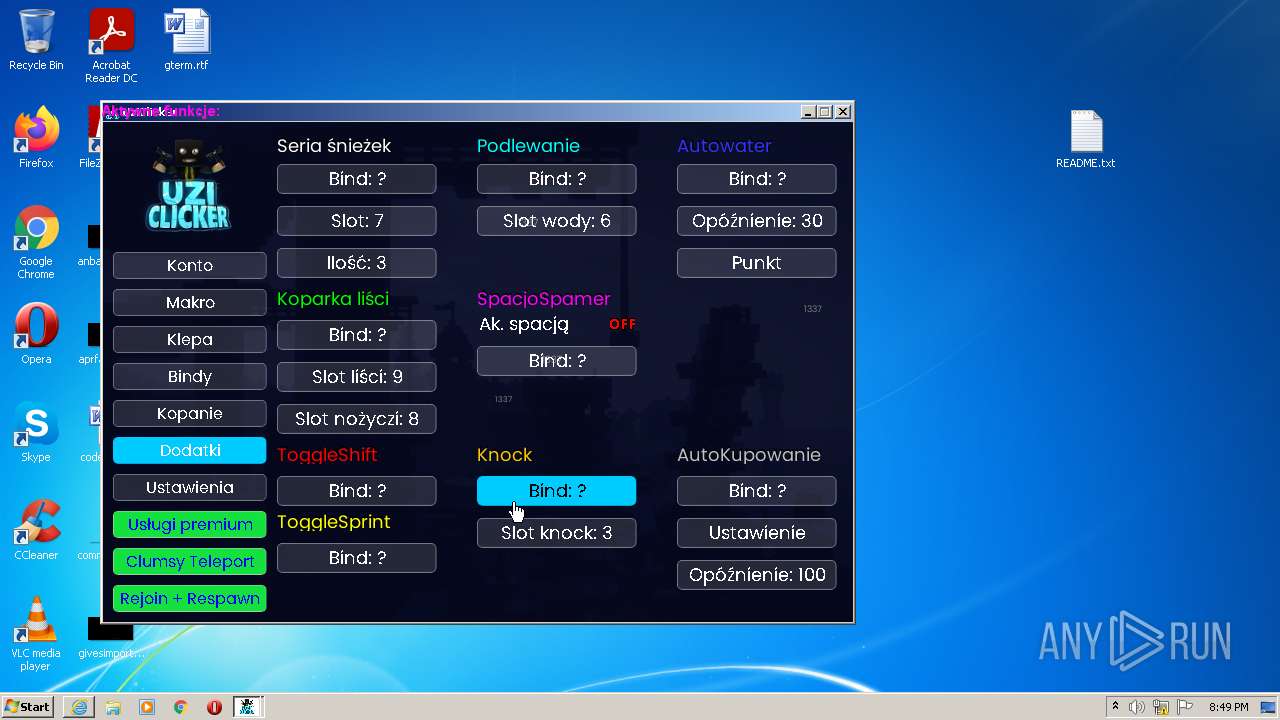
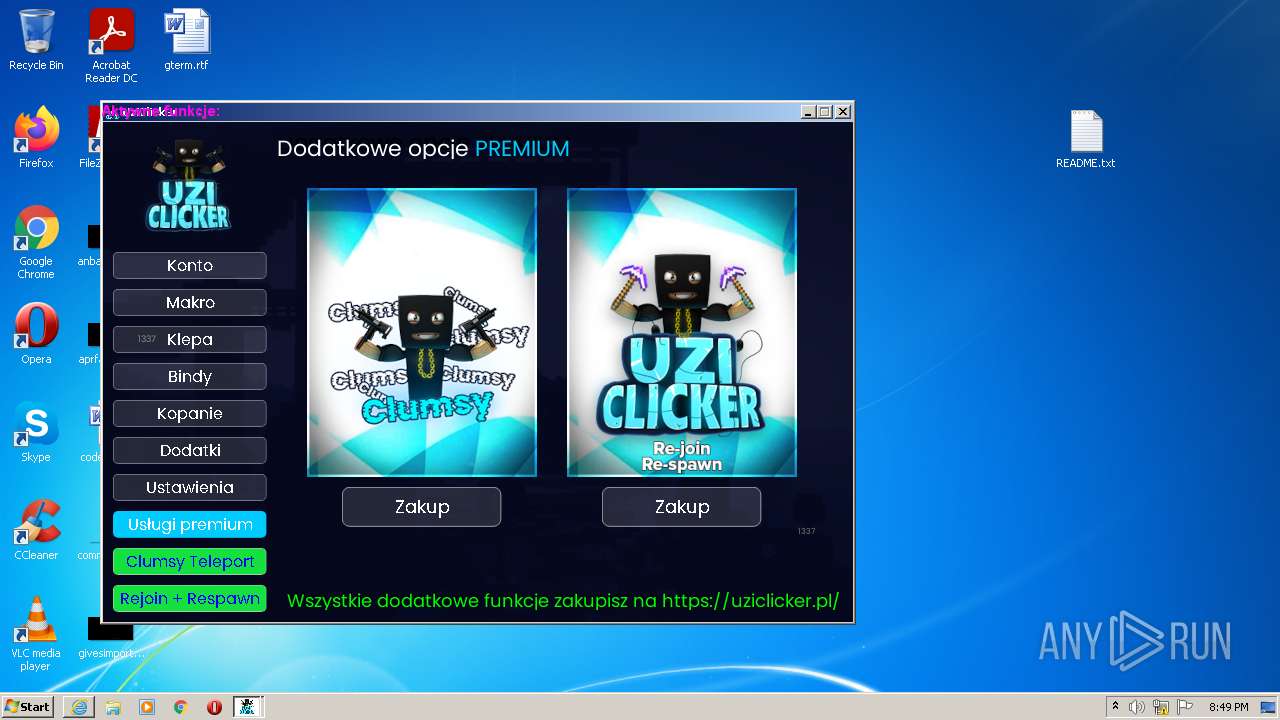
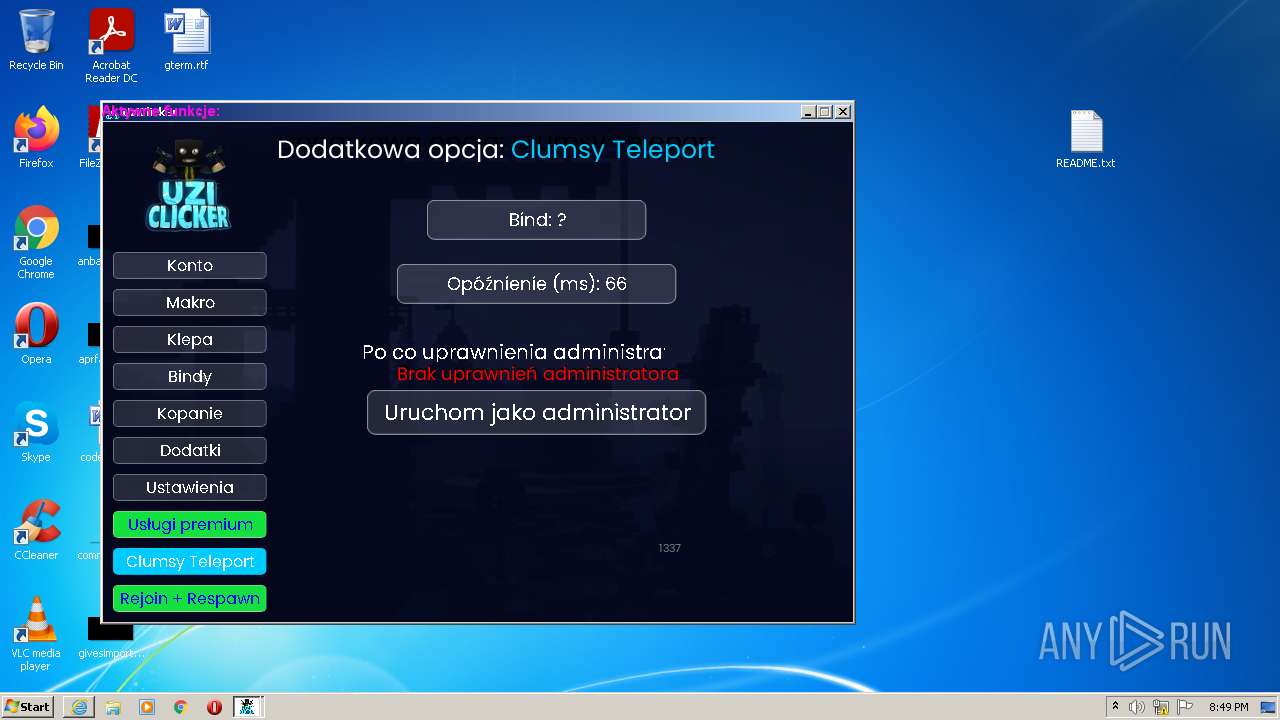
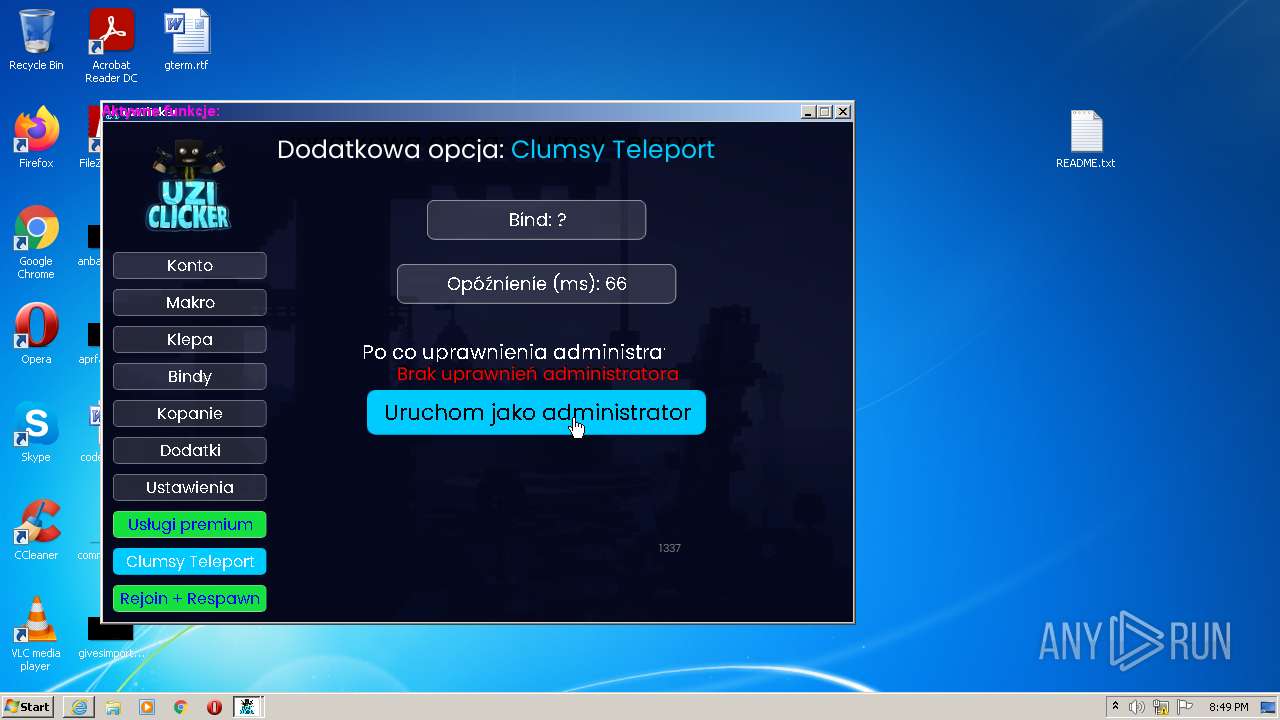
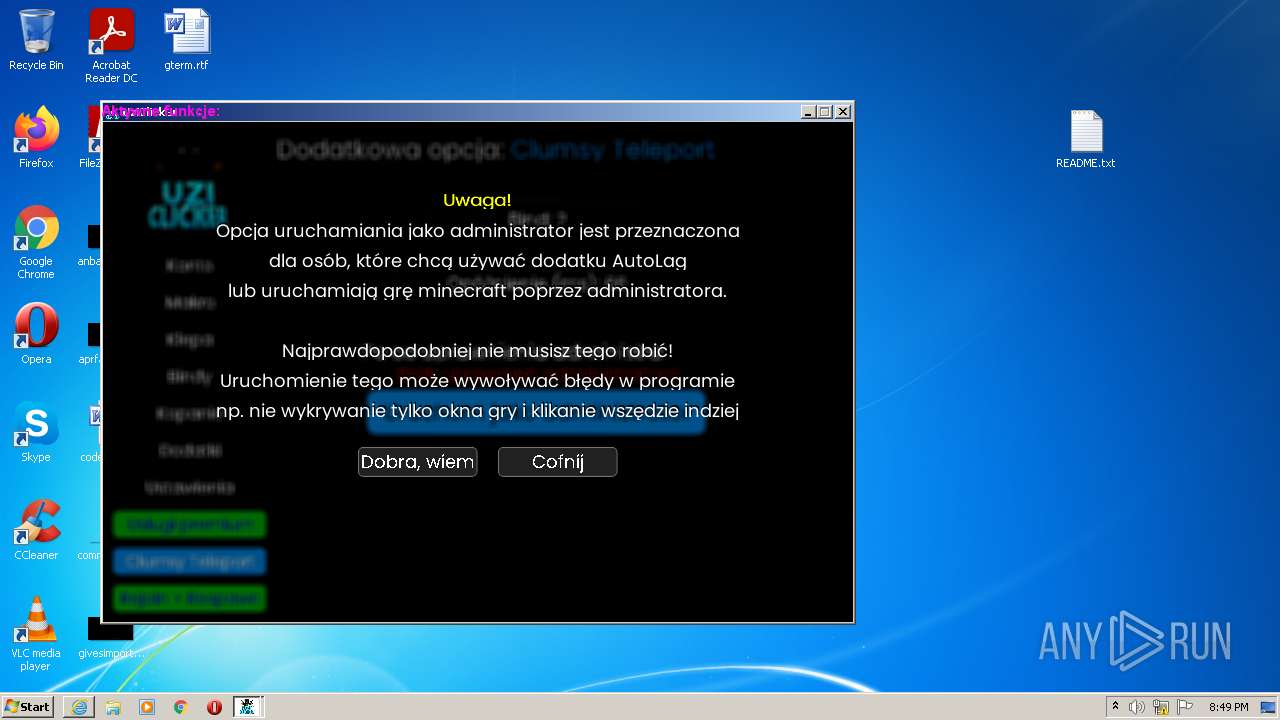
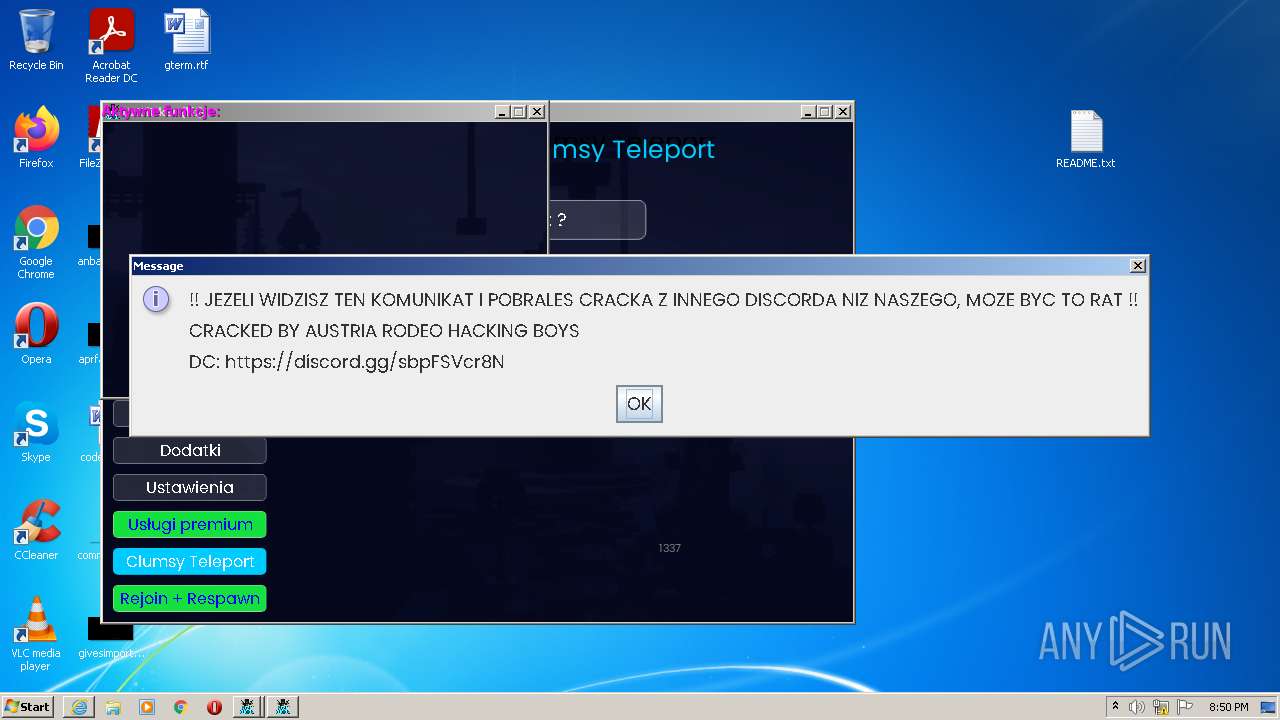
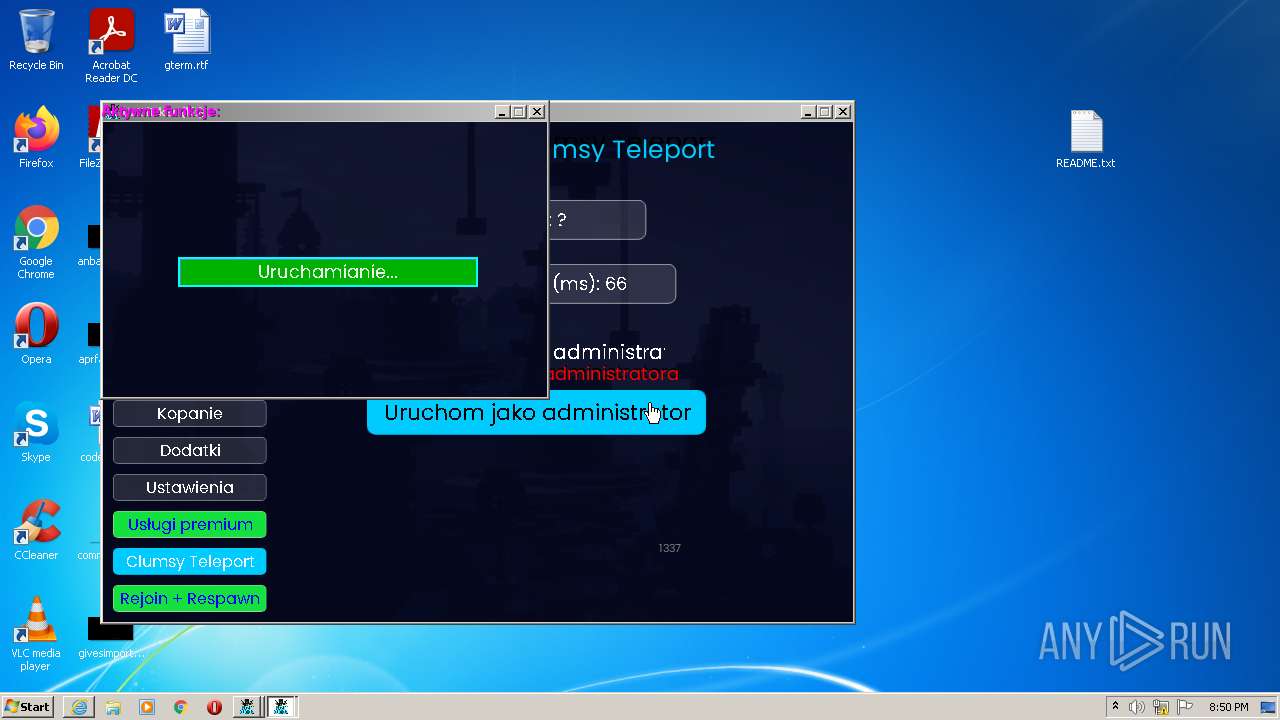
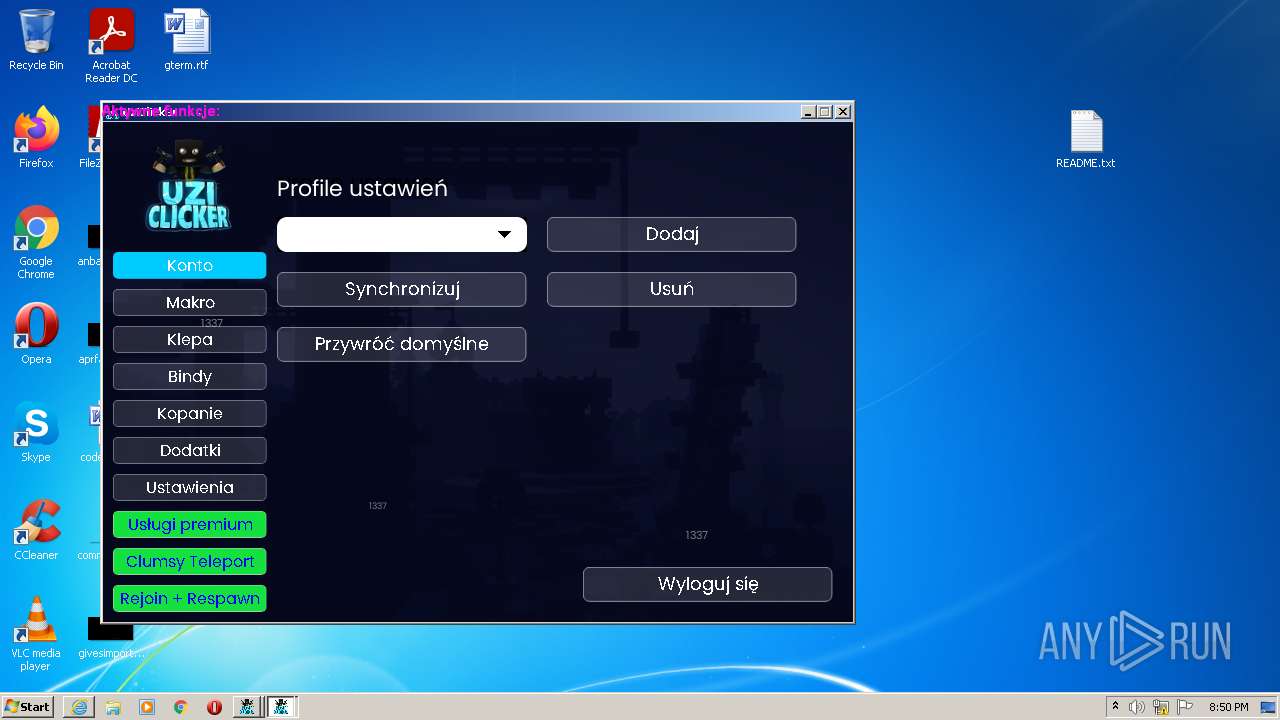
| URL: | https://cdn.bunkr.is/UziClicker-cracked-3RTVjETw.zip |
| Full analysis: | https://app.any.run/tasks/68858be2-b0a5-4819-9836-5c46fce4a5f1 |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2022, 20:46:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3804137EF703D091449218105697F34D |
| SHA1: | DA9E2ABC68F491E764EF299E1A56CD7705C8C209 |
| SHA256: | C7FBA1C238C16F3996C3ECE40CC5ACF339FEA120A928F2C967C8C31DEA311785 |
| SSDEEP: | 3:N8cWGa3+MZArZNASLkVn:2cWZ3zZkQSYVn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3980)
Reads the computer name
- WinRAR.exe (PID: 1808)
- javaw.exe (PID: 2948)
- java.exe (PID: 3448)
- javaw.exe (PID: 3244)
- wmic.exe (PID: 3976)
- javaw.exe (PID: 1040)
- wmic.exe (PID: 3260)
- wmic.exe (PID: 1992)
- wmic.exe (PID: 2668)
- powershell.exe (PID: 3332)
- java.exe (PID: 3984)
- wmic.exe (PID: 1104)
- wmic.exe (PID: 3728)
- wmic.exe (PID: 736)
- wmic.exe (PID: 3928)
- wmic.exe (PID: 2260)
- wmic.exe (PID: 3712)
Checks supported languages
- WinRAR.exe (PID: 1808)
- javaw.exe (PID: 2948)
- java.exe (PID: 3448)
- javaw.exe (PID: 3244)
- javaw.exe (PID: 1040)
- wmic.exe (PID: 3976)
- wmic.exe (PID: 3260)
- wmic.exe (PID: 1992)
- wmic.exe (PID: 2668)
- powershell.exe (PID: 3332)
- java.exe (PID: 3984)
- wmic.exe (PID: 1104)
- wmic.exe (PID: 736)
- wmic.exe (PID: 3928)
- wmic.exe (PID: 3728)
- wmic.exe (PID: 2260)
- wmic.exe (PID: 3712)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 2948)
Creates files in the program directory
- javaw.exe (PID: 2948)
Creates files in the user directory
- javaw.exe (PID: 2948)
- java.exe (PID: 3448)
- javaw.exe (PID: 3244)
- javaw.exe (PID: 1040)
Executes JAVA applets
- javaw.exe (PID: 2948)
Drops a file that was compiled in debug mode
- javaw.exe (PID: 3244)
- javaw.exe (PID: 1040)
- java.exe (PID: 3984)
Executable content was dropped or overwritten
- javaw.exe (PID: 3244)
- javaw.exe (PID: 1040)
- java.exe (PID: 3984)
Uses WMIC.EXE to obtain a system information
- javaw.exe (PID: 1040)
- java.exe (PID: 3984)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 1040)
- java.exe (PID: 3984)
Executes PowerShell scripts
- javaw.exe (PID: 1040)
Check for Java to be installed
- java.exe (PID: 3984)
INFO
Reads the computer name
- iexplore.exe (PID: 1252)
- iexplore.exe (PID: 3980)
- icacls.exe (PID: 3172)
Checks supported languages
- iexplore.exe (PID: 3980)
- iexplore.exe (PID: 1252)
- NOTEPAD.EXE (PID: 848)
- icacls.exe (PID: 3172)
- reg.exe (PID: 2560)
- reg.exe (PID: 2568)
Application launched itself
- iexplore.exe (PID: 1252)
Reads settings of System Certificates
- iexplore.exe (PID: 3980)
- iexplore.exe (PID: 1252)
Manual execution by user
- NOTEPAD.EXE (PID: 848)
- javaw.exe (PID: 2948)
- javaw.exe (PID: 3244)
- javaw.exe (PID: 1040)
Changes internet zones settings
- iexplore.exe (PID: 1252)
Reads internet explorer settings
- iexplore.exe (PID: 3980)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1252)
Checks Windows Trust Settings
- iexplore.exe (PID: 1252)
- iexplore.exe (PID: 3980)
- powershell.exe (PID: 3332)
Changes settings of System certificates
- iexplore.exe (PID: 1252)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1252)
Creates files in the user directory
- iexplore.exe (PID: 1252)
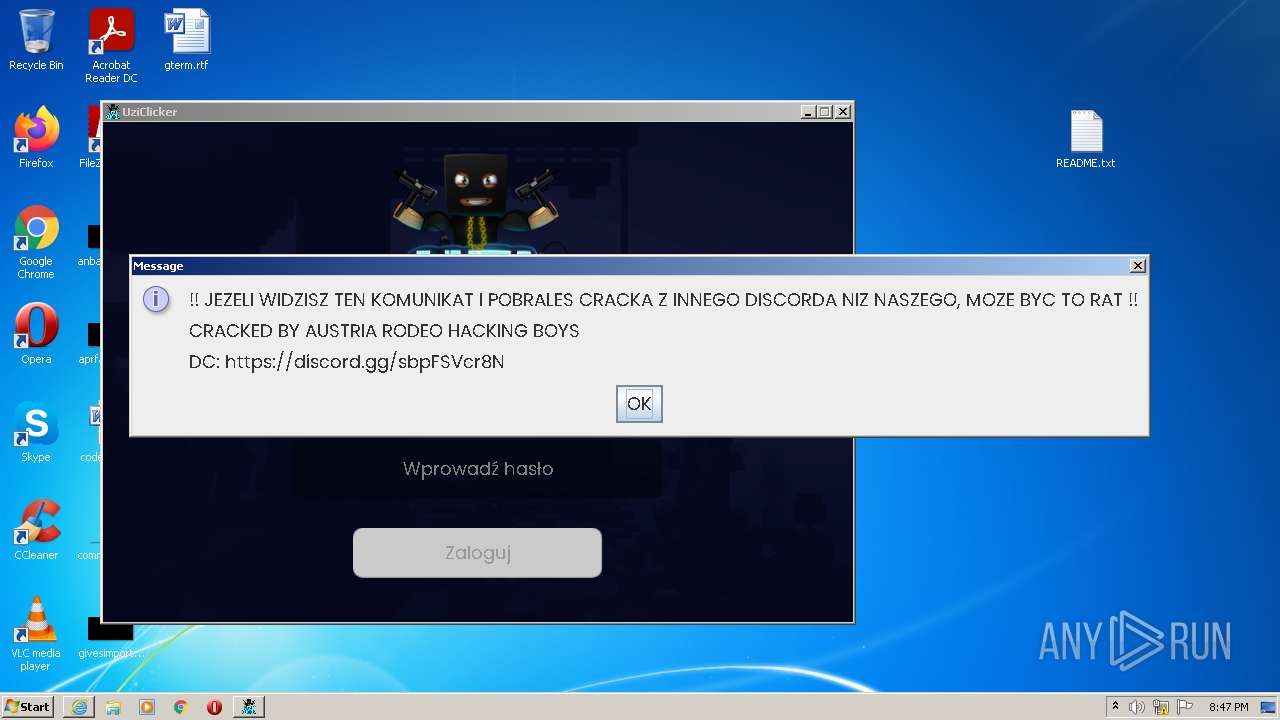
Dropped object may contain Bitcoin addresses
- javaw.exe (PID: 3244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
80
Monitored processes
23
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 736 | wmic cpu get Caption, DeviceID, Manufacturer, MaxClockSpeed, Name, NumberOfCores, NumberOfLogicalProcessors | C:\Windows\System32\Wbem\wmic.exe | — | java.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
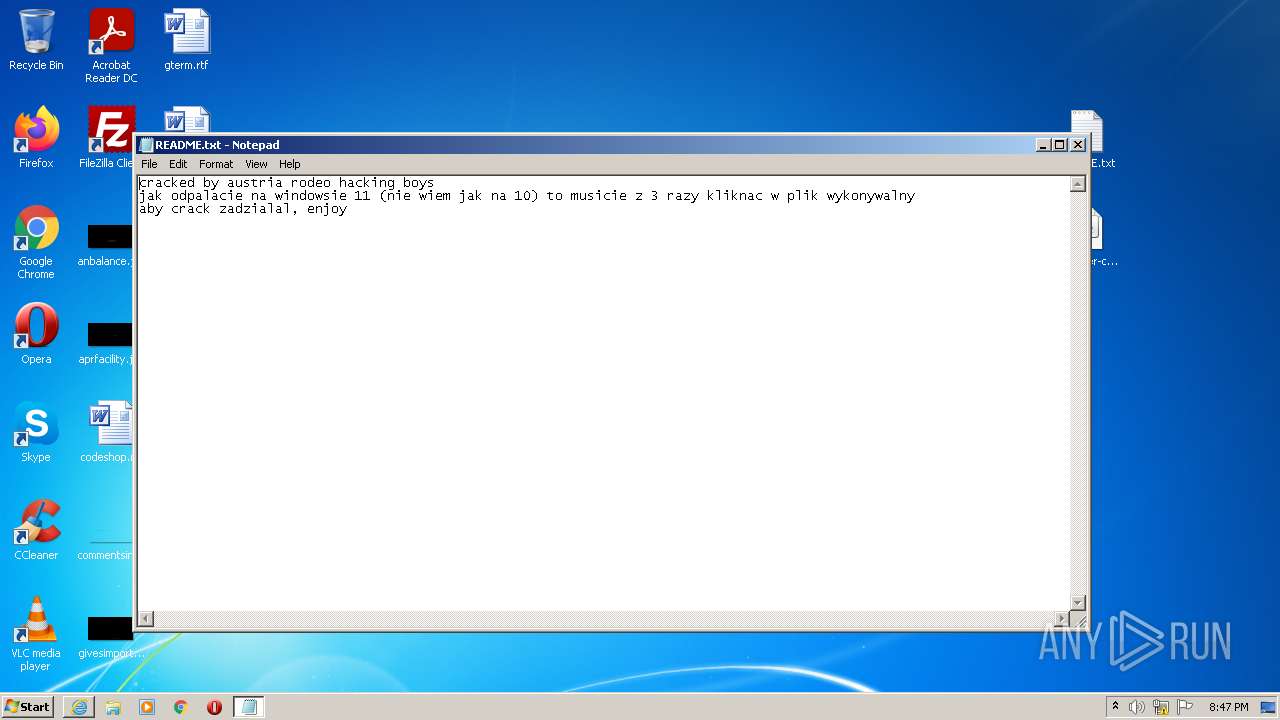
| 848 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\README.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
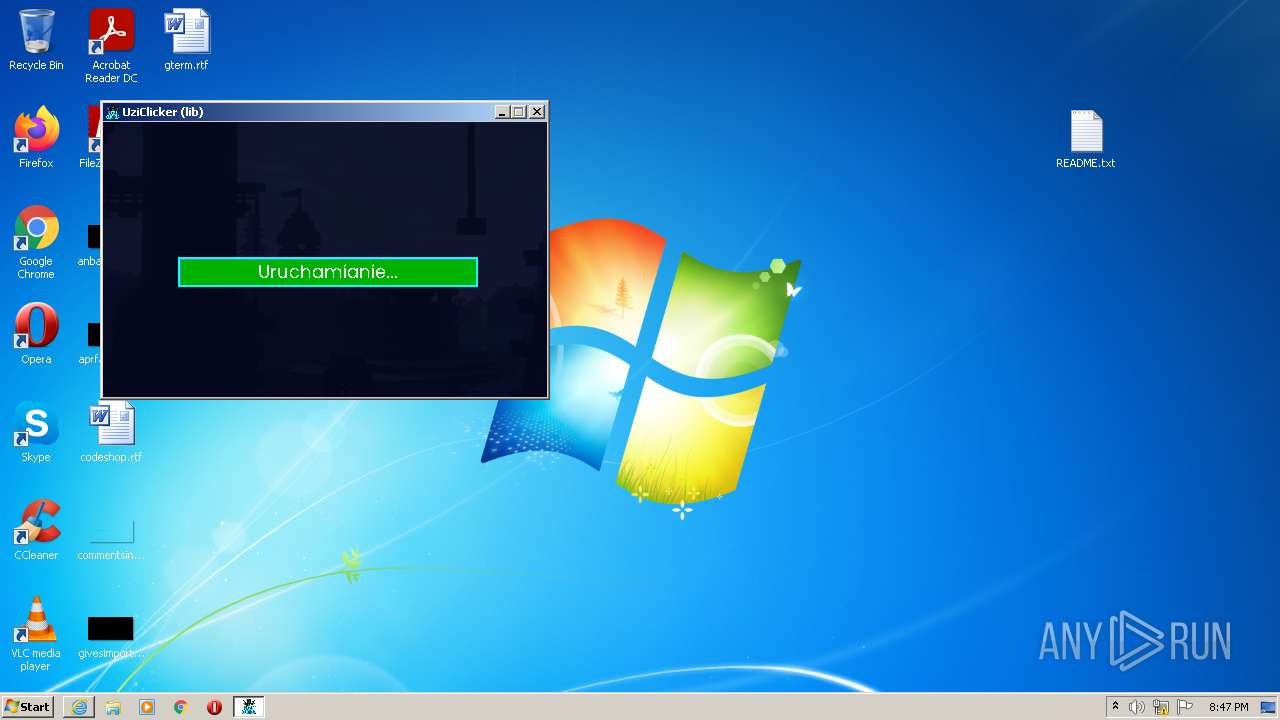
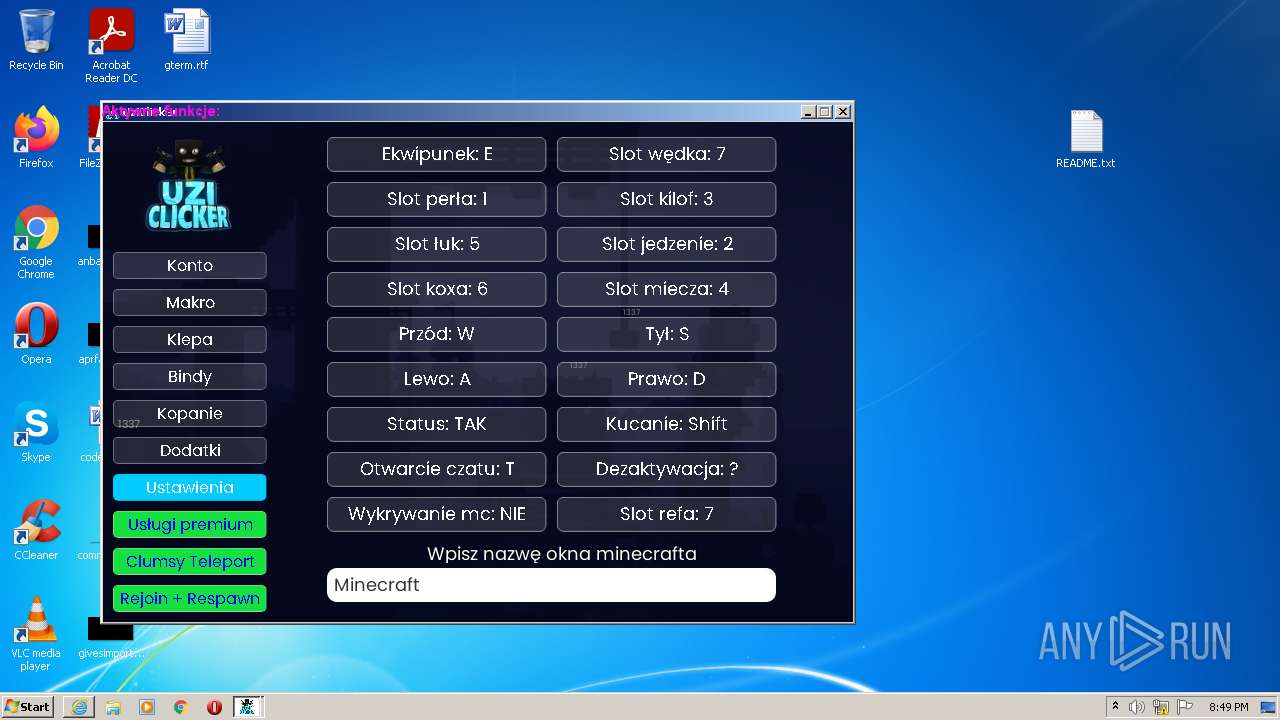
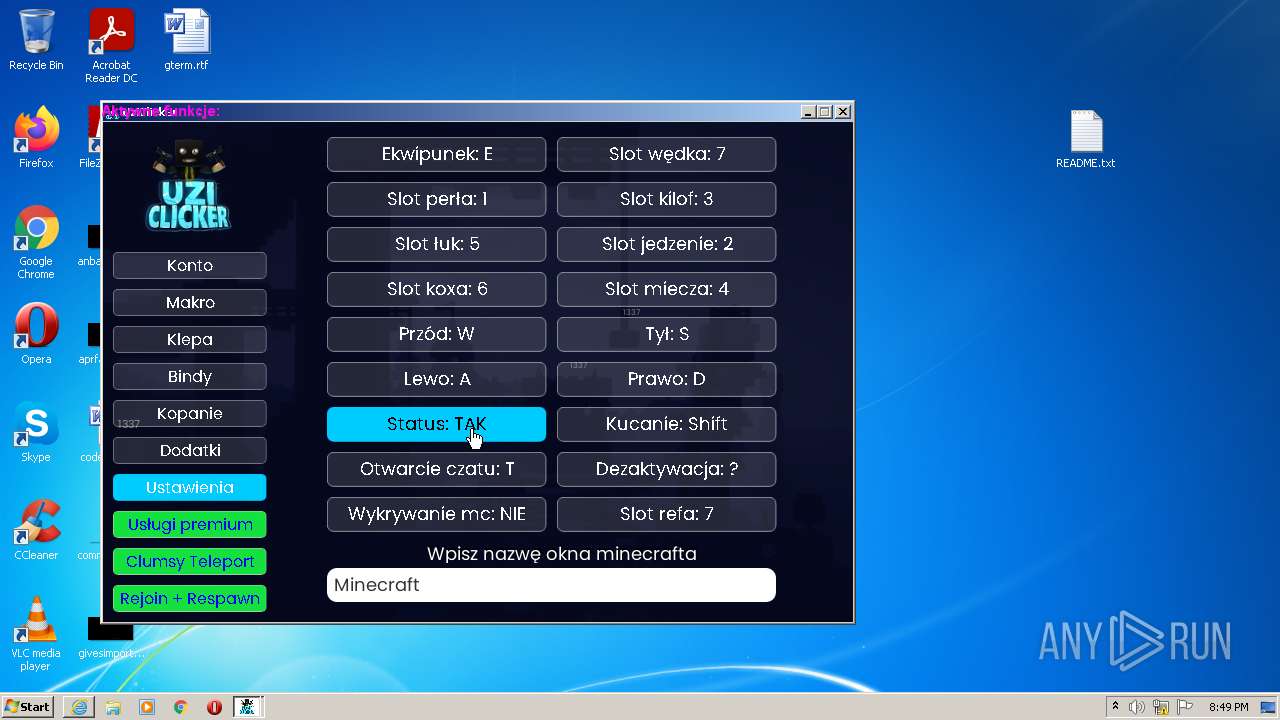
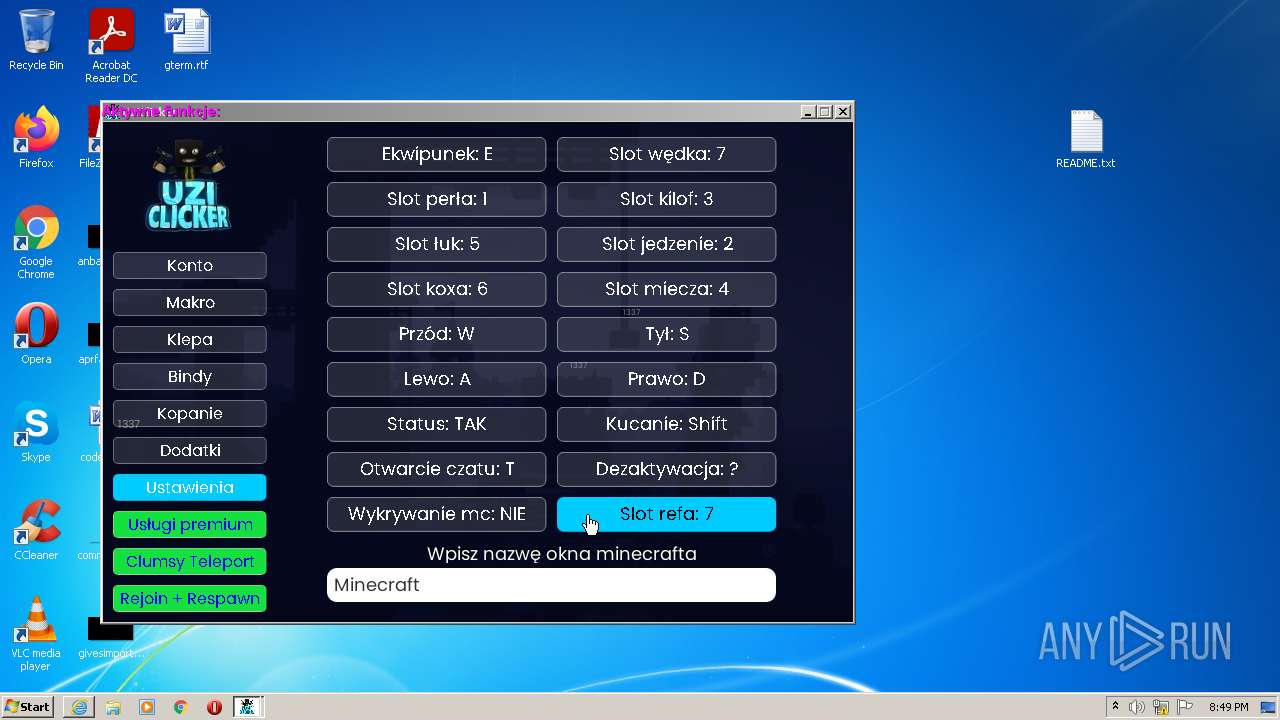
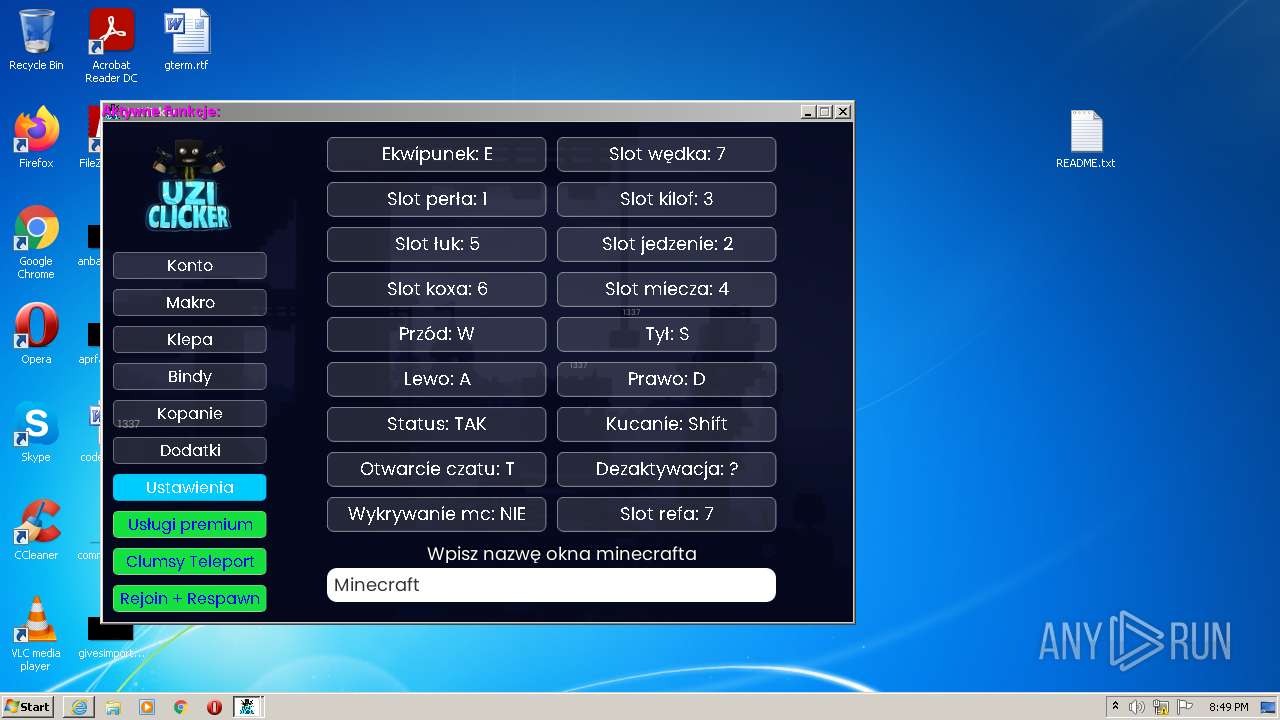
| 1040 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\uziclicker\UziClicker-cracked.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Explorer.EXE | |
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 | ||||
| 1104 | wmic baseboard get serialNumber | C:\Windows\System32\Wbem\wmic.exe | — | java.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1252 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cdn.bunkr.is/UziClicker-cracked-3RTVjETw.zip" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1808 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\UziClicker-cracked-3RTVjETw.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 | ||||
| 1992 | wmic baseboard get serialNumber | C:\Windows\System32\Wbem\wmic.exe | — | javaw.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2260 | wmic baseboard get serialNumber | C:\Windows\System32\Wbem\wmic.exe | — | java.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2560 | reg query "HKU\S-1-5-19" | C:\Windows\system32\reg.exe | — | javaw.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2568 | reg query "HKU\S-1-5-19" | C:\Windows\system32\reg.exe | — | java.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
10
Suspicious files
21
Text files
423
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 1252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4AFD512CEB502B1DC613B49BF7D04C42 | der | |
MD5:— | SHA256:— | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\UziClicker-cracked-3RTVjETw[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 1252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 1252 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 1252 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4AFD512CEB502B1DC613B49BF7D04C42 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
24
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1252 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3980 | iexplore.exe | GET | 200 | 104.89.32.83:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
1252 | iexplore.exe | GET | 200 | 2.16.106.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9ca690878a0951f4 | unknown | compressed | 4.70 Kb | whitelisted |
1252 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1252 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3980 | iexplore.exe | GET | 200 | 95.101.89.74:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQdAcRi1iuywAdx7FXNYziZUQ%3D%3D | unknown | der | 503 b | shared |
3980 | iexplore.exe | GET | 200 | 2.16.106.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?972a9daee2b5aa89 | unknown | compressed | 59.9 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3980 | iexplore.exe | 2.16.106.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
1252 | iexplore.exe | 88.221.39.148:443 | go.microsoft.com | Akamai International B.V. | — | suspicious |
1252 | iexplore.exe | 131.253.33.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
3980 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
3980 | iexplore.exe | 95.101.89.74:80 | r3.o.lencr.org | Akamai International B.V. | — | suspicious |
3984 | java.exe | 188.114.96.7:443 | uziclicker.pl | Cloudflare Inc | US | malicious |
1040 | javaw.exe | 188.114.96.7:443 | uziclicker.pl | Cloudflare Inc | US | malicious |
1252 | iexplore.exe | 13.92.246.37:443 | query.prod.cms.msn.com | Microsoft Corporation | US | whitelisted |
1252 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3980 | iexplore.exe | 185.243.216.175:443 | cdn.bunkr.is | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.bunkr.is |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |