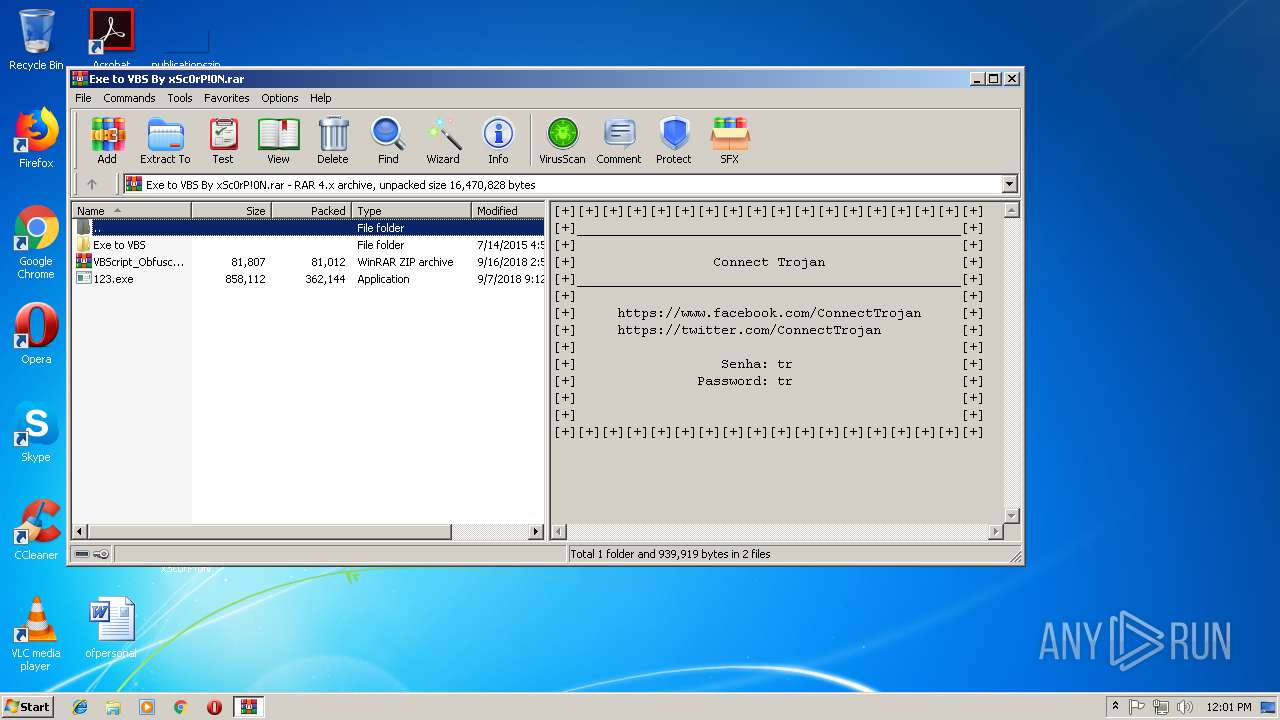
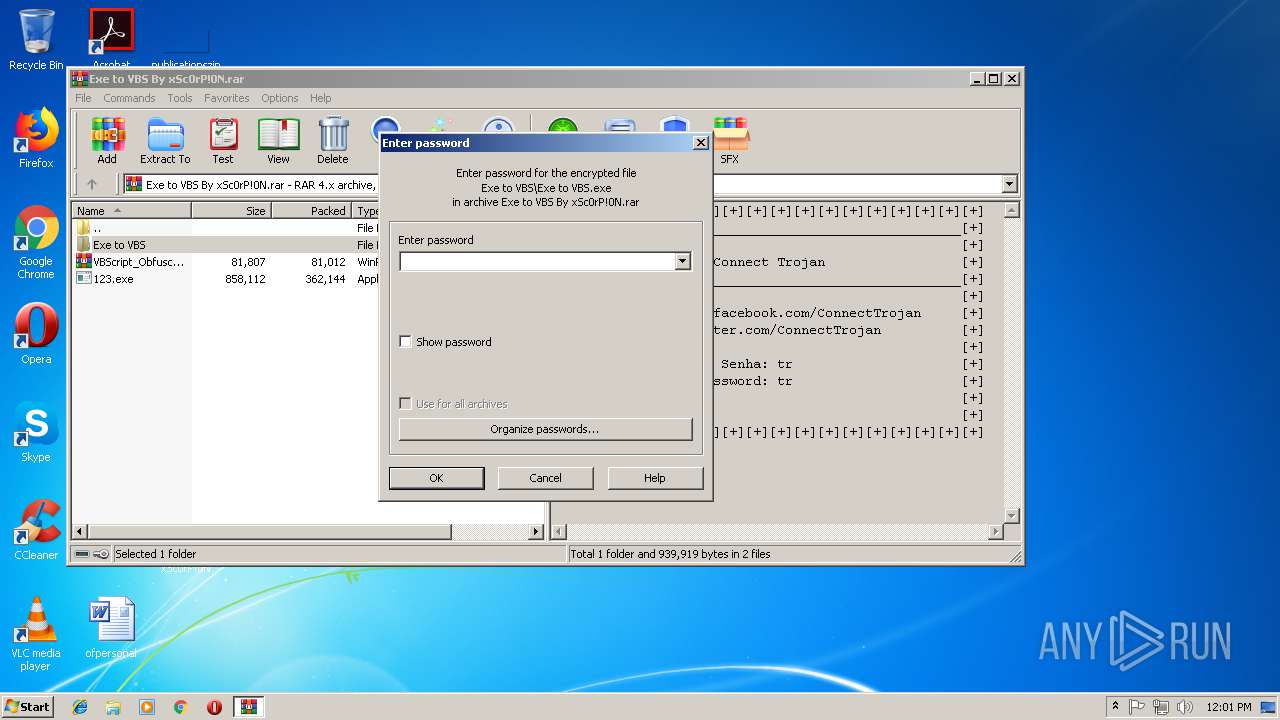
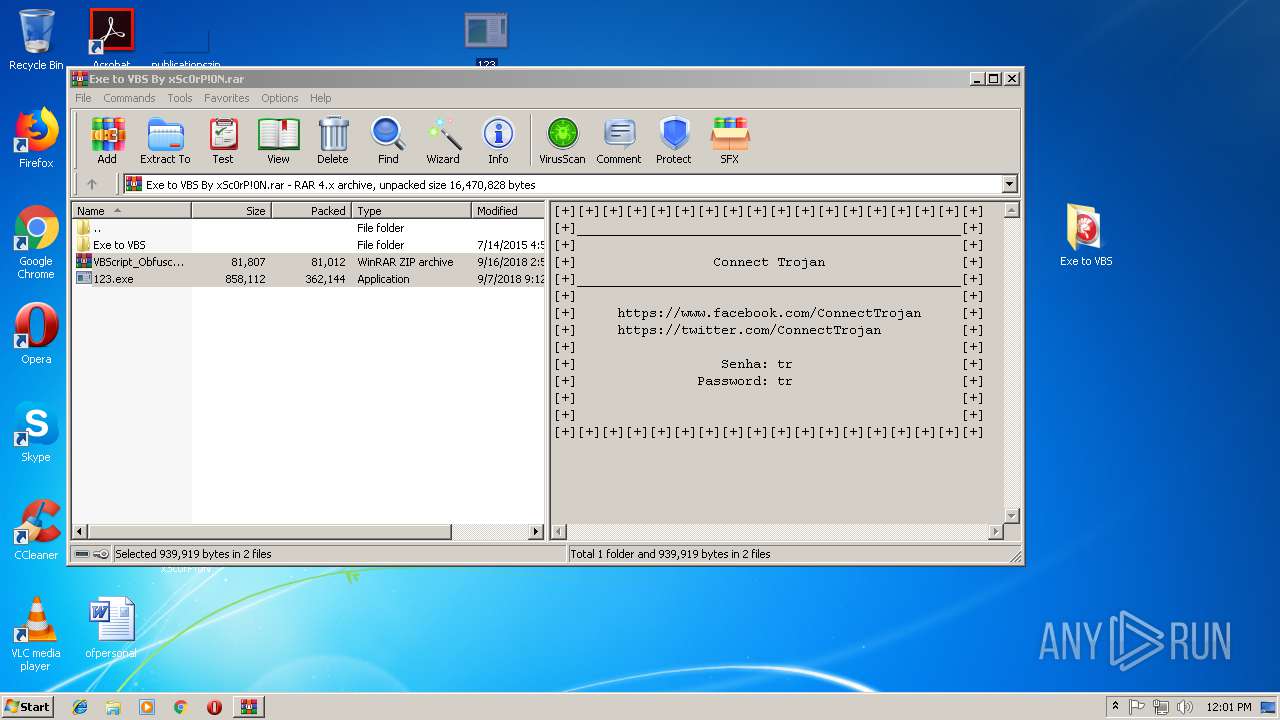
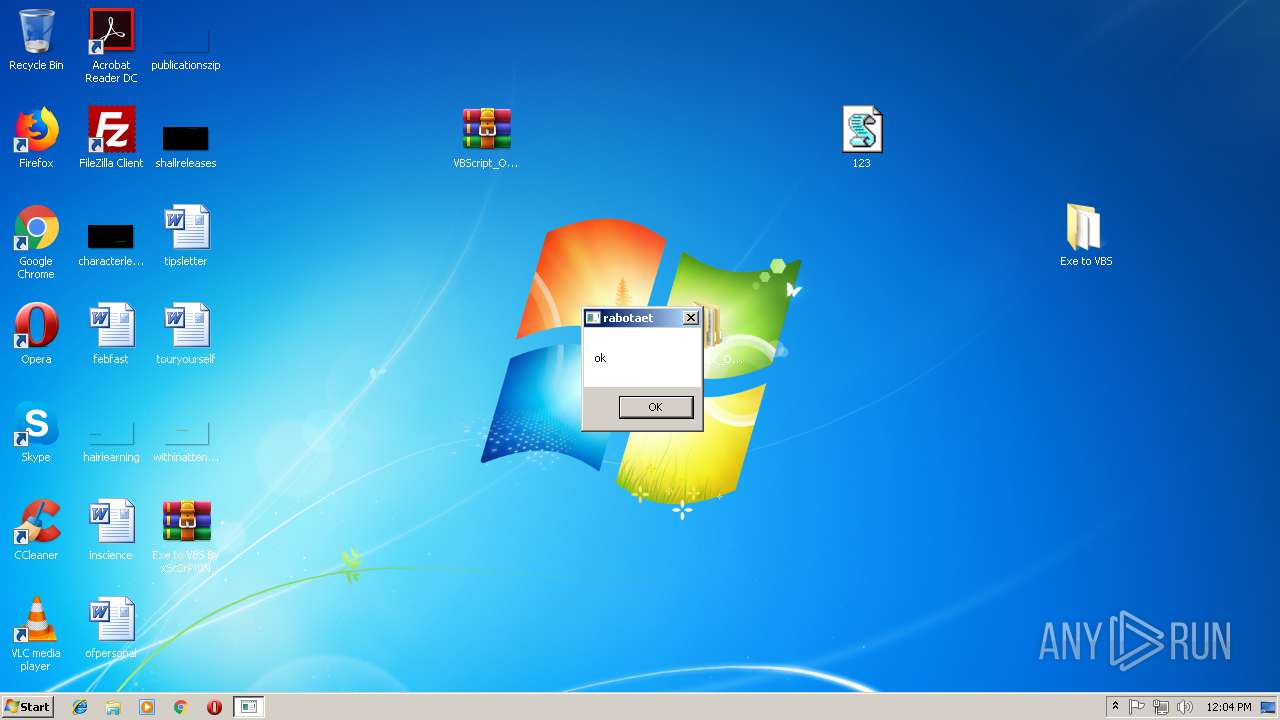
| File name: | Exe to VBS By xSc0rP!0N.rar |
| Full analysis: | https://app.any.run/tasks/cf7396a8-09df-4e5c-8e8c-8d0d3f71ada5 |
| Verdict: | Malicious activity |
| Analysis date: | September 16, 2018, 11:00:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 05BBDFEFDE9D69A9FB0CEEEA07975A12 |
| SHA1: | B5798704861CF871385FCA1D0CEBA9AA92E15F81 |
| SHA256: | C7F66A976A0EBE7062DC8EFDDE4ED41D4B610CCB711DDB58E73C8557D65B9BE3 |
| SSDEEP: | 98304:g9cX4Q5D0gSvRsesZPGDC9zWwJKPLJIpkYEs14VF5W:g97Q5pQRFsZeDHwJKDJyp2f5W |
MALICIOUS
Application was dropped or rewritten from another process
- Tempwinlogon.exe (PID: 2104)
- Tempwinlogon.exe (PID: 3512)
- Tempwinlogon.exe (PID: 4016)
SUSPICIOUS
Executable content was dropped or overwritten
- WScript.exe (PID: 1864)
- WScript.exe (PID: 2616)
Creates files in the user directory
- notepad++.exe (PID: 3104)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 2974475 |
|---|---|
| UncompressedSize: | 15530909 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:11:24 05:15:06 |
| PackingMethod: | Normal |
| ArchivedFileName: | Exe to VBS\Exe to VBS.exe |
Total processes
60
Monitored processes
17
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\vbs_rot47_obfuscator.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1684 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\VBScript_Obfuscator-master.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1864 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\123.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\AppData\Local\Tempwinlogon.exe" | C:\Users\admin\AppData\Local\Tempwinlogon.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2236 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\vbs_obfuscator.vbs" C:\Users\admin\Desktop\123.vbs | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2300 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\vbs_obfuscator_base64.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2448 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\vbs_obfuscator.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
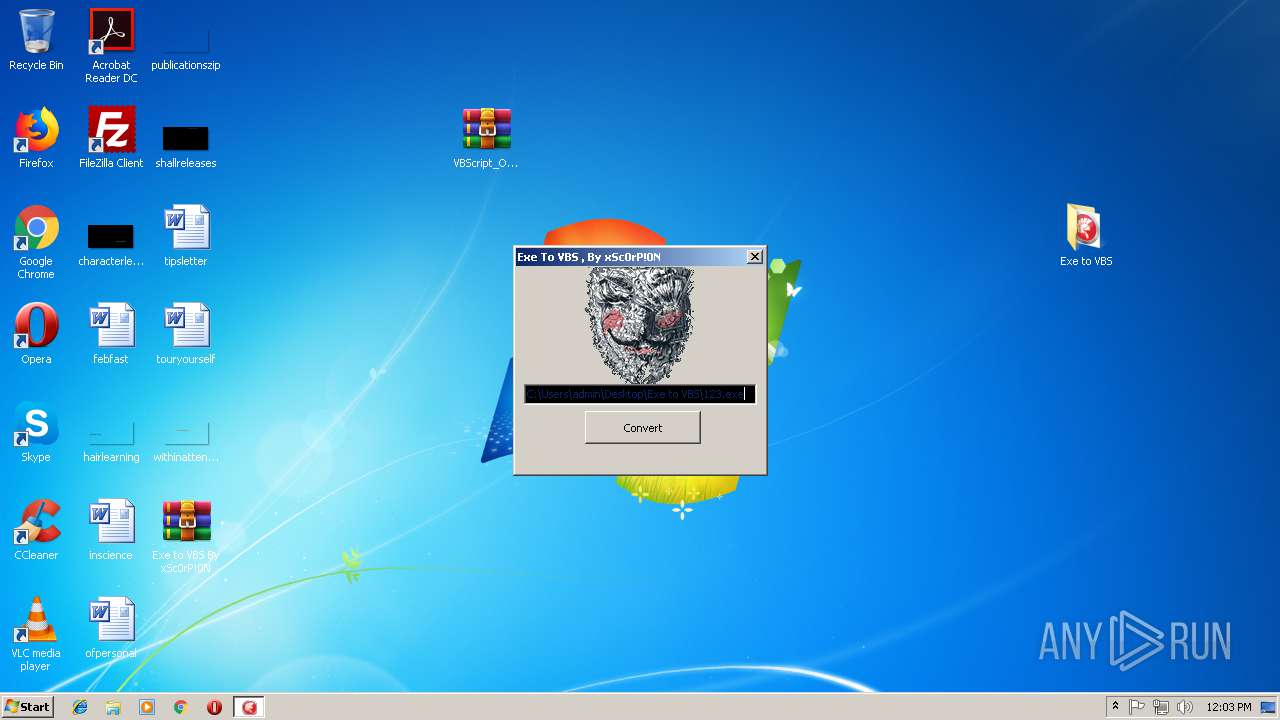
| 2488 | "C:\Users\admin\Desktop\Exe to VBS\Exe to VBS.exe" | C:\Users\admin\Desktop\Exe to VBS\Exe to VBS.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2616 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\123.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Exe to VBS By xSc0rP!0N.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 442
Read events
2 244
Write events
191
Delete events
7
Modification events
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Exe to VBS By xSc0rP!0N.rar | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
2
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2772.36027\Exe to VBS\Exe to VBS.exe | — | |
MD5:— | SHA256:— | |||
| 2772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2772.36676\123.exe | — | |
MD5:— | SHA256:— | |||
| 2772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2772.36676\VBScript_Obfuscator-master.zip | — | |
MD5:— | SHA256:— | |||
| 3104 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:— | SHA256:— | |||
| 3104 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:— | SHA256:— | |||
| 2488 | Exe to VBS.exe | C:\Users\admin\Desktop\Exe to VBS\123 | text | |
MD5:— | SHA256:— | |||
| 1684 | WinRAR.exe | C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\README.md | text | |
MD5:6177DCC3D1BA023EB2DB29416C14683F | SHA256:C62C3F86544B98A9E1AF4D895D3AD36D83DDC906AF82BCDF1C422C4E809AE322 | |||
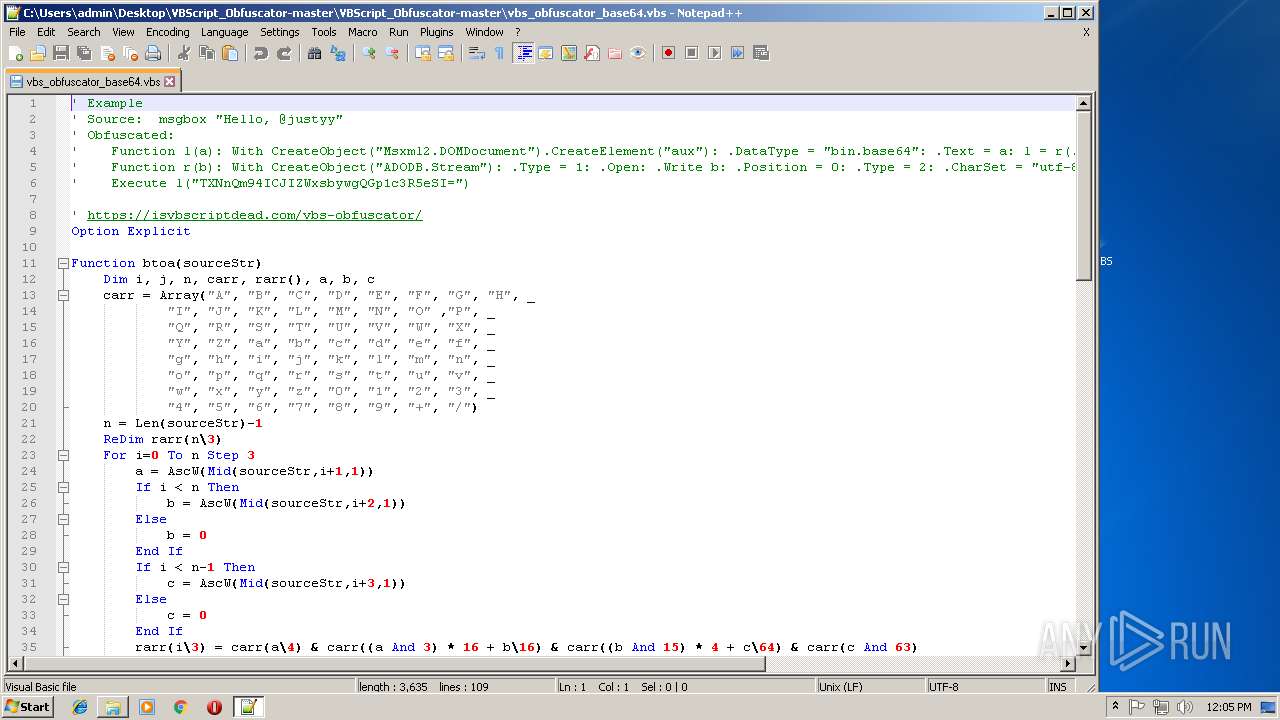
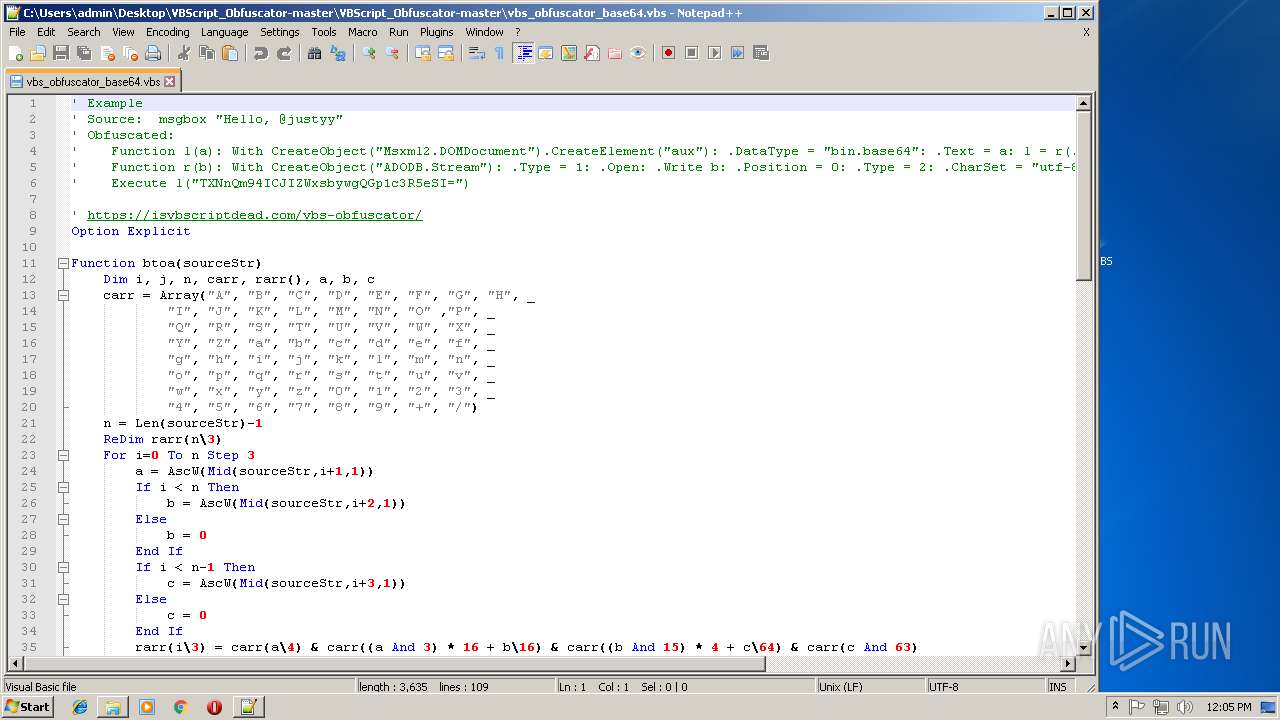
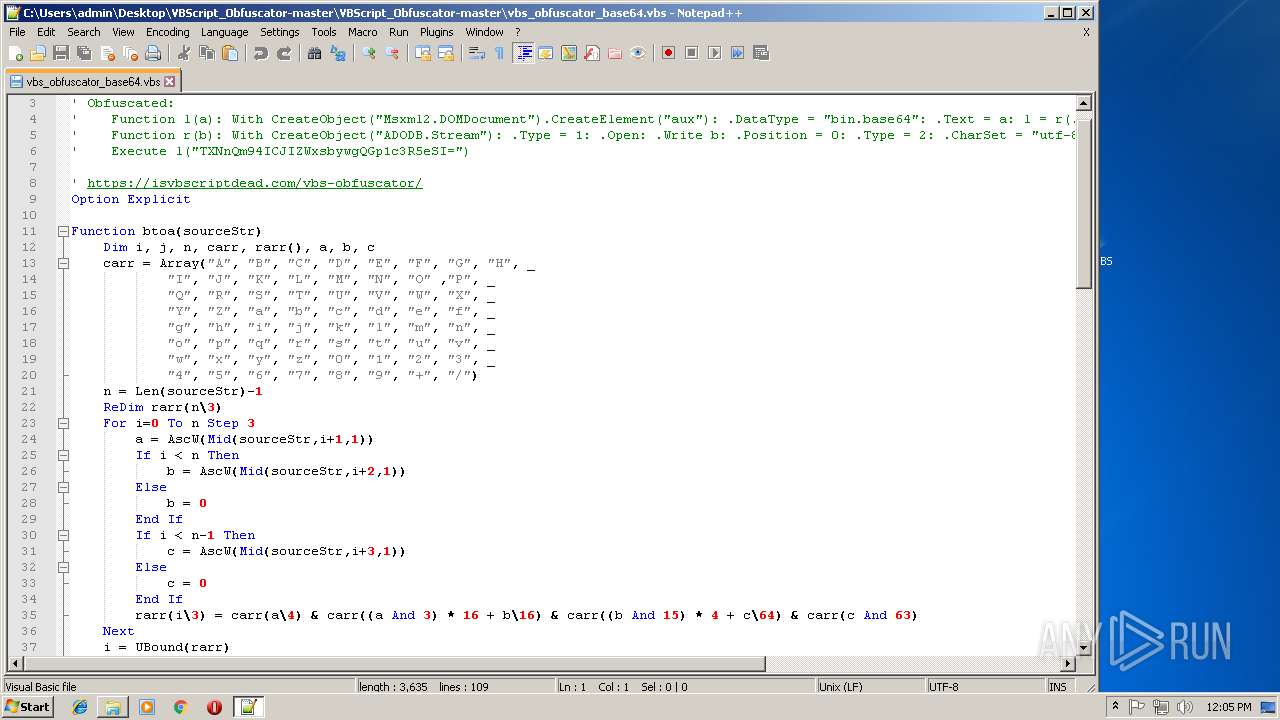
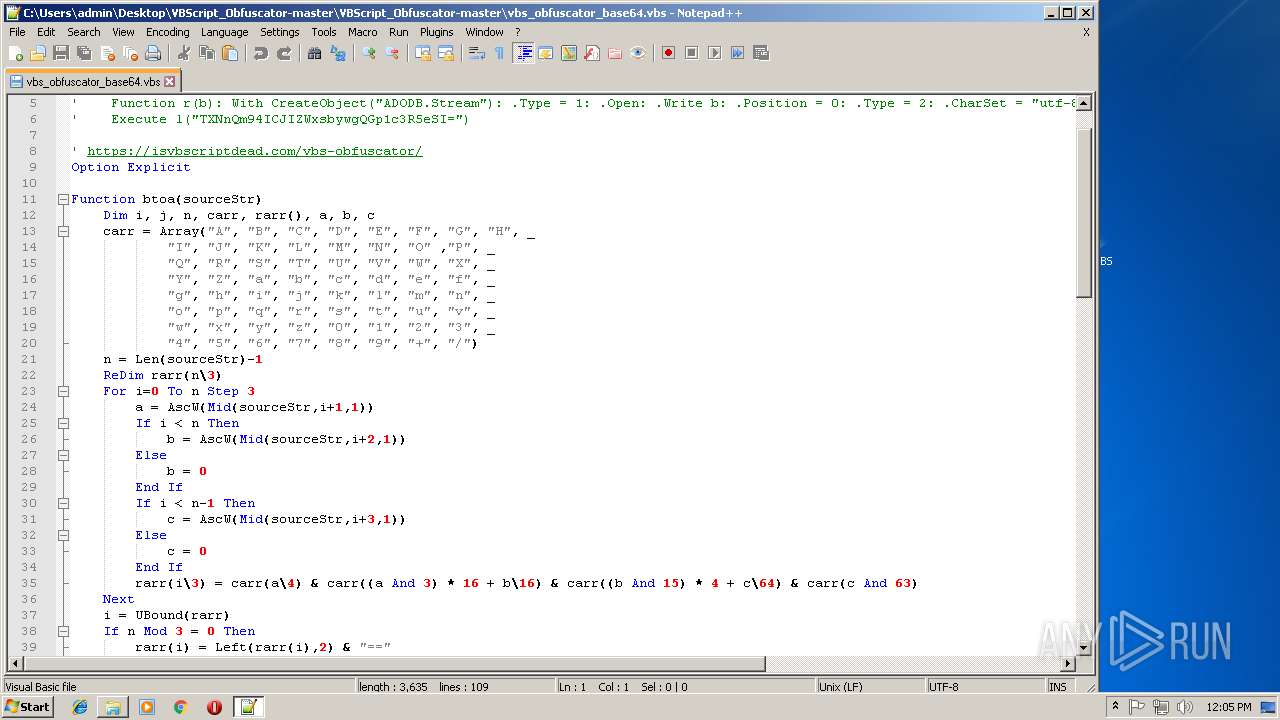
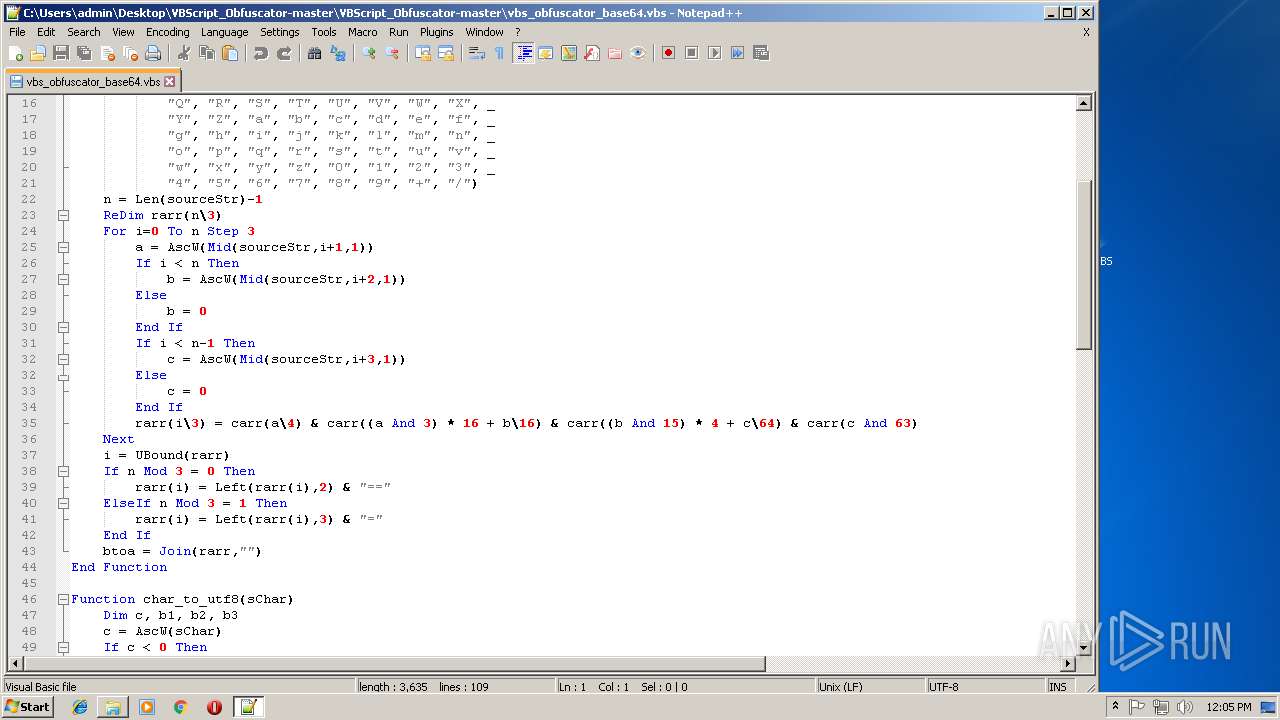
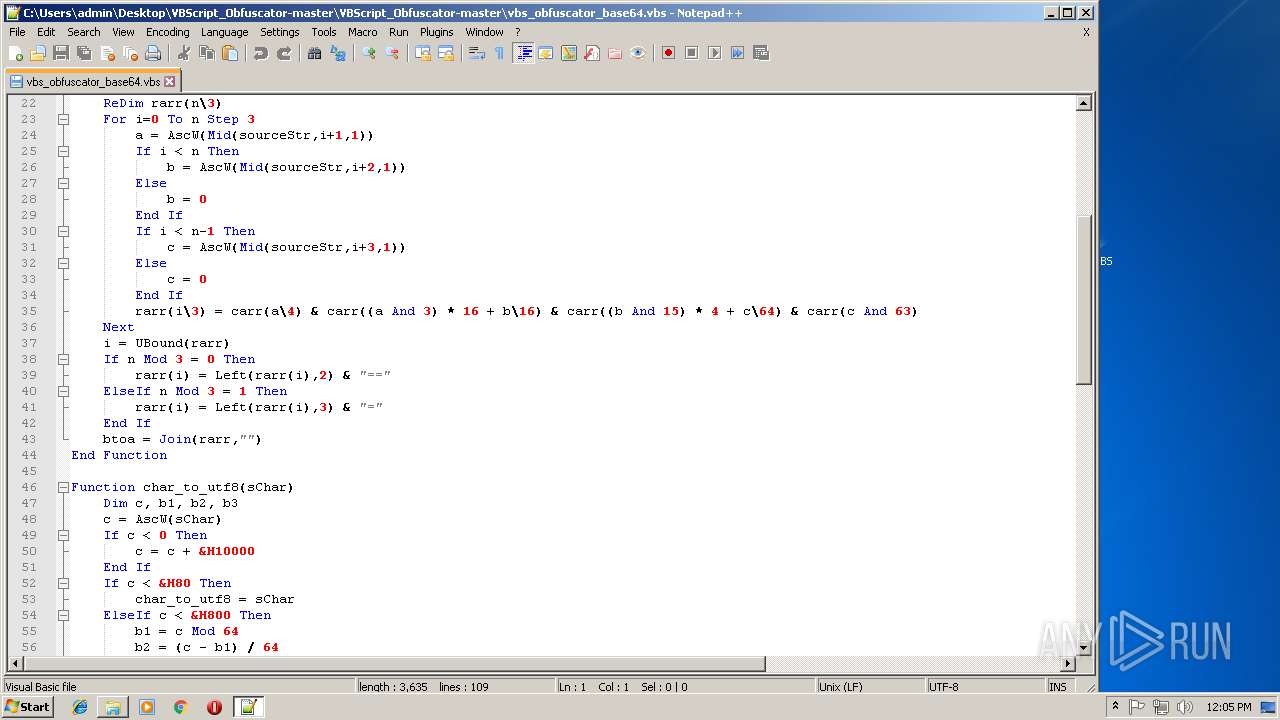
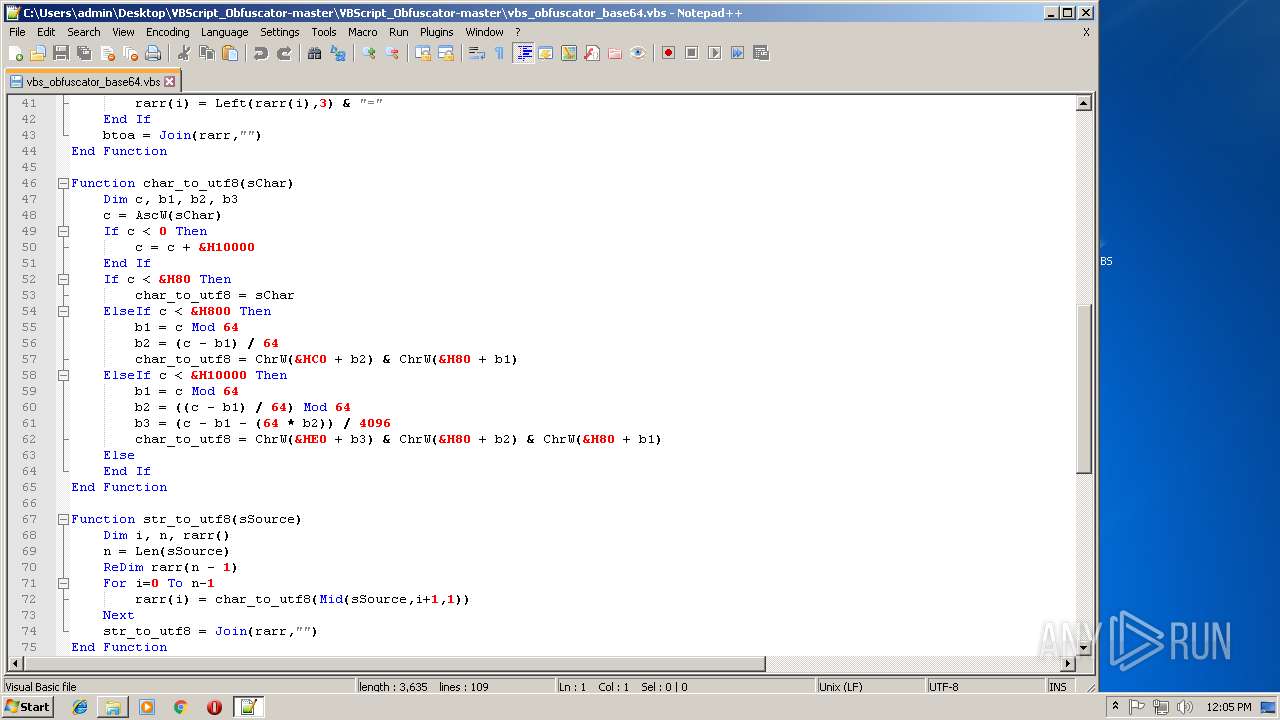
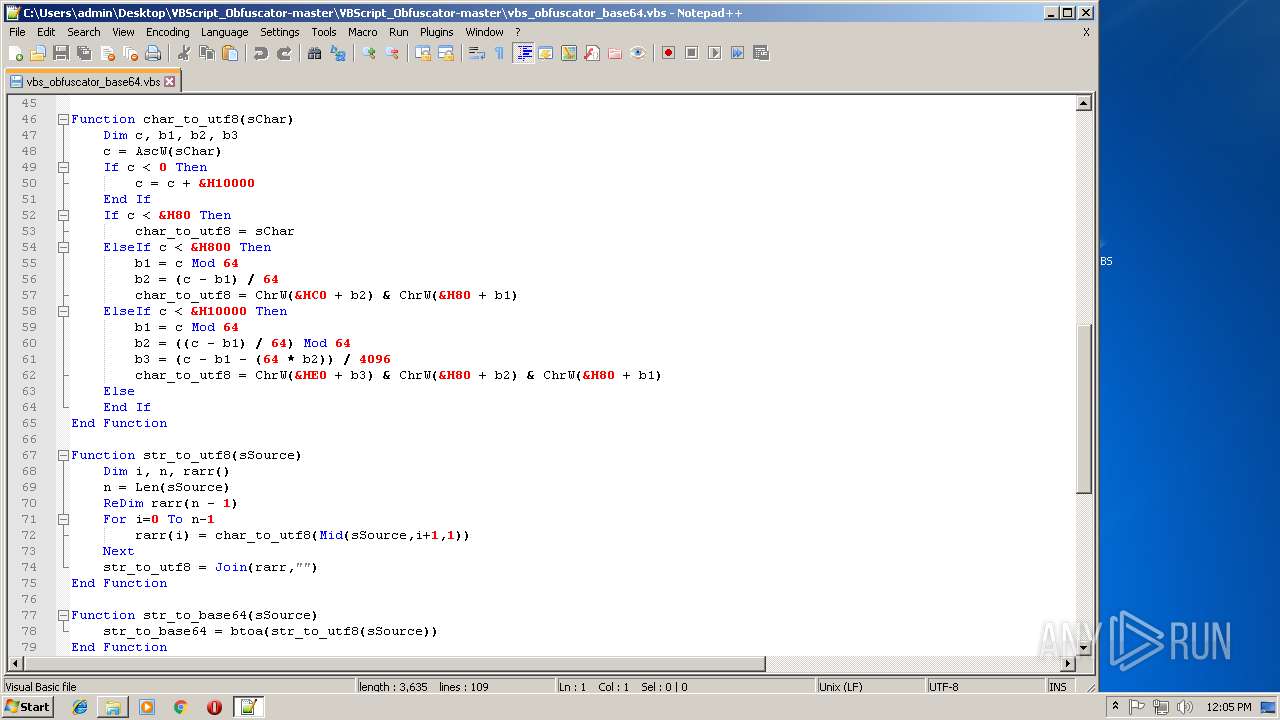
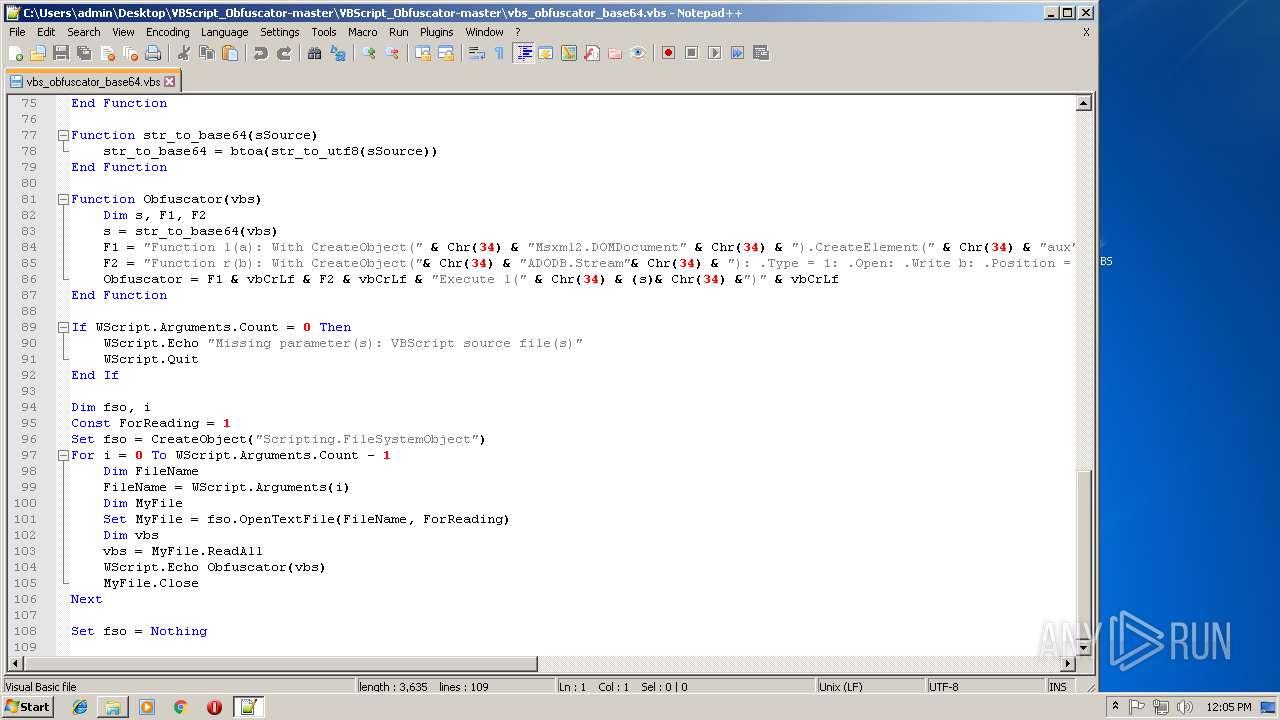
| 1684 | WinRAR.exe | C:\Users\admin\Desktop\VBScript_Obfuscator-master\VBScript_Obfuscator-master\vbs_obfuscator.vbs | text | |
MD5:8DF99CD324348F29CAC23D9061CC3257 | SHA256:36576E5B93DBB846CBB29166EC83FBA0BB572A1A3B98C3637B56CAE94A56030E | |||
| 1864 | WScript.exe | C:\Users\admin\AppData\Local\Tempwinlogon.exe | executable | |
MD5:C7EC0A4325030A4525625622E33C99A8 | SHA256:91684247AFEE1E61F2CBAF80BBCB3A4FC9474BD3F61E2FAC5A4D8270489BF311 | |||
| 3104 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:44982E1D48434C0AB3E8277E322DD1E4 | SHA256:3E661D3F1FF3977B022A0ACC26B840B5E57D600BC03DCFC6BEFDB408C665904C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.188.148:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 2.20.188.148:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
1056 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.20.188.148:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
3864 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
1056 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disablꌬѼ鋼⚌䶭ǔꊴѼVerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|