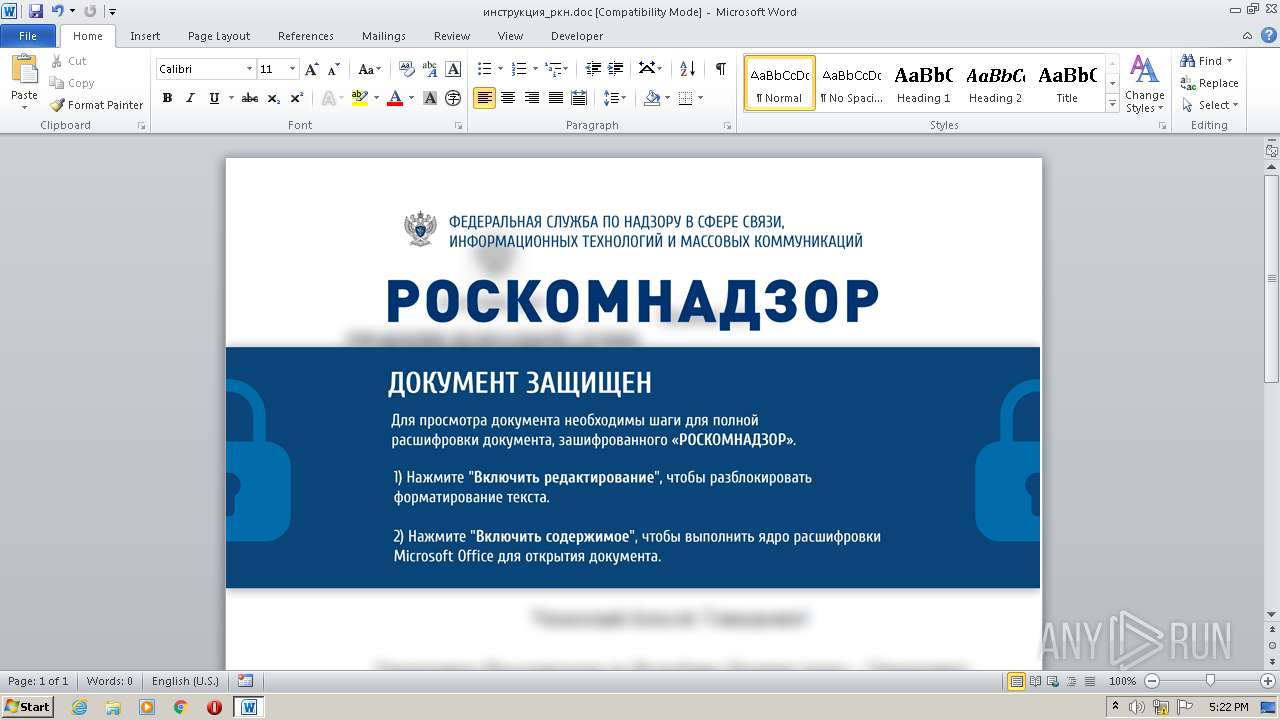
| File name: | инструкция_ркн.doc |
| Full analysis: | https://app.any.run/tasks/9280b2bb-d295-41a2-8d4f-ba22c389bf17 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 16:22:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: x, Template: Normal.dotm, Last Saved By: atel, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Mar 18 03:43:00 2022, Last Saved Time/Date: Fri Mar 18 15:20:00 2022, Number of Pages: 1, Number of Words: 99, Number of Characters: 570, Security: 0 |
| MD5: | 341610A5A0CC430F99F9F9BD694B04A9 |
| SHA1: | 9B520D709CEE6C57FBABA38F38A667B0B0691E86 |
| SHA256: | C7DD490ADB297B7F529950778B5A426E8068EA2DF58BE5D8FD49FE55B5331E28 |
| SSDEEP: | 24576:0Ltxfb5+PfLYk1eMavV4luzEMjor4Ln+oDSMrWRHeNDoH+sN7rUziacva0FmLZe+:0LtRbA7Yk1laewzjfCoDSM6xeNsH+Vc8 |
MALICIOUS
Starts POWERSHELL.EXE for commands execution
- WINWORD.EXE (PID: 2588)
Bypass execution policy to execute commands
- powershell.exe (PID: 3400)
Run PowerShell with an invisible window
- powershell.exe (PID: 3400)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 2588)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2588)
SUSPICIOUS
The process executes Powershell scripts
- WINWORD.EXE (PID: 2588)
The process hide an interactive prompt from the user
- WINWORD.EXE (PID: 2588)
The process hides Powershell's copyright startup banner
- WINWORD.EXE (PID: 2588)
Reads the Internet Settings
- powershell.exe (PID: 3400)
Unusual connection from system programs
- powershell.exe (PID: 3400)
INFO
The process uses the downloaded file
- WINWORD.EXE (PID: 2588)
The process checks LSA protection
- powershell.exe (PID: 3400)
Create files in a temporary directory
- powershell.exe (PID: 3400)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Lines: | 4 |
|---|---|
| Paragraphs: | 1 |
| Pages: | 1 |
| Characters: | 570 |
| Words: | 99 |
| TotalEditTime: | - |
| RevisionNumber: | 2 |
| LastPrinted: | 0000:00:00 00:00:00 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
| CompObjUserTypeLen: | 32 |
| HeadingPairs: |
|
| TitleOfParts: | |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 15 |
| CharCountWithSpaces: | 668 |
| Company: | - |
| CodePage: | Windows Cyrillic |
| Security: | None |
| ModifyDate: | 2022:03:18 15:20:00 |
| CreateDate: | 2022:03:18 03:43:00 |
| Software: | Microsoft Office Word |
| LastModifiedBy: | atel |
| Template: | Normal.dotm |
| Comments: | - |
| Keywords: | - |
| Author: | x |
| Subject: | - |
| Title: | - |
| Word97: | No |
| System: | Windows |
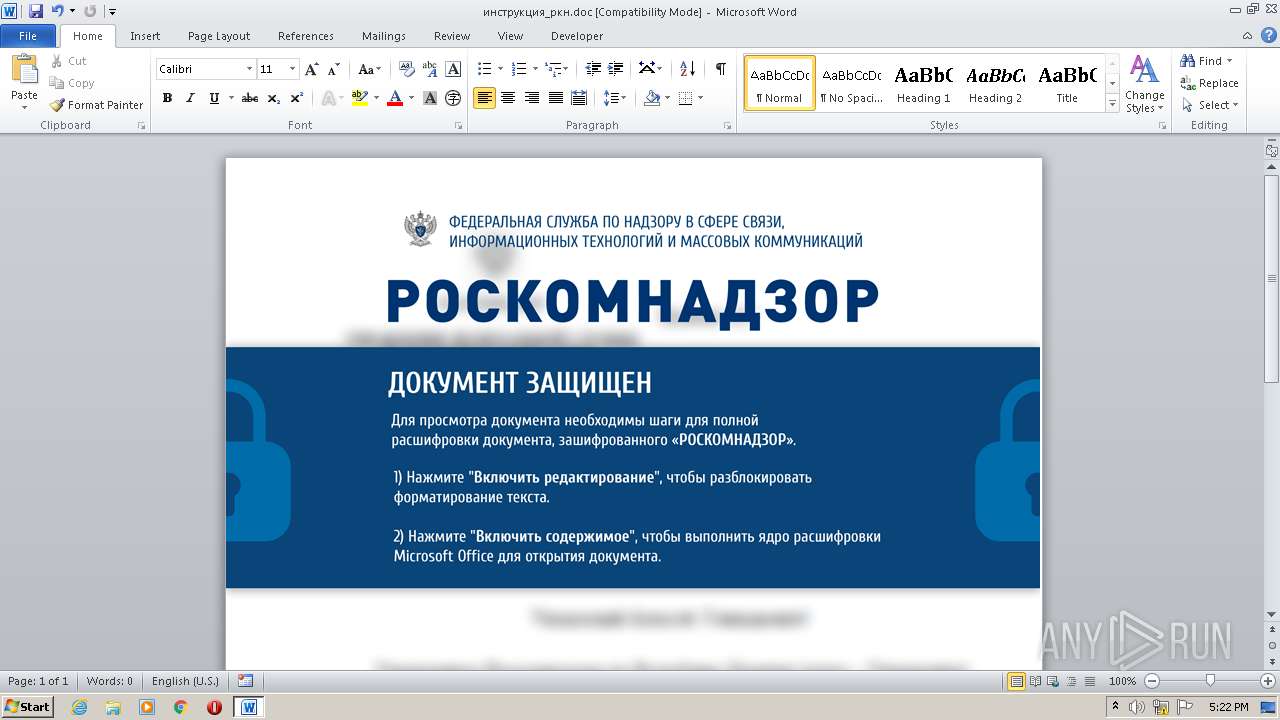
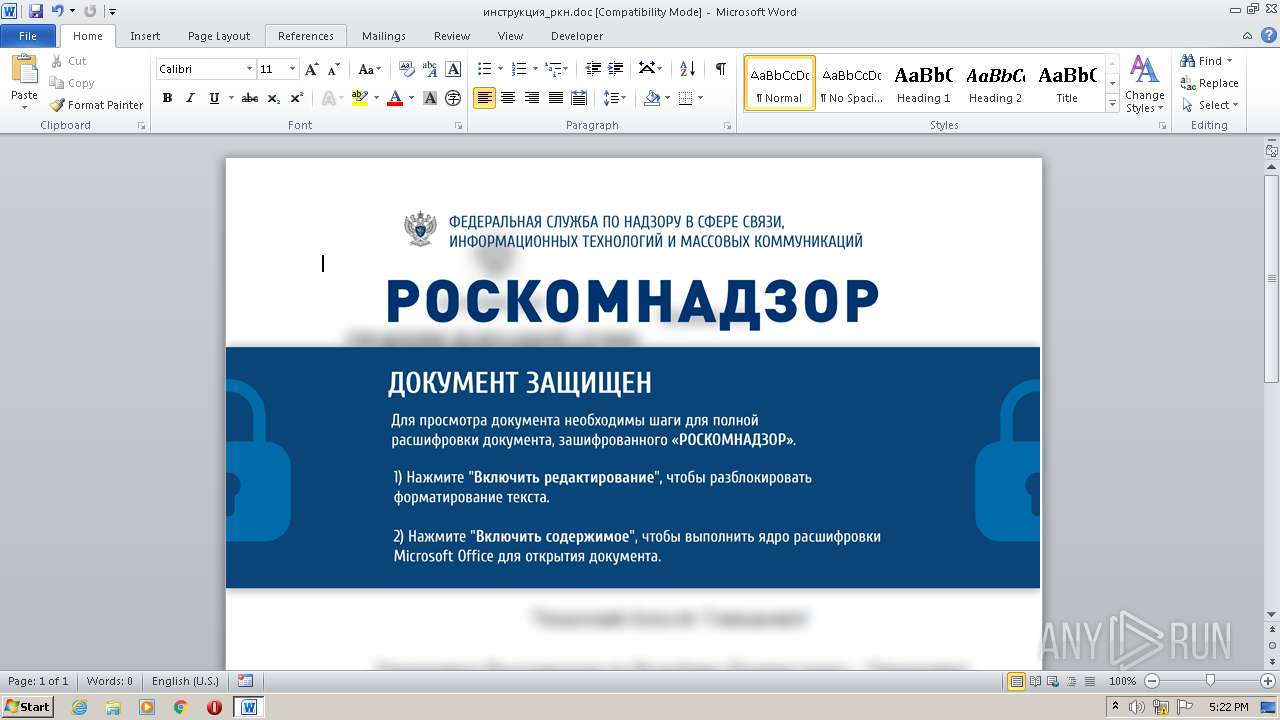
| DocFlags: | Has picture, 1Table, ExtChar |
| LanguageCode: | Russian |
| Identification: | Word 8.0 |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2588 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\инструкция_ркн.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3400 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ex bypass -NoLogo -WindowStyle Hidden -NonInteractive -f c:\users\admin\appdata\roaming\microsoft\templates\HkvWahS6osjcp1g.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
8 898
Read events
7 978
Write events
636
Delete events
284
Modification events
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2588) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
10
Text files
6
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF83B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C1D89D97.emf | emf | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$струкция_ркн.doc | pgc | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\HkvWahS6osjcp1g.ps1 | text | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\9sIAWssbW73TcYG.W4x9LosInhvOjtI | text | |
MD5:— | SHA256:— | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFA789B68BA867843F.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\9sIAWssbW73TcYG.W4x9LosInhvOjtI:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:D6B9E37780A881ABC68E64DB5E2F6E8F | SHA256:B96DAF2C8DC81081707312C0B41675CCF52A9A383969777B6991E1E51A5C4885 | |||
| 2588 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRL0001.tmp | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3400 | powershell.exe | 99.83.154.118:443 | swordoke.com | AMAZON-02 | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
swordoke.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Domain Observed Used for C2 Detected | ET MALWARE Win32/Backdoor Related Domain in DNS Lookup (swordoke .com) |
3400 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Backdoor Related Domain (swordoke .com in TLS SNI) |