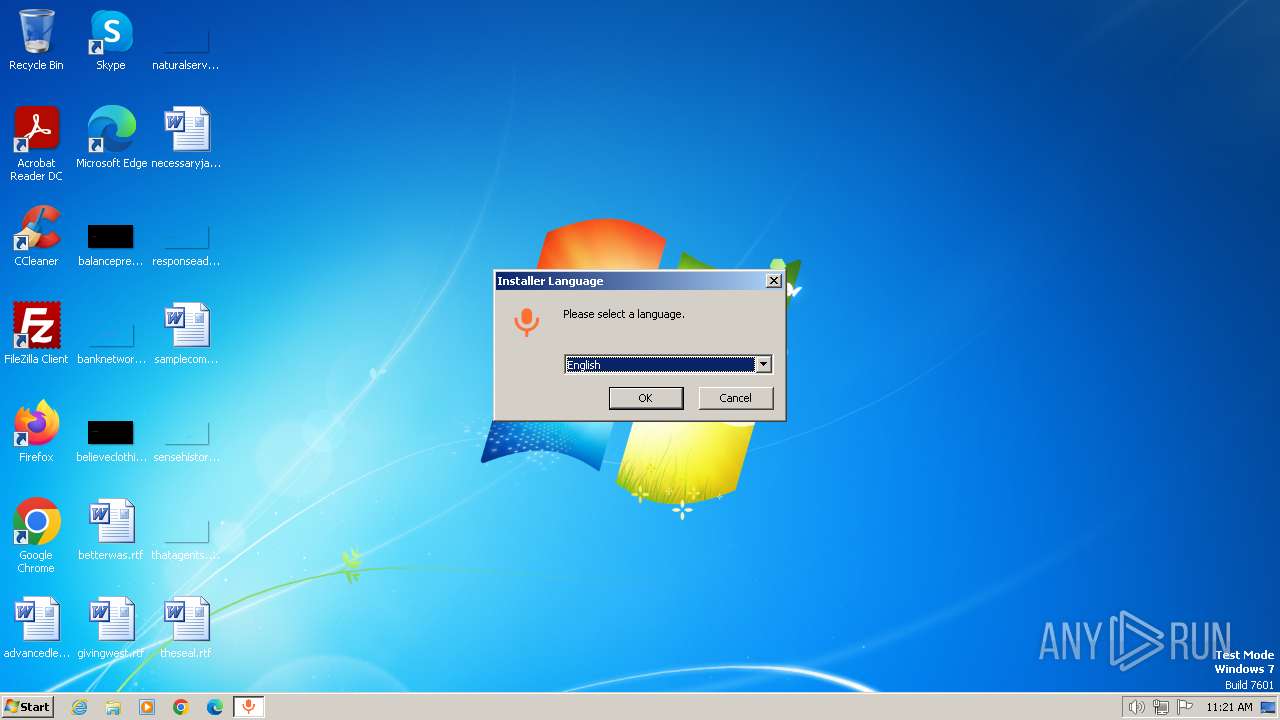
| File name: | WOMicClientSetup5_2.exe |
| Full analysis: | https://app.any.run/tasks/647a757f-6278-4b4c-b079-30ec9c103ea6 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2024, 11:21:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | D8C68825B8A2CD1F00736B617240684C |
| SHA1: | 7B68A0832785021E8883CEC41606E60FA4A887E6 |
| SHA256: | C7C7227A636B4C612CDF3F3D803BE3EF1CF8F9AEDAD1C5D6620E0B9F6E0931A8 |
| SSDEEP: | 24576:Y12rpcEd5xQyaYXnCTZh5GYP7INP4w6ZtwZdsIAljoXHNAi7JYYDd+7PJms:QkzSy/nClDzBaZfuo3HYnPJd |
MALICIOUS
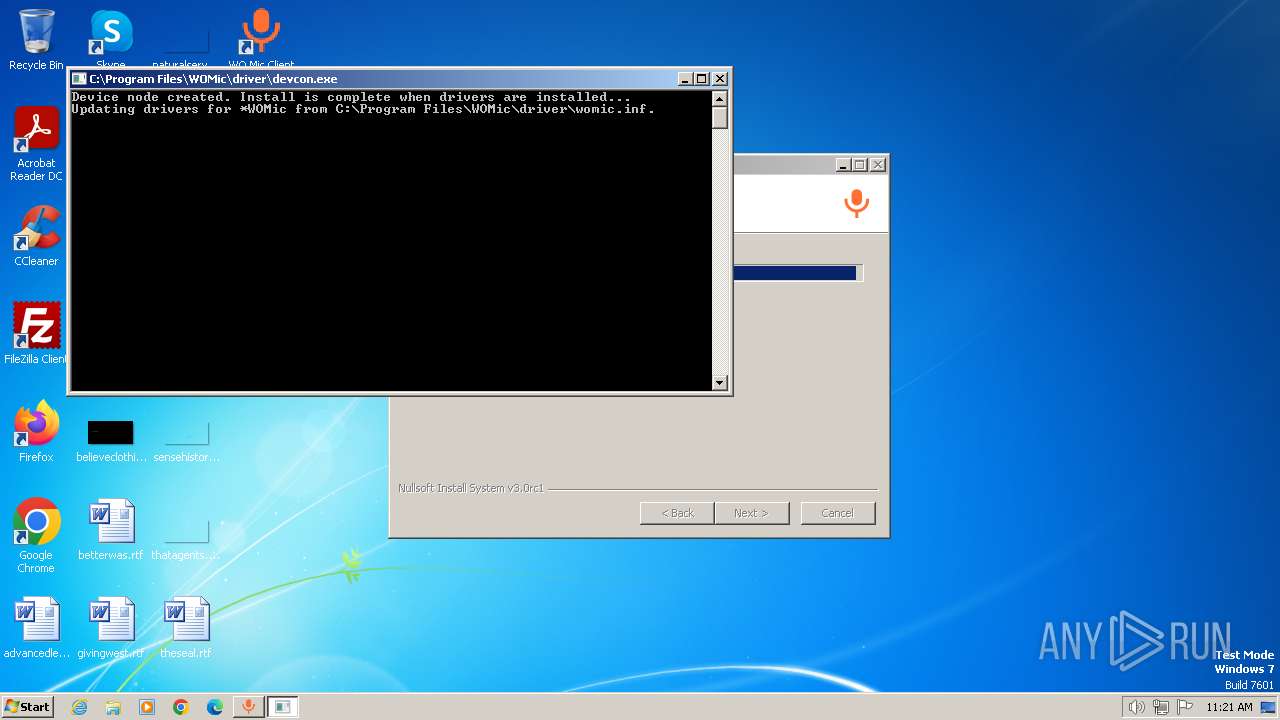
Drops the executable file immediately after the start
- WOMicClientSetup5_2.exe (PID: 2420)
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Creates a writable file in the system directory
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- WOMicClientSetup5_2.exe (PID: 2420)
The process creates files with name similar to system file names
- WOMicClientSetup5_2.exe (PID: 2420)
Executable content was dropped or overwritten
- WOMicClientSetup5_2.exe (PID: 2420)
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Starts application with an unusual extension
- WOMicClientSetup5_2.exe (PID: 2420)
Process drops legitimate windows executable
- WOMicClientSetup5_2.exe (PID: 2420)
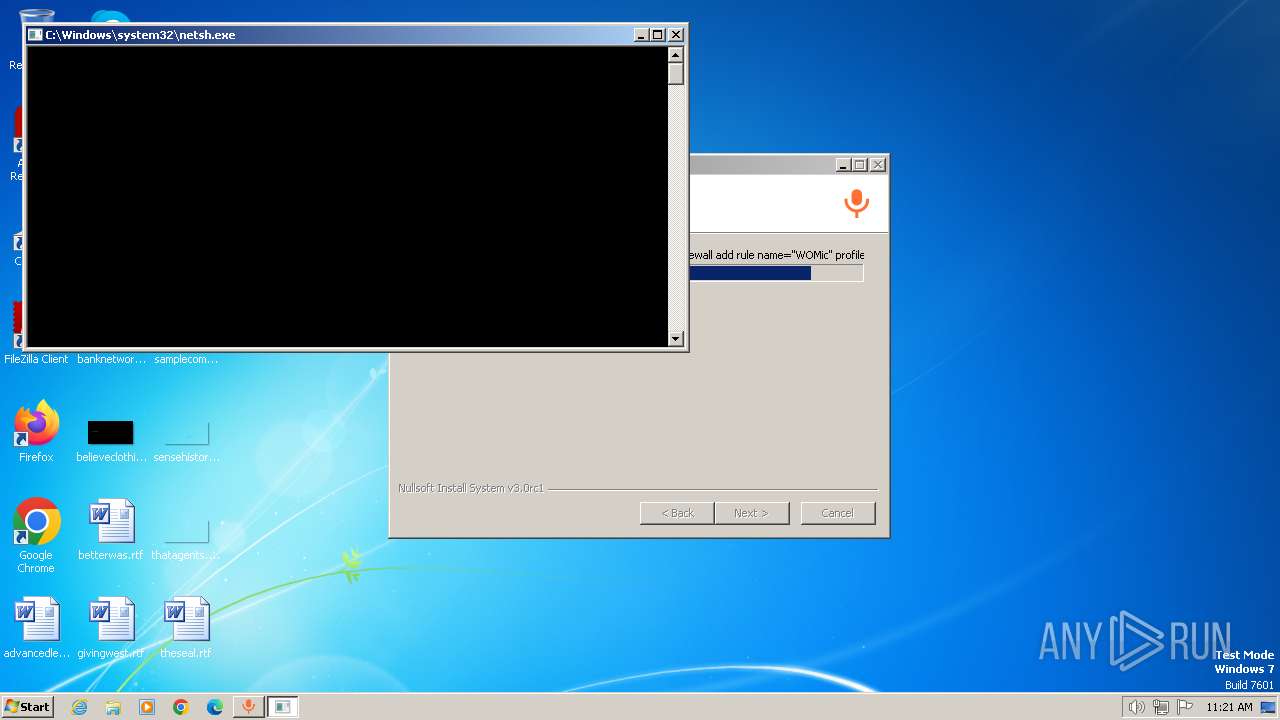
Uses NETSH.EXE to add a firewall rule or allowed programs
- WOMicClientSetup5_2.exe (PID: 2420)
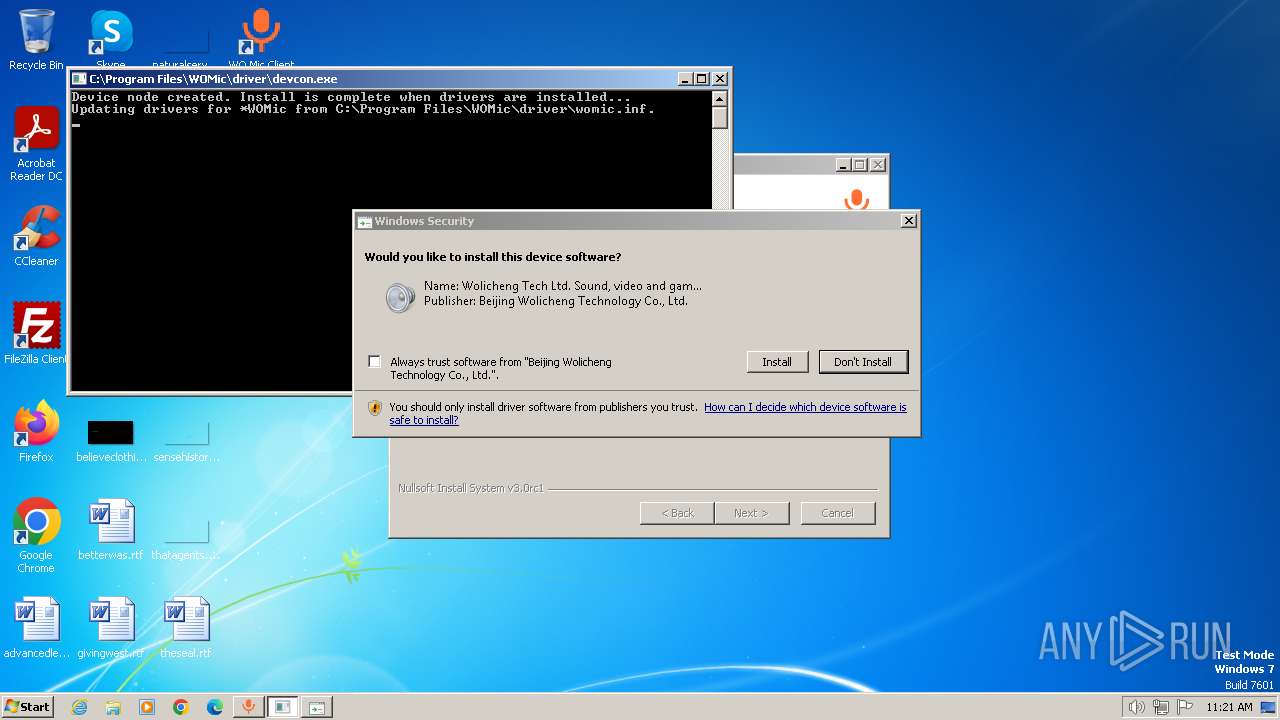
Drops a system driver (possible attempt to evade defenses)
- WOMicClientSetup5_2.exe (PID: 2420)
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Reads security settings of Internet Explorer
- devcon.exe (PID: 2480)
Checks Windows Trust Settings
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Reads settings of System Certificates
- devcon.exe (PID: 2480)
- rundll32.exe (PID: 2328)
Creates files in the driver directory
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Executes as Windows Service
- VSSVC.exe (PID: 1924)
INFO
Create files in a temporary directory
- WOMicClientSetup5_2.exe (PID: 2420)
- devcon.exe (PID: 2480)
Reads the computer name
- WOMicClientSetup5_2.exe (PID: 2420)
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Checks supported languages
- WOMicClientSetup5_2.exe (PID: 2420)
- nsB48.tmp (PID: 1380)
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
- WOMicClient.exe (PID: 2860)
Creates files in the program directory
- WOMicClientSetup5_2.exe (PID: 2420)
Creates files or folders in the user directory
- WOMicClientSetup5_2.exe (PID: 2420)
Reads the machine GUID from the registry
- devcon.exe (PID: 2480)
- drvinst.exe (PID: 632)
- drvinst.exe (PID: 1000)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2328)
Manual execution by a user
- WOMicClient.exe (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:03 22:19:02+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x32a0 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
56
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{5cfc84ad-f2d9-7b3d-70ec-a455e5d01b34}\womic.inf" "0" "66d2d8b0f" "000003DC" "WinSta0\Default" "00000550" "208" "c:\program files\womic\driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="WOMic" profile=any dir=in action=allow program="C:\Program Files\WOMic\womicclient.exe" enable=yes protocol=TCP | C:\Windows\System32\netsh.exe | — | WOMicClientSetup5_2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | DrvInst.exe "2" "211" "ROOT\MEDIA\0000" "C:\Windows\INF\oem2.inf" "womic.inf:StdMfg.ntx86:WOVAD_MicArray:1.5.0.0:*womic" "66d2d8b0f" "000003DC" "000005E0" "000005E8" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\nsB48.tmp" devcon.exe hwids *WOMic | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\nsB48.tmp | — | WOMicClientSetup5_2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225501 Modules
| |||||||||||||||
| 1652 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="WOMic" profile=any dir=in action=allow program="C:\Program Files\WOMic\womicclient.exe" enable=yes protocol=UDP | C:\Windows\System32\netsh.exe | — | WOMicClientSetup5_2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1924 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Local\Temp\WOMicClientSetup5_2.exe" | C:\Users\admin\AppData\Local\Temp\WOMicClientSetup5_2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2128 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="WOMic" profile=any dir=out action=allow program="C:\Program Files\WOMic\womicclient.exe" enable=yes protocol=UDP | C:\Windows\System32\netsh.exe | — | WOMicClientSetup5_2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | C:\Windows\system32\netsh.exe advfirewall firewall add rule name="WOMic" profile=any dir=out action=allow program="C:\Program Files\WOMic\womicclient.exe" enable=yes protocol=TCP | C:\Windows\System32\netsh.exe | — | WOMicClientSetup5_2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{6e096c00-ed77-7f01-e649-a36dc6ef8c11} Global\{277f914e-640b-48a5-c6ef-8c11c151084f} C:\Windows\System32\DriverStore\Temp\{50db485e-6bb2-31a0-4ccd-410942755312}\womic.inf C:\Windows\System32\DriverStore\Temp\{50db485e-6bb2-31a0-4ccd-410942755312}\womic.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 470
Read events
18 919
Write events
551
Delete events
0
Modification events
| (PID) Process: | (2420) WOMicClientSetup5_2.exe | Key: | HKEY_CURRENT_USER\Software\Wolicheng\WOMic |
| Operation: | write | Name: | language |
Value: 1033 | |||
| (PID) Process: | (1652) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (764) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2128) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2172) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2480) devcon.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (632) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2328) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (632) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (632) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
28
Suspicious files
22
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\System.dll | executable | |
MD5:0FF2D70CFDC8095EA99CA2DABBEC3CD7 | SHA256:982C5FB7ADA7D8C9BC3E419D1C35DA6F05BC5DD845940C179AF3A33D00A36A8B | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\LangDLL.dll | executable | |
MD5:174708997758321CF926B69318C6C3F5 | SHA256:F577B66492E97C7B8BF515398D8DEB745ABAFD74F56FC03E67FCE248EBBEB873 | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\nsB48.tmp | executable | |
MD5:01E76FE9D2033606A48D4816BD9C2D9D | SHA256:EE052FD5141BF769B841846170AABF0D7C2BB922C74C623C3F109344534F7A70 | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\nsExec.dll | executable | |
MD5:01E76FE9D2033606A48D4816BD9C2D9D | SHA256:EE052FD5141BF769B841846170AABF0D7C2BB922C74C623C3F109344534F7A70 | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Program Files\WOMic\WOMicClient.exe | executable | |
MD5:26BA164873F020120E2267AC1CF16D43 | SHA256:9E07DBCE584991A821EA7030BC8228271D1D2AA8CE3D4BF8F1D2309796D7EBCF | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Program Files\WOMic\driver\devcon.exe | executable | |
MD5:47CB56A5F8217519BBF46E0D03194770 | SHA256:24F585E58A7C4FD289DC9FF782EB3D82C125AEFDAFAB11AAFBB877D0282304BD | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Program Files\WOMic\Resource_en.dll | executable | |
MD5:A164EFB21A00F532510311E6FBBA17D0 | SHA256:98549D94B3CBDB7A905A83FAB84BBD393DDD18AF5A4455BB5CDB04919BB0C104 | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Program Files\WOMic\Resource_ru.dll | executable | |
MD5:E26ED7B860D4D5FC63E822F82A25D4A0 | SHA256:82099AA1A1334A60624B0EB59AF38BDE790142A23E8727634E10B46BD161CF1D | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2420 | WOMicClientSetup5_2.exe | C:\Users\admin\AppData\Local\Temp\nsgFEA5.tmp\nsDialogs.dll | executable | |
MD5:D6C3DD680C6467D07D730255D0EE5D87 | SHA256:AEDB5122C12037BCF5C79C2197D1474E759CF47C67C37CDB21CF27428854A55B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.74:49165 | — | — | — | unknown |