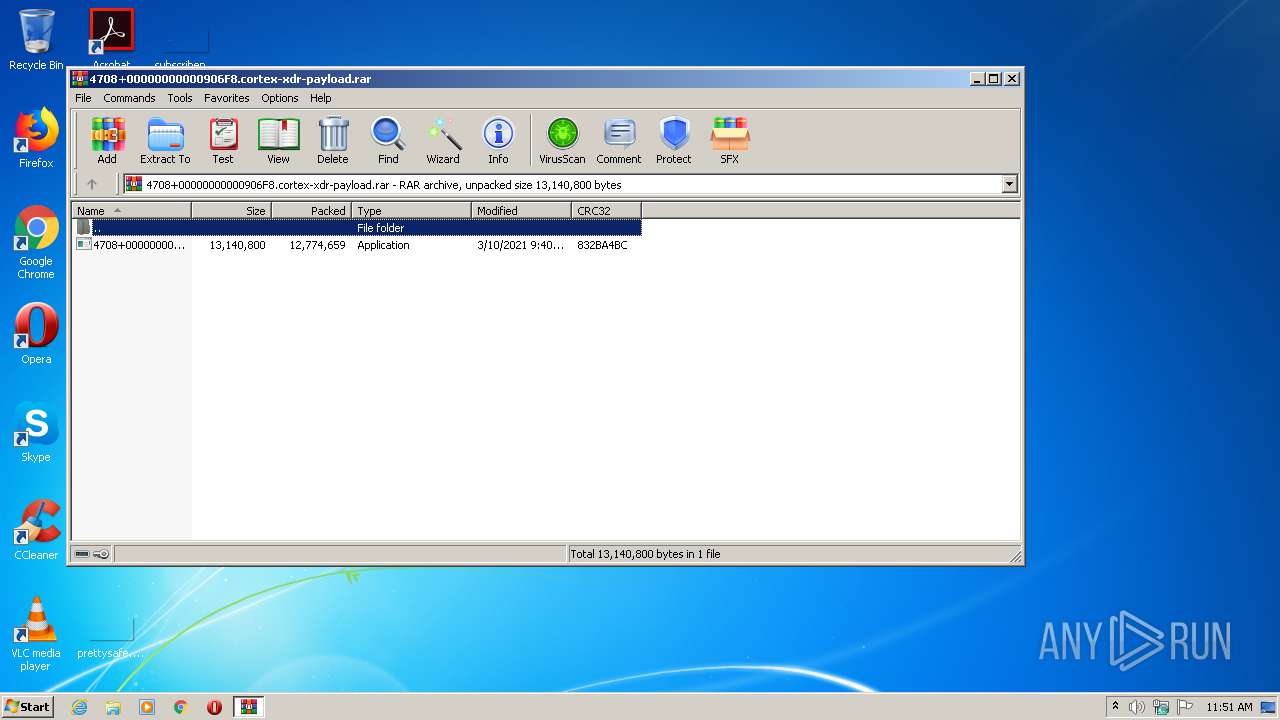
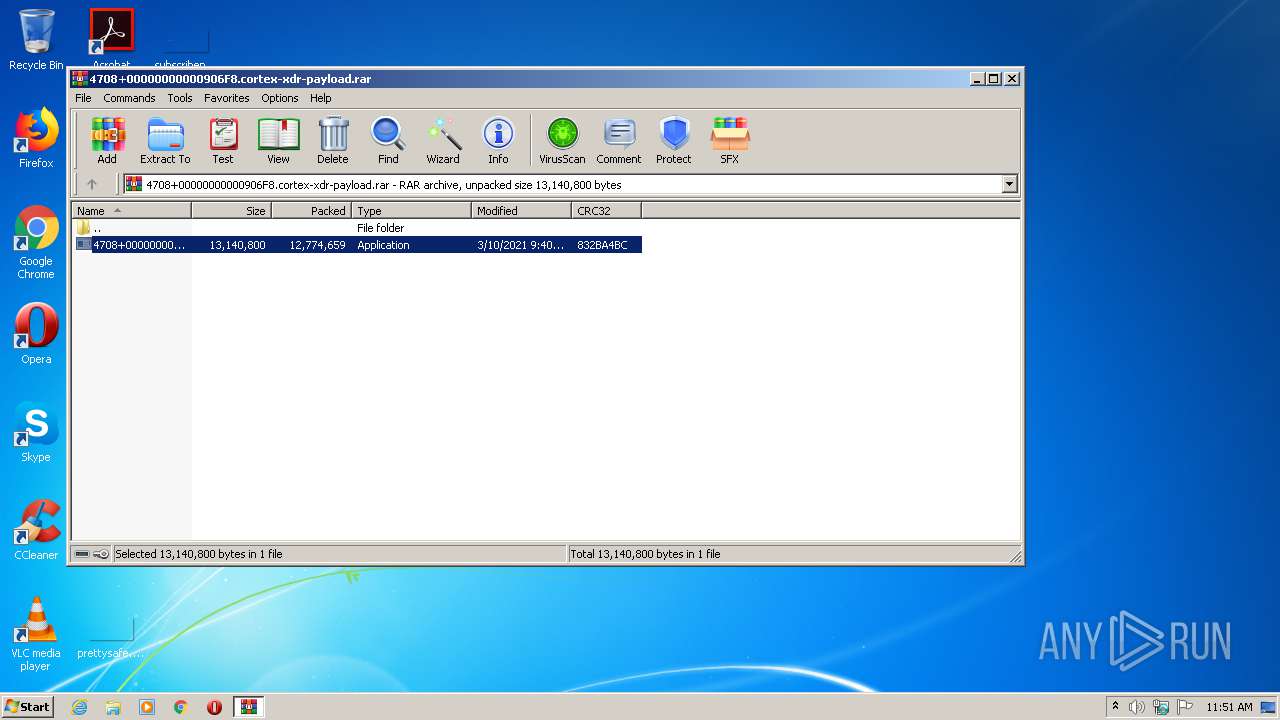
| File name: | 4708+00000000000906F8.cortex-xdr-payload.rar |
| Full analysis: | https://app.any.run/tasks/81543193-9917-4edf-bb08-55e7bd552a0d |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2021, 10:50:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A45C9B2EC20A41D56859C668F978C4C8 |
| SHA1: | 56F9A05F304D2E6398F318FAC91102CDDF0BAB55 |
| SHA256: | C7AC5E124DD773027168EEA4EBC307CE39D7D093347EAA8E19A638A0E6403EC2 |
| SSDEEP: | 393216:5a3/FjAP/M0DNf62Dkrx8Fvn4DLl1Z03s2h8aywoVn5:50/Fekf++89qR1C3flE |
MALICIOUS
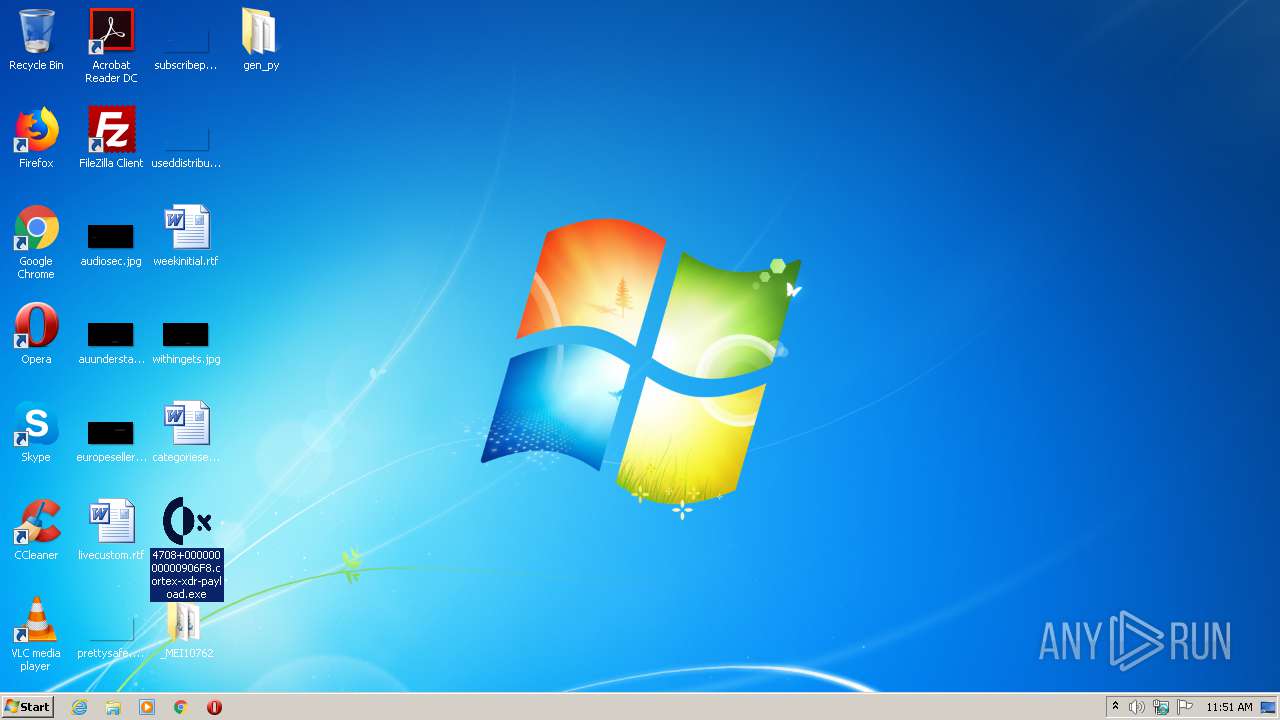
Application was dropped or rewritten from another process
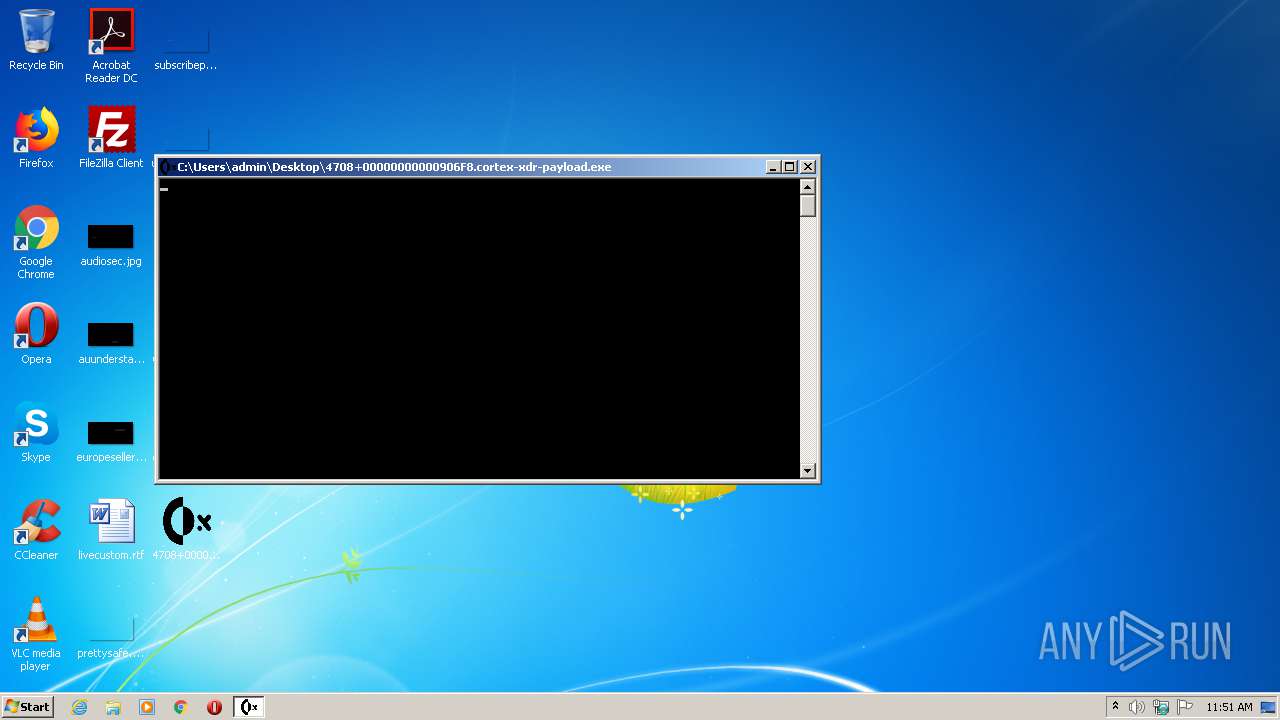
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1424)
Loads dropped or rewritten executable
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1424)
Drops executable file immediately after starts
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2776)
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
Drops a file with a compile date too recent
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
Drops a file with too old compile date
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
Application launched itself
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
Drops a file that was compiled in debug mode
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
Loads Python modules
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1424)
INFO
Dropped object may contain Bitcoin addresses
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
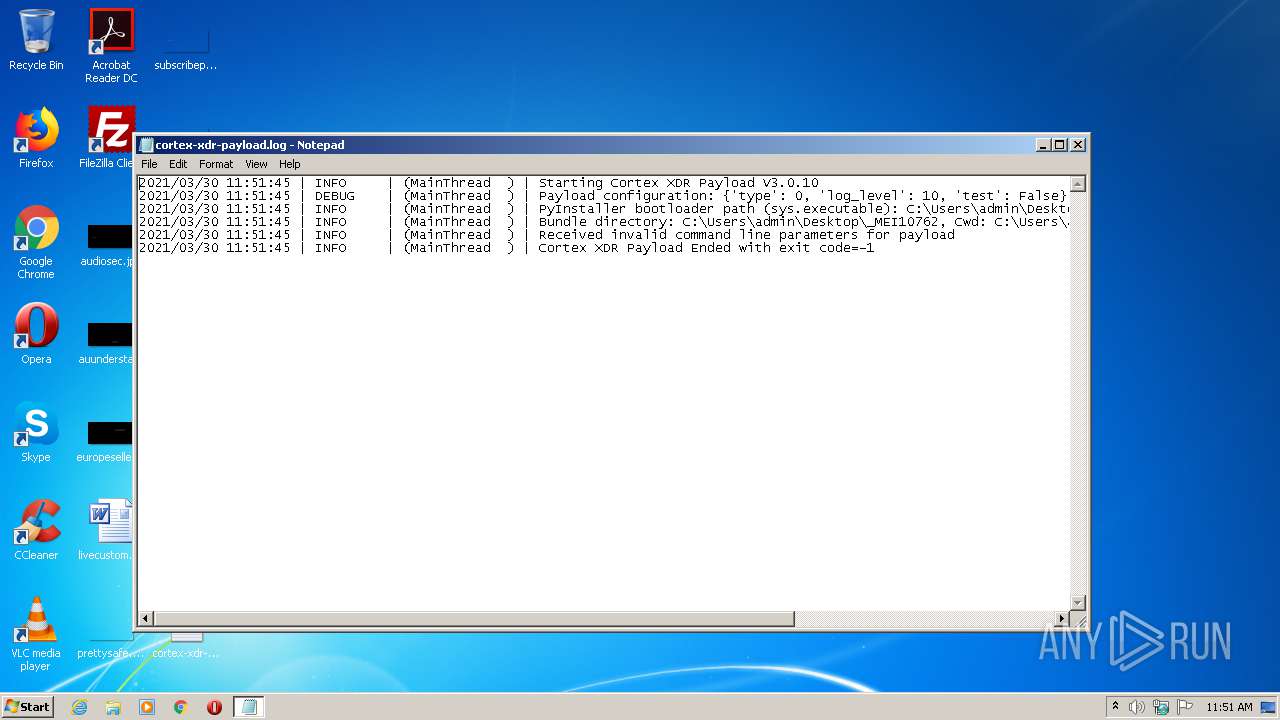
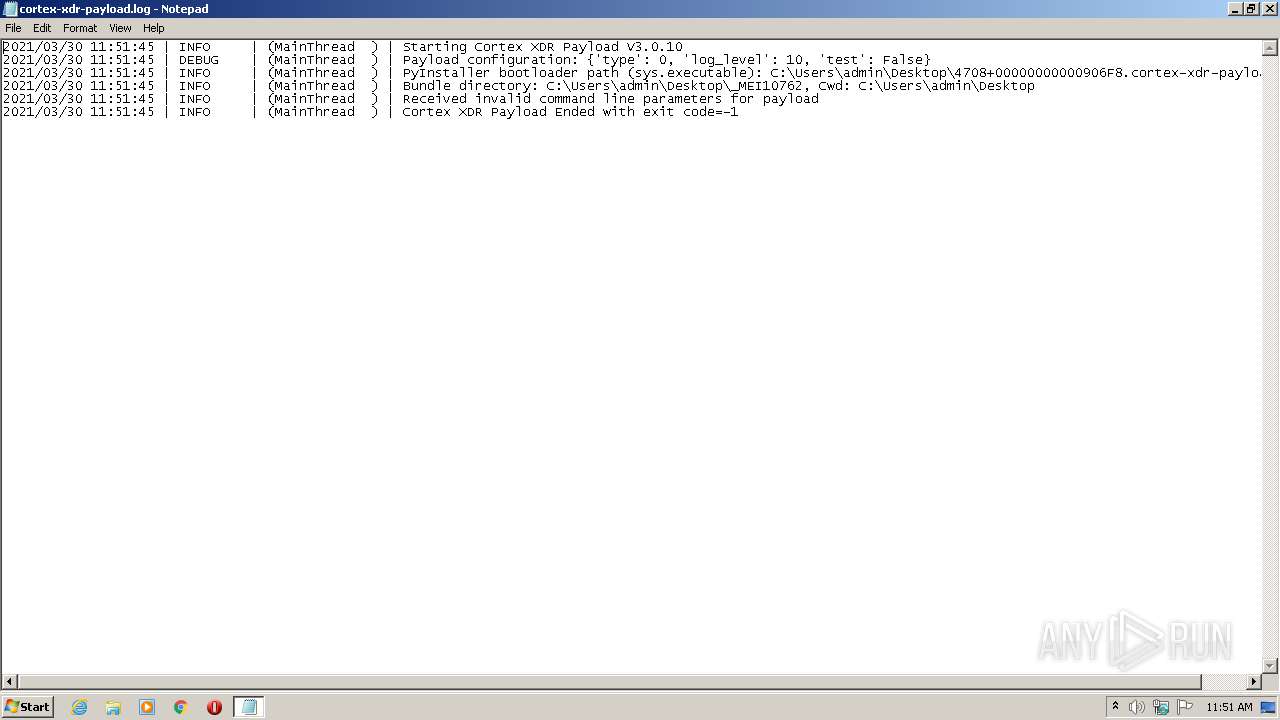
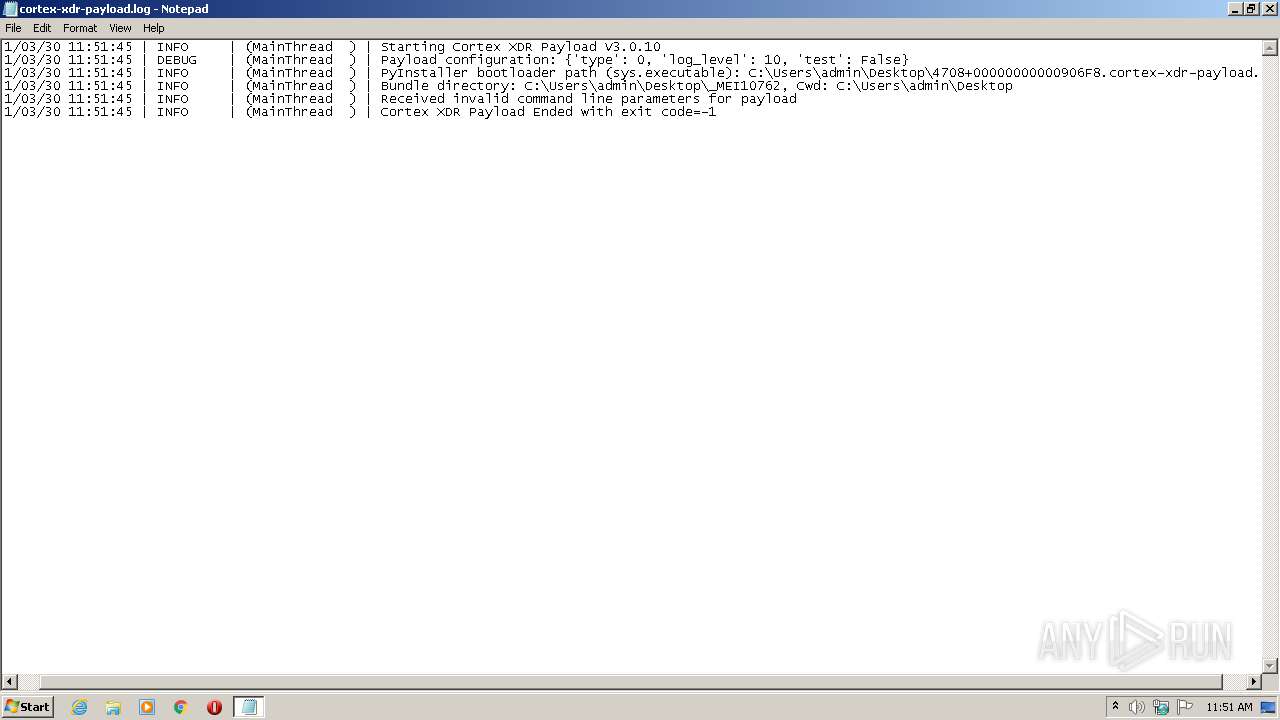
Manual execution by user
- 4708+00000000000906F8.cortex-xdr-payload.exe (PID: 1076)
- NOTEPAD.EXE (PID: 1880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1076 | "C:\Users\admin\Desktop\4708+00000000000906F8.cortex-xdr-payload.exe" | C:\Users\admin\Desktop\4708+00000000000906F8.cortex-xdr-payload.exe | explorer.exe | ||||||||||||
User: admin Company: Palo Alto Networks Integrity Level: HIGH Description: Cortex XDR Payload Exit code: 0 Version: 3.0.10 Modules
| |||||||||||||||
| 1424 | "C:\Users\admin\Desktop\4708+00000000000906F8.cortex-xdr-payload.exe" | C:\Users\admin\Desktop\4708+00000000000906F8.cortex-xdr-payload.exe | — | 4708+00000000000906F8.cortex-xdr-payload.exe | |||||||||||
User: admin Company: Palo Alto Networks Integrity Level: HIGH Description: Cortex XDR Payload Exit code: 0 Version: 3.0.10 Modules
| |||||||||||||||
| 1880 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\cortex-xdr-payload.log | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2776 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\4708+00000000000906F8.cortex-xdr-payload.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
482
Read events
460
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4708+00000000000906F8.cortex-xdr-payload.rar | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
90
Suspicious files
2
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2776 | WinRAR.exe | C:\Users\admin\Desktop\4708+00000000000906F8.cortex-xdr-payload.exe | executable | |
MD5:— | SHA256:— | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_sqlite3.pyd | executable | |
MD5:218DA11C9B2295D5C645ECB7629CD44D | SHA256:5987B2FCCA0698710F3572F222A6AEF3EFD9A6A32C002A11DD33C816BD9B58D8 | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_multiprocessing.pyd | executable | |
MD5:05AB494CF791A50E4F8D2FFE1D3E1F3C | SHA256:4959342924E22B6A16EBC5C1ED39552E981515401EDA770E4AC87FD12ACF53F8 | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_decimal.pyd | executable | |
MD5:5596249B64C074374EAA1D4084E336C3 | SHA256:673BD4CACF3B5F8DA67C9C84E03E238961CA98683483DE78D0A6410200F7ABA6 | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_lzma.pyd | executable | |
MD5:F91A9F1F2EFEE2F5DBAE42EA5D5D7153 | SHA256:1F82BB06C79B6B392C92CAD87FFA736377FA25CD6D10DA8D61441D42C0D0101E | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_queue.pyd | executable | |
MD5:234F63AE981F5A8E87DBABDA8CEEA32A | SHA256:3E1304AFDCD900748F62D15F93005E65457B9466454E322D065852603C510AC8 | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_socket.pyd | executable | |
MD5:B3AF79BBFD7D5C5285660819792A3A9C | SHA256:EB6132B253C40D7C3E00B2BBB392A1573075F8BBC0B2D59E2B077D2CFE8B028C | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_ssl.pyd | executable | |
MD5:2825BAE93CD459D835B74892C9BD80DB | SHA256:AF4379FDC8BD41F7A8A4B509DE949202CCDB5E4825797D7A5DDDD5E77671382C | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\_hashlib.pyd | executable | |
MD5:4F51ED287BBAE386090A9BCC3531B2B8 | SHA256:5B6DA4B43C258B459159C4FBC7AD3521B387C377C058FE77AD74BA000606D72E | |||
| 1076 | 4708+00000000000906F8.cortex-xdr-payload.exe | C:\Users\admin\Desktop\_MEI10762\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:B951011BA021C374455E8D1E18AF84D2 | SHA256:1C057286BDF0CB90F7DD1FECF5E8AFBCFF1E27F2A94612967C0634AE639CA43D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report