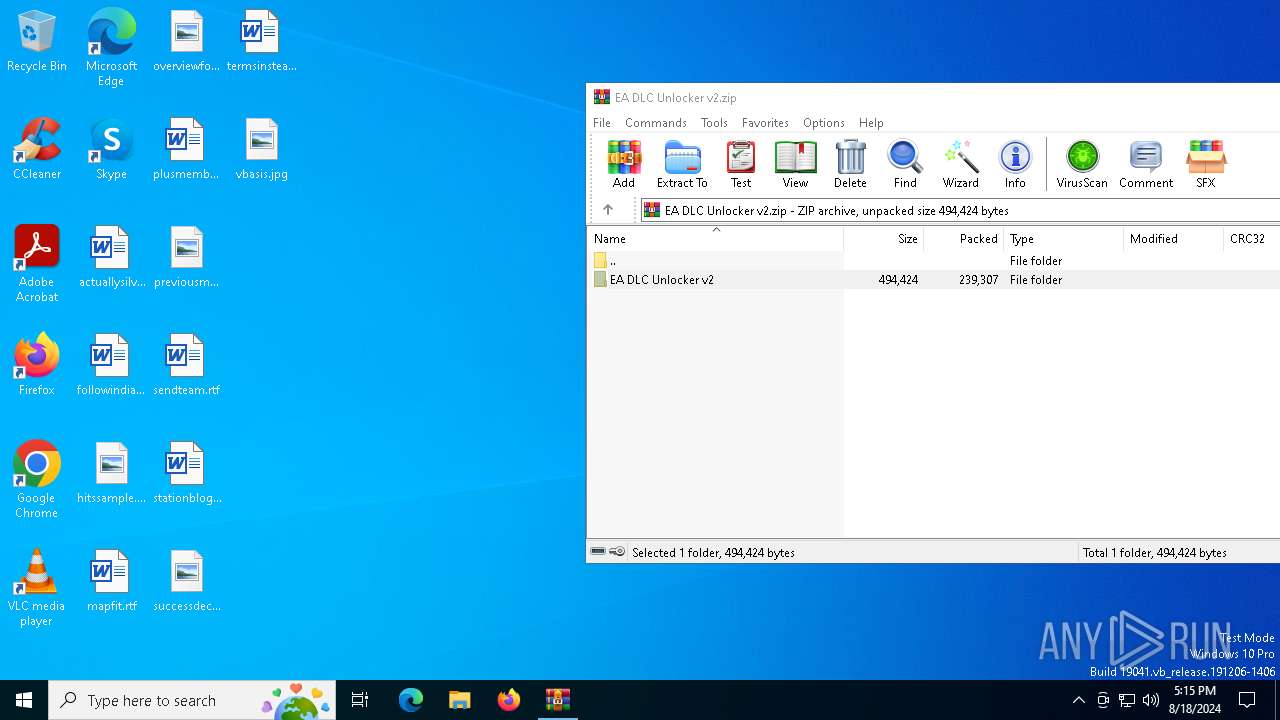
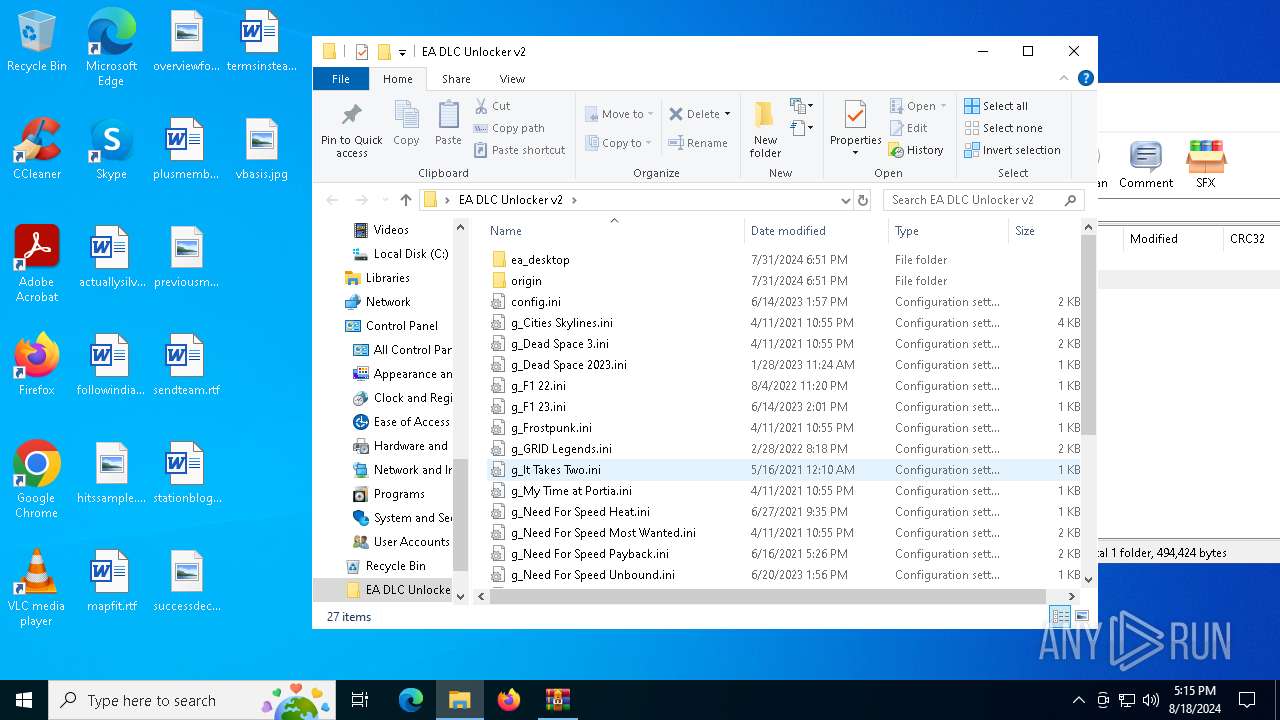
| File name: | EA DLC Unlocker v2.zip |
| Full analysis: | https://app.any.run/tasks/23725fb7-1c61-47a4-b5c0-38cc4ad93263 |
| Verdict: | Malicious activity |
| Analysis date: | August 18, 2024, 17:15:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 25E0C5EB4374D190D0507B17DFC4F54A |
| SHA1: | C52649721B684F1B0F8DADFF00929C1D225450BD |
| SHA256: | C797312153628FA1AA735E28DCD1646DD8BC97900047FCFFA55F7398E05096BD |
| SSDEEP: | 6144:vLUdDKwwV33Lj/p3rNvKEQ9yOoOi+BBttJrWFXydjNKfXiS:vLs+RJpbBFUi+BBttJyUa7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6392)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6892)
Application launched itself
- cmd.exe (PID: 6892)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6892)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6892)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6892)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6892)
INFO
Manual execution by a user
- cmd.exe (PID: 6892)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:06:14 13:57:52 |
| ZipCRC: | 0x6b4c0420 |
| ZipCompressedSize: | 748 |
| ZipUncompressedSize: | 1360 |
| ZipFileName: | EA DLC Unlocker v2/config.ini |
Total processes
139
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6792 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
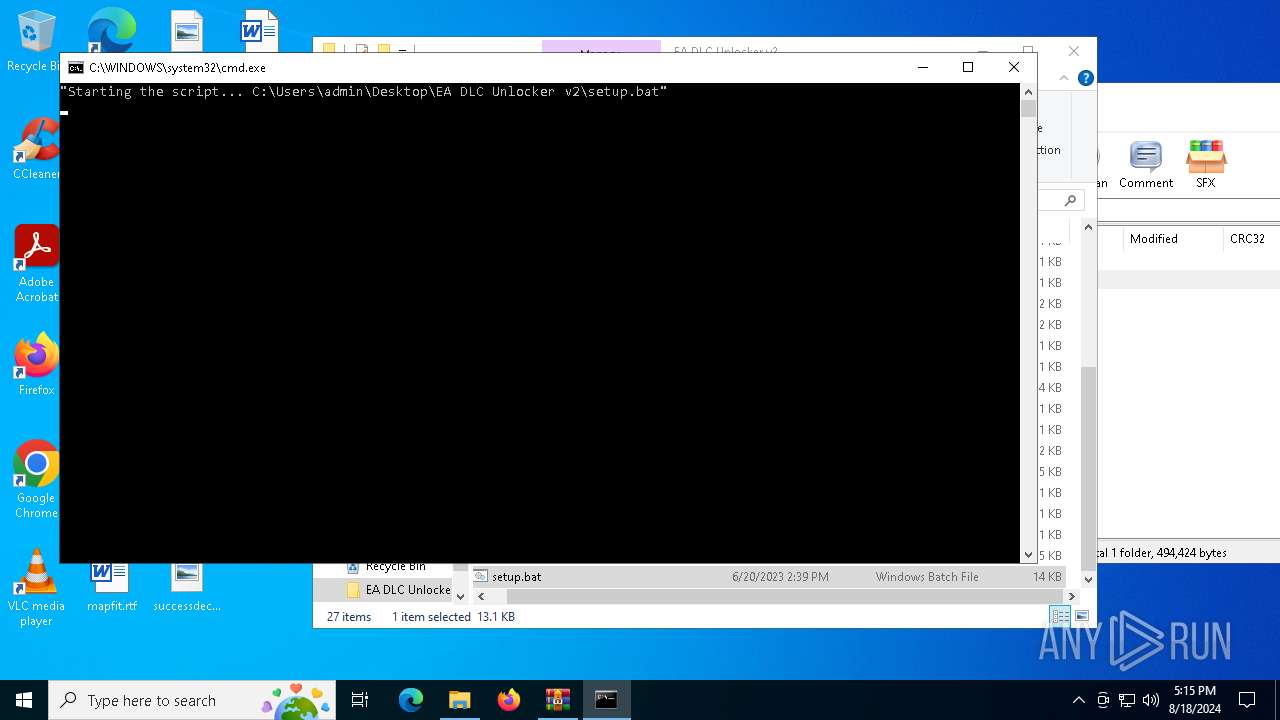
| 6892 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EA DLC Unlocker v2\setup.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6952 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo marco " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6968 | findstr /C:"polo" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6996 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo marco " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7004 | findstr /V /C:"polo" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7044 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "C:\Users\admin\Desktop\EA DLC Unlocker v2\" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | findstr /V /C:"C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 250
Read events
10 242
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EA DLC Unlocker v2.zip | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
0
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\ea_desktop\version.dll | executable | |
MD5:B69243228B677FDACAC06CE9365A4571 | SHA256:70553A2B4D53EDDF1EEB290E346A9B562C71F52D46874BFB708E9D962469A736 | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\config.ini | ini | |
MD5:9CD8592F5B8934FEC8B47994C4FDA5B6 | SHA256:16C7A3A47096394E59F204FAB91360F71AA2157BB1EDCFCCF1824B3A0D9352FF | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_Dead Space 3.ini | text | |
MD5:19F5DEDA4368C463D16687109ABF543D | SHA256:8996053E41CE56F0822A2A3E9449F3960FF1D395C6587ACDDB608AB306A3E6EE | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_F1 22.ini | text | |
MD5:FECE8042278EFC32B3F32A4109ADB50C | SHA256:F0435DC6ECF94DFCFE718EAC51293924617B7377C11DF5A9747EF60E83791F1D | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_F1 23.ini | text | |
MD5:18416EFA57D527355F065064172A821D | SHA256:CFBE14FC02F08A2B941DB25DE2379A5849CEDA301E529514004948D0088945FA | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_Dead Space 2023.ini | text | |
MD5:FC3F0C4D744A4310C775B2879399C468 | SHA256:934211FE00D6151381796B7001D7AEF5BC883DAA9F1B1F68AF60A7AF93EB1835 | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_Frostpunk.ini | text | |
MD5:FB2516CAACEBCDB02E9F2194BA72DE12 | SHA256:8A28296795FC669C047ED3AFBEB82791C4C86D3160B5A6843A144D814AE578C2 | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_GRID Legends.ini | text | |
MD5:73C304A751F7F202EE692A49A5D91533 | SHA256:9662D42DDC89C9B52B712087A819619208D2E826AC86A57493D5A49452DAE91B | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_It Takes Two.ini | text | |
MD5:31561ACF01F495280B2E03EC26B7812F | SHA256:3435BE593EE7214A75789417B0B6E90FB7939B26DC43A8CCA197620E72EC48AF | |||
| 6392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6392.13619\EA DLC Unlocker v2\g_Need For Speed Heat.ini | text | |
MD5:C11C8268AA87FD021F691D4AE9529CCB | SHA256:FDA16758BDF3AA61BAA0B598BD419F1DAE695787D8F8DD9DA8FEA4629BF041D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
29
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6672 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6320 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4088 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3164 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4088 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
4436 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4436 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |