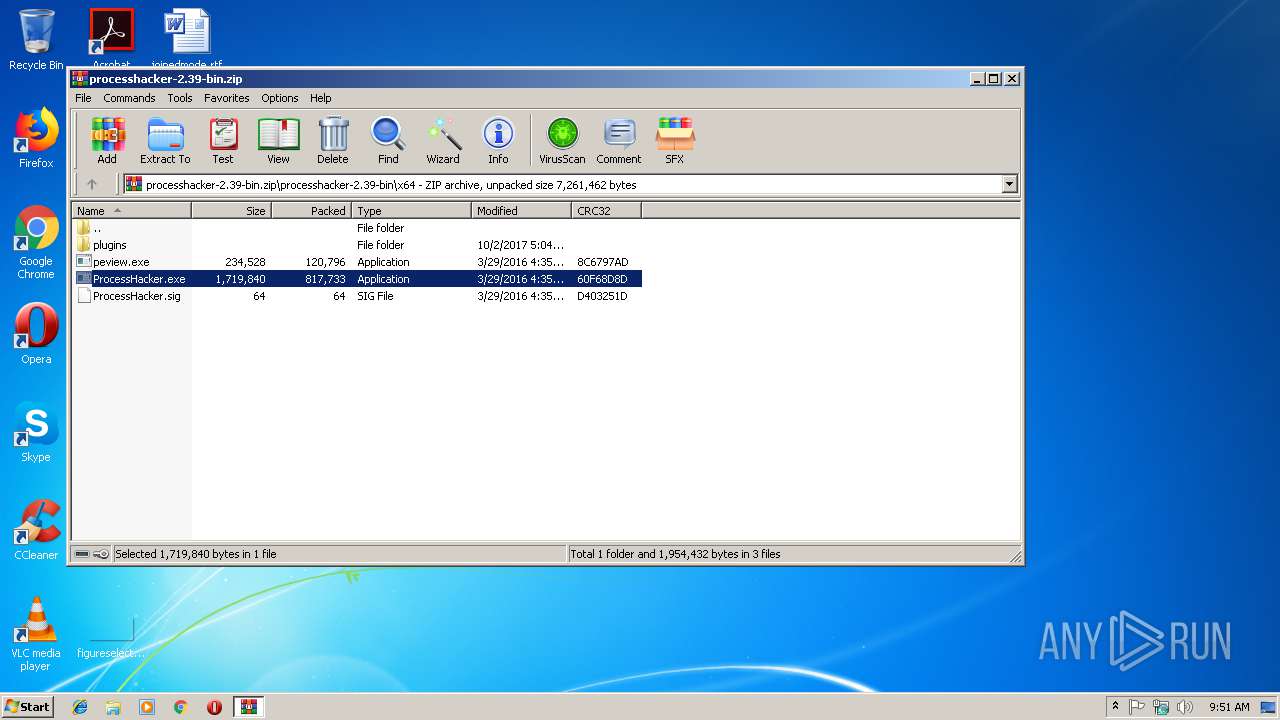
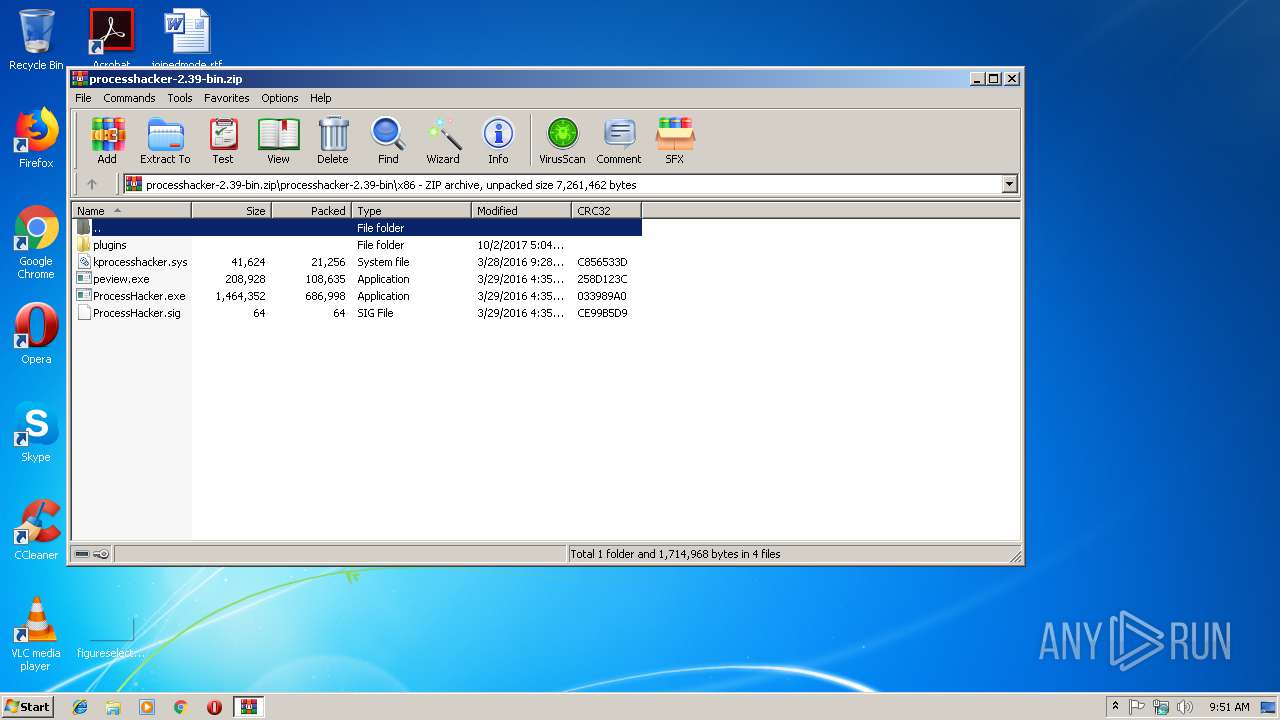
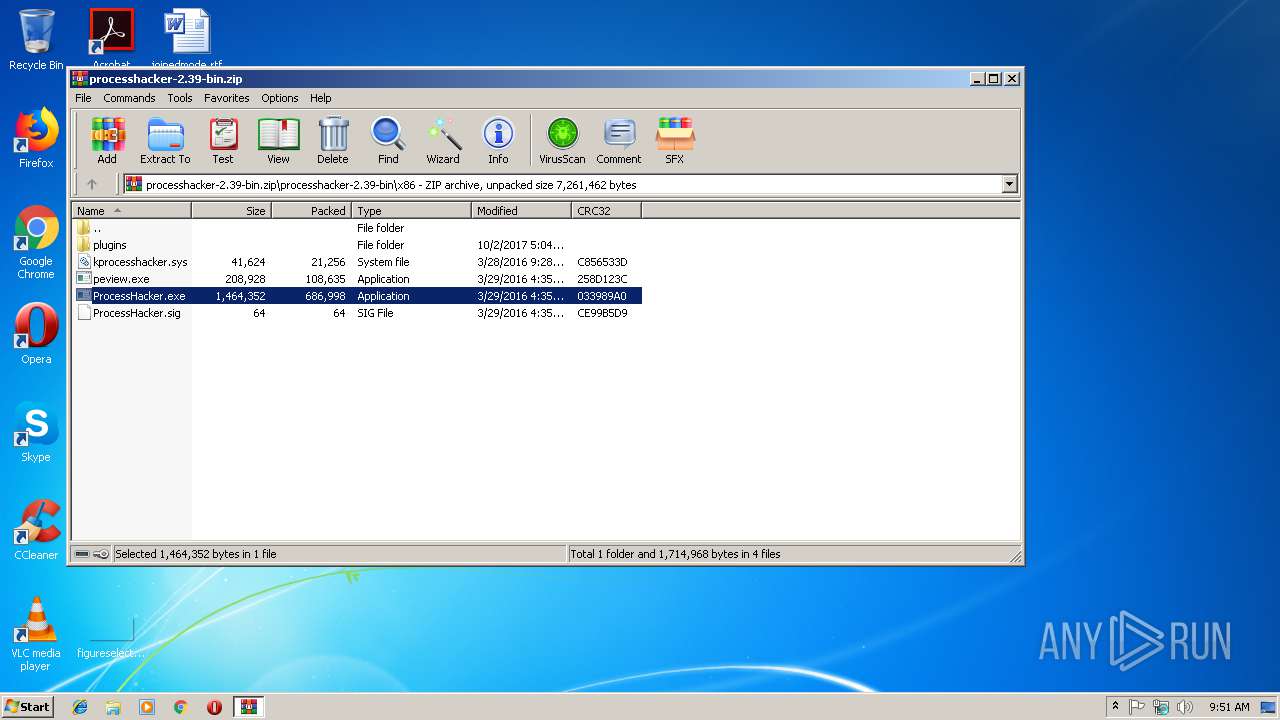
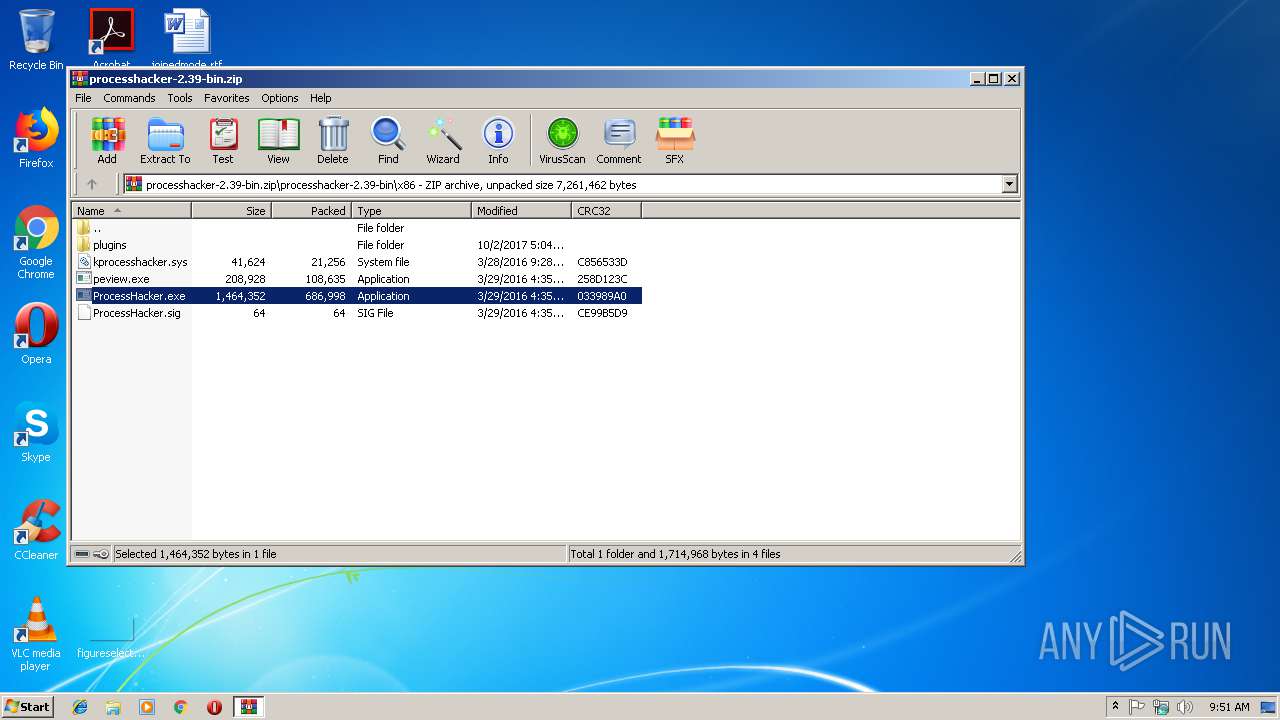
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/c0c966d5-3232-4ed3-8b6d-4db2302e16ea |
| Verdict: | Malicious activity |
| Analysis date: | February 27, 2019, 09:50:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 41CE544132439494CEA046F7CFBB6422 |
| SHA1: | AE42490C5412EA13455498CCB1DF329388F001BD |
| SHA256: | C7921C71A40EC56CDE34CAC854C7164AF456BBB7393BCBF8C306702BFF15719F |
| SSDEEP: | 49152:l85pB0X687BimNifJTbWhzV71f/6HzsQ+rMuhu5vEQ1tYFZzgs993VdbrD1O:S5pan1OWhzV9CHzR+rWeHz9zQ |
MALICIOUS
Loads dropped or rewritten executable
- ProcessHacker.exe (PID: 2564)
- ProcessHacker.exe (PID: 3744)
Application was dropped or rewritten from another process
- ProcessHacker.exe (PID: 3744)
- ProcessHacker.exe (PID: 2564)
SUSPICIOUS
Application launched itself
- ProcessHacker.exe (PID: 3744)
Creates files in the user directory
- ProcessHacker.exe (PID: 3744)
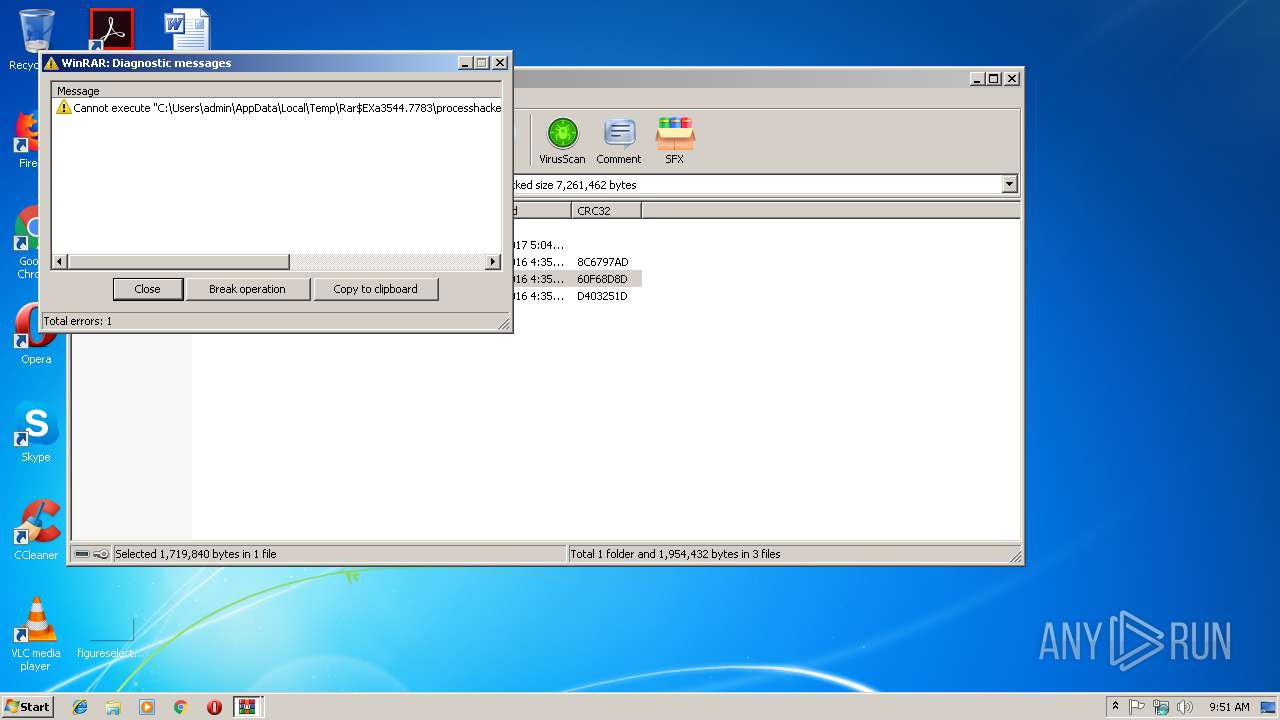
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3544)
INFO
Reads settings of System Certificates
- ProcessHacker.exe (PID: 3744)
- ProcessHacker.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:10:02 17:04:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | processhacker-2.39-bin/ |
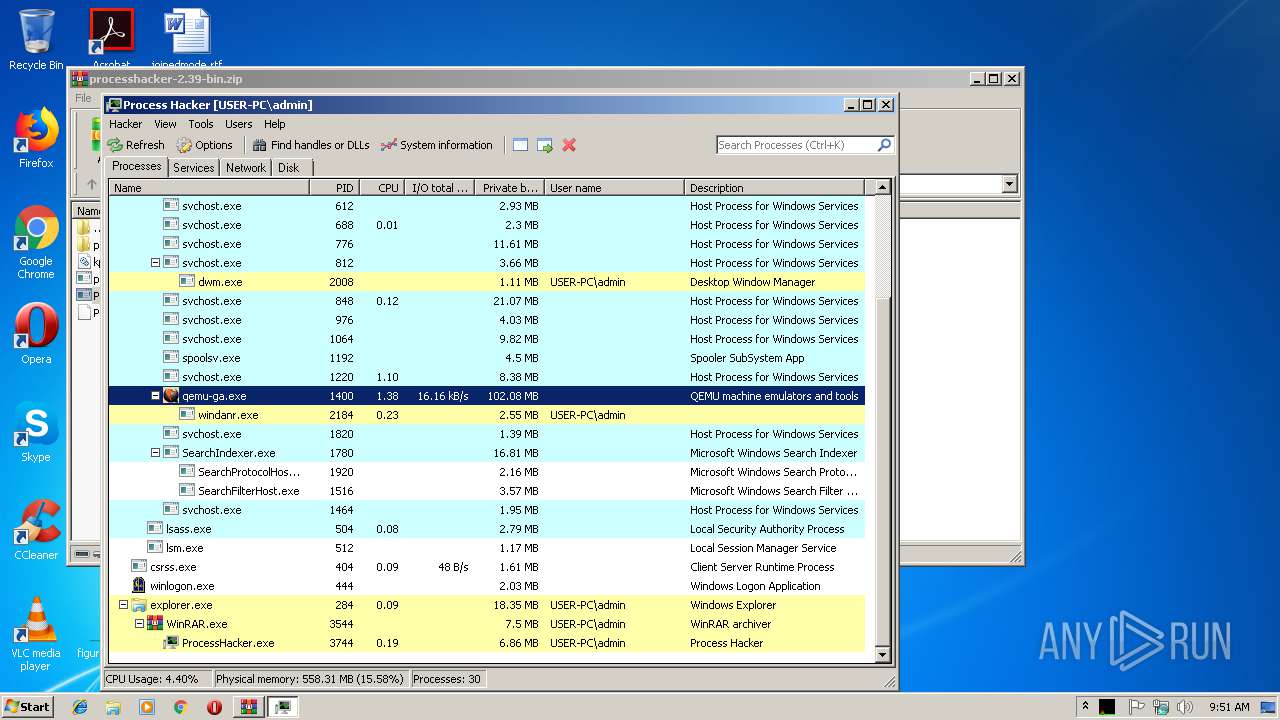
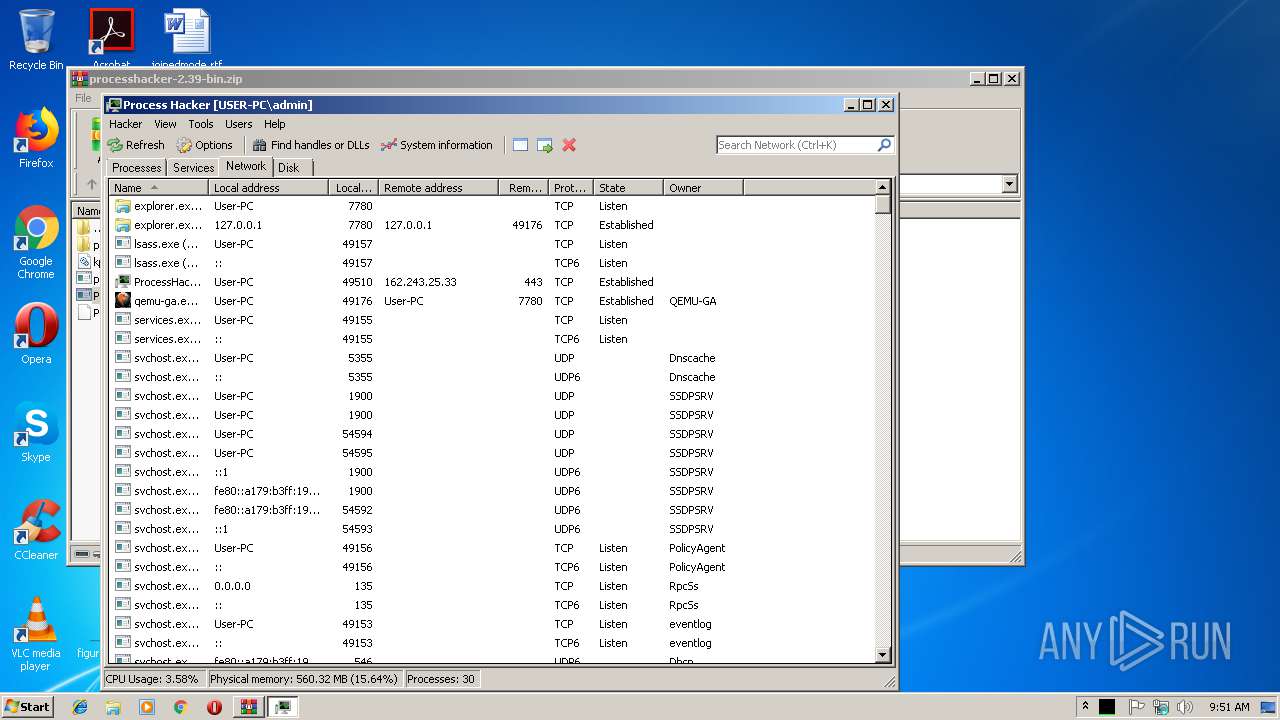
Total processes
35
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
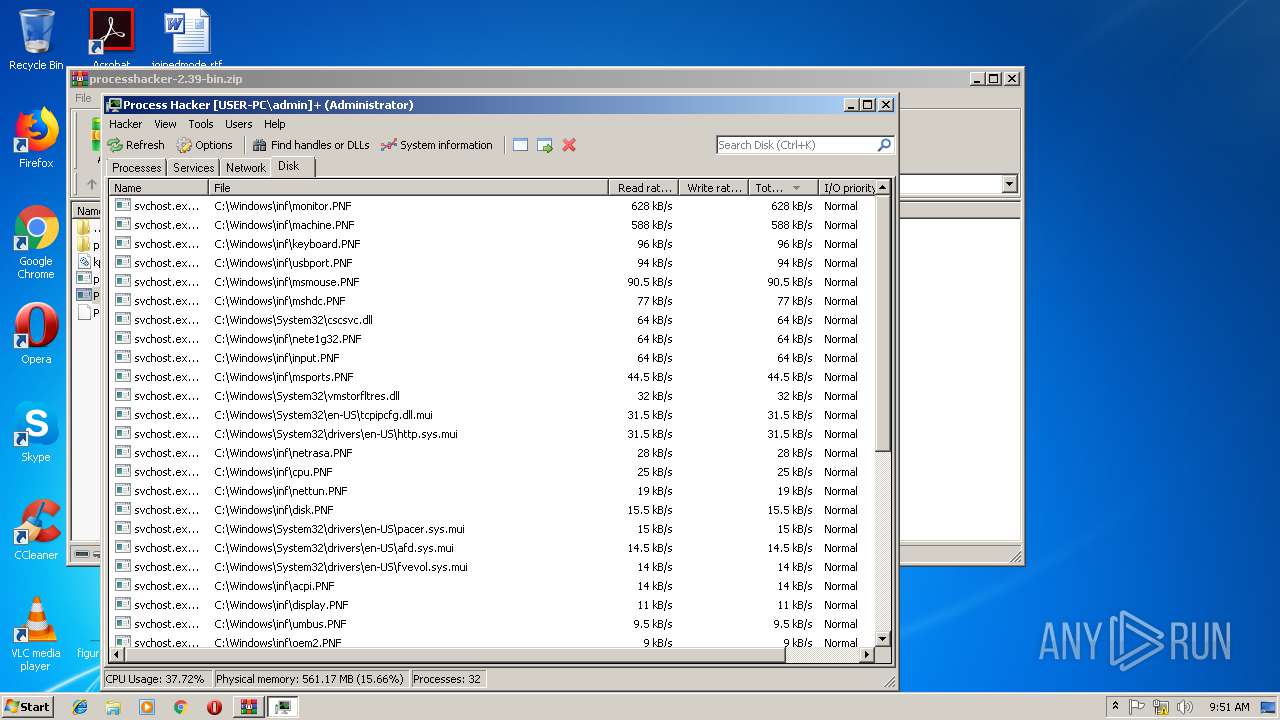
| 2564 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.9224\processhacker-2.39-bin\x86\ProcessHacker.exe" -v -selecttab Disk | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.9224\processhacker-2.39-bin\x86\ProcessHacker.exe | ProcessHacker.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 3544 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\processhacker-2.39-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3744 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.9224\processhacker-2.39-bin\x86\ProcessHacker.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.9224\processhacker-2.39-bin\x86\ProcessHacker.exe | WinRAR.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
Total events
939
Read events
900
Write events
39
Delete events
0
Modification events
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\processhacker-2.39-bin.zip | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
58
Suspicious files
2
Text files
10
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\LICENSE.txt | text | |
MD5:EB59E0A5D01D0A5B02DA0C9E7786969F | SHA256:C38E811F6F83428921D0CECD998A44B717149B577B4C1A63B66064F03C34E4E7 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\NetworkTools.dll | executable | |
MD5:D6BED1D6FDBED480E32FDD2DD4C13352 | SHA256:476AA6AF14DD0B268786E32543B9A6917A298D4D90E1015DAC6FB2B522CF5D2E | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\COPYRIGHT.txt | text | |
MD5:39B07060A5C6199730219E29C747C061 | SHA256:319CD301CF40BE03C00CD086560D4E810E0F6D0DBFDC2D28D6AF3522C027CF49 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\CHANGELOG.txt | text | |
MD5:B13DE4E8531AF294F87FFDDCCB08D7CE | SHA256:69E38F590A9A25F656E7507AF76229A3A6678A8C57B4E879FF8CE7E52FD704FF | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\README.txt | text | |
MD5:72AC5A8DD6491E525B9783C9BC439FE6 | SHA256:0C4F051675A690EA4DB6AB2EB81FDCED6990E2538AD21DC4610AA5925253A090 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\ExtendedServices.dll | executable | |
MD5:4858BDB7731BF0B46B247A1F01F4A282 | SHA256:5AE7C0972FD4E4C4AE14C0103602CA854377FEFCBCCD86FA68CFC5A6D1F99F60 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\ExtendedNotifications.dll | executable | |
MD5:BE4DC4D2D1D05001AB0BB2BB8659BFAD | SHA256:61E8CD8DE80A5C0D7CED280FE04AD8387A846A7BF2EE51BCBBA96B971C7C1795 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\ExtendedTools.dll | executable | |
MD5:BC61E6FB02FBBFE16FB43CC9F4E949F1 | SHA256:F2805E0F81513641A440F1A21057A664961C22192CB33FCA3870362C8F872D87 | |||
| 3544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3544.7783\processhacker-2.39-bin\x64\plugins\OnlineChecks.dll | executable | |
MD5:12C25FB356E51C3FD81D2D422A66BE89 | SHA256:7336D66588BBCFEA63351A2EB7C8D83BBD49B5D959BA56A94B1FE2E905A5B5DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3744 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |