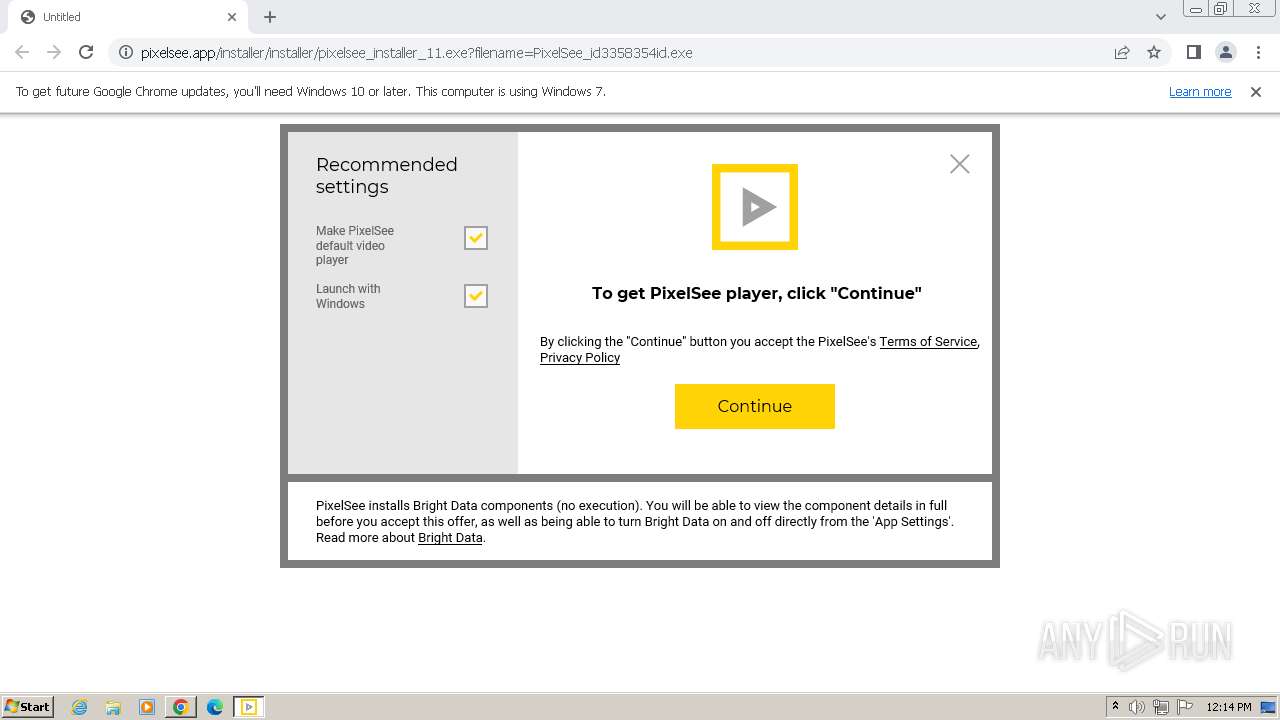
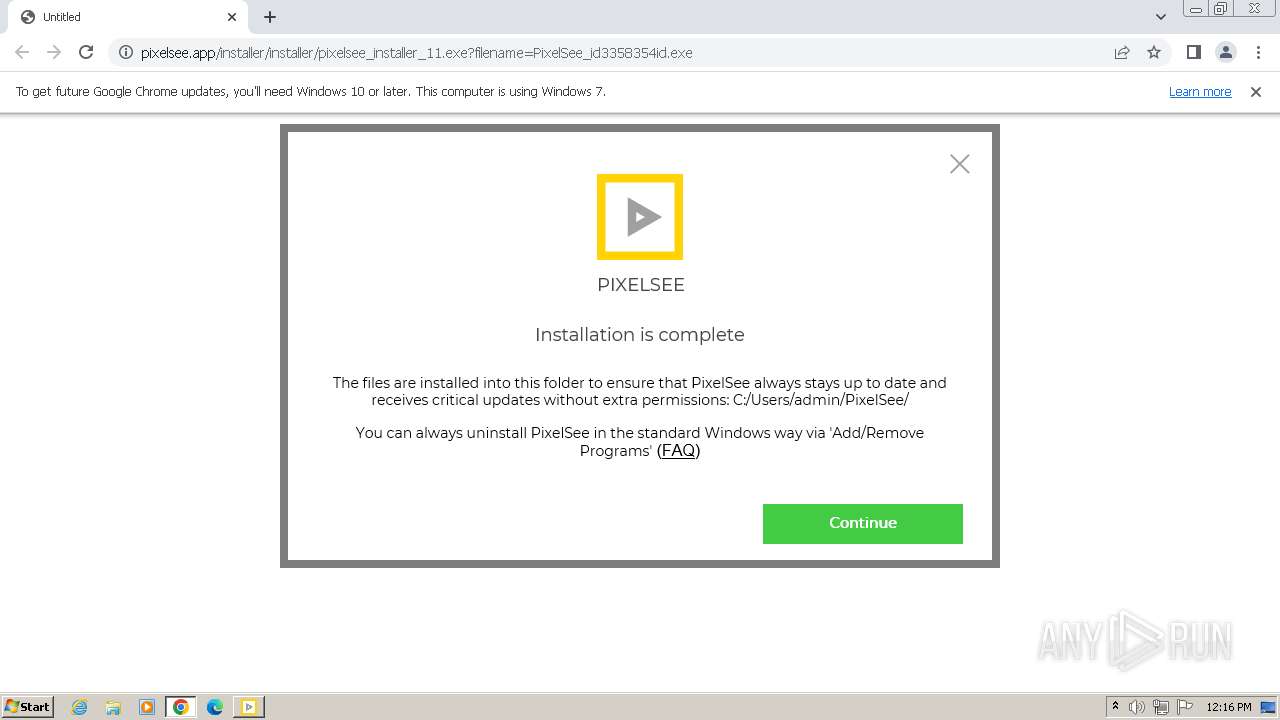
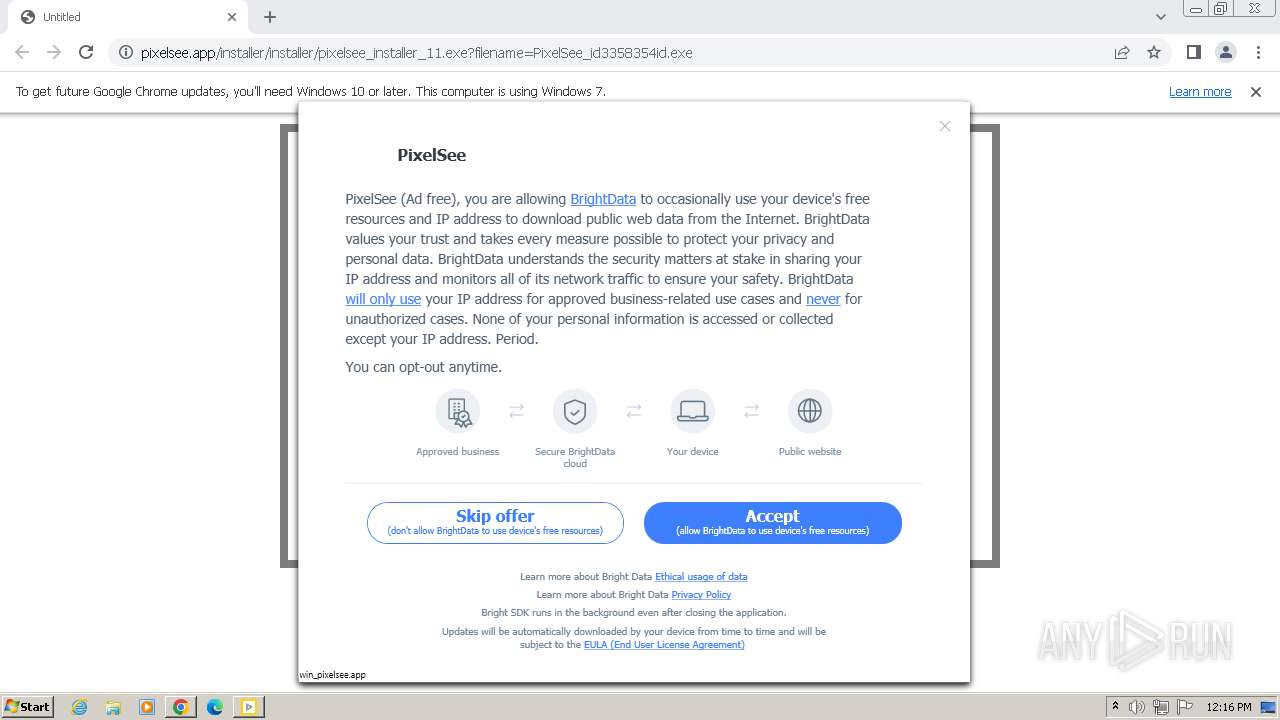
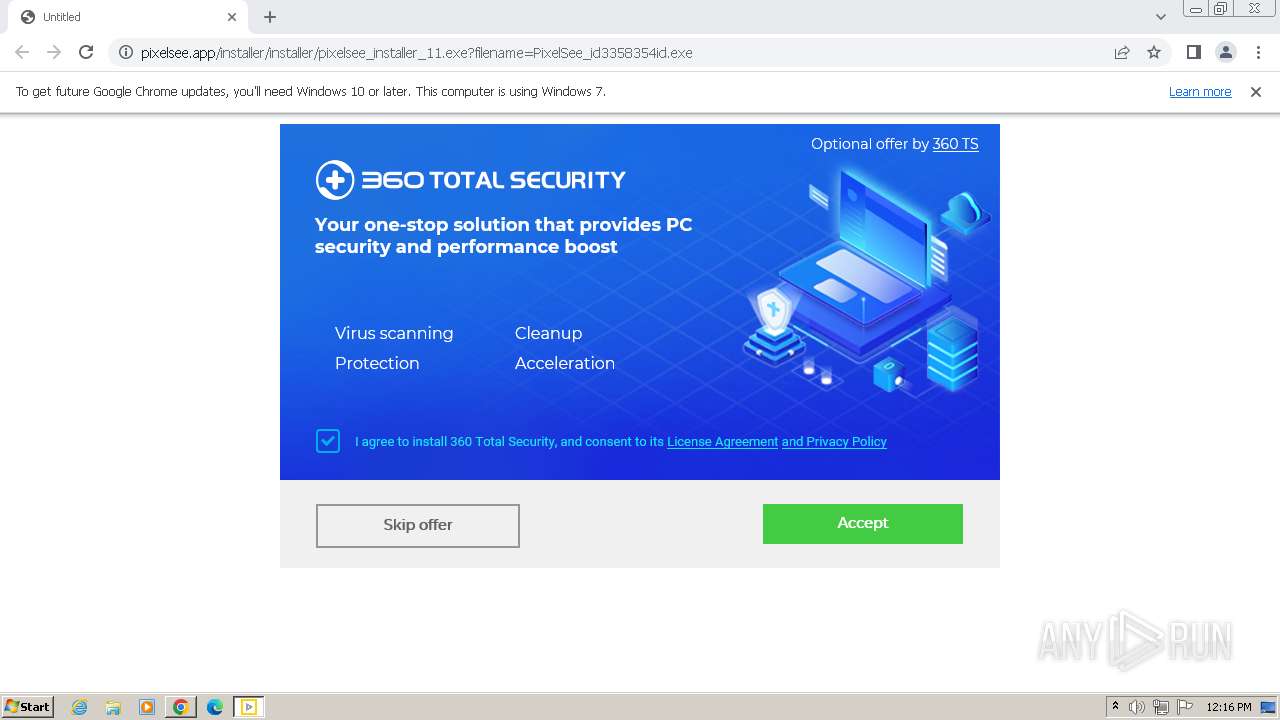
| URL: | https://pixelsee.app/installer/installer/pixelsee_installer_11.exe?filename=PixelSee_id3358354id.exe |
| Full analysis: | https://app.any.run/tasks/5ef1d3a4-3b4d-4406-8181-1f16a7534f77 |
| Verdict: | Malicious activity |
| Analysis date: | October 26, 2023, 11:14:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 6CB46890409D3827A840150C69EFA0CCFBBA82B0 |
| SHA256: | C779C714EBCEF9DBD3F820F0D130CBF47E1B005A69A9C8E42A607C51956D441D |
| SSDEEP: | 3:N8ISDKMLWEJOXKMXJOXKVcwkyEJOXcJxOiYMtl6zXCn:2IEKkOXXZOXh5ygOXCVtuXC |
MALICIOUS
Application was dropped or rewritten from another process
- PixelSee_id3358354id.exe (PID: 2876)
- PixelSee_id3358354id.exe (PID: 3016)
- lum_inst.exe (PID: 3432)
- luminati-m-controller.exe (PID: 1052)
- test_wpf.exe (PID: 1892)
- pixelsee.exe (PID: 2704)
- pixelsee_crashpad_handler.exe (PID: 560)
- QtWebEngineProcess.exe (PID: 668)
- pixelsee.exe (PID: 2440)
- antivirus360.exe (PID: 2016)
- QtWebEngineProcess.exe (PID: 2128)
- QtWebEngineProcess.exe (PID: 3584)
- pixelsee_crashpad_handler.exe (PID: 2348)
Actions looks like stealing of personal data
- PixelSee_id3358354id.exe (PID: 3016)
- 360TS_Setup.exe (PID: 4052)
Drops the executable file immediately after the start
- lum_inst.exe (PID: 3432)
- lum_inst.tmp (PID: 2416)
- luminati-m-controller.exe (PID: 1052)
- antivirus360.exe (PID: 2016)
- PixelSee_id3358354id.exe (PID: 3016)
- 360TS_Setup.exe (PID: 1864)
- 360TS_Setup.exe (PID: 4052)
Loads dropped or rewritten executable
- luminati-m-controller.exe (PID: 1052)
- QtWebEngineProcess.exe (PID: 668)
- pixelsee_crashpad_handler.exe (PID: 560)
- antivirus360.exe (PID: 2016)
- QtWebEngineProcess.exe (PID: 2128)
- QtWebEngineProcess.exe (PID: 3584)
- pixelsee.exe (PID: 2440)
- pixelsee.exe (PID: 2704)
- pixelsee_crashpad_handler.exe (PID: 2348)
- 360TS_Setup.exe (PID: 1864)
- 360TS_Setup.exe (PID: 4052)
SUSPICIOUS
Reads the Internet Settings
- PixelSee_id3358354id.exe (PID: 3016)
- lum_inst.tmp (PID: 2416)
- luminati-m-controller.exe (PID: 1052)
- pixelsee.exe (PID: 2704)
- antivirus360.exe (PID: 2016)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 4052)
Reads Microsoft Outlook installation path
- PixelSee_id3358354id.exe (PID: 3016)
Reads Internet Explorer settings
- PixelSee_id3358354id.exe (PID: 3016)
Process drops legitimate windows executable
- PixelSee_id3358354id.exe (PID: 3016)
- luminati-m-controller.exe (PID: 1052)
- 360TS_Setup.exe (PID: 4052)
The process drops C-runtime libraries
- PixelSee_id3358354id.exe (PID: 3016)
- luminati-m-controller.exe (PID: 1052)
Reads the Windows owner or organization settings
- lum_inst.tmp (PID: 2416)
Reads settings of System Certificates
- luminati-m-controller.exe (PID: 1052)
- pixelsee.exe (PID: 2704)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 4052)
Detected use of alternative data streams (AltDS)
- luminati-m-controller.exe (PID: 1052)
Adds/modifies Windows certificates
- lum_inst.tmp (PID: 2416)
Process requests binary or script from the Internet
- antivirus360.exe (PID: 2016)
Starts itself from another location
- 360TS_Setup.exe (PID: 1864)
Reads security settings of Internet Explorer
- 360TS_Setup.exe (PID: 4052)
Checks Windows Trust Settings
- 360TS_Setup.exe (PID: 4052)
The process verifies whether the antivirus software is installed
- 360TS_Setup.exe (PID: 4052)
Drops 7-zip archiver for unpacking
- 360TS_Setup.exe (PID: 4052)
INFO
The process uses the downloaded file
- chrome.exe (PID: 372)
- chrome.exe (PID: 2996)
- chrome.exe (PID: 1792)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 2544)
Application launched itself
- chrome.exe (PID: 372)
- msedge.exe (PID: 4008)
Checks supported languages
- PixelSee_id3358354id.exe (PID: 3016)
- lum_inst.tmp (PID: 2416)
- luminati-m-controller.exe (PID: 1052)
- test_wpf.exe (PID: 1892)
- lum_inst.exe (PID: 3432)
- pixelsee.exe (PID: 2704)
- pixelsee_crashpad_handler.exe (PID: 560)
- QtWebEngineProcess.exe (PID: 668)
- antivirus360.exe (PID: 2016)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- pixelsee_crashpad_handler.exe (PID: 2348)
- 360TS_Setup.exe (PID: 1864)
- 360TS_Setup.exe (PID: 4052)
- QtWebEngineProcess.exe (PID: 3584)
Reads the computer name
- PixelSee_id3358354id.exe (PID: 3016)
- lum_inst.tmp (PID: 2416)
- luminati-m-controller.exe (PID: 1052)
- test_wpf.exe (PID: 1892)
- pixelsee.exe (PID: 2704)
- QtWebEngineProcess.exe (PID: 668)
- antivirus360.exe (PID: 2016)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 1864)
- 360TS_Setup.exe (PID: 4052)
Checks proxy server information
- PixelSee_id3358354id.exe (PID: 3016)
- luminati-m-controller.exe (PID: 1052)
- antivirus360.exe (PID: 2016)
- 360TS_Setup.exe (PID: 4052)
Drops the executable file immediately after the start
- chrome.exe (PID: 372)
- chrome.exe (PID: 2888)
Create files in a temporary directory
- PixelSee_id3358354id.exe (PID: 3016)
- lum_inst.exe (PID: 3432)
- antivirus360.exe (PID: 2016)
- 360TS_Setup.exe (PID: 1864)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 4052)
Reads the machine GUID from the registry
- PixelSee_id3358354id.exe (PID: 3016)
- luminati-m-controller.exe (PID: 1052)
- test_wpf.exe (PID: 1892)
- pixelsee.exe (PID: 2704)
- antivirus360.exe (PID: 2016)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 4052)
Creates files or folders in the user directory
- PixelSee_id3358354id.exe (PID: 3016)
- luminati-m-controller.exe (PID: 1052)
- pixelsee.exe (PID: 2704)
- QtWebEngineProcess.exe (PID: 668)
- pixelsee_crashpad_handler.exe (PID: 560)
- antivirus360.exe (PID: 2016)
- pixelsee.exe (PID: 2440)
- QtWebEngineProcess.exe (PID: 2128)
- 360TS_Setup.exe (PID: 4052)
Application was dropped or rewritten from another process
- lum_inst.tmp (PID: 2416)
Creates files in the program directory
- luminati-m-controller.exe (PID: 1052)
- 360TS_Setup.exe (PID: 1864)
- 360TS_Setup.exe (PID: 4052)
Reads Environment values
- luminati-m-controller.exe (PID: 1052)
- pixelsee.exe (PID: 2704)
- pixelsee.exe (PID: 2440)
Process checks computer location settings
- luminati-m-controller.exe (PID: 1052)
- QtWebEngineProcess.exe (PID: 3584)
- 360TS_Setup.exe (PID: 4052)
Manual execution by a user
- pixelsee.exe (PID: 2440)
Dropped object may contain TOR URL's
- 360TS_Setup.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
104
Monitored processes
60
Malicious processes
14
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3612 --field-trial-handle=1176,i,7219288565268048659,7555226863002751099,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2516 --field-trial-handle=1172,i,1444335867857748108,13119054930654378232,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://pixelsee.app/installer/installer/pixelsee_installer_11.exe?filename=PixelSee_id3358354id.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 520 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 560 | C:\Users\admin\PixelSee\pixelsee_crashpad_handler.exe --no-rate-limit "--database=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps" "--metrics-dir=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps" --url=https://o612922.ingest.sentry.io:443/api/6420364/minidump/?sentry_client=sentry.native/0.4.6&sentry_key=297ce3230e5f4bcf957dbf23e9597dc9 "--attachment=C:/Users/admin/AppData/Local/PixelSee LLC/PixelSee/crashdumps/logs/log" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\08e7791c-9ea5-4bc0-5e81-0c7a0feb9956.run\__sentry-event" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\08e7791c-9ea5-4bc0-5e81-0c7a0feb9956.run\__sentry-breadcrumb1" "--attachment=C:\Users\admin\AppData\Local\PixelSee LLC\PixelSee\crashdumps\08e7791c-9ea5-4bc0-5e81-0c7a0feb9956.run\__sentry-breadcrumb2" --initial-client-data=0x380,0x384,0x388,0x354,0x38c,0x6acd7b7c,0x6acd7b90,0x6acd7ba0 | C:\Users\admin\PixelSee\pixelsee_crashpad_handler.exe | — | pixelsee.exe | |||||||||||
User: admin Company: SIA Circle Solutions Integrity Level: HIGH Description: PixelSee Crash Handler Exit code: 0 Version: 12.0.0.0 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3760 --field-trial-handle=1172,i,1444335867857748108,13119054930654378232,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\PixelSee\QtWebEngineProcess.exe" --type=utility --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --lang=en-US --service-sandbox-type=network --application-name=PixelSee --webengine-schemes=qrc:sLV --mojo-platform-channel-handle=1660 /prefetch:8 | C:\Users\admin\PixelSee\QtWebEngineProcess.exe | — | pixelsee.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2596 --field-trial-handle=1172,i,1444335867857748108,13119054930654378232,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1460 --field-trial-handle=1176,i,7219288565268048659,7555226863002751099,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\PixelSee\Luminati-m\luminati-m-controller.exe" switch_on | C:\Users\admin\PixelSee\Luminati-m\luminati-m-controller.exe | lum_inst.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 100 Modules
| |||||||||||||||
Total events
46 348
Read events
45 812
Write events
501
Delete events
35
Modification events
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (372) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
818
Suspicious files
740
Text files
362
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1eaaf3.TMP | — | |
MD5:— | SHA256:— | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1eab13.TMP | text | |
MD5:CDCC923CEC2CD9228330551E6946A9C2 | SHA256:592F4750166BE662AA88728F9969537163FEC5C3E95E81537C8C6917F8D0929E | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1eab13.TMP | text | |
MD5:D5C9ECBD2DCA29D89266782824D7AF99 | SHA256:D22D1243ACC064A30823180D0E583C853E9395367C78C2AD9DE59A463904F702 | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:B806171F9E7C87423595645872D869B0 | SHA256:851A8D533BEBF6A69C5518375396E97463302C1E2031D04F8EB5851C5C82CEB9 | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF1eadc2.TMP | — | |
MD5:— | SHA256:— | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1eac0d.TMP | text | |
MD5:561161B0FF5BCA89BF47F8AC972A7499 | SHA256:ECCA5CCFA0BEED7581B39FCE03D0FD3B694DF0F92BFFF780F702118AD51FC17D | |||
| 372 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a0ae83b6-3f02-477e-9eef-721344ae037d.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
133
DNS requests
85
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 5.44 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.9 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 23.4 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.9 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 175 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 98.4 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.9 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 48.4 Kb | unknown |
2016 | antivirus360.exe | GET | — | 18.245.60.13:80 | http://int.down.360safe.com/totalsecurity/360TS_Setup_11.0.0.1046.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
372 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1484 | chrome.exe | 51.158.130.233:443 | pixelsee.app | Online S.a.s. | FR | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1484 | chrome.exe | 142.250.185.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
372 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1484 | chrome.exe | 142.250.184.206:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
1484 | chrome.exe | 142.250.186.36:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
pixelsee.app |
| unknown |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
clients1.google.com |
| whitelisted |
perr.lum-sdk.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2016 | antivirus360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
2016 | antivirus360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
2016 | antivirus360.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
2016 | antivirus360.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
pixelsee.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
pixelsee.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
pixelsee.exe | > __thiscall Application::Application(int &,char *[])
|
pixelsee.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
pixelsee.exe | > __thiscall PixelseeSettings::PixelseeSettings(void)
|
pixelsee.exe | > int __thiscall Application::exec(void)
|
pixelsee.exe | INSTALL ID: "" _ OLD ID: ""
|
pixelsee.exe | reseller - "" installId ""
|
pixelsee.exe | > void __thiscall PixelseeSettings::flushSettings(void)
|
pixelsee.exe | main libvlc debug: Copyright © 1996-2021 the VideoLAN team
|