| File name: | rust_cheat.exe.analyzeme.dll |
| Full analysis: | https://app.any.run/tasks/4b0f48cc-4189-41d7-a26d-ad19c6b615cf |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2018, 20:46:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 20E5599513E6224D9FE6CC366FA153FC |
| SHA1: | 0F211D370664128556FC3D4726D3029F4E7201E8 |
| SHA256: | C761B88C1202E321C7B0B684A40D3AF04714E2B7F45A48022E6823C1B7D3CFD9 |
| SSDEEP: | 384:hQWFsp4F2/5skg3XLaSIWsHnYYfiBisYpdd0ZMoZmAQxdi6RoW:T25TgHLaS6yzYpkZMoZmAQxHWW |
MALICIOUS
Loads dropped or rewritten executable
- explorer.exe (PID: 1676)
- conhost.exe (PID: 2880)
- svchost.exe (PID: 868)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:05:16 22:37:12+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.13 |
| CodeSize: | 20480 |
| InitializedDataSize: | 16896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11055 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 16-May-2018 20:37:12 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 16-May-2018 20:37:12 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.textbss | 0x00001000 | 0x00010000 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.text | 0x00011000 | 0x00004ECD | 0x00005000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 4.41627 |
.rdata | 0x00016000 | 0x00002019 | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.86668 |
.data | 0x00019000 | 0x00000594 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.344302 |
.idata | 0x0001A000 | 0x00000A67 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.9316 |
.00cfg | 0x0001B000 | 0x00000104 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.0611629 |
.rsrc | 0x0001C000 | 0x0000043C | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.14043 |
.reloc | 0x0001D000 | 0x000004FE | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.25162 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
KERNEL32.dll |
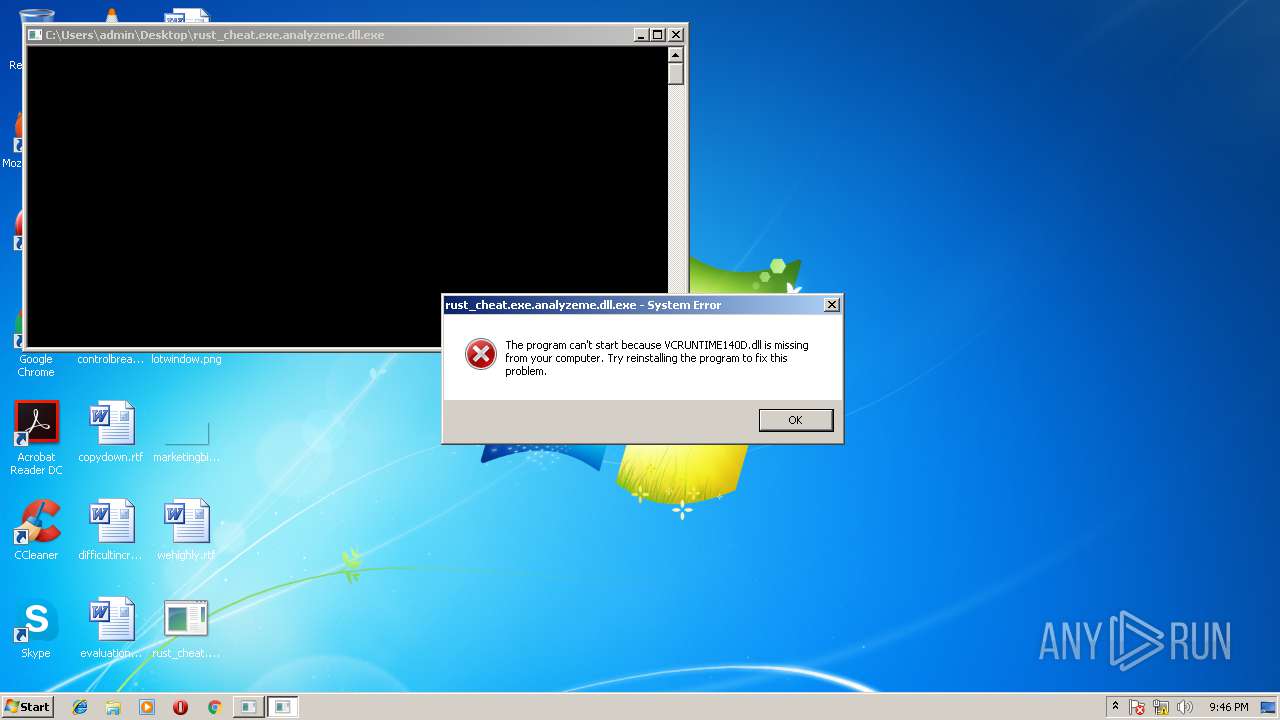
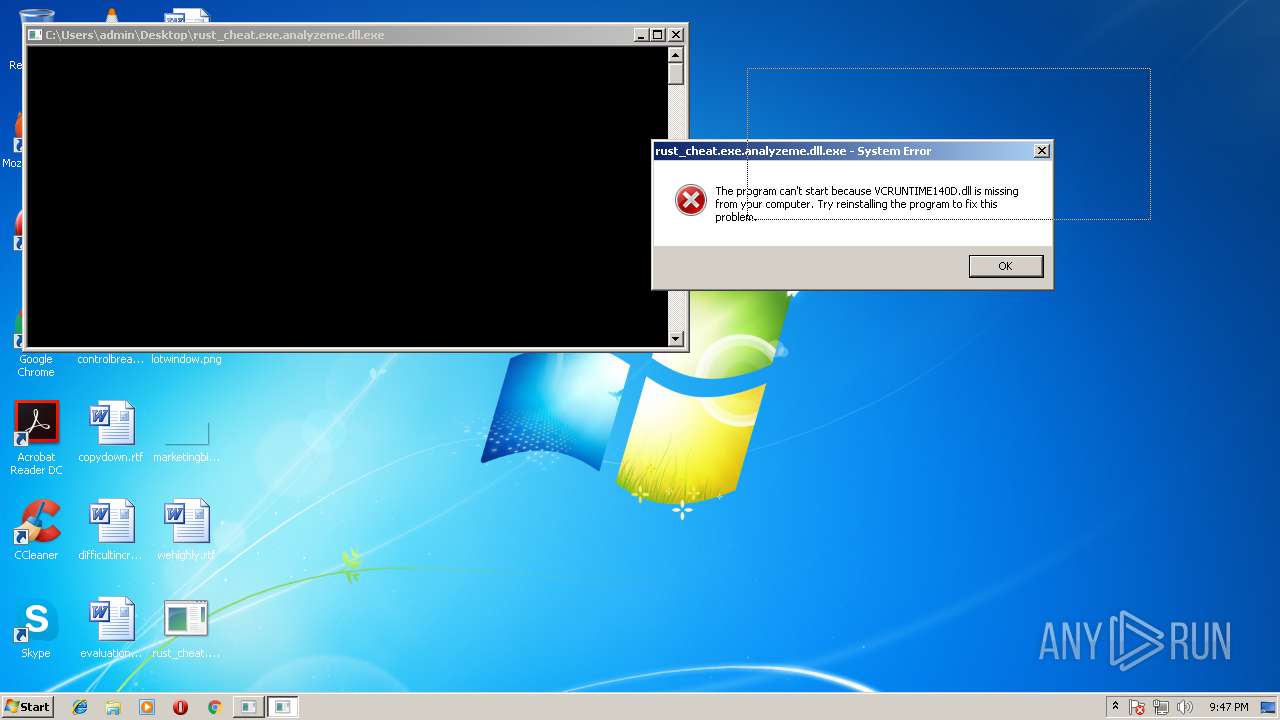
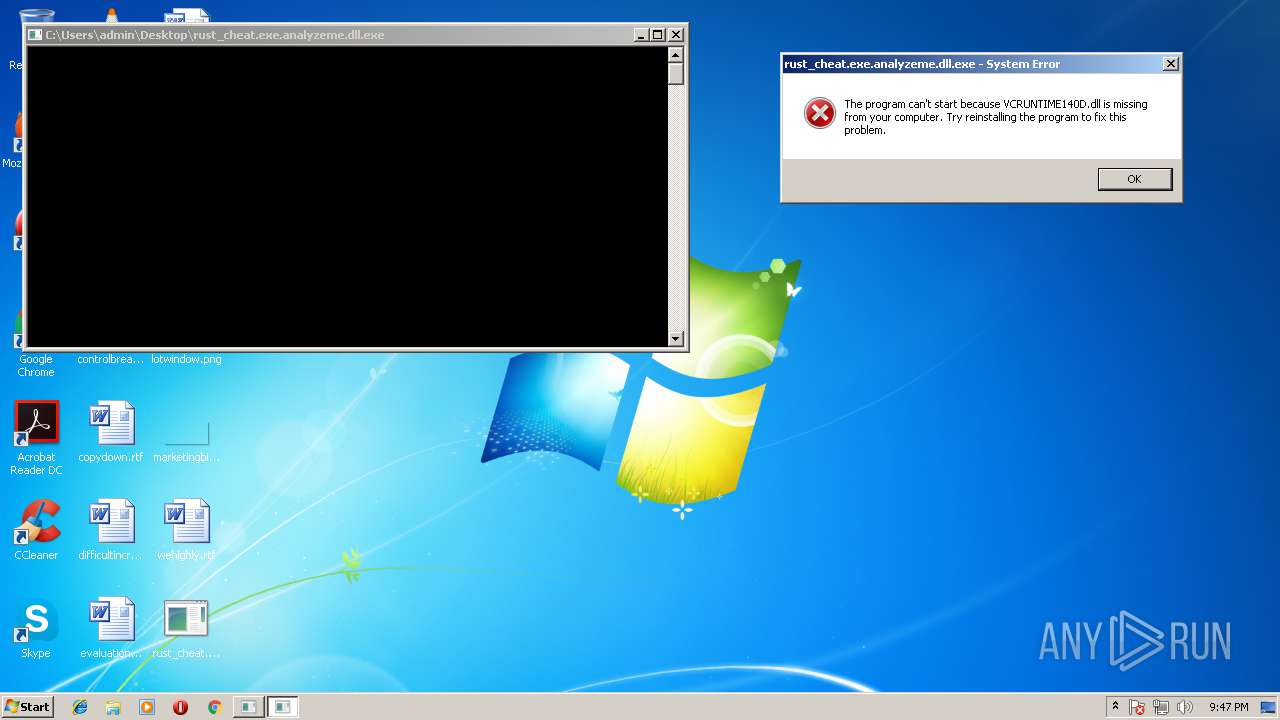
VCRUNTIME140D.dll |
ucrtbased.dll |
Total processes
33
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1676 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | \??\C:\Windows\system32\conhost.exe | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\Desktop\rust_cheat.exe.analyzeme.dll.exe" | C:\Users\admin\Desktop\rust_cheat.exe.analyzeme.dll.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
Total events
822
Read events
811
Write events
11
Delete events
0
Modification events
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\Qrfxgbc\ehfg_purng.rkr.nanylmrzr.qyy.rkr |
Value: 0000000000000000000000000F000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000000A0000000E00000012820A000400000001000000190801004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000000000000000000000000230000000000000000000000000000000000000000000000000000002A0C580260E9180213005802E20B58026FA9A5750600000005000000E20B580230B5580204E91802E8AAA5757B030119F8E8180200EB180230B55802000000000500000001000000DCE918026229A8757B03011930B5580206000000C80C58020000000000EB180208EB180210A65802CC0A580210000000000000000000000000000000000000000600000000000000230000006C61746E64666C740000000040000000AC54A57500000000C054A5757B03011930B55802000000000000000000000000E00B580230B55802ACE9183138EE18023F0400009021230038EA18021100000010471E0008471E00000000003F040000D6160E747B03011928EA0000150DB2ADD8E918028291E67528EA1802448B0000010DB2ADECE91802B69CE675488B25004C06000004EA1802B886250010EA1802789CE6753691E67540B018761100000010471E0008471E00D88625007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA180200000000070000003FE402007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000005802EC0A5802D0E818025869A67500000000D0075802F0E818020B8CA5750100000000000000537AA575560401020020000000000000010000003CE918023617DB7556040102100858020500000000000000FFFFFFFFD00758020000000038E9180264E9180200000000000000000000000090E9180218EC2300000000004091A4750900800188E918023559DB7556040102D09028000500000070E91802506AA6751CC0AA7501000000EF7AA575560401021D0000000020000088E918026359DB7590E918020000000000000000560401024066A07501000000F4E91802A13673750000000000000000C80B2300F4E91802B8367375E09276750000000000001B00D090280000000000F0E91802070014006AC2C1C10000000000000000CF6771758890280001000000C8902800FCE91802E82C0677C80B2300CF67717518EC1802C89028001100000010471E0008471E00000000007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA180200000000070000003FE402007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000005802EC0A5802D0E818025869A67500000000D0075802F0E818020B8CA5750100000000000000537AA575560401020020000000000000010000003CE918023617DB7556040102100858020500000000000000FFFFFFFFD00758020000000038E9180264E9180200000000000000000000000090E9180218EC2300000000004091A4750900800188E918023559DB7556040102D09028000500000070E91802506AA6751CC0AA7501000000EF7AA575560401021D0000000020000088E918026359DB7590E918020000000000000000560401024066A07501000000F4E91802A13673750000000000000000C80B2300F4E91802B8367375E09276750000000000001B00D090280000000000F0E91802070014006AC2C1C10000000000000000CF6771758890280001000000C8902800FCE91802E82C0677C80B2300CF67717518EC1802C89028001100000010471E0008471E00000000007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA1802 | |||
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\93\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\Qrfxgbc\ehfg_purng.rkr.nanylmrzr.qyy.rkr |
Value: 0000000000000000010000000F000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1676) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000000A0000000F00000012820A000400000001000000190801004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000000000000000000000000230000000000000000000000000000000000000000000000000000002A0C580260E9180213005802E20B58026FA9A5750600000005000000E20B580230B5580204E91802E8AAA5757B030119F8E8180200EB180230B55802000000000500000001000000DCE918026229A8757B03011930B5580206000000C80C58020000000000EB180208EB180210A65802CC0A580210000000000000000000000000000000000000000600000000000000230000006C61746E64666C740000000040000000AC54A57500000000C054A5757B03011930B55802000000000000000000000000E00B580230B55802ACE9183138EE18023F0400009021230038EA18021100000010471E0008471E00000000003F040000D6160E747B03011928EA0000150DB2ADD8E918028291E67528EA1802448B0000010DB2ADECE91802B69CE675488B25004C06000004EA1802B886250010EA1802789CE6753691E67540B018761100000010471E0008471E00D88625007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA180200000000070000003FE402007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000005802EC0A5802D0E818025869A67500000000D0075802F0E818020B8CA5750100000000000000537AA575560401020020000000000000010000003CE918023617DB7556040102100858020500000000000000FFFFFFFFD00758020000000038E9180264E9180200000000000000000000000090E9180218EC2300000000004091A4750900800188E918023559DB7556040102D09028000500000070E91802506AA6751CC0AA7501000000EF7AA575560401021D0000000020000088E918026359DB7590E918020000000000000000560401024066A07501000000F4E91802A13673750000000000000000C80B2300F4E91802B8367375E09276750000000000001B00D090280000000000F0E91802070014006AC2C1C10000000000000000CF6771758890280001000000C8902800FCE91802E82C0677C80B2300CF67717518EC1802C89028001100000010471E0008471E00000000007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA180200000000070000003FE402007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000005802EC0A5802D0E818025869A67500000000D0075802F0E818020B8CA5750100000000000000537AA575560401020020000000000000010000003CE918023617DB7556040102100858020500000000000000FFFFFFFFD00758020000000038E9180264E9180200000000000000000000000090E9180218EC2300000000004091A4750900800188E918023559DB7556040102D09028000500000070E91802506AA6751CC0AA7501000000EF7AA575560401021D0000000020000088E918026359DB7590E918020000000000000000560401024066A07501000000F4E91802A13673750000000000000000C80B2300F4E91802B8367375E09276750000000000001B00D090280000000000F0E91802070014006AC2C1C10000000000000000CF6771758890280001000000C8902800FCE91802E82C0677C80B2300CF67717518EC1802C89028001100000010471E0008471E00000000007CEA0000C10EB2AD2CEA18028291E6757CEA180230EA18022795E67500000000448B250058EA1802CD94E675448B250004EB1802B8862500E194E67500000000B886250004EB180260EA1802 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 868 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report