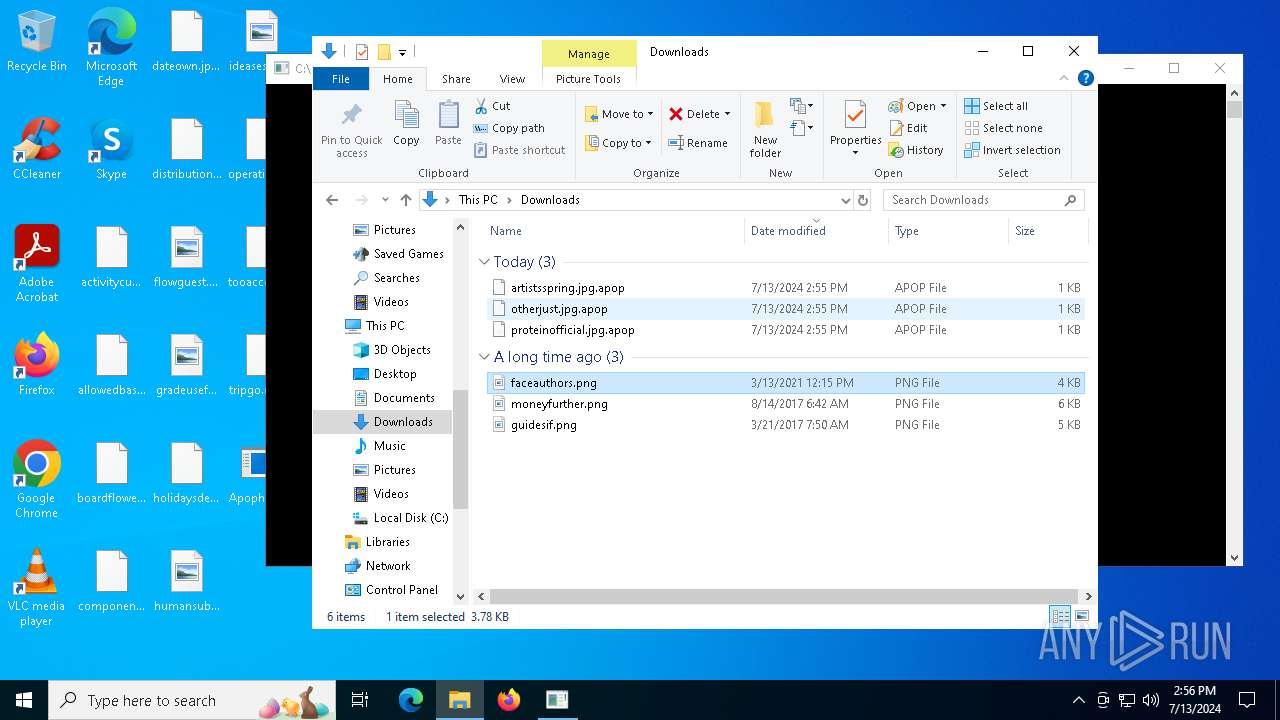
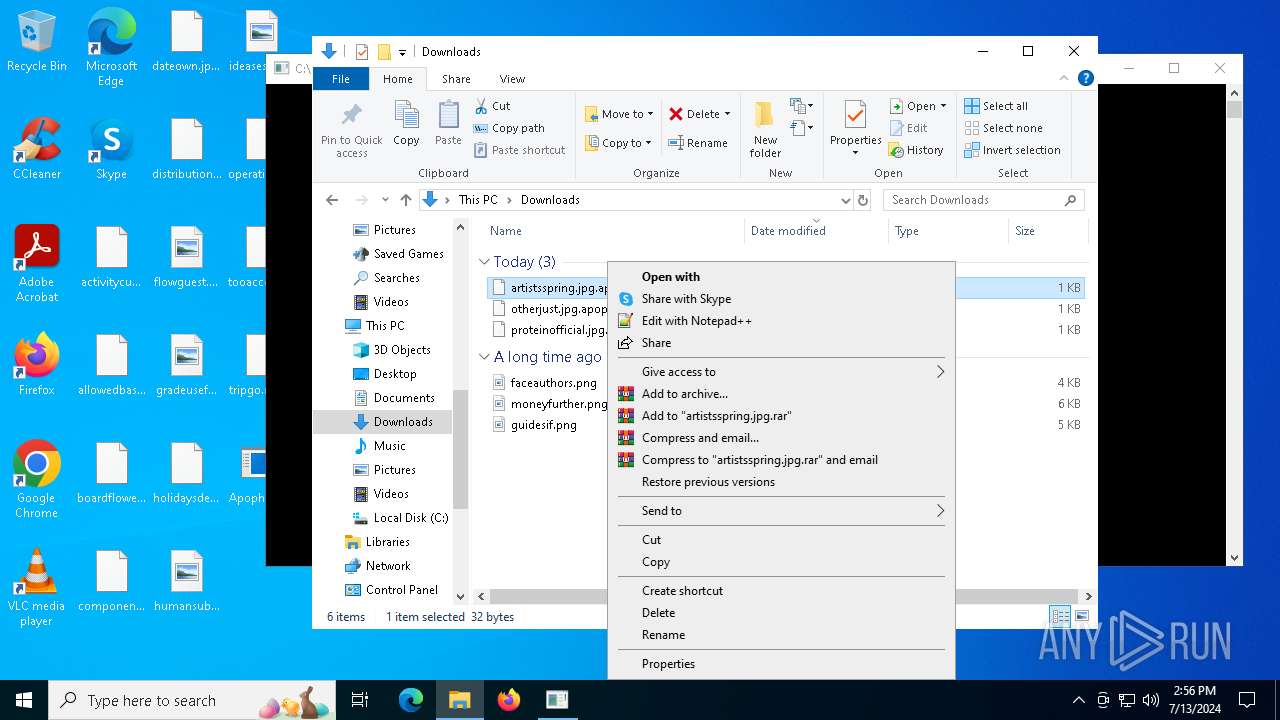
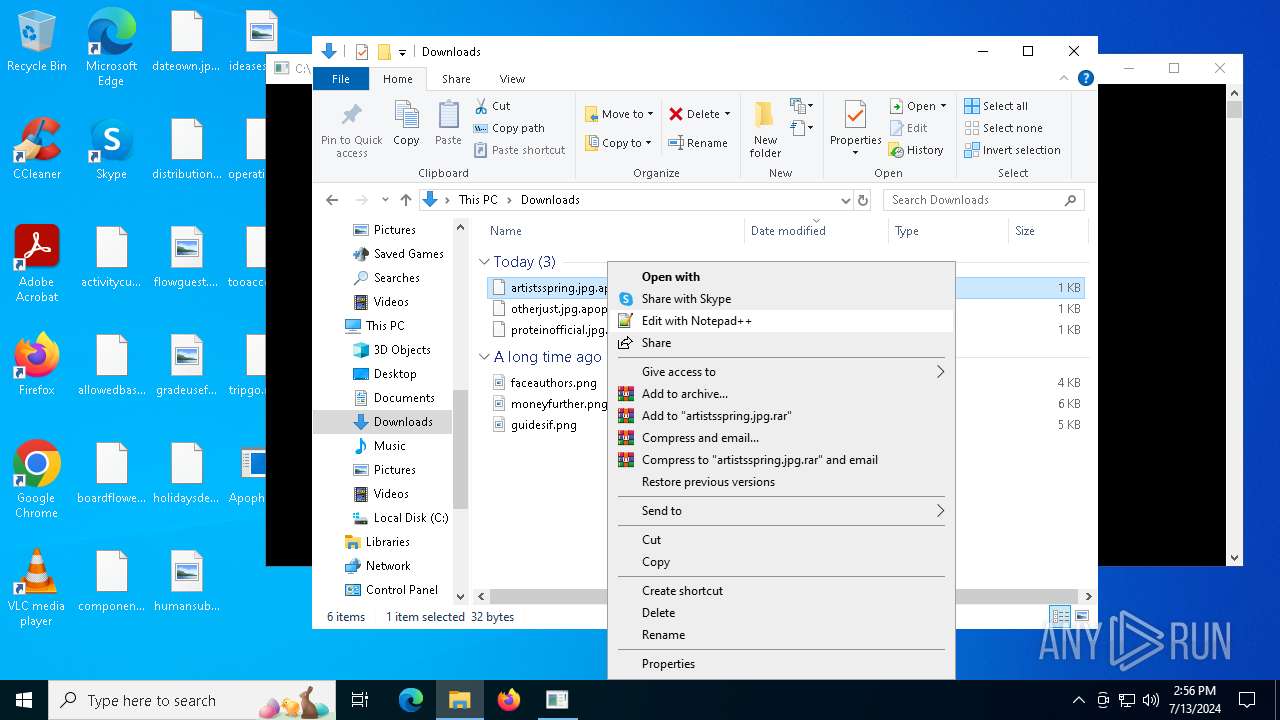
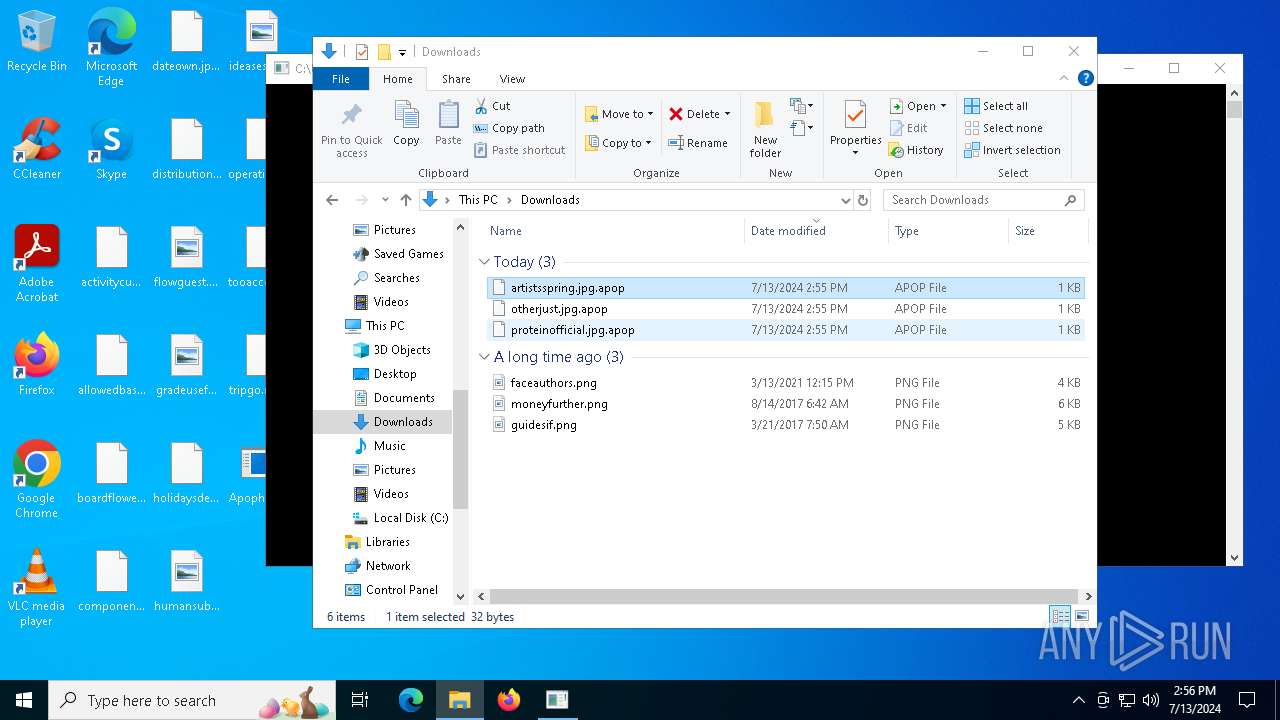
| File name: | Apophis.exe |
| Full analysis: | https://app.any.run/tasks/66df6c0c-a69b-410d-8fda-255e0cae2833 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2024, 14:54:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 5C6A8F498BF0A0014DBC120773B7D2EE |
| SHA1: | ED3EF4968F339A3C79DE8FCF92D955265A127A00 |
| SHA256: | C72481335D4C374FE18DA9D546E3D0E15BF9E0BCBC66669049836C4CD555752C |
| SSDEEP: | 384:orXcLDaAIOh3cwyzZH3sGY0qWetyeJ6hCyeCCepdI/+FDIlBzSz:wXcgOpa8GYzByCGCepm/+FABC |
MALICIOUS
Drops the executable file immediately after the start
- Apophis.exe (PID: 4320)
Modifies files in the Chrome extension folder
- Apophis.exe (PID: 4320)
Actions looks like stealing of personal data
- Apophis.exe (PID: 4320)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- Apophis.exe (PID: 4320)
Checks supported languages
- Apophis.exe (PID: 4320)
Reads the machine GUID from the registry
- Apophis.exe (PID: 4320)
Creates files in the program directory
- Apophis.exe (PID: 4320)
Manual execution by a user
- mspaint.exe (PID: 4456)
- notepad++.exe (PID: 1580)
Creates files or folders in the user directory
- Apophis.exe (PID: 4320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2053:10:30 02:47:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 26112 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8546 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Apophis |
| FileVersion: | 1.0.0.0 |
| InternalName: | Apophis.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Apophis.exe |
| ProductName: | Apophis |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
126
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
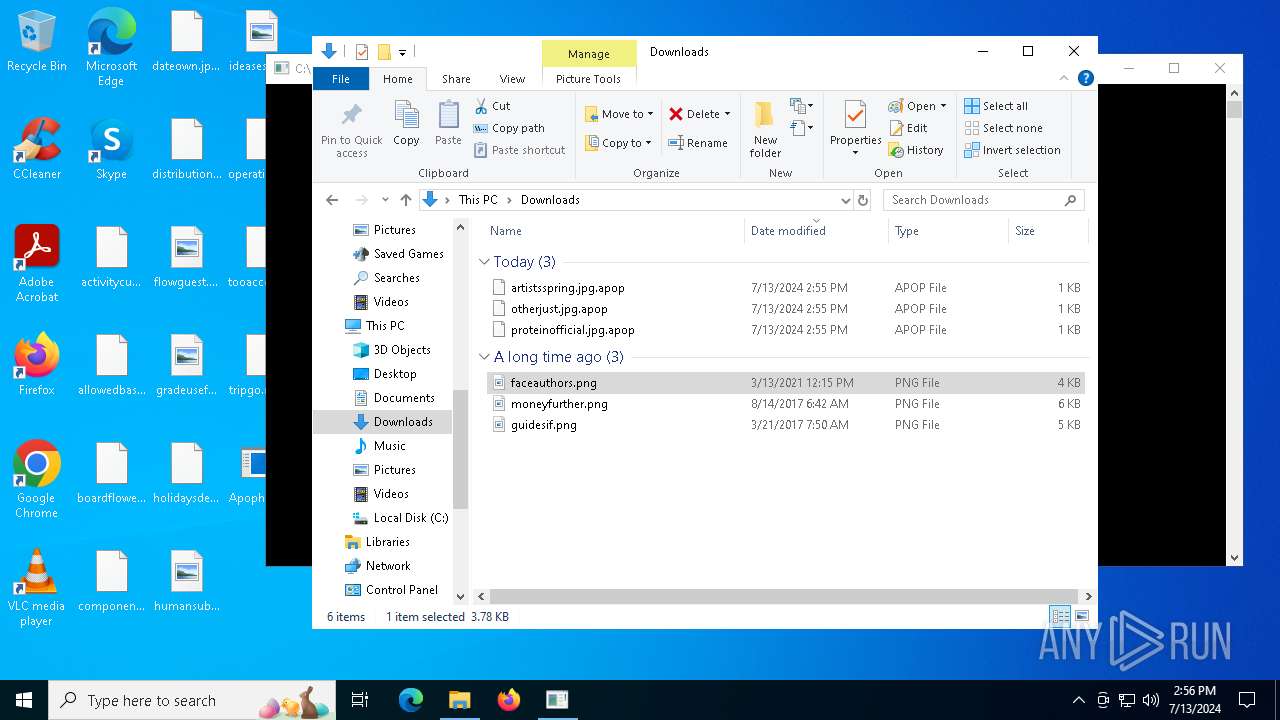
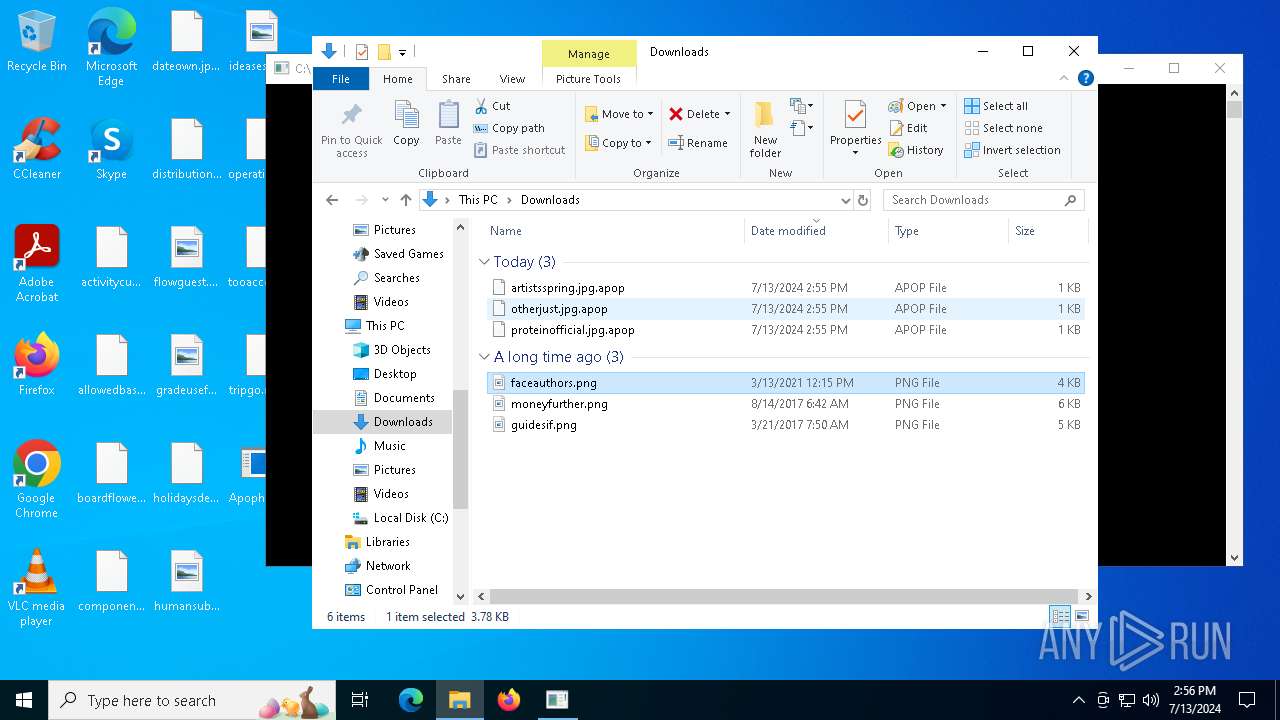
| 1580 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\artistsspring.jpg.apop" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 | |||||||||||||||
| 1824 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | "C:\Users\admin\Desktop\Apophis.exe" | C:\Users\admin\Desktop\Apophis.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Apophis Version: 1.0.0.0 Modules
| |||||||||||||||
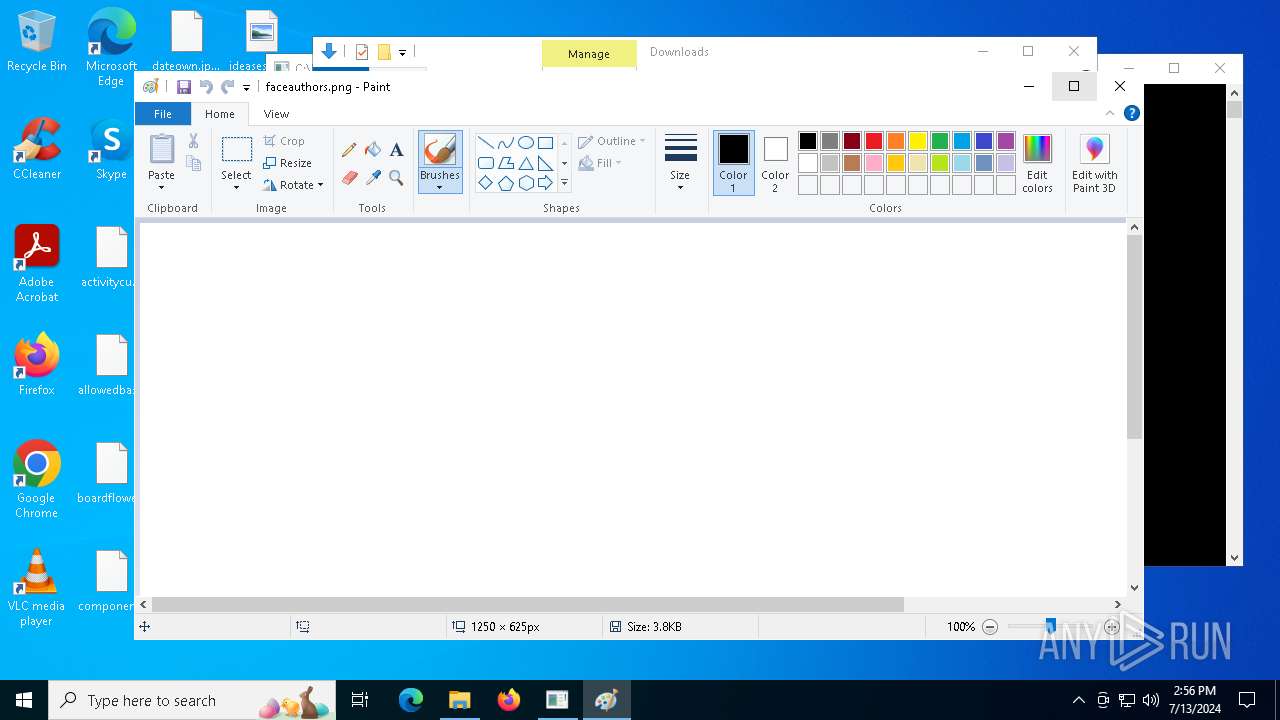
| 4456 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\faceauthors.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 5856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Apophis.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
407
Read events
407
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
555
Text files
27
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER79B3.tmp.WERInternalMetadata.xml.apop | bs | |
MD5:2439FC97951920898A54B2B79EE44A10 | SHA256:21DD772EBF8821C1E36761979F9BF8FBE1AAF3B2D0838400F6A1044253BBFE95 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBA99.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:4A239E06430FBECC08A7CE06B7723EEF | SHA256:A2C78FA20F1C7C338726EFCD9AFCDA3CCBDAB1A0919CC9F563593516B3511A58 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER67EF.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:665A6203869DA8FE4C129DFB7021C879 | SHA256:57B9AE909C2D7B75425CEFCA8F52E5C4812AA1F6FC2AC506E6116CE995028A89 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC588.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:053CD3690FD5ABB387E2EC72E66782F0 | SHA256:9EDEF85CCDBD503DBB519774FBC65CC9AD29DF5700A1AB25CF9B3F788005F8E2 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER56E6.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:710276BE5976CE12FED7D680742F2ED6 | SHA256:6FBEC0DC9429F11BA01123DBC8964CA6CCF6110D4BC2B7EE94667F8DA5F091A4 | |||
| 4320 | Apophis.exe | C:\Users\admin\AppData\Local\IconCache.db.apop | binary | |
MD5:80740707A906156A0285C2583E9B4C62 | SHA256:E955E7C4FC17AD0B9FCC4ED79F560D22BA89CB8ECEC968D9D6B551B53AAC3A67 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCF5D.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:02616024603EC24DAEAB429DCECDFBE4 | SHA256:3E0401C3268B53EA62E24855238CD361839485FE32AF78E6309813CC826C9872 | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA077.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:27F15E3014AC5F424D6DF335EC231B17 | SHA256:7C039C50751422FD18BB87E3720D08D73B80F591476FA347E7CAB90A994DD23C | |||
| 4320 | Apophis.exe | C:\Users\admin\AppData\Local\ConnectedDevicesPlatform\ActivitiesCache.db.apop | binary | |
MD5:FB37C0F0E824CCEE3CD0E66336FE8501 | SHA256:24A399F5F05F17F2DA63420C0712B2B777F9065AC5F76F2710F11BF6B7109DAF | |||
| 4320 | Apophis.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCA8A.tmp.WERInternalMetadata.xml.apop | binary | |
MD5:803045FF8DF78BB5C51471DB30D6F4FA | SHA256:3DC8CDB0B7BBAA13A030A2CB784BE14479303673854F101743031C97CA51EAAF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2052 | svchost.exe | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2120 | RUXIMICS.exe | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2120 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2052 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.50.73.10:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 92.123.104.19:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2052 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2448 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2052 | svchost.exe | 2.16.164.99:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
2120 | RUXIMICS.exe | 2.16.164.99:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
2120 | RUXIMICS.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2052 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |