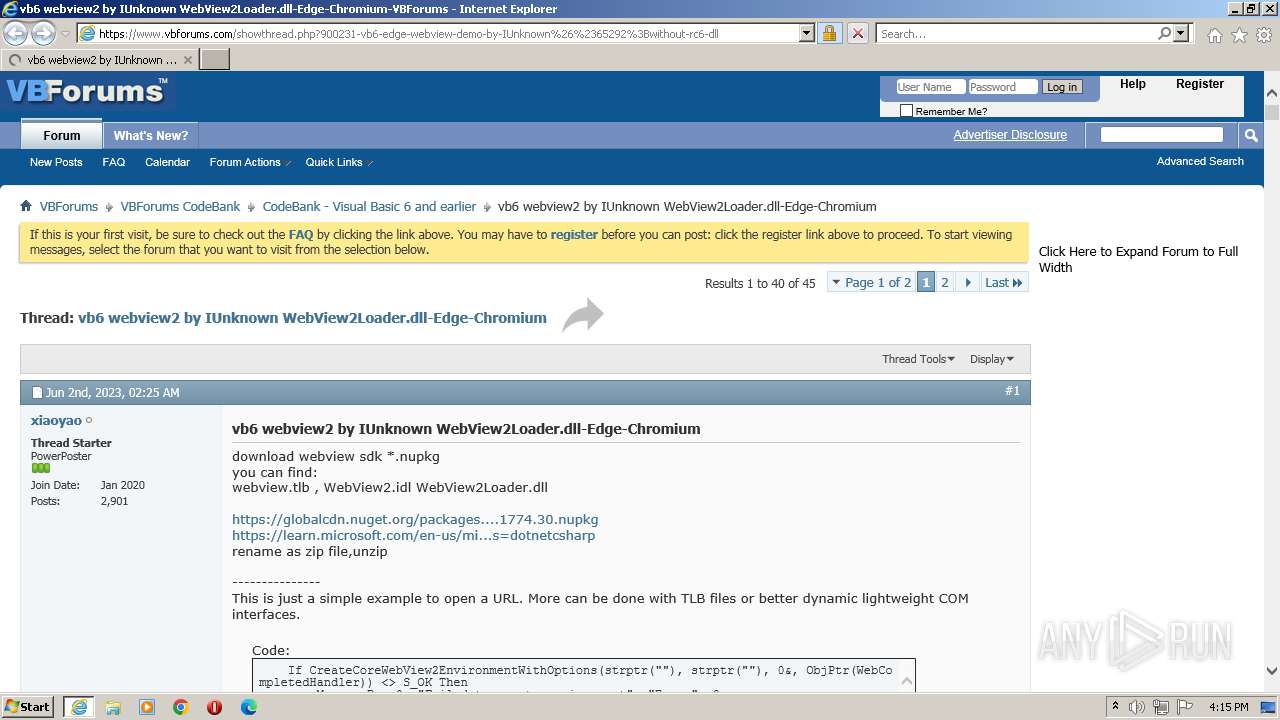
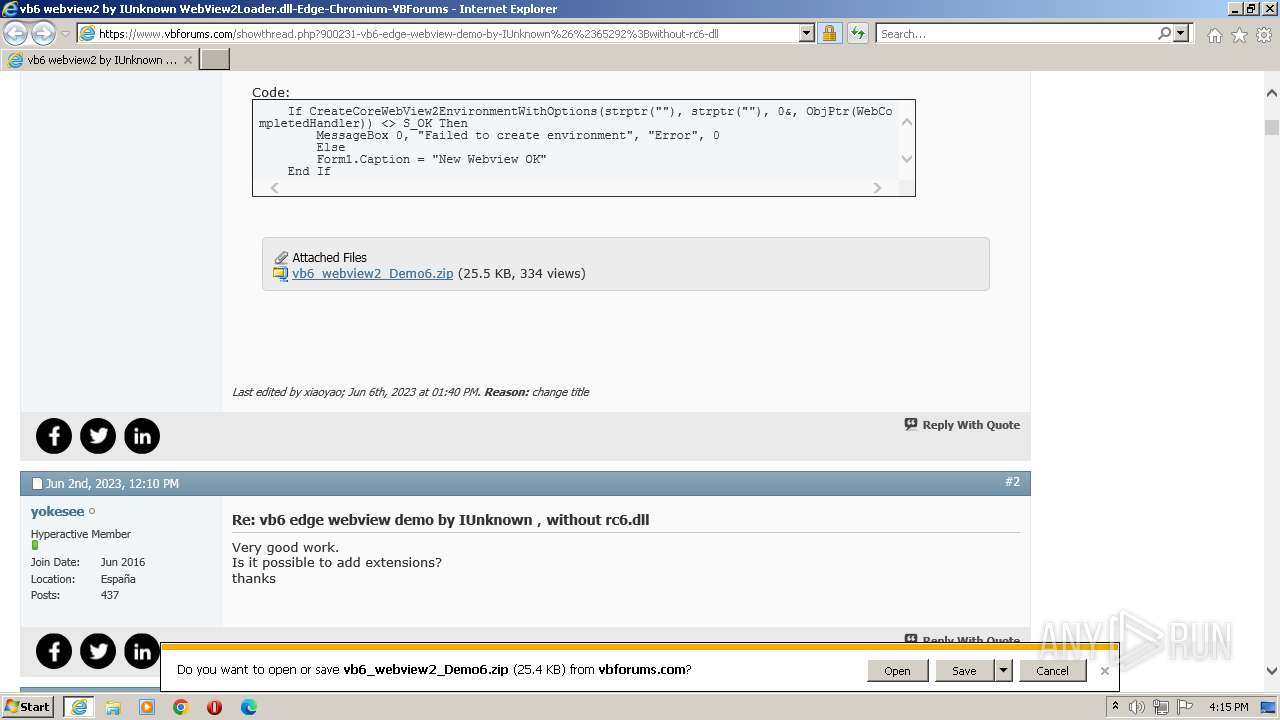
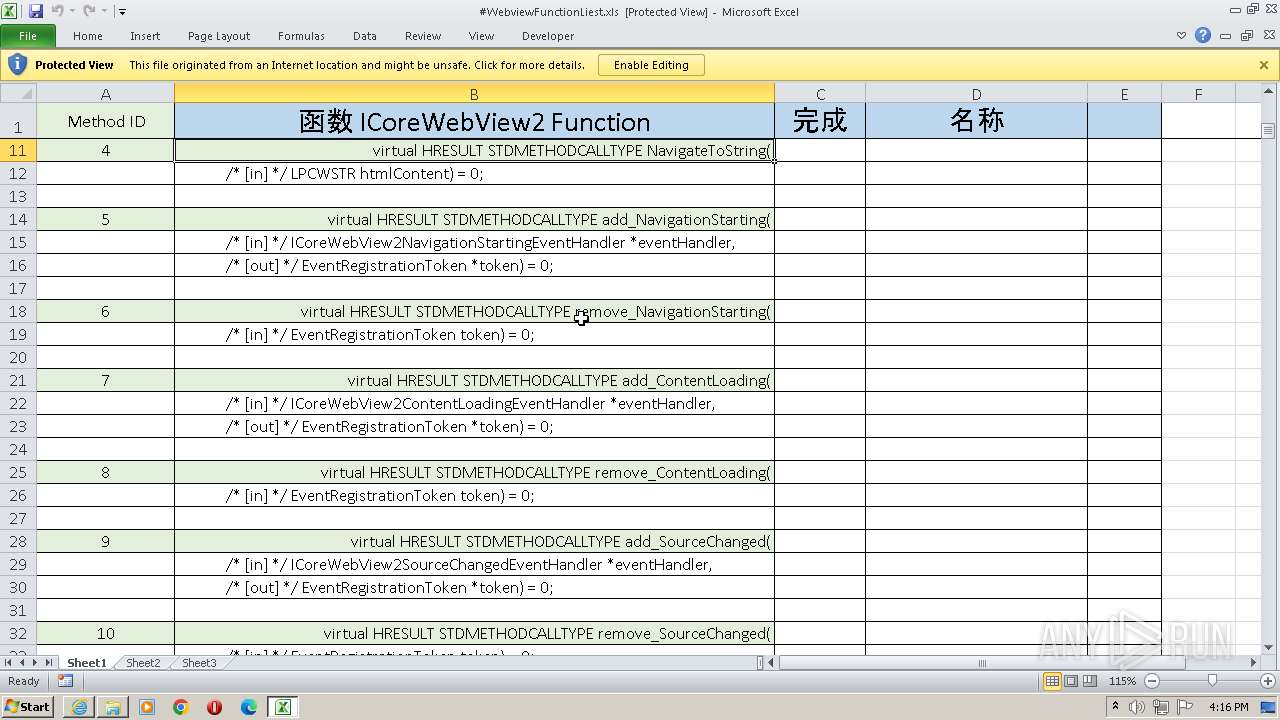
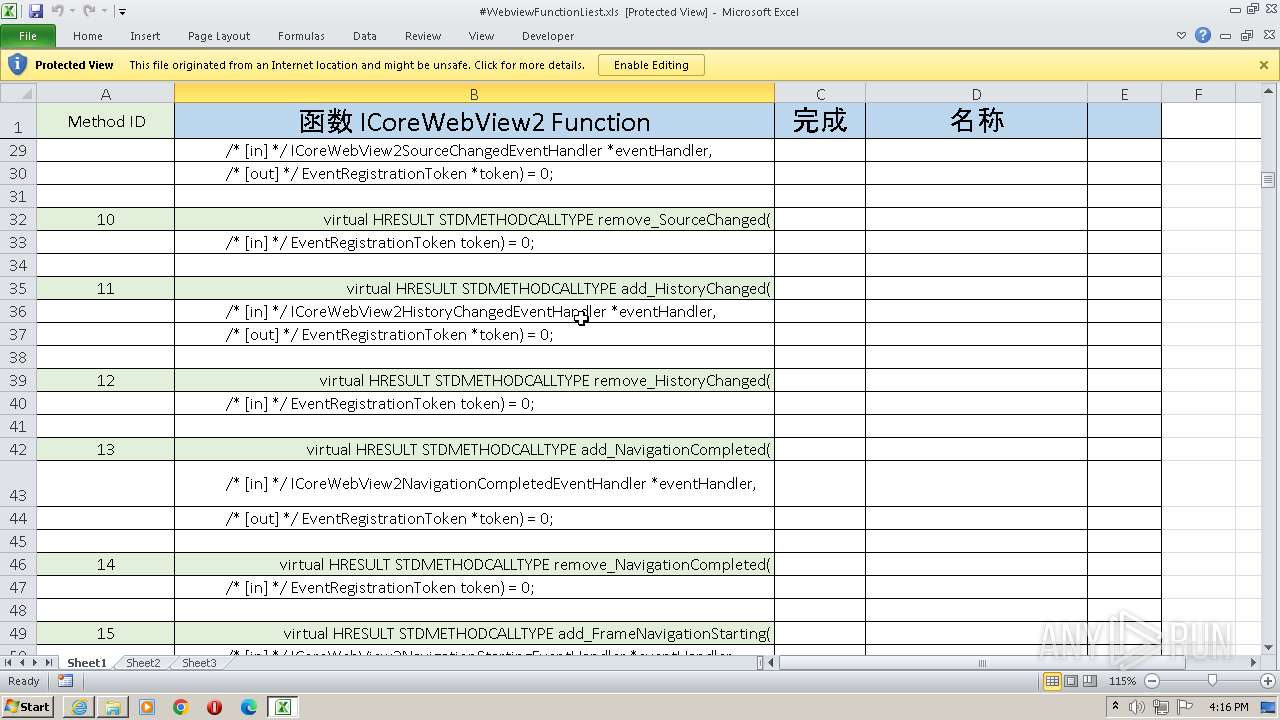
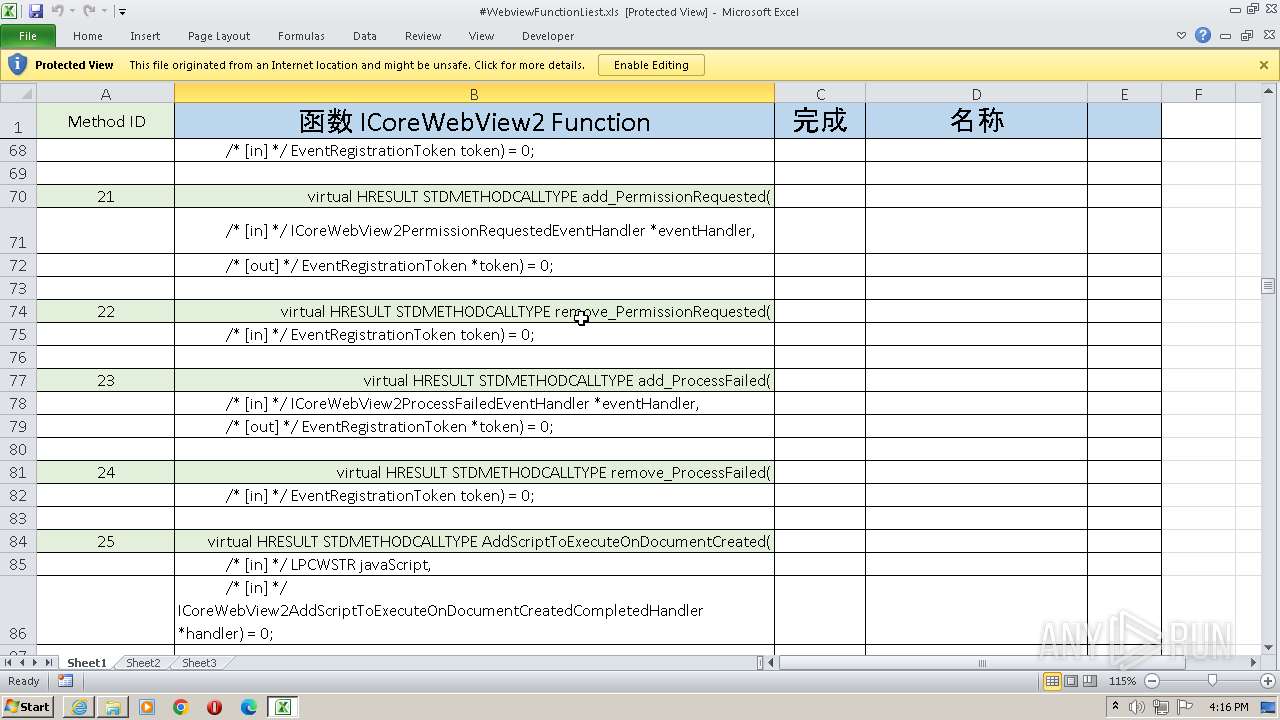
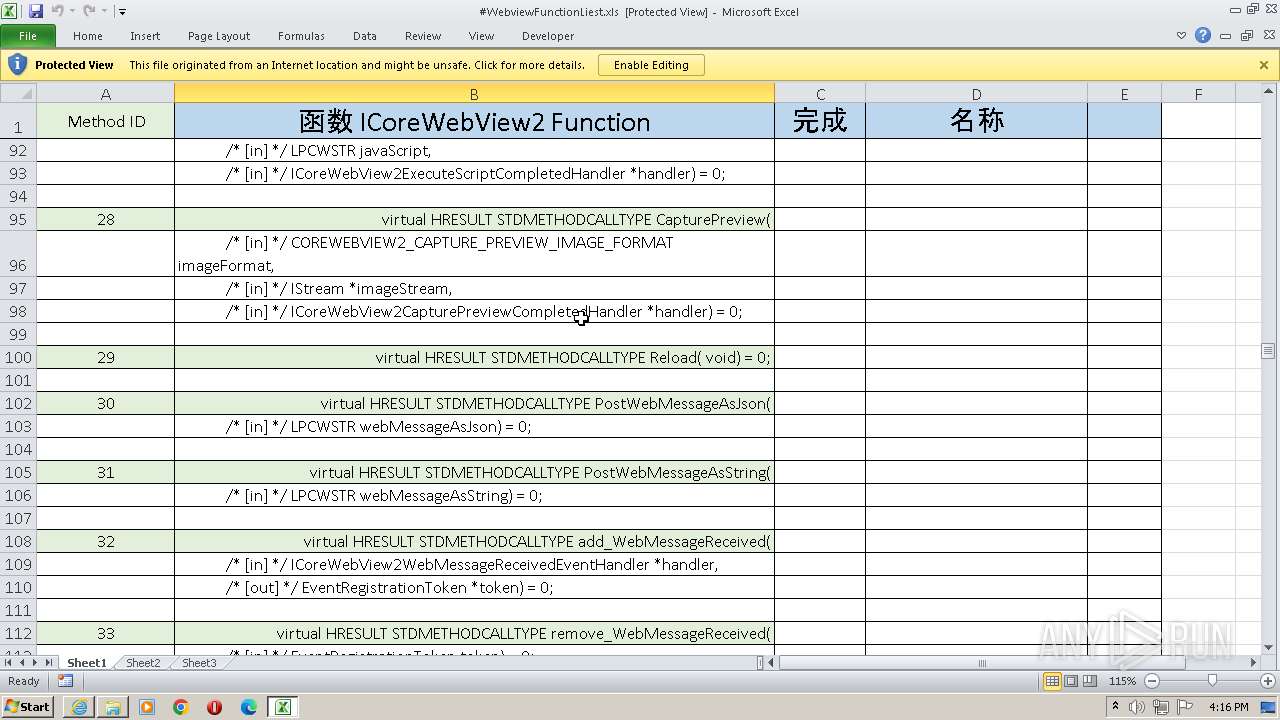
| URL: | https://www.vbforums.com/showthread.php?900231-vb6-edge-webview-demo-by-IUnknown%26%2365292%3Bwithout-rc6-dll |
| Full analysis: | https://app.any.run/tasks/0d7c3ec8-d092-47e3-957e-8f52df454508 |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2023, 15:14:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A3620880D89F2F3BE9349A0552F404CC |
| SHA1: | 965B9B27E5C4B95150EABBF00BFB55592BF979C5 |
| SHA256: | C6EF3E3F598C9D355A00C8612CD71EFC11B22345214E852A8E4441C198DBC568 |
| SSDEEP: | 3:N8DSLLQQIHTKWNJ19RG/qZswYEIXZJ:2OL8QIzNN39RUcsJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- EXCEL.EXE (PID: 3776)
INFO
Application launched itself
- iexplore.exe (PID: 3508)
Manual execution by a user
- WinRAR.exe (PID: 1896)
- EXCEL.EXE (PID: 3776)
The process uses the downloaded file
- EXCEL.EXE (PID: 3776)
- iexplore.exe (PID: 3508)
- WinRAR.exe (PID: 1896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1896 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\vb6_webview2_Demo6.zip" C:\Users\admin\Downloads\vb6_webview2_Demo6\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3508 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3508 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.vbforums.com/showthread.php?900231-vb6-edge-webview-demo-by-IUnknown%26%2365292%3Bwithout-rc6-dll" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3628 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\microsoft office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3776 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\microsoft office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
20 569
Read events
20 457
Write events
92
Delete events
20
Modification events
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3508) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
44
Text files
102
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2LE7VT9W.txt | text | |
MD5:70B02EEA96460A34E1CF0AB8E4DD95F3 | SHA256:17BC75408888DE0D97212C11498E07A49731AC57A6FF3E5A240F85B1316C8A85 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:E0CC2BF4811BC1C204DFD212AE09441E | SHA256:6B0ECD21EB093329E5F2015EC297EFF209A4A5A61FB3B357D661C7BF646463CB | |||
| 3508 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:DA3174E4F36DBAD1FE775AD86E659CFA | SHA256:FB197C8BE97F2DCC6F6B0750FF91AA914330FF2D0F970DEA191255B00496D784 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\logo[1].gif | image | |
MD5:EA1DACCEB6C29763F2116DDDFCDA11D8 | SHA256:743D3C5B12F13F8AC5283605522BC5D17ECD2D2C6E9E5C36431EA5E293820D34 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\navbit-home[1].png | image | |
MD5:7528111AF2F88BFBC3EDD48F35113F1B | SHA256:C85826F4126BE1FBE84F09341F1C93E26C763854B672FC220374E3699E29390C | |||
| 3508 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:24BE8A92460B5B7A555B1DA559296958 | SHA256:77A3CFE6B7EB676AF438D5DE88C7EFCB6ABCC494E0B65DA90201969E6D79B2A3 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\vbulletin_lightbox[1].js | text | |
MD5:4ACC0E668744AC0255DBCBC3146CC5B5 | SHA256:EE716546D8E7E7FB70B5DCEAD0E4B854621FB55B6FE75637544EC990379ADF4B | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\css[1].css | text | |
MD5:85A1D6F86886CB048BF0A0C82D7C9C62 | SHA256:CB839F422A4F2539B9F4143A785C960B6C2160EB65FB23D349ADCE491254DAF6 | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\vbulletin-core[1].js | text | |
MD5:4354280604E5FB0C1D52A661EBCDD6CC | SHA256:CA69F49952AB3287A0AB4BFB477863C0E8831D309C3D66D0AFDE86E1C6774558 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
64
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3508 | iexplore.exe | GET | 200 | 8.253.145.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9f75ce26aa17a5b2 | unknown | compressed | 4.66 Kb | unknown |
3508 | iexplore.exe | GET | 200 | 8.253.145.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7b4d5311b636771a | unknown | compressed | 4.66 Kb | unknown |
2388 | iexplore.exe | GET | 200 | 8.253.145.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?49361a3f17fc7612 | unknown | compressed | 61.6 Kb | unknown |
2388 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD%2BlF2iY2d5QgqUIklwaLMG | unknown | der | 472 b | unknown |
2388 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | der | 1.41 Kb | unknown |
2388 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | der | 717 b | unknown |
2388 | iexplore.exe | GET | 200 | 8.253.145.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6f8dc1c745099382 | unknown | compressed | 4.66 Kb | unknown |
3508 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | unknown | der | 1.47 Kb | unknown |
2388 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECbJRxmm8kW4EEL68gvw1os%3D | unknown | der | 471 b | unknown |
2388 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHial9FOU3O4CQrtdaiOeXk%3D | unknown | der | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2388 | iexplore.exe | 151.101.2.132:443 | www.vbforums.com | FASTLY | US | unknown |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2388 | iexplore.exe | 8.253.145.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3508 | iexplore.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3508 | iexplore.exe | 8.253.145.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3508 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2388 | iexplore.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
2388 | iexplore.exe | 151.101.66.132:443 | www.vbforums.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.vbforums.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
s.ntv.io |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
ml314.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |