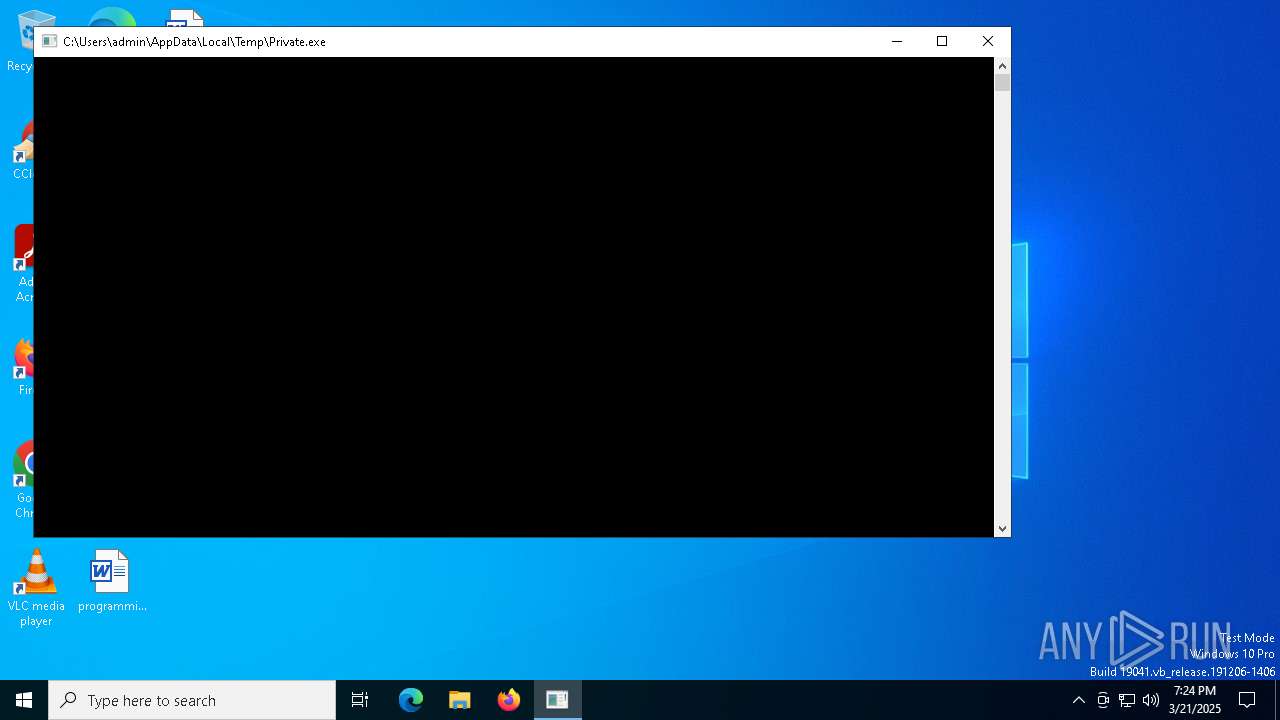
| File name: | Private.exe |
| Full analysis: | https://app.any.run/tasks/e969c96c-ccdc-4dcf-91f5-4337f7f06736 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2025, 19:24:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 10 sections |
| MD5: | 22A77A45372DF8284A85B67B7795AB86 |
| SHA1: | 823CCB179BC9043D7CD75FB5A73DC995379749FE |
| SHA256: | C6ECB7EB35F52071D651E46C97547F16C6899319080B27D96EBB5F3500077FB0 |
| SSDEEP: | 98304:X3yRs+45MLRp3QQj6ZaQbW1e/+GvWpVhfllLebYG7uUENy9b5QzmQT1STWd6Z0rk:DePshWX77zNLwfOH5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- Private.exe (PID: 7596)
Executable content was dropped or overwritten
- Private.exe (PID: 7596)
Detected use of alternative data streams (AltDS)
- Private.exe (PID: 7596)
- WerFault.exe (PID: 8176)
Executes application which crashes
- Private.exe (PID: 7596)
INFO
Creates files in the program directory
- Private.exe (PID: 7596)
Reads the machine GUID from the registry
- Private.exe (PID: 7596)
Reads the computer name
- Private.exe (PID: 7596)
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 7980)
Creates files or folders in the user directory
- WerFault.exe (PID: 8176)
Create files in a temporary directory
- Private.exe (PID: 7596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:11 18:43:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 1896960 |
| InitializedDataSize: | 6184448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x165ccf0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
146
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7416 | "C:\Users\admin\AppData\Local\Temp\Private.exe" | C:\Users\admin\AppData\Local\Temp\Private.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7596 | "C:\Users\admin\AppData\Local\Temp\Private.exe" | C:\Users\admin\AppData\Local\Temp\Private.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 7612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Private.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7964 | C:\WINDOWS\system32\cmd.exe /c certutil -hashfile "C:\Users\admin\AppData\Local\Temp\Private.exe" MD5 | find /i /v "md5" | find /i /v "certutil" | C:\Windows\System32\cmd.exe | — | Private.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7980 | certutil -hashfile "C:\Users\admin\AppData\Local\Temp\Private.exe" MD5 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7988 | find /i /v "md5" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8004 | find /i /v "certutil" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8176 | C:\WINDOWS\system32\WerFault.exe -u -p 7596 -s 684 | C:\Windows\System32\WerFault.exe | — | Private.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 307
Read events
2 302
Write events
4
Delete events
1
Modification events
| (PID) Process: | (7980) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (7980) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (7980) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (8176) WerFault.exe | Key: | \REGISTRY\A\{f546dff4-1460-4752-047a-ddd45b2abe03}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (8176) WerFault.exe | Key: | \REGISTRY\A\{f546dff4-1460-4752-047a-ddd45b2abe03}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Private.exe_6a6842dad8b34b76982b3c1a24d856397db63_e31941c7_fbce5ac2-a141-44a5-ae5a-1d5598cf913c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8176 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\7596.dmp | — | |
MD5:— | SHA256:— | |||
| 7596 | Private.exe | C:\Users\admin\AppData\Local\Temp\Loader.exe | executable | |
MD5:22A77A45372DF8284A85B67B7795AB86 | SHA256:C6ECB7EB35F52071D651E46C97547F16C6899319080B27D96EBB5F3500077FB0 | |||
| 8176 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:BAF4C6C4EBAE05618BC571651B23179D | SHA256:7F61F9051AECC3682B95089E3B867F70A21C9A4AD43E30F44E4B008D13BF9442 | |||
| 7596 | Private.exe | C:\Users\admin\AppData\Local\Temp\Private.exe:Ethera.enc | executable | |
MD5:22A77A45372DF8284A85B67B7795AB86 | SHA256:C6ECB7EB35F52071D651E46C97547F16C6899319080B27D96EBB5F3500077FB0 | |||
| 7596 | Private.exe | C:\ProgramData\KeyAuth\Debug\Private\03-21-2025.txt | text | |
MD5:360C16CE3832F3E58238F62B78870FC4 | SHA256:A2EF99CF99104C0046088CE936A986539414436D49E2CF2BFD5708B816955316 | |||
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE09E.tmp.dmp | binary | |
MD5:528FD8159EFFDF17C24906098DE7805E | SHA256:FB5FA68CA00A2922E39ECFA3D2920D98B1A1E2B5BCD133E1443E9EE906028674 | |||
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE1E8.tmp.xml | xml | |
MD5:0BE4BAF3F90225F8A8CE2CD6E59A5B6B | SHA256:27621C84C3E4B0ACB41DC6E36F7C6CFB78CD4B8ADAA735A33621DD2B6C59A362 | |||
| 8176 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE1C8.tmp.WERInternalMetadata.xml | binary | |
MD5:9401206673790B349285B164D38D7202 | SHA256:A655F92021E94E4D450BC961F07656083F3098EA3A8C8232F4DC5627083E412E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
27
DNS requests
14
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2516 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2516 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7716 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5364 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7596 | Private.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
keyauth.win |
| malicious |
x1.c.lencr.org |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7596 | Private.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
7596 | Private.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
7596 | Private.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
7596 | Private.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
7596 | Private.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |