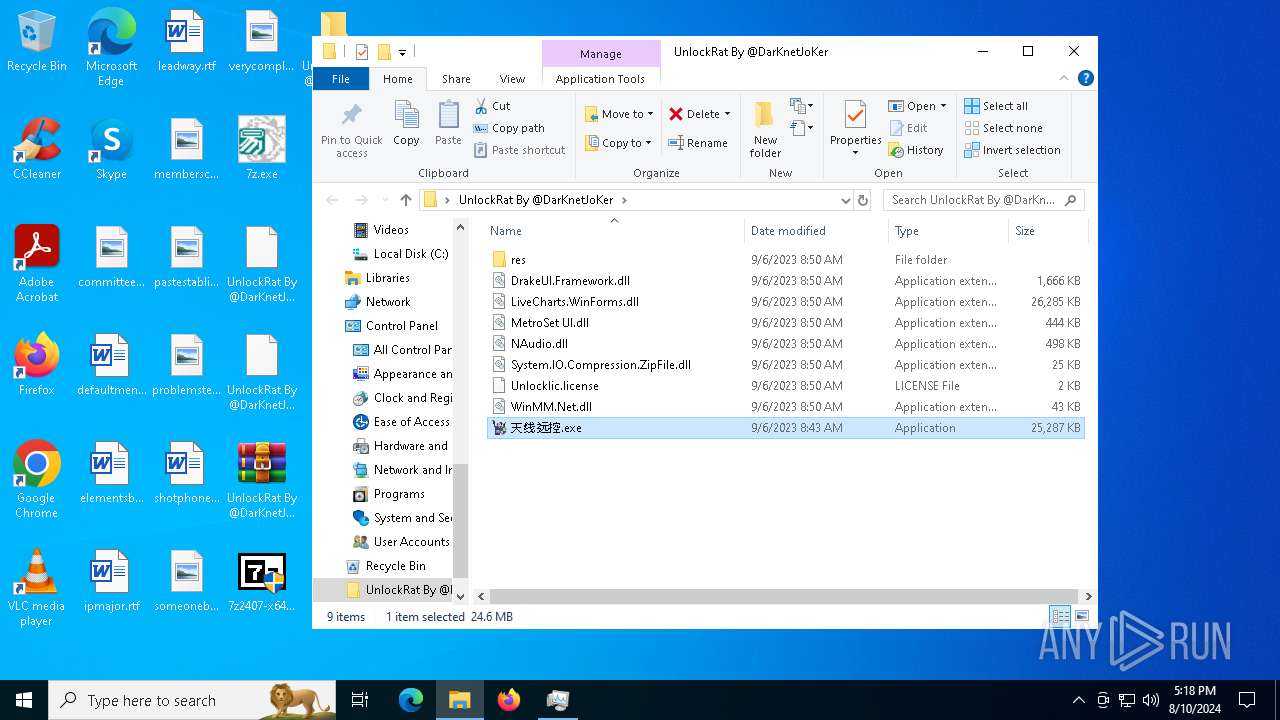
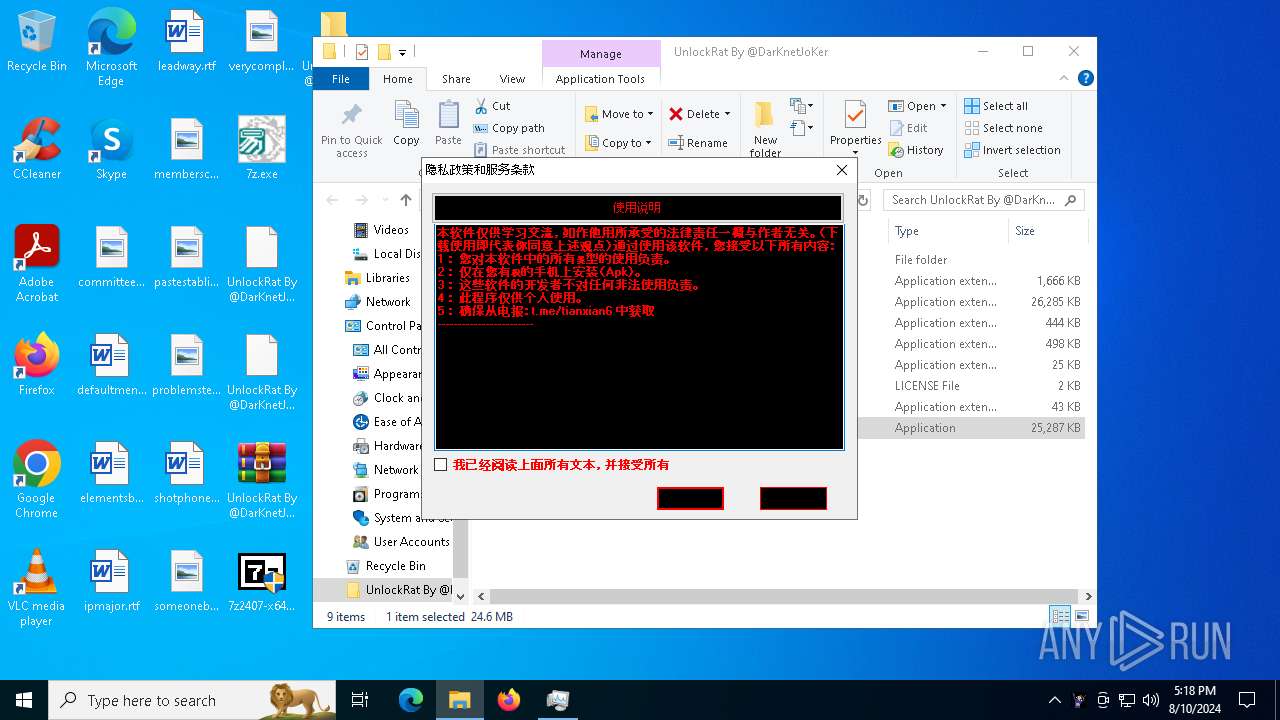
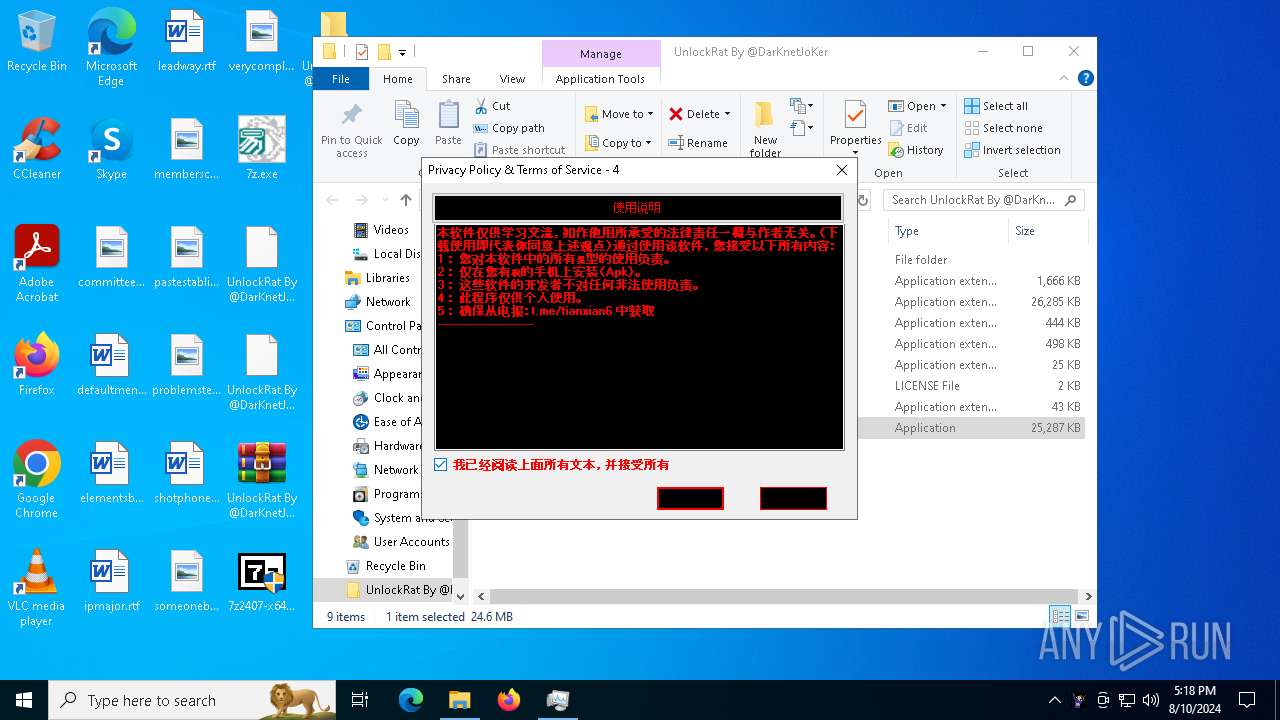
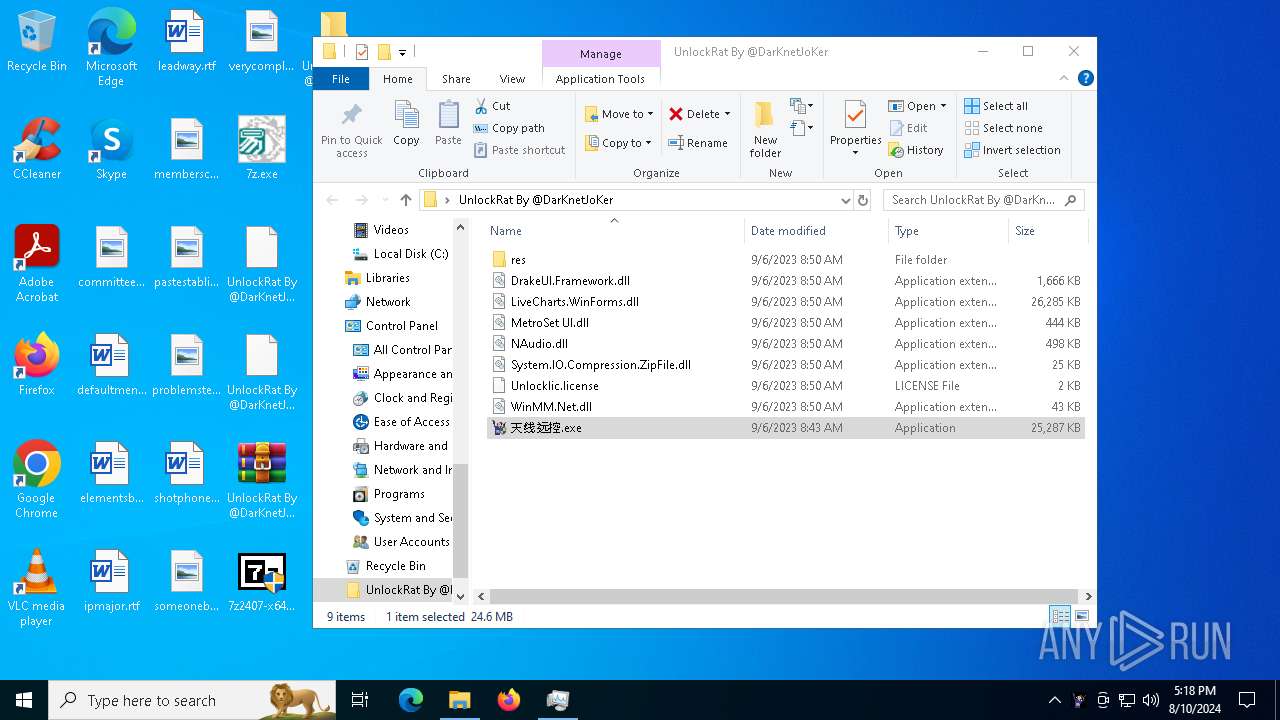
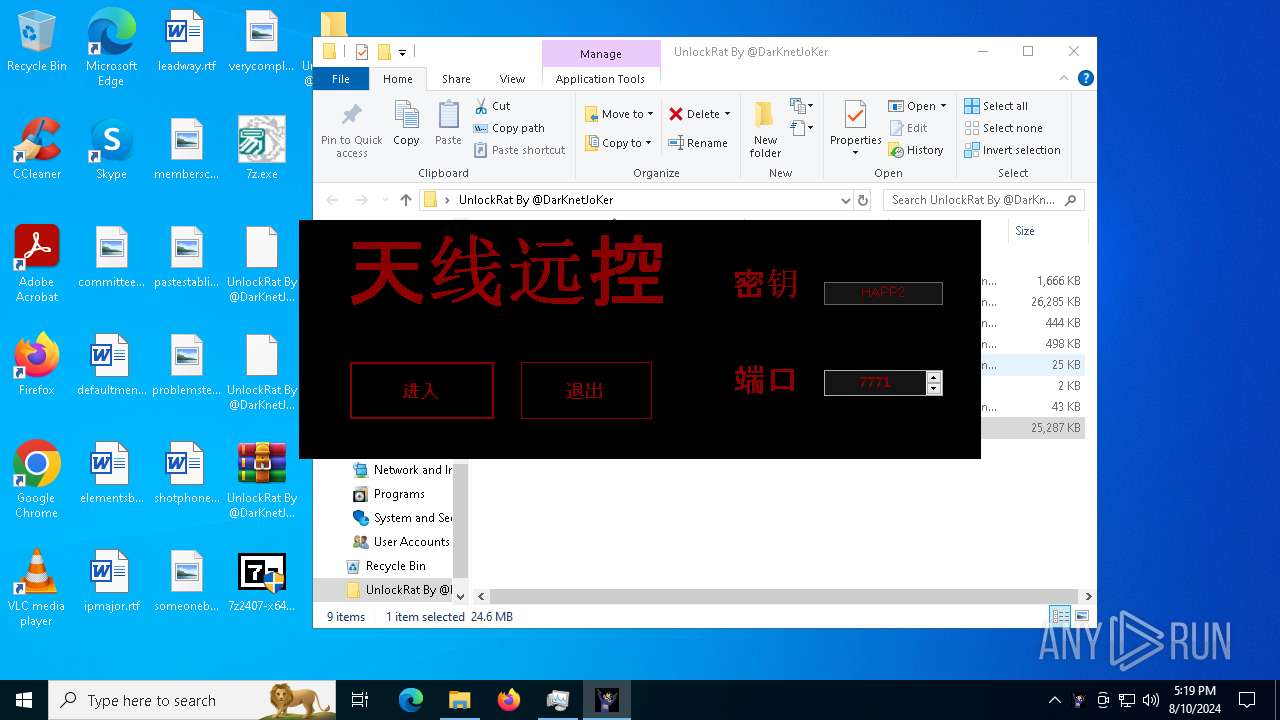
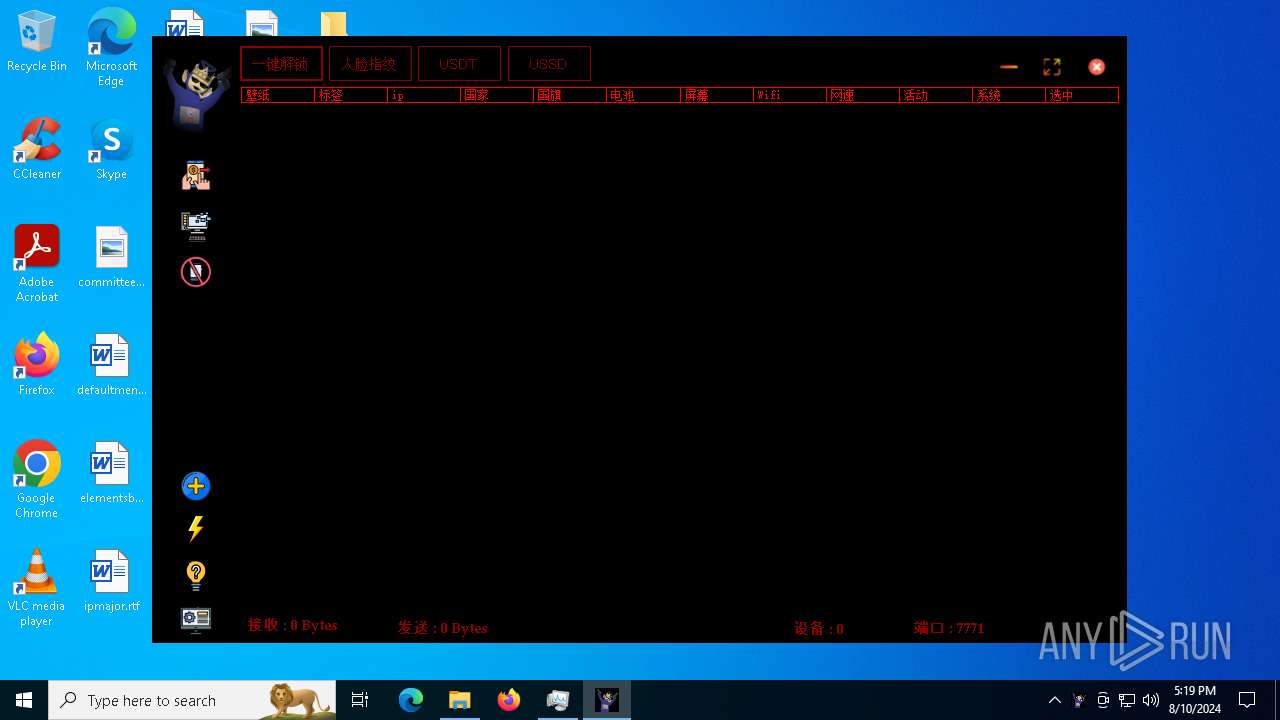
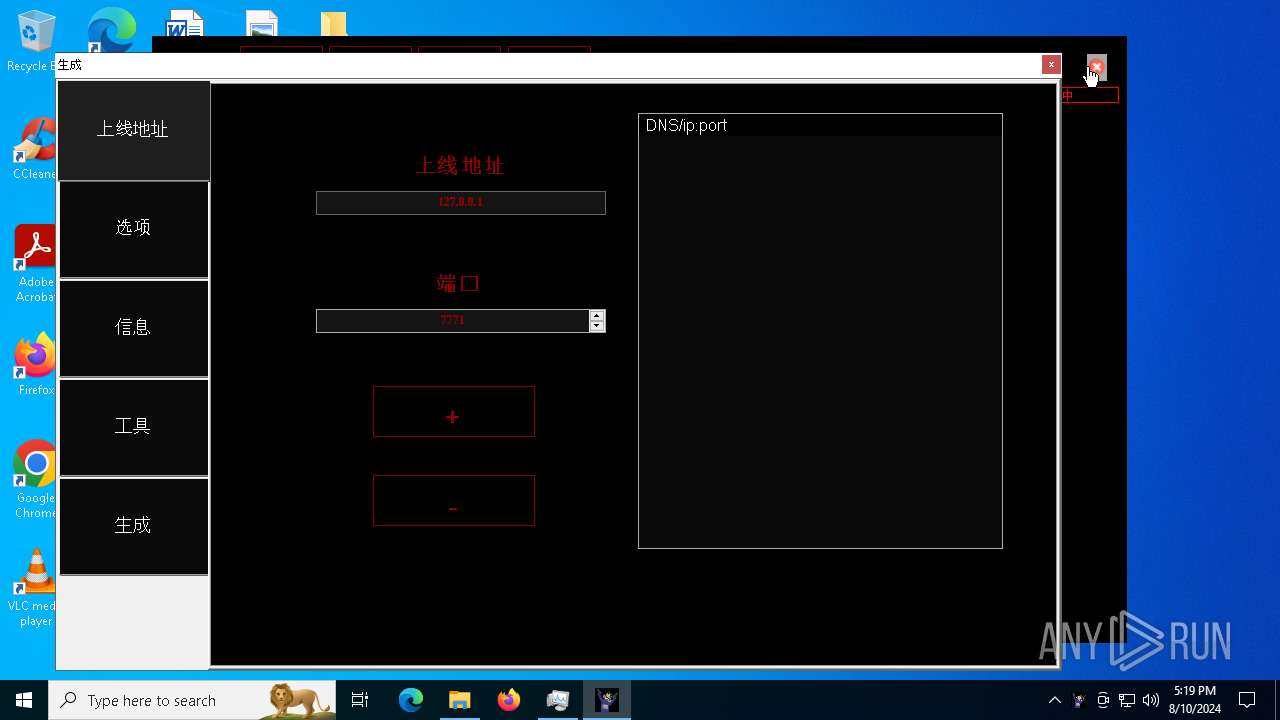
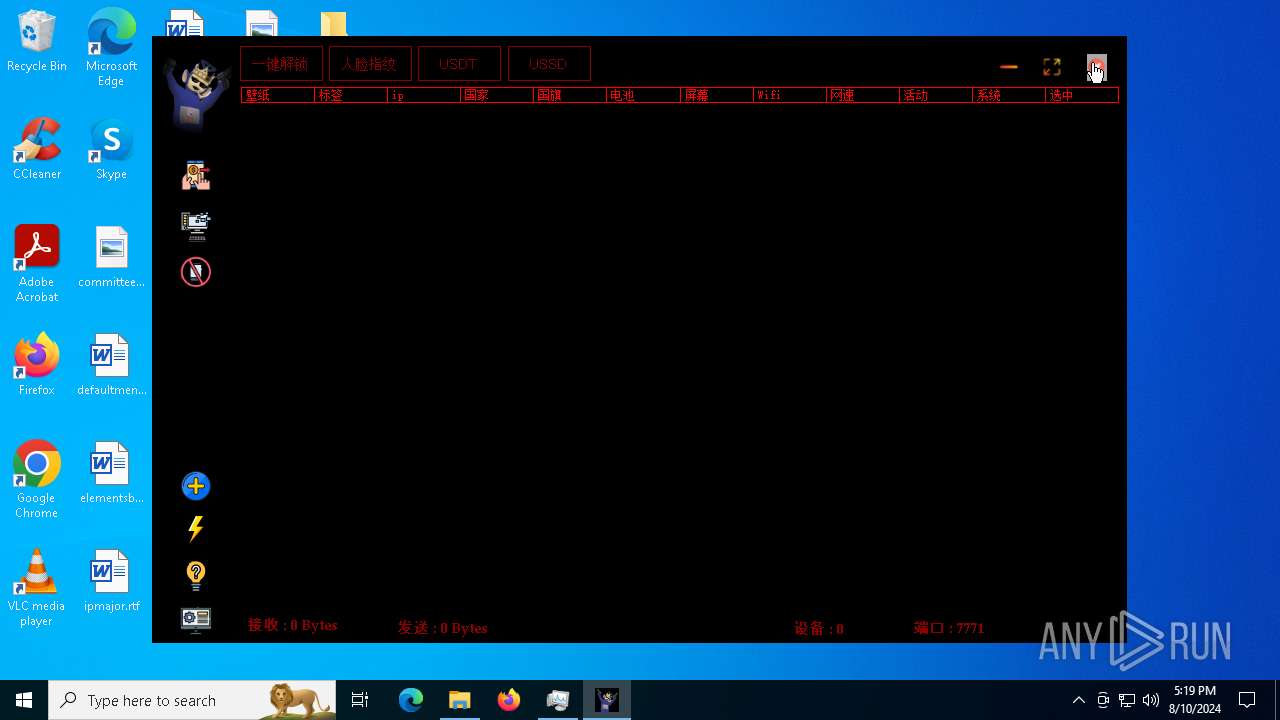
| File name: | 7z.exe |
| Full analysis: | https://app.any.run/tasks/6f997323-2d2d-4440-8b86-bd88c17a2ccb |
| Verdict: | Malicious activity |
| Analysis date: | August 10, 2024, 17:16:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C90AF375BC40D0506C16B4ED75EFCCB6 |
| SHA1: | CD29F79B128BA67BC30E44E7A0365C5FFD3BE376 |
| SHA256: | C6E3AA8B8B76B9E3B9DF71B3F31D1B7A23F2A031099ACEB68C39F38945B65DC0 |
| SSDEEP: | 49152:A3HzLnqOaNMCFJ6kPvO1cg0i7YCD7n4HnS24Hcst:er7ayGJ6kHOSRCXxnt |
MALICIOUS
Changes the autorun value in the registry
- 7z.exe (PID: 6612)
Connects to the CnC server
- Synaptics.exe (PID: 7068)
SUSPICIOUS
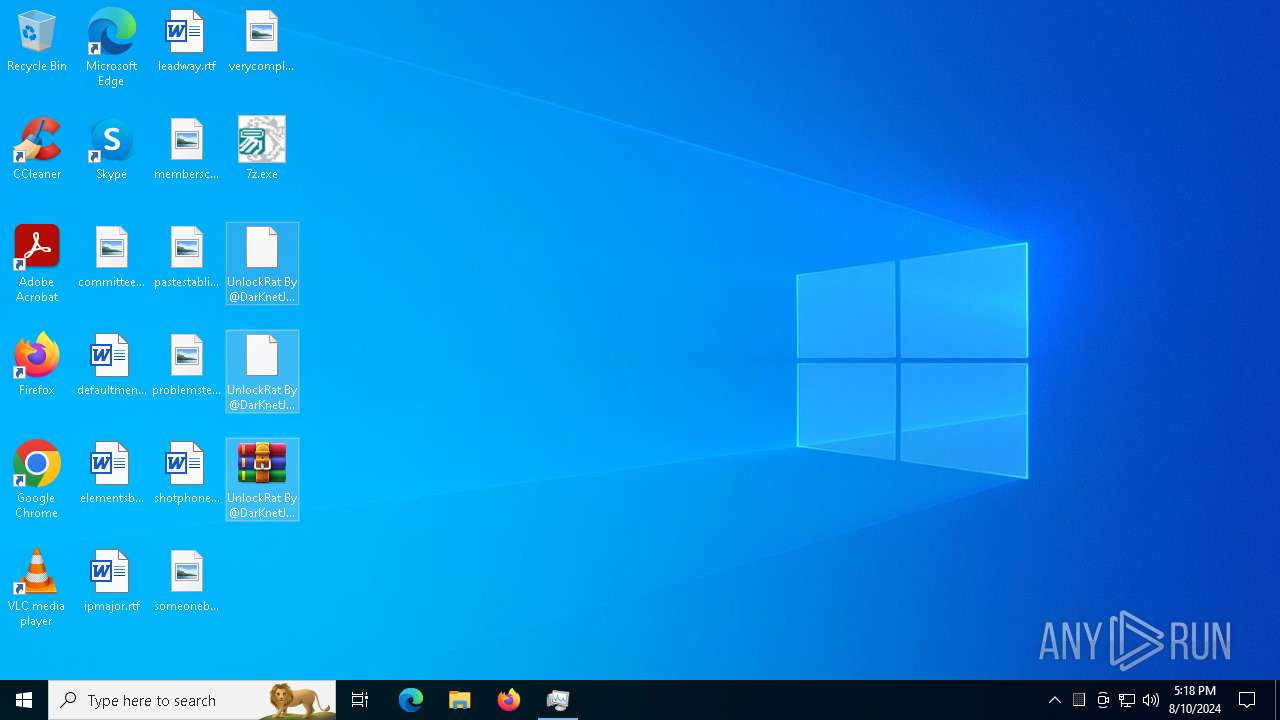
Drops the executable file immediately after the start
- runas.exe (PID: 6316)
- 7z.exe (PID: 6612)
- 7z2407-x64.exe (PID: 872)
- 7zG.exe (PID: 5372)
Executable content was dropped or overwritten
- 7z.exe (PID: 6612)
- 7z2407-x64.exe (PID: 872)
- 7zG.exe (PID: 5372)
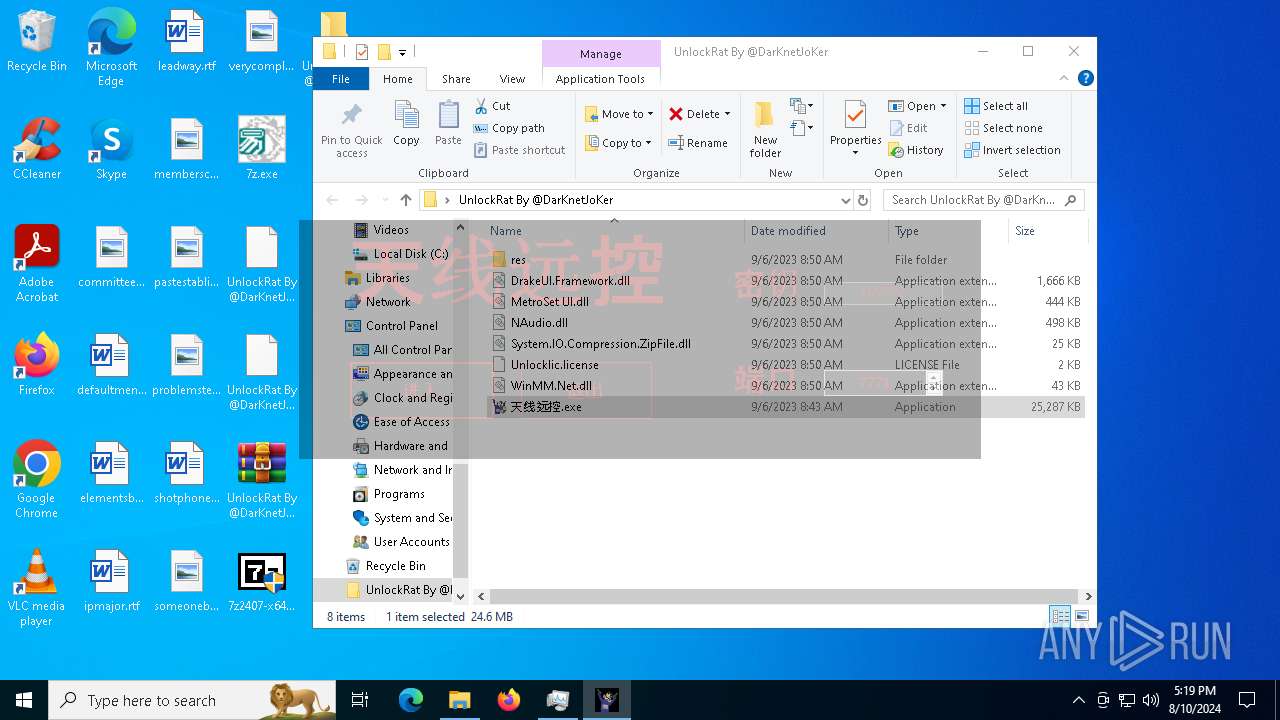
Drops 7-zip archiver for unpacking
- 7z.exe (PID: 6612)
- 7z2407-x64.exe (PID: 872)
Reads the date of Windows installation
- 7z.exe (PID: 6612)
Reads security settings of Internet Explorer
- 7z.exe (PID: 6612)
- Synaptics.exe (PID: 7068)
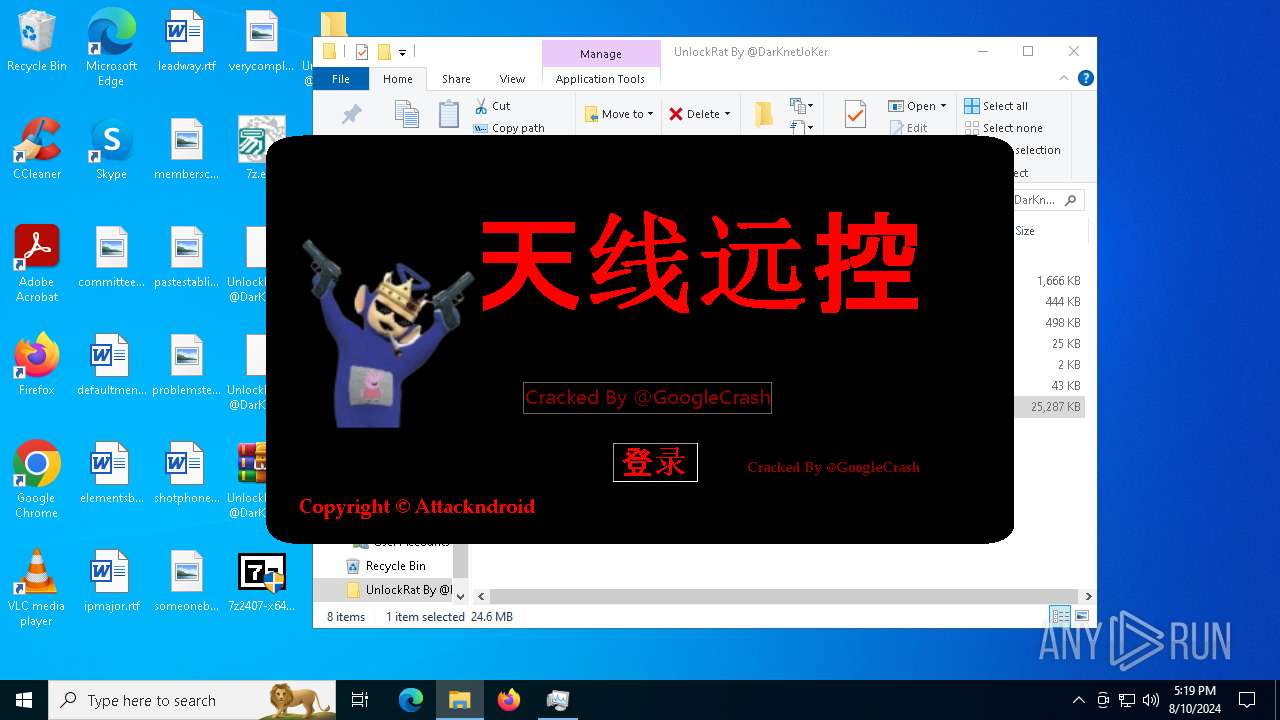
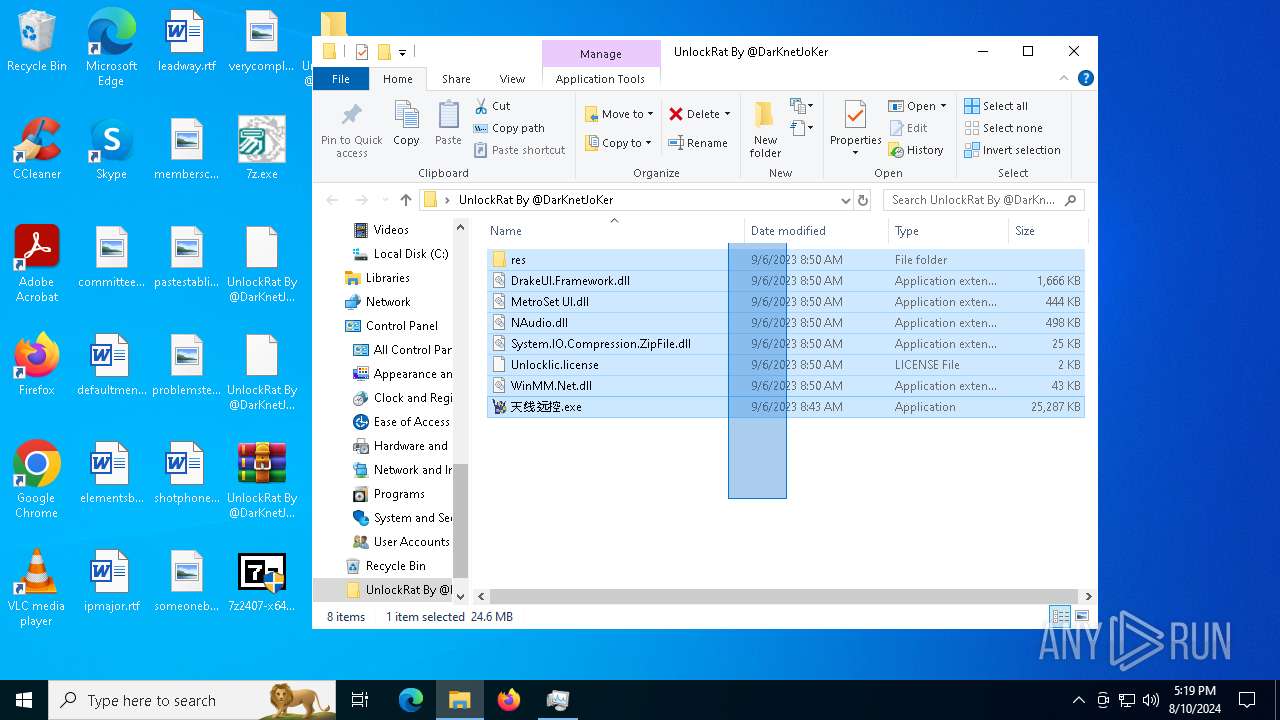
- 天线远控.exe (PID: 6352)
- 天线远控.exe (PID: 5244)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 7068)
Creates a software uninstall entry
- 7z2407-x64.exe (PID: 872)
Creates/Modifies COM task schedule object
- 7z2407-x64.exe (PID: 872)
Process drops legitimate windows executable
- 7zG.exe (PID: 5372)
INFO
Checks supported languages
- 7z.exe (PID: 6612)
- ._cache_7z.exe (PID: 1288)
- Synaptics.exe (PID: 7068)
- 7zG.exe (PID: 5372)
- 7z2407-x64.exe (PID: 872)
- 天线远控.exe (PID: 5244)
- 天线远控.exe (PID: 6352)
Reads the computer name
- 7z.exe (PID: 6612)
- Synaptics.exe (PID: 7068)
- 7zG.exe (PID: 5372)
- 7z2407-x64.exe (PID: 872)
- 天线远控.exe (PID: 6352)
- 天线远控.exe (PID: 5244)
Creates files in the program directory
- 7z.exe (PID: 6612)
- Synaptics.exe (PID: 7068)
- 7z2407-x64.exe (PID: 872)
Checks proxy server information
- Synaptics.exe (PID: 7068)
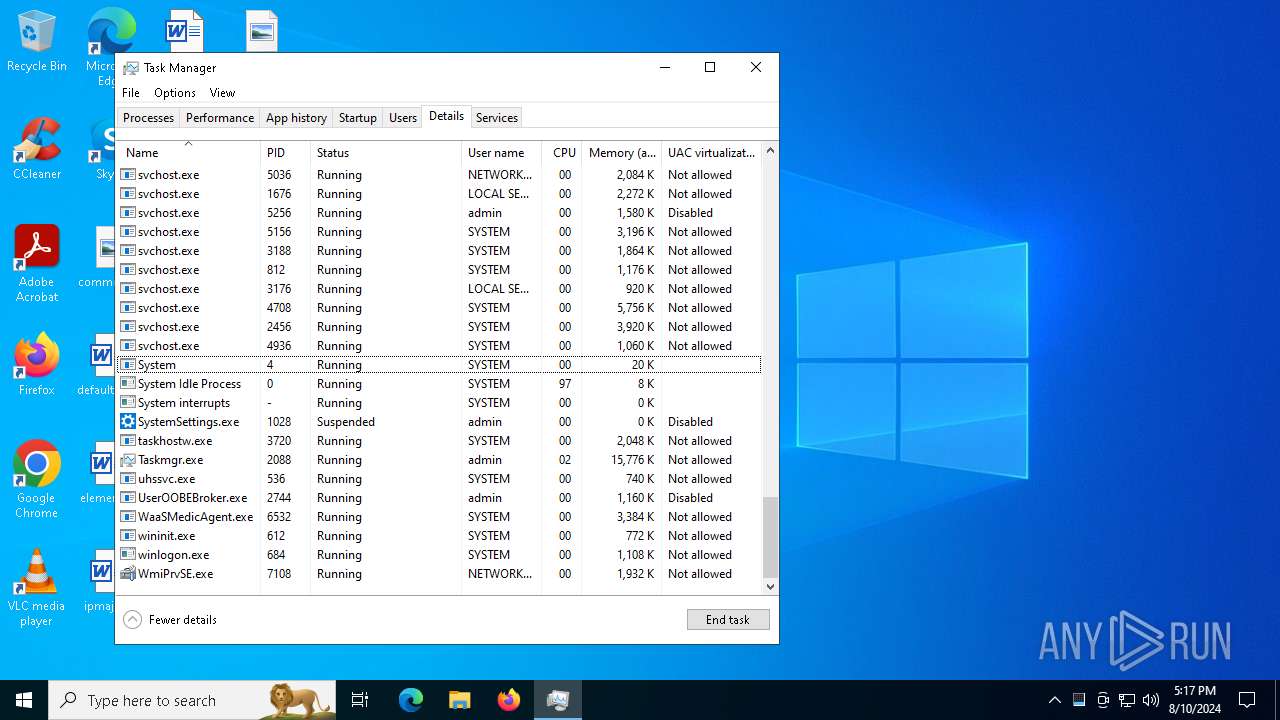
Manual execution by a user
- Taskmgr.exe (PID: 4920)
- Taskmgr.exe (PID: 2088)
- 7z2407-x64.exe (PID: 4784)
- 7zG.exe (PID: 5372)
- 7z2407-x64.exe (PID: 872)
- 天线远控.exe (PID: 5244)
- 天线远控.exe (PID: 4784)
- 天线远控.exe (PID: 6696)
- 天线远控.exe (PID: 6352)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2088)
Reads the machine GUID from the registry
- 天线远控.exe (PID: 6352)
- 天线远控.exe (PID: 5244)
.NET Reactor protector has been detected
- 天线远控.exe (PID: 6352)
Creates files or folders in the user directory
- 天线远控.exe (PID: 6352)
- 天线远控.exe (PID: 5244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 469504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.0 |
| FileDescription: | 易语言程序 |
| ProductName: | 易语言程序 |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | 本程序使用易语言编写(http://www.eyuyan.com) |
Total processes
158
Monitored processes
16
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | "C:\Users\admin\Desktop\7z2407-x64.exe" | C:\Users\admin\Desktop\7z2407-x64.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 24.07 Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1288 | "C:\WINDOWS\system32\._cache_7z.exe" | C:\Windows\SysWOW64\._cache_7z.exe | — | 7z.exe | |||||||||||
User: Administrator Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 0 Version: 22.00 Modules
| |||||||||||||||
| 2088 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\Users\admin\Desktop\7z2407-x64.exe" | C:\Users\admin\Desktop\7z2407-x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Installer Exit code: 3221226540 Version: 24.07 Modules
| |||||||||||||||
| 4784 | "C:\Users\admin\Desktop\UnlockRat By @DarKnetJoKer\天线远控.exe" | C:\Users\admin\Desktop\UnlockRat By @DarKnetJoKer\天线远控.exe | — | explorer.exe | |||||||||||
User: admin Company: 天线远控 - t.me/tianxian8 Integrity Level: MEDIUM Description: 天线远控 Exit code: 3221226540 Version: 5.0 Modules
| |||||||||||||||
| 4920 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\Desktop\UnlockRat By @DarKnetJoKer\天线远控.exe" | C:\Users\admin\Desktop\UnlockRat By @DarKnetJoKer\天线远控.exe | explorer.exe | ||||||||||||
User: admin Company: 天线远控 - t.me/tianxian8 Integrity Level: HIGH Description: 天线远控 Exit code: 0 Version: 5.0 Modules
| |||||||||||||||
| 5372 | "C:\Program Files\7-Zip\7zG.exe" x -o"C:\Users\admin\Desktop\*\" -spe -an -ai#7zMap29155:344:7zEvent4990 | C:\Program Files\7-Zip\7zG.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip GUI Exit code: 0 Version: 24.07 Modules
| |||||||||||||||
| 6316 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\7z.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 148
Read events
10 075
Write events
70
Delete events
3
Modification events
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {596AB062-B4D2-4215-9F74-E9109B0A8153} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000E46EBF2849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions |
| Operation: | write | Name: | HasFlushedShellExtCache |
Value: 1 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {4234D49B-0245-4DF3-B780-3893943456E1} {000214E6-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000FE3FD72849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {B41DB860-8EE4-11D2-9906-E49FADC173CA} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000632FDC2849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {F81E9010-6EA4-11CE-A7FF-00AA003CA9F6} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000C986E52849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {99D353BC-C813-41EC-8F28-EAE61E702E57} {A08CE4D0-FA25-44AB-B57C-C7B1C323E0B9} 0xFFFF |
Value: 010000000000000088EAE72849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {E2BF9676-5F8F-435C-97EB-11607A5BEDF7} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000FC79F12849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {E2BF9676-5F8F-435C-97EB-11607A5BEDF7} {A08CE4D0-FA25-44AB-B57C-C7B1C323E0B9} 0xFFFF |
Value: 0100000000000000FC79F12849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {470C0EBD-5D73-4D58-9CED-E91E22E23282} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000CC40F62849EBDA01 | |||
| (PID) Process: | (6612) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {1D27F844-3A1F-4410-85AC-14651078412D} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000CC40F62849EBDA01 | |||
Executable files
19
Suspicious files
37
Text files
554
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_96.db | binary | |
MD5:2A8875D2AF46255DB8324AAD9687D0B7 | SHA256:54097CCCAE0CFCE5608466BA5A5CA2A3DFEAC536964EEC532540F3B837F5A7C7 | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_32.db | binary | |
MD5:60476A101249AEDFF09A43E047040191 | SHA256:35BC77A06BFDDE8C8F3A474C88520262B88C7B8992EE6B2D5CF41DDDC77A83FB | |||
| 6612 | 7z.exe | C:\Windows\SysWOW64\._cache_7z.exe | executable | |
MD5:453821572A13CC6EA0736F9DB6424E13 | SHA256:B8C3871A5D6A473A2E9D08684A481AEA7467A97D0A433CF55B127323EF61218F | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_48.db | binary | |
MD5:AE6FBDED57F9F7D048B95468DDEE47CA | SHA256:D3C9D1FF7B54B653C6A1125CAC49F52070338A2DD271817BBA8853E99C0F33A9 | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_1280.db | binary | |
MD5:2DD3F3C33E7100EC0D4DBBCA9774B044 | SHA256:5A00CC998E0D0285B729964AFD20618CBAECFA7791FECDB843B535491A83AE21 | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_1920.db | binary | |
MD5:635E15CB045FF4CF0E6A31C827225767 | SHA256:67219E5AD98A31E8FA8593323CD2024C1CA54D65985D895E8830AE356C7BDF1D | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_256.db | binary | |
MD5:F6B463BE7B50F3CC5D911B76002A6B36 | SHA256:16E4D1B41517B48CE562349E3895013C6D6A0DF4FCFFC2DA752498E33C4D9078 | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_2560.db | binary | |
MD5:2D84AD5CFDF57BD4E3656BCFD9A864EA | SHA256:D241584A3FD4A91976FAFD5EC427E88F6E60998954DEC39E388AF88316AF3552 | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_idx.db | binary | |
MD5:EC358D5DB53AF875E847737A5C8AC74A | SHA256:699F113E9C978A3DCF1D576E69940AA1C7E0E3773E5440DF02283473F81049AC | |||
| 6612 | 7z.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\Explorer\iconcache_custom_stream.db | binary | |
MD5:F732BF1006B6529CFFBA2B9F50C4B07F | SHA256:77739084A27CB320F208AC1927D3D9C3CAC42748DBDF6229684EF18352D95067 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
48
DNS requests
20
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2456 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7068 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4708 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3028 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2456 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2456 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3 ETPRO signatures available at the full report