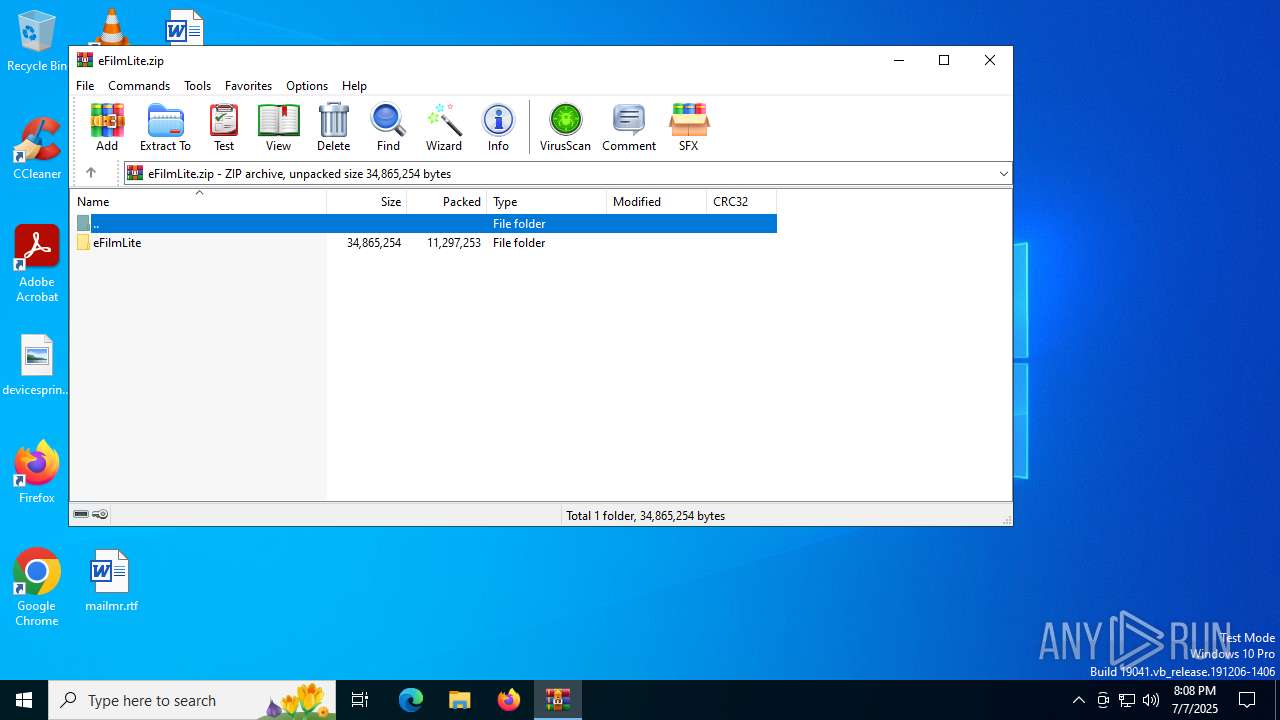
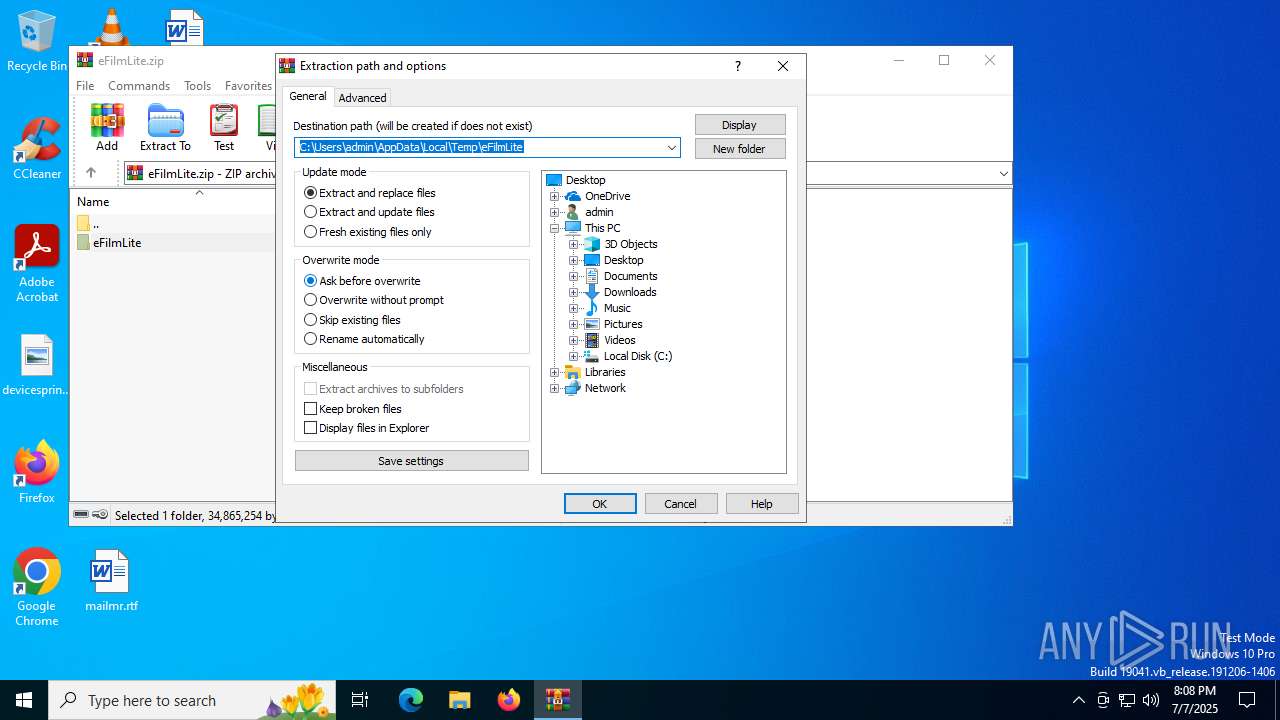
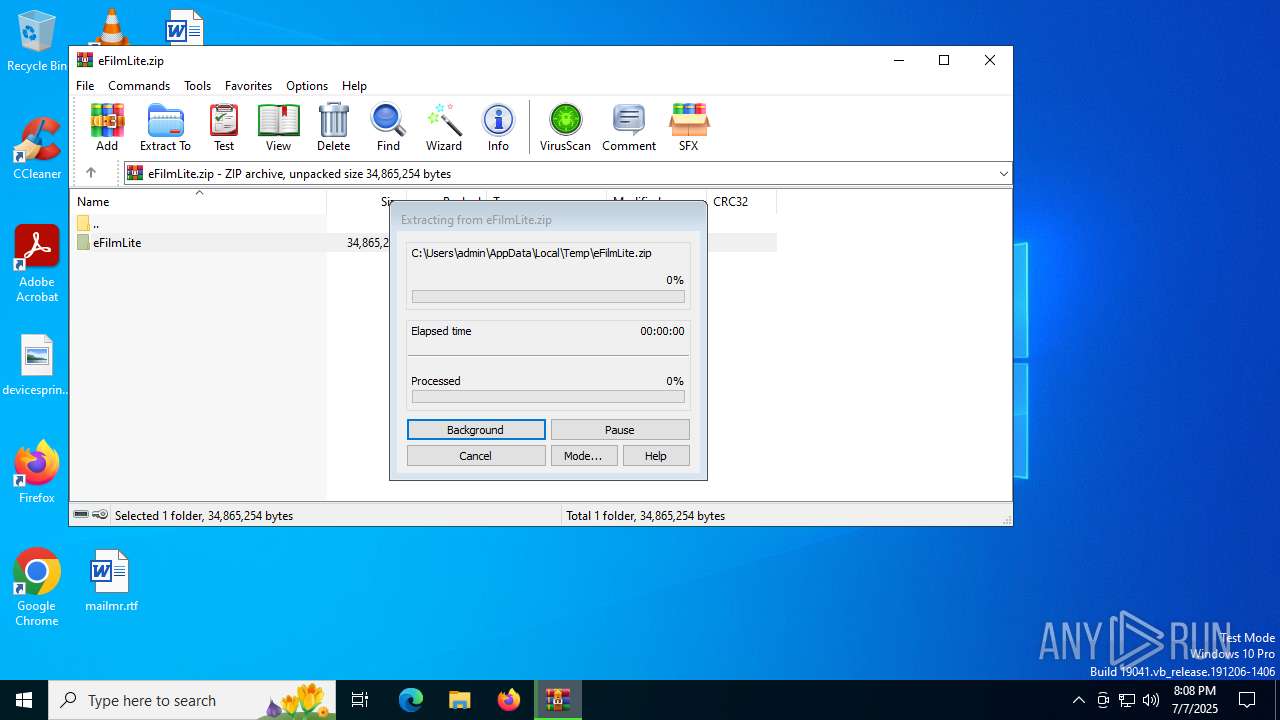
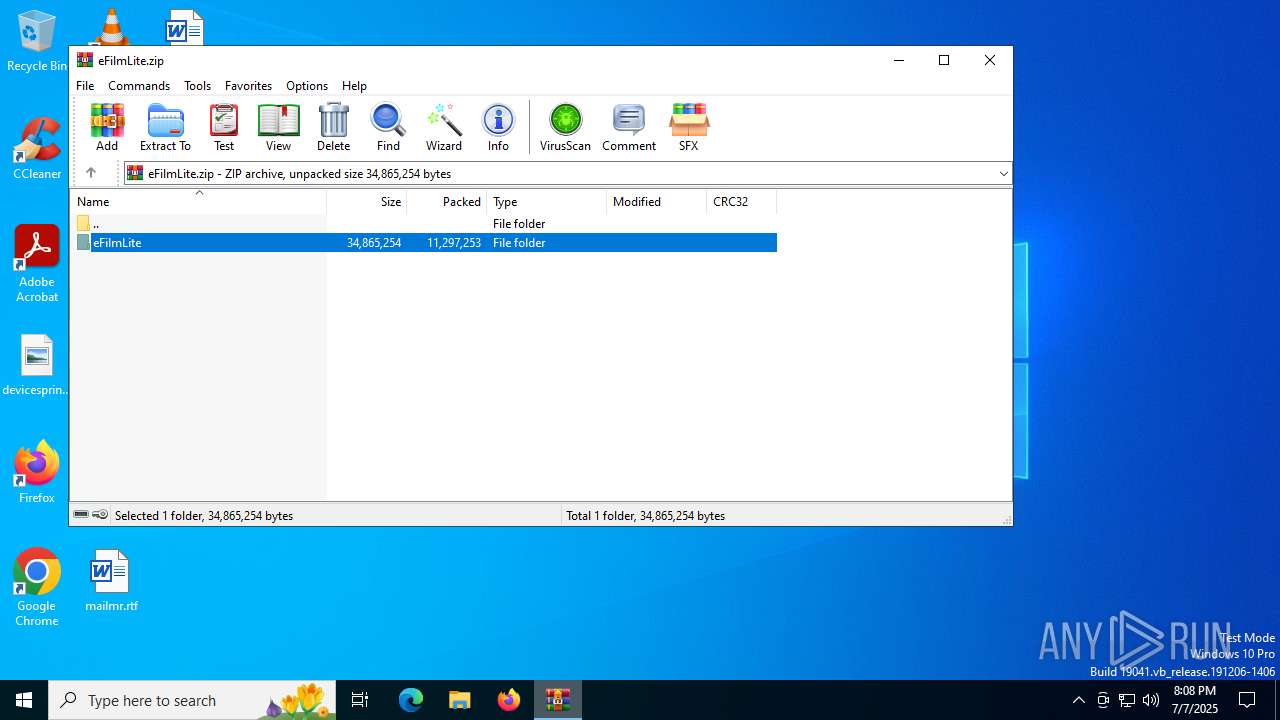
| File name: | eFilmLite.zip |
| Full analysis: | https://app.any.run/tasks/8c5a132e-e499-4aa0-aebb-bc15e440880c |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2025, 20:08:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 235831FA5D734E363CA3CB86CA21D762 |
| SHA1: | 57E9142943875EB8258A01D5927A64C5045A0EC4 |
| SHA256: | C6D3F920B20B8A617EFCE1EC4A4F3155A845D822AD147562978A5AFAD41A5BD3 |
| SSDEEP: | 98304:oK553Jverujz8xQgru8Xg3AkpuDqY/a/2ll0aBhl7k0uKNvU/YfuOfUXTnf14ljJ:SoFXM7hZuSfBwG1HHbUidsT0 |
MALICIOUS
Executing a file with an untrusted certificate
- eFilmLt.exe (PID: 1948)
- eFilmLt.exe (PID: 1812)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4788)
Reads security settings of Internet Explorer
- eFilmLt.exe (PID: 1812)
There is functionality for taking screenshot (YARA)
- eFilmLt.exe (PID: 1812)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4788)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4788)
Manual execution by a user
- eFilmLt.exe (PID: 1948)
- eFilmLt.exe (PID: 1812)
Checks supported languages
- eFilmLt.exe (PID: 1812)
Process checks computer location settings
- eFilmLt.exe (PID: 1812)
Reads the computer name
- eFilmLt.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:07:07 09:50:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | eFilmLite/1252/ |
Total processes
139
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1812 | "C:\Users\admin\Desktop\eFilmLite\eFilmLt.exe" | C:\Users\admin\Desktop\eFilmLite\eFilmLt.exe | explorer.exe | ||||||||||||
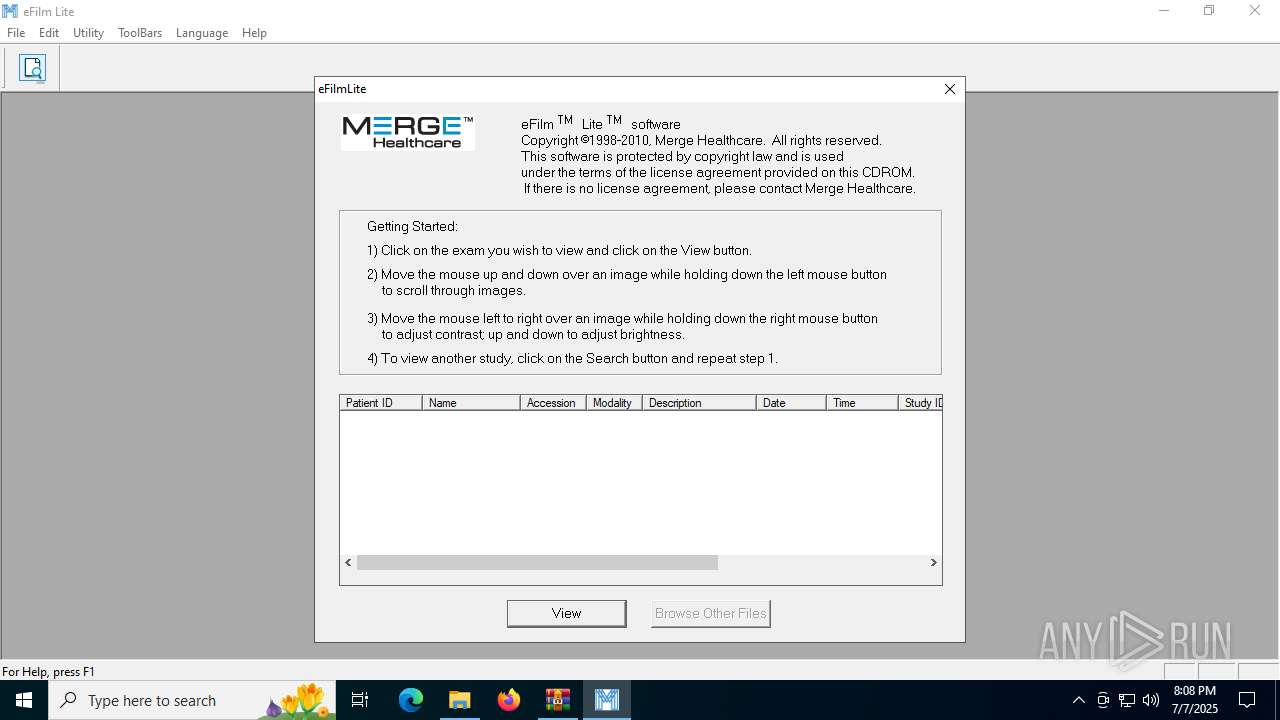
User: admin Company: Merge Healthcare Integrity Level: HIGH Description: eFilm Version: 3.4.0.10 Modules
| |||||||||||||||
| 1948 | "C:\Users\admin\Desktop\eFilmLite\eFilmLt.exe" | C:\Users\admin\Desktop\eFilmLite\eFilmLt.exe | — | explorer.exe | |||||||||||
User: admin Company: Merge Healthcare Integrity Level: MEDIUM Description: eFilm Exit code: 3221226540 Version: 3.4.0.10 Modules
| |||||||||||||||
| 4572 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\eFilmLite.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7152 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 505
Read events
5 479
Write events
13
Delete events
13
Modification events
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\eFilmLite.zip | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
64
Suspicious files
2
Text files
32
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\1252\Satellite_eFilm.dll | executable | |
MD5:6BB7C4AF27191214954B5099F51EAF75 | SHA256:4C0ED39A04361DDD99F4FE1DD6EF67FEB7CC92C5D6C5F646CB3F7937D17267D2 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\ColorOpacityPresetList.xml | xml | |
MD5:F51821A03FAFFCDD977D4226A73B832A | SHA256:3AA26E076F8C2D4DEB6CD74740AE6AB58DBA9526A7405917BE5BA80D11893923 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\2052\Satellite_eFilm.dll | executable | |
MD5:9FBAF1E7B77F1E8BB6DACFD30027DA5E | SHA256:F7C6299856E9D67D1E9DD80530C79D7D700F31022C277AF925FDDA3048FE5895 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\efCommon.dll | executable | |
MD5:981BA72A5562FBAED6EA069A7DA85376 | SHA256:F0FF159792251C7960CFF67DEFBB1009C9B1258B9751A9315AFEE3B02E01E531 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\dimpl8.dll | executable | |
MD5:EB9D12BAFF1122E346CD604112C999AF | SHA256:C215AA1B262B2B75695BCAA37261532989858C3AF105C5DBE584DA25F25621BC | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\efCmprss.dll | executable | |
MD5:D36D79EE1702959C6123BF13D4F88687 | SHA256:2991CBA45558F14ADCEB75ABB6F0228DC6A22A634A748C5D6AF105A9A618B2F1 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\efSheriffLocal.dll | executable | |
MD5:841DC8FDCF8162FD673FB995AFB80F6F | SHA256:DF2F2FA13228CFB7D45A2339B5B79C7E7F1077534C7189053B033802134D29CE | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\eFilmLt.exe | executable | |
MD5:E57821B90966F8F3AABB83FE78B23DE5 | SHA256:F75817BE6D91436DDCB7030C54CCCA245477AABA6DD751FC7CCFB62A44226287 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\efMC3DICOM.dll | executable | |
MD5:A85FFA4D3728B53D45158BA25DEE9CA4 | SHA256:9F08E46D30B9ACFC264F9F5226EC68F275B6FFBEBE6EE992435665F99AEF1765 | |||
| 4788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\eFilmLite\eFilmLite\efLUTMgr.dll | executable | |
MD5:B6450D5B49316C98779E6540FED1D80B | SHA256:AFC895D05D38EC303DB7EE788975004BAF36711B0BAFABCB4DCEB6AABD36E202 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1204 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2140 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2552 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2552 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |