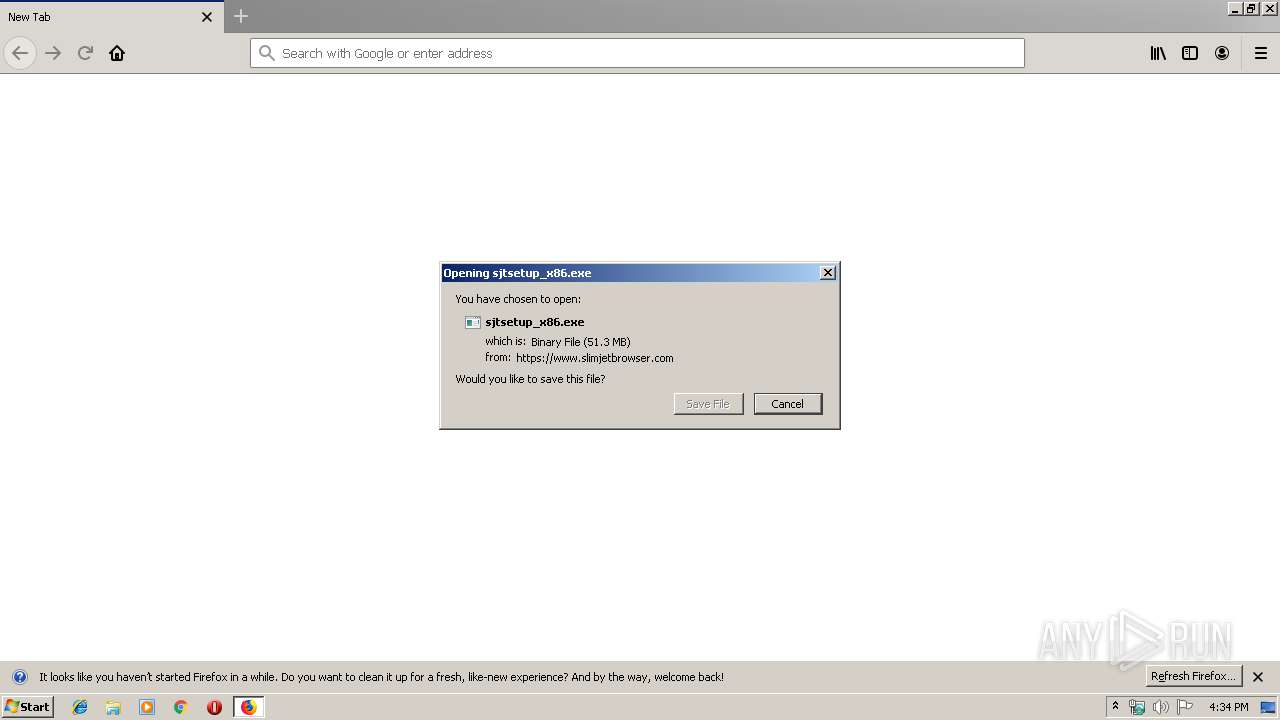
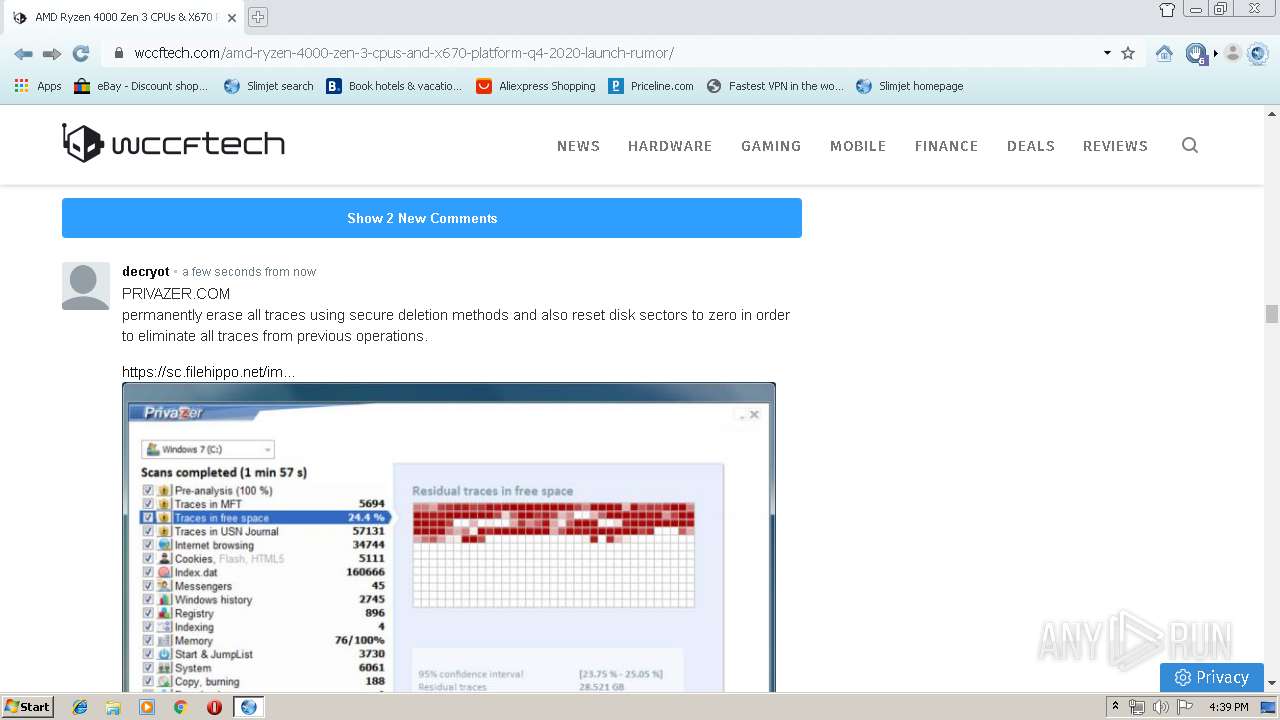
| URL: | https://www.slimjetbrowser.com/release/sjtsetup_x86.exe |
| Full analysis: | https://app.any.run/tasks/b75e9731-91f4-447d-86ee-238706aad2fa |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 16:34:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E91E2DB7F63DAE1B404C18C8F482E072 |
| SHA1: | E397CDC889E79227CDCD78FAD78EC0F0F6D8DD88 |
| SHA256: | C6B048696D61AF71EE9A0129597533C7BAA33EE6CEECF7CE7270DA91241E0B5A |
| SSDEEP: | 3:N8DSL0c3YyyKBr6ft:2OLGKBO |
MALICIOUS
Application was dropped or rewritten from another process
- sjtsetup_x86.exe (PID: 3924)
- ns5826.tmp (PID: 2860)
- sjtsetup_x86.exe (PID: 4000)
- slimjet.exe (PID: 3988)
- slimjet.exe (PID: 1516)
- slimjet.exe (PID: 2140)
- slimjet.exe (PID: 1776)
- slimjet.exe (PID: 4008)
- slimjet.exe (PID: 436)
- slimjet.exe (PID: 3576)
- slimjet.exe (PID: 1648)
- slimjet.exe (PID: 3632)
- slimjet.exe (PID: 1744)
- slimjet.exe (PID: 1484)
- slimjet.exe (PID: 2448)
- slimjet.exe (PID: 3520)
- slimjet.exe (PID: 3736)
- slimjet.exe (PID: 3892)
- slimjet.exe (PID: 2080)
- slimjet.exe (PID: 3116)
- slimjet.exe (PID: 3120)
- slimjet.exe (PID: 1244)
- slimjet.exe (PID: 3196)
- slimjet.exe (PID: 2116)
- slimjet.exe (PID: 3468)
- slimjet.exe (PID: 1876)
- slimjet.exe (PID: 736)
- slimjet.exe (PID: 1576)
- slimjet.exe (PID: 2400)
- slimjet.exe (PID: 2232)
- slimjet.exe (PID: 4072)
- slimjet.exe (PID: 3312)
- slimjet.exe (PID: 2796)
- slimjet.exe (PID: 3964)
- slimjet.exe (PID: 1504)
- slimjet.exe (PID: 892)
- slimjet.exe (PID: 3868)
- slimjet.exe (PID: 1216)
- slimjet.exe (PID: 2588)
- slimjet.exe (PID: 2336)
- slimjet.exe (PID: 4024)
- slimjet.exe (PID: 3796)
- slimjet.exe (PID: 2416)
- slimjet.exe (PID: 2436)
- slimjet.exe (PID: 3512)
- slimjet.exe (PID: 3292)
- slimjet.exe (PID: 2120)
- slimjet.exe (PID: 2308)
Loads dropped or rewritten executable
- sjtsetup_x86.exe (PID: 3924)
- slimjet.exe (PID: 4008)
- slimjet.exe (PID: 2140)
- slimjet.exe (PID: 3988)
- slimjet.exe (PID: 1776)
- slimjet.exe (PID: 3576)
- slimjet.exe (PID: 1516)
- slimjet.exe (PID: 436)
- slimjet.exe (PID: 1648)
- slimjet.exe (PID: 3632)
- slimjet.exe (PID: 1744)
- slimjet.exe (PID: 3892)
- slimjet.exe (PID: 3520)
- slimjet.exe (PID: 1484)
- slimjet.exe (PID: 2448)
- slimjet.exe (PID: 3736)
- slimjet.exe (PID: 2080)
- slimjet.exe (PID: 2116)
- slimjet.exe (PID: 3120)
- slimjet.exe (PID: 3116)
- slimjet.exe (PID: 3196)
- slimjet.exe (PID: 1244)
- slimjet.exe (PID: 3468)
- slimjet.exe (PID: 1876)
- slimjet.exe (PID: 2400)
- slimjet.exe (PID: 736)
- slimjet.exe (PID: 1576)
- slimjet.exe (PID: 2232)
- slimjet.exe (PID: 3312)
- slimjet.exe (PID: 3964)
- slimjet.exe (PID: 2796)
- slimjet.exe (PID: 1504)
- slimjet.exe (PID: 4072)
- slimjet.exe (PID: 3868)
- slimjet.exe (PID: 1216)
- slimjet.exe (PID: 892)
- slimjet.exe (PID: 2588)
- slimjet.exe (PID: 2336)
- slimjet.exe (PID: 4024)
- slimjet.exe (PID: 2120)
- slimjet.exe (PID: 3796)
- slimjet.exe (PID: 3292)
- slimjet.exe (PID: 2308)
- slimjet.exe (PID: 2416)
- slimjet.exe (PID: 2436)
- slimjet.exe (PID: 3512)
SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 3140)
- sjtsetup_x86.exe (PID: 3924)
- sjt7z_x86_console.exe (PID: 3016)
Creates files in the program directory
- firefox.exe (PID: 3140)
- sjtsetup_x86.exe (PID: 3924)
- sjt7z_x86_console.exe (PID: 3016)
Starts application with an unusual extension
- sjtsetup_x86.exe (PID: 3924)
Creates files in the user directory
- sjtsetup_x86.exe (PID: 3924)
Application launched itself
- slimjet.exe (PID: 4008)
- slimjet.exe (PID: 1776)
Modifies the open verb of a shell class
- slimjet.exe (PID: 4008)
Executed via COM
- explorer.exe (PID: 3168)
Creates a software uninstall entry
- sjtsetup_x86.exe (PID: 3924)
INFO
Application launched itself
- firefox.exe (PID: 3340)
- firefox.exe (PID: 3140)
Reads CPU info
- firefox.exe (PID: 3140)
Reads settings of System Certificates
- firefox.exe (PID: 3140)
Creates files in the user directory
- firefox.exe (PID: 3140)
Dropped object may contain Bitcoin addresses
- sjt7z_x86_console.exe (PID: 3016)
- slimjet.exe (PID: 1776)
Reads the hosts file
- slimjet.exe (PID: 4008)
- slimjet.exe (PID: 1776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
104
Monitored processes
58
Malicious processes
10
Suspicious processes
21
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files\Slimjet\slimjet.exe" --type=gpu-process --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --gpu-preferences=IAAAAAAAAADgAAAwAAAAAAAAYAAAAAAACAAAAAAAAAAoAAAABAAAACAAAAAAAAAAKAAAAAAAAAAwAAAAAAAAADgAAAAAAAAAEAAAAAAAAAAAAAAABQAAABAAAAAAAAAAAAAAAAYAAAAQAAAAAAAAAAEAAAAFAAAAEAAAAAAAAAABAAAABgAAAA== --service-request-channel-token=16185062514229571951 --mojo-platform-channel-handle=932 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 736 | "C:\Program Files\Slimjet\slimjet.exe" --type=utility --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --lang=en-US --no-sandbox --service-request-channel-token=3912432830619106854 --mojo-platform-channel-handle=3700 /prefetch:8 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: MEDIUM Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 820 | "C:\Windows\explorer.exe" "C:\Program Files\Slimjet\slimjet.exe" | C:\Windows\explorer.exe | — | sjtsetup_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | "C:\Program Files\Slimjet\slimjet.exe" --type=utility --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --lang=en-US --no-sandbox --service-request-channel-token=2070800848452054307 --mojo-platform-channel-handle=5032 /prefetch:8 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: MEDIUM Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Slimjet\slimjet.exe" --type=renderer --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --disable-gpu-compositing --lang=en-US --enable-auto-reload --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17779275881610895784 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4468 /prefetch:1 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Slimjet\slimjet.exe" --type=utility --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7345680047283312218 --mojo-platform-channel-handle=4104 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Slimjet\slimjet.exe" --type=renderer --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --lang=en-US --extension-process --enable-auto-reload --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3704461873644171601 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2732 /prefetch:1 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Slimjet\slimjet.exe" --type=renderer --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --disable-gpu-compositing --lang=en-US --enable-auto-reload --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11436757199162408987 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4580 /prefetch:1 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Slimjet\slimjet.exe" --type=crashpad-handler --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Slimjet\User Data" /prefetch:7 --monitor-self --monitor-self-argument=--type=crashpad-handler --monitor-self-argument=--type=crashpad-handler "--monitor-self-argument=--user-data-dir=C:\Users\admin\AppData\Local\Slimjet\User Data" --monitor-self-argument=/prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Slimjet\User Data\Crash Reports" "--metrics-dir=C:\Users\admin\AppData\Local\Slimjet\User Data" --annotation=plat=Win32 --annotation=prod=Slimjet --annotation=ver=24.0.6.0 --initial-client-data=0x30,0x34,0x38,0x2c,0x3c,0x6e0beaf8,0x6e0beb08,0x6e0beb14 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: MEDIUM Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Slimjet\slimjet.exe" --type=utility --field-trial-handle=920,5613996580707881192,1287565917702557277,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8992180267049290226 --mojo-platform-channel-handle=4740 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Slimjet\slimjet.exe | — | slimjet.exe | |||||||||||
User: admin Company: FlashPeak Inc. Integrity Level: LOW Description: FlashPeak Slimjet Exit code: 0 Version: 24.0.6.0 Modules
| |||||||||||||||
Total events
2 072
Read events
1 571
Write events
494
Delete events
7
Modification events
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 2E4C5F1803000000 | |||
| (PID) Process: | (3340) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: E81B581803000000 | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (3140) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
Executable files
23
Suspicious files
191
Text files
711
Unknown types
131
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\doomed\8727 | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_UpwRmQEMRJdQgcd | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
127
DNS requests
124
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3924 | sjtsetup_x86.exe | GET | — | 50.62.135.162:80 | http://www.slimjet.com/getcountry.php | US | — | — | suspicious |
3140 | firefox.exe | POST | 200 | 172.217.18.163:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3140 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1776 | slimjet.exe | GET | 301 | 50.62.135.162:80 | http://www.slimjet.com/bing_search_api.php?id=5b318f6f-255d-4dd9-b49c-a4d0b002f8b1 | US | html | 291 b | suspicious |
1776 | slimjet.exe | GET | 302 | 172.217.22.46:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 513 b | whitelisted |
1776 | slimjet.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
1776 | slimjet.exe | GET | 200 | 173.194.184.43:80 | http://r5---sn-p5qs7nes.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=85.203.20.94&mm=28&mn=sn-p5qs7nes&ms=nvh&mt=1575304584&mv=m&mvi=4&pl=25&shardbypass=yes | US | crx | 816 Kb | whitelisted |
1776 | slimjet.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEChOOcFLOG2InHKZ5YzQWlc%3D | US | der | 727 b | whitelisted |
3140 | firefox.exe | POST | 200 | 172.217.18.163:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
1776 | slimjet.exe | GET | 200 | 104.31.67.198:80 | http://www.slimjetbrowser.com/version.txt | US | text | 102 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3140 | firefox.exe | 52.89.218.39:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3140 | firefox.exe | 52.222.158.66:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
3140 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3140 | firefox.exe | 54.149.210.11:443 | push.services.mozilla.com | Amazon.com, Inc. | US | malicious |
3140 | firefox.exe | 54.186.225.209:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3140 | firefox.exe | 143.204.214.76:443 | content-signature-2.cdn.mozilla.net | — | US | suspicious |
3140 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3140 | firefox.exe | 2.16.186.50:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3140 | firefox.exe | 13.35.253.117:443 | firefox.settings.services.mozilla.com | — | US | suspicious |
3140 | firefox.exe | 172.217.16.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
d228z91au11ukj.cloudfront.net |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
6 ETPRO signatures available at the full report