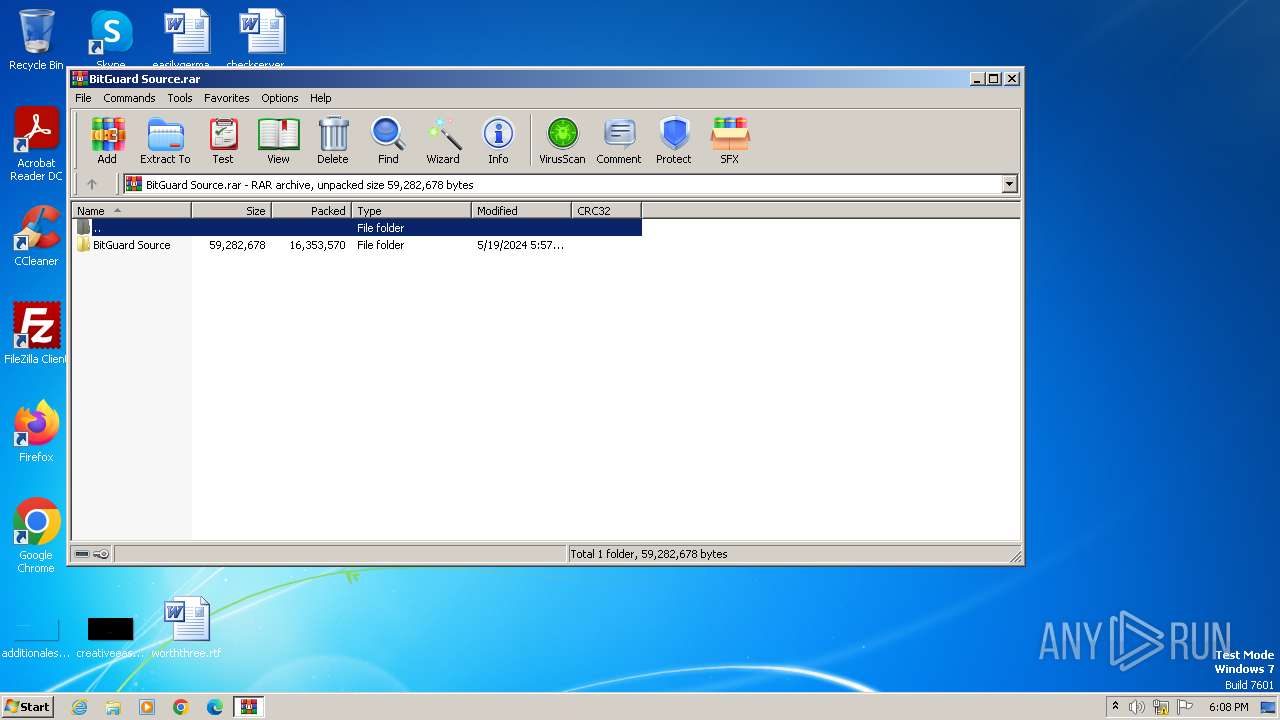
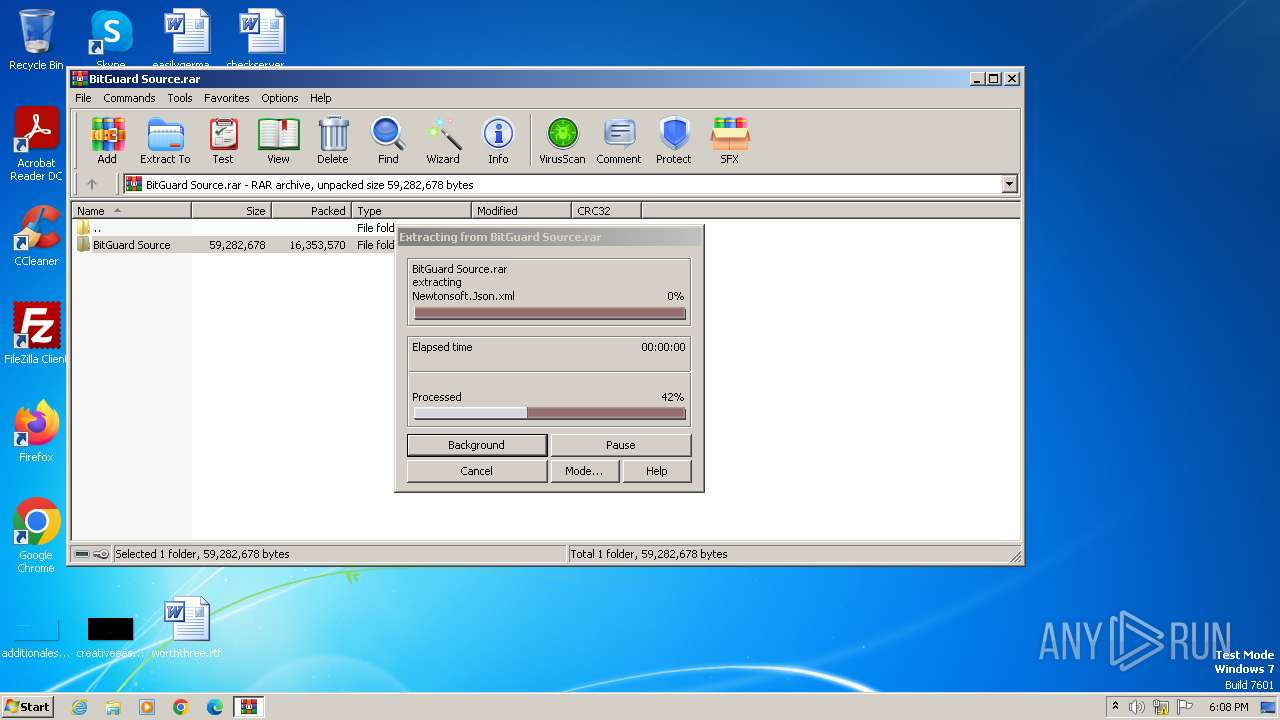
| File name: | BitGuard Source.rar |
| Full analysis: | https://app.any.run/tasks/01fdc987-a02e-47c5-a68f-3593e19b4e86 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2024, 17:08:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A238A45EC5F2FA04A850370B00EAB14D |
| SHA1: | 918A94A190E440113758DCA7228013B22FCB2E61 |
| SHA256: | C6975D7A512D22CE2619E50F25EAC9E4C24BC88A2E2880EE44374FA157F904F1 |
| SSDEEP: | 98304:85aIPrqumUMBjgXXNHDGjyQ6tT7tZkBp5avtqQf5Y+BPZuFGJ73tKwkG8Zl+fNgo:cc4hAVZ8GBgn8/Vu+zggFPwTFdG+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3992)
Reads the Internet Settings
- BitGuardUI.exe (PID: 1944)
Reads settings of System Certificates
- BitGuardUI.exe (PID: 1944)
INFO
Manual execution by a user
- BitGuardUI.exe (PID: 1944)
- wmpnscfg.exe (PID: 824)
- YeetFuscatorEpicUI.exe (PID: 2592)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3992)
Reads Environment values
- BitGuardUI.exe (PID: 1944)
Reads the machine GUID from the registry
- BitGuardUI.exe (PID: 1944)
- YeetFuscatorEpicUI.exe (PID: 2592)
Disables trace logs
- BitGuardUI.exe (PID: 1944)
Reads the computer name
- BitGuardUI.exe (PID: 1944)
- wmpnscfg.exe (PID: 824)
- YeetFuscatorEpicUI.exe (PID: 2592)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3992)
Reads the software policy settings
- BitGuardUI.exe (PID: 1944)
Checks supported languages
- BitGuardUI.exe (PID: 1944)
- wmpnscfg.exe (PID: 824)
- YeetFuscatorEpicUI.exe (PID: 2592)
Create files in a temporary directory
- BitGuardUI.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 824 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
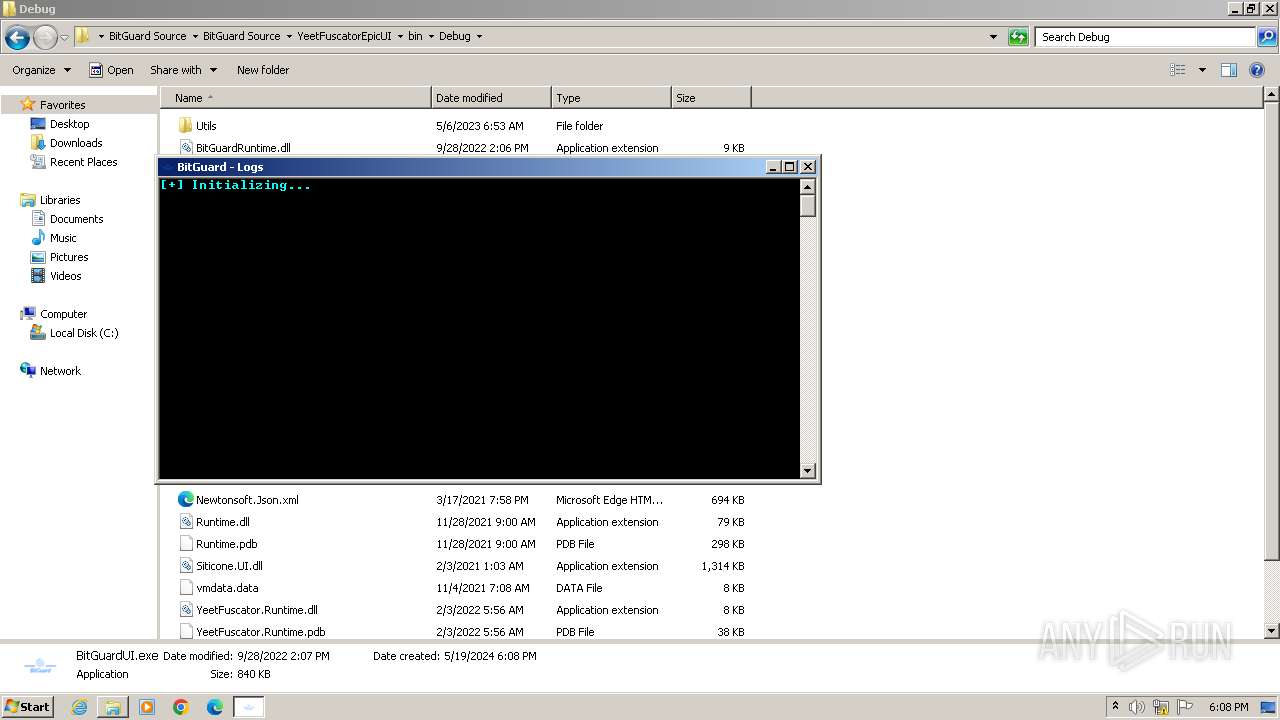
| 1944 | "C:\Users\admin\Desktop\BitGuard Source\BitGuard Source\YeetFuscatorEpicUI\bin\Debug\BitGuardUI.exe" | C:\Users\admin\Desktop\BitGuard Source\BitGuard Source\YeetFuscatorEpicUI\bin\Debug\BitGuardUI.exe | explorer.exe | ||||||||||||
User: admin Company: Yeetret Integrity Level: MEDIUM Description: BitGuard Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
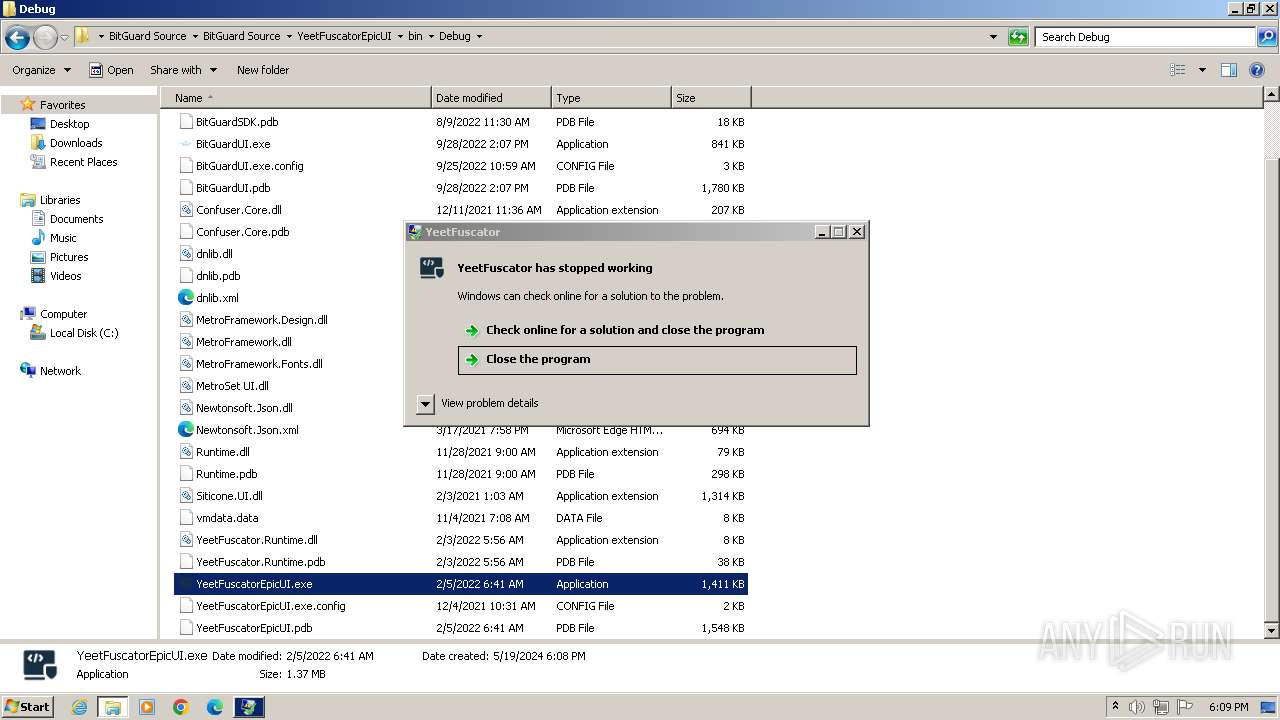
| 2592 | "C:\Users\admin\Desktop\BitGuard Source\BitGuard Source\YeetFuscatorEpicUI\bin\Debug\YeetFuscatorEpicUI.exe" | C:\Users\admin\Desktop\BitGuard Source\BitGuard Source\YeetFuscatorEpicUI\bin\Debug\YeetFuscatorEpicUI.exe | explorer.exe | ||||||||||||
User: admin Company: Yeetret Integrity Level: MEDIUM Description: YeetFuscator Exit code: 3762504530 Version: 4.0.0.0 Modules
| |||||||||||||||
| 3992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\BitGuard Source.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 744
Read events
8 696
Write events
48
Delete events
0
Modification events
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BitGuard Source.rar | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
70
Suspicious files
58
Text files
371
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\Dependencies\dnlib.dll | executable | |
MD5:34E6D4964DF3294B85849FBC44140731 | SHA256:49A32696E2FA95CFD50660D12CC59B9BFA9C58AD624195B18FC78A48DD794683 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\bin\Release\Runtime.dll | executable | |
MD5:61073D3F5861F017709AE8C3F17D30C0 | SHA256:27525D7B1B8207DFE0022733DE3B4A6190F0C4D9A42392A6CE1B4F00CF1698AE | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\BitGuard.sln | text | |
MD5:6CA7AF37829BFF6B6AC5CF714462DFF2 | SHA256:9CB28B83BDE21E11072CFCC64680DA6B981E64A9C9EA41BB42CC3482EA395878 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\.vs\BitGuard\v17\.suo | binary | |
MD5:4AF608F1DFA88F8301B800FE361AE7BB | SHA256:0237FB96B227DF12AF5E2625EC6834BAFC806E96CCC0C23E85386837649F414F | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\Dependencies\Confuser.Core.dll | executable | |
MD5:D76FFCE9EF3B5C3BB0BAD7F738FF6D5A | SHA256:3B2F8505A2765909AA0AE9D00BBDA0AAF9BFF56C3335A42FAE54CDDC6813C6E8 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\Dependencies\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\.vs\BitGuard\FileContentIndex\8b2c7fab-9810-4e0d-88b5-171cedddded8.vsidx | binary | |
MD5:CE2C0AF0FB9D4E6E56DAFCD20C171E7F | SHA256:89FD1550ACB423AF46F5BB22641E706F1D7569B305B8202AA6C36D571C4FA910 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\packages\dnlib.3.1.0\lib\net461\dnlib.pdb | binary | |
MD5:21C60A87ACE4343CFA8F62253B6A3D15 | SHA256:D4AC3C2A2EDCA85A82CF31ADD585521F4BD1A07DD2304BBFFD759B42481E1B48 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\packages\dnlib.3.1.0\dnlib.3.1.0.nupkg | compressed | |
MD5:A48F4AB1B704964CBFEEE2F882E3718C | SHA256:9EA763C9D9C8CE1346F0AC5D9C9E371CC19C4FE411044A07E5C3293E4DFE9A60 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3992.30853\BitGuard Source\BitGuard Source\packages\dnlib.3.1.0\.signature.p7s | binary | |
MD5:4EE69DAA480DC4E6A962B066FB4B3F34 | SHA256:9CB022467F7CC87569945B8600017CED6205D03CDDB244F4036A43BF083B54DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | BitGuardUI.exe | GET | 200 | 92.123.133.34:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4bb8e789d886b072 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1944 | BitGuardUI.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | unknown |
1944 | BitGuardUI.exe | 92.123.133.34:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keyauth.win |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain in DNS Lookup (keyauth .win) |
1944 | BitGuardUI.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |