| File name: | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe |
| Full analysis: | https://app.any.run/tasks/9bd44f37-0886-4926-a46e-a29b61f89d1b |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2024, 03:51:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 46CE83FD31D1B64C184E4307862DBC11 |
| SHA1: | B5937BC379C27A4C48D2C34D542AFBD2DA71BF59 |
| SHA256: | C6931330AC5B1674F9B2C3691F2C061B51066839622A49A97F4608A3959E1767 |
| SSDEEP: | 98304:Ssi3qWmzqqmJl1VaEvgyPCCZ8QN9zMxjQs5dFdroIuBo5zOB+Cm86JM3XmuuSaCA:NalIVXRTj |
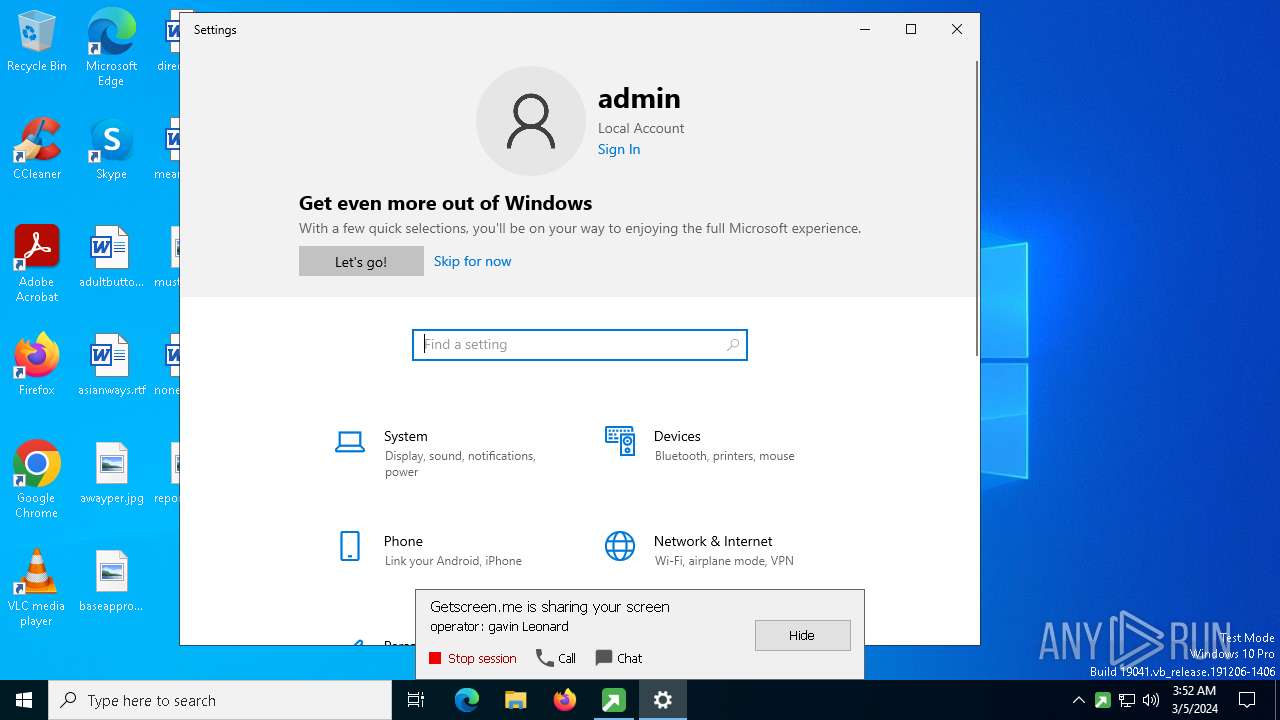
MALICIOUS
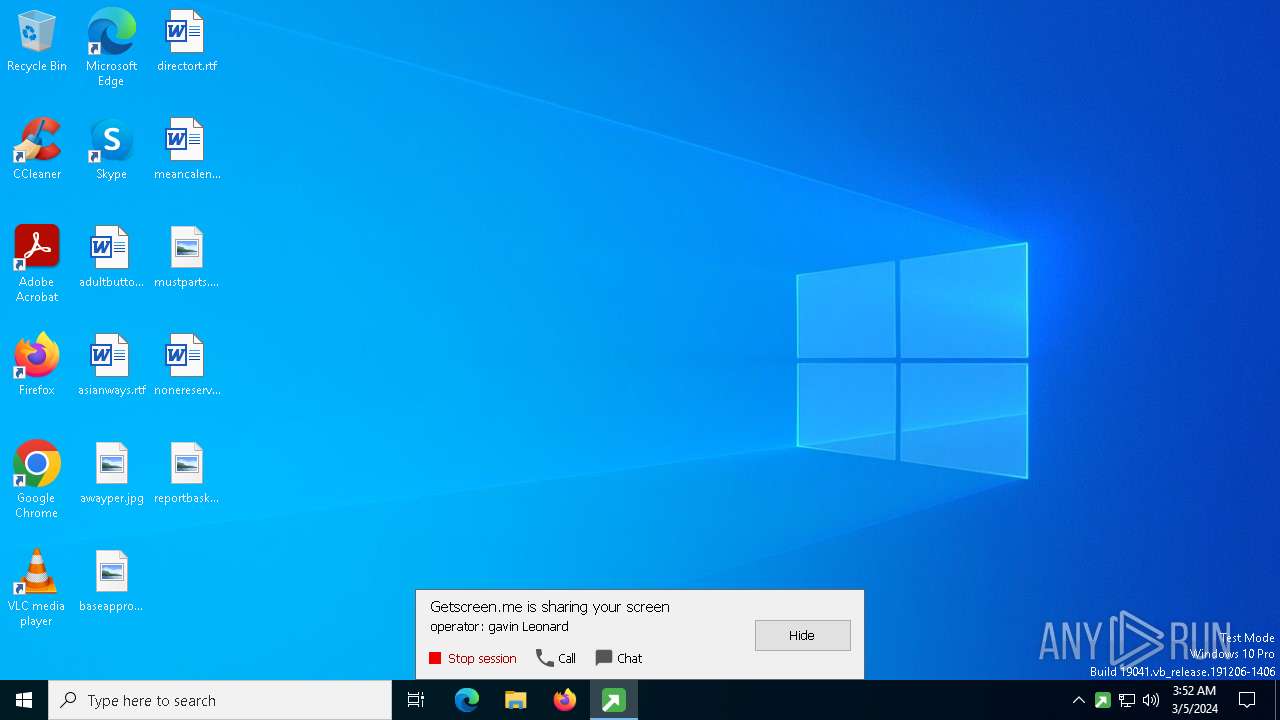
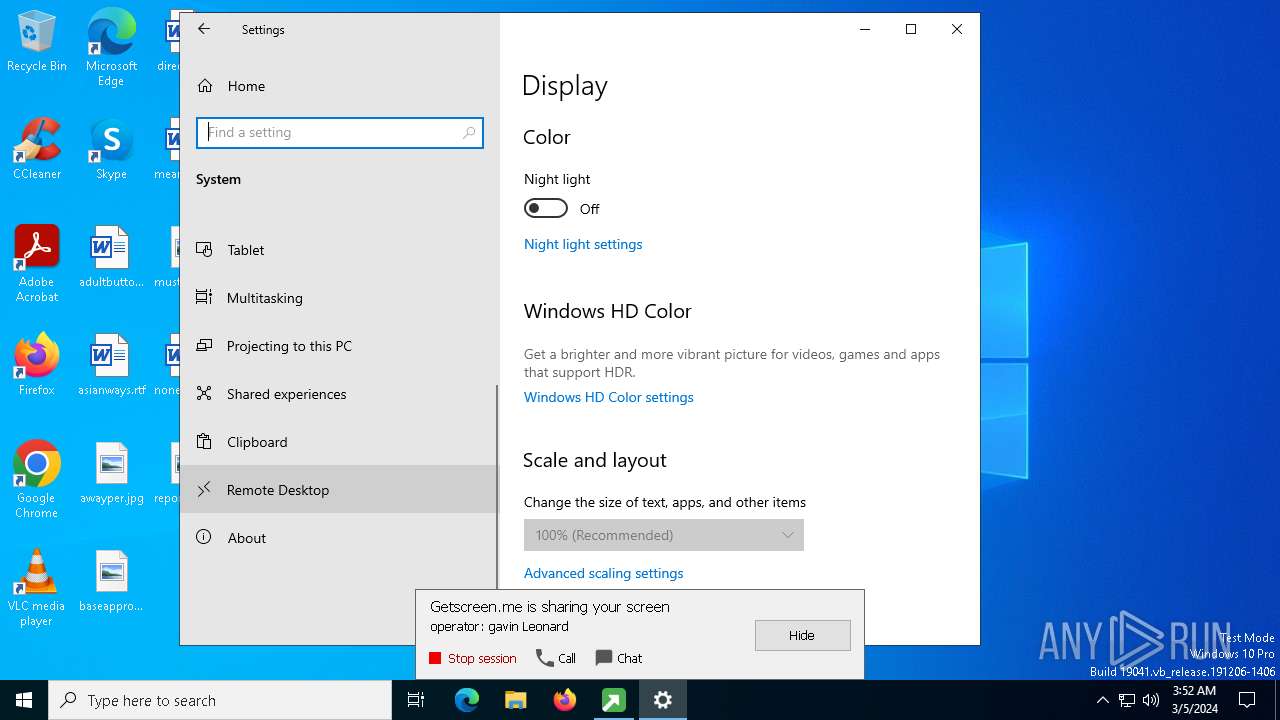
Drops the executable file immediately after the start
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
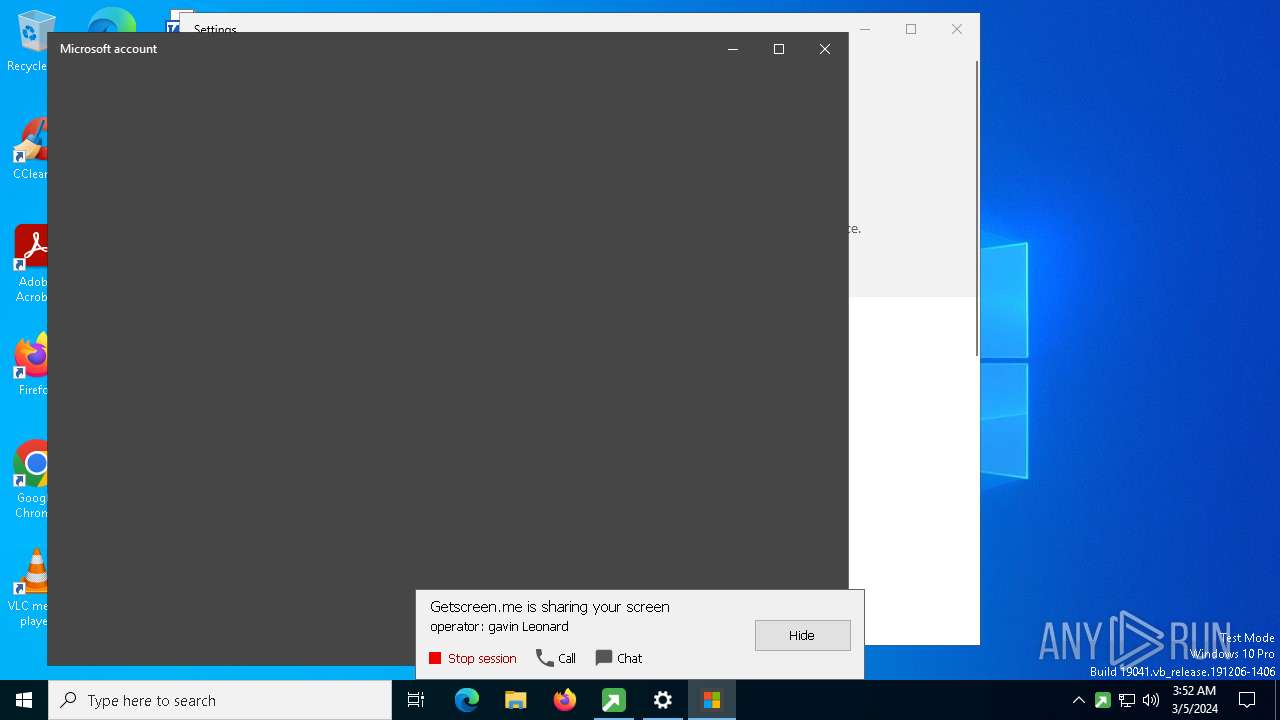
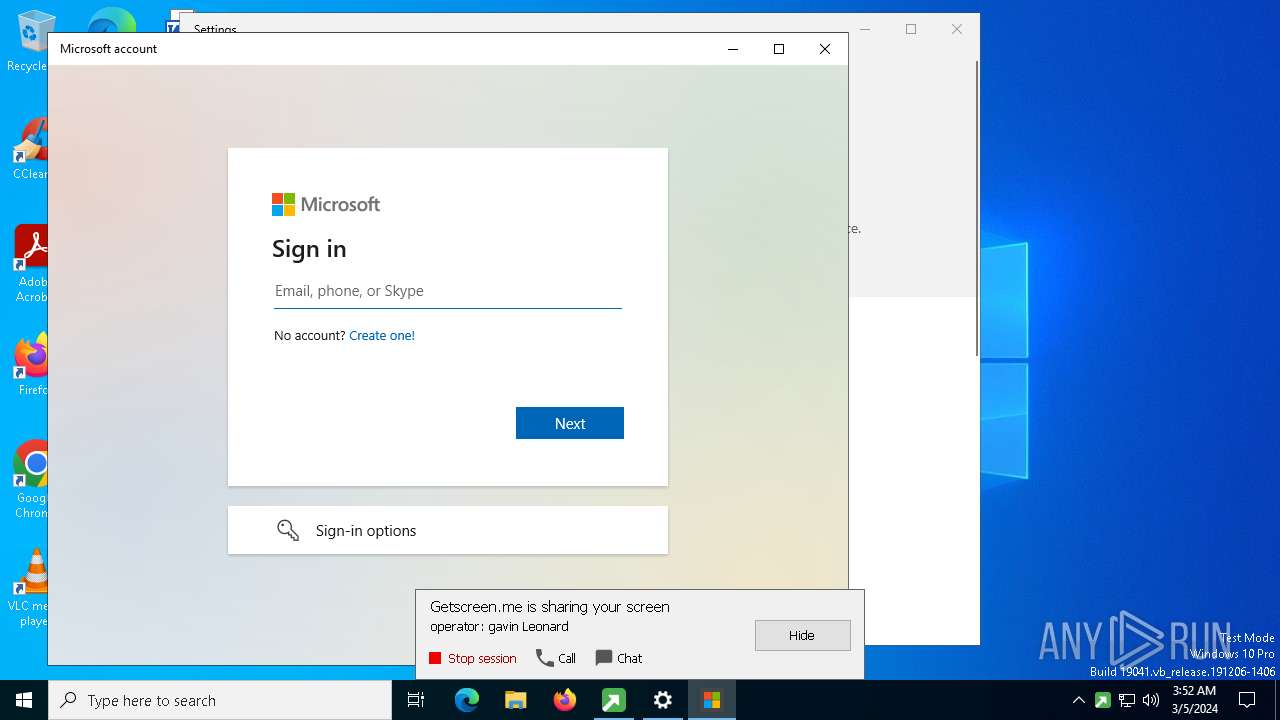
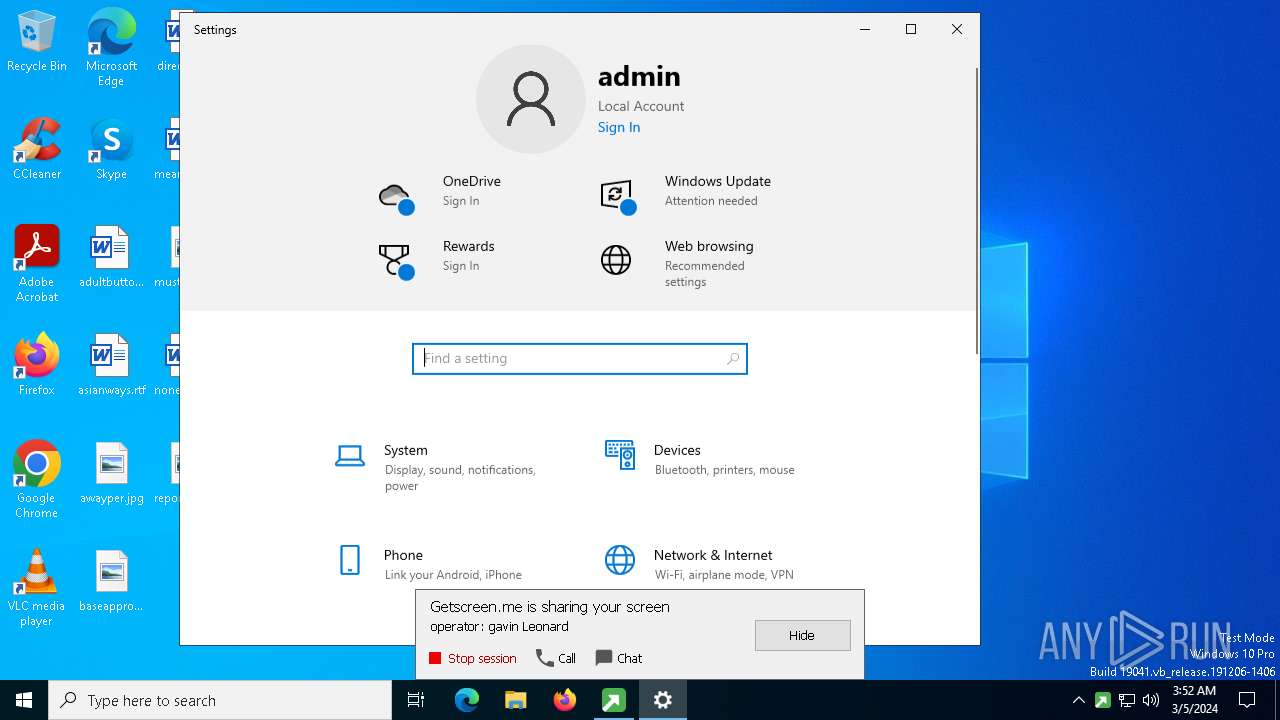
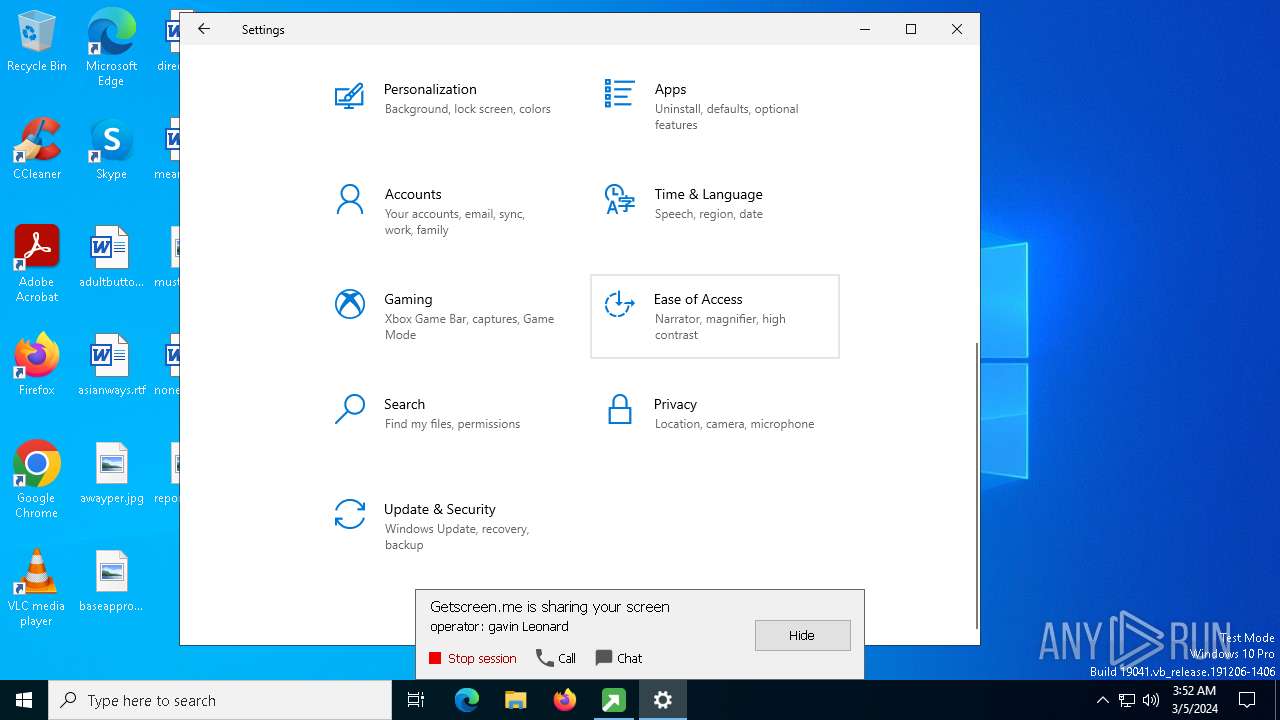
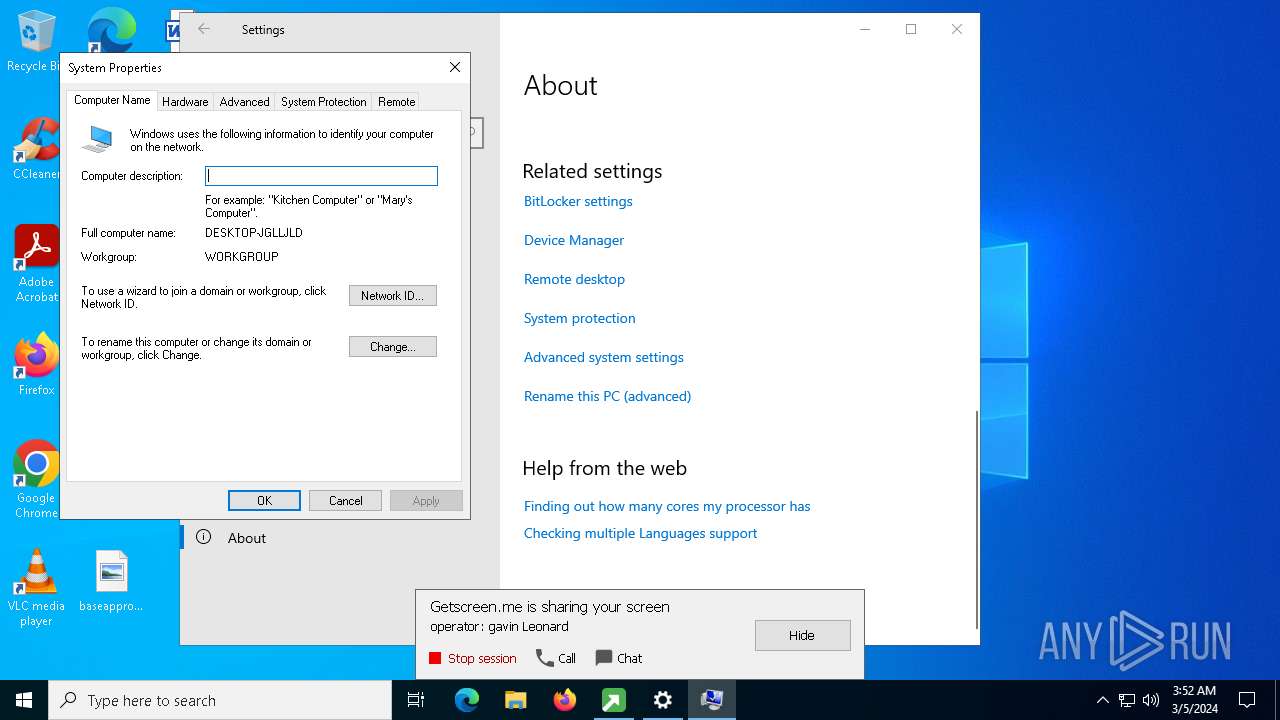
GETMESCREEN has been detected (SURICATA)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
SUSPICIOUS
Reads the date of Windows installation
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
Reads security settings of Internet Explorer
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
Application launched itself
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
Changes Internet Explorer settings (feature browser emulation)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5296)
Executable content was dropped or overwritten
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
Executes as Windows Service
- jfygsjxzleqyshllfljmdpsktgilorp-elevate.exe (PID: 5788)
Connects to unusual port
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
INFO
Checks supported languages
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5296)
- jfygsjxzleqyshllfljmdpsktgilorp-elevate.exe (PID: 5788)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 6660)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 2888)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4496)
Process checks computer location settings
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
Creates files or folders in the user directory
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
- WWAHost.exe (PID: 2196)
Creates files in the program directory
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
Reads the computer name
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5296)
- jfygsjxzleqyshllfljmdpsktgilorp-elevate.exe (PID: 5788)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 6660)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4496)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 2888)
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 4420)
Reads mouse settings
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 2888)
Checks proxy server information
- c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe (PID: 5332)
- WWAHost.exe (PID: 2196)
- slui.exe (PID: 2128)
Reads the software policy settings
- WWAHost.exe (PID: 2196)
- slui.exe (PID: 2128)
Reads security settings of Internet Explorer
- WWAHost.exe (PID: 2196)
Application launched itself
- chrome.exe (PID: 1556)
Manual execution by a user
- chrome.exe (PID: 1556)
Reads Microsoft Office registry keys
- chrome.exe (PID: 1556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:01 07:59:26+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.36 |
| CodeSize: | 4235264 |
| InitializedDataSize: | 20480 |
| UninitializedDataSize: | 21577728 |
| EntryPoint: | 0x189e680 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.18.1.0 |
| ProductVersionNumber: | 2.18.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| CompanyName: | Getscreen.me |
| InternalName: | Getscreen.me |
| OriginalFileName: | getscreen.exe |
| ProductName: | Getscreen.me |
| FileVersion: | 2.18.1 |
| LegalCopyright: | Copyright (C) 2023 |
| ProductVersion: | 2.18.1 |
Total processes
177
Monitored processes
27
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=112.0.5615.50 --initial-client-data=0x100,0x104,0x108,0xfc,0x10c,0x7ff89605aa60,0x7ff89605aa70,0x7ff89605aa80 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4872 --field-trial-handle=1920,i,9645818428824889520,13016201756516363829,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2128 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2092 --field-trial-handle=1920,i,9645818428824889520,13016201756516363829,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2196 | "C:\WINDOWS\system32\wwahost.exe" -ServerName:App.wwa | C:\Windows\System32\WWAHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft WWA Host Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4400 --field-trial-handle=1920,i,9645818428824889520,13016201756516363829,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\AppData\Local\Temp\c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe" -cpipe \\.\pipe\PCommand96yzkwsyuchnmtbnq -child | C:\Users\admin\AppData\Local\Temp\c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | ||||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 0 Version: 2.18.1 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4828 --field-trial-handle=1920,i,9645818428824889520,13016201756516363829,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
Total events
17 171
Read events
17 081
Write events
78
Delete events
12
Modification events
| (PID) Process: | (4420) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4420) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4420) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4420) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5332) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\36\52C64B7E |
| Operation: | write | Name: | @%systemroot%\system32\FirewallControlPanel.dll,-12122 |
Value: Windows Defender Firewall | |||
| (PID) Process: | (5296) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe |
Value: 11001 | |||
| (PID) Process: | (5296) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe |
Value: 11001 | |||
| (PID) Process: | (5296) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\getscreen.me |
| Operation: | write | Name: | http |
Value: 2 | |||
| (PID) Process: | (5296) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\getscreen.me |
| Operation: | write | Name: | https |
Value: 2 | |||
| (PID) Process: | (5296) c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\EscDomains\getscreen.me |
| Operation: | write | Name: | http |
Value: 2 | |||
Executable files
1
Suspicious files
129
Text files
87
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | C:\ProgramData\Getscreen.me\memory\0000pipe0PCommand96yzkwsyuchnmtbnq0 | — | |
MD5:— | SHA256:— | |||
| 5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | C:\ProgramData\Getscreen.me\memory\6FBC8D83AD6EDA010CFED87CB06EDA01D4140000FFFFFFFF | — | |
MD5:— | SHA256:— | |||
| 2196 | WWAHost.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windows.cloudexperiencehost_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\LS7D5GPM\microsoft.windows[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | C:\ProgramData\Getscreen.me\folder\settings.dat | binary | |
MD5:5F5D66467C9C30E1B45189F314FF1341 | SHA256:A4E119198F47952AA3F328E3D4110A08CD3B62F289F09B49C84CC22CF15A8422 | |||
| 2196 | WWAHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.CloudExperienceHost_cw5n1h2txyewy\LocalState\_sessionState.json~RF13ea15.TMP | — | |
MD5:— | SHA256:— | |||
| 5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | C:\Users\admin\AppData\Local\Getscreen.me\folder\settings.dat | binary | |
MD5:5F5D66467C9C30E1B45189F314FF1341 | SHA256:A4E119198F47952AA3F328E3D4110A08CD3B62F289F09B49C84CC22CF15A8422 | |||
| 5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | C:\ProgramData\Getscreen.me\jfygsjxzleqyshllfljmdpsktgilorp-elevate.exe | executable | |
MD5:46CE83FD31D1B64C184E4307862DBC11 | SHA256:C6931330AC5B1674F9B2C3691F2C061B51066839622A49A97F4608A3959E1767 | |||
| 2196 | WWAHost.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windows.cloudexperiencehost_cw5n1h2txyewy\AC\INetCache\GJHHWLZS\Converged_v21033_mG-wAdV--_sq1kXms675SA2[1].css | text | |
MD5:986FB001D57EFBFB2AD645E6B3AEF948 | SHA256:DE304CB4D64E769DD16A7B4500603205D2606FE0877DD046460C7B8DF06A31B3 | |||
| 2196 | WWAHost.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windows.cloudexperiencehost_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\CCTJ07GC\login.live[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 2196 | WWAHost.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windows.cloudexperiencehost_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:087C973EE582BD54DC1F633E1392277A | SHA256:313EDF9F05C9069903ED0F3D07C1157B12C6C79DE9A9FD31011983AAEB31A915 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
135
DNS requests
58
Threats
418
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
4072 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
1248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
1608 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
5184 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
5184 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
5184 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2196 | WWAHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2196 | WWAHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
2188 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | binary | 242 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4072 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6896 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5928 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | 78.47.165.25:443 | getscreen.me | Hetzner Online GmbH | DE | unknown |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | 45.65.9.108:3478 | px-us1.getscreen.me | — | — | unknown |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | 95.85.71.16:3478 | px-in1.getscreen.me | — | — | unknown |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | 162.55.165.163:3478 | px-eu1.getscreen.me | — | — | unknown |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | 5.188.225.23:3478 | px-br1.getscreen.me | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
getscreen.me |
| unknown |
image.getscreen.me |
| unknown |
ocsp.digicert.com |
| whitelisted |
px-us1.getscreen.me |
| unknown |
px-br1.getscreen.me |
| unknown |
px-eu1.getscreen.me |
| unknown |
px-au1.getscreen.me |
| unknown |
px-il1.getscreen.me |
| unknown |
px-us2.getscreen.me |
| unknown |
px-in1.getscreen.me |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desctop Software (TURN) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
5332 | c6931330ac5b1674f9b2c3691f2c061b51066839622a49a97f4608a3959e1767.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |