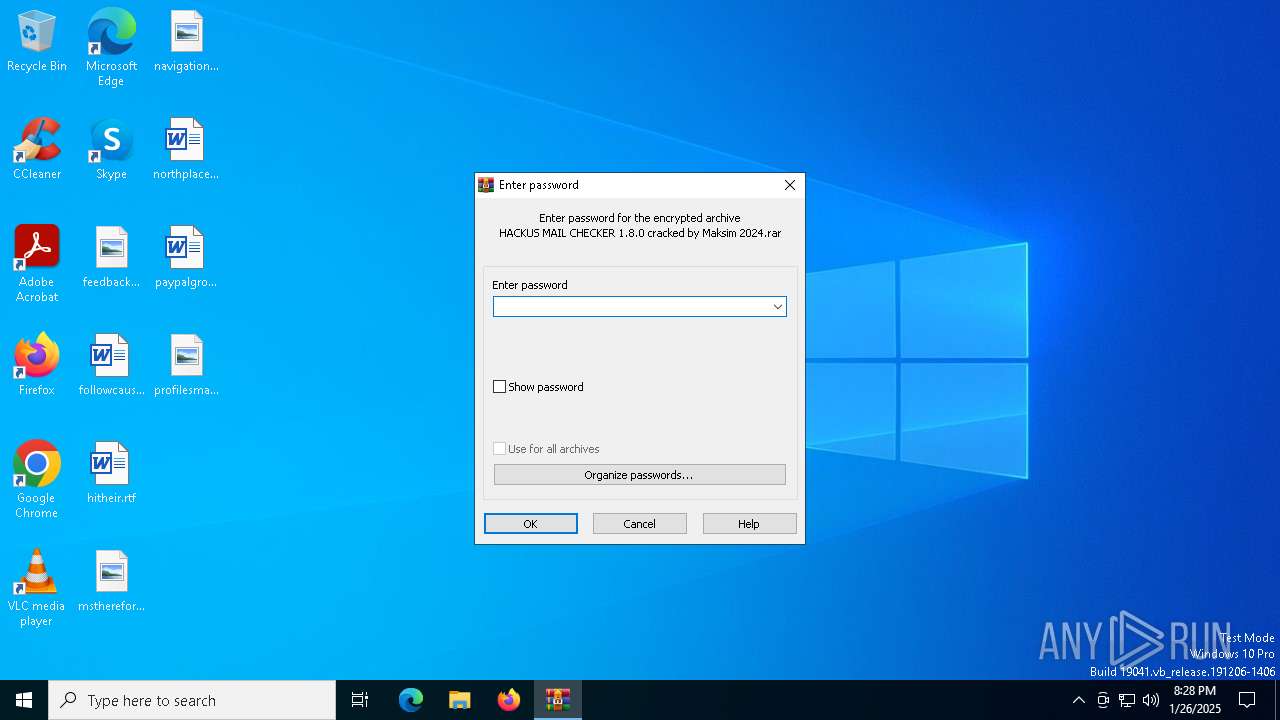
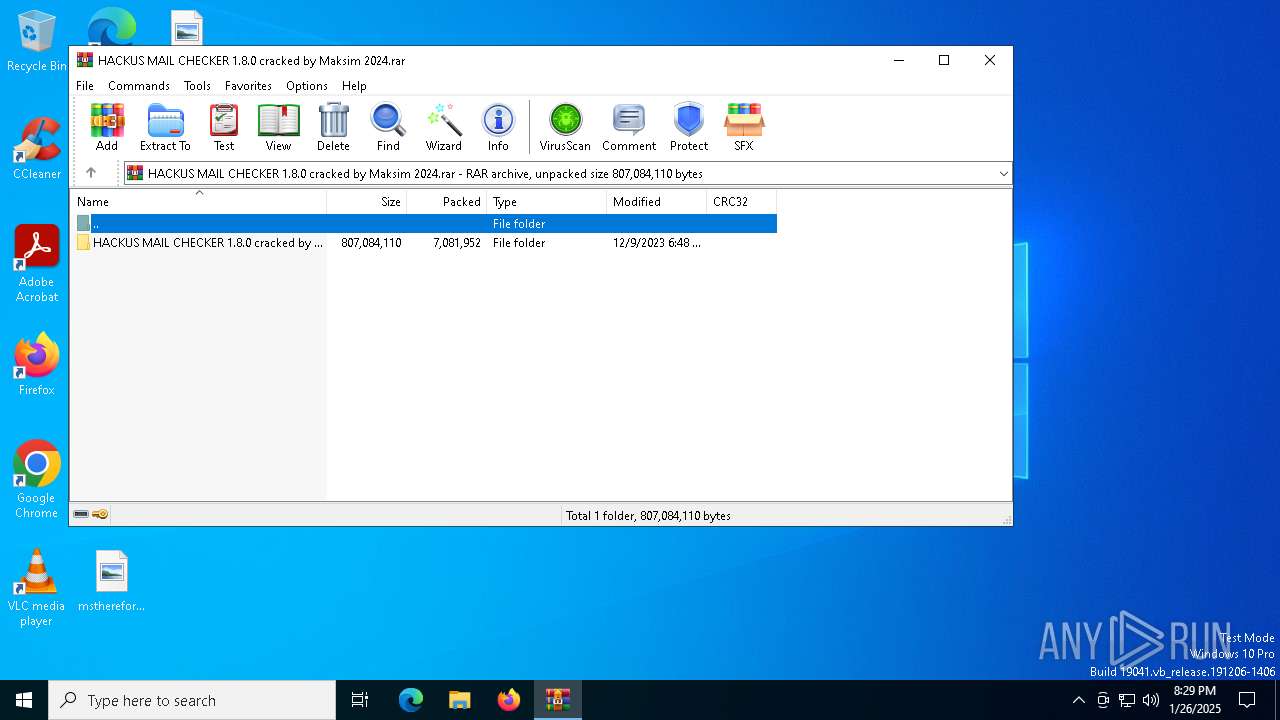
| File name: | HACKUS MAIL CHECKER 1.8.0 cracked by Maksim 2024.rar |
| Full analysis: | https://app.any.run/tasks/cb6d2830-1d64-4e2e-bdfa-465f6c5f2f60 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 20:28:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3FF89BFFB435502900A36B74A33B5501 |
| SHA1: | 67EE1B7E7BB2DC7F2778733794F03A565572B820 |
| SHA256: | C68997C328258A0B59F56610E8055D122B7E1A8EE0CD0EBF6EAF926CDE844474 |
| SSDEEP: | 98304:IILpOj4NnwJxbkELEOpCeZVfK+TBfSMiZJHolx/INSuTu/uKBfMVQCLcjKD8SUHa:NTOupvIsKvrJ3Ki6 |
MALICIOUS
Adds path to the Windows Defender exclusion list
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 432)
- LZMYBCTLTD.exe (PID: 3912)
- HMC.exe (PID: 488)
Uses Task Scheduler to run other applications
- LZMYBCTLTD.exe (PID: 3912)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6584)
Starts a Microsoft application from unusual location
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Reads the BIOS version
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Reads security settings of Internet Explorer
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Application launched itself
- HMC.exe (PID: 2600)
- HMC.exe (PID: 3848)
Script adds exclusion path to Windows Defender
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 432)
- LZMYBCTLTD.exe (PID: 3912)
- HMC.exe (PID: 488)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3188)
Found regular expressions for crypto-addresses (YARA)
- HMC.exe (PID: 556)
Starts CMD.EXE for commands execution
- HMC.exe (PID: 556)
Executing commands from a ".bat" file
- HMC.exe (PID: 556)
Starts POWERSHELL.EXE for commands execution
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 488)
The process executes via Task Scheduler
- LZMYBCTLTD.exe (PID: 432)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6584)
Manual execution by a user
- HMC.exe (PID: 2600)
- HMC.exe (PID: 3848)
The sample compiled with english language support
- WinRAR.exe (PID: 6584)
Checks supported languages
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Reads the computer name
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 432)
- LZMYBCTLTD.exe (PID: 3912)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Process checks computer location settings
- HMC.exe (PID: 2600)
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 3848)
- HMC.exe (PID: 488)
Process checks whether UAC notifications are on
- HMC.exe (PID: 556)
- LZMYBCTLTD.exe (PID: 3912)
- LZMYBCTLTD.exe (PID: 432)
- HMC.exe (PID: 488)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4388)
- powershell.exe (PID: 4392)
- powershell.exe (PID: 4864)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 1228)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 3508)
- powershell.exe (PID: 2260)
Creates files in the program directory
- HMC.exe (PID: 556)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4388)
- powershell.exe (PID: 4392)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 4864)
- powershell.exe (PID: 1228)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 3508)
Themida protector has been detected
- HMC.exe (PID: 556)
Create files in a temporary directory
- HMC.exe (PID: 556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
156
Monitored processes
29
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\ProgramData\active\LZMYBCTLTD.exe" | C:\ProgramData\active\LZMYBCTLTD.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 488 | "C:\Users\admin\Desktop\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\HMC.exe" | C:\Users\admin\Desktop\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\HMC.exe | HMC.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 556 | "C:\Users\admin\Desktop\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\HMC.exe" | C:\Users\admin\Desktop\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\HMC.exe | HMC.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 648 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /RL HIGHEST /tn "LZMYBCTLTD" /tr C:\ProgramData\active\LZMYBCTLTD.exe /f | C:\Windows\SysWOW64\schtasks.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | HMC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 482
Read events
45 473
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim 2024.rar | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
2
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6584.20558\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\HMC.exe | — | |
MD5:— | SHA256:— | |||
| 556 | HMC.exe | C:\ProgramData\active\LZMYBCTLTD.exe | — | |
MD5:— | SHA256:— | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6584.20558\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\License.dll | text | |
MD5:B08A5C34CF0A06615DA2CA89010D8B4F | SHA256:04CC5B3B49A7E9E9B6C66C7BE59A20992BF2653746B5D43829C383FB233F88FA | |||
| 4388 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xqrhaw3d.jzu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6584.20558\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\SMDiagnostics.dll | executable | |
MD5:F1D92AC71001BCC24B99044EE675619F | SHA256:5DF3A2E0329D7668AD0F6C426F6E4C6D1ECD45225B2C39D96B15CD7B6A1BBE53 | |||
| 6324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gxg0qhw4.ytt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4388 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2feful3.522.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6584.20558\HACKUS MAIL CHECKER 1.8.0 cracked by Maksim\updater.ini | binary | |
MD5:BDB71E725923415AD118571A96A58F9C | SHA256:CDFD1E0DB31EF98BE246AC26C14CBD47B24A11F85DD255FE55F93F8FB9FCAB11 | |||
| 4388 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nttv24pz.unp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3fazf5xw.sxd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6456 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4328 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |