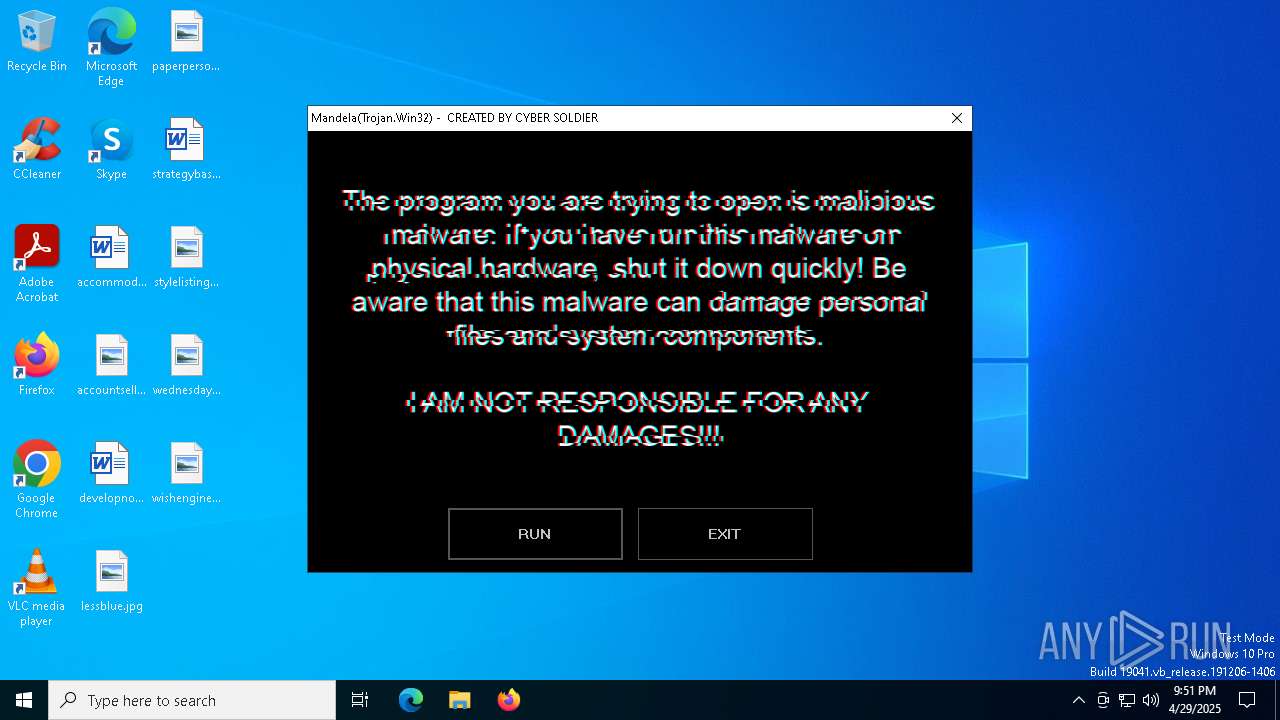
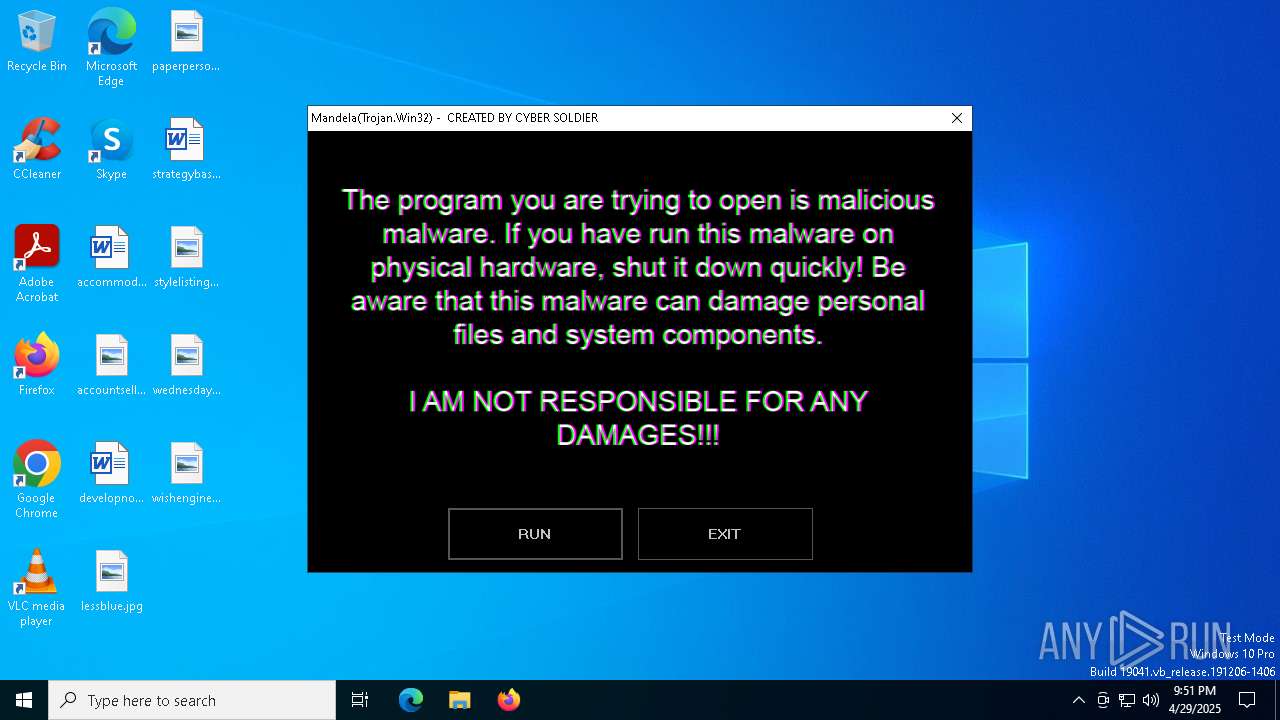
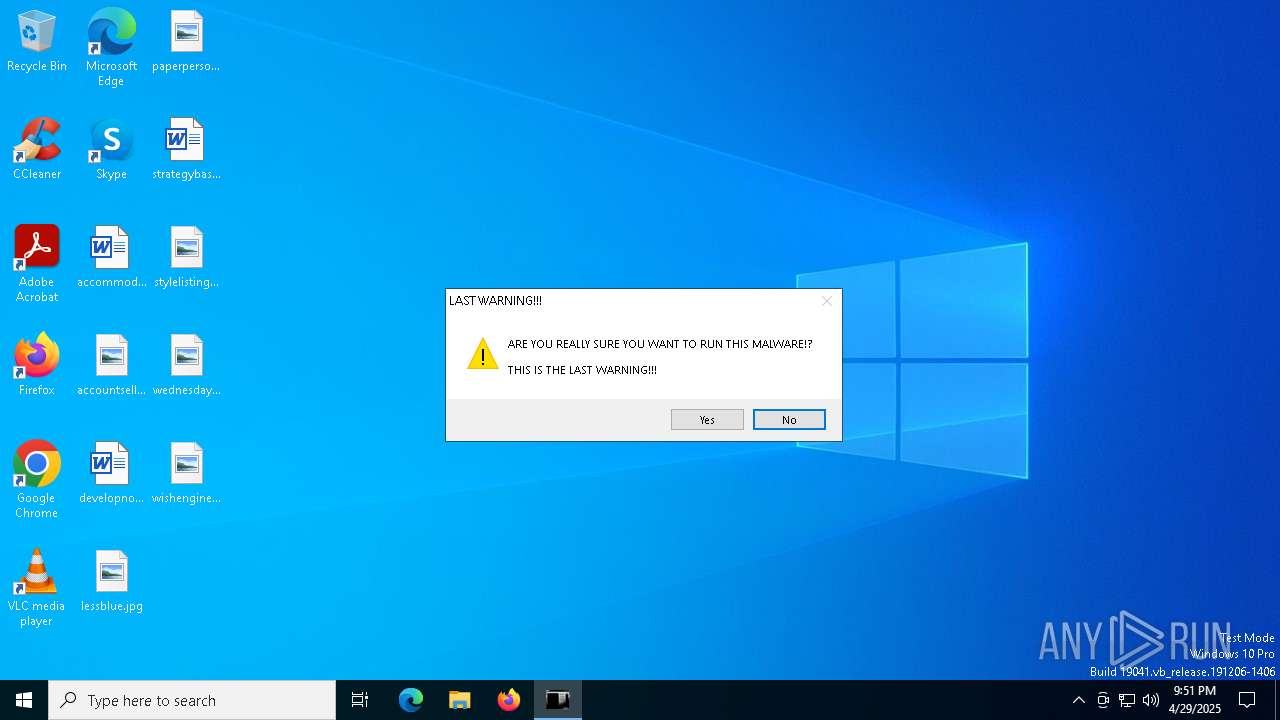
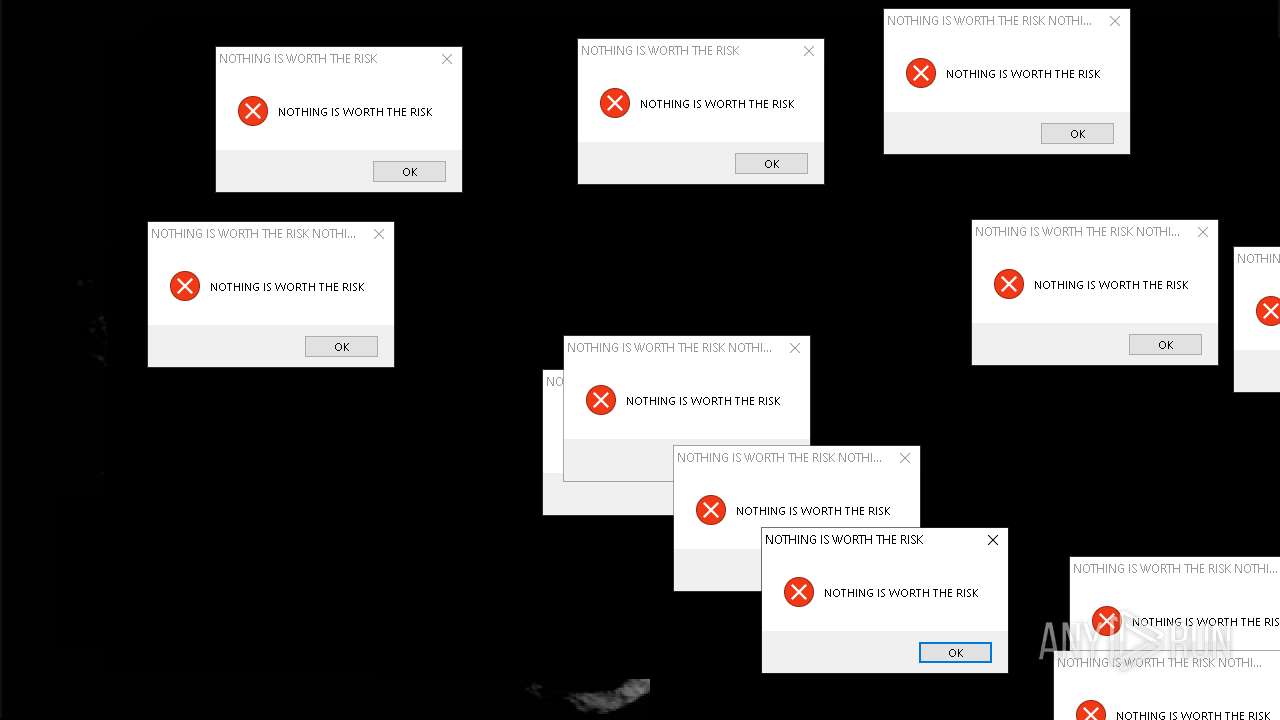
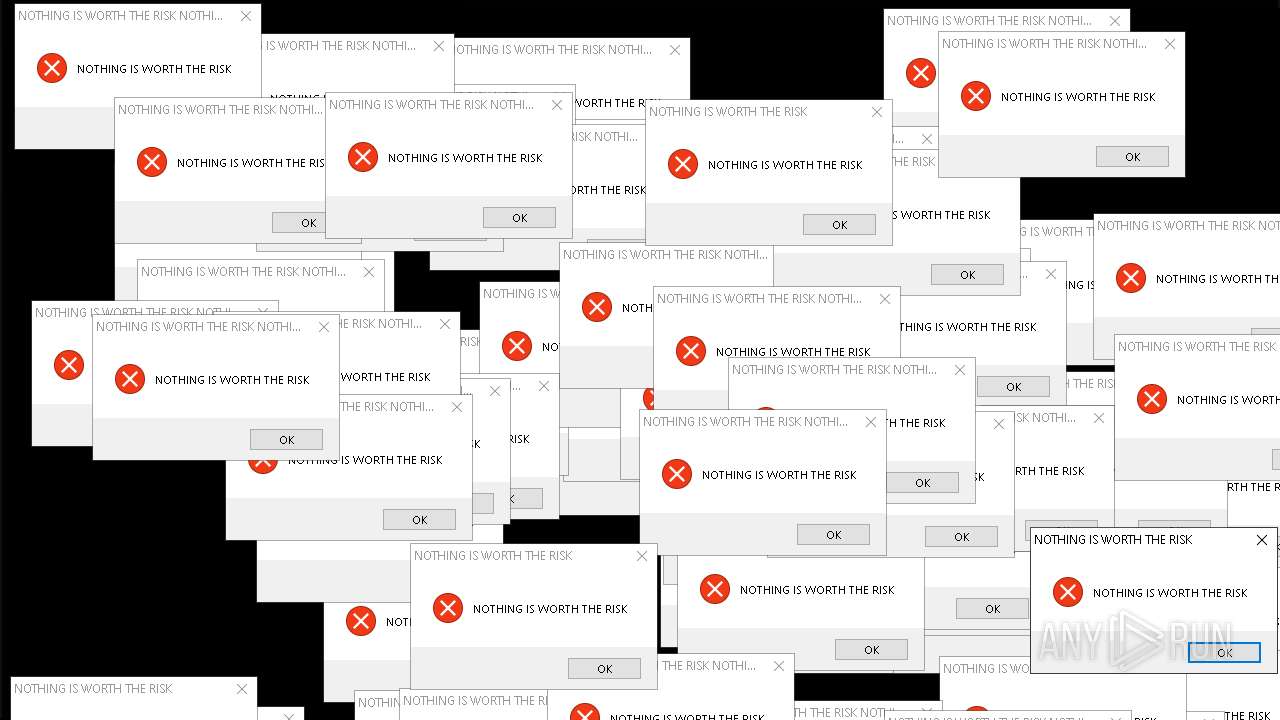
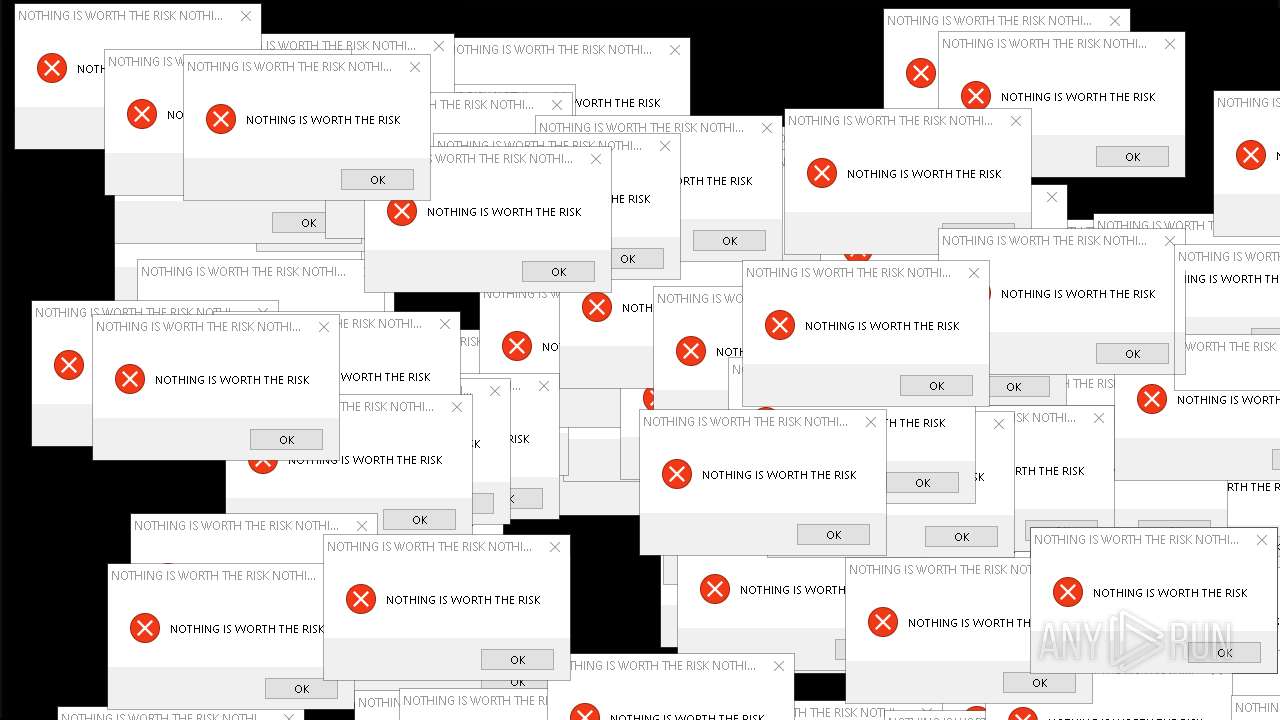
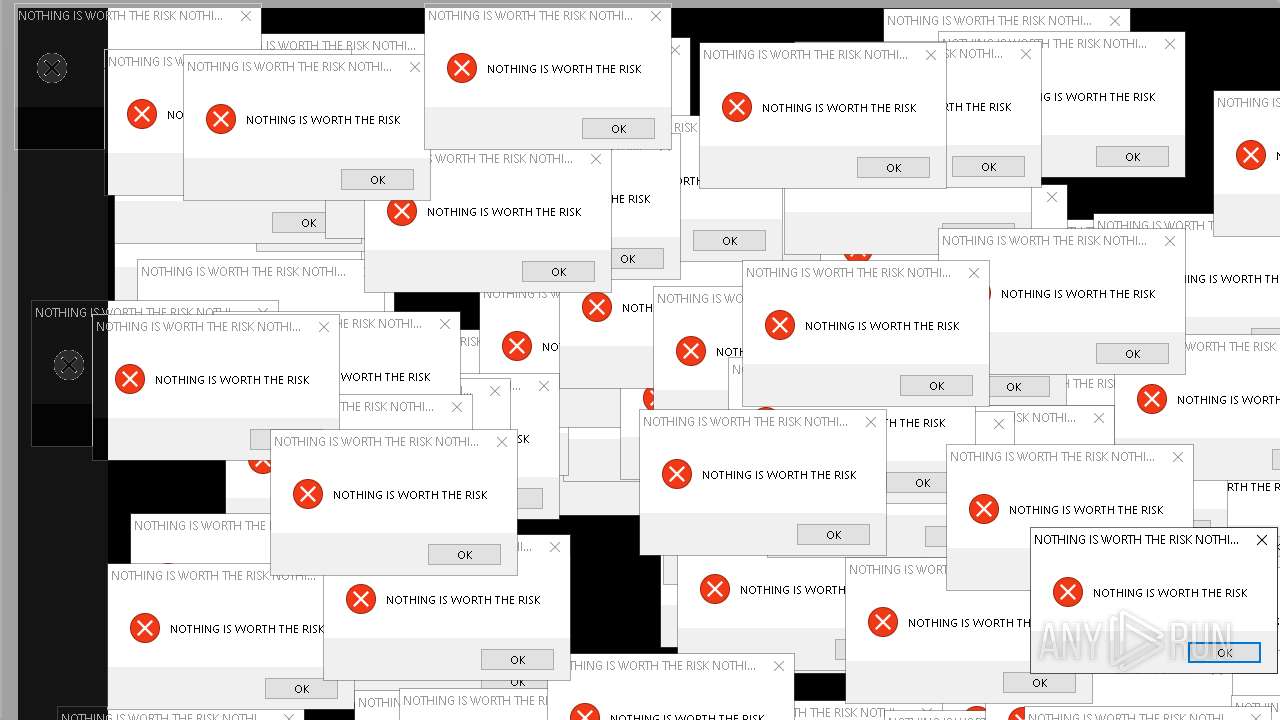
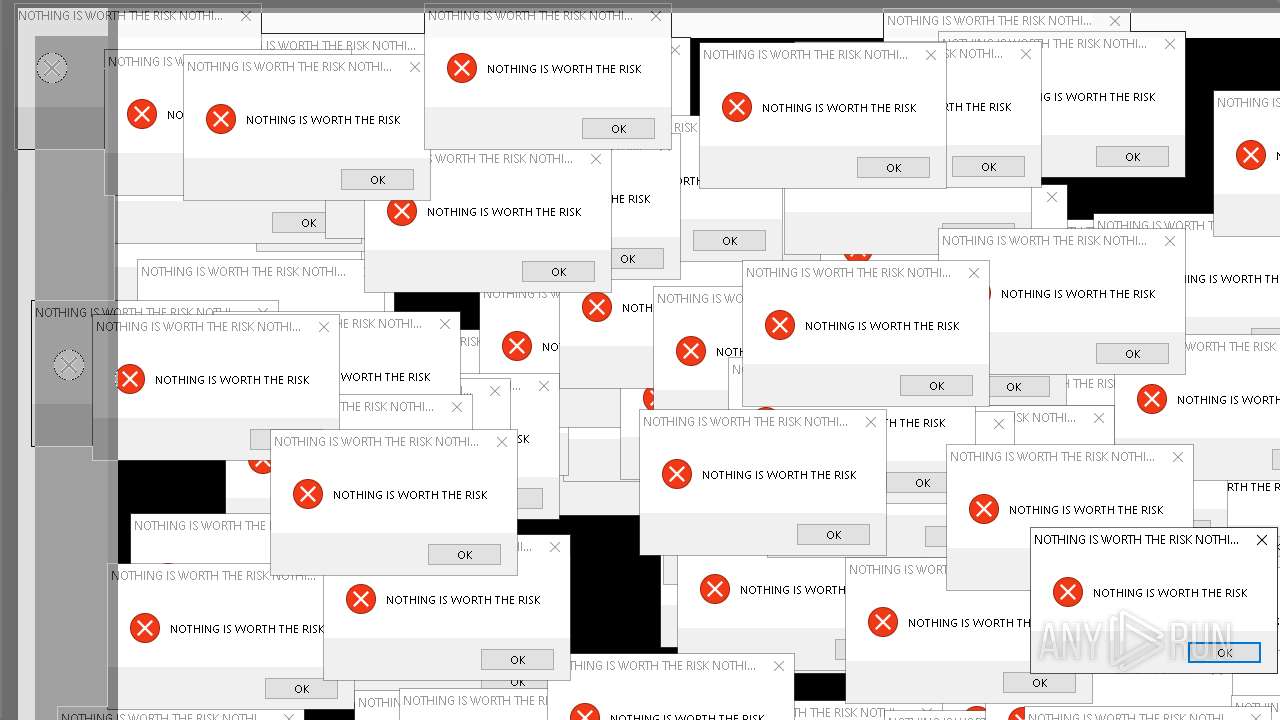
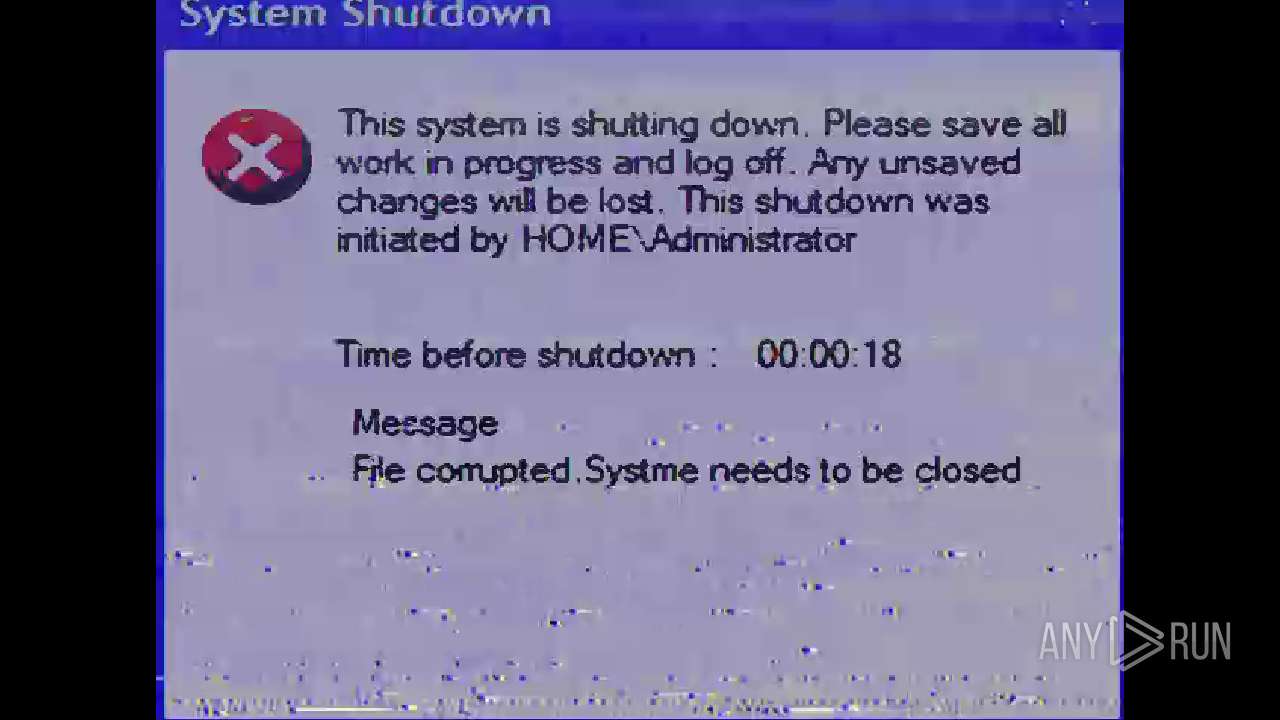
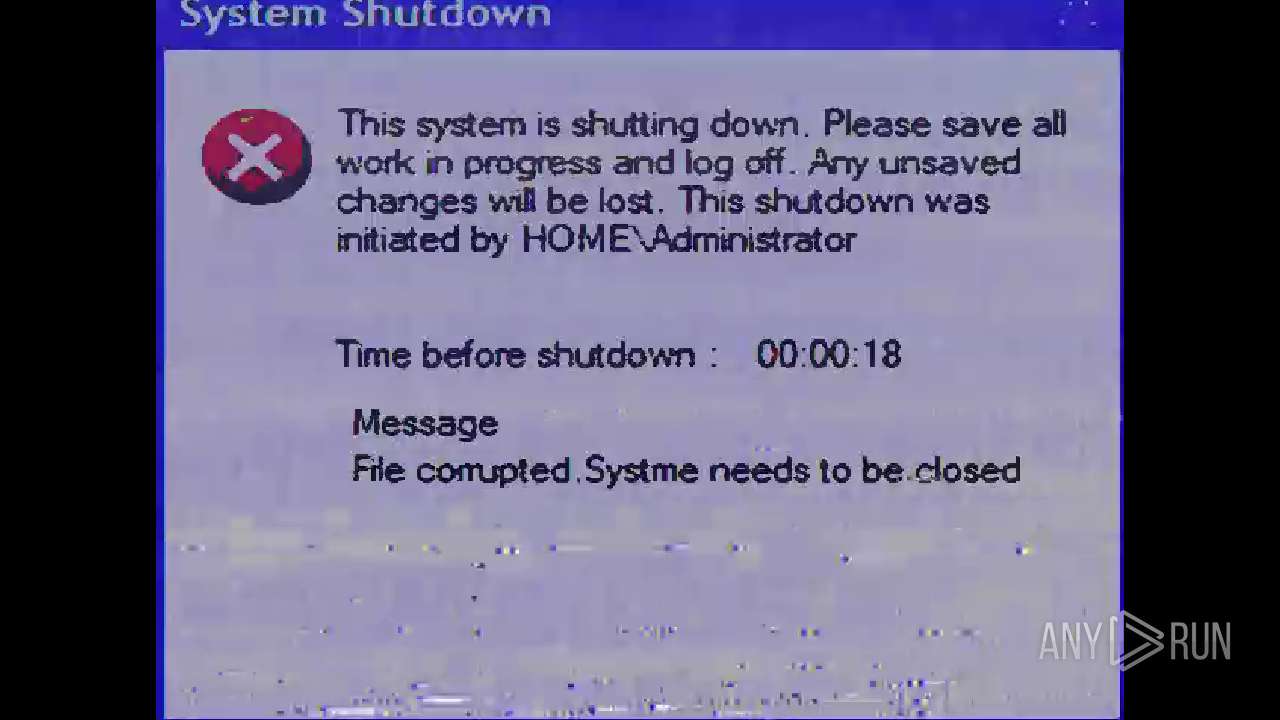
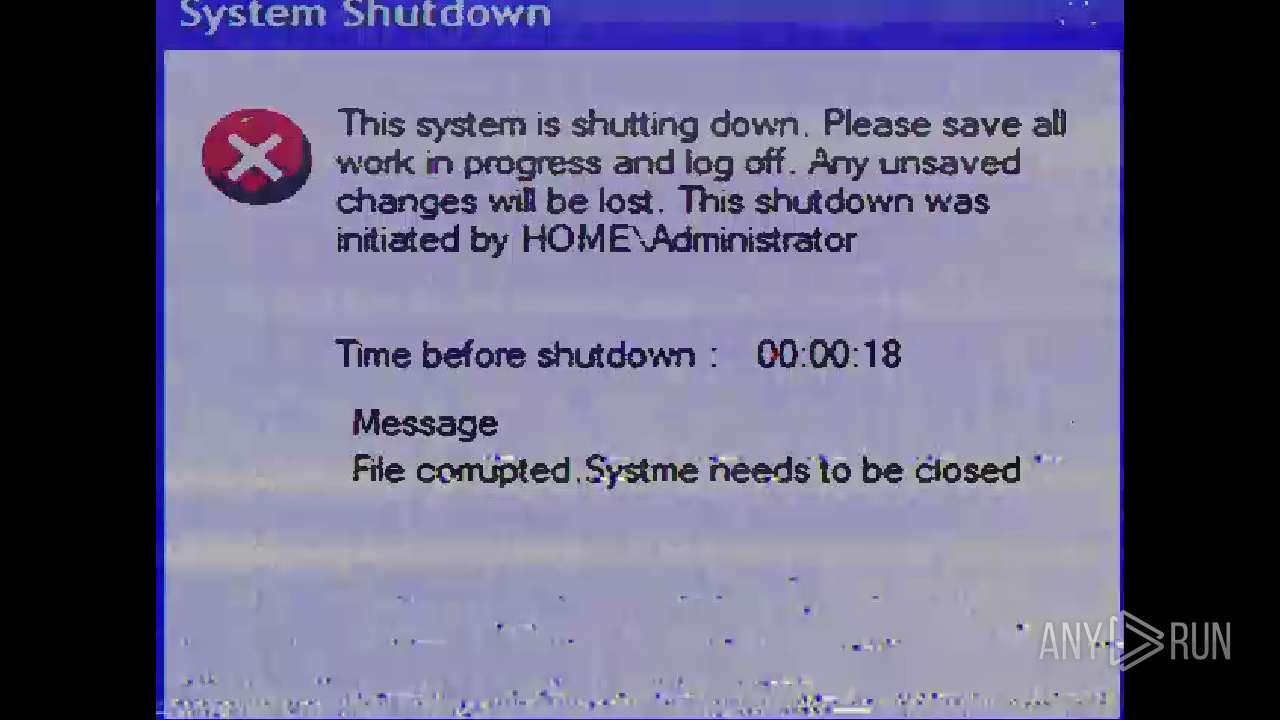
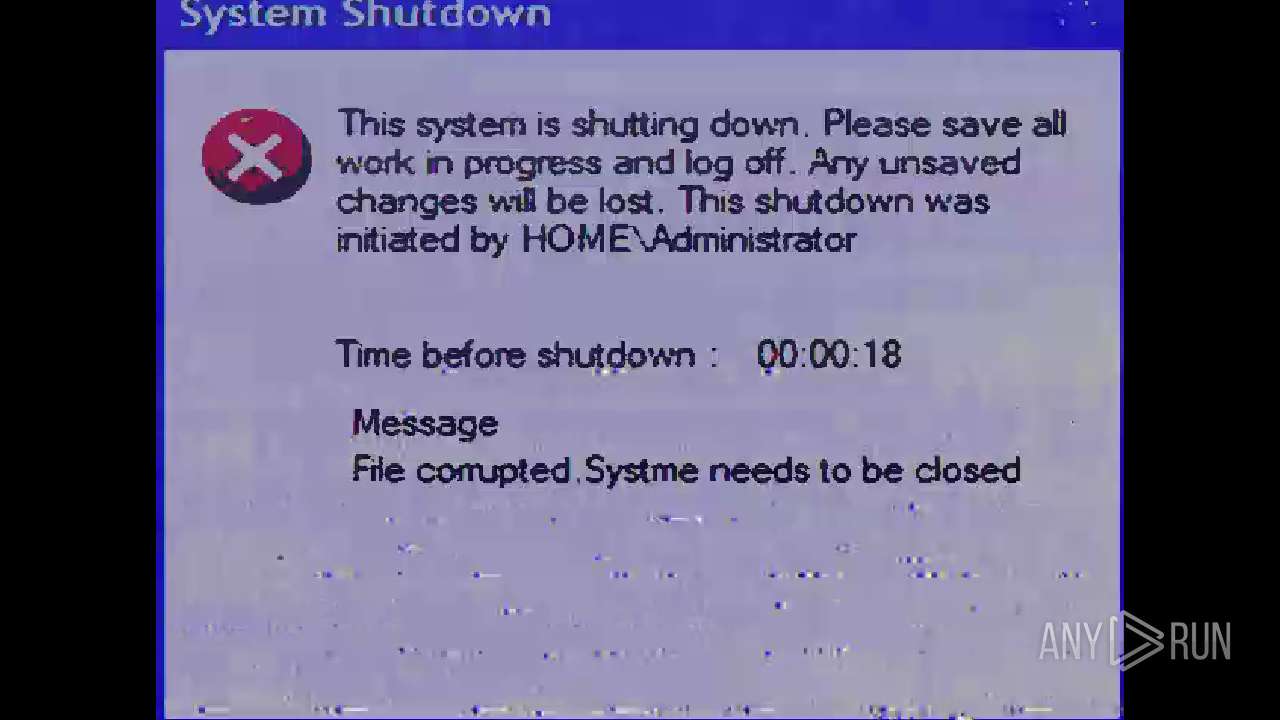
| File name: | Mandela.exe |
| Full analysis: | https://app.any.run/tasks/681f66d8-0be7-4af5-b2c2-33b9b7e29e1c |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 21:50:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 68558A4A7DF242046A8A7345501ADCF7 |
| SHA1: | EAC84B6BC1BE332AF4BAFC1BDAC30B40041A1295 |
| SHA256: | C6818DA28A36A7ED628E5A86EDE3A642B609B34B2F61AE4DBA9A4814D6822D2F |
| SSDEEP: | 393216:3S2Jj2w9YgIrP/gHase3j3LINmWuwd6CZ/OK4jXo/jH599sl:Cm3YgIrXg6sELLIQWXsCZGKgY/jxa |
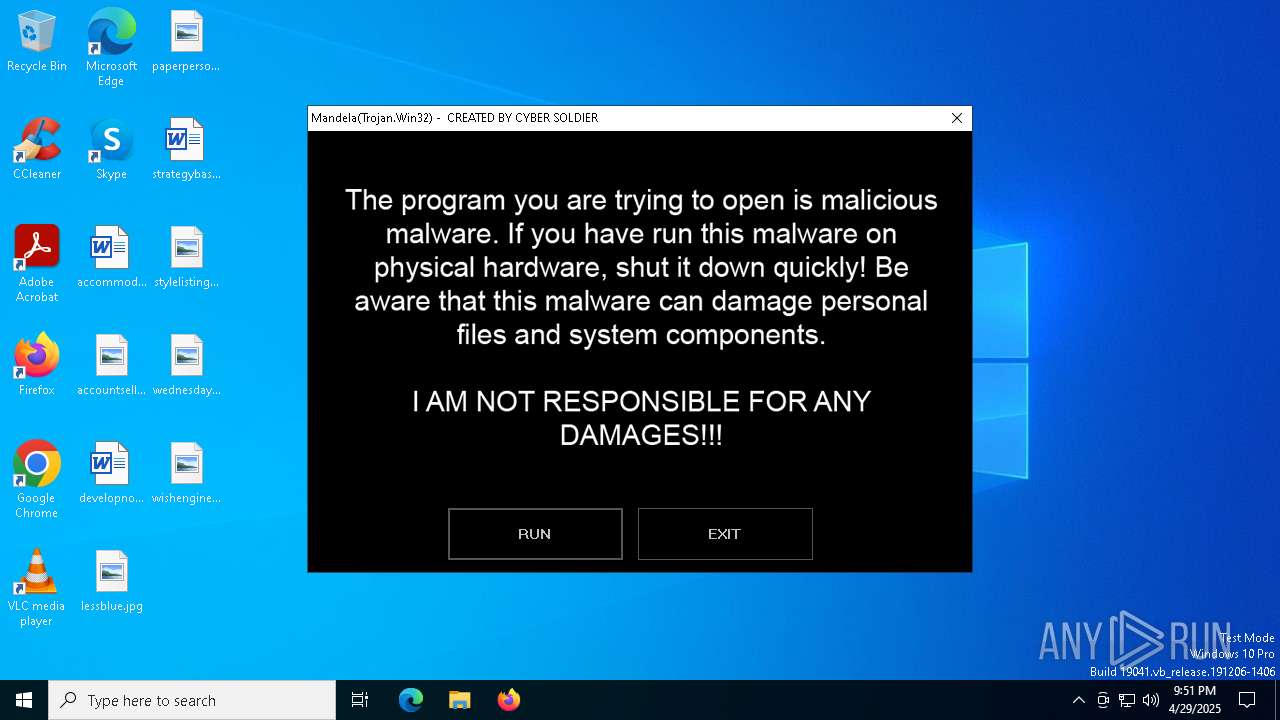
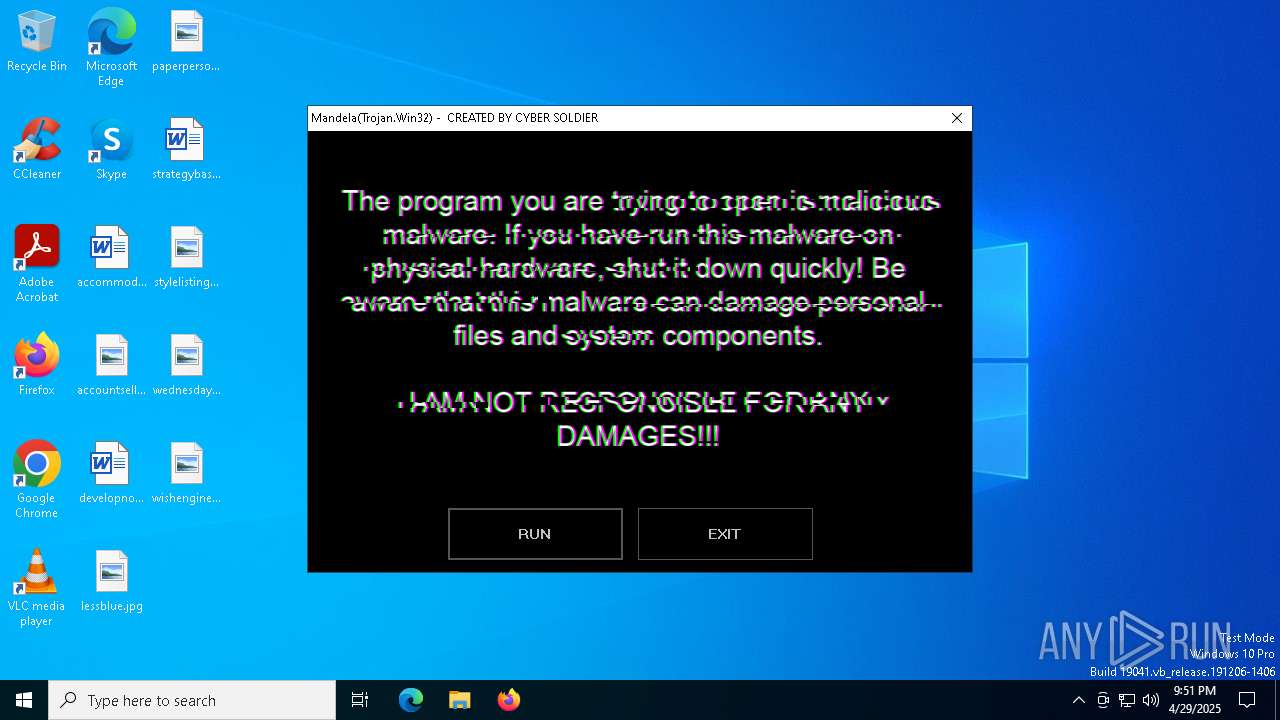
MALICIOUS
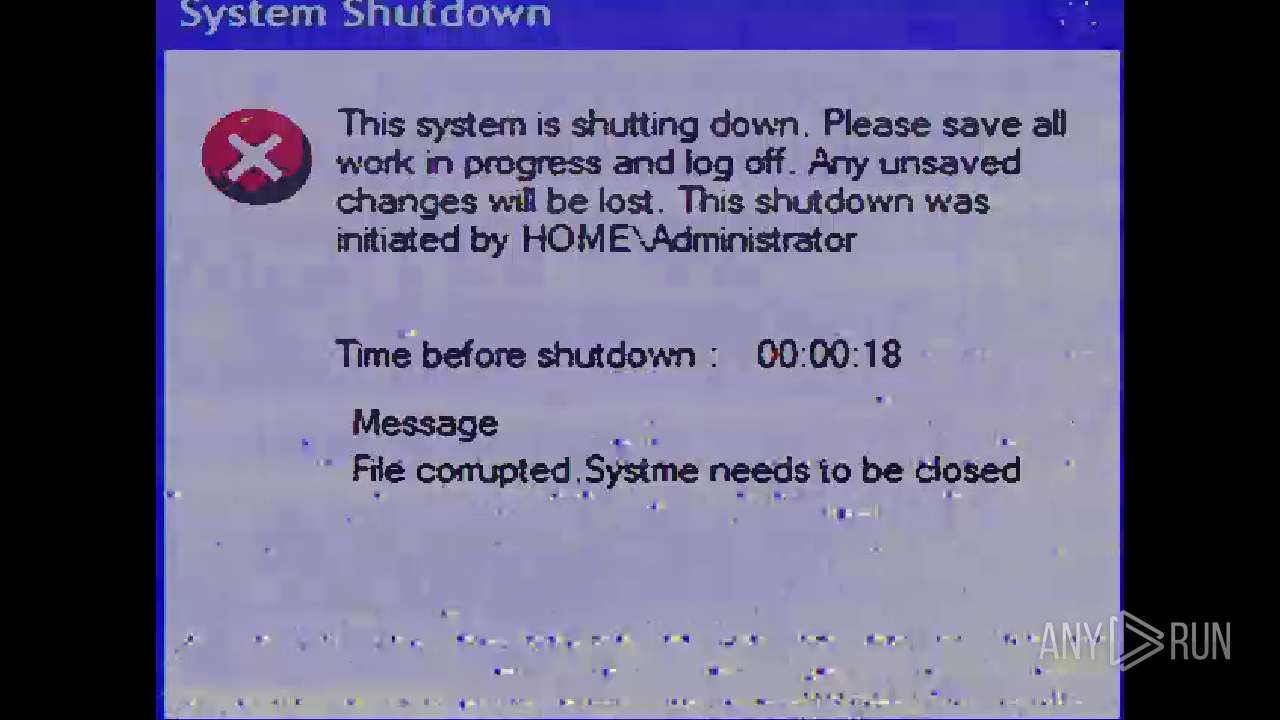
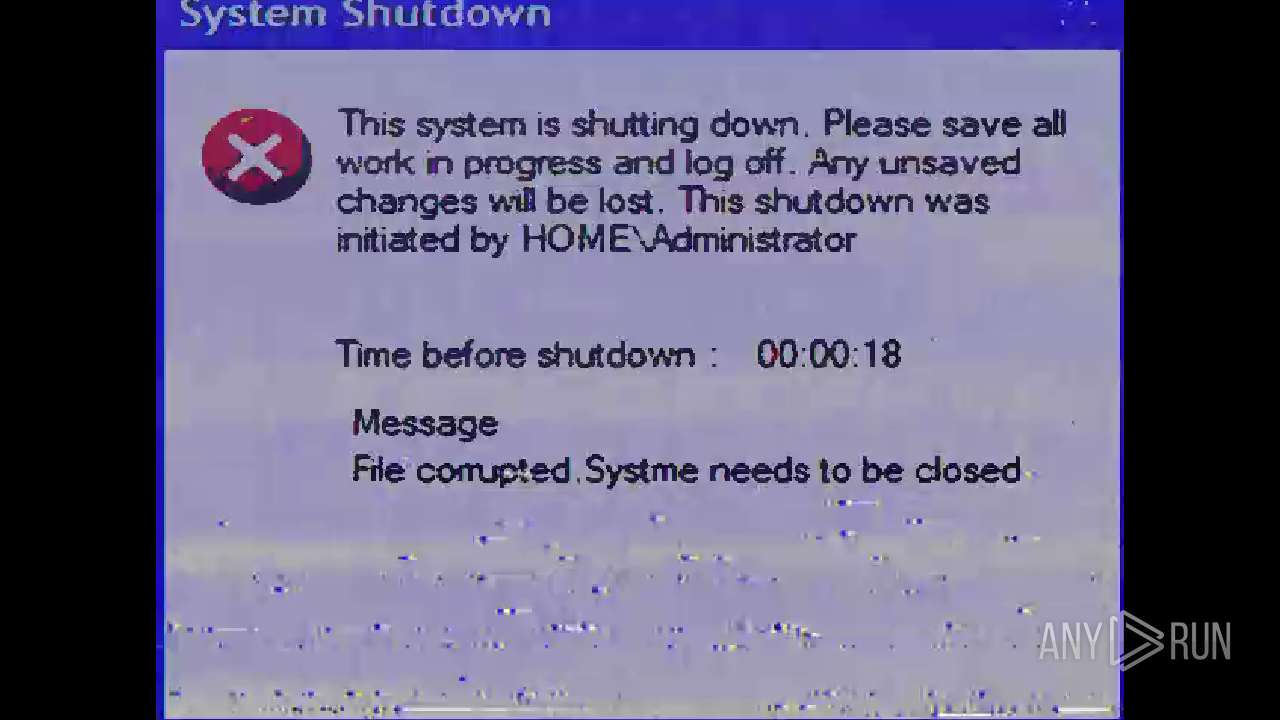
Changes the login/logoff helper path in the registry
- Mandela.exe (PID: 7408)
Disables Windows Defender
- Mandela.exe (PID: 7408)
UAC/LUA settings modification
- Mandela.exe (PID: 7408)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Mandela.exe (PID: 7408)
Executable content was dropped or overwritten
- Mandela.exe (PID: 7408)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7844)
- Mandela.exe (PID: 7408)
Reads the date of Windows installation
- Mandela.exe (PID: 7408)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6428)
- cmd.exe (PID: 5416)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4128)
- PLUGScheduler.exe (PID: 888)
Starts CMD.EXE for commands execution
- Mandela.exe (PID: 7408)
- mandela.exe (PID: 4432)
INFO
Creates files or folders in the user directory
- Mandela.exe (PID: 7408)
.NET Reactor protector has been detected
- Mandela.exe (PID: 7408)
Reads the computer name
- Mandela.exe (PID: 7408)
- ShellExperienceHost.exe (PID: 7844)
Reads the machine GUID from the registry
- Mandela.exe (PID: 7408)
Checks supported languages
- Mandela.exe (PID: 7408)
- ShellExperienceHost.exe (PID: 7844)
Process checks whether UAC notifications are on
- Mandela.exe (PID: 7408)
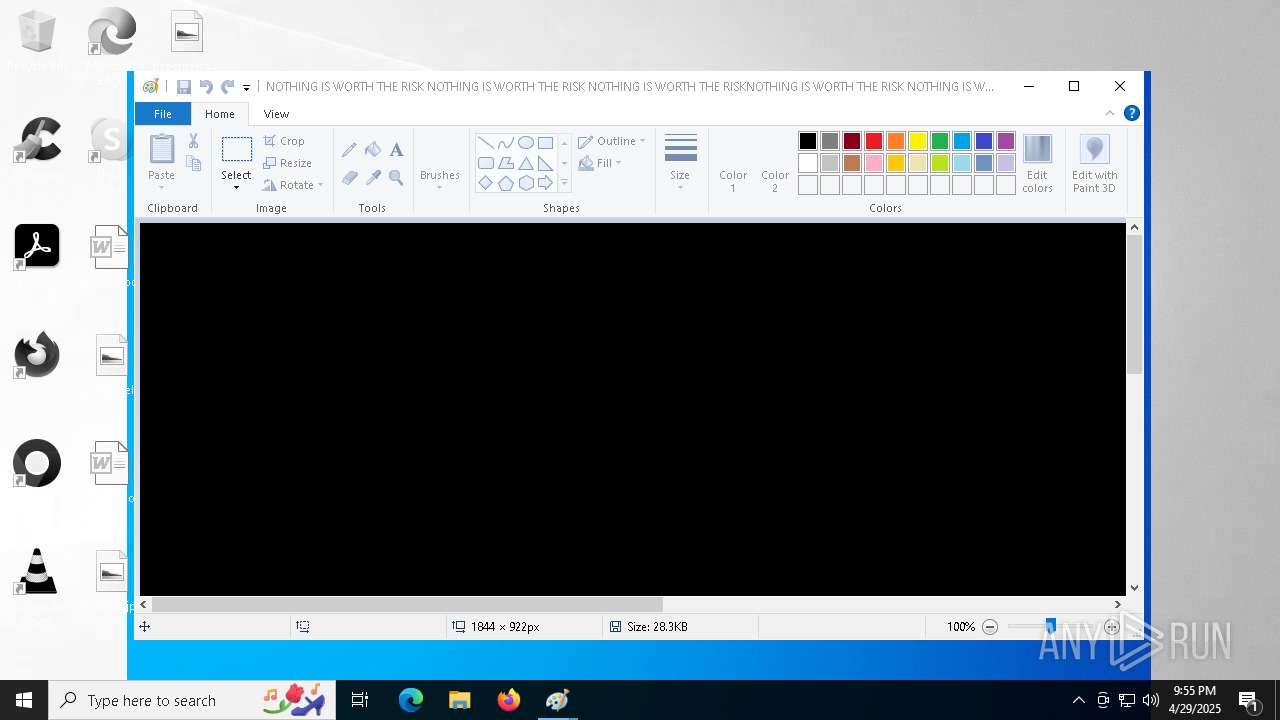
Manual execution by a user
- mspaint.exe (PID: 6508)
- mspaint.exe (PID: 6632)
Process checks computer location settings
- Mandela.exe (PID: 7408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2054:04:04 15:20:39+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 15806976 |
| InitializedDataSize: | 110080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xf151de |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | NOTHING IS WORTH THE RISK |
| CompanyName: | NOTHING IS WORTH THE RISK |
| FileDescription: | NOTHING IS WORTH THE RISK |
| FileVersion: | 1.0.0.0 |
| InternalName: | Mandela.exe |
| LegalCopyright: | NOTHING IS WORTH THE RISK |
| LegalTrademarks: | NOTHING IS WORTH THE RISK |
| OriginalFileName: | Mandela.exe |
| ProductName: | NOTHING IS WORTH THE RISK |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
396
Monitored processes
16
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | taskkill /f /im explorer.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4432 | mandela.exe | C:\Windows\mandela.exe | — | userinit.exe | |||||||||||
User: admin Company: NOTHING IS WORTH THE RISK Integrity Level: HIGH Description: NOTHING IS WORTH THE RISK Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4592 | mandela.exe | C:\Windows\mandela.exe | — | userinit.exe | |||||||||||
User: admin Company: NOTHING IS WORTH THE RISK Integrity Level: HIGH Description: NOTHING IS WORTH THE RISK Version: 1.0.0.0 Modules
| |||||||||||||||
| 5072 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5416 | "C:\Windows\System32\cmd.exe" /k taskkill /f /im explorer.exe | C:\Windows\System32\cmd.exe | — | Mandela.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6428 | "C:\Windows\System32\cmd.exe" /k taskkill /f /im explorer.exe | C:\Windows\System32\cmd.exe | — | mandela.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 335
Read events
18 628
Write events
12 706
Delete events
1
Modification events
| (PID) Process: | (7408) Mandela.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | FilterAdministratorToken |
Value: 1 | |||
| (PID) Process: | (7408) Mandela.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7408) Mandela.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (7408) Mandela.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Keyboard Layout |
| Operation: | write | Name: | Scancode Map |
Value: 00000000000000004A000000000021E000006CE000006DE0000011E000006BE0000050E000004BE000004DE0000048E0000040E0000042E000003BE000003EE000003CE000003FE0000058E0000007E0000041E0000057E0000043E0000023E000003DE0000008E052001E004F00300052002E004F002000520012004C0021004B0022004900230048001700510024004C002500280026004A0032003400310029001800270019001A001000370013000C001F007D0014005300160056E02F0035E011004A002D00520015004F002C0000001CE000005DE000000E00000046E000003A00000053E000004FE000001C0000000100000047E0000052E00000380000001D0000002A0000005BE00000450000005EE0000038E000001DE00000360000005CE000005FE00000390000000F0000000000 | |||
| (PID) Process: | (7408) Mandela.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, mandela.exe | |||
| (PID) Process: | (7844) ShellExperienceHost.exe | Key: | \REGISTRY\A\{86e6f884-a21f-5957-810e-7e5720011563}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000569EEFD550B9DB01 | |||
| (PID) Process: | (7844) ShellExperienceHost.exe | Key: | \REGISTRY\A\{86e6f884-a21f-5957-810e-7e5720011563}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000A851F0D550B9DB01 | |||
| (PID) Process: | (4432) mandela.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\mandela.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 696E000000000000 | |||
| (PID) Process: | (4432) mandela.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | UniqueID |
Value: {3962BEA4-58D3-4766-8745-02CA4DDD56D0} | |||
| (PID) Process: | (4432) mandela.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-JGLLJLD | |||
Executable files
1
Suspicious files
89
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\education.mp4 | — | |
MD5:— | SHA256:— | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\entity.bmp | image | |
MD5:6B80387C1369B969100C113E85E301D5 | SHA256:0AE1757A6803D51F34D38DB026C8945F23BF2E0A59353B0CB823572D353C88A5 | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\mask.bmp | image | |
MD5:8A5FC7A21228596BC1D4F48B3B905491 | SHA256:A6F3C0CAE53808BED3E86A4BCADCD027E4EFE2E2BC93F47E872B396CE2C24A11 | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\momo.bmp | image | |
MD5:CF6D2C56E76DD4F62FDC478F1EF952D7 | SHA256:6B4C497C22754112A387E0286179E28989740DF614CEEF96F745C3333D05DB6D | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\nosleep.bmp | image | |
MD5:065C5858DA1C8B5806BCC39BE71C0B91 | SHA256:EC9DD0C0E6DFE1FA66D51BC0C64AB28ADEF7BDF33E63978BD6F8DD27FF14ABAC | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\nosleep2.bmp | image | |
MD5:B9805B16E8F3BC852EB4CBFF59828D1E | SHA256:32934EBCAA300EF712736003E0504B96ED07F11F64404FBD25E1D535BBDEE0E0 | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\watching.bmp | image | |
MD5:A0446D6B6A4B68F596ACFB5F39A3056B | SHA256:858BF072C6C1202874365ABF2C3B52BD6AAB50B8AE8A71DAAF4E8EC9B79F1039 | |||
| 7408 | Mandela.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\cybersoldier_angry.bmp | image | |
MD5:92A182A679271E505758459B02872170 | SHA256:59B66AB942D4C67F06D2ED55D3F4ACF366A9C6F79F8EE527D6C484328C979C08 | |||
| 888 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 888 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
60
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3176 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3176 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5288 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4428 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4864 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5324 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |