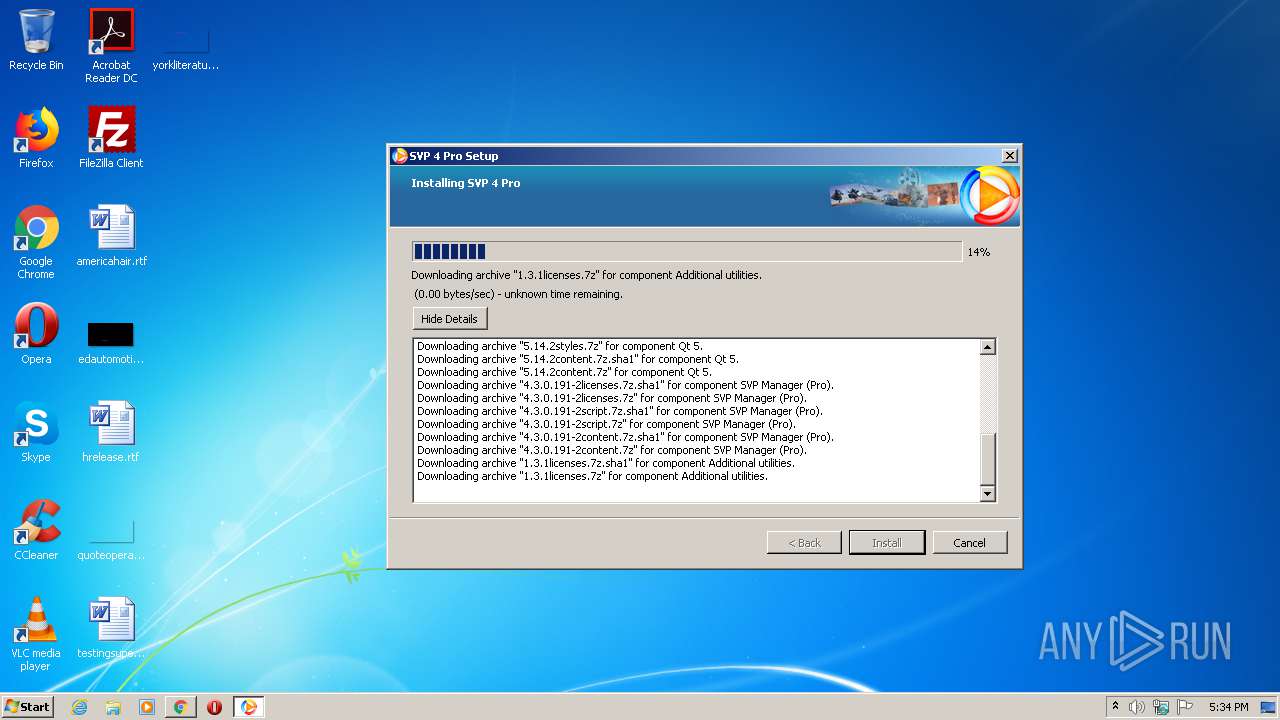
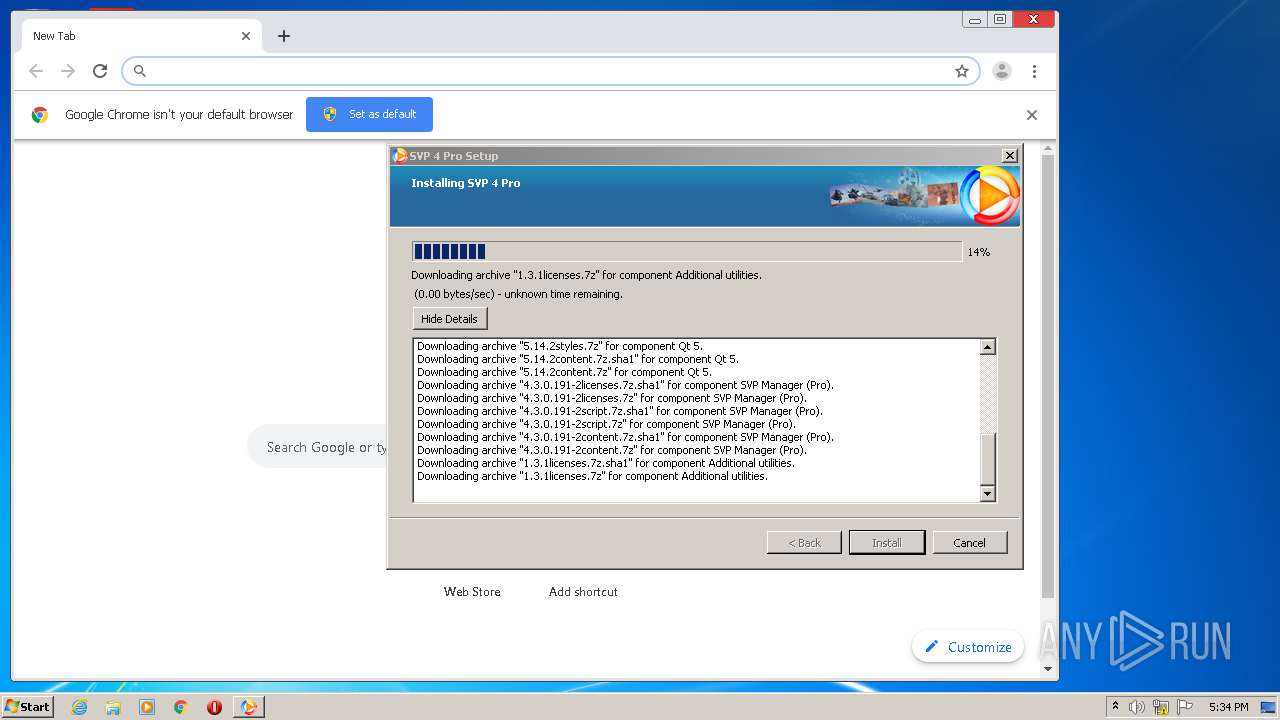
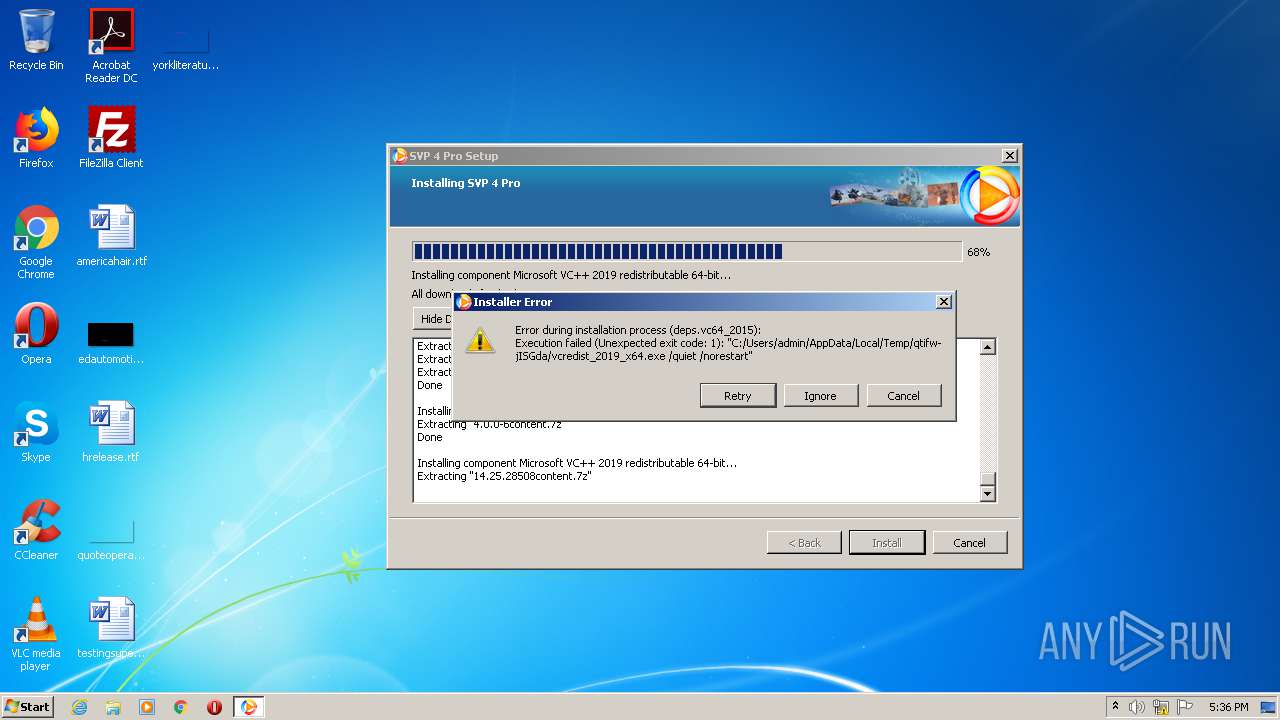
| download: | svp4-latest.php |
| Full analysis: | https://app.any.run/tasks/b63ca55e-ed03-4506-bfed-70d142ef18ca |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2020, 16:33:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed |
| MD5: | E5846D32FCD44498AE327F64C137AC23 |
| SHA1: | 74CCDCFF79D1AE59A22A2912D7E63570EB1E6945 |
| SHA256: | C66DF47214505EEF354F042F115C715C72643AA9764D876709E91C87CD7FD631 |
| SSDEEP: | 196608:9QiR8HqjmKDzupjPfa+3Vvml9Ky3sRjBPFYz9LOuk:9Q4tDzupjqIVvw9KEslO9Lk |
MALICIOUS
Application was dropped or rewritten from another process
- vcredist_2019_x86.exe (PID: 1148)
- VC_redist.x86.exe (PID: 4056)
- vcredist_2019_x86.exe (PID: 2180)
- vcredist_2019_x64.exe (PID: 2224)
- vcredist_2019_x64.exe (PID: 3484)
- vcredist_2019_x64.exe (PID: 1908)
- AviSynth_plus.exe (PID: 916)
- vcredist_2019_x64.exe (PID: 3624)
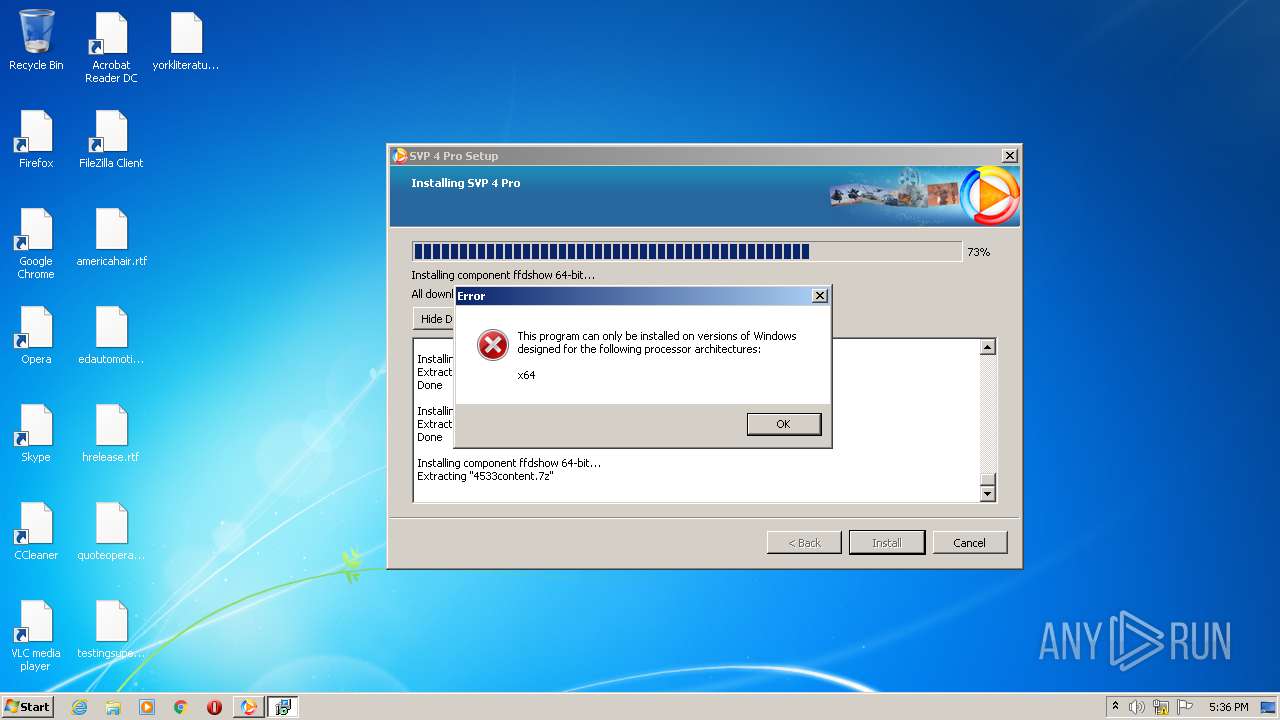
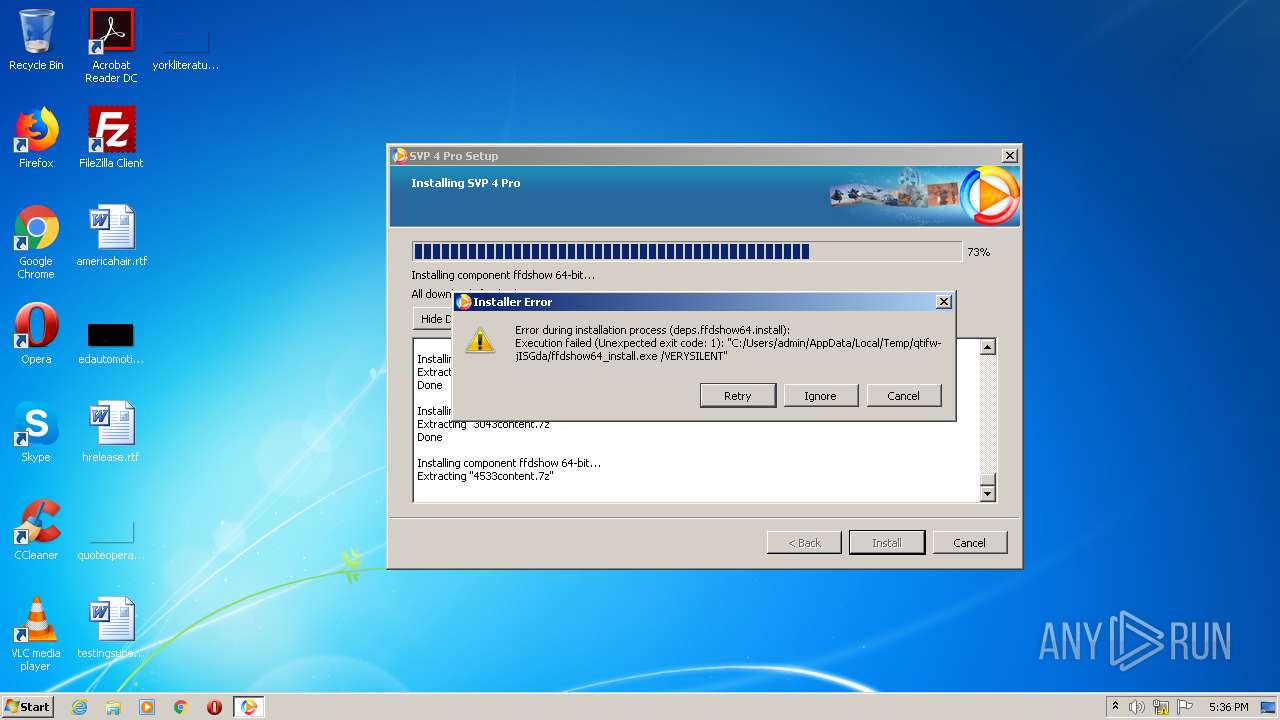
- ffdshow64_install.exe (PID: 2884)
- VC_redist.x86.exe (PID: 1840)
- SVPManager.exe (PID: 604)
- VC_redist.x86.exe (PID: 1736)
- MPC-HC.x64.exe (PID: 4008)
- SVPManager.exe (PID: 2084)
- VC_redist.x86.exe (PID: 3112)
Loads dropped or rewritten executable
- vcredist_2019_x86.exe (PID: 2180)
- VC_redist.x86.exe (PID: 1840)
- SVPManager.exe (PID: 604)
- vcredist_2019_x64.exe (PID: 2224)
- vcredist_2019_x64.exe (PID: 3484)
- SVPManager.exe (PID: 2084)
Changes the autorun value in the registry
- VC_redist.x86.exe (PID: 4056)
Changes settings of System certificates
- msiexec.exe (PID: 3400)
SUSPICIOUS
Application launched itself
- svp4-latest.php.exe (PID: 2444)
- VC_redist.x86.exe (PID: 1840)
Creates files in the Windows directory
- vcredist_2019_x86.exe (PID: 1148)
- vcredist_2019_x86.exe (PID: 2180)
- msiexec.exe (PID: 3400)
- VC_redist.x86.exe (PID: 1840)
- vcredist_2019_x64.exe (PID: 3624)
- vcredist_2019_x64.exe (PID: 2224)
- vcredist_2019_x64.exe (PID: 3484)
- AviSynth_plus.tmp (PID: 2828)
- vcredist_2019_x64.exe (PID: 1908)
Executable content was dropped or overwritten
- vcredist_2019_x86.exe (PID: 1148)
- vcredist_2019_x86.exe (PID: 2180)
- svp4-latest.php.exe (PID: 1512)
- VC_redist.x86.exe (PID: 4056)
- msiexec.exe (PID: 3400)
- VC_redist.x86.exe (PID: 1840)
- VC_redist.x86.exe (PID: 1736)
- vcredist_2019_x64.exe (PID: 3624)
- vcredist_2019_x64.exe (PID: 1908)
- vcredist_2019_x64.exe (PID: 2224)
- AviSynth_plus.exe (PID: 916)
- AviSynth_plus.tmp (PID: 2828)
- ffdshow64_install.exe (PID: 2884)
- MPC-HC.x64.exe (PID: 4008)
- cscript.exe (PID: 4028)
Executed as Windows Service
- vssvc.exe (PID: 2760)
Starts itself from another location
- vcredist_2019_x86.exe (PID: 2180)
Searches for installed software
- VC_redist.x86.exe (PID: 4056)
Creates files in the program directory
- VC_redist.x86.exe (PID: 4056)
- svp4-latest.php.exe (PID: 1512)
Creates a software uninstall entry
- VC_redist.x86.exe (PID: 4056)
- VC_redist.x86.exe (PID: 1736)
- svp4-latest.php.exe (PID: 1512)
Removes files from Windows directory
- vcredist_2019_x86.exe (PID: 1148)
- vcredist_2019_x86.exe (PID: 2180)
- VC_redist.x86.exe (PID: 1840)
- vcredist_2019_x64.exe (PID: 3624)
- vcredist_2019_x64.exe (PID: 2224)
- vcredist_2019_x64.exe (PID: 3484)
- vcredist_2019_x64.exe (PID: 1908)
Creates files in the user directory
- svp4-latest.php.exe (PID: 1512)
- SVPManager.exe (PID: 2084)
- SVPManager.exe (PID: 604)
Starts CMD.EXE for commands execution
- svp4-latest.php.exe (PID: 1512)
Reads the Windows organization settings
- AviSynth_plus.tmp (PID: 2828)
Reads Windows owner or organization settings
- AviSynth_plus.tmp (PID: 2828)
Creates COM task schedule object
- AviSynth_plus.tmp (PID: 2828)
Executes scripts
- svp4-latest.php.exe (PID: 1512)
Adds / modifies Windows certificates
- msiexec.exe (PID: 3400)
INFO
Reads the hosts file
- chrome.exe (PID: 3928)
- chrome.exe (PID: 3048)
Manual execution by user
- chrome.exe (PID: 3928)
Application launched itself
- chrome.exe (PID: 3928)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2760)
Reads settings of System Certificates
- chrome.exe (PID: 3048)
- msiexec.exe (PID: 3400)
Creates a software uninstall entry
- msiexec.exe (PID: 3400)
- AviSynth_plus.tmp (PID: 2828)
Dropped object may contain Bitcoin addresses
- svp4-latest.php.exe (PID: 1512)
Application was dropped or rewritten from another process
- AviSynth_plus.tmp (PID: 2828)
- ffdshow64_install.tmp (PID: 960)
- MPC-HC.x64.tmp (PID: 2316)
Dropped object may contain TOR URL's
- svp4-latest.php.exe (PID: 1512)
Creates files in the program directory
- AviSynth_plus.tmp (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:11:06 09:11:13+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 9502720 |
| InitializedDataSize: | 225280 |
| UninitializedDataSize: | 16752640 |
| EntryPoint: | 0x190a970 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 385.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 3.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Nov-2019 08:11:13 |
| Detected languages: |
|
| TLS Callbacks: | 1 callback(s) detected. |
| FileVersion: | 3.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 06-Nov-2019 08:11:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00FFA000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00FFB000 | 0x00910000 | 0x0090FC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.93403 |
.rsrc | 0x0190B000 | 0x00037000 | 0x00036600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.7692 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08474 | 1119 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.30941 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 4.03304 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 6.4265 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 6.64193 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.61672 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.11499 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 5.62416 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 7.57143 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
IDI_ICON1 | 6.54811 | 132 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
GDI32.dll |
IMM32.DLL |
IPHLPAPI.DLL |
KERNEL32.DLL |
MPR.DLL |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
UxTheme.dll |
Total processes
79
Monitored processes
35
Malicious processes
15
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,15919327323304082966,8438678919213270925,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8885806148757891779 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2528 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 604 | "C:\Program Files\SVP 4\SVPManager.exe" -main -quit | C:\Program Files\SVP 4\SVPManager.exe | svp4-latest.php.exe | ||||||||||||
User: admin Company: SVP-Team.com Integrity Level: HIGH Description: SVP 4 Pro Exit code: 0 Version: 4.3.0."##VCS_REVISION##" Modules
| |||||||||||||||
| 648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6f43a9d0,0x6f43a9e0,0x6f43a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | C:\Users\admin\AppData\Local\Temp\qtifw-jISGda\AviSynth_plus.exe /VERYSILENT | C:\Users\admin\AppData\Local\Temp\qtifw-jISGda\AviSynth_plus.exe | svp4-latest.php.exe | ||||||||||||
User: admin Company: The Public Integrity Level: HIGH Description: AviSynth+ Setup Exit code: 0 Version: 3.5.0.3043 Modules
| |||||||||||||||
| 960 | "C:\Users\admin\AppData\Local\Temp\is-HTK4T.tmp\ffdshow64_install.tmp" /SL5="$A0136,4529113,119296,C:\Users\admin\AppData\Local\Temp\qtifw-jISGda\ffdshow64_install.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-HTK4T.tmp\ffdshow64_install.tmp | — | ffdshow64_install.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=964,15919327323304082966,8438678919213270925,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=1130033247317475819 --mojo-platform-channel-handle=1052 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1148 | C:\Users\admin\AppData\Local\Temp\qtifw-jISGda\vcredist_2019_x86.exe /quiet /norestart | C:\Users\admin\AppData\Local\Temp\qtifw-jISGda\vcredist_2019_x86.exe | svp4-latest.php.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x86) - 14.25.28508 Exit code: 0 Version: 14.25.28508.3 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\AppData\Local\Temp\svp4-latest.php.exe" --startserver PRODUCTION,{56666830-7f79-41d6-962a-7ddd1b208aa3},{a323f6e8-a48f-4ed0-9ec1-6c38948f7629} | C:\Users\admin\AppData\Local\Temp\svp4-latest.php.exe | svp4-latest.php.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,15919327323304082966,8438678919213270925,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3945532483186040729 --mojo-platform-channel-handle=3456 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1736 | "C:\ProgramData\Package Cache\{49697869-be8e-427d-81a0-c334d1d14950}\VC_redist.x86.exe" -q -burn.elevated BurnPipe.{BFA22871-E124-4A73-A51D-4BAE12BE9D03} {96FA4E2B-DF66-4231-8DF0-9D7B56DE557F} 1840 | C:\ProgramData\Package Cache\{49697869-be8e-427d-81a0-c334d1d14950}\VC_redist.x86.exe | VC_redist.x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2019 Redistributable (x86) - 14.21.27702 Exit code: 0 Version: 14.21.27702.2 Modules
| |||||||||||||||
Total events
3 802
Read events
1 779
Write events
1 729
Delete events
294
Modification events
| (PID) Process: | (2444) svp4-latest.php.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2444) svp4-latest.php.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2444) svp4-latest.php.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
137
Suspicious files
85
Text files
1 646
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\svp4-latest.Hp2444 | — | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\Updates.xml | html | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\core-4.0.0-6-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\opt.reclock-1.9.0.6-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\opt.mpc_hc32-1.9.2-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\deps.vc32_2015-14.25.28508-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\opt.lavf-0.74-1-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\opt.madvr-0.92.17-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\deps.python32-3.8.2-meta.7z | compressed | |
MD5:— | SHA256:— | |||
| 2444 | svp4-latest.php.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-vRqybW\opt.mpc_hc64-1.9.2-meta.7z | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
81
TCP/UDP connections
74
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/deps.ffdshow32.install/4533meta.7z | US | compressed | 880 b | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/deps.ffdshow64/4533meta.7z | US | compressed | 1.00 Kb | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/opt.reclock/1.9.0.6meta.7z | US | compressed | 656 b | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/core/4.0.0-6meta.7z | US | compressed | 5.17 Kb | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/deps.ffdshow32/4533meta.7z | US | compressed | 1.01 Kb | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/opt.madvr/0.92.17meta.7z | US | compressed | 392 b | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/Updates.xml?full=main&168322092 | US | html | 4.60 Kb | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/deps.vc64_2015/14.25.28508meta.7z | US | compressed | 431 b | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/opt.lavf/0.74-1meta.7z | US | compressed | 450 b | suspicious |
2444 | svp4-latest.php.exe | GET | 200 | 104.26.12.243:80 | http://cdn.svp-team.com/repo/full/opt.mpc_hc64/1.9.2meta.7z | US | compressed | 1.88 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3048 | chrome.exe | 172.217.18.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3048 | chrome.exe | 172.217.18.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3048 | chrome.exe | 172.217.22.46:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
2444 | svp4-latest.php.exe | 104.26.13.243:80 | cdn.svp-team.com | Cloudflare Inc | US | suspicious |
3048 | chrome.exe | 172.217.23.110:443 | apis.google.com | Google Inc. | US | whitelisted |
— | — | 104.26.12.243:80 | cdn.svp-team.com | Cloudflare Inc | US | suspicious |
3048 | chrome.exe | 172.217.22.67:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3048 | chrome.exe | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
2444 | svp4-latest.php.exe | 104.26.12.243:80 | cdn.svp-team.com | Cloudflare Inc | US | suspicious |
3048 | chrome.exe | 216.58.212.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.svp-team.com |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
Threats
Process | Message |
|---|---|
SVPManager.exe | 17:36:31.495 [I]: Main: starting up SVP 4 Pro [4.3.0.191]...
|
SVPManager.exe | 17:36:31.511 [W]: Main: running as Administrator
|
SVPManager.exe | 17:36:31.511 [W]: Settings: creating profiles.cfg with default values
|
SVPManager.exe | 17:36:31.511 [I]: Main: args: -main -quit
|
SVPManager.exe | 17:36:31.511 [W]: Settings: creating frc.cfg with default values
|
SVPManager.exe | 17:36:31.511 [W]: Settings: creating main.cfg with default values
|
SVPManager.exe | 17:36:31.511 [W]: Settings: creating ui.cfg with default values
|
SVPManager.exe | 17:36:31.511 [I]: Main: working dir is C:\Program Files\SVP 4\
|
SVPManager.exe | 17:36:31.511 [I]: Main: data dir set to C:\Users\admin\AppData\Roaming\SVP4\
|
SVPManager.exe | 17:36:31.511 [I]: Settings: loading ui.cfg OK
|