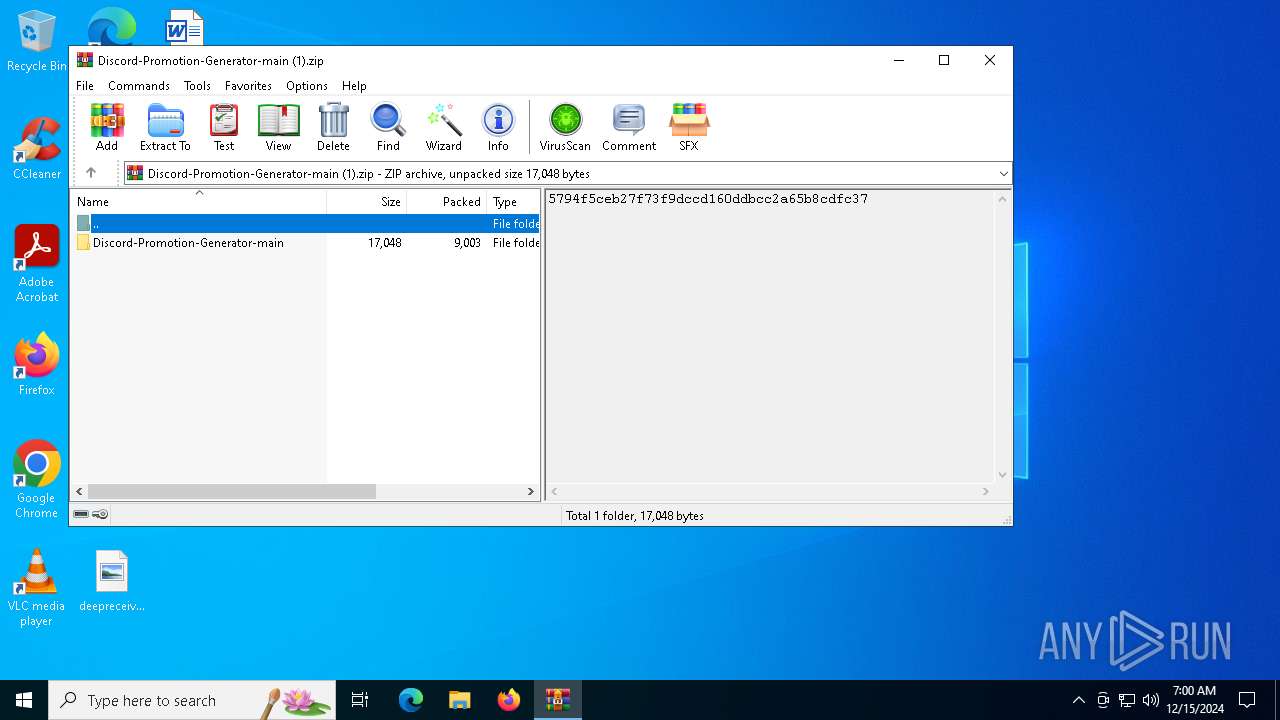
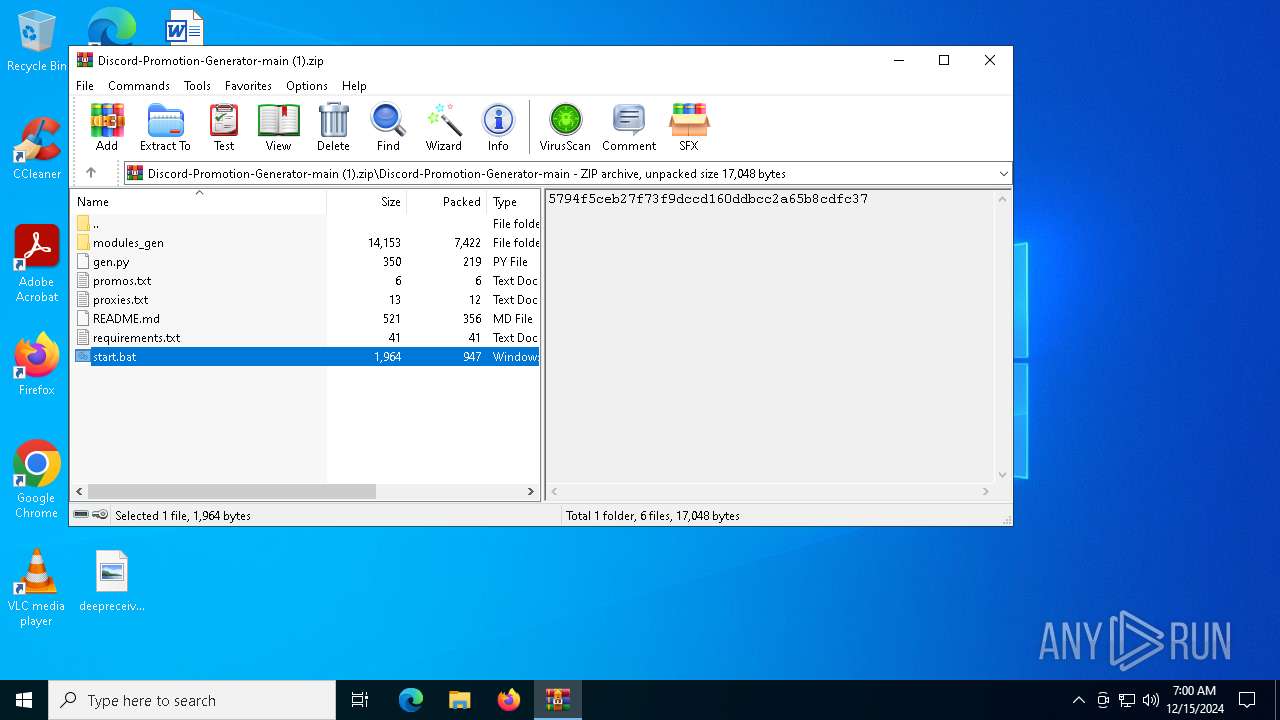
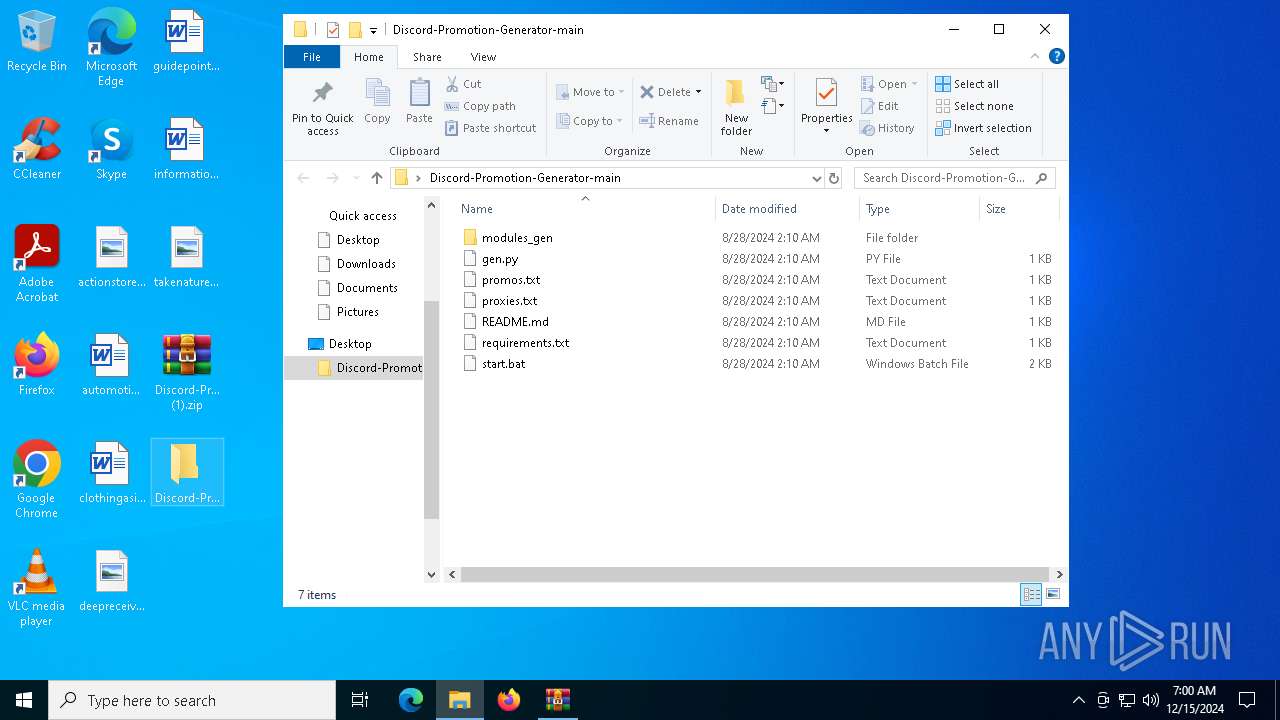
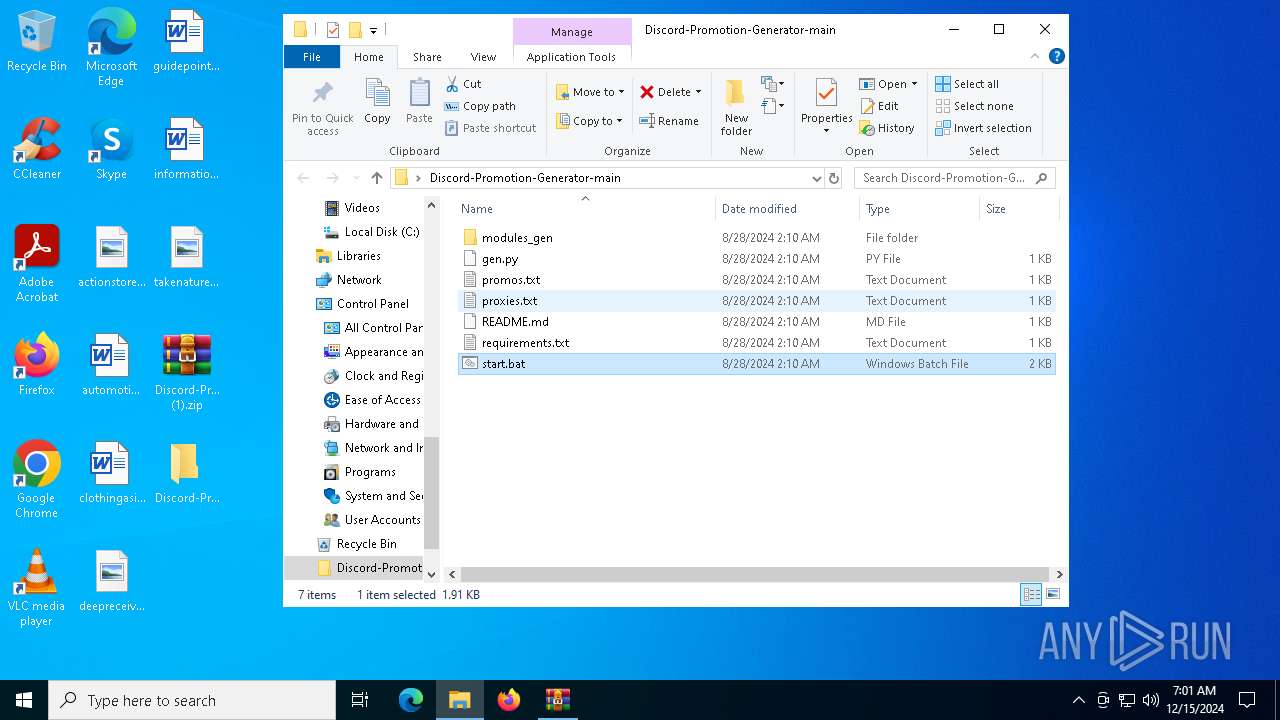
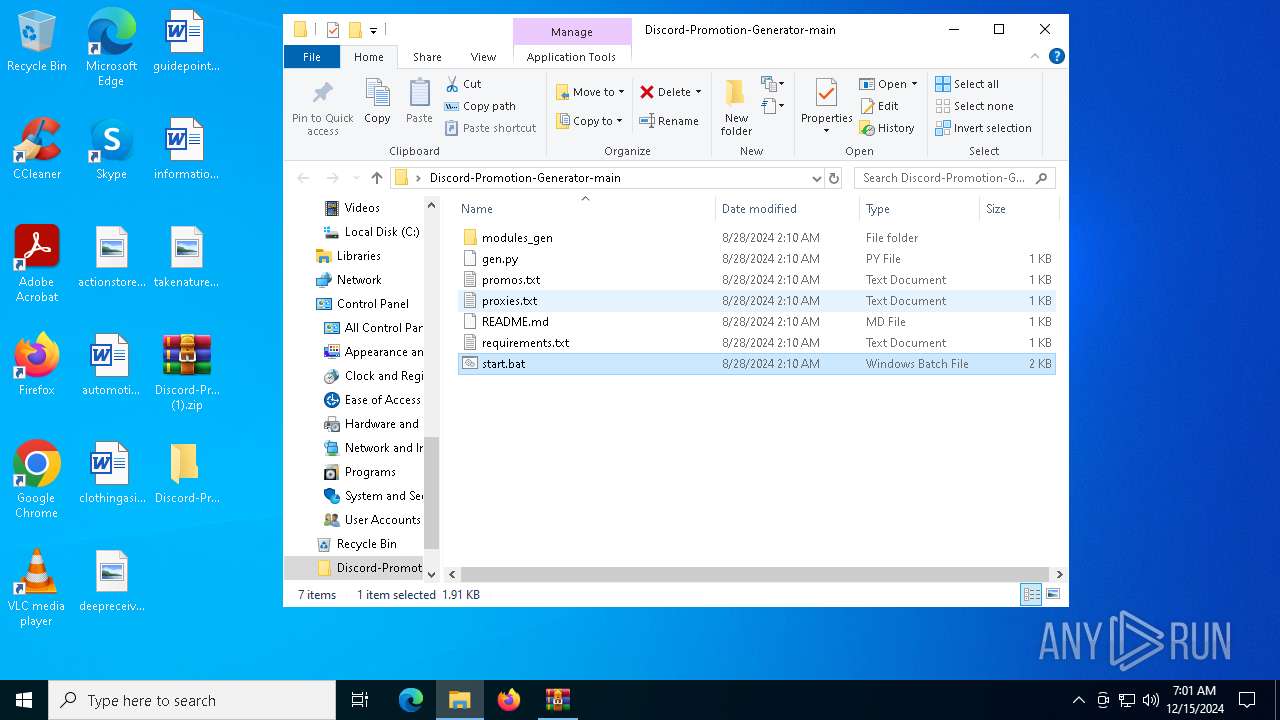
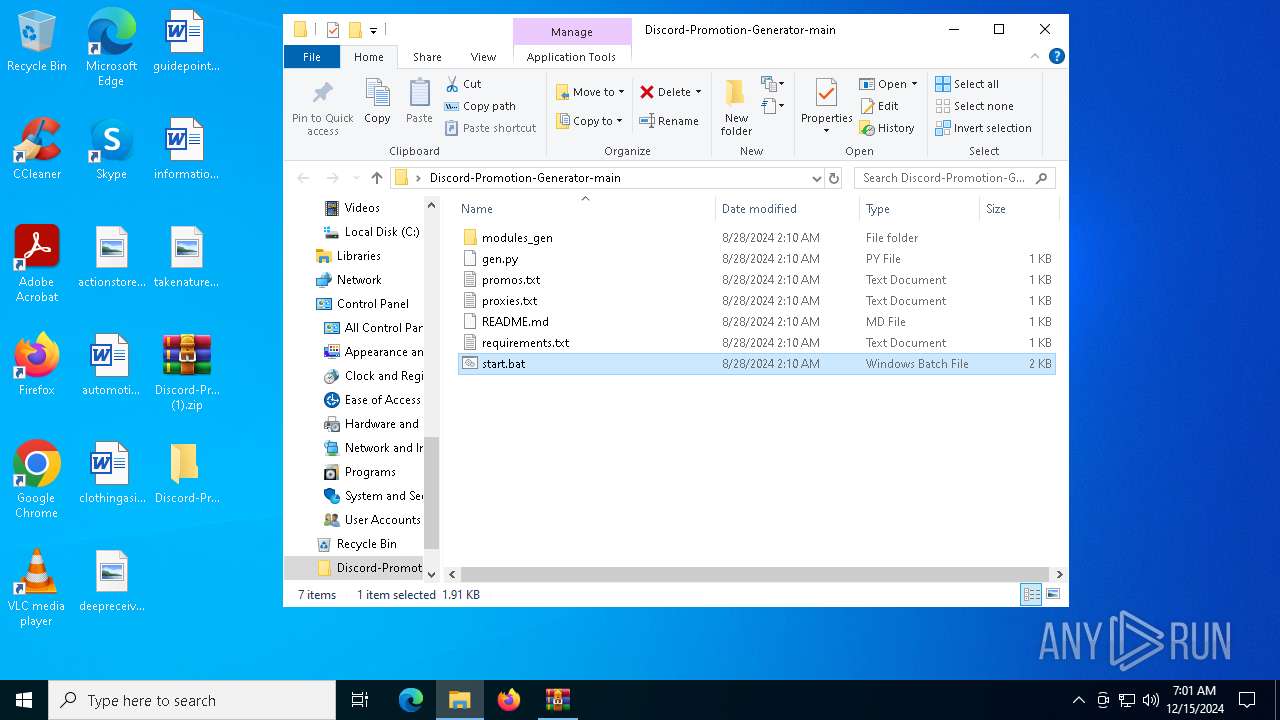
| File name: | Discord-Promotion-Generator-main (1).zip |
| Full analysis: | https://app.any.run/tasks/9e86d22c-fa24-42aa-9af6-76267dad35e2 |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2024, 07:00:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 04B021CAECD6BC17060A7FA198BD2444 |
| SHA1: | 570E911D6388E47DF80970192A41C19EFB987292 |
| SHA256: | C65DD9691BBC93805AC6A1C755000075546843293F5695CF8F8719E0563DB3D0 |
| SSDEEP: | 384:gZYnT6J9sx3bZXBgaIkUOgGNGu54KpQsGk:gunE9erZXPUOgGou54KmBk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 488)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 488)
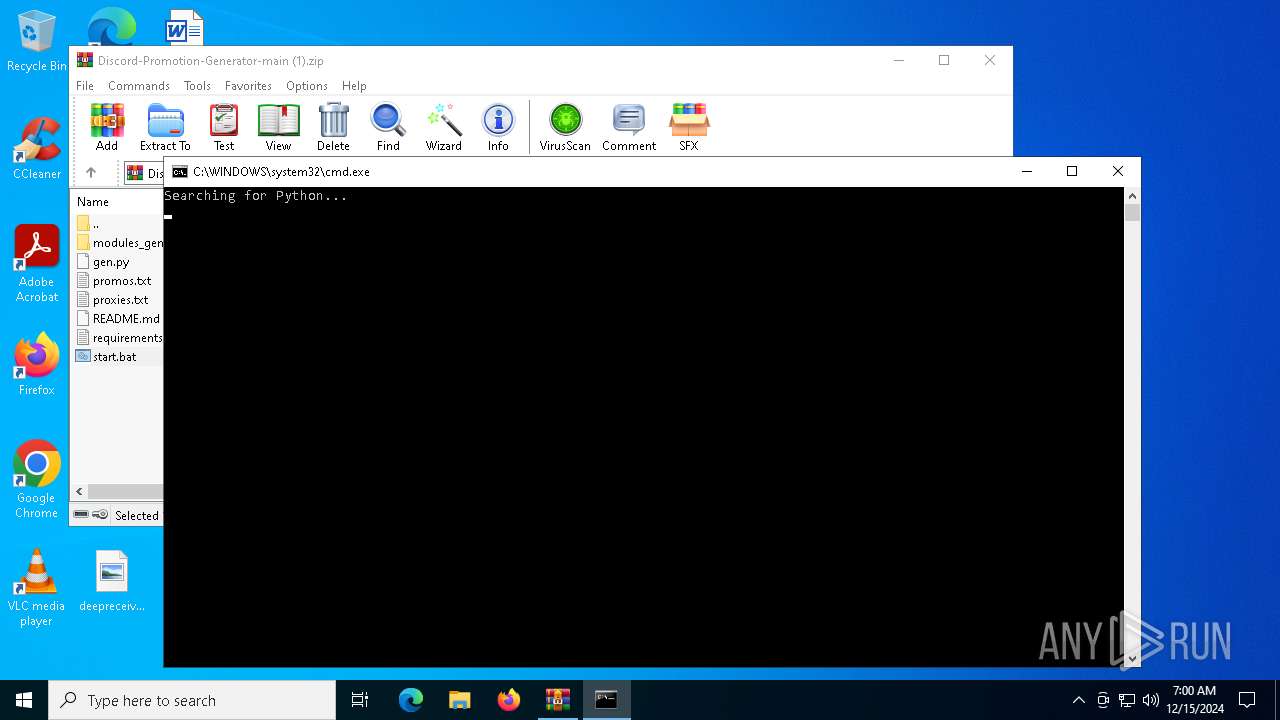
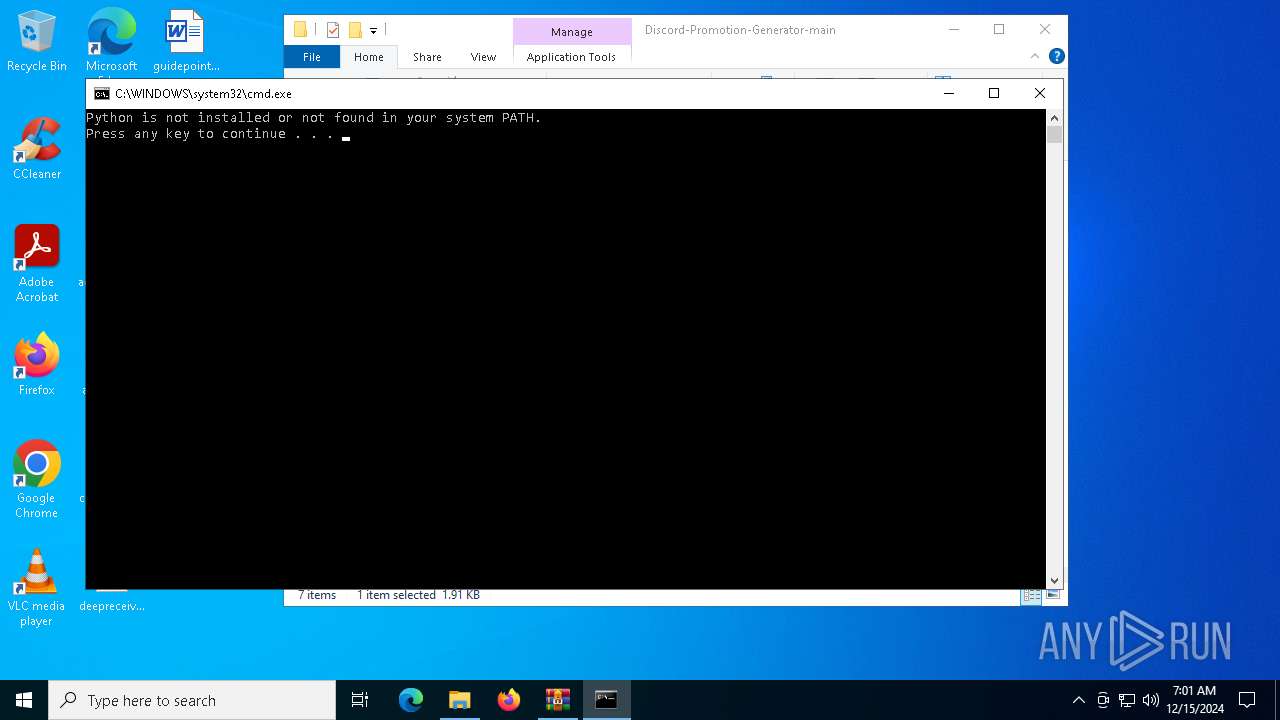
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6276)
- WinRAR.exe (PID: 488)
- cmd.exe (PID: 7064)
Hides command output
- cmd.exe (PID: 6340)
- cmd.exe (PID: 7124)
Application launched itself
- cmd.exe (PID: 6276)
- cmd.exe (PID: 7064)
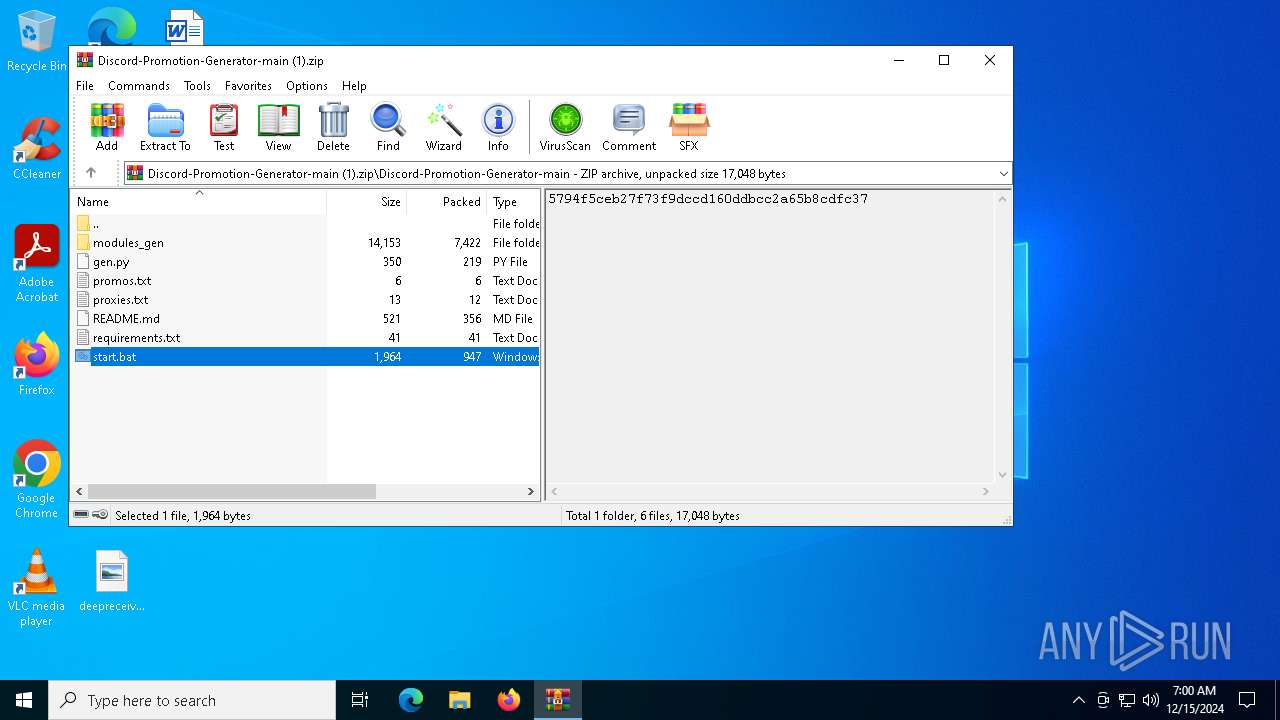
Executing commands from a ".bat" file
- WinRAR.exe (PID: 488)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 488)
Manual execution by a user
- WinRAR.exe (PID: 6664)
- cmd.exe (PID: 7064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:27 19:10:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Discord-Promotion-Generator-main/ |
Total processes
138
Monitored processes
11
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Discord-Promotion-Generator-main (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6276 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa488.34288\start.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | C:\WINDOWS\system32\cmd.exe /c where python 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | where python | C:\Windows\System32\where.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6664 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Discord-Promotion-Generator-main (1).zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6840 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7064 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Discord-Promotion-Generator-main\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7124 | C:\WINDOWS\system32\cmd.exe /c where python 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 844
Read events
1 832
Write events
12
Delete events
0
Modification events
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Discord-Promotion-Generator-main (1).zip | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6664) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
4
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\promos.txt | text | |
MD5:ED19CA99581136D44B35BBB2240A6BF6 | SHA256:AEA52D27230B89CA1B732866AFBE137A98E65100049A56B3293DEF8D5FE7DDA0 | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\modules_gen\__pycache__\session_manager.cpython-311.pyc | binary | |
MD5:BB0BCC56DAD2963276145B90066B07AF | SHA256:AD2656B4AC34EB4FB3AE445D7813A44BFBD409F77CA2ED7AB52BAE7465888FBB | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\modules_gen\promo_generator.py | text | |
MD5:1B8A52CDC7CF8E707DDFF9939B126DEC | SHA256:EC91B10B6D4F333D5B0D3F032618108FDE6F041F8A0168DC3B913A087212B06D | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\README.md | text | |
MD5:F11D2C423CCD498F6B8E51240FBCF05C | SHA256:1EB4E274878F6F568924469142CE25F2C5DE6BFCB56014D3663849D1B654D140 | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\modules_gen\session_manager.py | text | |
MD5:4DF70ACC615F19B90D893FE189EE56BF | SHA256:E01BDD7129808642BD5A9761687C24F72DBDD6409CB42687808297E3D36CDC0B | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\proxies.txt | text | |
MD5:29206AC8A57CA738EA02F16789BF37FC | SHA256:DAF70676E9FDAD5154E5D2C783EE7B578EC32723B8B8A5819EF3A9FC454D9D72 | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\start.bat | text | |
MD5:8B7E6C46BAB2FE7E1C4E3A33C8FA1B79 | SHA256:C78FB7D3EDA7014A84EE4618B3E28B1F5551F8E487B29A7179AEBB219EEB0877 | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\requirements.txt | text | |
MD5:5B6A4911FDA0E682CE27EAD2C8F2A90F | SHA256:48F1C4026AF3187B165DC852D8EBCDAAD8FC5AAEE12EB78BC3F577FDD7CAE4B2 | |||
| 6664 | WinRAR.exe | C:\Users\admin\Desktop\Discord-Promotion-Generator-main\gen.py | text | |
MD5:59873253FE07E222D3258409A0E7ABBE | SHA256:61C0610C84A0C75AEE1F5D97D24CCE2995834F177AA423F9509554017BEC3CEE | |||
| 488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa488.34288\start.bat | text | |
MD5:8B7E6C46BAB2FE7E1C4E3A33C8FA1B79 | SHA256:C78FB7D3EDA7014A84EE4618B3E28B1F5551F8E487B29A7179AEBB219EEB0877 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6540 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6540 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3688 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1488 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.185:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |