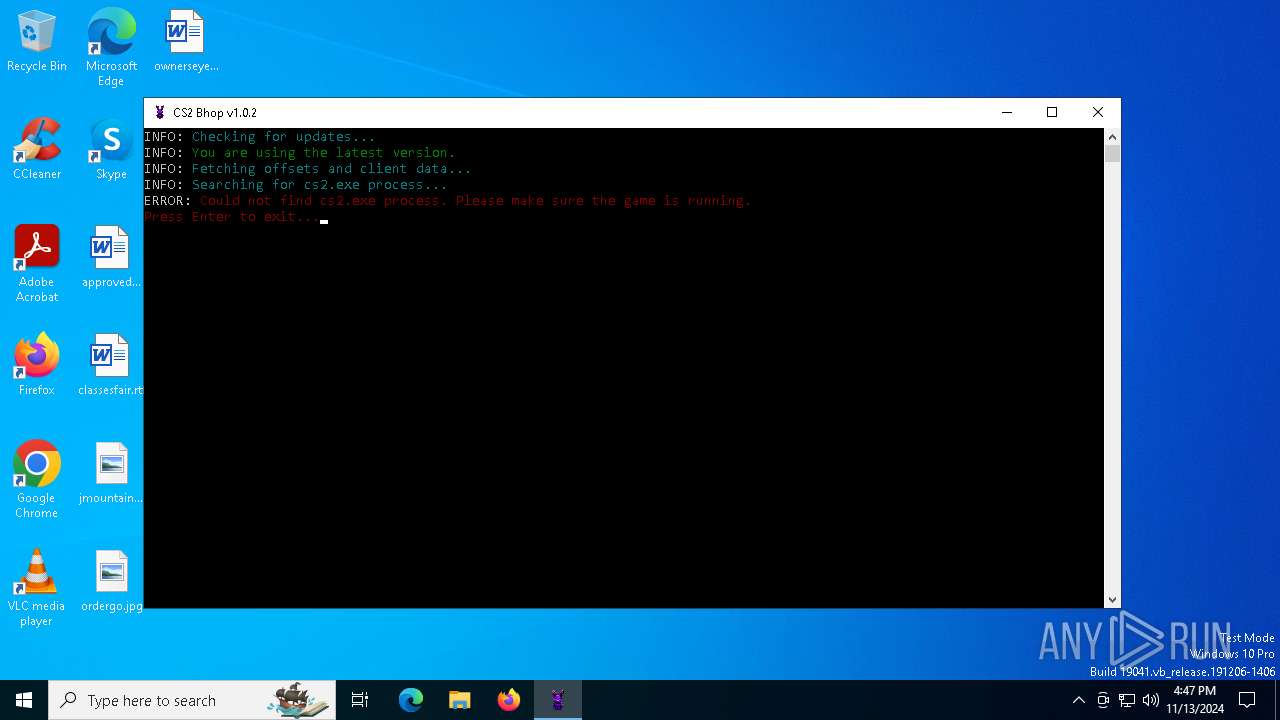
| File name: | CS2.Bhop.exe |
| Full analysis: | https://app.any.run/tasks/8d8f8c45-967c-468e-96ed-2e21cd54fab5 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2024, 16:46:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 6F9758A0A1EFC422F2F2F9CAFEA719FB |
| SHA1: | 5BB110F31C4796373B9A3118CC988D4922798767 |
| SHA256: | C65940B9C0293BB48CEA7B6BD037E21B51438F3742FF825E93A1B04CB21EDC6D |
| SSDEEP: | 98304:JIyDPrEddwfpIclaLYvI9yf+8Gm11Syu4YJbebWn7CvlpaMh3pmV4Cssw/EelmPD:pjZQ8AOkm6k6P43uvnjqB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- CS2.Bhop.exe (PID: 6624)
The process drops C-runtime libraries
- CS2.Bhop.exe (PID: 6624)
Process drops legitimate windows executable
- CS2.Bhop.exe (PID: 6624)
Process drops python dynamic module
- CS2.Bhop.exe (PID: 6624)
Loads Python modules
- CS2.Bhop.exe (PID: 5832)
Executable content was dropped or overwritten
- CS2.Bhop.exe (PID: 6624)
INFO
Reads the computer name
- CS2.Bhop.exe (PID: 5832)
- CS2.Bhop.exe (PID: 6624)
Checks supported languages
- CS2.Bhop.exe (PID: 6624)
- CS2.Bhop.exe (PID: 5832)
Create files in a temporary directory
- CS2.Bhop.exe (PID: 6624)
Checks proxy server information
- CS2.Bhop.exe (PID: 5832)
Creates files or folders in the user directory
- CS2.Bhop.exe (PID: 5832)
PyInstaller has been detected (YARA)
- CS2.Bhop.exe (PID: 6624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:03 07:16:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.2.0 |
| ProductVersionNumber: | 1.0.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | ItsJesewe |
| FileDescription: | CS2 Bhop |
| FileVersion: | 1.0.2.0 |
| InternalName: | CS2 Bhop |
| LegalCopyright: | © ItsJesewe. MIT License. |
| OriginalFileName: | CS2 Bhop.exe |
| ProductName: | CS2 Bhop |
| ProductVersion: | 1.0.2.0 |
Total processes
130
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5832 | "C:\Users\admin\AppData\Local\Temp\CS2.Bhop.exe" | C:\Users\admin\AppData\Local\Temp\CS2.Bhop.exe | CS2.Bhop.exe | ||||||||||||
User: admin Company: ItsJesewe Integrity Level: MEDIUM Description: CS2 Bhop Version: 1.0.2.0 Modules
| |||||||||||||||
| 6216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CS2.Bhop.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6624 | "C:\Users\admin\AppData\Local\Temp\CS2.Bhop.exe" | C:\Users\admin\AppData\Local\Temp\CS2.Bhop.exe | explorer.exe | ||||||||||||
User: admin Company: ItsJesewe Integrity Level: MEDIUM Description: CS2 Bhop Version: 1.0.2.0 Modules
| |||||||||||||||
Total events
440
Read events
440
Write events
0
Delete events
0
Modification events
Executable files
28
Suspicious files
1
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_multiprocessing.pyd | executable | |
MD5:EB859FC7F54CBA118A321440AD088096 | SHA256:14BDD15D60B9D6141009AEEDC606007C42B46C779A523D21758E57CF126DC2A4 | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_decimal.pyd | executable | |
MD5:CEA3B419C7CA87140A157629C6DBD299 | SHA256:95B9850E6FB335B235589DD1348E007507C6B28E332C9ABB111F2A0035C358E5 | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_wmi.pyd | executable | |
MD5:BED7B0CED98FA065A9B8FE62E328713F | SHA256:5818679010BB536A3D463EEEE8CE203E880A8CD1C06BF1CB6C416AB0DC024D94 | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_queue.pyd | executable | |
MD5:7D91DD8E5F1DBC3058EA399F5F31C1E6 | SHA256:76BBA42B1392DC57A867AEF385B990FA302A4F1DCF453705AC119C9C98A36E8D | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_socket.pyd | executable | |
MD5:E43AED7D6A8BCD9DDFC59C2D1A2C4B02 | SHA256:2C2A6A6BA360E38F0C2B5A53B4626F833A3111844D95615EBF35BE0E76B1EF7A | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_lzma.pyd | executable | |
MD5:8CFBAFE65D6E38DDE8E2E8006B66BB3E | SHA256:6D548DB0AB73291F82CF0F4CA9EC0C81460185319C8965E829FAEACAE19444FF | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_ssl.pyd | executable | |
MD5:6A2B0F8F50B47D05F96DEFF7883C1270 | SHA256:68DAD60FF6FB36C88EF1C47D1855517BFE8DE0F5DDEA0F630B65B622A645D53A | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\base_library.zip | compressed | |
MD5:605CF0C0EF63FE301E94CBC073A503B8 | SHA256:730A7BC70FDC6F06751D8F96604A5106563E0954602B0413F086956DBD3E9D5C | |||
| 6624 | CS2.Bhop.exe | C:\Users\admin\AppData\Local\Temp\_MEI66242\_asyncio.pyd | executable | |
MD5:CC0F232F2A8A359DEE29A573667E6D77 | SHA256:7A5C88CE496BAFDF31A94AE6D70B017070703BC0A7DA1DFAE7C12B21BB61030D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7112 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5640 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5832 | CS2.Bhop.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
5832 | CS2.Bhop.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
api.github.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |