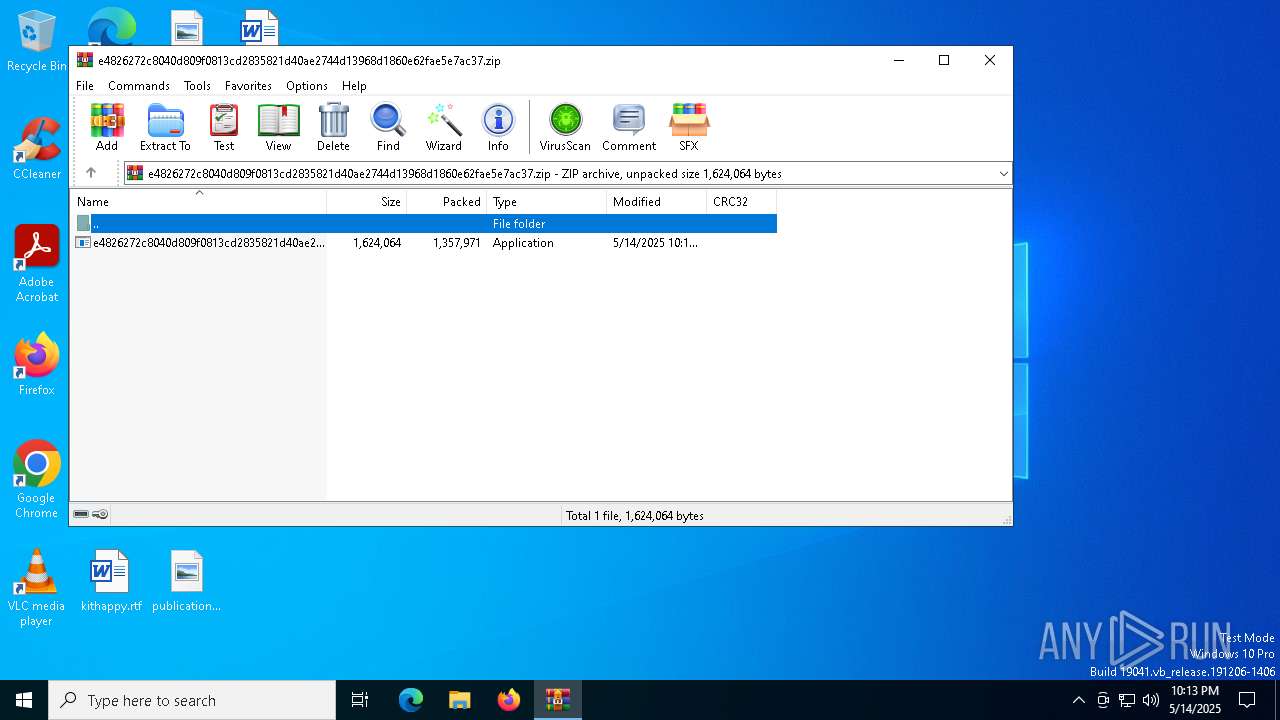
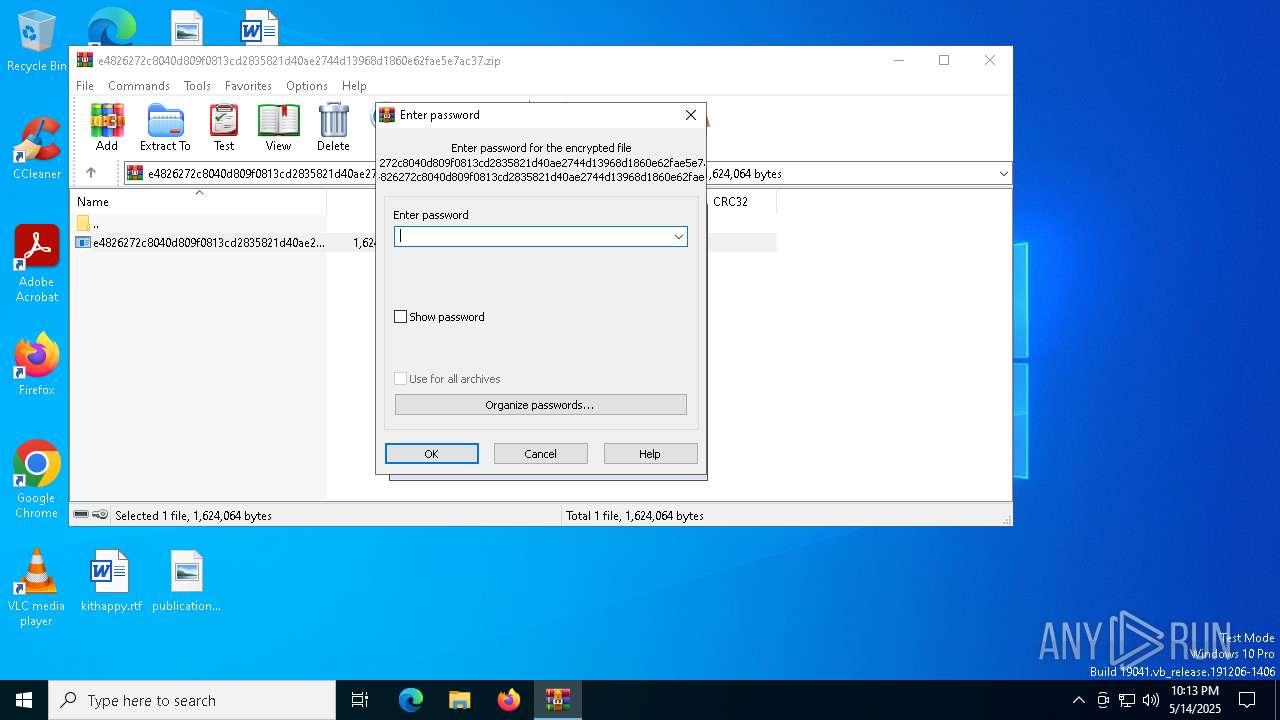
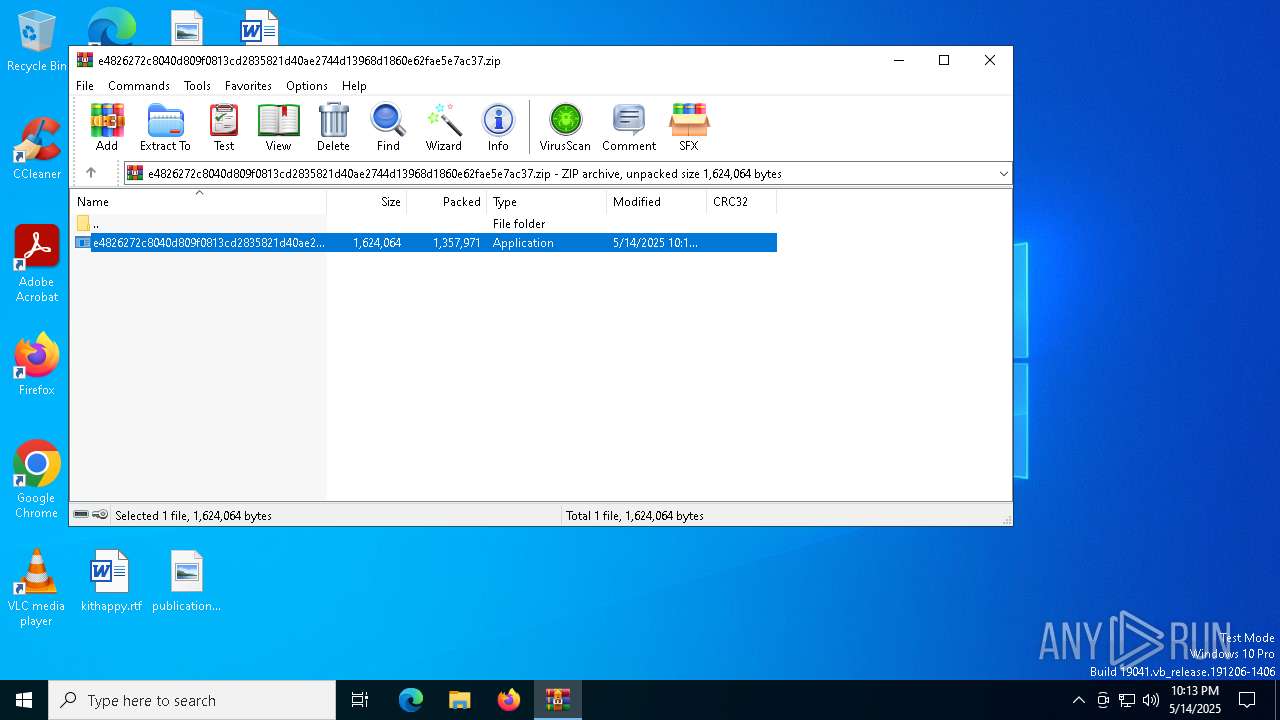
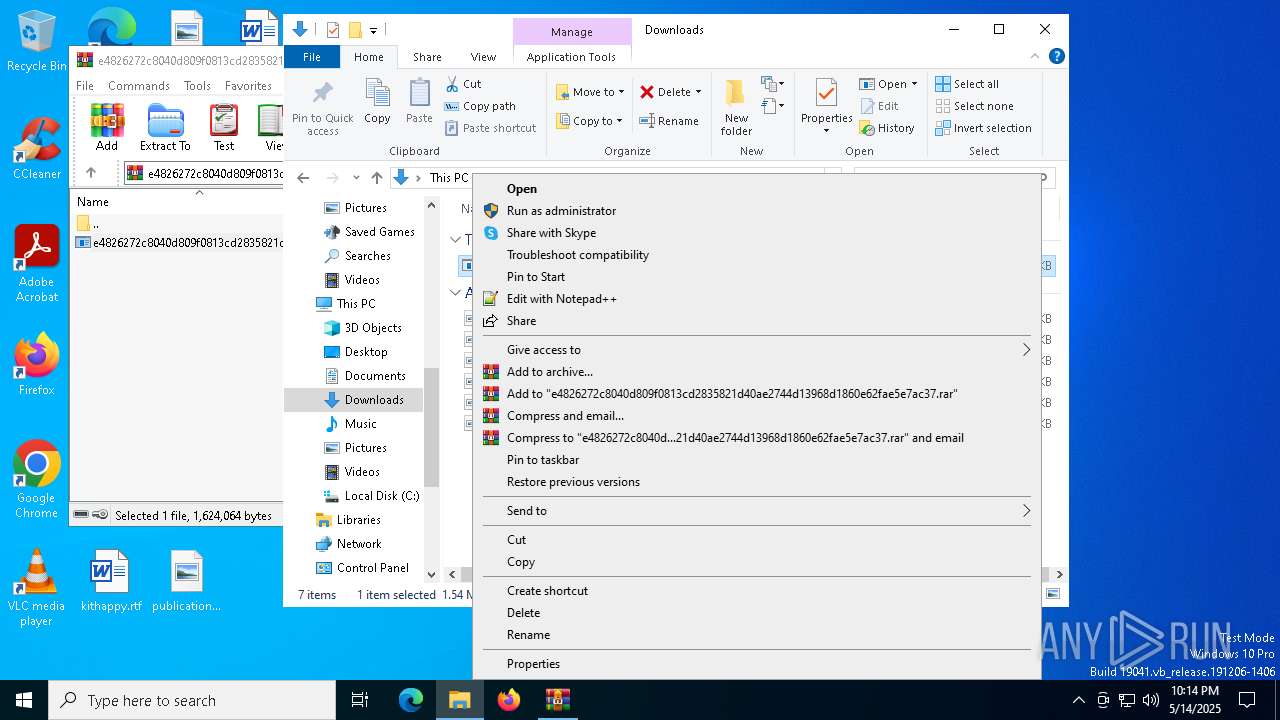
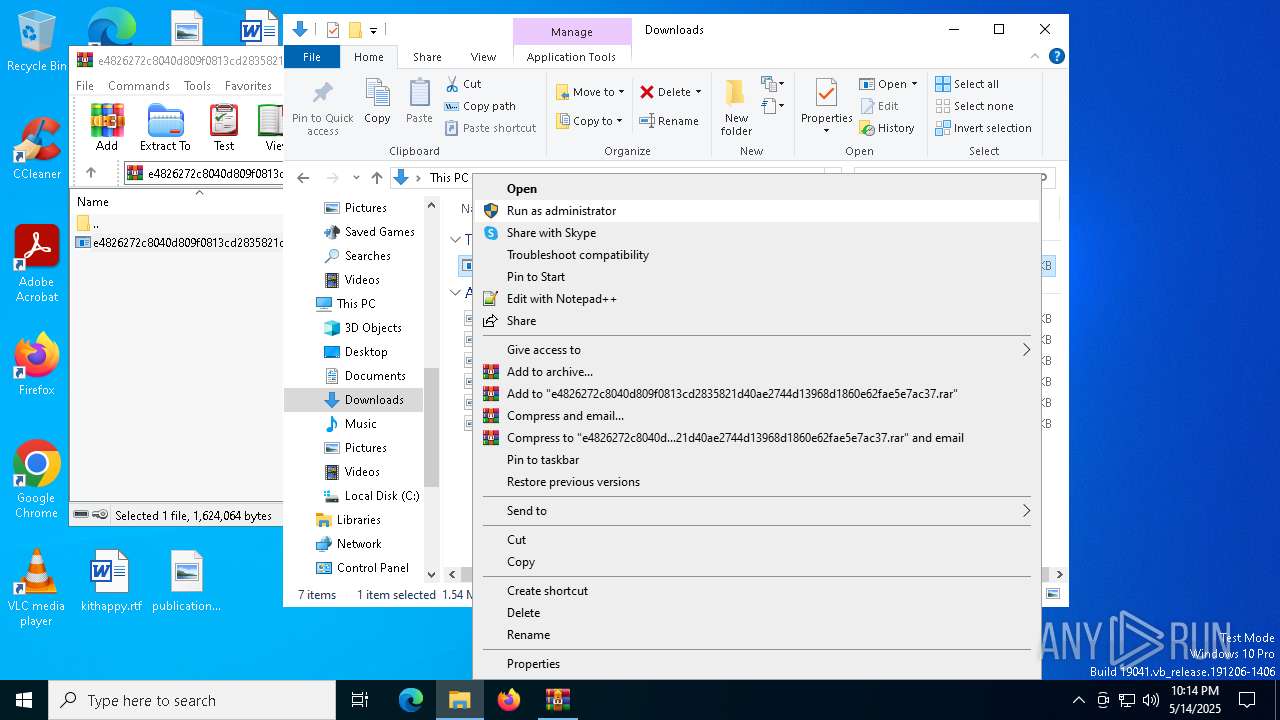
| File name: | e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.zip |
| Full analysis: | https://app.any.run/tasks/18b1036f-8b29-46cf-97b9-14731a3d75a1 |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 22:13:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 4C3BF6AB2DC464DDB1B3BF1D1B2A5988 |
| SHA1: | 1DA1784CD74148E5908462843797933A46E02083 |
| SHA256: | C6572F63F290B4F2E314A5AA4433AA973653A4DBCDF3B819B5A9158A27B7C9BB |
| SSDEEP: | 49152:o+K0UMwOveQf+bKHPC/LWdjOsuWyYx2D3VBmWLjXQ/xD8R4TK0P2ZpvGatlYlCGD:4Mw6mbKHaD0cdYx2D3VBmWnA/xo0A5G9 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7356)
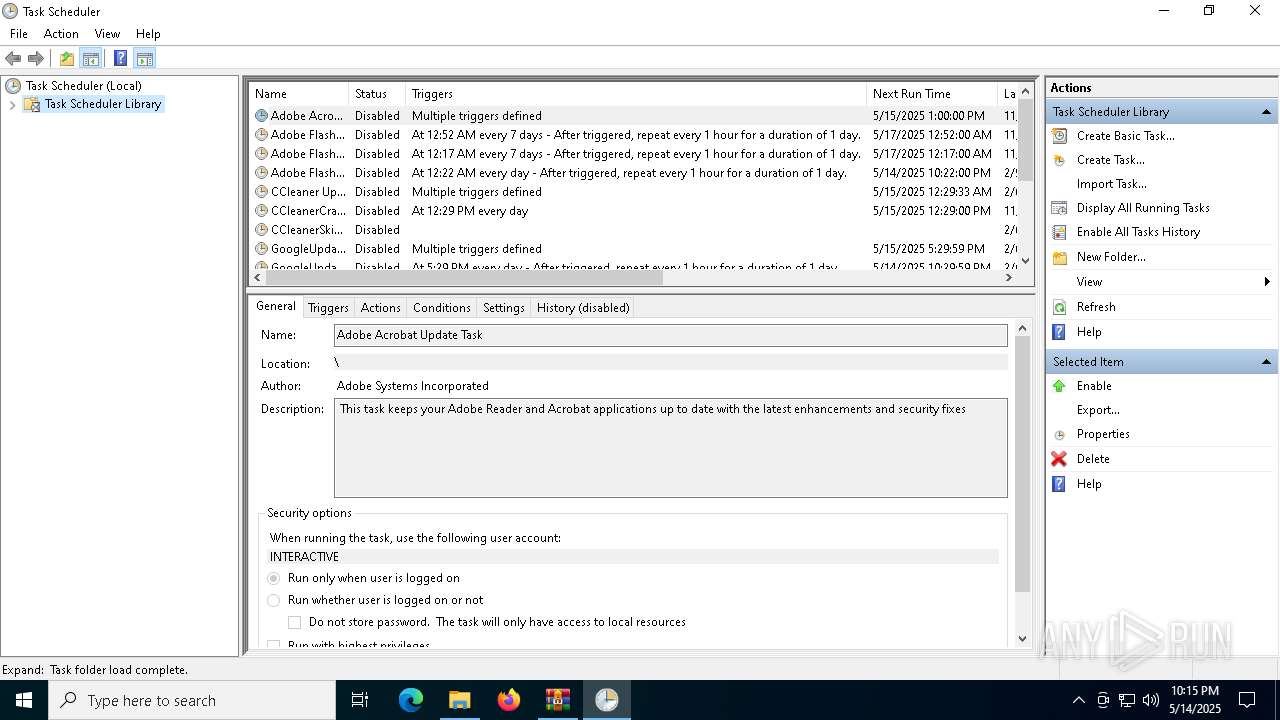
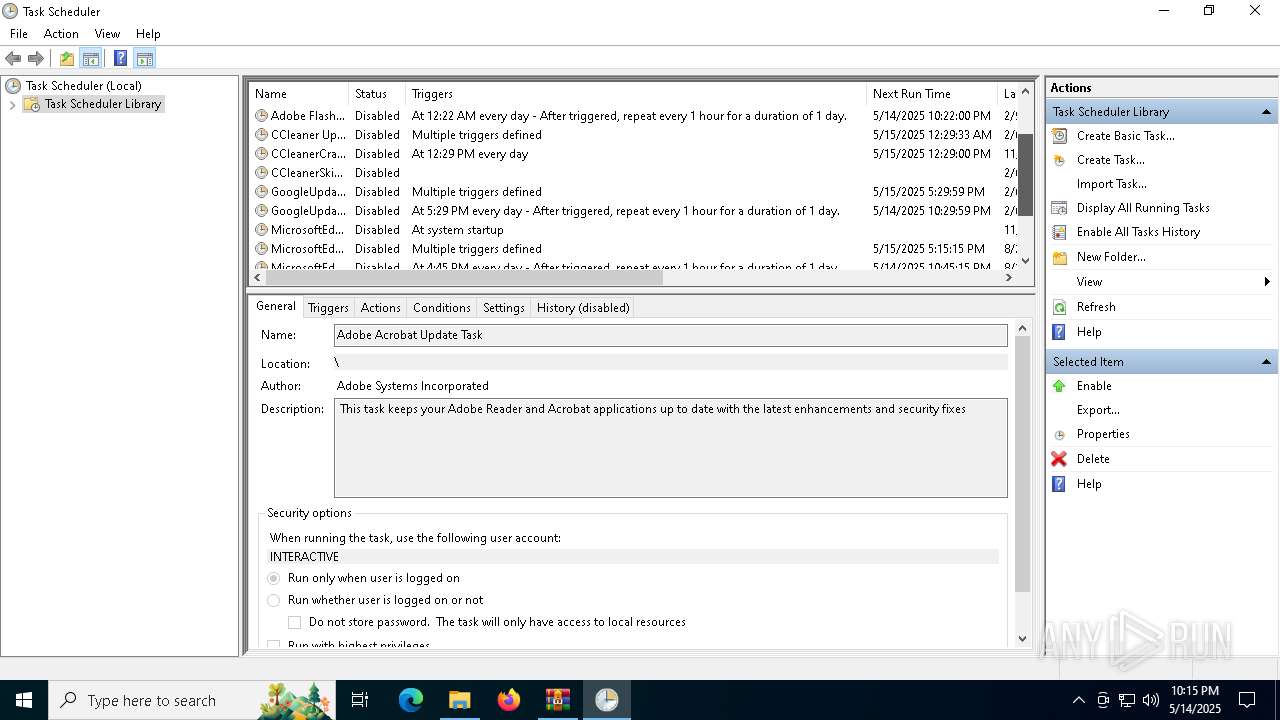
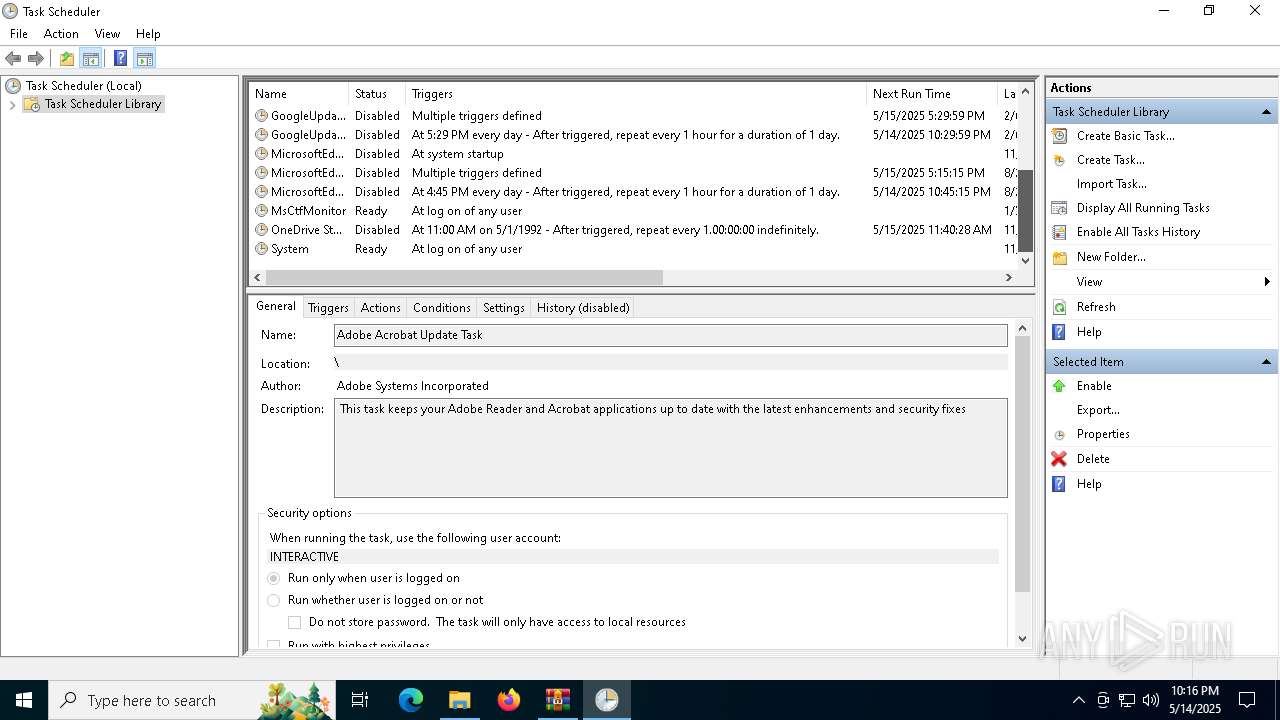
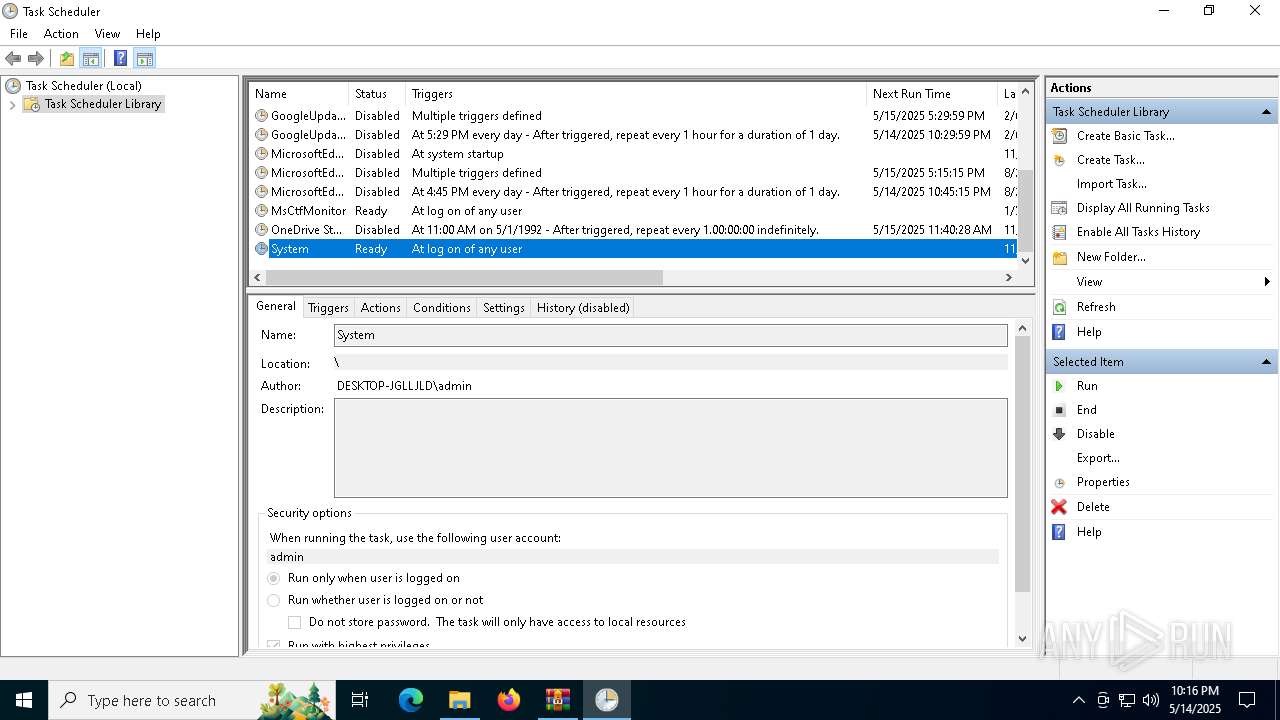
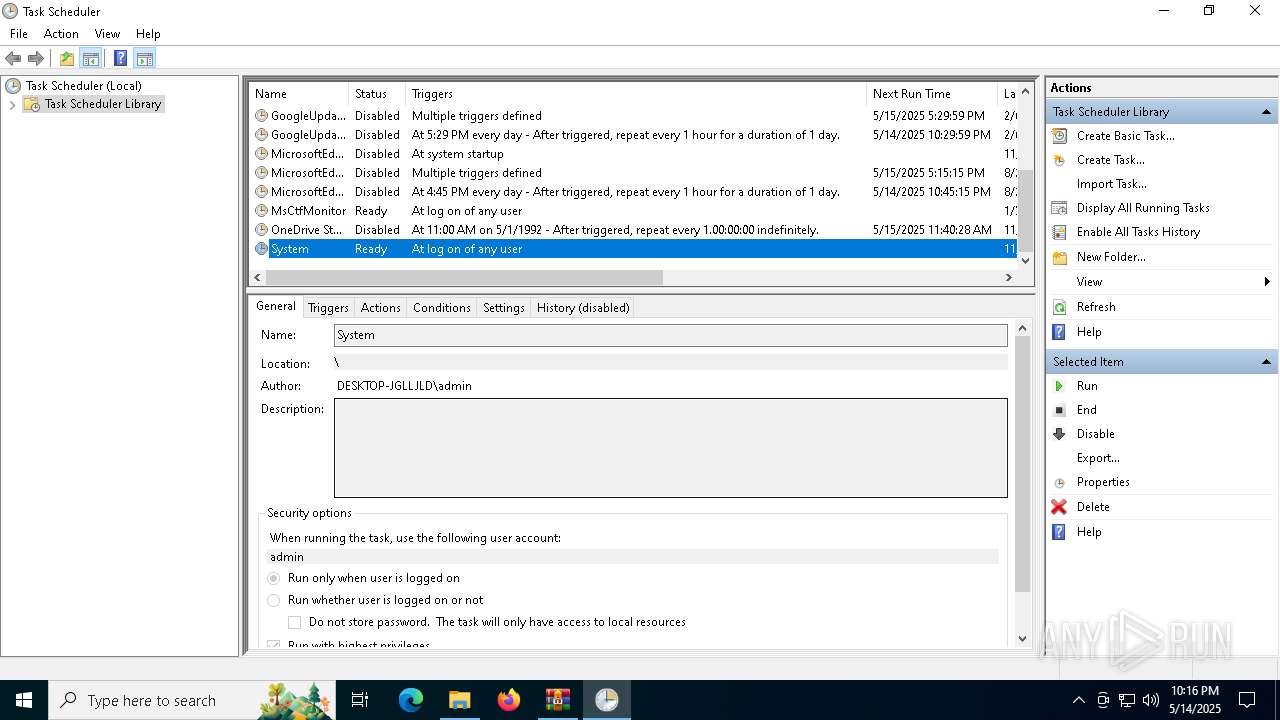
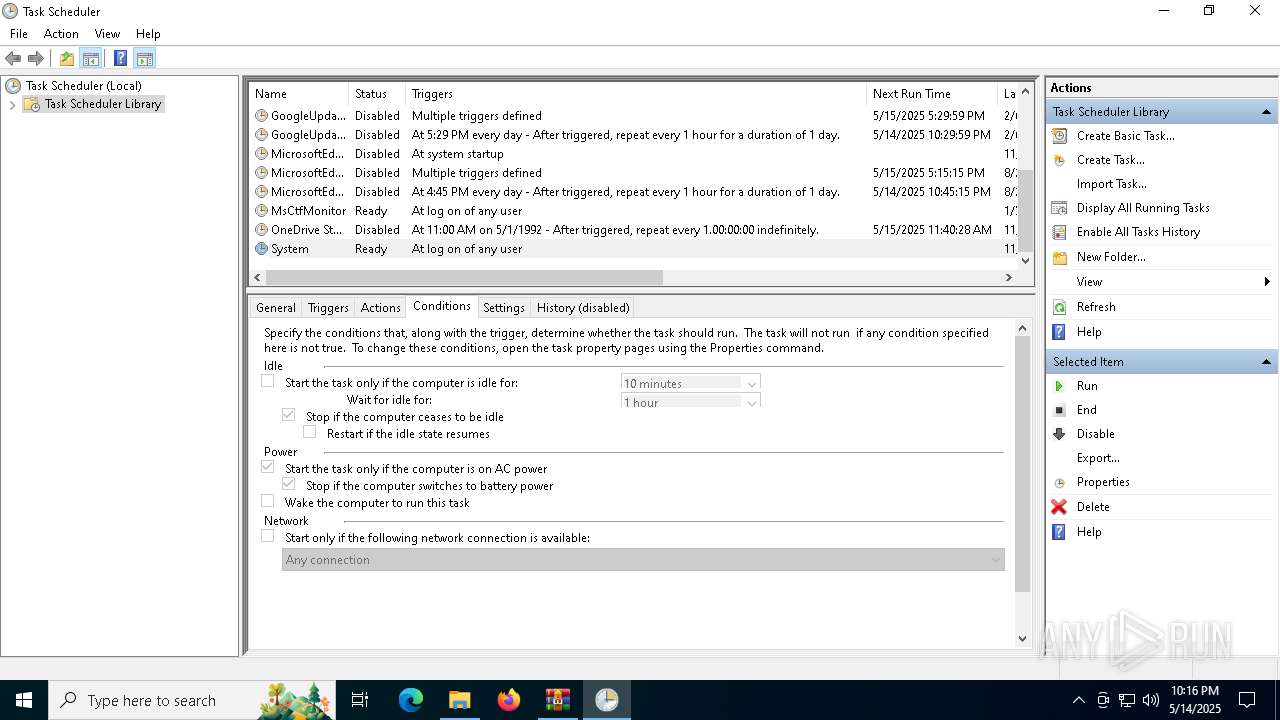
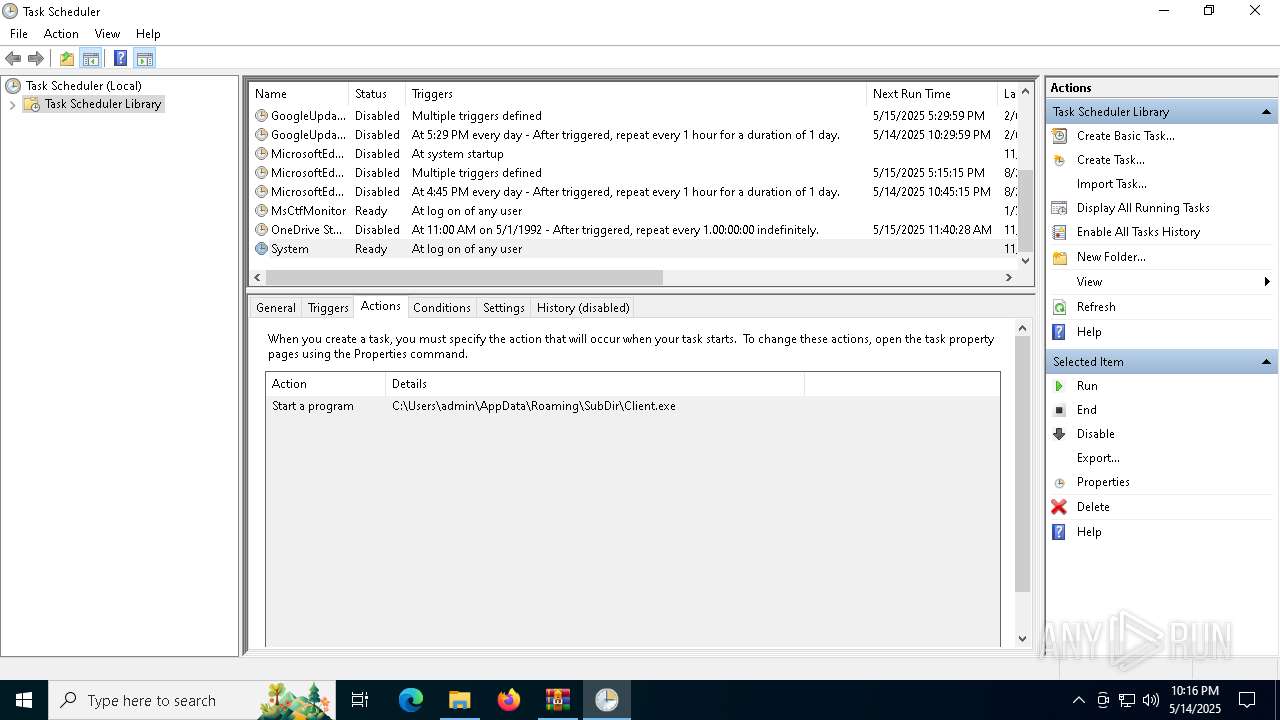
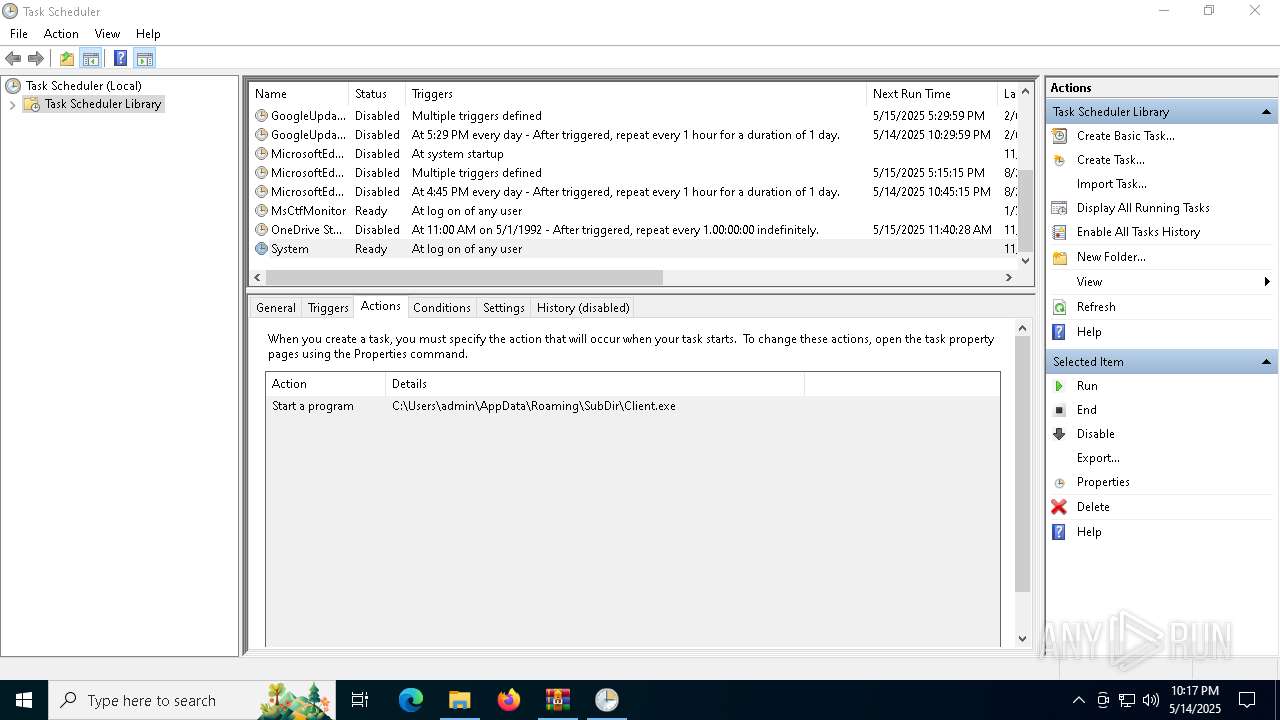
Uses Task Scheduler to autorun other applications
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
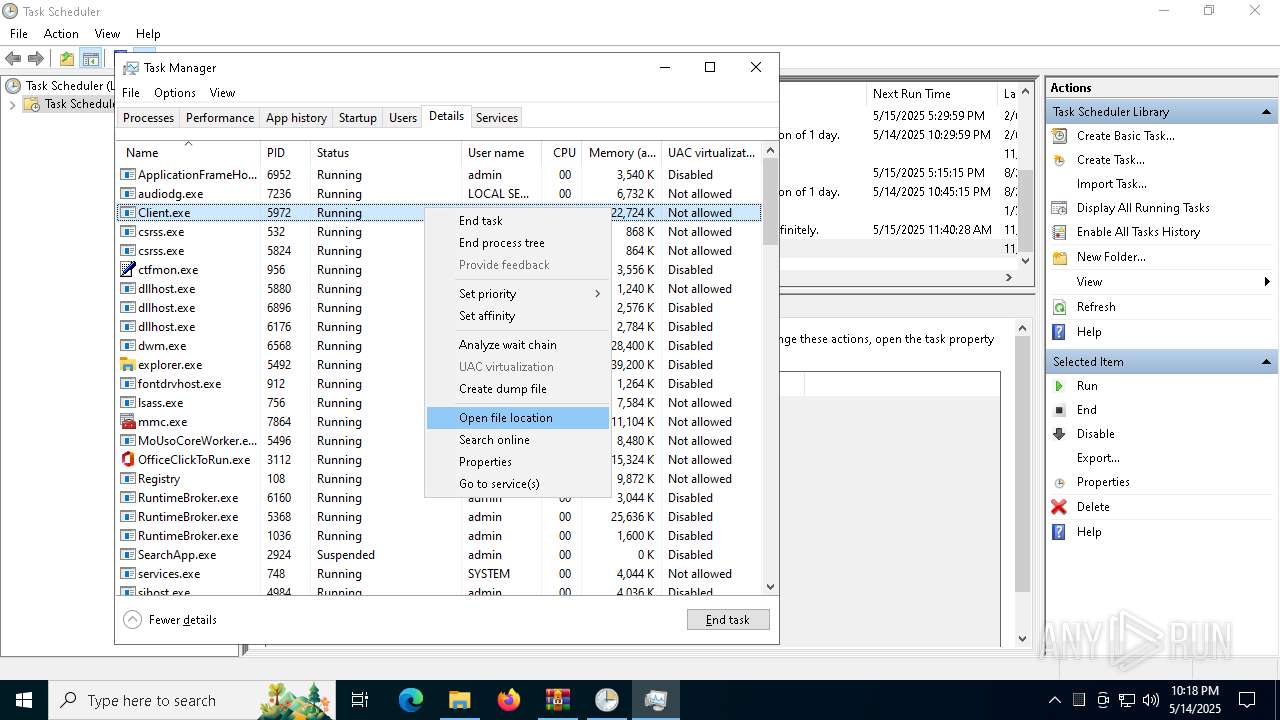
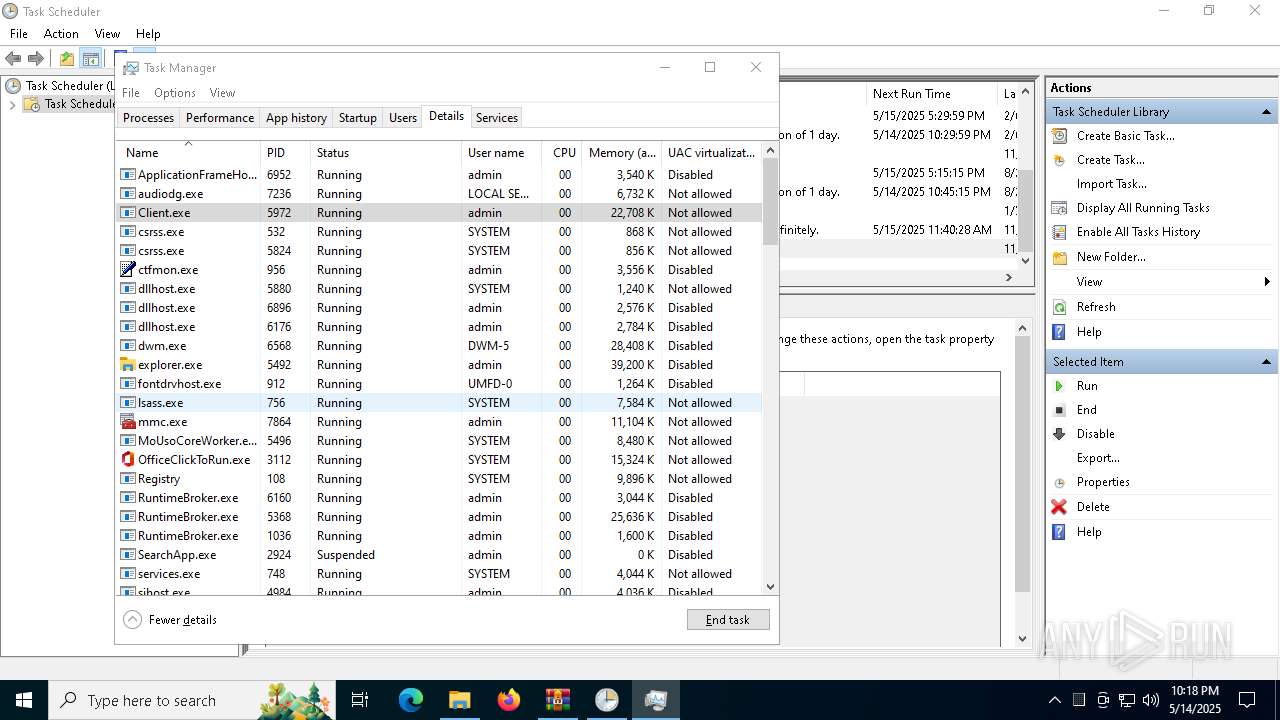
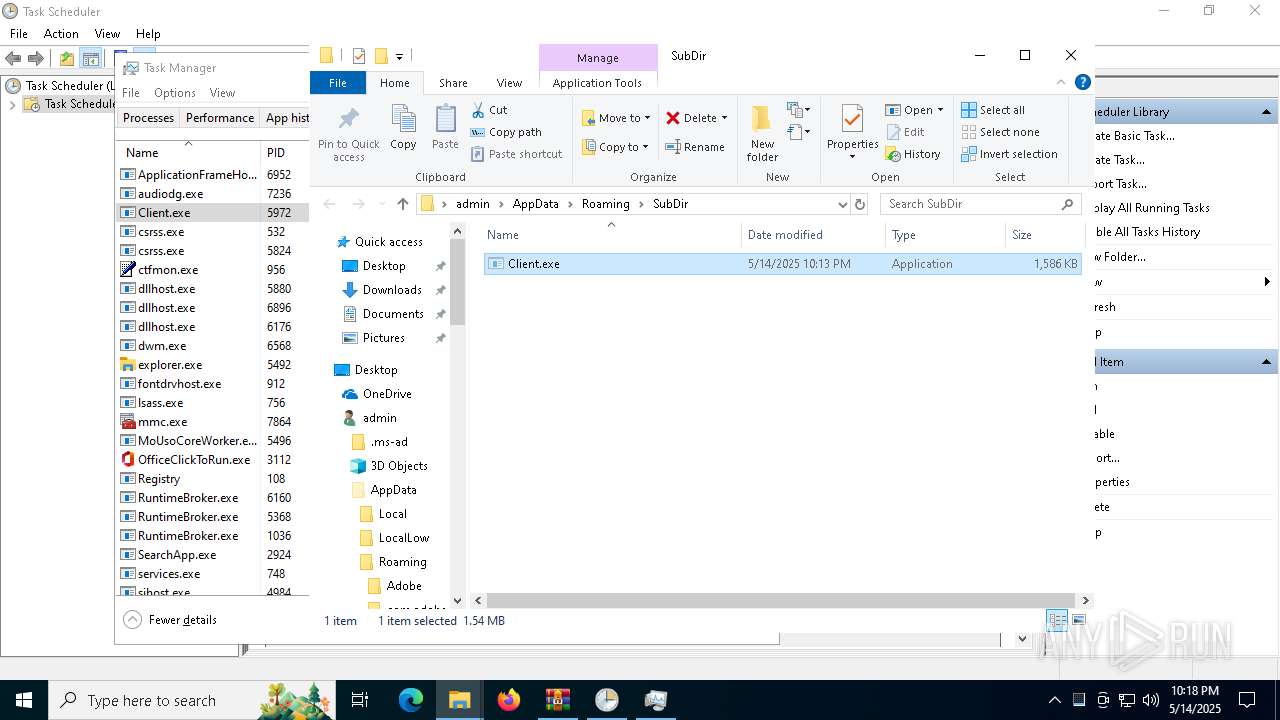
- Client.exe (PID: 5972)
SUSPICIOUS
Starts itself from another location
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
Executable content was dropped or overwritten
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
There is functionality for taking screenshot (YARA)
- Client.exe (PID: 5972)
Found regular expressions for crypto-addresses (YARA)
- Client.exe (PID: 5972)
Connects to unusual port
- Client.exe (PID: 5972)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2196)
INFO
Manual execution by a user
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- mmc.exe (PID: 7804)
- mmc.exe (PID: 7864)
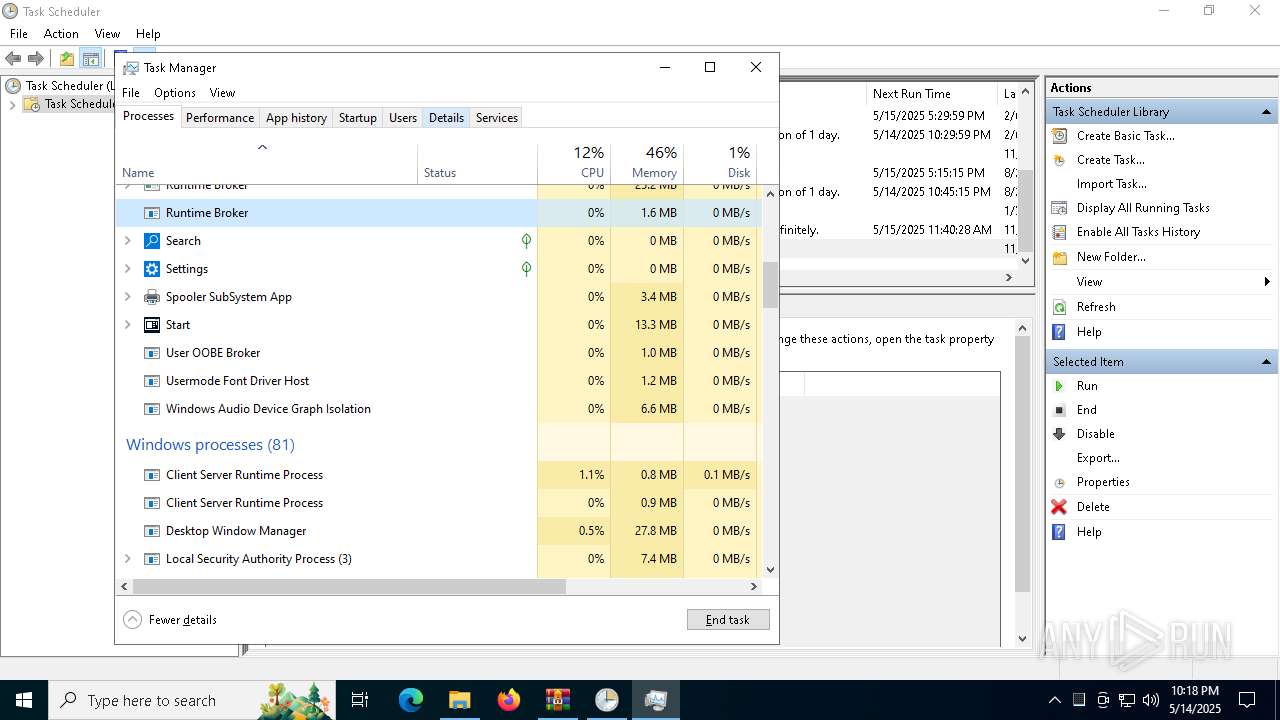
- Taskmgr.exe (PID: 4436)
- Taskmgr.exe (PID: 6724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7356)
Creates files or folders in the user directory
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- Client.exe (PID: 5972)
Checks supported languages
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- Client.exe (PID: 5972)
Reads the machine GUID from the registry
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- Client.exe (PID: 5972)
Reads the computer name
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- Client.exe (PID: 5972)
Reads Environment values
- e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe (PID: 5868)
- Client.exe (PID: 5972)
Checks proxy server information
- slui.exe (PID: 1312)
Reads the software policy settings
- slui.exe (PID: 7524)
- slui.exe (PID: 1312)
Reads security settings of Internet Explorer
- mmc.exe (PID: 7864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:14 22:13:14 |
| ZipCRC: | 0x3743127c |
| ZipCompressedSize: | 1357971 |
| ZipUncompressedSize: | 1624064 |
| ZipFileName: | e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe |
Total processes
154
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "schtasks" /create /tn "System" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4436 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | "schtasks" /create /tn "System" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
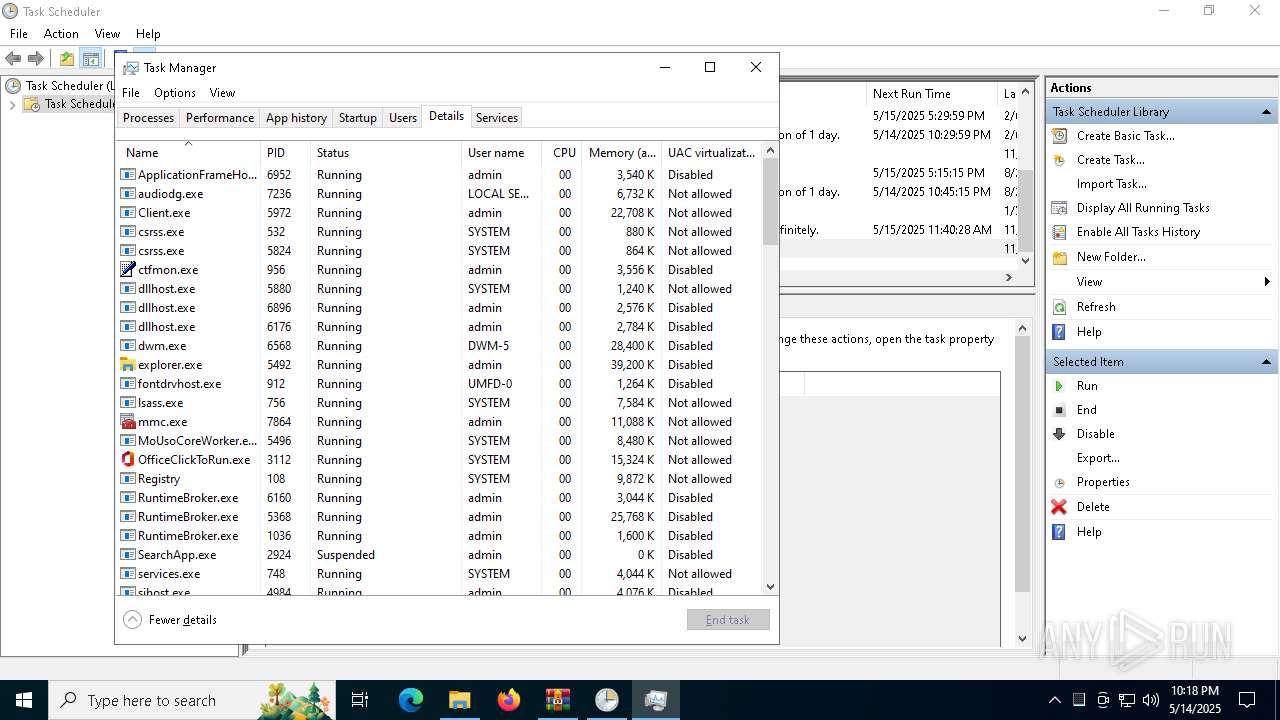
| 5868 | "C:\Users\admin\Downloads\e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe" | C:\Users\admin\Downloads\e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Version: 1.6.0 Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.6.0 Modules
| |||||||||||||||
| 6724 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 865
Read events
7 829
Write events
22
Delete events
14
Modification events
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
Executable files
2
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4436 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5972 | Client.exe | C:\Users\admin\AppData\Roaming\Logs\2025-05-14 | binary | |
MD5:879756021319D55C7EA455DB100816E0 | SHA256:7598CD1475BF70BF42F2628B15710BEC1005EFD720A3CEBDD481ADDBD64790D9 | |||
| 7356 | WinRAR.exe | C:\Users\admin\Downloads\e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe | executable | |
MD5:C123B58147122786BAACC6961B3D2318 | SHA256:E4826272C8040D809F0813CD2835821D40AE2744D13968D1860E62FAE5E7AC37 | |||
| 5868 | e4826272c8040d809f0813cd2835821d40ae2744d13968d1860e62fae5e7ac37.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:C123B58147122786BAACC6961B3D2318 | SHA256:E4826272C8040D809F0813CD2835821D40AE2744D13968D1860E62FAE5E7AC37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
288
DNS requests
35
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8124 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8124 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
alexnikolov-51855.portmap.io |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO DNS Query to a Reverse Proxy Service Observed |
2196 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |