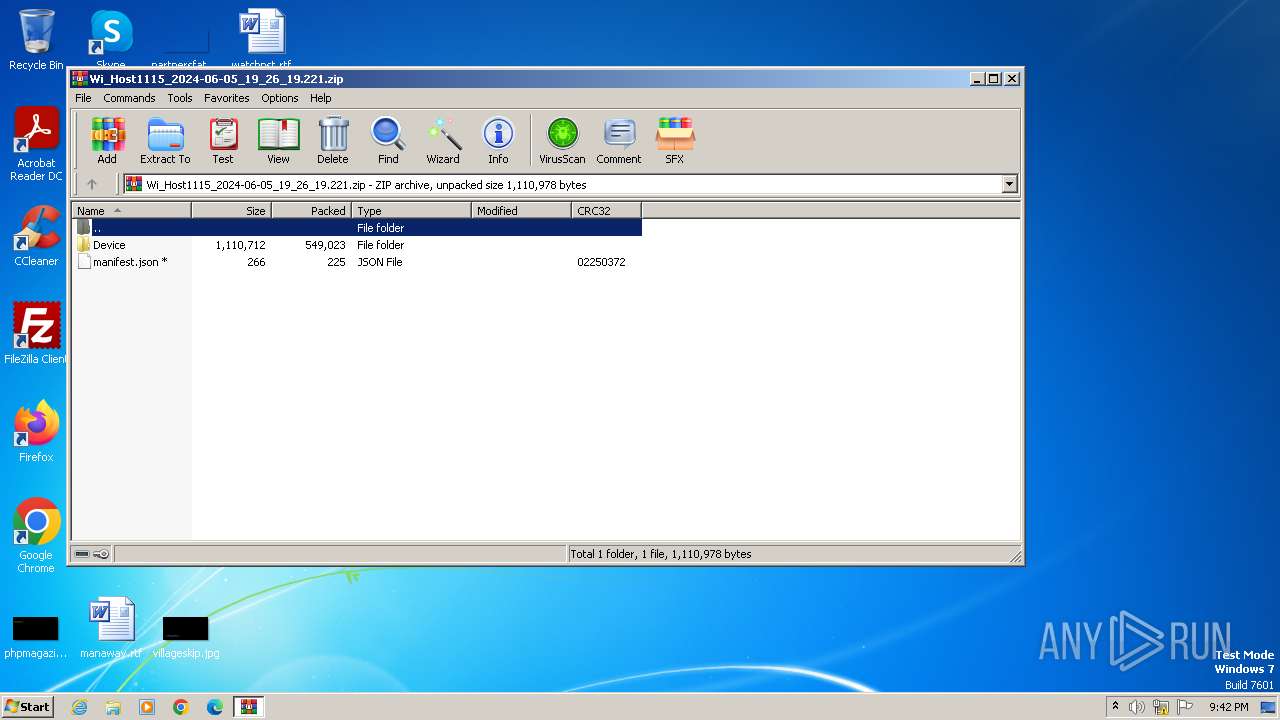
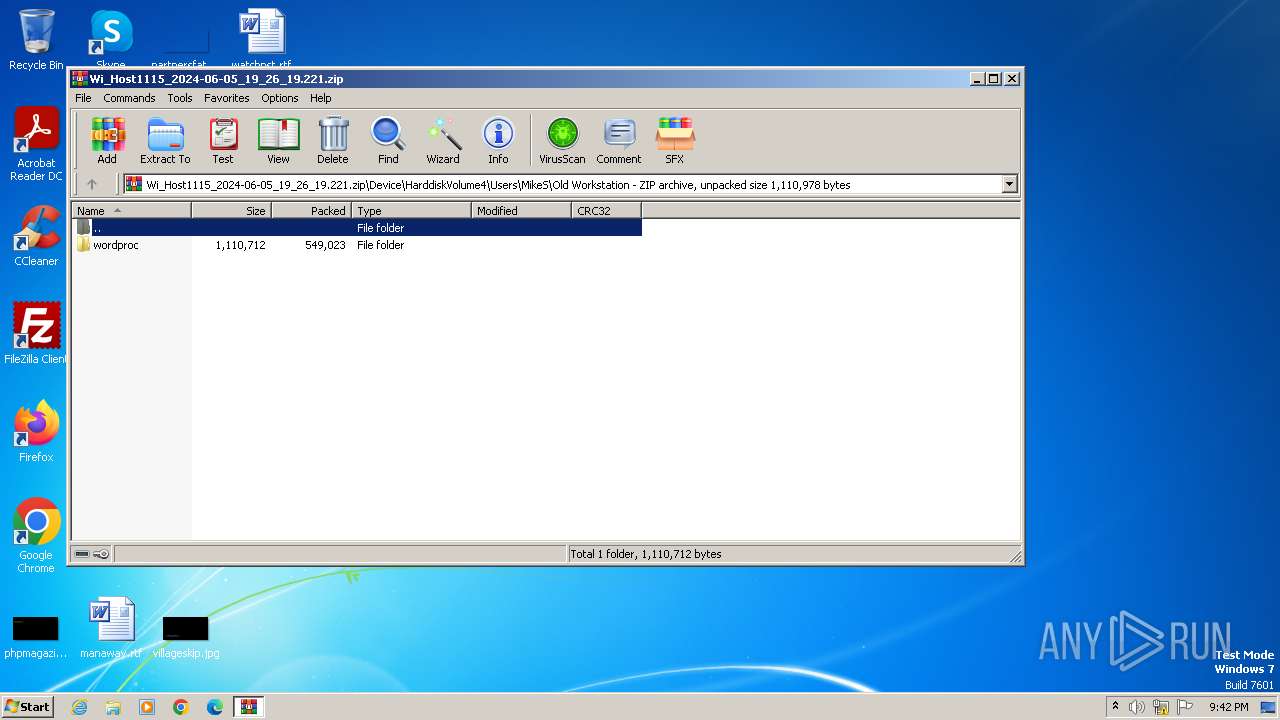
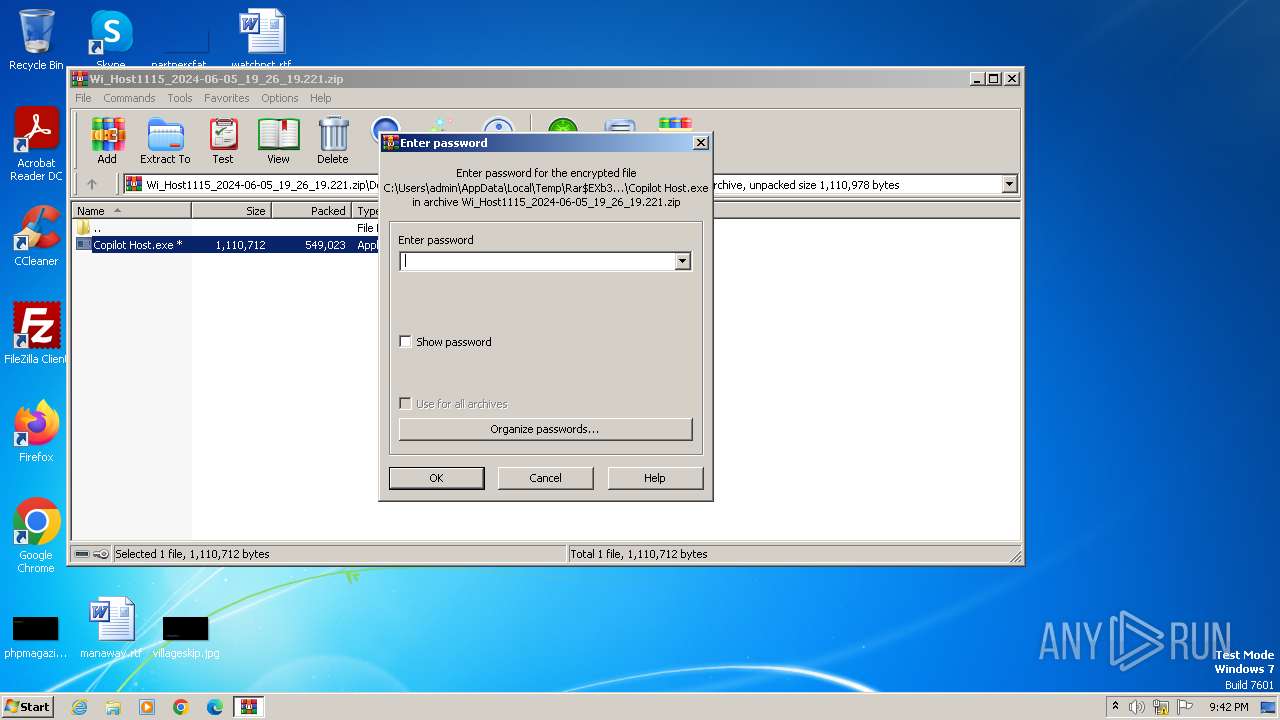
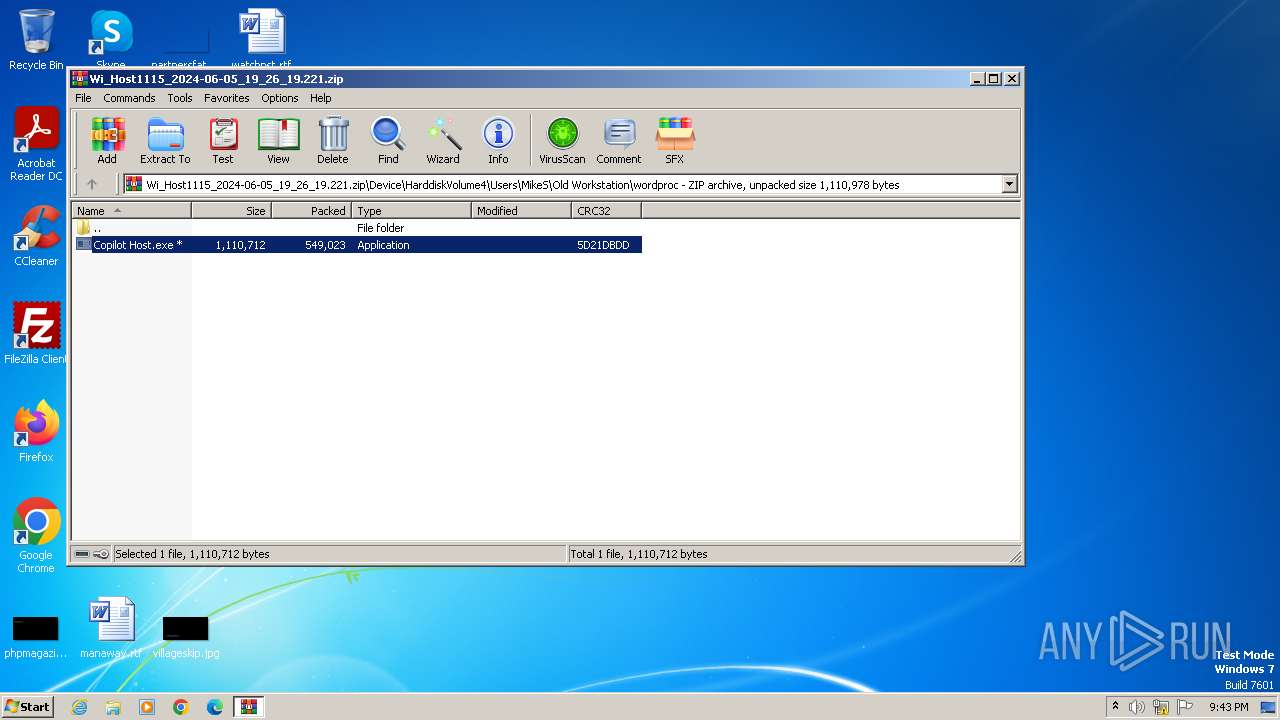
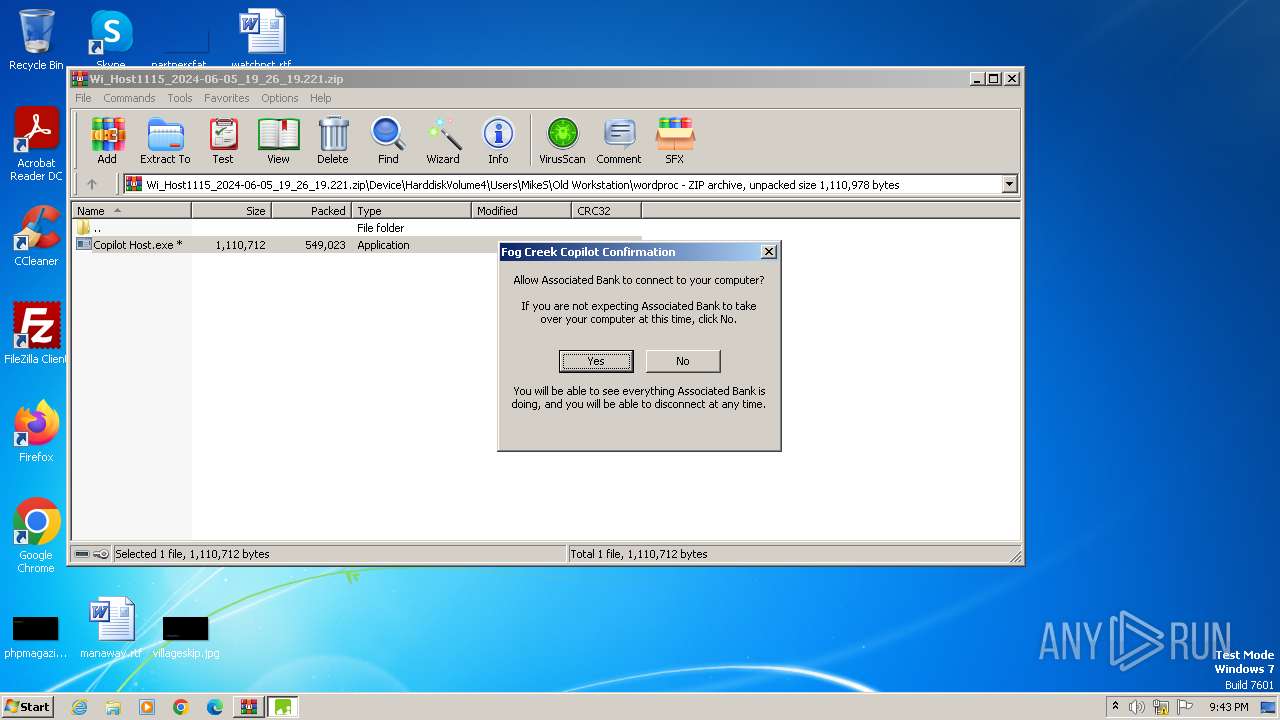
| File name: | Wi_Host1115_2024-06-05_19_26_19.221.zip |
| Full analysis: | https://app.any.run/tasks/93b61815-6dcc-4f98-85bf-1928bccef243 |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2024, 20:42:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F057204F97CCE228AD5E5E5F890425AB |
| SHA1: | D20C217FA0CAE1861DFA7FFC61596555100F588E |
| SHA256: | C63B425204BCA7A8444A0B999D5EFA90F265A3D6152B5FBF2FDE7BA2B50A2ECD |
| SSDEEP: | 24576:sDFafbokfhjp960KGNKnHRYiBqcLkl4sB0s5bM9QXHFidPRbZZw5urgk:sDFafbokfhjX60KGNKnxYiBqcLkl4sB+ |
MALICIOUS
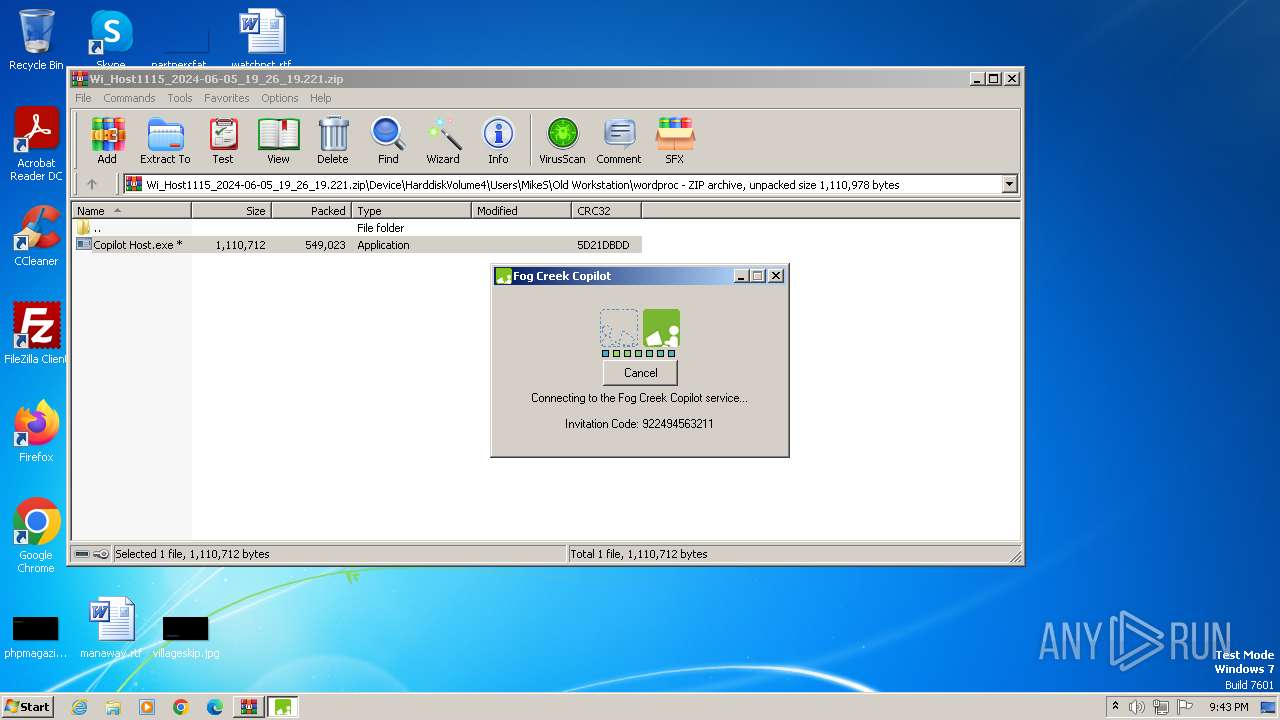
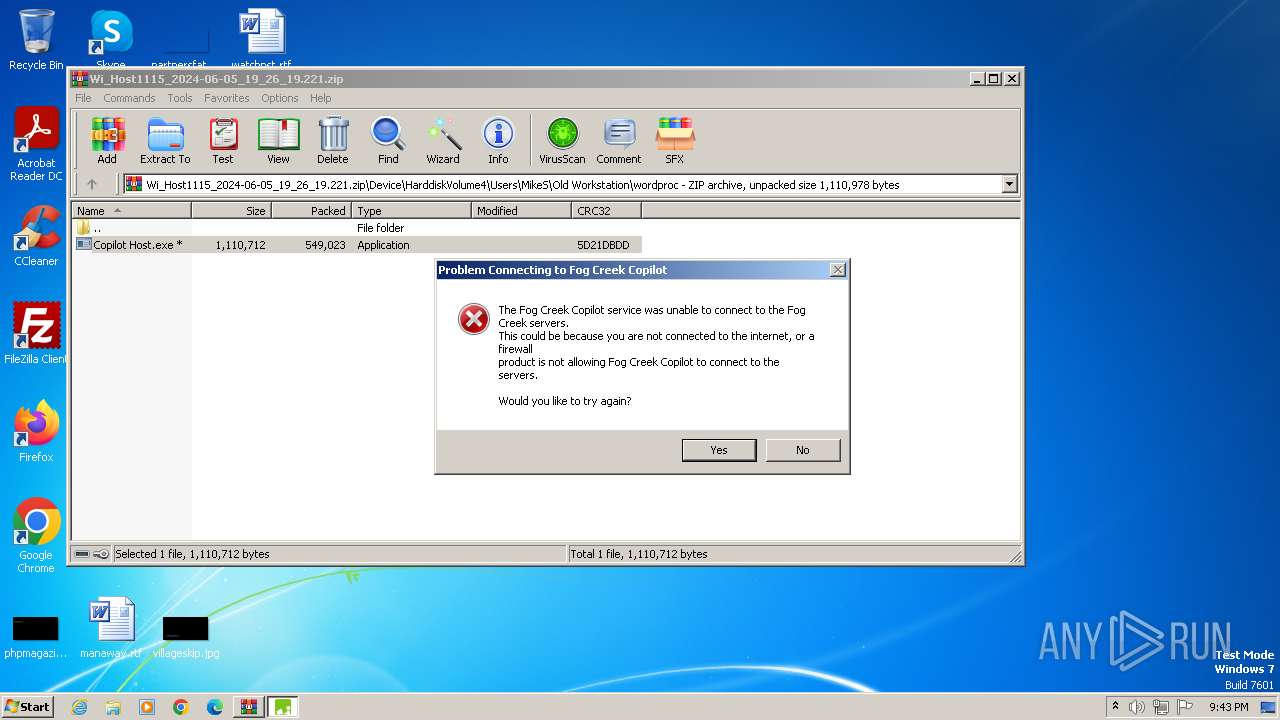
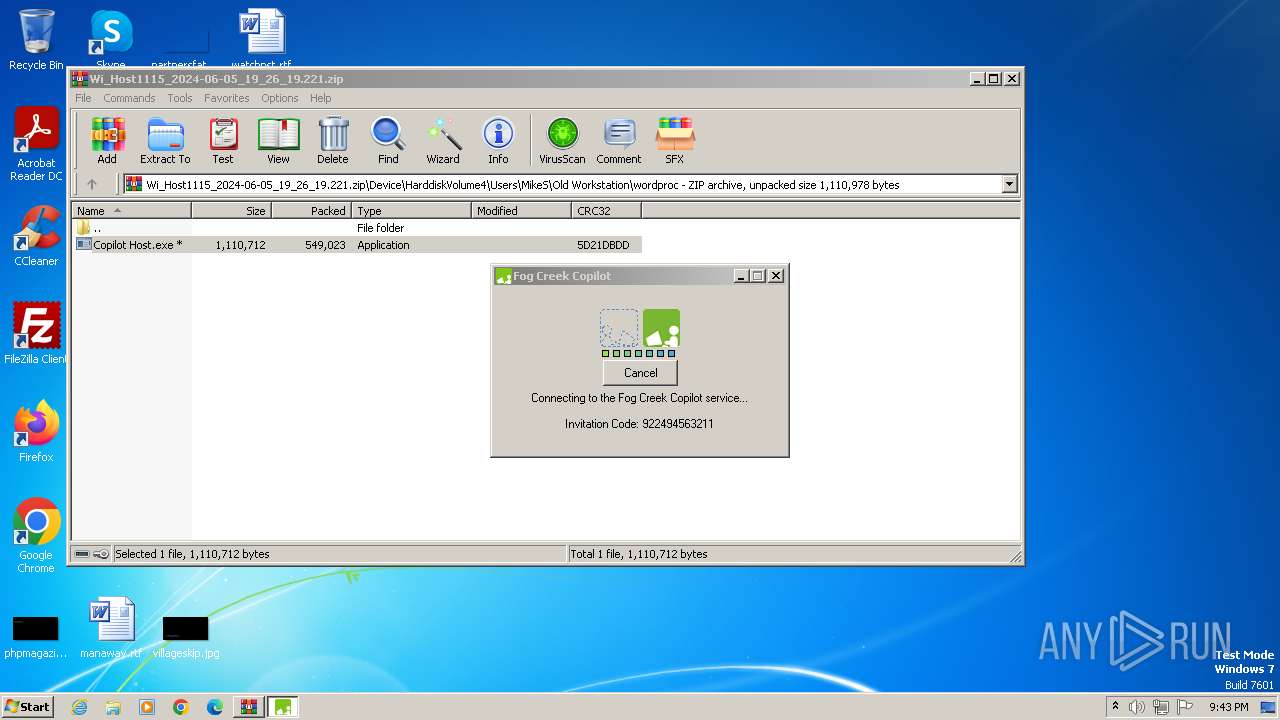
Drops the executable file immediately after the start
- Copilot Host.exe (PID: 1136)
- HostShell.exe (PID: 1580)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3988)
- Copilot Host.exe (PID: 1136)
- HostShell.exe (PID: 1580)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3988)
- Copilot Host.exe (PID: 1136)
Reads the Internet Settings
- Copilot Host.exe (PID: 1136)
- FogCreekCopilotHost.exe (PID: 660)
Reads settings of System Certificates
- Copilot Host.exe (PID: 1136)
Checks Windows Trust Settings
- Copilot Host.exe (PID: 1136)
Adds/modifies Windows certificates
- Copilot Host.exe (PID: 1136)
Executable content was dropped or overwritten
- Copilot Host.exe (PID: 1136)
- HostShell.exe (PID: 1580)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3988)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3988)
Checks supported languages
- Copilot Host.exe (PID: 1136)
- HostShell.exe (PID: 1580)
- FogCreekCopilotHost.exe (PID: 660)
- wmpnscfg.exe (PID: 1236)
Reads the computer name
- Copilot Host.exe (PID: 1136)
- wmpnscfg.exe (PID: 1236)
- FogCreekCopilotHost.exe (PID: 660)
Checks proxy server information
- Copilot Host.exe (PID: 1136)
- FogCreekCopilotHost.exe (PID: 660)
Reads the machine GUID from the registry
- Copilot Host.exe (PID: 1136)
- FogCreekCopilotHost.exe (PID: 660)
Reads the software policy settings
- Copilot Host.exe (PID: 1136)
Create files in a temporary directory
- Copilot Host.exe (PID: 1136)
- HostShell.exe (PID: 1580)
- FogCreekCopilotHost.exe (PID: 660)
Creates files or folders in the user directory
- Copilot Host.exe (PID: 1136)
Manual execution by a user
- wmpnscfg.exe (PID: 1236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x5d21dbdd |
| ZipCompressedSize: | 549023 |
| ZipUncompressedSize: | 1110712 |
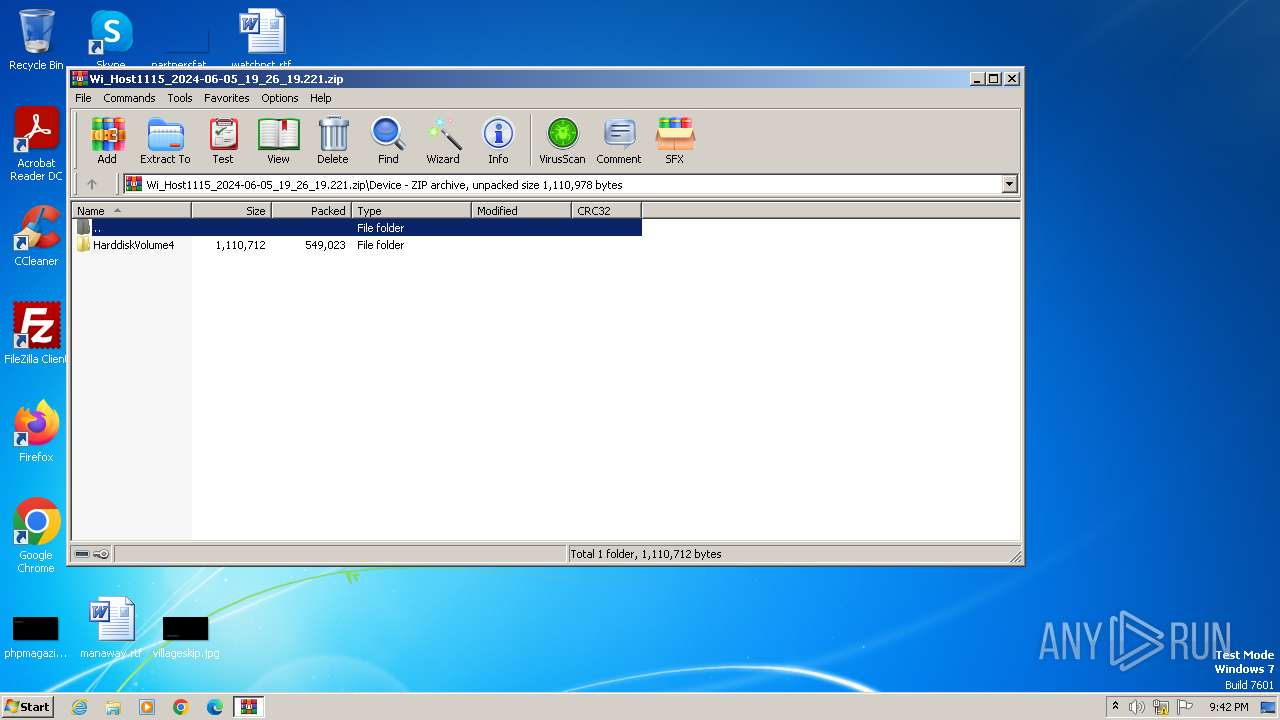
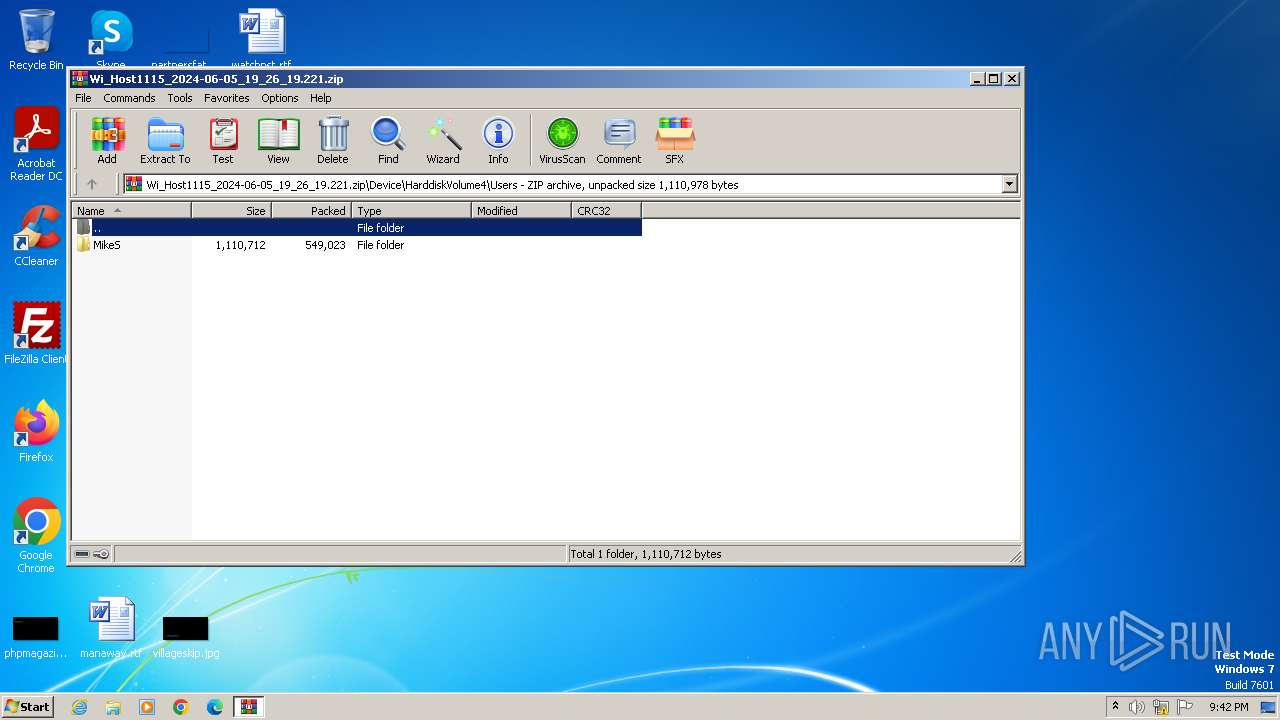
| ZipFileName: | Device/HarddiskVolume4/Users/MikeS/Old Workstation/wordproc/Copilot Host.exe |
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | FogCreekCopilotHost.exe [C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe | C:\Users\admin\AppData\Local\Temp\FogCreekCopilotHost.exe | HostShell.exe | ||||||||||||
User: admin Company: Fog Creek Software Integrity Level: HIGH Description: Fog Creek Copilot Host Version: 3, 0, 0, 0 Modules
| |||||||||||||||
| 1136 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1580 | C:\Users\admin\AppData\Local\Temp\HostShell.exe [C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe | C:\Users\admin\AppData\Local\Temp\HostShell.exe | Copilot Host.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3988 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Wi_Host1115_2024-06-05_19_26_19.221.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4036 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\Device\HarddiskVolume4\Users\MikeS\Old Workstation\wordproc\Copilot Host.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
10 630
Read events
10 491
Write events
127
Delete events
12
Modification events
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Wi_Host1115_2024-06-05_19_26_19.221.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
8
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:49AEBF8CBD62D92AC215B2923FB1B9F5 | SHA256:B33EFCB95235B98B48508E019AFA4B7655E80CF071DEFABD8B2123FC8B29307F | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\Local\Temp\Tar83C9.tmp | binary | |
MD5:4EA6026CF93EC6338144661BF1202CD1 | SHA256:8EFBC21559EF8B1BCF526800D8070BAAD42474CE7198E26FA771DBB41A76B1D8 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3988.48709\manifest.json | ini | |
MD5:DC77E341B8308990EA7E8CCB9DA51312 | SHA256:DB237C126053A0AC54872253CB65A899CE9F75797C7D2C09CB16E25F4A91268D | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\Local\Temp\Cab83C8.tmp | compressed | |
MD5:49AEBF8CBD62D92AC215B2923FB1B9F5 | SHA256:B33EFCB95235B98B48508E019AFA4B7655E80CF071DEFABD8B2123FC8B29307F | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:C978B851F8802CCD3F5A486F8CE5ECC4 | SHA256:3A13F81BAB2E1E2C0A26E7A46D34C41EE8CAE4652F8547A444B9F92167923259 | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\Local\Temp\HostShell.exe | executable | |
MD5:B9624A08AEEC0460AF8A3DD25971F8B6 | SHA256:0D5311ACB41EA5781A26E65CE8B200F267EA744AA331BC332B22F9D7A75A046E | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:91418772CE41913F773E17856790EDE7 | SHA256:8BC5D0F7AA437AEB7B52E53EF6CBC596FF0AA1D7743165DE959290AC327A5888 | |||
| 1580 | HostShell.exe | C:\Users\admin\AppData\Local\Temp\FogCreekCopilotHost.exe | executable | |
MD5:6E302031D41C4B74A0A8396785CA870B | SHA256:65D2982107439508132DCB65D1BD64579DBBB33E6B288D753BA64853AD799F4D | |||
| 1580 | HostShell.exe | C:\Users\admin\AppData\Local\Temp\FogCreekCopilotHooks.dll | executable | |
MD5:5284A0946FCF4D082BCC1147B2447E92 | SHA256:F5AA1302696F59A82A57D9BA061CB5A0F36669FE8C702FFDB082128AE0705DAF | |||
| 1136 | Copilot Host.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1136 | Copilot Host.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?956b38654546f56c | unknown | — | — | unknown |
1136 | Copilot Host.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2755af7cbee6f323 | unknown | — | — | unknown |
1136 | Copilot Host.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1136 | Copilot Host.exe | 76.76.21.98:443 | www.copilot.com | AMAZON-02 | US | unknown |
1136 | Copilot Host.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1136 | Copilot Host.exe | 2.23.197.184:80 | x1.c.lencr.org | CW Vodafone Group PLC | GB | unknown |
660 | FogCreekCopilotHost.exe | 49.13.77.253:443 | reflector.copilot.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.copilot.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
reflector.copilot.com |
| unknown |
dns.msftncsi.com |
| shared |