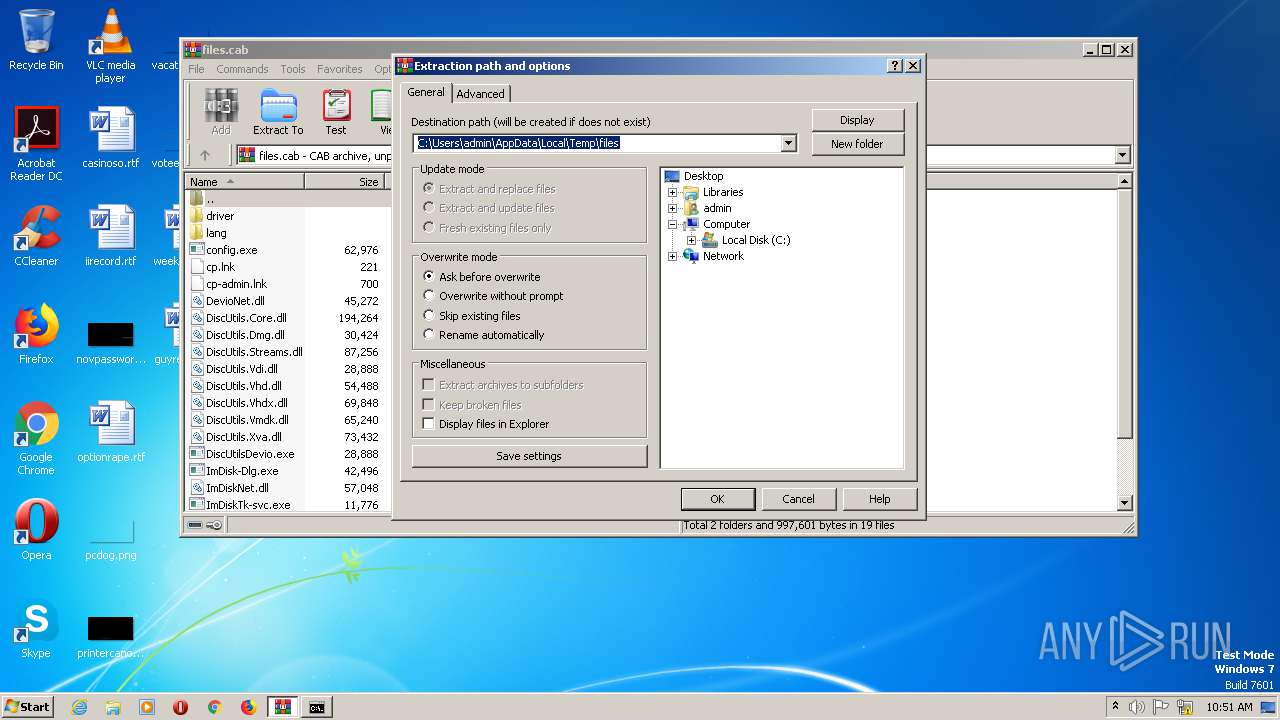
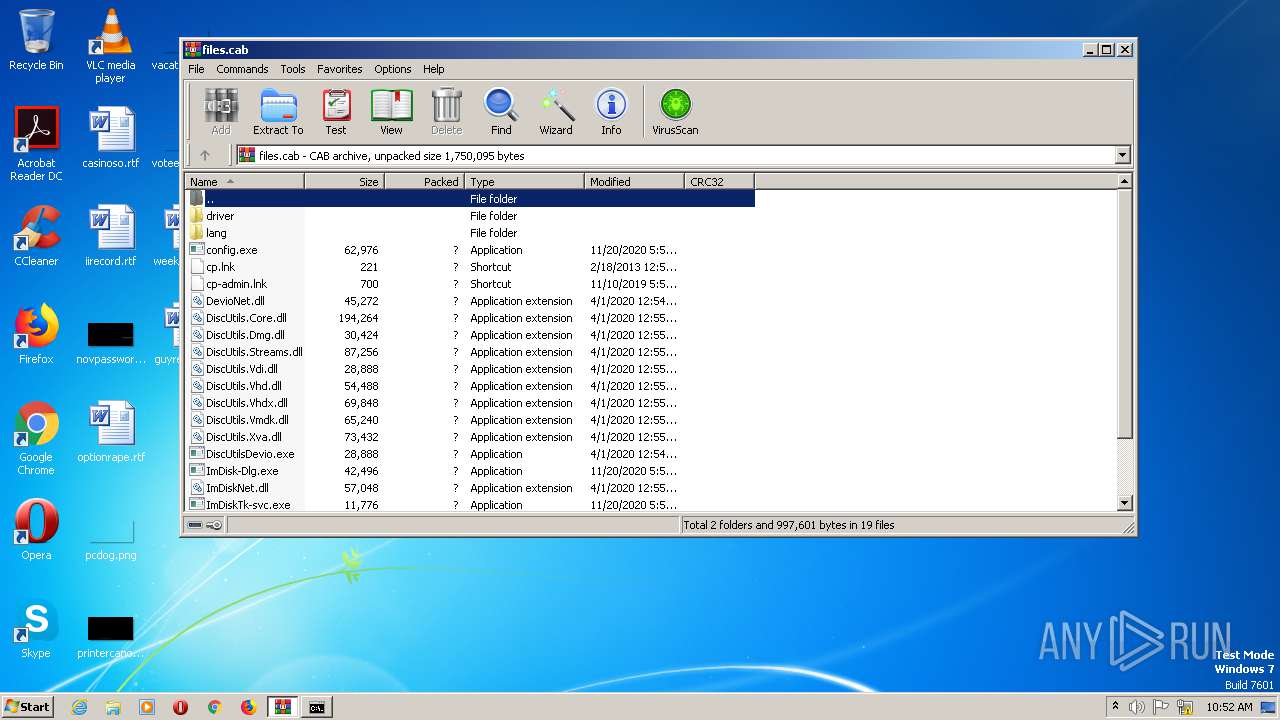
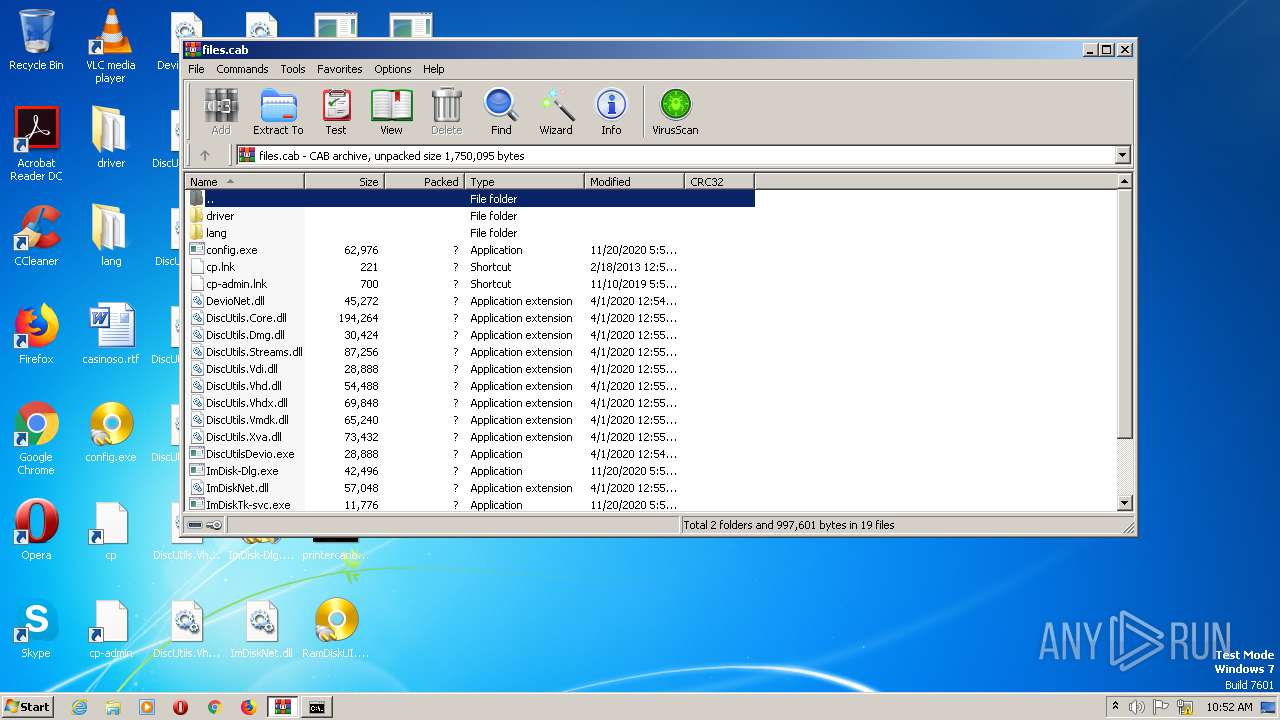
| File name: | files.cab |
| Full analysis: | https://app.any.run/tasks/2a3fd1fd-7c1e-4278-bb72-a310015364f3 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 10:51:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, 473611 bytes, 42 files |
| MD5: | 87FB33B0283C6D949B7F0EA16037B324 |
| SHA1: | 175FD2D0F8140DBDF6F72E588B60EDBC09188BD8 |
| SHA256: | C63876DD54C912A87450EE3344B215793794CB9AB1EDA264C7774A700BEAD70D |
| SSDEEP: | 12288:JY69daSc4mGtteR0S84o2d1cuVRYR7gv23oW:KSNtsR+p2suc6vbW |
MALICIOUS
Application was dropped or rewritten from another process
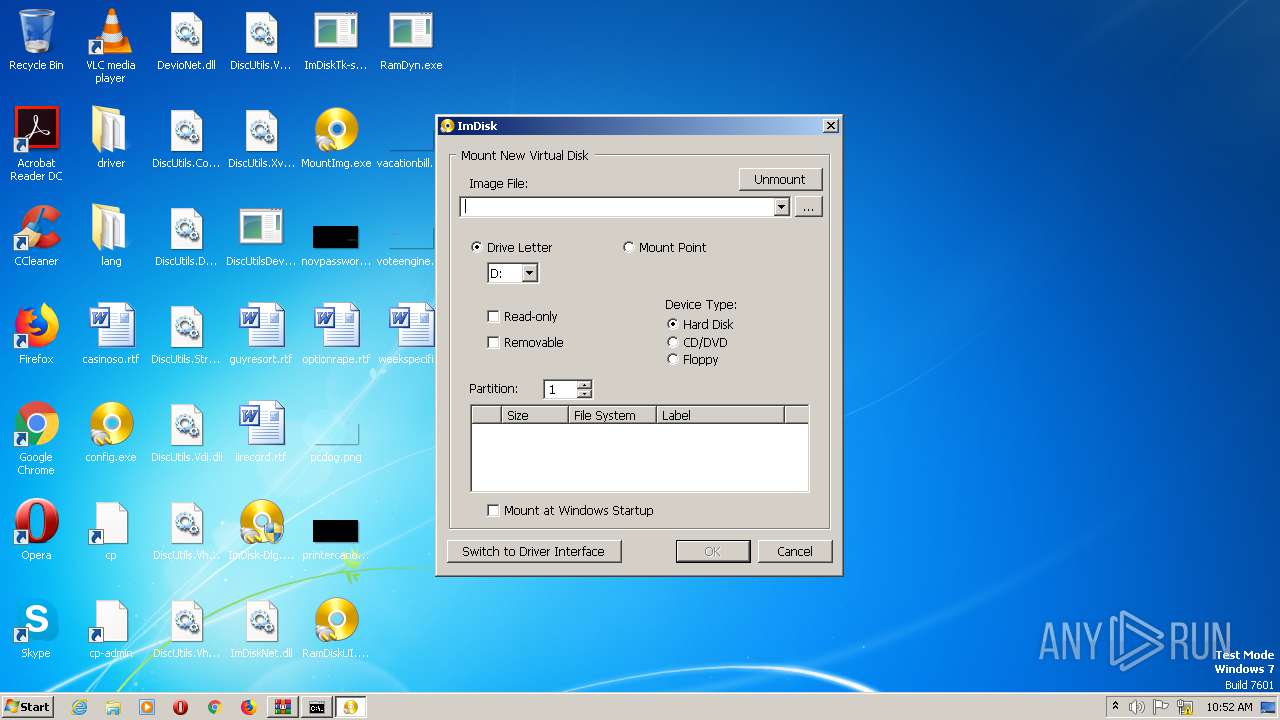
- ImDisk-Dlg.exe (PID: 2448)
- MountImg.exe (PID: 1396)
- ImDisk-Dlg.exe (PID: 2312)
- MountImg.exe (PID: 1448)
SUSPICIOUS
Application launched itself
- MountImg.exe (PID: 1448)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1608)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1608)
Drops a file with too old compile date
- WinRAR.exe (PID: 1608)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1608)
INFO
Manual execution by user
- cmd.exe (PID: 1412)
- MountImg.exe (PID: 1448)
- ImDisk-Dlg.exe (PID: 2448)
- ImDisk-Dlg.exe (PID: 2312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
47
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1396 | "C:\Users\admin\Desktop\MountImg.exe" /UAC 4 "C:\Users\admin\Desktop\MountImg.exe" | C:\Users\admin\Desktop\MountImg.exe | MountImg.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Mount new virtual disk Exit code: 0 Modules
| |||||||||||||||
| 1412 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\Desktop\MountImg.exe" | C:\Users\admin\Desktop\MountImg.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Mount new virtual disk Exit code: 0 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\files.cab" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\Desktop\ImDisk-Dlg.exe" | C:\Users\admin\Desktop\ImDisk-Dlg.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: ImDisk Exit code: 1 Modules
| |||||||||||||||
| 2448 | "C:\Users\admin\Desktop\ImDisk-Dlg.exe" | C:\Users\admin\Desktop\ImDisk-Dlg.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ImDisk Exit code: 3221226540 Modules
| |||||||||||||||
Total events
612
Read events
588
Write events
24
Delete events
0
Modification events
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\files.cab | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1608) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1448) MountImg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
26
Suspicious files
0
Text files
14
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Core.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\config.exe | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Vmdk.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Dmg.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Streams.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DevioNet.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Vdi.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Vhd.dll | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtilsDevio.exe | executable | |
MD5:— | SHA256:— | |||
| 1608 | WinRAR.exe | C:\Users\admin\Desktop\DiscUtils.Vhdx.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report