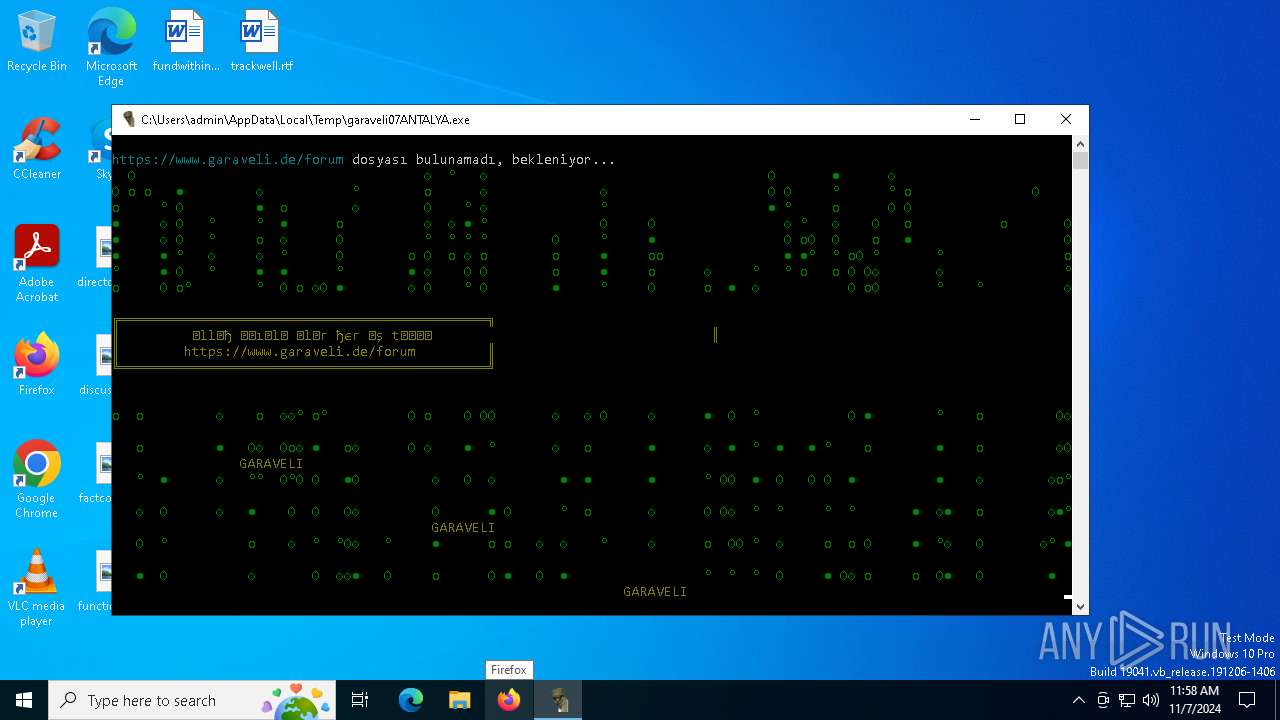
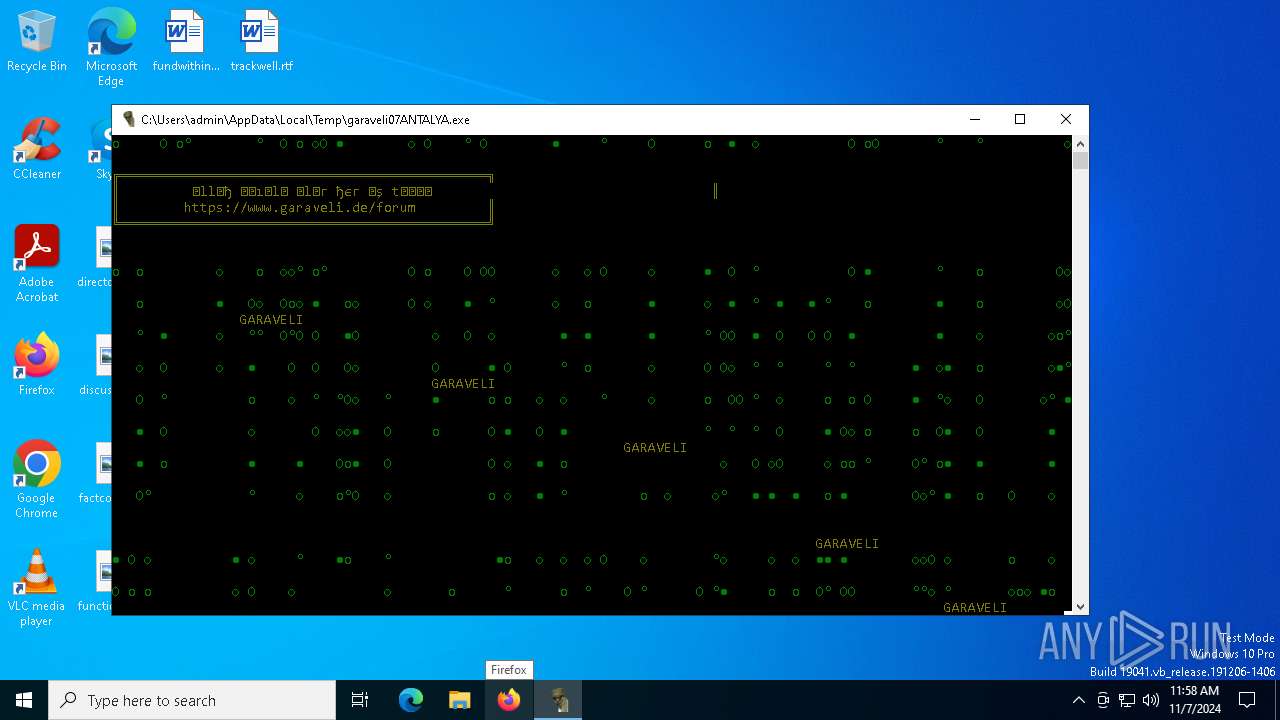
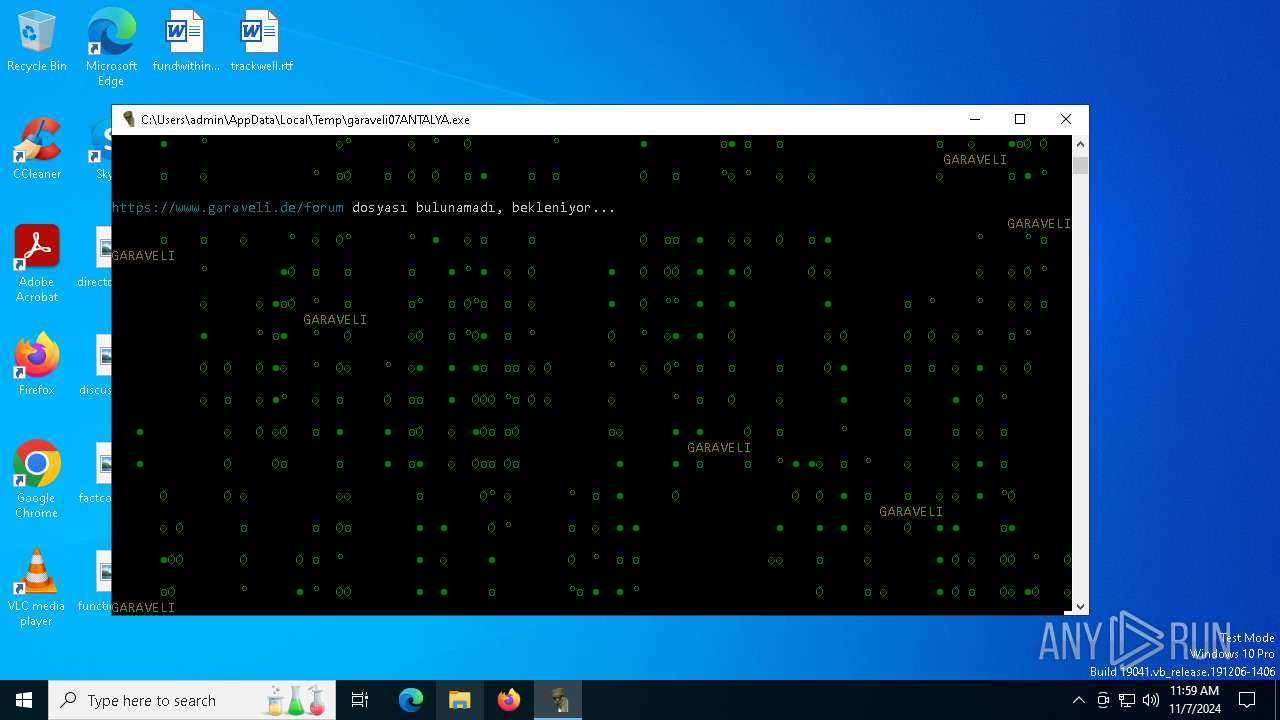
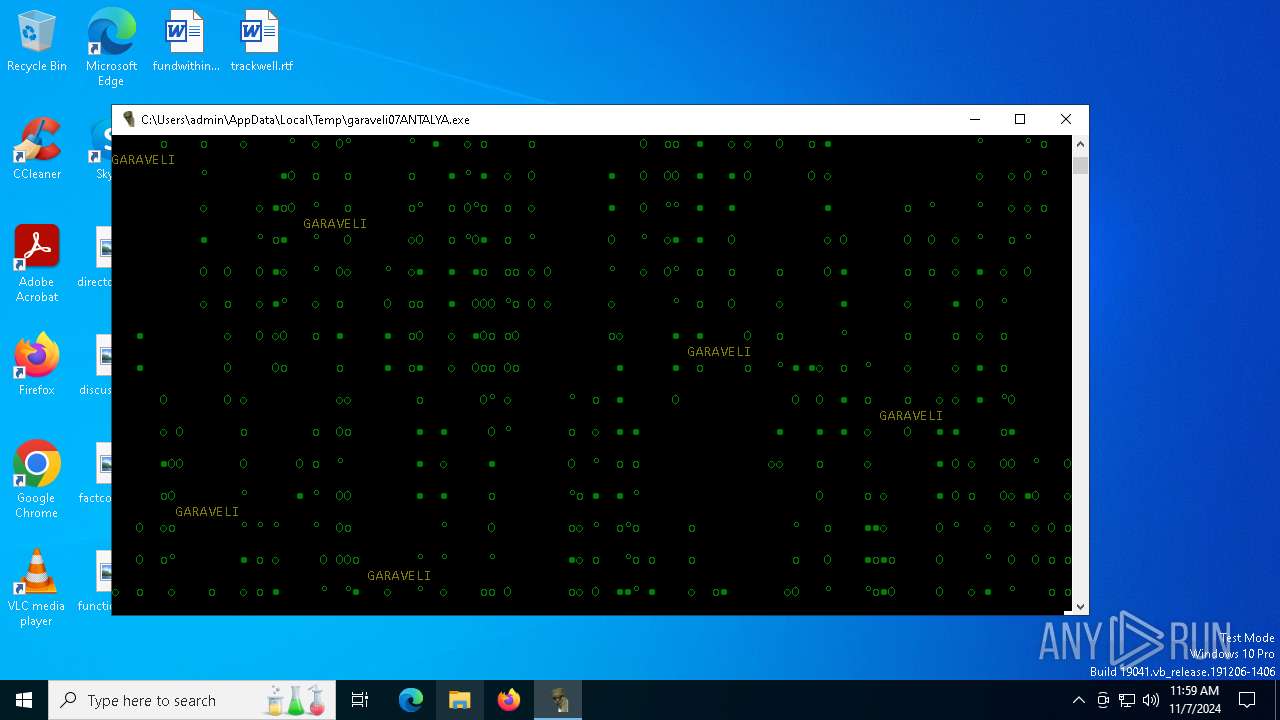
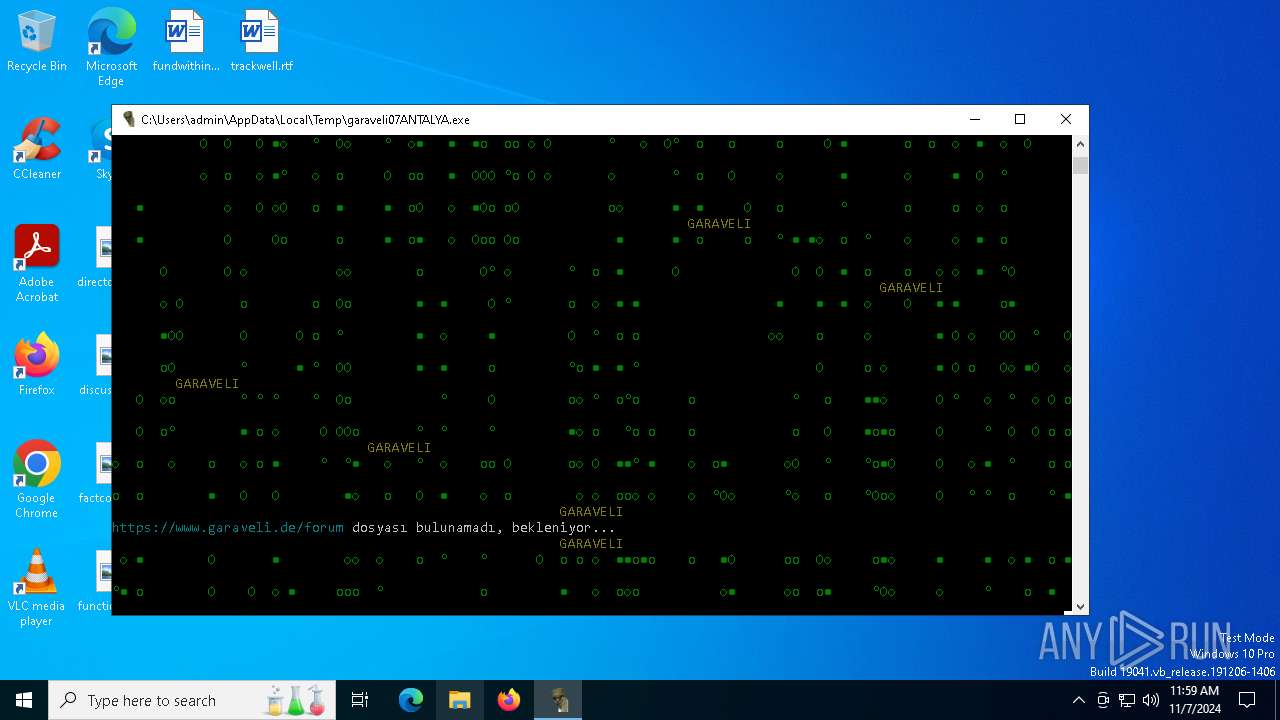
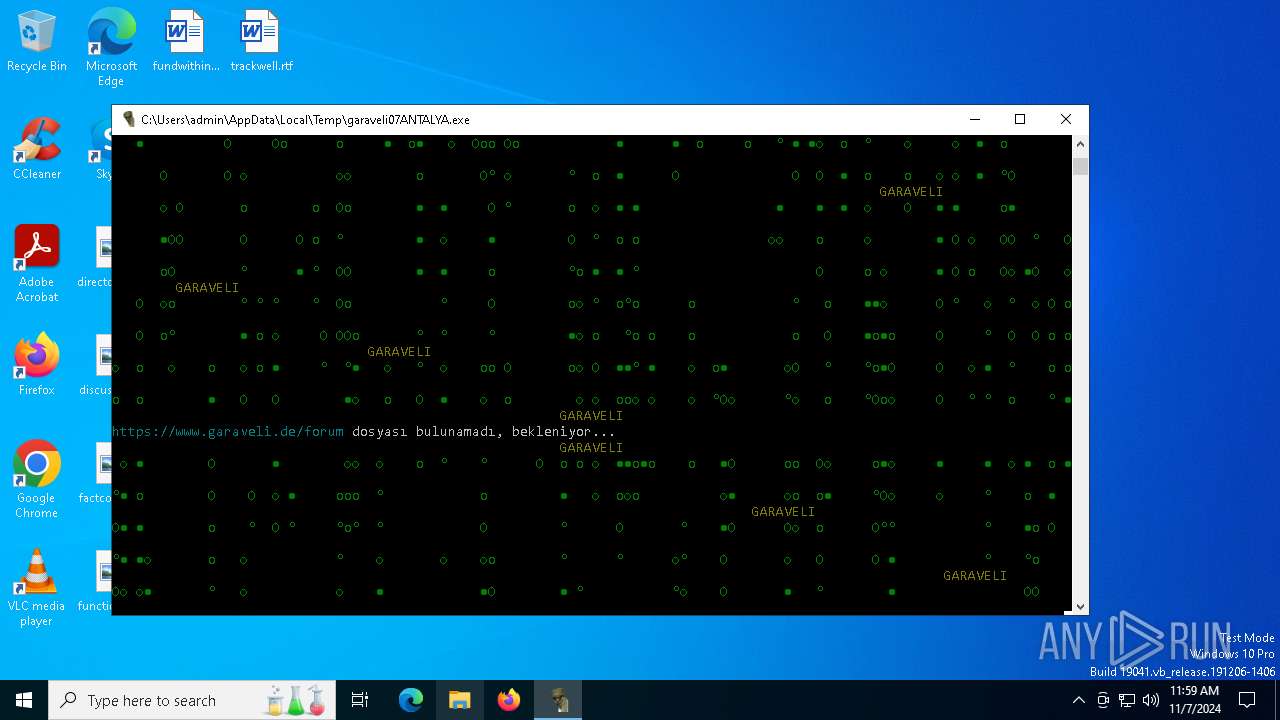
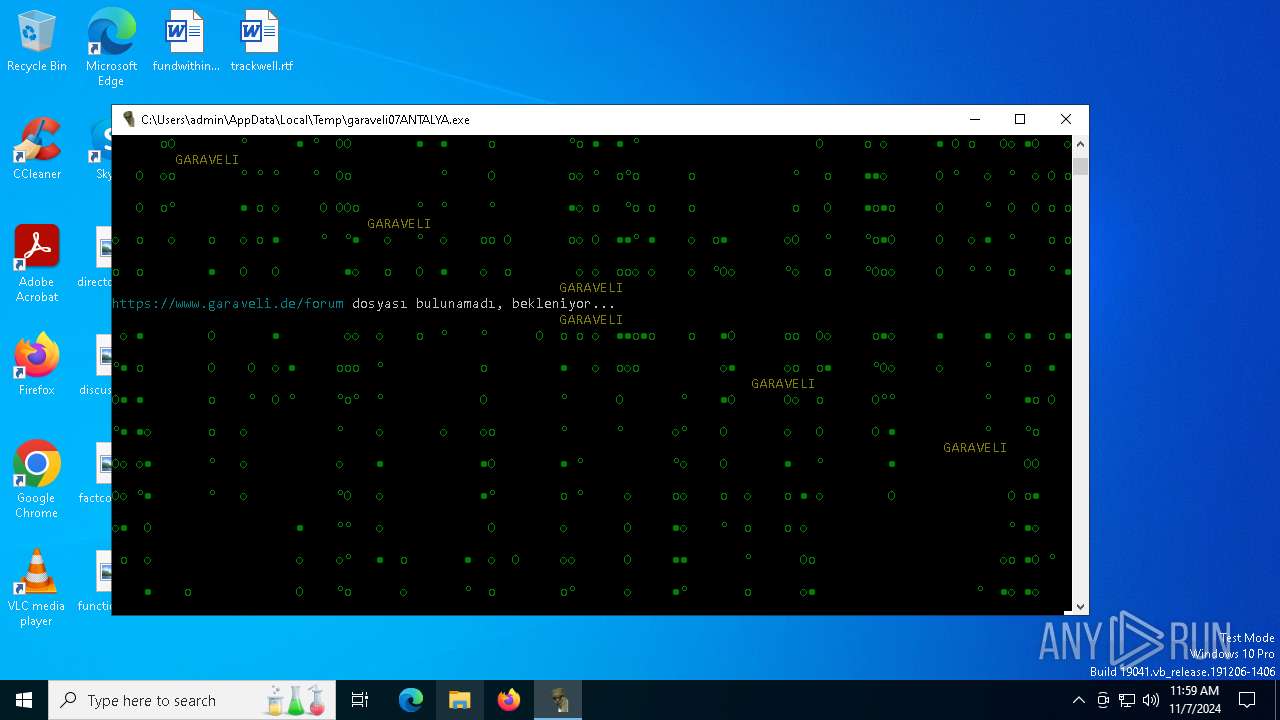
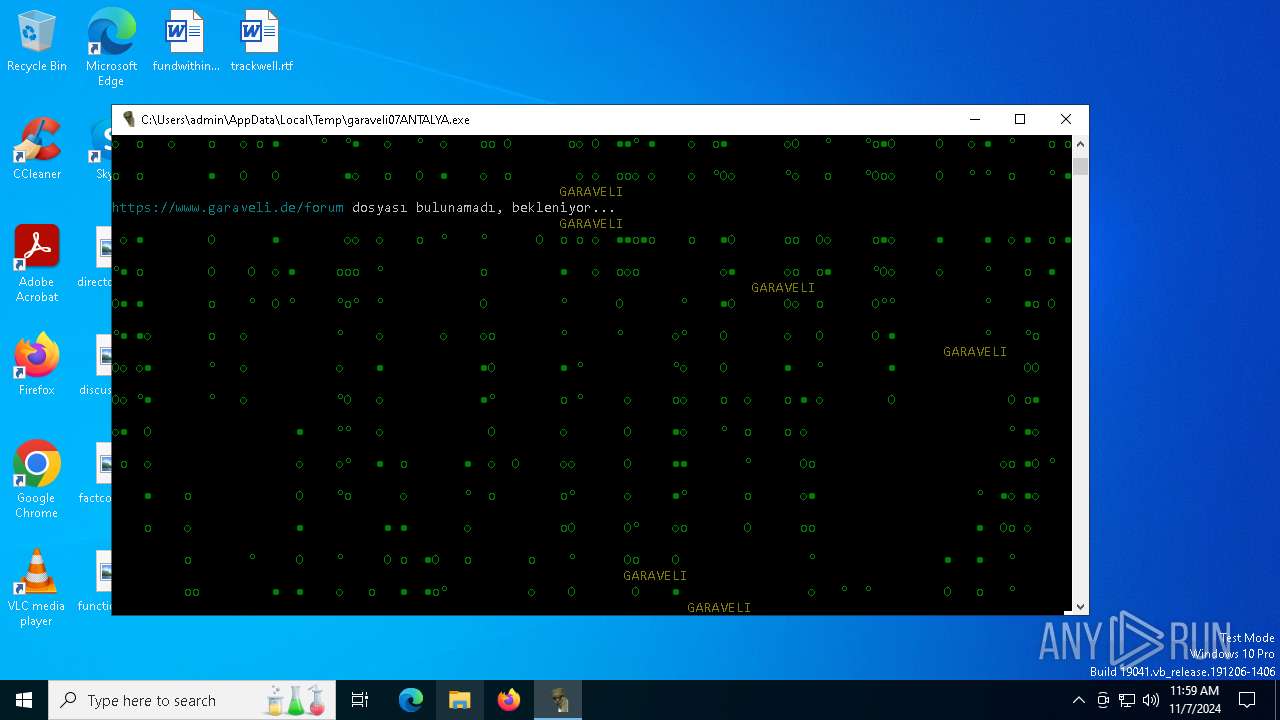
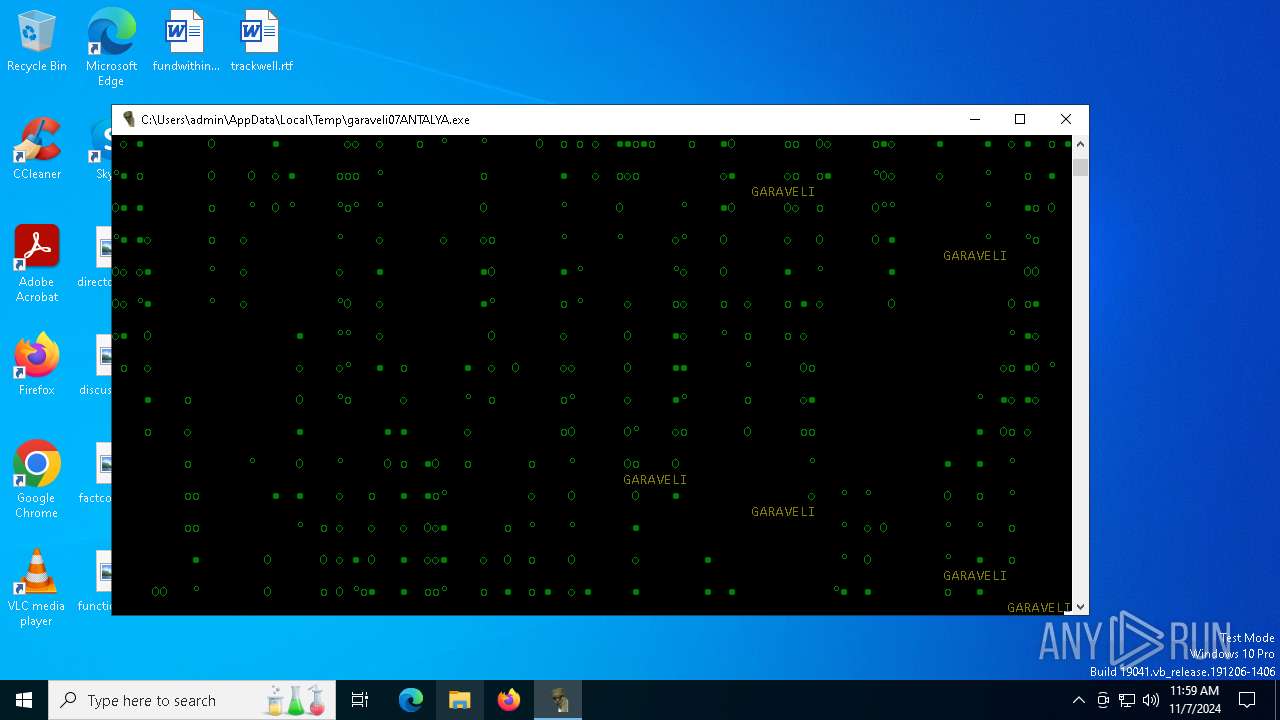
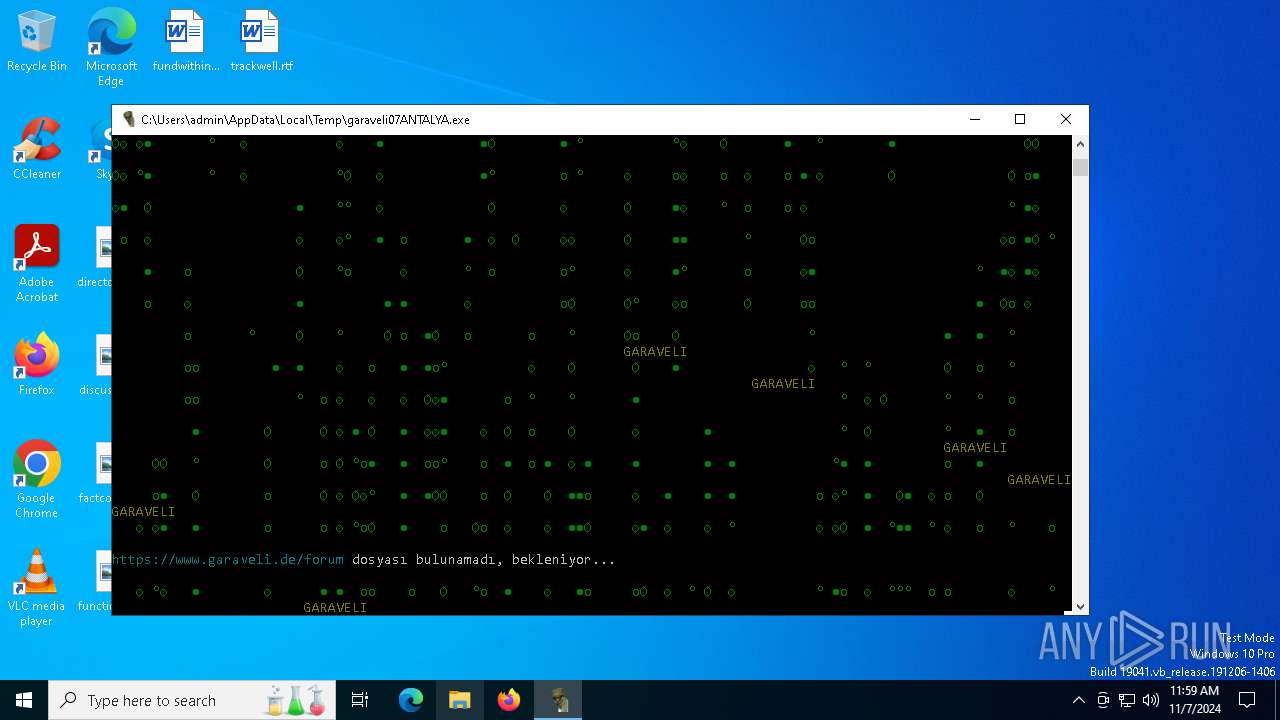
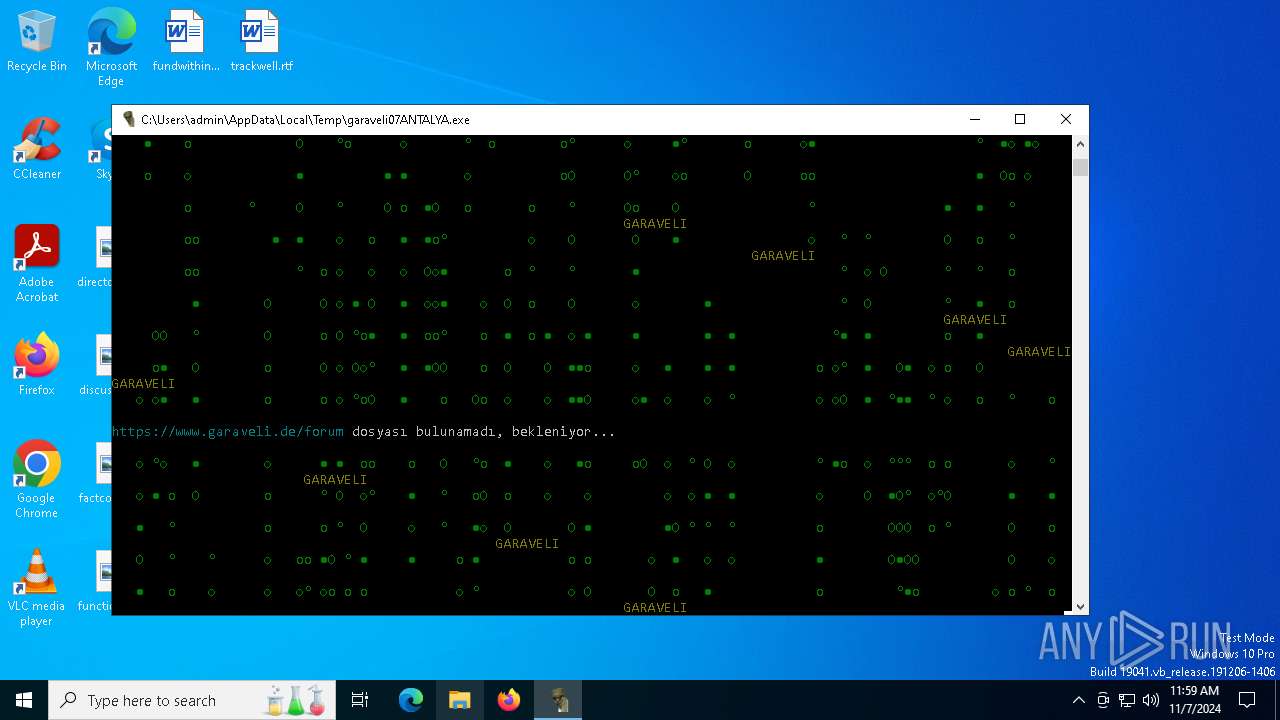
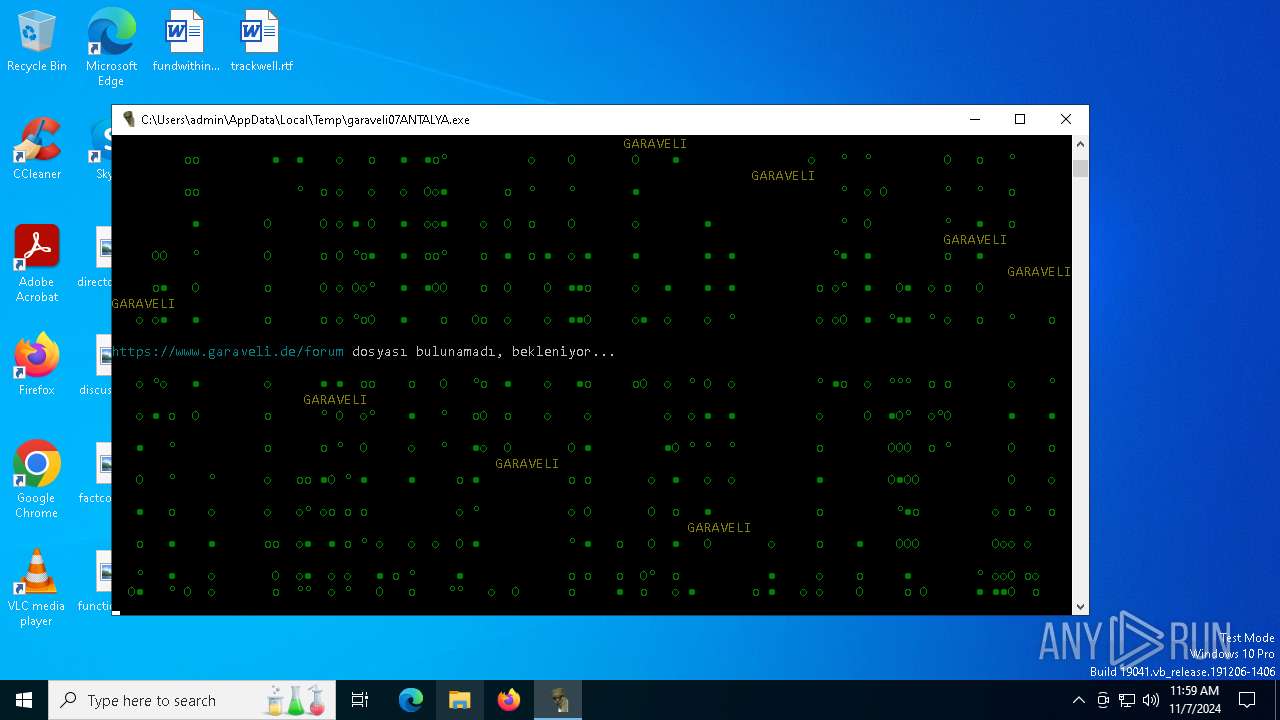
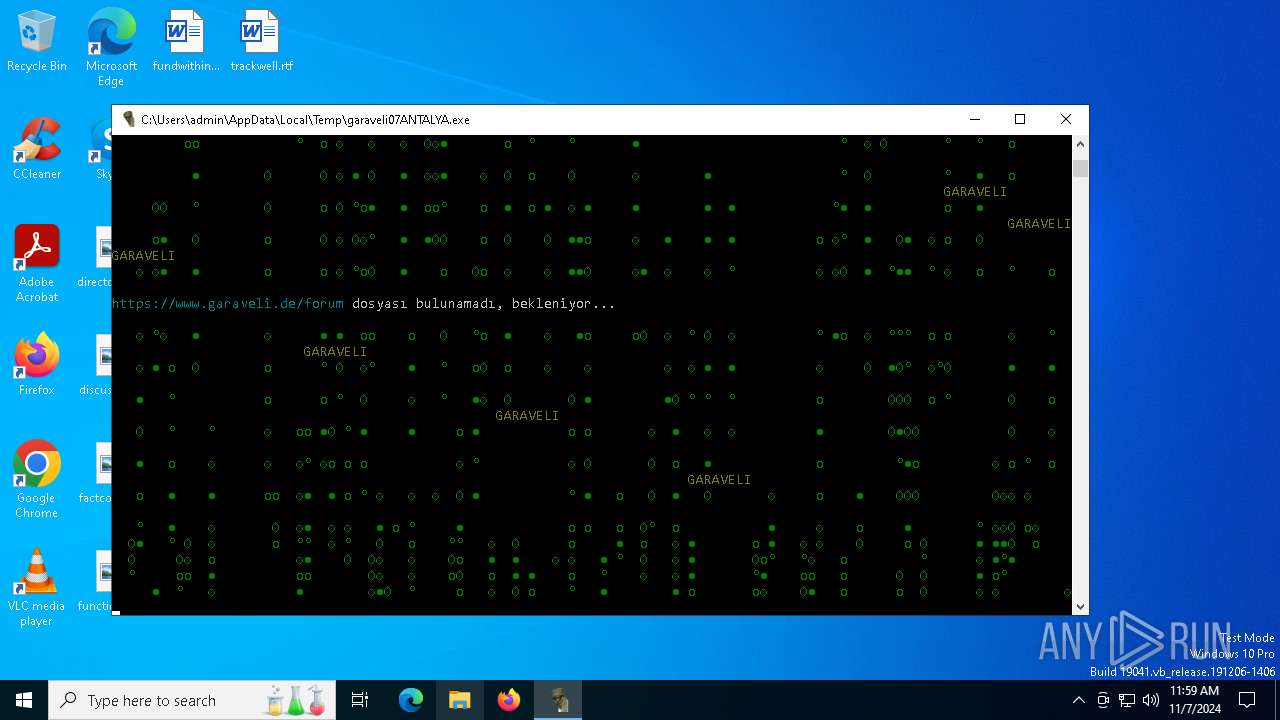
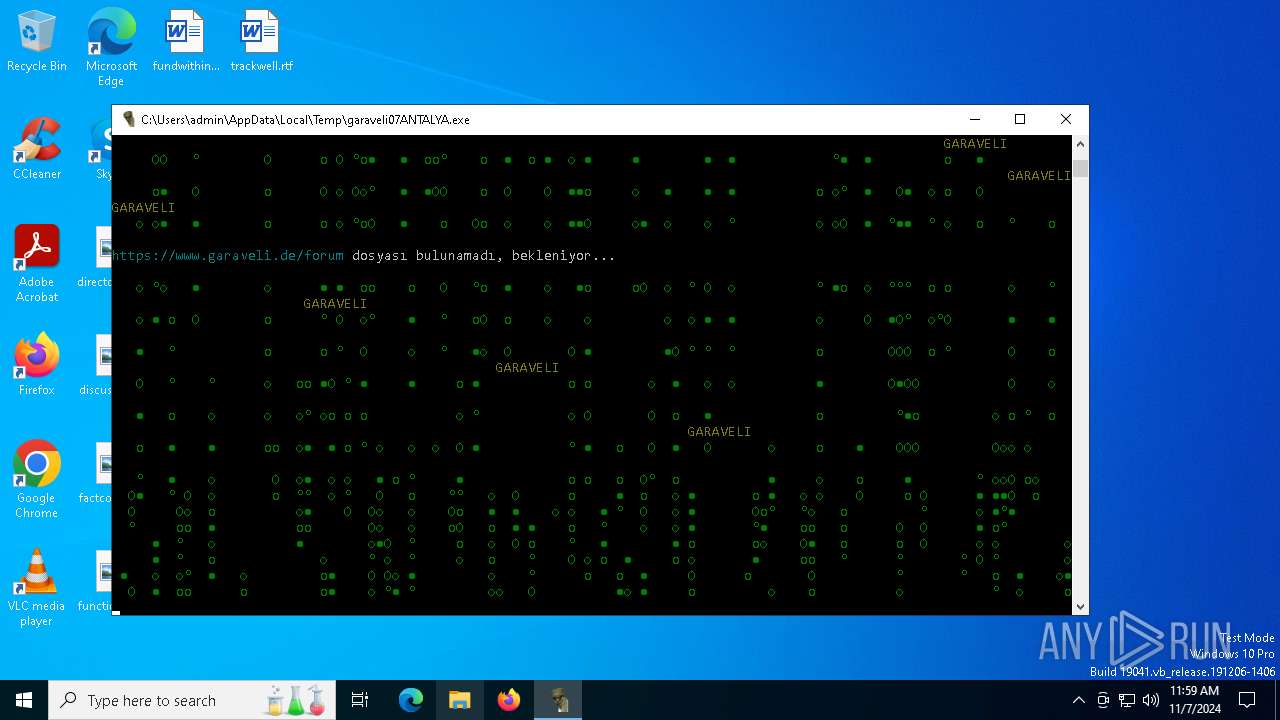
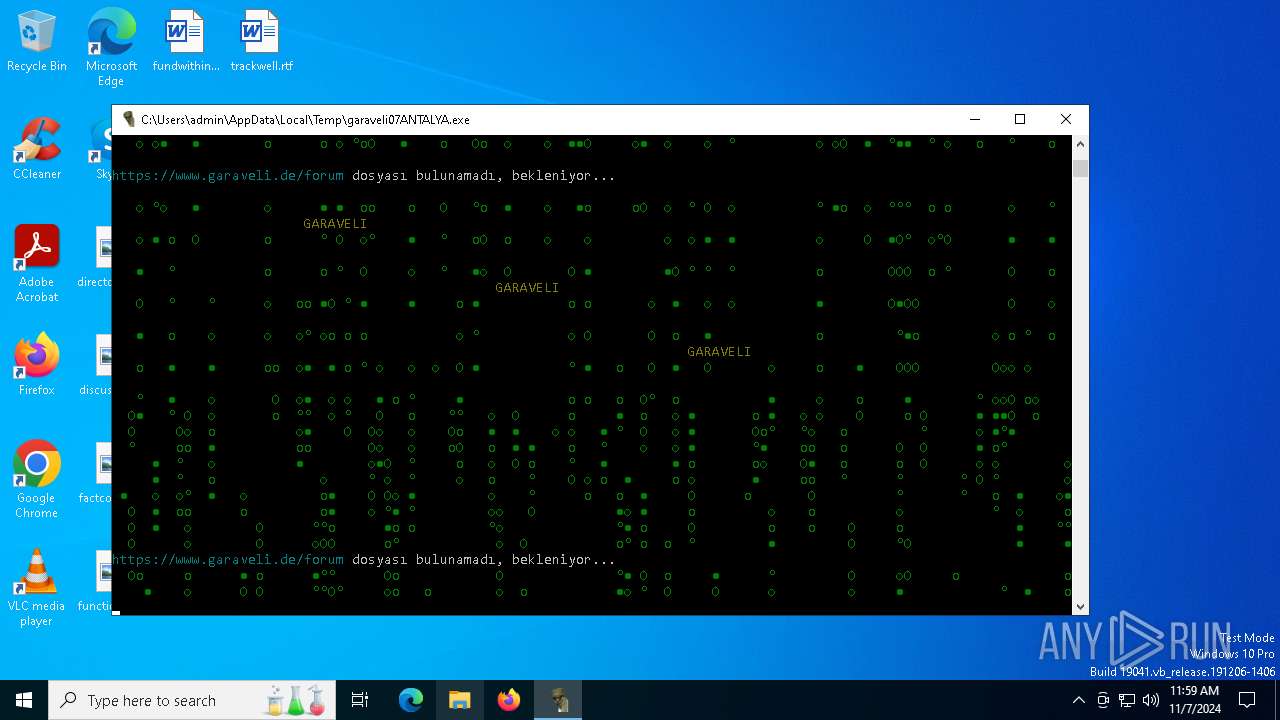
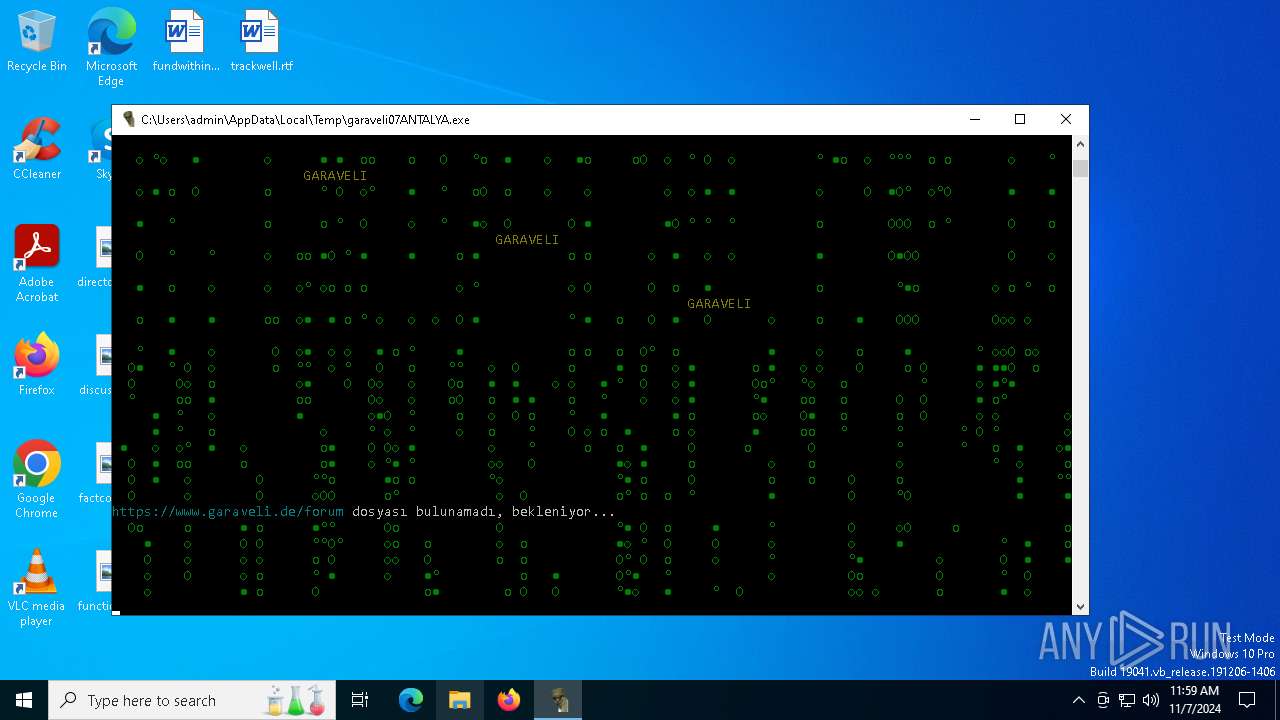
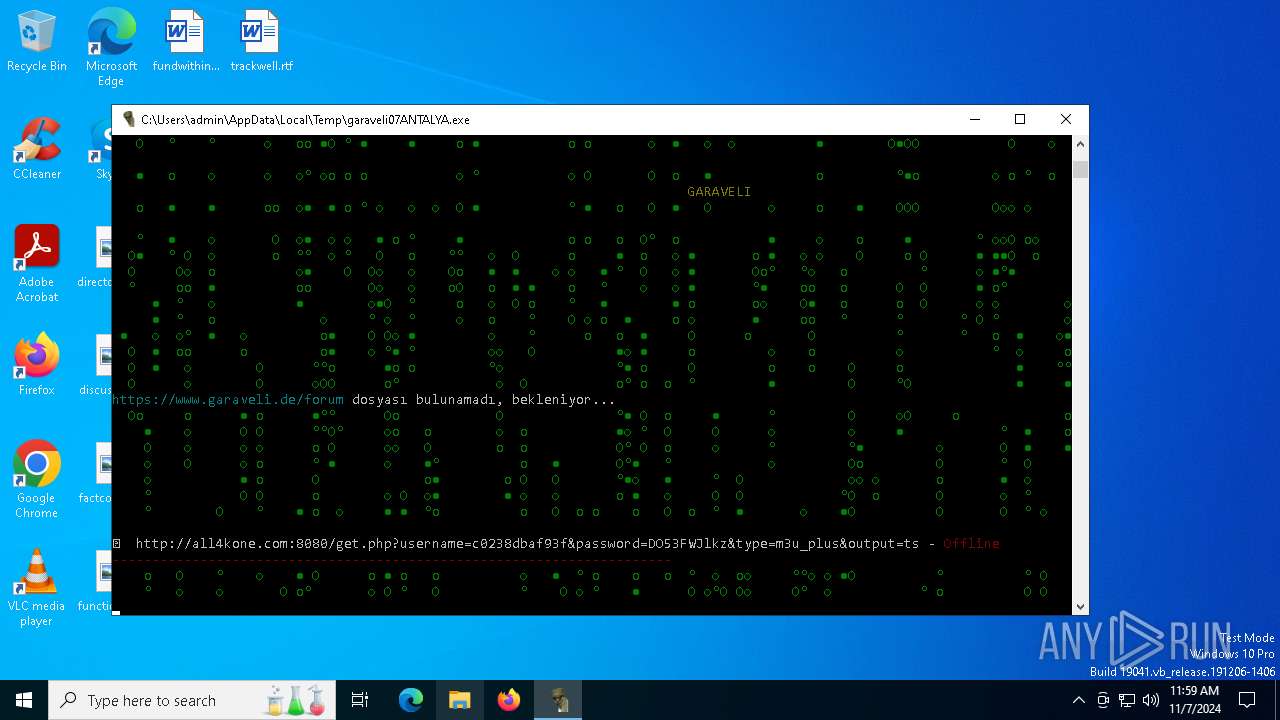
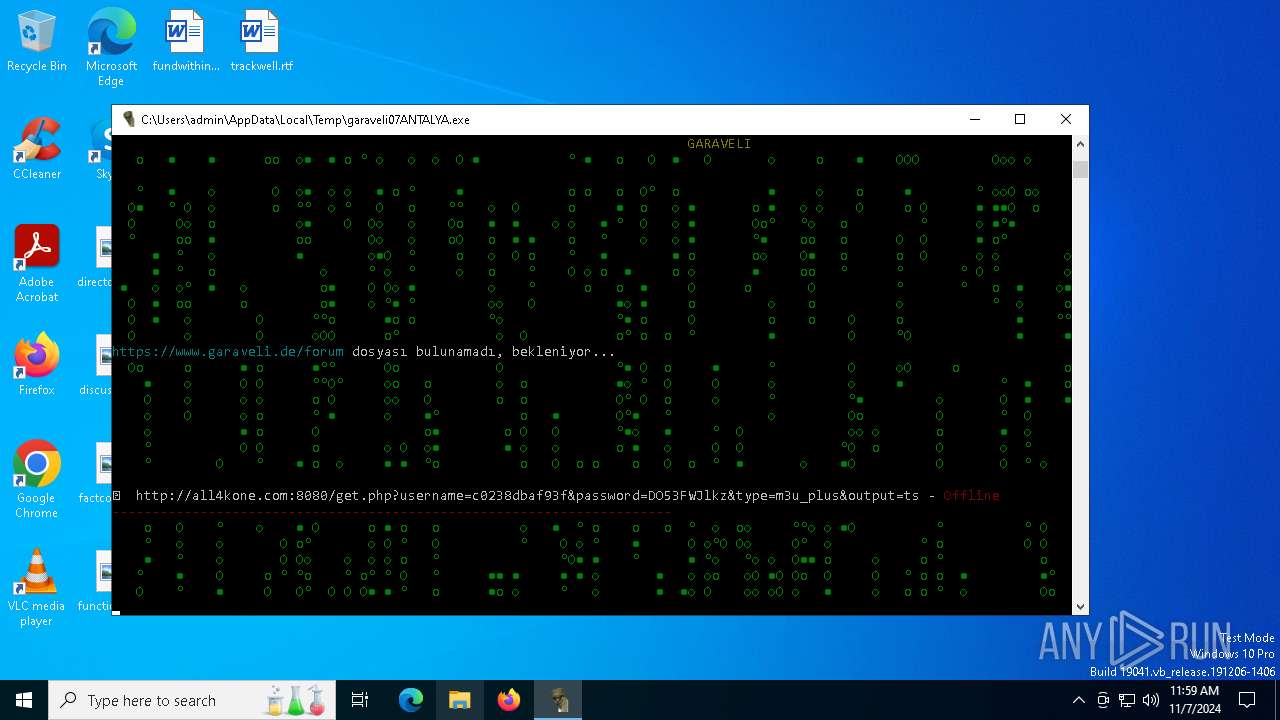
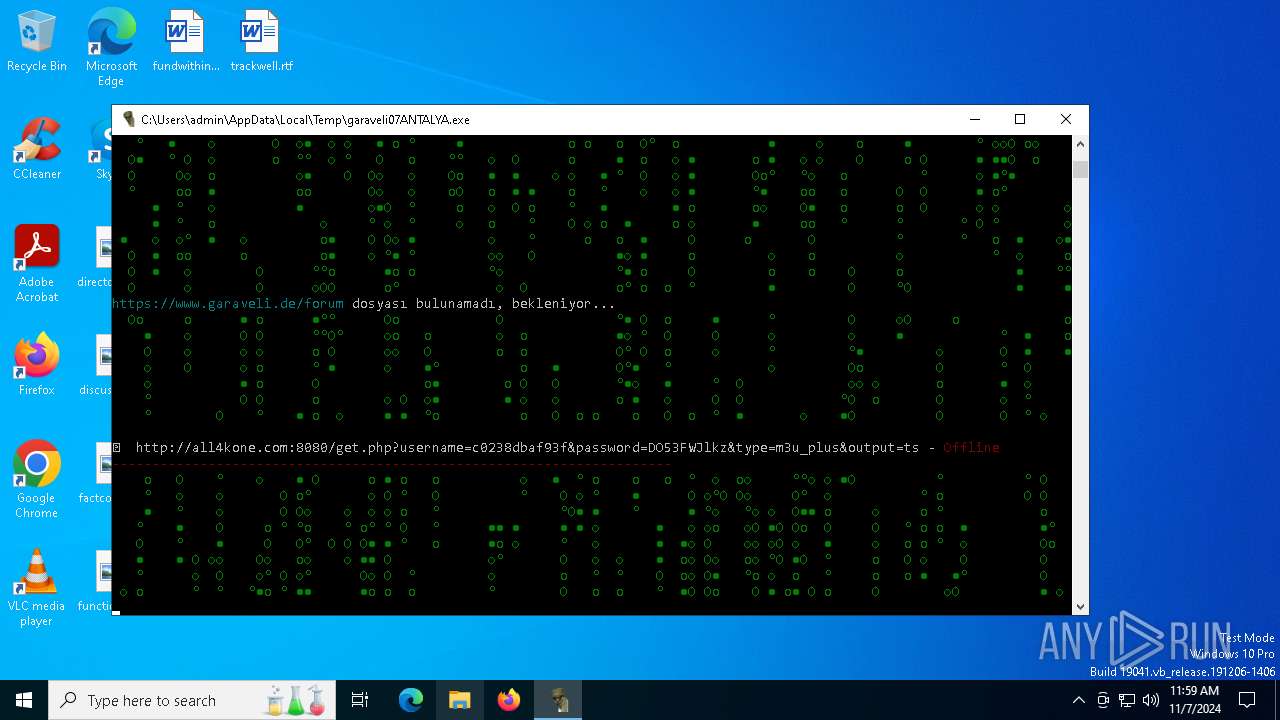
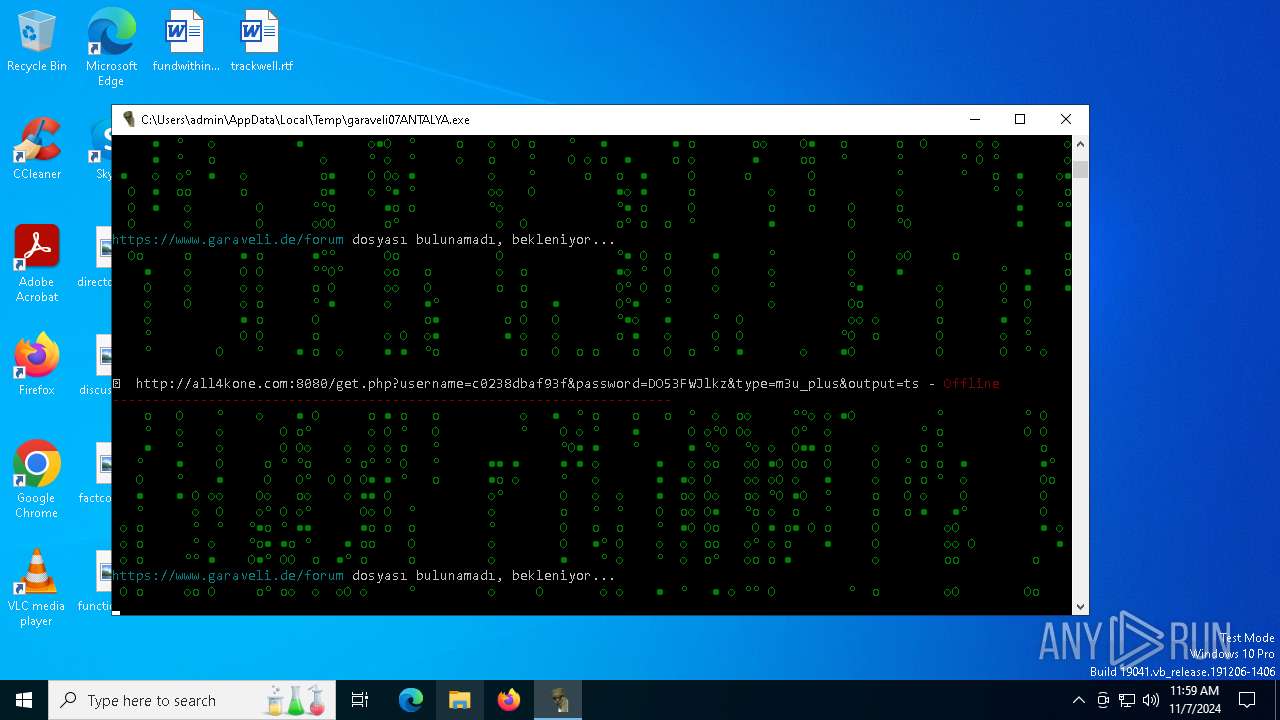
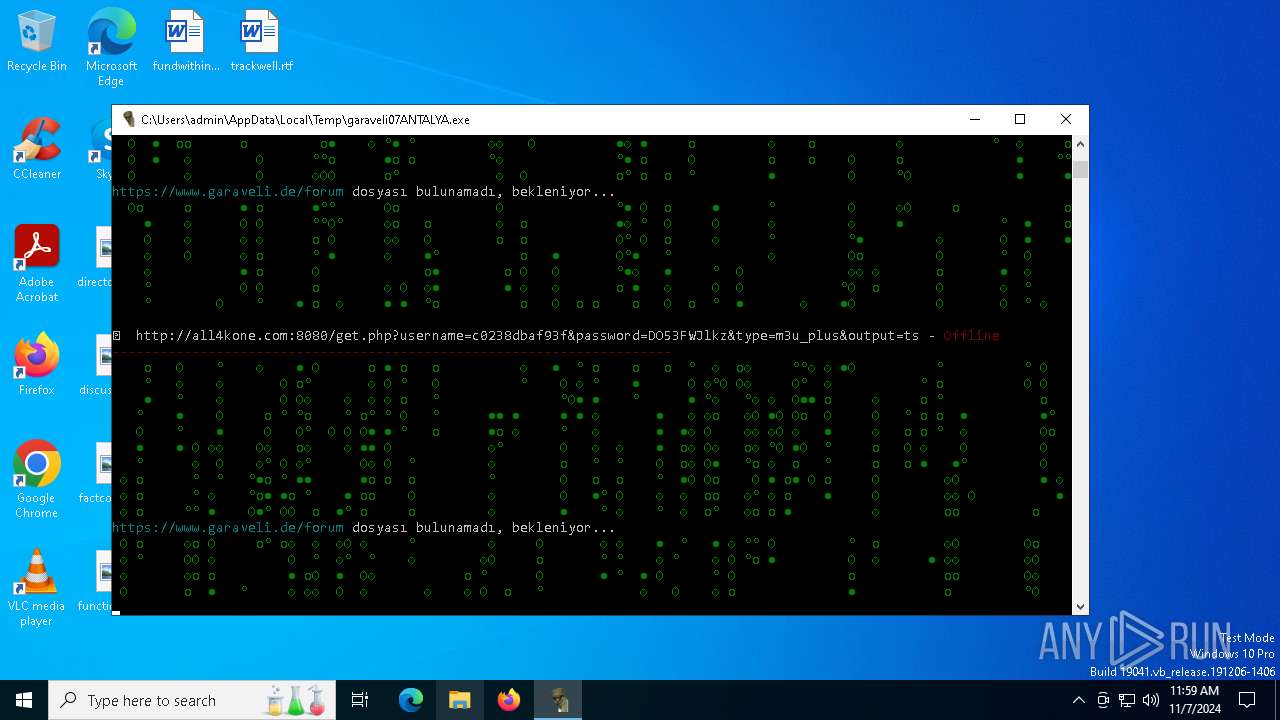
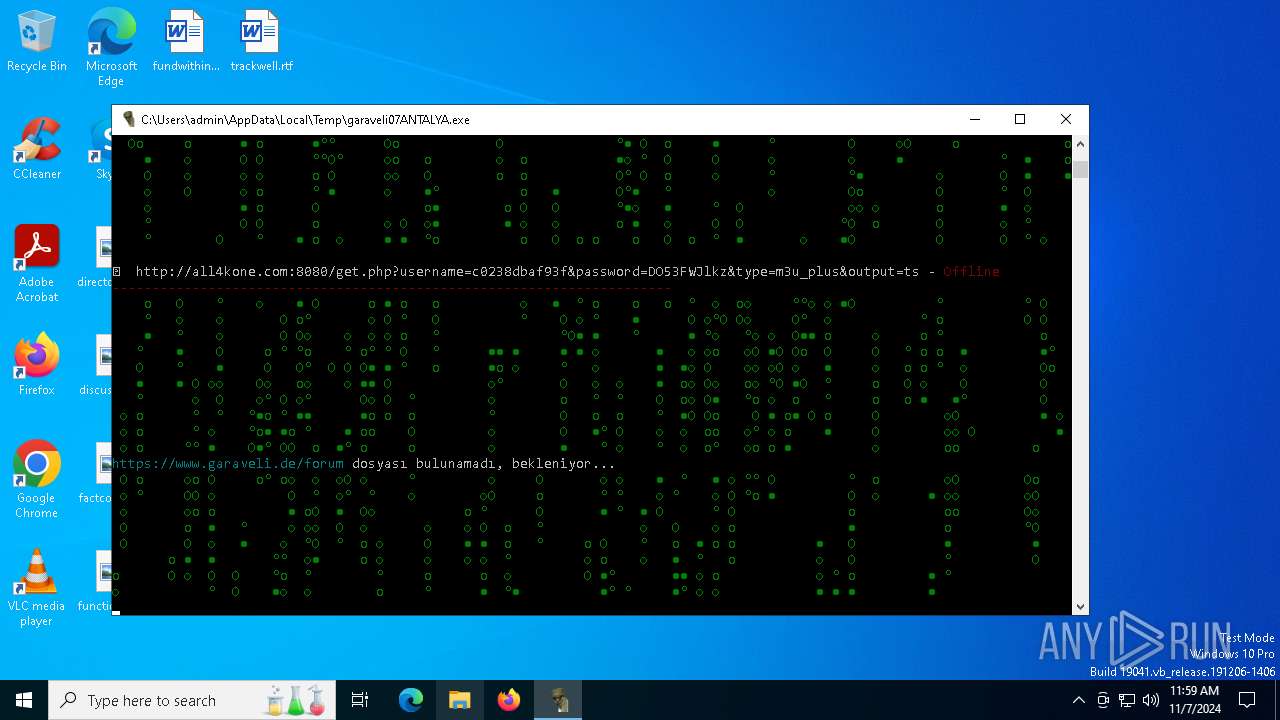
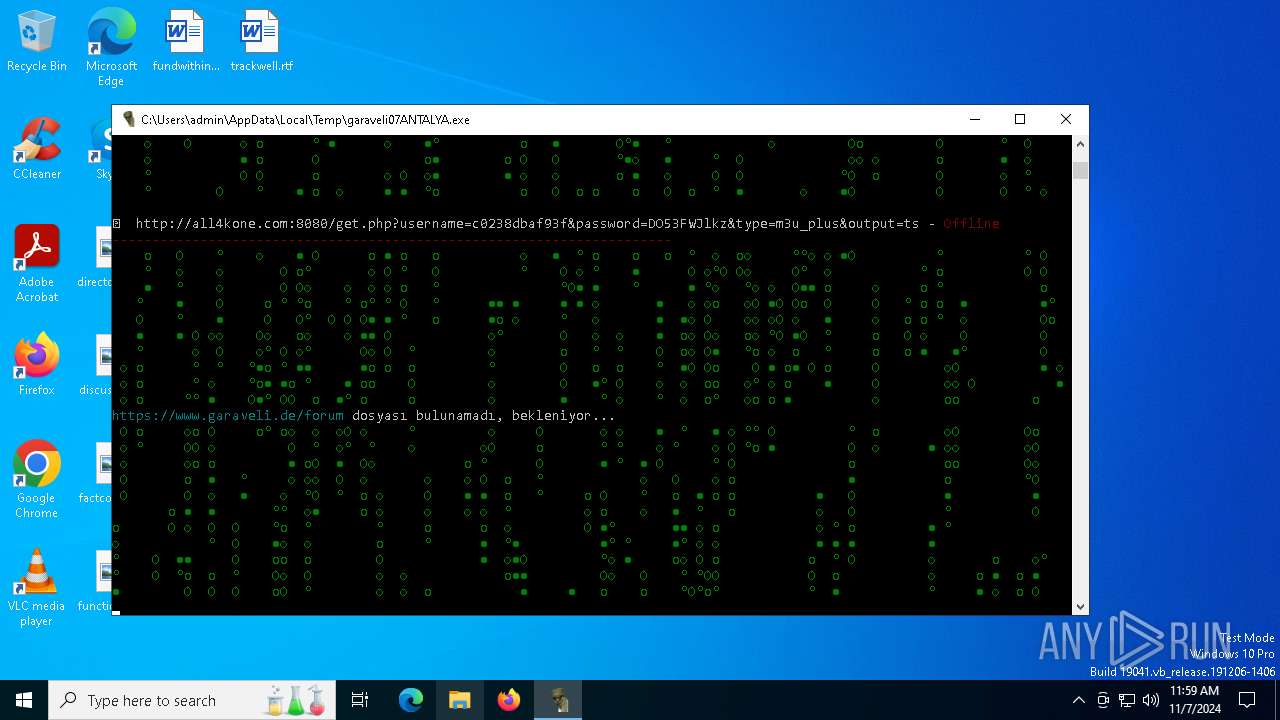
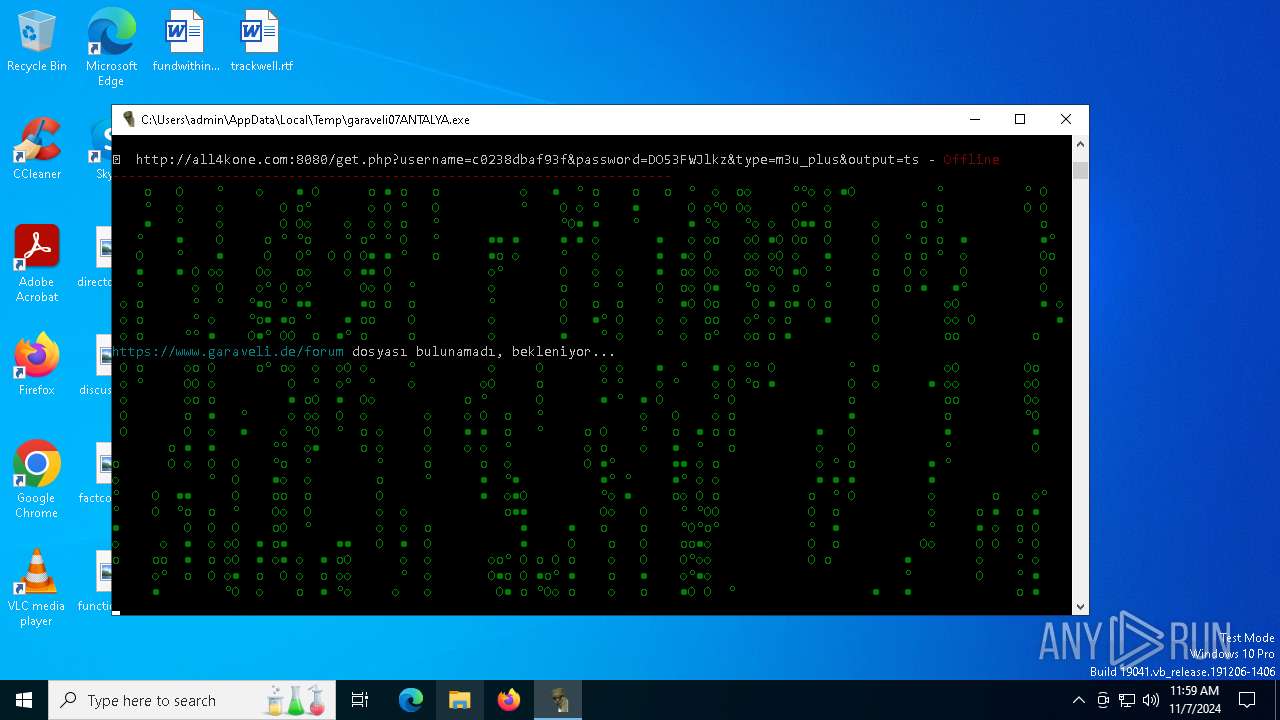
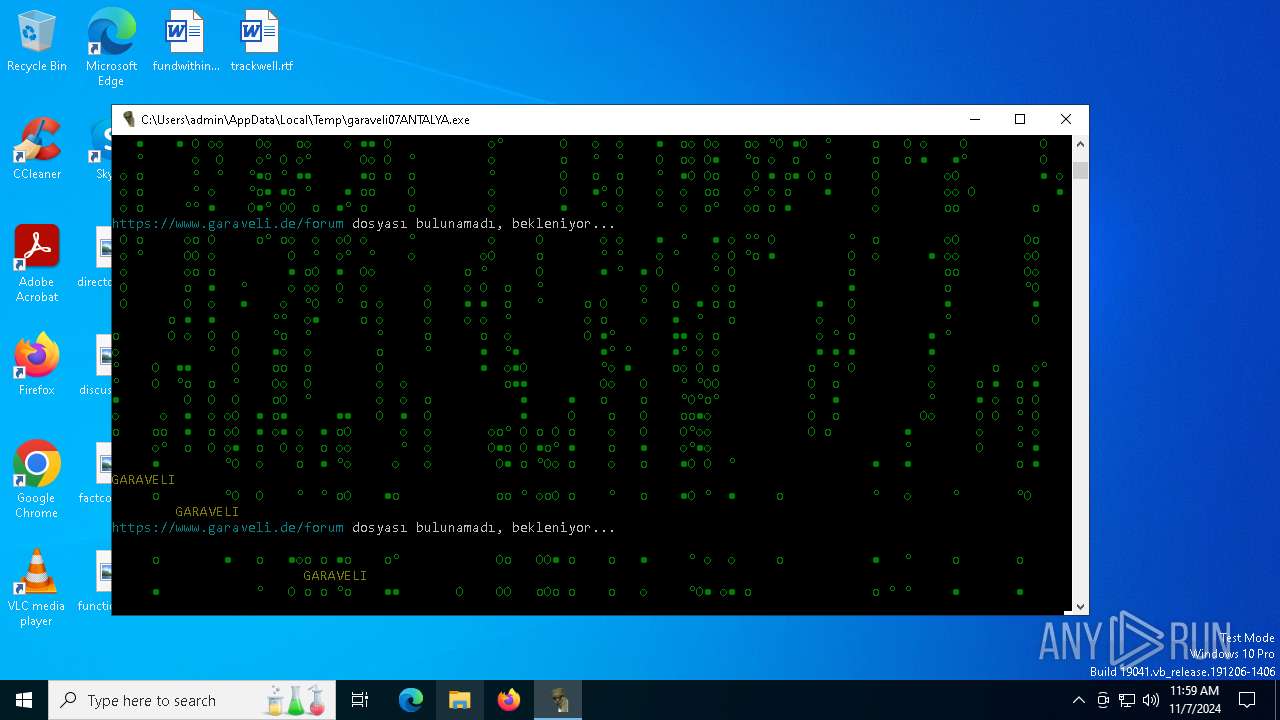
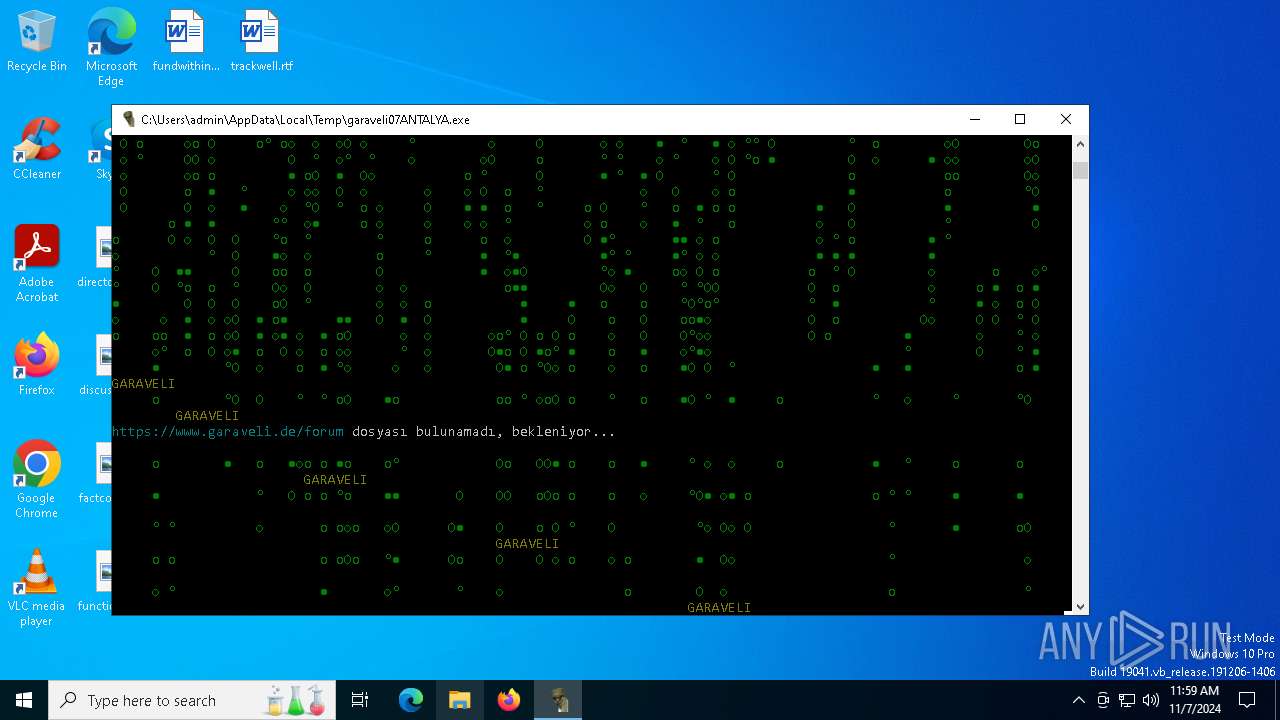
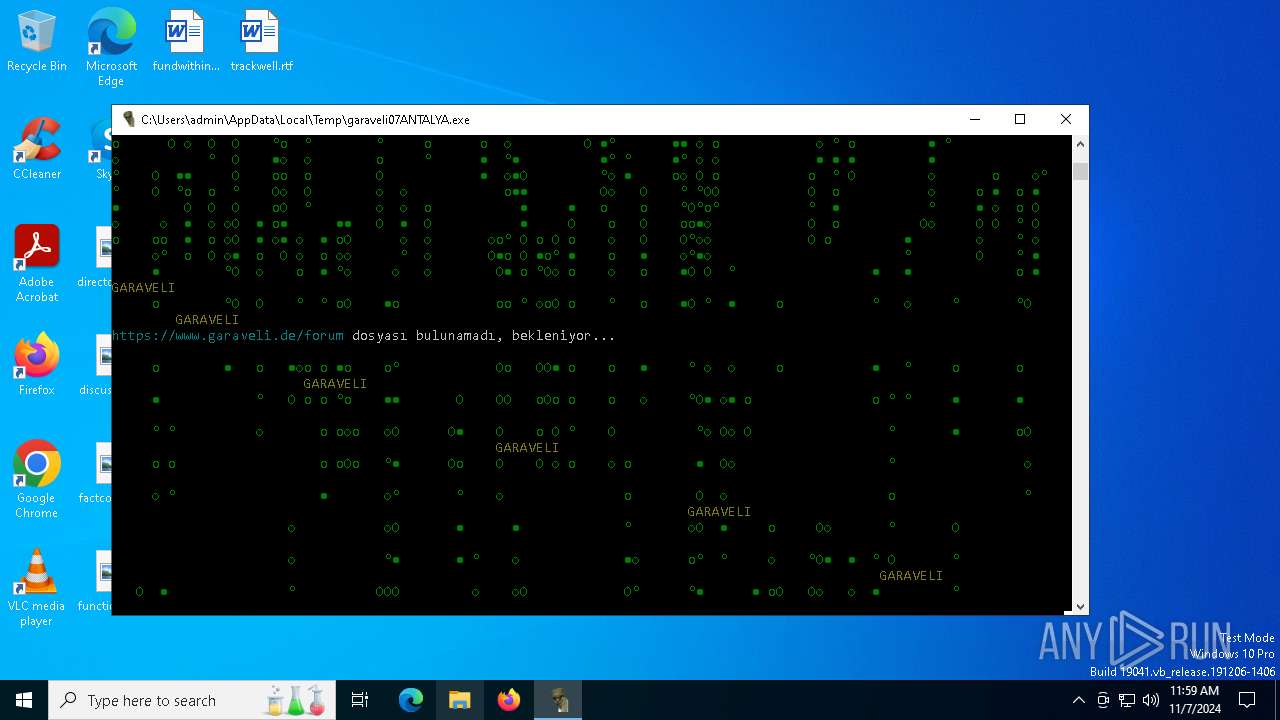
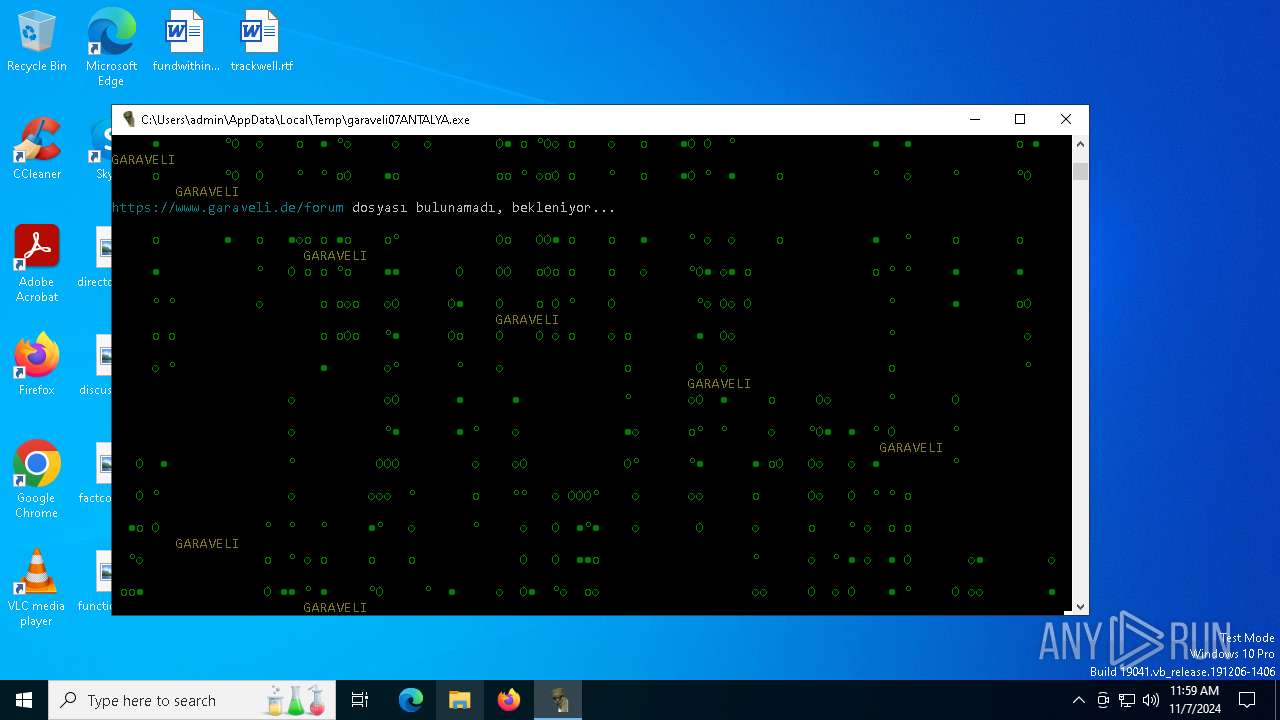
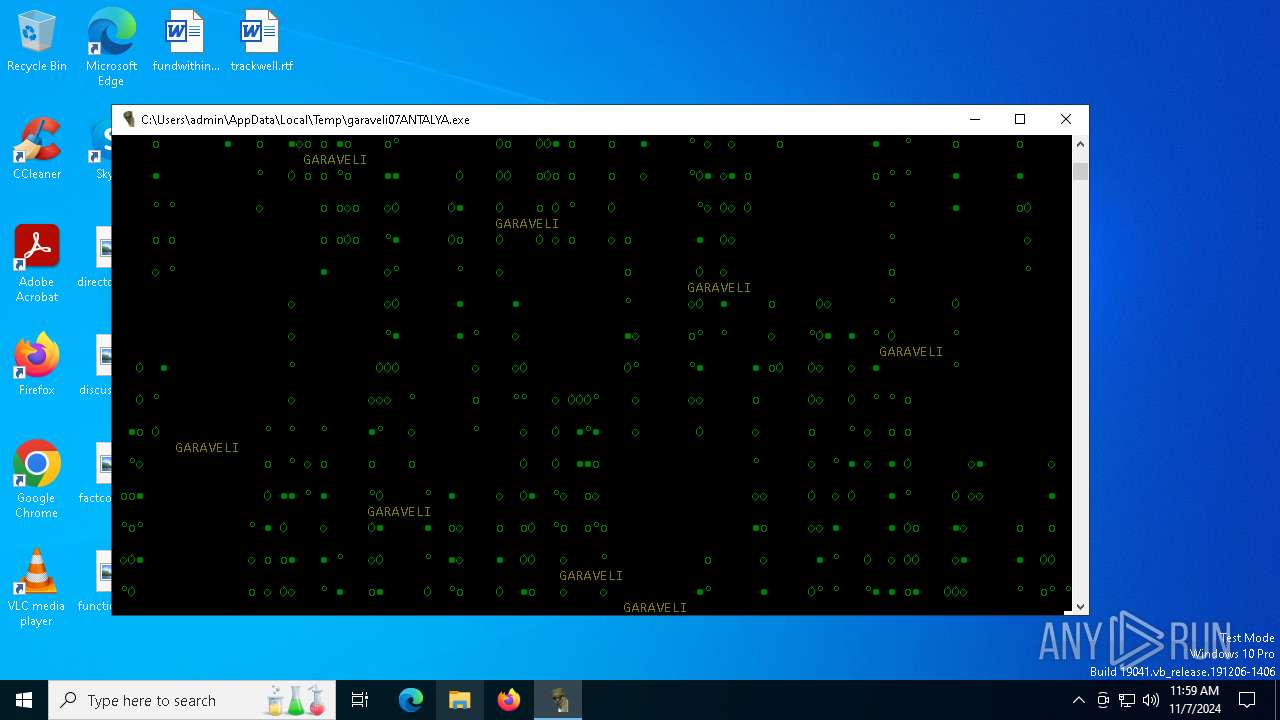
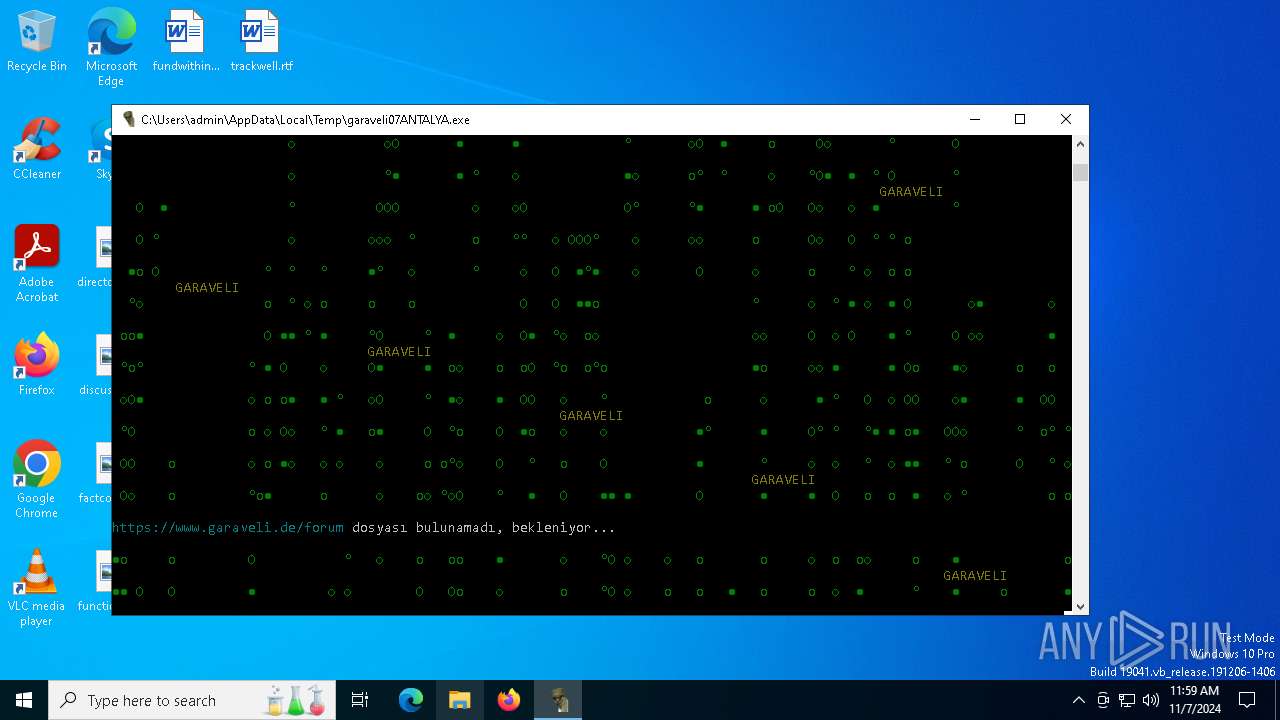
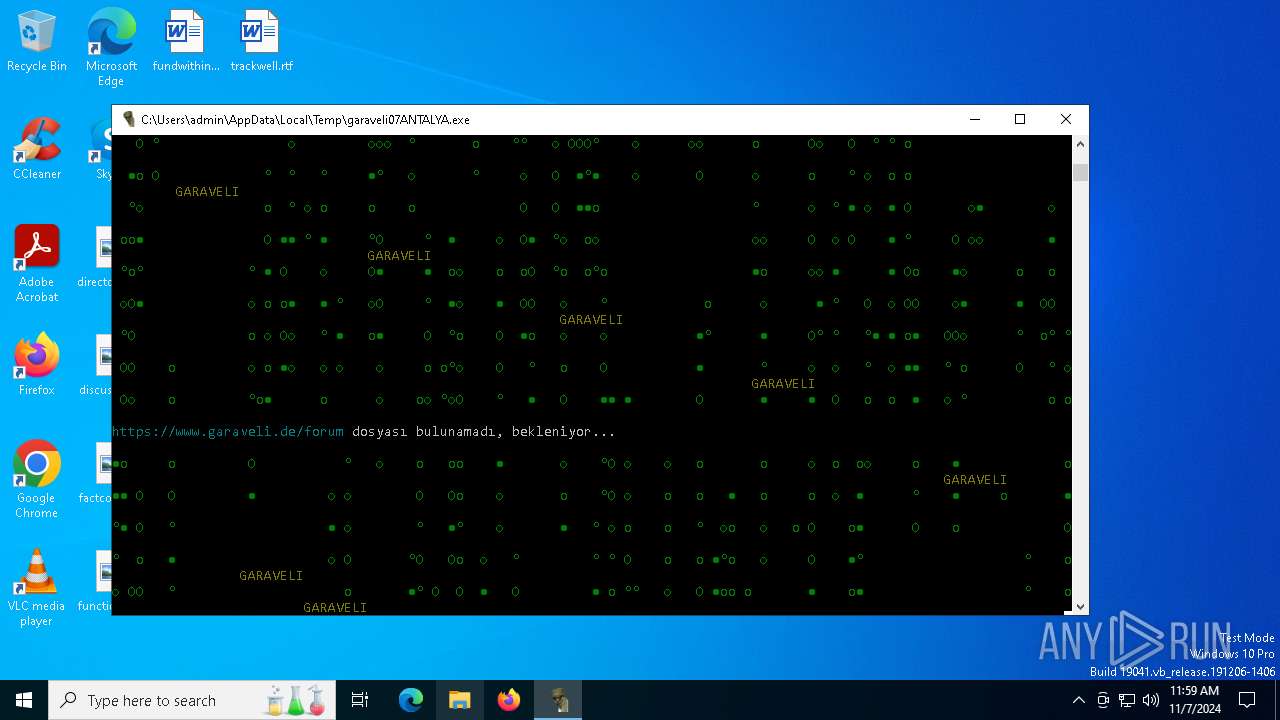
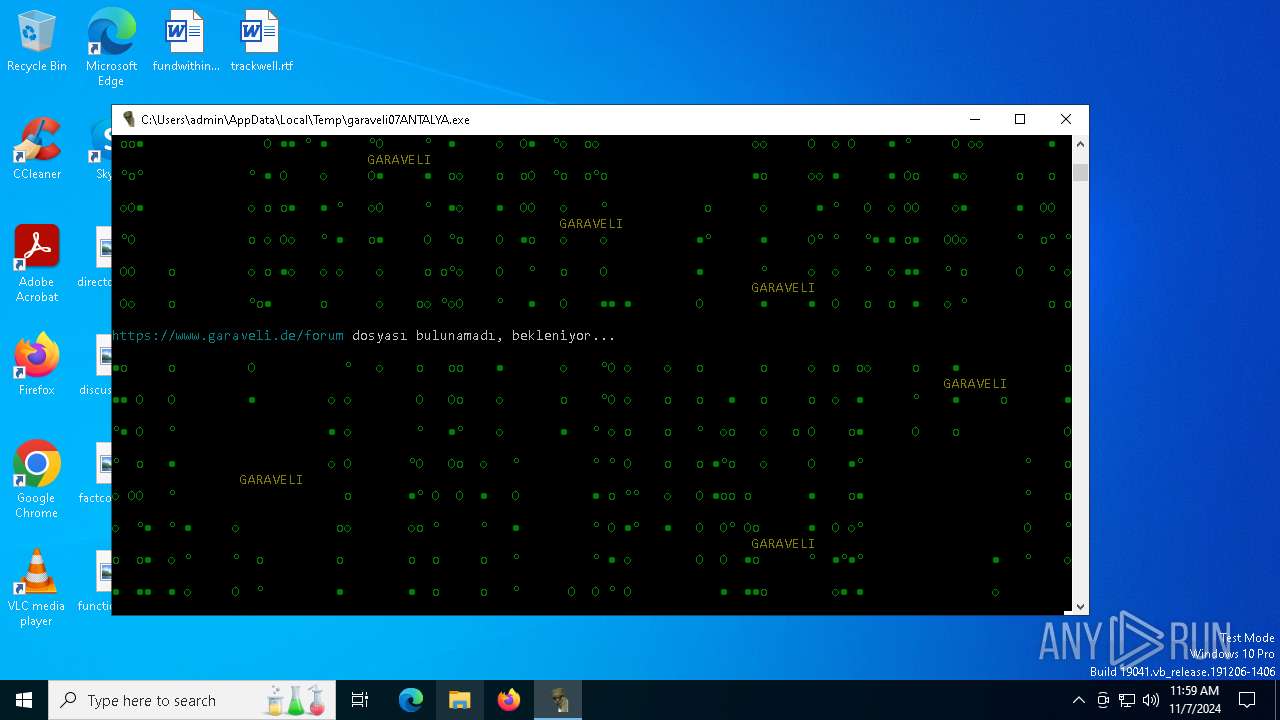
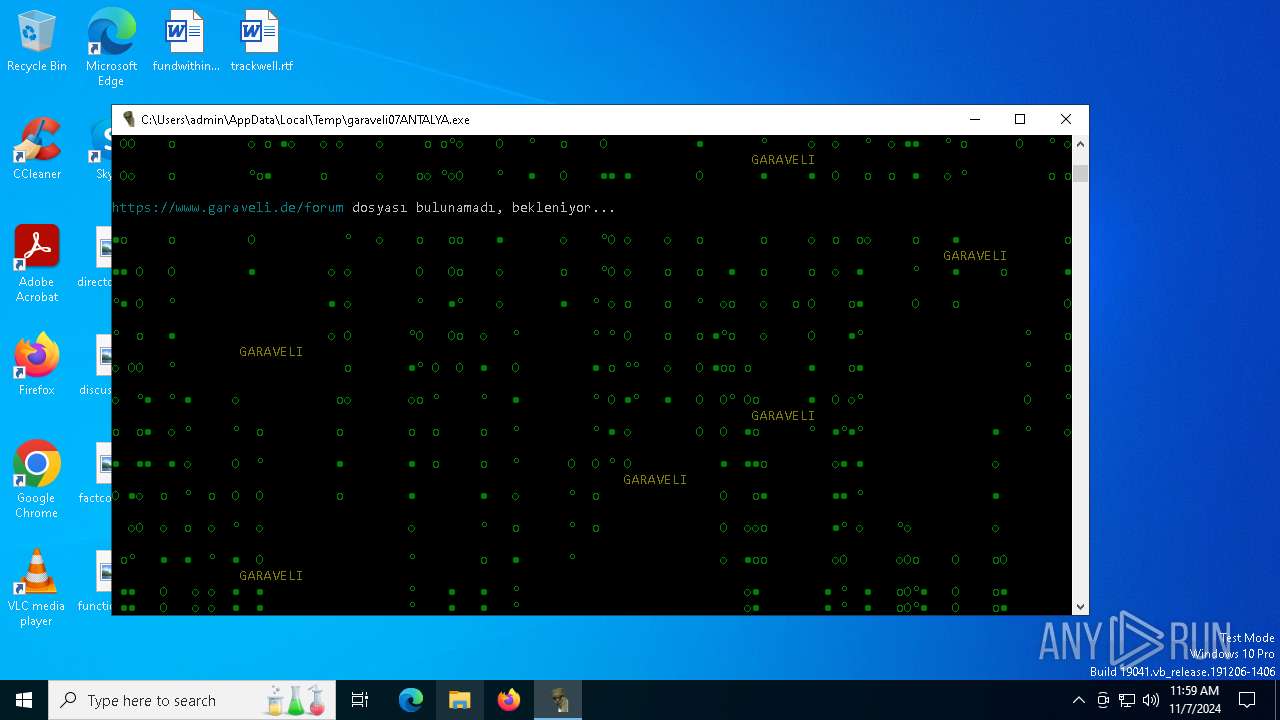
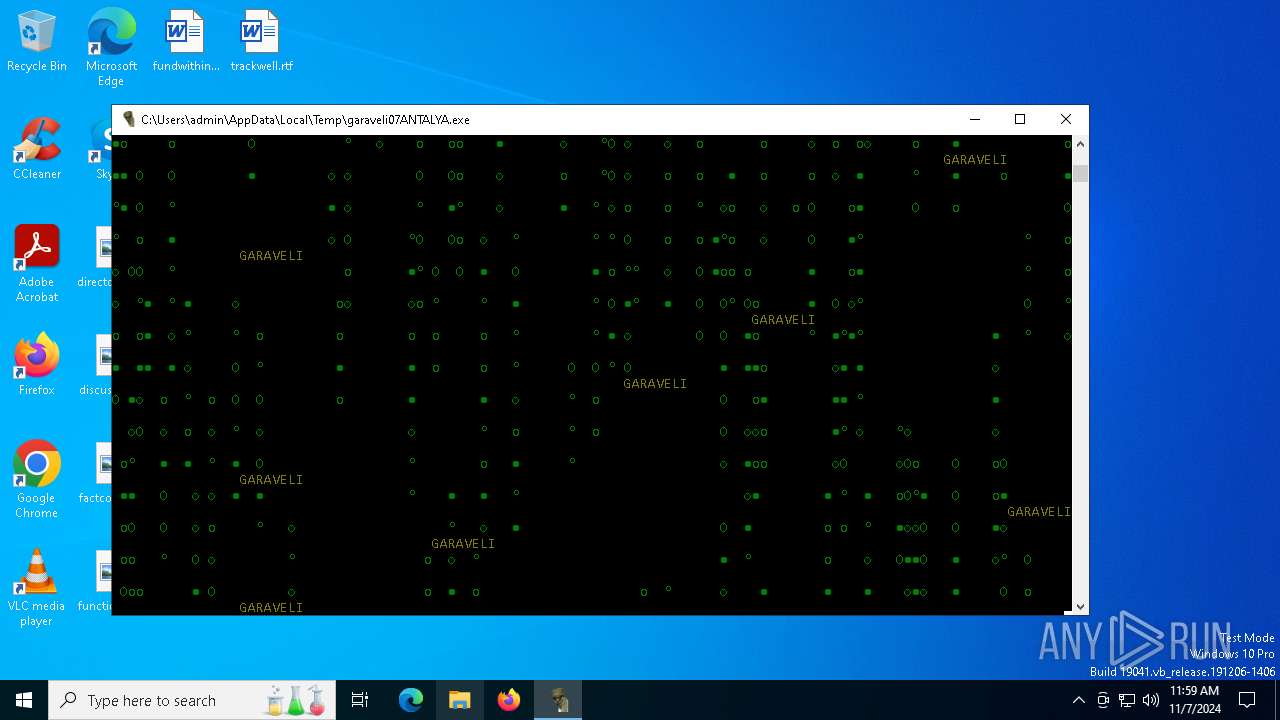
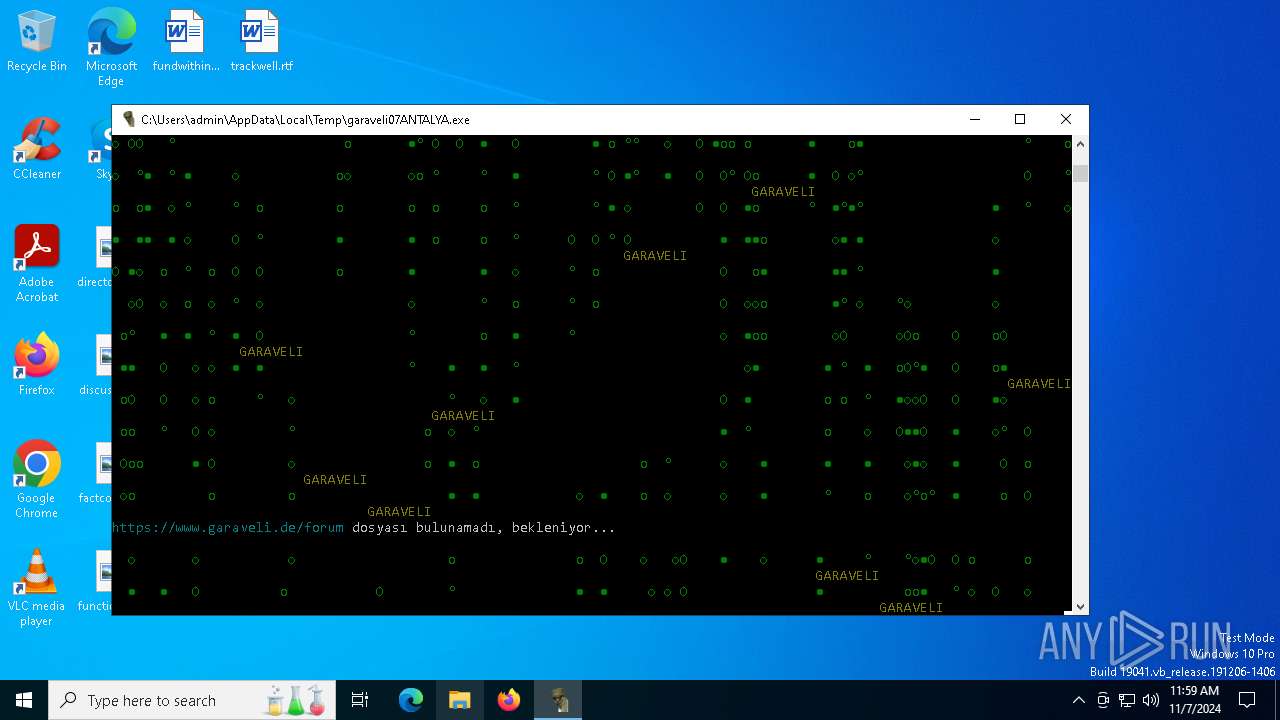
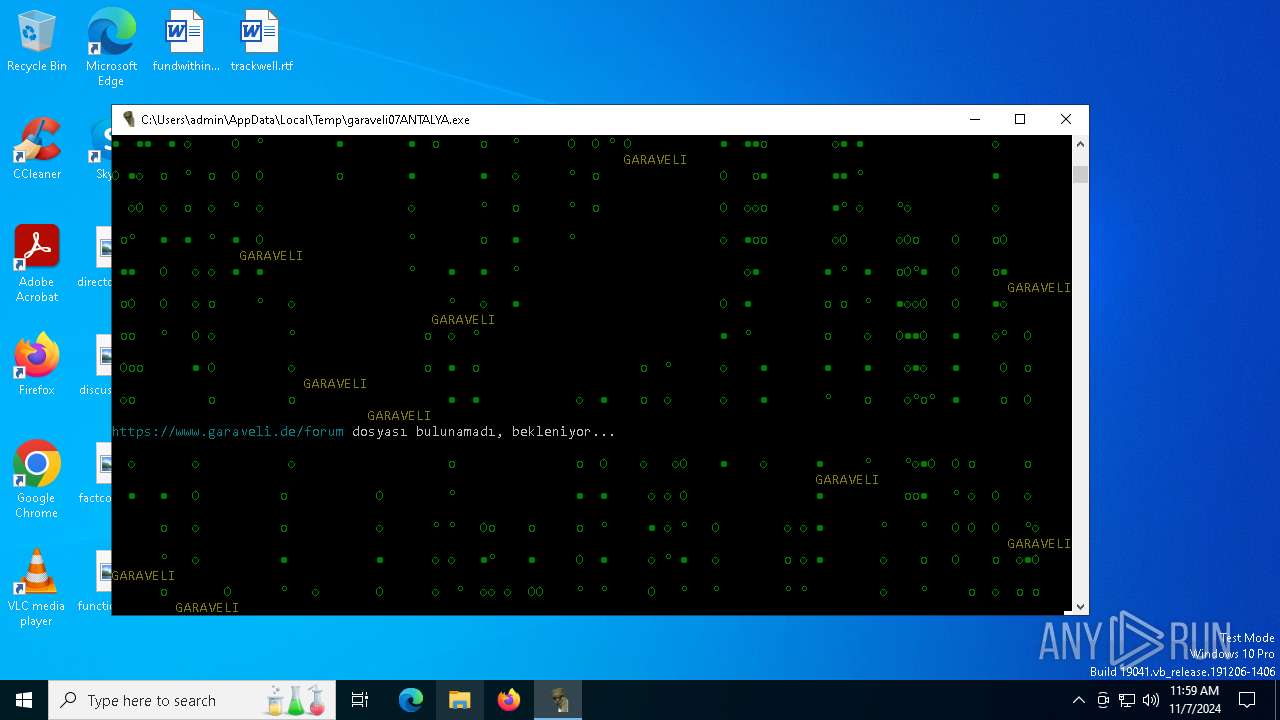
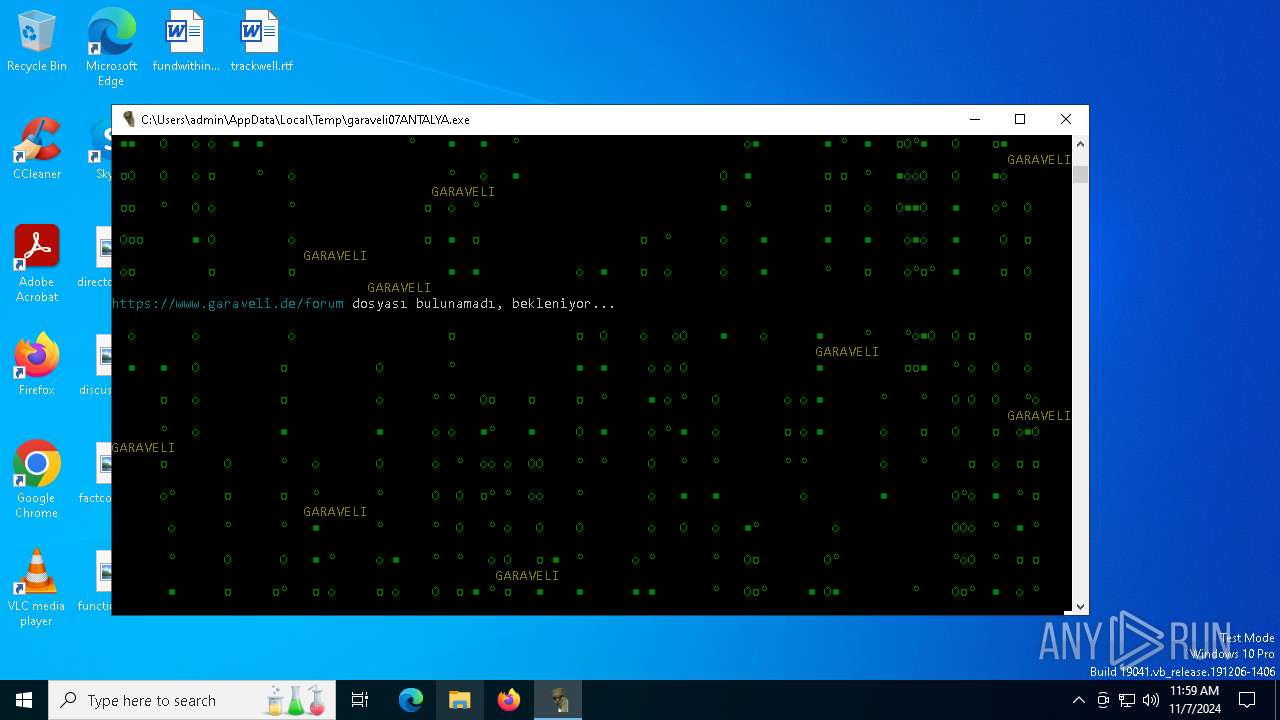
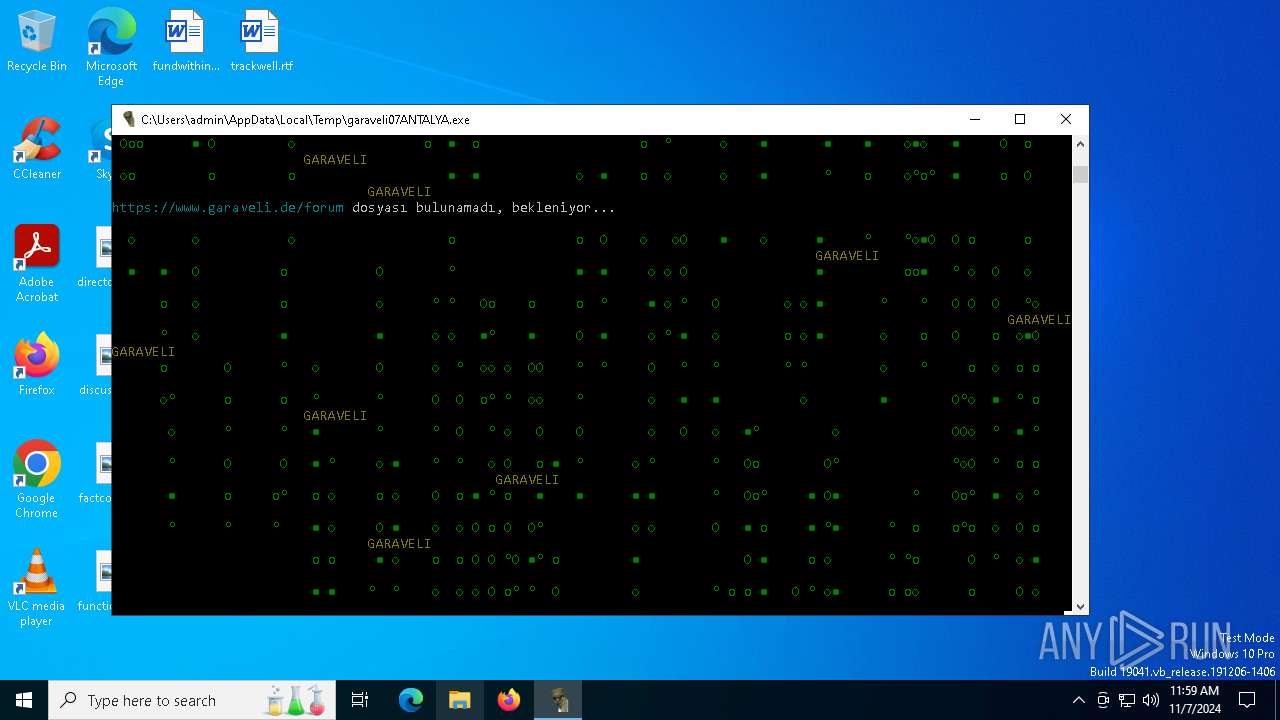
| File name: | garaveli07ANTALYA.exe |
| Full analysis: | https://app.any.run/tasks/388c94f5-a72f-4f85-a5c6-8da8c587981b |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2024, 11:58:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 9533FDC44E32F4651D34B29524604446 |
| SHA1: | D6C2F0203F37CD63FD9BE1A666925CC0B2CE17A7 |
| SHA256: | C630CF80906AE68D90BD5076580CBF516DF2B11CAFAD4954AD10D7F3FA094682 |
| SSDEEP: | 98304:FIyDP5QOByhZwlB4N+wcTAScUCYUlSA2ibMlq0ThIbjQrfmpfaQD7UJDZ2pli9TI:VcTyYIwnGoLkIW |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- garaveli07ANTALYA.exe (PID: 4088)
Process drops legitimate windows executable
- garaveli07ANTALYA.exe (PID: 4088)
Executable content was dropped or overwritten
- garaveli07ANTALYA.exe (PID: 4088)
Process drops python dynamic module
- garaveli07ANTALYA.exe (PID: 4088)
Application launched itself
- garaveli07ANTALYA.exe (PID: 4088)
Loads Python modules
- garaveli07ANTALYA.exe (PID: 6100)
Potential Corporate Privacy Violation
- garaveli07ANTALYA.exe (PID: 6100)
INFO
Checks supported languages
- garaveli07ANTALYA.exe (PID: 4088)
- garaveli07ANTALYA.exe (PID: 6100)
Create files in a temporary directory
- garaveli07ANTALYA.exe (PID: 4088)
Reads the computer name
- garaveli07ANTALYA.exe (PID: 4088)
- garaveli07ANTALYA.exe (PID: 6100)
Checks proxy server information
- garaveli07ANTALYA.exe (PID: 6100)
PyInstaller has been detected (YARA)
- garaveli07ANTALYA.exe (PID: 4088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:06 18:16:20+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
126
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4088 | "C:\Users\admin\AppData\Local\Temp\garaveli07ANTALYA.exe" | C:\Users\admin\AppData\Local\Temp\garaveli07ANTALYA.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | garaveli07ANTALYA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6100 | "C:\Users\admin\AppData\Local\Temp\garaveli07ANTALYA.exe" | C:\Users\admin\AppData\Local\Temp\garaveli07ANTALYA.exe | garaveli07ANTALYA.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
561
Read events
561
Write events
0
Delete events
0
Modification events
Executable files
15
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\base_library.zip | compressed | |
MD5:A9CBD0455B46C7D14194D1F18CA8719E | SHA256:DF6C19637D239BFEDC8CD13D20E0938C65E8FDF340622FF334DB533F2D30FA19 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\_lzma.pyd | executable | |
MD5:1BA022D42024A655CF289544AE461FB8 | SHA256:D080EABD015A3569813A220FD4EA74DFF34ED2A8519A10473EB37E22B1118A06 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\_ctypes.pyd | executable | |
MD5:A55E57D7594303C89B5F7A1D1D6F2B67 | SHA256:F63C6C7E71C342084D8F1A108786CA6975A52CEFEF8BE32CC2589E6E2FE060C8 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\_bz2.pyd | executable | |
MD5:CB8C06C8FA9E61E4AC5F22EEBF7F1D00 | SHA256:FC3B481684B926350057E263622A2A5335B149A0498A8D65C4F37E39DD90B640 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\python313.dll | executable | |
MD5:B9DE917B925DD246B709BB4233777EFD | SHA256:0C0A66505093B6A4BB3475F716BD3D9552095776F6A124709C13B3F9552C7D99 | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\select.pyd | executable | |
MD5:20831703486869B470006941B4D996F2 | SHA256:78E5994C29D8851F28B5B12D59D742D876683AEA58ECEEA1FB895B2036CDCDEB | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
| 4088 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\_MEI40882\unicodedata.pyd | executable | |
MD5:0902D299A2A487A7B0C2D75862B13640 | SHA256:2693C7EE4FBA55DC548F641C0CB94485D0E18596FFEF16541BD43A5104C28B20 | |||
| 6100 | garaveli07ANTALYA.exe | C:\Users\admin\AppData\Local\Temp\GARAVELI\benutzerkennwörter.txt | text | |
MD5:48447FCF3EBBBB64F4D2084887EC0E84 | SHA256:79EB48ADA5AB36A7DB12D5C1DF13E0E79EC1DDA5B80F2FD93F367818A9E30DAB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
80
DNS requests
21
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
6100 | garaveli07ANTALYA.exe | POST | 200 | 212.227.140.86:80 | http://netiptv.eu/token | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.16.110.195:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.216.77.24:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6100 | garaveli07ANTALYA.exe | 212.227.140.86:80 | netiptv.eu | IONOS SE | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
netiptv.eu |
| unknown |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
41 ETPRO signatures available at the full report