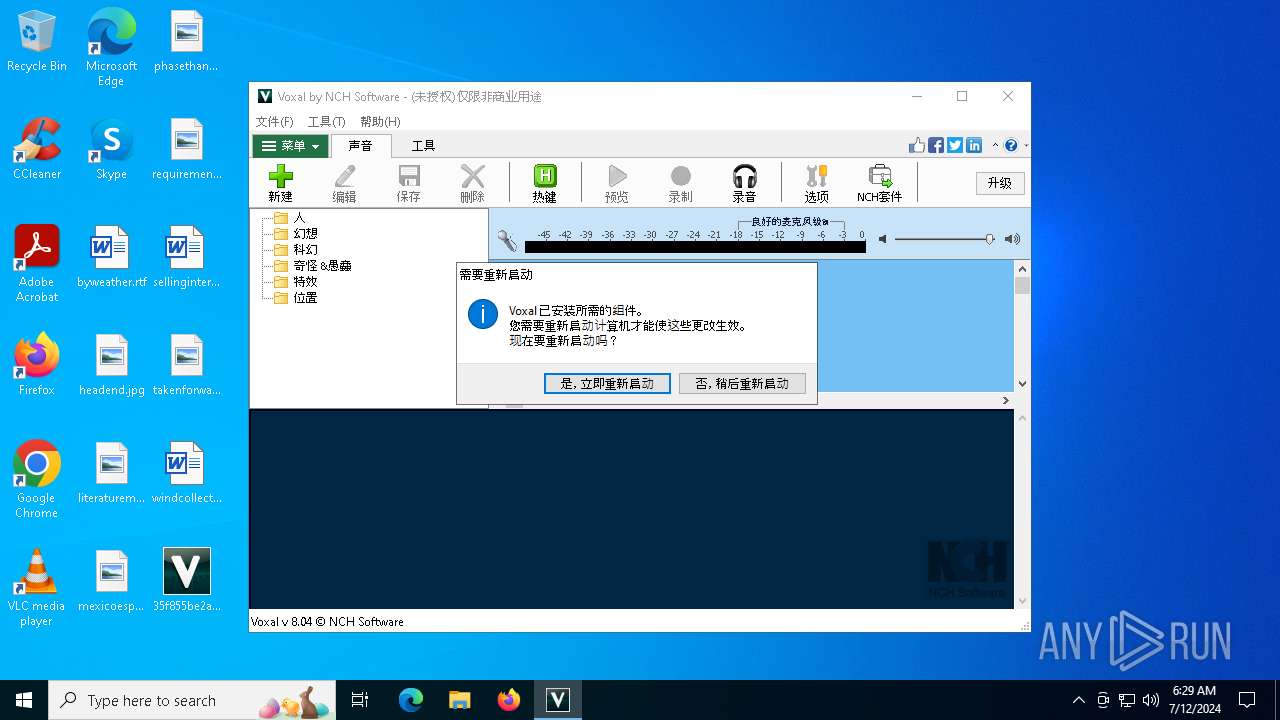
| File name: | 35f855be2a5cb77effee001a12bdd940N.exe |
| Full analysis: | https://app.any.run/tasks/02b96d90-9eb1-42ba-8573-ac6500f3d7c0 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2024, 06:28:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 35F855BE2A5CB77EFFEE001A12BDD940 |
| SHA1: | 44A9138F6FC9B3A616665EF93FD4658D01A953F2 |
| SHA256: | C62DDC1ECEBD58081C6B363550E9192DE5EE21D7C0BDF2F3D5555913F615B39C |
| SSDEEP: | 98304:/m9/MrCkWSO1K50PpwiuynkHLrKsPi4iyzsov75o:H2 |
MALICIOUS
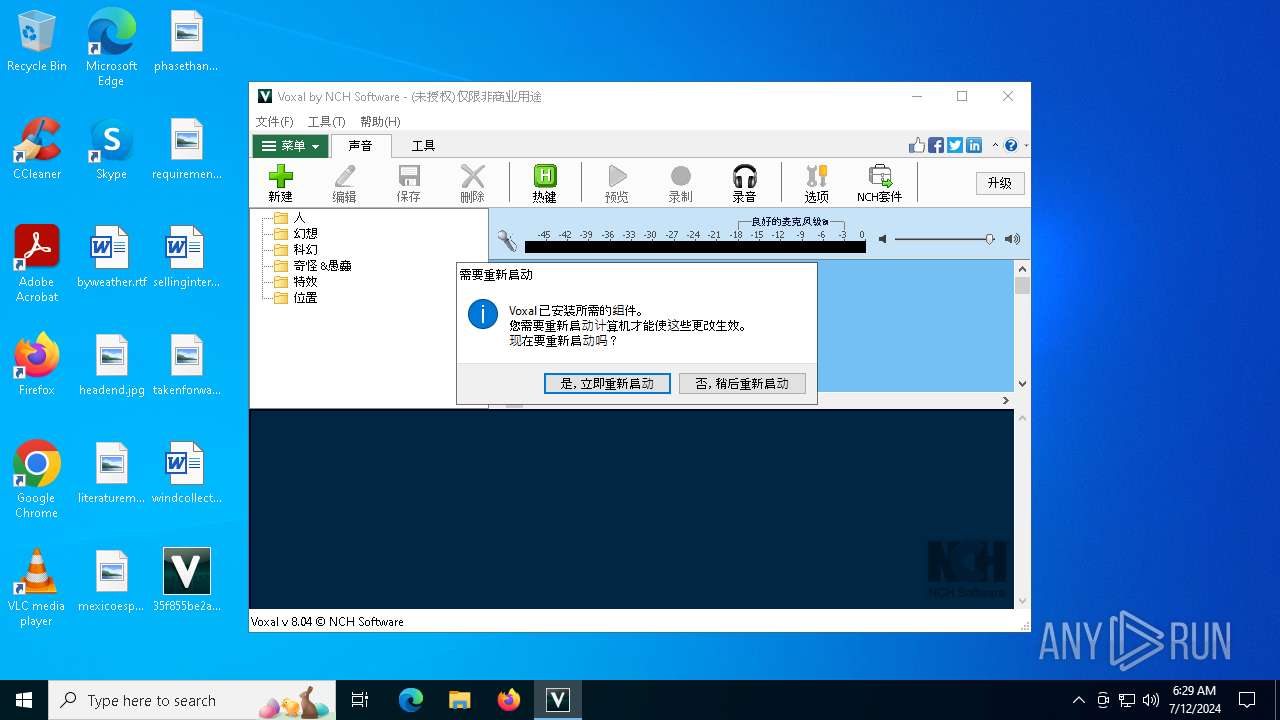
Drops the executable file immediately after the start
- 35f855be2a5cb77effee001a12bdd940N.exe (PID: 5432)
Scans artifacts that could help determine the target
- RUXIMICS.exe (PID: 4684)
SUSPICIOUS
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4032)
INFO
Checks supported languages
- 35f855be2a5cb77effee001a12bdd940N.exe (PID: 5432)
- PLUGScheduler.exe (PID: 4032)
- RUXIMICS.exe (PID: 4684)
- RUXIMICS.exe (PID: 4844)
Reads the computer name
- 35f855be2a5cb77effee001a12bdd940N.exe (PID: 5432)
- RUXIMICS.exe (PID: 4684)
- PLUGScheduler.exe (PID: 4032)
Creates files in the program directory
- 35f855be2a5cb77effee001a12bdd940N.exe (PID: 5432)
- PLUGScheduler.exe (PID: 4032)
- RUXIMICS.exe (PID: 4844)
Reads Environment values
- RUXIMICS.exe (PID: 4684)
Create files in a temporary directory
- 35f855be2a5cb77effee001a12bdd940N.exe (PID: 5432)
Reads the machine GUID from the registry
- RUXIMICS.exe (PID: 4684)
Reads the software policy settings
- RUXIMICS.exe (PID: 4684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:02 01:39:58+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 1910272 |
| InitializedDataSize: | 1087488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1bc645 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (Australian) |
| CharacterSet: | Unicode |
| CompanyName: | NCH Software |
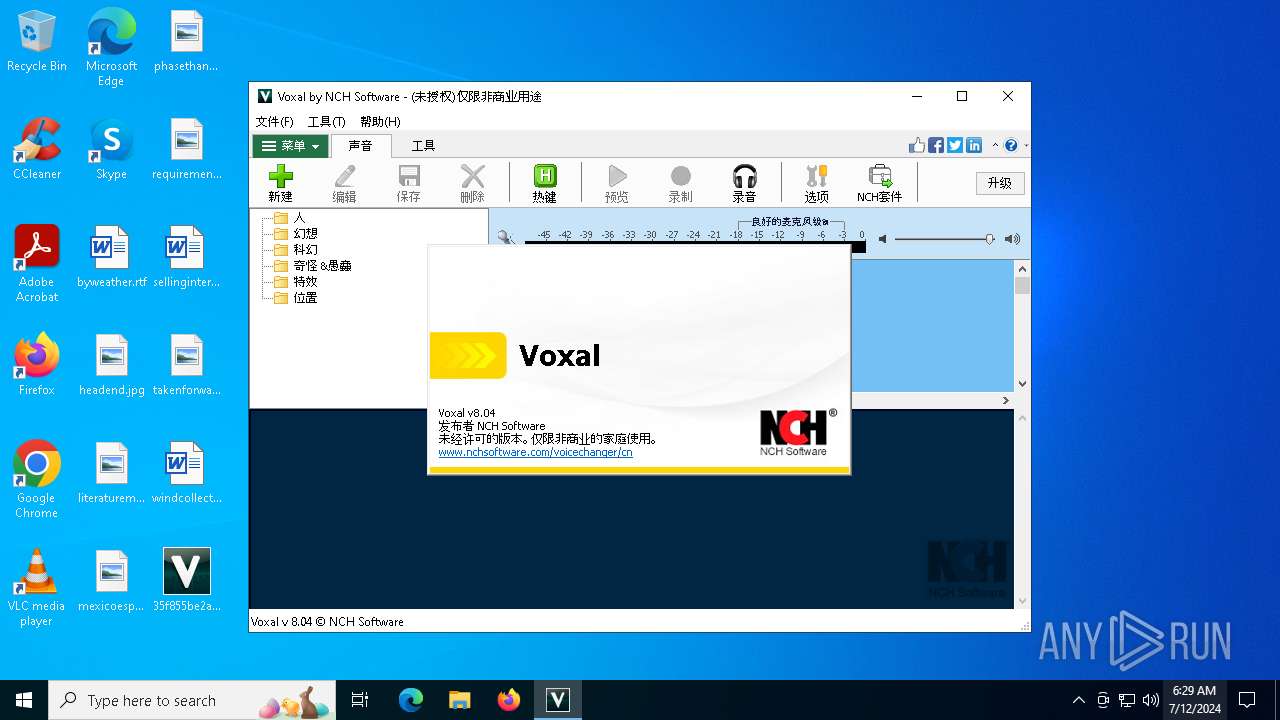
| FileDescription: | Voxal 变声器 |
| FileVersion: | 8.04CN |
| ProductVersion: | 8.04CN |
| ProductName: | Voxal |
| LegalCopyright: | NCH Software |
| InternalName: | Voxal |
| OriginalFileName: | Voxal.exe |
Total processes
233
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4032 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4684 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /onlyloadcampaigns | C:\Program Files\RUXIM\RUXIMICS.exe | PLUGScheduler.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /nonetwork | C:\Program Files\RUXIM\RUXIMICS.exe | — | PLUGScheduler.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5432 | "C:\Users\admin\Desktop\35f855be2a5cb77effee001a12bdd940N.exe" | C:\Users\admin\Desktop\35f855be2a5cb77effee001a12bdd940N.exe | — | explorer.exe | |||||||||||
User: admin Company: NCH Software Integrity Level: MEDIUM Description: Voxal 变声器 Exit code: 1073807364 Version: 8.04CN Modules
| |||||||||||||||
Total events
5 137
Read events
5 104
Write events
33
Delete events
0
Modification events
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Software |
| Operation: | write | Name: | SVar |
Value: LLIBControlon | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Registration |
| Operation: | write | Name: | Name |
Value: | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Registration\NCH |
| Operation: | write | Name: | Voxal |
Value: 1 | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Registration |
| Operation: | write | Name: | RD |
Value: 1720765746 | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Software |
| Operation: | write | Name: | SVar |
Value: LLIBControlonLLIBSpllnkulon | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Software |
| Operation: | write | Name: | SVar |
Value: LLIBControlonLLIBSpllnkulonLLIBSpltxtfadeoff | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Software |
| Operation: | write | Name: | SVar |
Value: LLIBControlonLLIBSpllnkulonLLIBSpltxtfadeoffVOXALDarkv3off | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Software |
| Operation: | write | Name: | SVar |
Value: LLIBControlonLLIBSpllnkulonLLIBSpltxtfadeoffVOXALDarkv3offVOXALTtbhamon | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Settings |
| Operation: | write | Name: | VoxalRunTimes |
Value: 1 | |||
| (PID) Process: | (5432) 35f855be2a5cb77effee001a12bdd940N.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NCH Software\Voxal\Audio |
| Operation: | write | Name: | LiveModeDefault |
Value: 1 | |||
Executable files
0
Suspicious files
41
Text files
0
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5432 | 35f855be2a5cb77effee001a12bdd940N.exe | C:\Users\admin\AppData\Local\Temp\VoxalCounts.txt | binary | |
MD5:F1D3FF8443297732862DF21DC4E57262 | SHA256:DF3F619804A92FDB4057192DC43DD748EA778ADC52BC498CE80524C014B81119 | |||
| 5432 | 35f855be2a5cb77effee001a12bdd940N.exe | C:\Users\admin\AppData\Local\Temp\~DFDA220FD392FDEF1C.TMP | binary | |
MD5:40D741E6DE7A8A8F6A2B65EF388DC587 | SHA256:001B837CC2BEE2896FFD9ED0CA177B2E235725B0CA170F75231EEA5764859833 | |||
| 5432 | 35f855be2a5cb77effee001a12bdd940N.exe | C:\Users\admin\AppData\Local\Temp\_voxal_rl_admin | binary | |
MD5:F15DA93E1D36F2944236CC0BB9A0626F | SHA256:A379866F999EB63C086C9A7C2C109AC2172774FB9F831176A27598DCC7AE27C5 | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.023.etl | etl | |
MD5:868E79A00A8204448B2FFC4F4D5C08EA | SHA256:148FE324431CB4C826BCF0436147D946AC389A877732612CF40629048B8517DC | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.022.etl | etl | |
MD5:44A0E917AD0C126931B1BCD959285A9A | SHA256:DDFBE47E7DFD6D8B7517F2F6FF9808ECF3C0A25F588A9F96D04F4E2B4A578573 | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.028.etl | etl | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.024.etl | etl | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.025.etl | etl | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.020.etl | etl | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 4032 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.017.etl | etl | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.126.37.160:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 52.109.28.46:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.16026&crev=3 | unknown | xml | 170 Kb | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/officeclicktorun/16.0.16026.20140/Production/CC?&Clientid=%7b48BA7FDF-353C-4FE5-8D8F-9E31911A3891%7d&Application=officeclicktorun&Platform=win32&Version=16.0.16026.20140&MsoVersion=16.0.16026.20140&ProcessName=officeclicktorun.exe&Audience=Production&Build=ship&Architecture=x64&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bAEDD9124-9B12-400D-8C5C-5D905C8D4402%7d&LabMachine=false | unknown | text | 334 Kb | unknown |
— | — | GET | 200 | 104.126.37.160:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.76 Kb | unknown |
— | — | POST | 200 | 20.189.173.16:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 104.126.37.131:443 | https://r.bing.com/rb/19/cir3,ortl,cc,nc/CYGXBN1kkA_ojDY5vKbCoG4Zy0E.css?bu=C9gIigOJBLIJmQiDCLgGWFhYWA&or=w | unknown | text | 19.9 Kb | unknown |
— | — | POST | 200 | 13.89.179.10:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 104.126.37.153:443 | https://r.bing.com/rb/16/jnc,nj/VhBuVeELUODW7ZIeVxh355D0F-g.js?bu=DygxcoQBiAGMAYEBe36_AcIBMbIBMcUB&or=w | unknown | s | 21.8 Kb | unknown |
— | — | POST | — | 104.126.37.153:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
376 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3164 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.116.246.105:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | DE | unknown |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |