| File name: | x2s443bc.cs1.exe |
| Full analysis: | https://app.any.run/tasks/722af6f4-c1d1-470c-950d-bcfc82dbd3b6 |
| Verdict: | Malicious activity |
| Analysis date: | September 01, 2024, 09:32:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CF2A00CDA850B570F0AA6266B9A5463E |
| SHA1: | AB9EB170448C95ECCB65BF0665AC9739021200B6 |
| SHA256: | C62CB66498344FC2374C0924D813711FF6FA00CAEA8581AE104C3C03B9233455 |
| SSDEEP: | 393216:x4qAB9wufflSR+eSHLZBsUOAyyYpqf9pzJfvht54QY3lZUEsB0:ODwuFeELZay06BJfpr4d4zB0 |
MALICIOUS
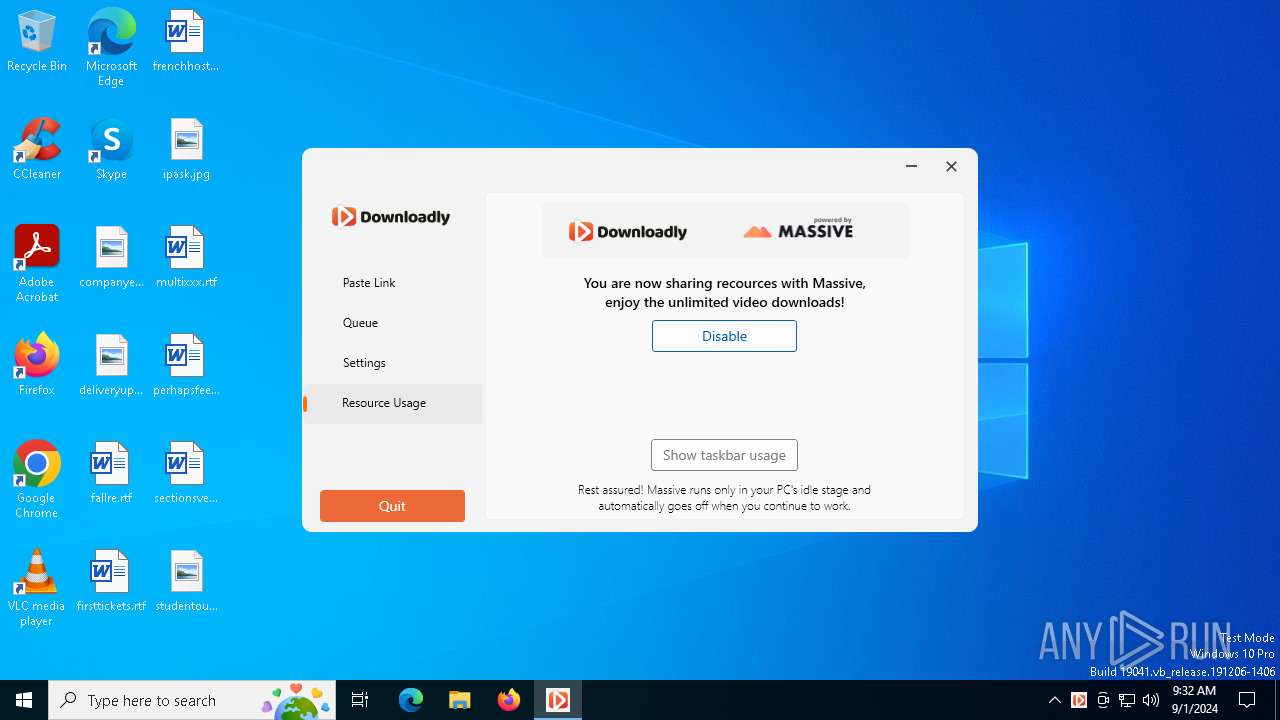
Changes the autorun value in the registry
- x2s443bc.cs1.tmp (PID: 6824)
- downloadly_installer.tmp (PID: 6196)
SUSPICIOUS
Executable content was dropped or overwritten
- x2s443bc.cs1.exe (PID: 5140)
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.exe (PID: 5284)
- MassiveInstaller.tmp (PID: 6560)
- downloadly_installer.exe (PID: 6840)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 2640)
- MassiveInstaller.exe (PID: 7004)
- MassiveInstaller.tmp (PID: 5900)
Drops the executable file immediately after the start
- x2s443bc.cs1.exe (PID: 5140)
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.exe (PID: 5284)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 2640)
- downloadly_installer.exe (PID: 6840)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.exe (PID: 7004)
- MassiveInstaller.tmp (PID: 5900)
Reads the Windows owner or organization settings
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
Reads security settings of Internet Explorer
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- Massive.exe (PID: 6628)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 6888)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
Uses TASKKILL.EXE to kill process
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
Reads the date of Windows installation
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 2640)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
Process drops legitimate windows executable
- x2s443bc.cs1.tmp (PID: 6824)
- downloadly_installer.tmp (PID: 6196)
Searches for installed software
- Downloadly.exe (PID: 2640)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 6888)
- MassiveInstaller.tmp (PID: 5900)
Checks Windows Trust Settings
- Downloadly.exe (PID: 2640)
The process checks if it is being run in the virtual environment
- Massive.exe (PID: 6628)
- Massive.exe (PID: 6492)
INFO
Checks supported languages
- x2s443bc.cs1.exe (PID: 5140)
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- MassiveInstaller.exe (PID: 5284)
- MassiveInstaller.tmp (PID: 6560)
- Massive.exe (PID: 6628)
- crashpad_handler.exe (PID: 1688)
- downloadly_installer.exe (PID: 6840)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 6888)
- MassiveInstaller.exe (PID: 7004)
- MassiveInstaller.tmp (PID: 5900)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
- crashpad_handler.exe (PID: 6488)
- crashpad_handler.exe (PID: 5264)
Create files in a temporary directory
- x2s443bc.cs1.exe (PID: 5140)
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.exe (PID: 5284)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 2640)
- downloadly_installer.exe (PID: 6840)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.exe (PID: 7004)
- MassiveInstaller.tmp (PID: 5900)
Reads the computer name
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- MassiveInstaller.tmp (PID: 6560)
- Massive.exe (PID: 6628)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 6888)
- MassiveInstaller.tmp (PID: 5900)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
Reads the machine GUID from the registry
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- Massive.exe (PID: 6628)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 6888)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
Reads the software policy settings
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- downloadly_installer.tmp (PID: 6196)
- Massive.exe (PID: 6628)
- Downloadly.exe (PID: 6888)
- Massive.exe (PID: 1448)
Process checks computer location settings
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 2640)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
The process uses the downloaded file
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- Downloadly.exe (PID: 2640)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
Creates a software uninstall entry
- x2s443bc.cs1.tmp (PID: 6824)
- MassiveInstaller.tmp (PID: 6560)
- downloadly_installer.tmp (PID: 6196)
- MassiveInstaller.tmp (PID: 5900)
Creates files or folders in the user directory
- x2s443bc.cs1.tmp (PID: 6824)
- Downloadly.exe (PID: 2640)
- Massive.exe (PID: 6628)
- crashpad_handler.exe (PID: 1688)
- downloadly_installer.tmp (PID: 6196)
- Downloadly.exe (PID: 6888)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
Reads Environment values
- Downloadly.exe (PID: 2640)
- Massive.exe (PID: 6628)
- Downloadly.exe (PID: 6888)
- Massive.exe (PID: 6492)
- Massive.exe (PID: 1448)
Checks proxy server information
- Downloadly.exe (PID: 2640)
- Massive.exe (PID: 6628)
- Downloadly.exe (PID: 6888)
Disables trace logs
- Downloadly.exe (PID: 2640)
- Downloadly.exe (PID: 6888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:06:03 08:09:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 37376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
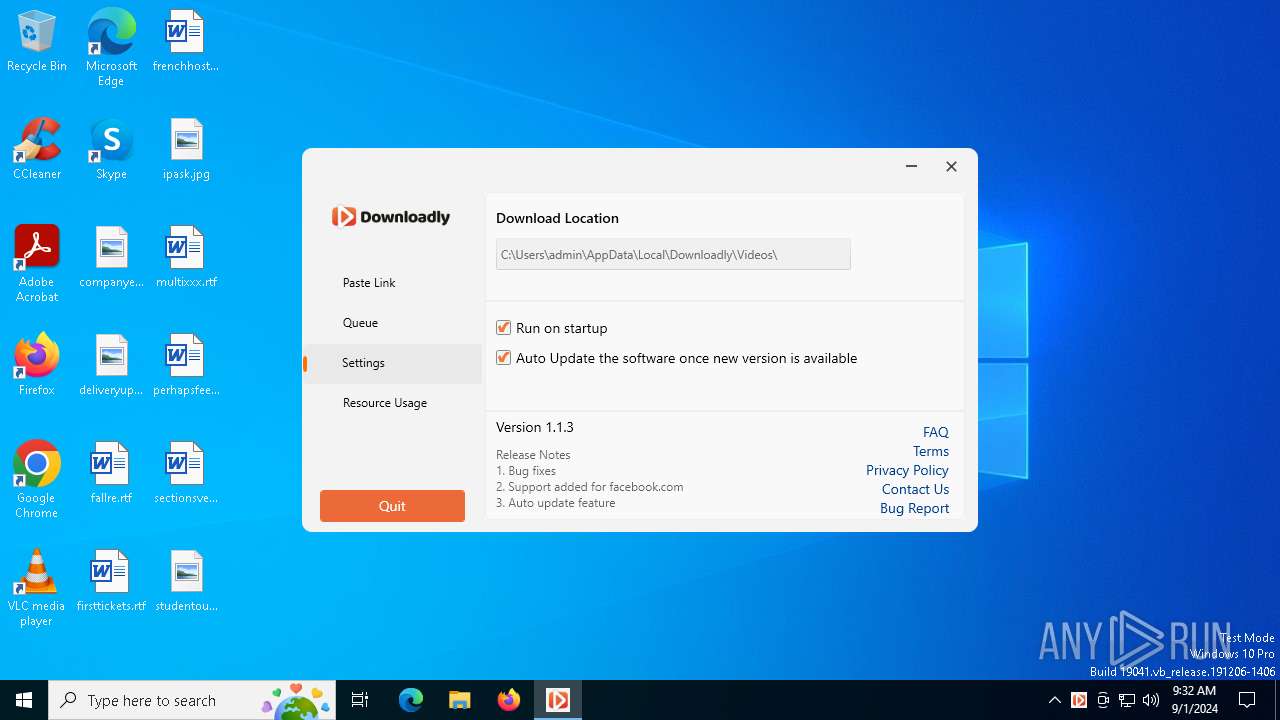
| Comments: | This installation was built with Inno Setup. |
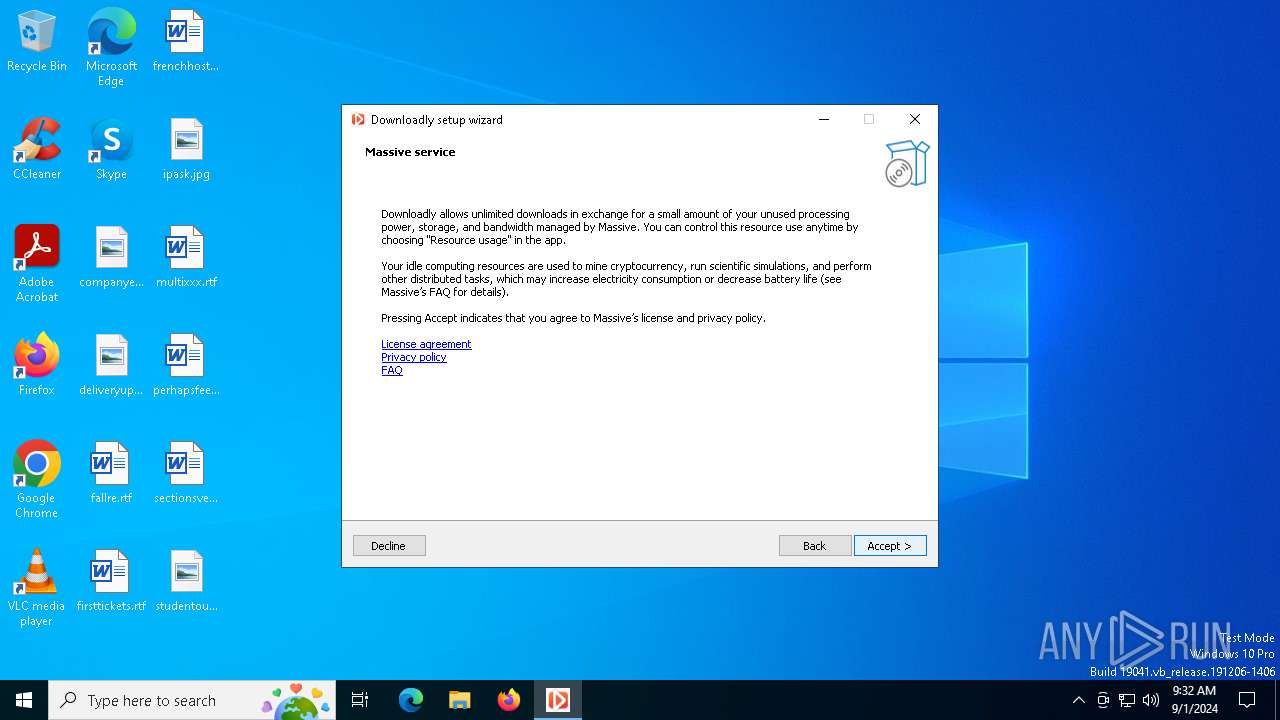
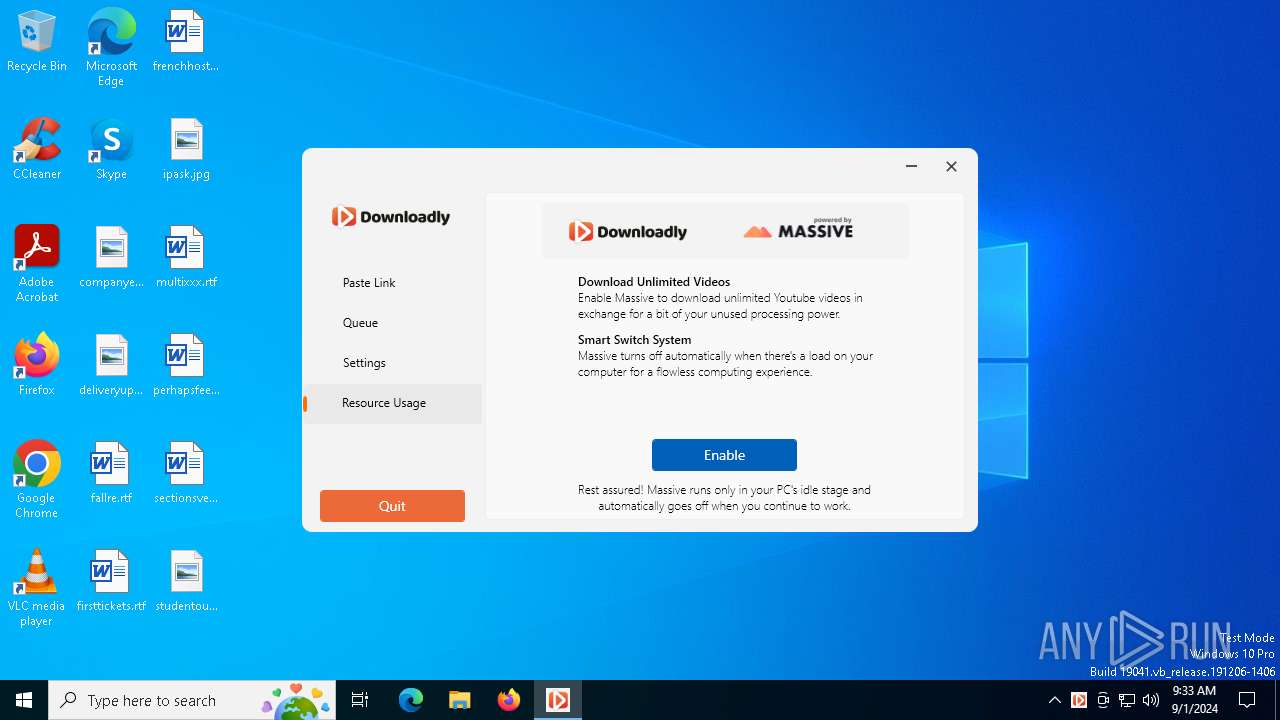
| CompanyName: | Massive Computing, Inc. |
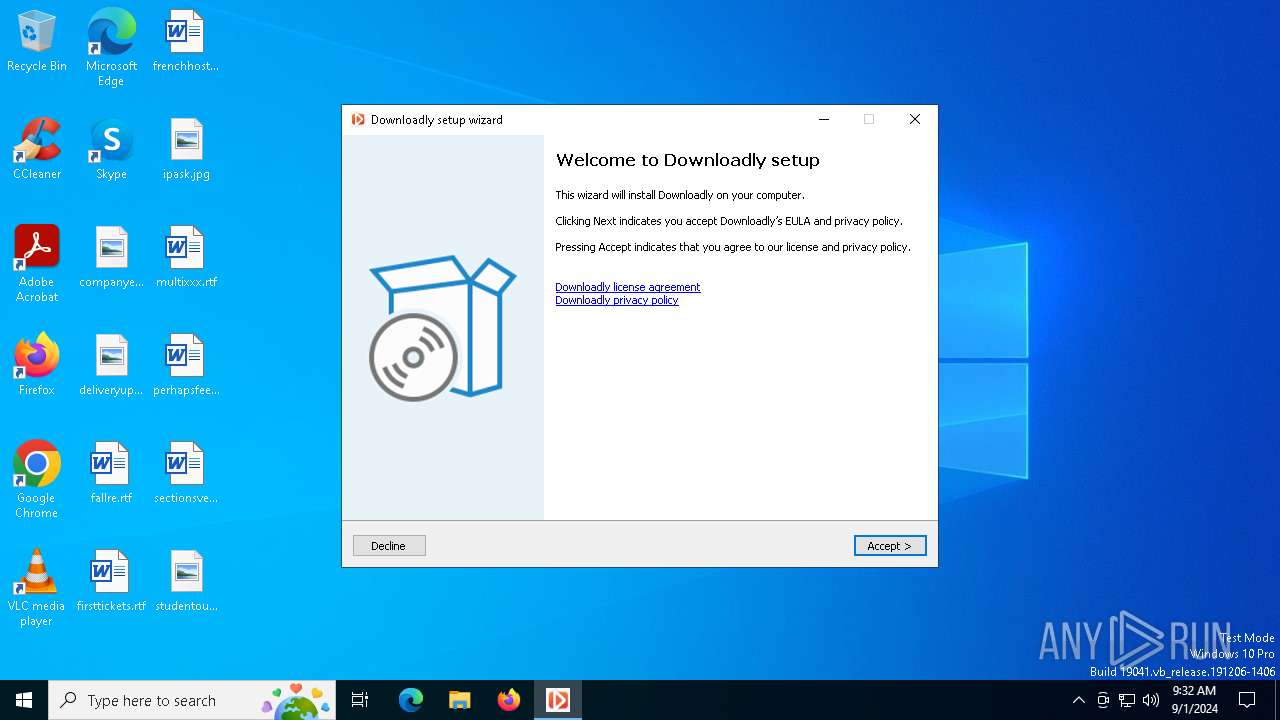
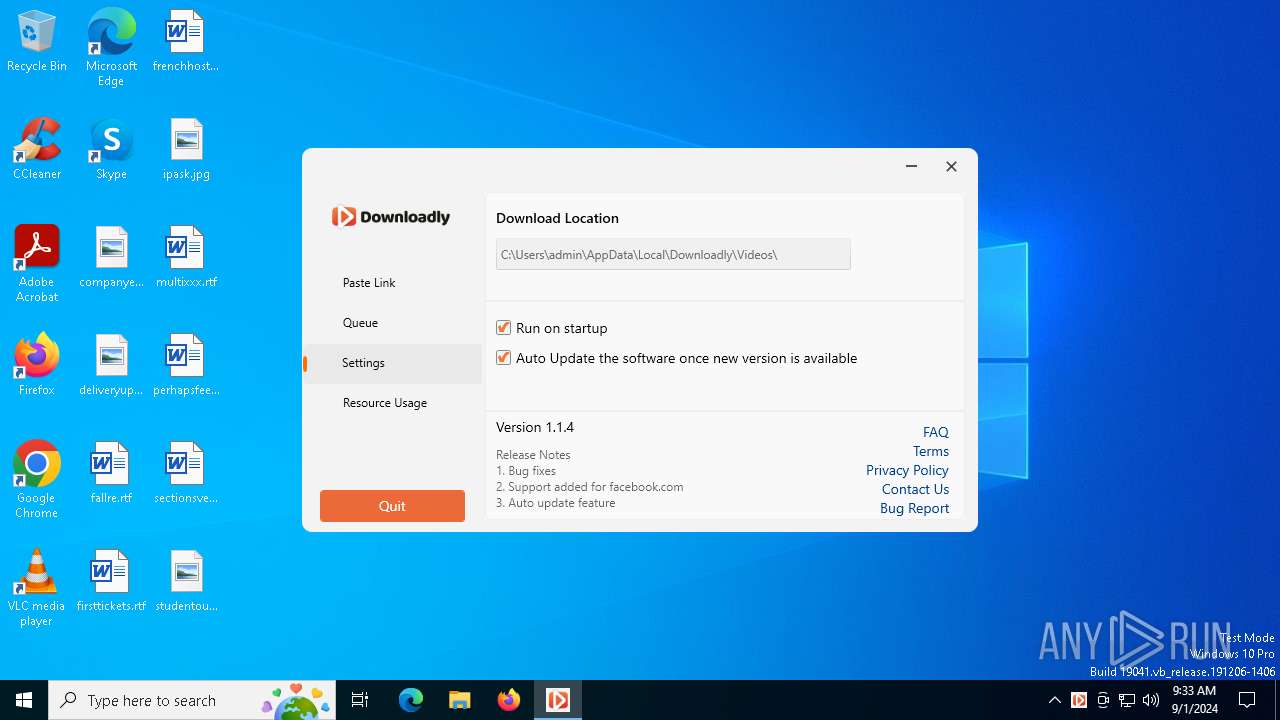
| FileDescription: | Downloadly setup |
| FileVersion: | 2.1.0 |
| LegalCopyright: | Copyright 2021-2022 Massive Computing, Inc. All rights reserved. |
| OriginalFileName: | |
| ProductName: | Downloadly |
| ProductVersion: | 1.1.3 |
Total processes
156
Monitored processes
30
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Windows\System32\taskkill.exe" /f /im MassiveUI.exe | C:\Windows\SysWOW64\taskkill.exe | — | MassiveInstaller.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | C:\Users\admin\Programs\Massive\Massive.exe | C:\Users\admin\Programs\Massive\Massive.exe | Downloadly.exe | ||||||||||||
User: admin Company: Massive Computing, Inc. Integrity Level: MEDIUM Description: Massive Exit code: 1 Version: 0.10.4.0 Modules
| |||||||||||||||
| 1688 | C:\Users\admin\Programs\Massive\crashpad_handler.exe --no-rate-limit --database=C:\Users\admin\AppData\Local\Massive\crashdumps --metrics-dir=C:\Users\admin\AppData\Local\Massive\crashdumps --url=https://o428832.ingest.sentry.io:443/api/5375291/minidump/?sentry_client=sentry.native/0.4.9&sentry_key=5647f16acff64576af0bbfb18033c983 --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\1633f0f3-aeed-41fa-af46-04d7a5bfe4cc.run\__sentry-event --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\1633f0f3-aeed-41fa-af46-04d7a5bfe4cc.run\__sentry-breadcrumb1 --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\1633f0f3-aeed-41fa-af46-04d7a5bfe4cc.run\__sentry-breadcrumb2 --initial-client-data=0x418,0x41c,0x420,0x3f0,0x424,0x7ff63e4b2fe0,0x7ff63e4b2fa0,0x7ff63e4b2fb0 | C:\Users\admin\Programs\Massive\crashpad_handler.exe | — | Massive.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | "C:\Windows\System32\taskkill.exe" /f /im Massive.exe | C:\Windows\SysWOW64\taskkill.exe | — | MassiveInstaller.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2640 | "C:\Users\admin\Programs\Downloadly\Downloadly.exe" EnablePro | C:\Users\admin\Programs\Downloadly\Downloadly.exe | x2s443bc.cs1.tmp | ||||||||||||
User: admin Company: Massive Computing, Inc. Integrity Level: MEDIUM Description: Download YouTube videos for free Exit code: 1 Version: 1.1.3.0 Modules
| |||||||||||||||
| 3028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4524 | "C:\Windows\System32\taskkill.exe" /f /im Downloadly.exe | C:\Windows\SysWOW64\taskkill.exe | — | downloadly_installer.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5140 | "C:\Users\admin\AppData\Local\Temp\x2s443bc.cs1.exe" | C:\Users\admin\AppData\Local\Temp\x2s443bc.cs1.exe | explorer.exe | ||||||||||||
User: admin Company: Massive Computing, Inc. Integrity Level: MEDIUM Description: Downloadly setup Exit code: 0 Version: 2.1.0 Modules
| |||||||||||||||
| 5264 | C:\Users\admin\Programs\Massive\crashpad_handler.exe --no-rate-limit --database=C:\Users\admin\AppData\Local\Massive\crashdumps --metrics-dir=C:\Users\admin\AppData\Local\Massive\crashdumps --url=https://o428832.ingest.sentry.io:443/api/5375291/minidump/?sentry_client=sentry.native/0.4.9&sentry_key=5647f16acff64576af0bbfb18033c983 --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\e6c01a32-0d65-4d3f-906e-9b4a1cba1bb8.run\__sentry-event --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\e6c01a32-0d65-4d3f-906e-9b4a1cba1bb8.run\__sentry-breadcrumb1 --attachment=C:\Users\admin\AppData\Local\Massive\crashdumps\e6c01a32-0d65-4d3f-906e-9b4a1cba1bb8.run\__sentry-breadcrumb2 --initial-client-data=0x3a4,0x3a8,0x3ac,0x378,0x3b0,0x7ff6fabd2dc8,0x7ff6fabd2de8,0x7ff6fabd2e00 | C:\Users\admin\Programs\Massive\crashpad_handler.exe | — | Massive.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5284 | C:\Users\admin\Programs\Downloadly\MassiveInstaller.exe /SP- /VERYSILENT /NOICONS /SUPPRESSMSGBOXES /AllowStatusPage=false /ShowUI=false /DIR="C:\Users\admin\Programs\Massive" | C:\Users\admin\Programs\Downloadly\MassiveInstaller.exe | Downloadly.exe | ||||||||||||
User: admin Company: Massive Computing, Inc. Integrity Level: MEDIUM Description: Massive setup Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
30 127
Read events
29 913
Write events
187
Delete events
27
Modification events
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A81A0000B7A5C7D251FCDA01 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: CE492D0B229D28EBEEDFB85D7E7A7B35E9C2CB582CBE1C93A3CCBB4AFFF7FD3D | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\Programs\Downloadly\MassiveInstaller.exe | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 8E7B1A46917DB47FD576F96CD97317D07E66E414B5B6233445978ED975680C48 | |||
| (PID) Process: | (6824) x2s443bc.cs1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Downloadly |
Value: "C:\Users\admin\Programs\Downloadly\Downloadly.exe" | |||
Executable files
241
Suspicious files
20
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5140 | x2s443bc.cs1.exe | C:\Users\admin\AppData\Local\Temp\is-1JSD0.tmp\x2s443bc.cs1.tmp | executable | |
MD5:0D5DC73779288FD019D9102766B0C7DE | SHA256:0A3D1D00BFDBDED550D21DF30275BE9BCA83FB74CA3B2AABD4B0886A5D7CC289 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\is-E4SSD.tmp | executable | |
MD5:DF851A46DF574A7DDF3D79F20B3A8D70 | SHA256:02BDDE9831C72990FAD44EE43602215EC1A66F2CF25C8B012772BE5AF8142904 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\is-A1V70.tmp | executable | |
MD5:0D5DC73779288FD019D9102766B0C7DE | SHA256:0A3D1D00BFDBDED550D21DF30275BE9BCA83FB74CA3B2AABD4B0886A5D7CC289 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\unins000.exe | executable | |
MD5:0D5DC73779288FD019D9102766B0C7DE | SHA256:0A3D1D00BFDBDED550D21DF30275BE9BCA83FB74CA3B2AABD4B0886A5D7CC289 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\AppData\Local\Temp\is-NTNAV.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\Downloadly.exe | executable | |
MD5:C64463E64B12C0362C622176C404B6AF | SHA256:140DCFC3BDE8405D26CFE50E08DE2A084FB3BE7CF33894463A182E12001F5CE7 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\is-3SGIP.tmp | executable | |
MD5:0E2101E01D27DCDCB065676702EB7513 | SHA256:F666932A8D2F66C01A32DF6C7FCB16EF2274EAC765B0D085DB43D4264139FEE1 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\libvideo.dll | executable | |
MD5:0E2101E01D27DCDCB065676702EB7513 | SHA256:F666932A8D2F66C01A32DF6C7FCB16EF2274EAC765B0D085DB43D4264139FEE1 | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\GalaSoft.MvvmLight.dll | executable | |
MD5:B0126AE2C9BE757BDA6E741924C4DEA9 | SHA256:C13AD1D38FEFB9D8AED071A82BD5BCE2687EC1CABB819F30850088842E6DBE7B | |||
| 6824 | x2s443bc.cs1.tmp | C:\Users\admin\Programs\Downloadly\is-71G8T.tmp | executable | |
MD5:7151DE121B4FE6857717320F96DBF93D | SHA256:4BE4FBB5E480F7DCE0ECAB4D0EF297EE9D761FD60BF1E4FE41A114B03D88F217 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
53
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2640 | Downloadly.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2640 | Downloadly.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
2640 | Downloadly.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5048 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6056 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6424 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6824 | x2s443bc.cs1.tmp | 18.244.18.77:443 | api.joinmassive.com | — | US | suspicious |
6056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 20.7.1.246:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1944 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1944 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.joinmassive.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
Process | Message |
|---|---|
Downloadly.exe | log4net: Configuration update mode [Merge].
|
Downloadly.exe | log4net: Logger [root] Level string is [ALL].
|
Downloadly.exe | log4net: Logger [root] level set to [name="ALL",value=-2147483648].
|
Downloadly.exe | log4net: Loading Appender [RollingLogFileAppender] type: [log4net.Appender.RollingFileAppender]
|
Downloadly.exe | log4net: Parameter [file] specified subtype [log4net.Util.PatternString]
|
Downloadly.exe | log4net: Converter [literal] Option [C:\Users\admin\AppData\Local\\Downloadly\\Logs\\downloadly.log] Format [min=-1,max=2147483647,leftAlign=False]
|
Downloadly.exe | log4net: Performing additional conversion of value from [PatternString] to [String]
|
Downloadly.exe | log4net: Setting Property [File] to String value [C:\Users\admin\AppData\Local\\Downloadly\\Logs\\downloadly.log]
|
Downloadly.exe | log4net: Setting Property [LockingModel] to object [log4net.Appender.FileAppender+MinimalLock]
|
Downloadly.exe | log4net: Setting Property [AppendToFile] to Boolean value [True]
|