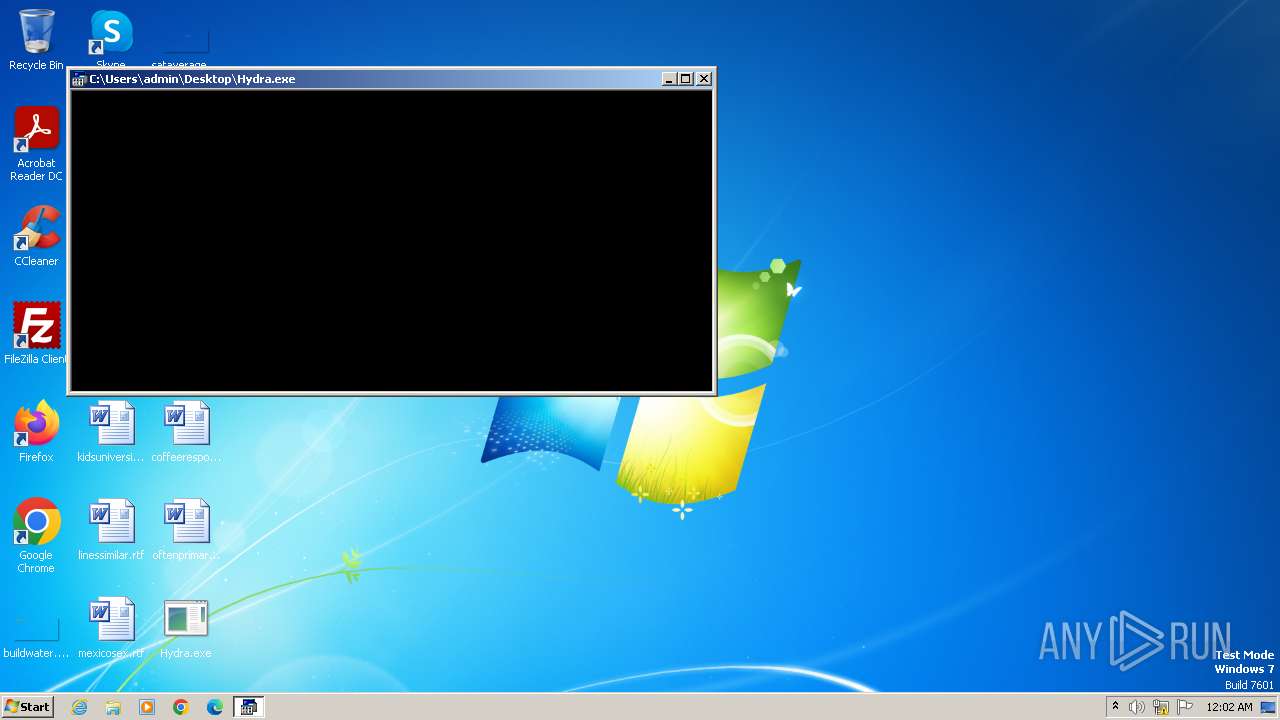
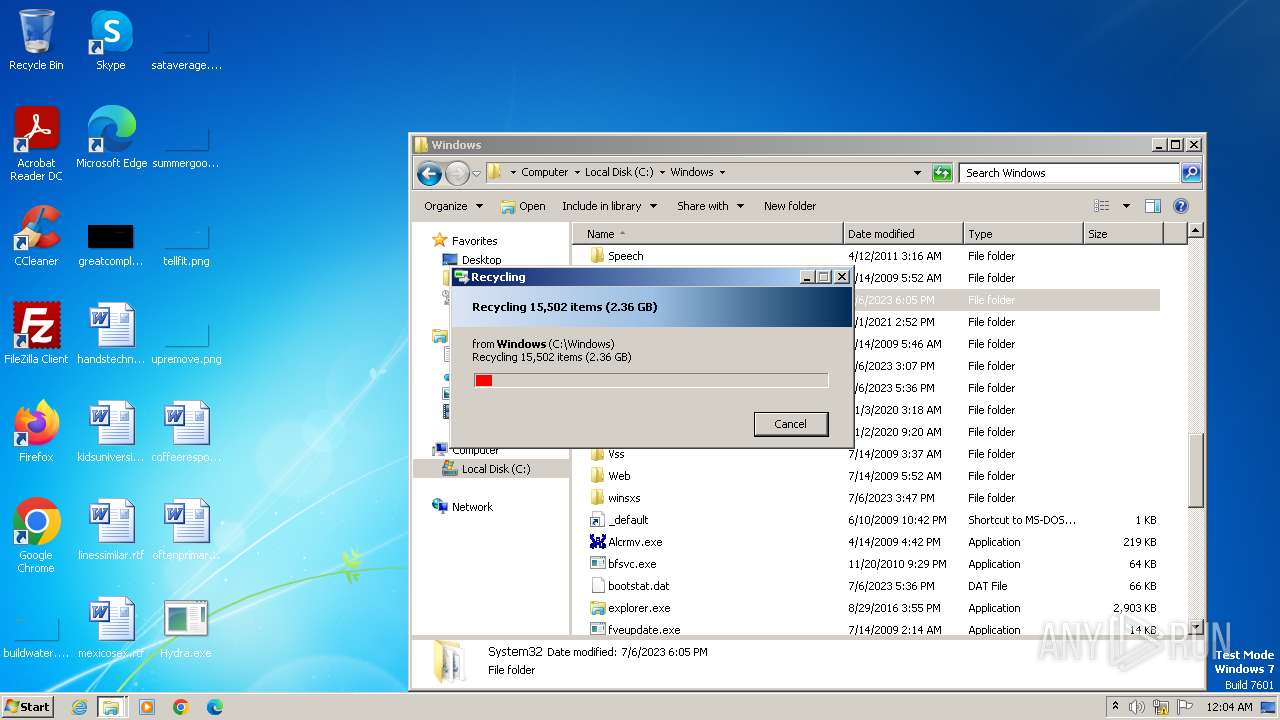
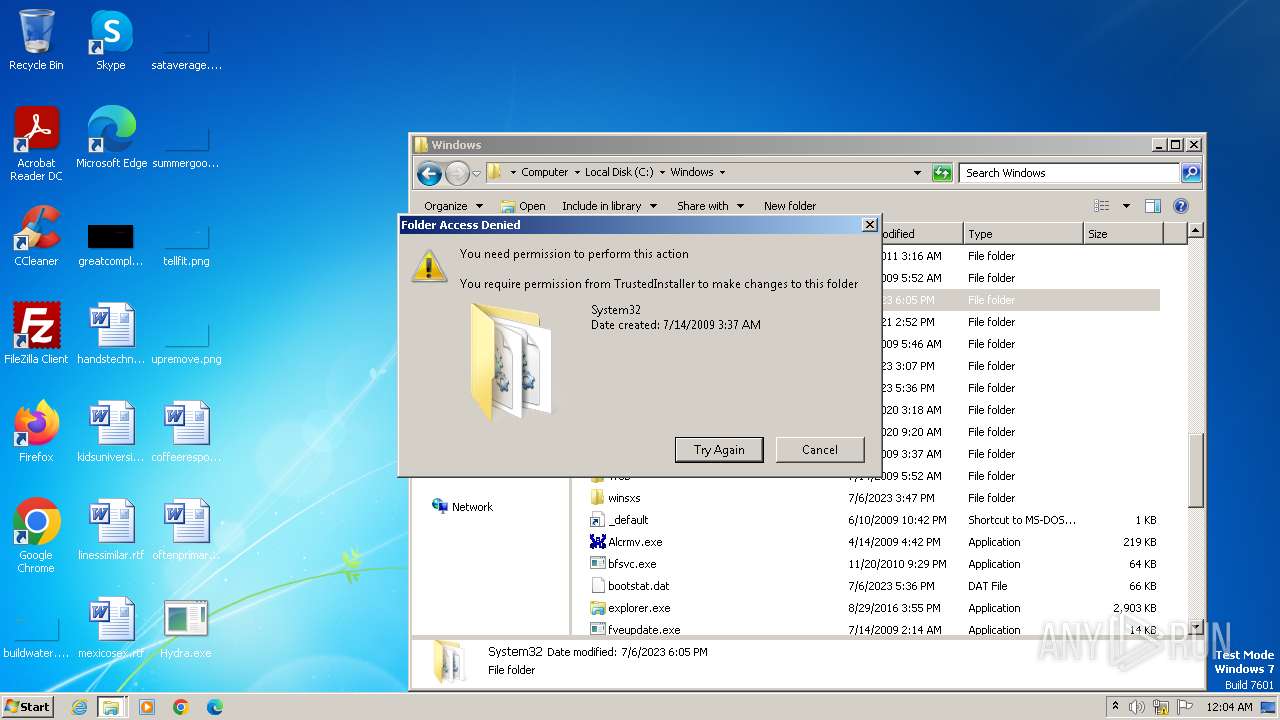
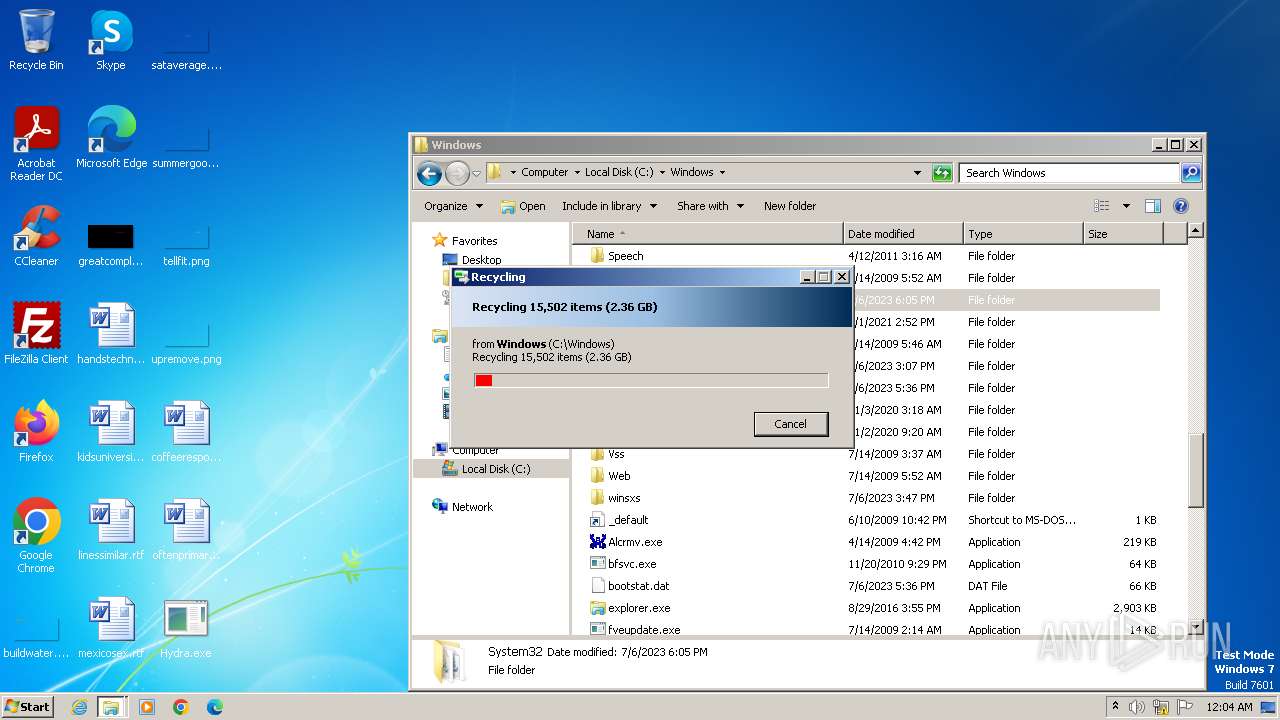
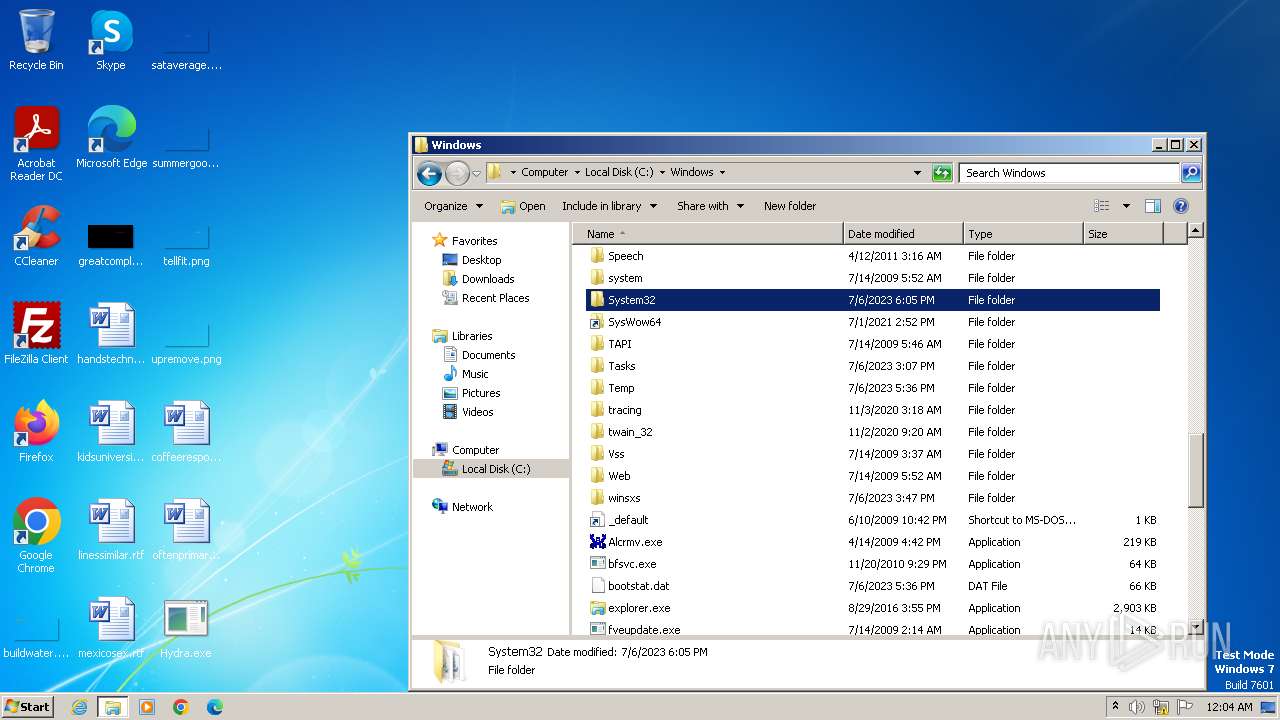
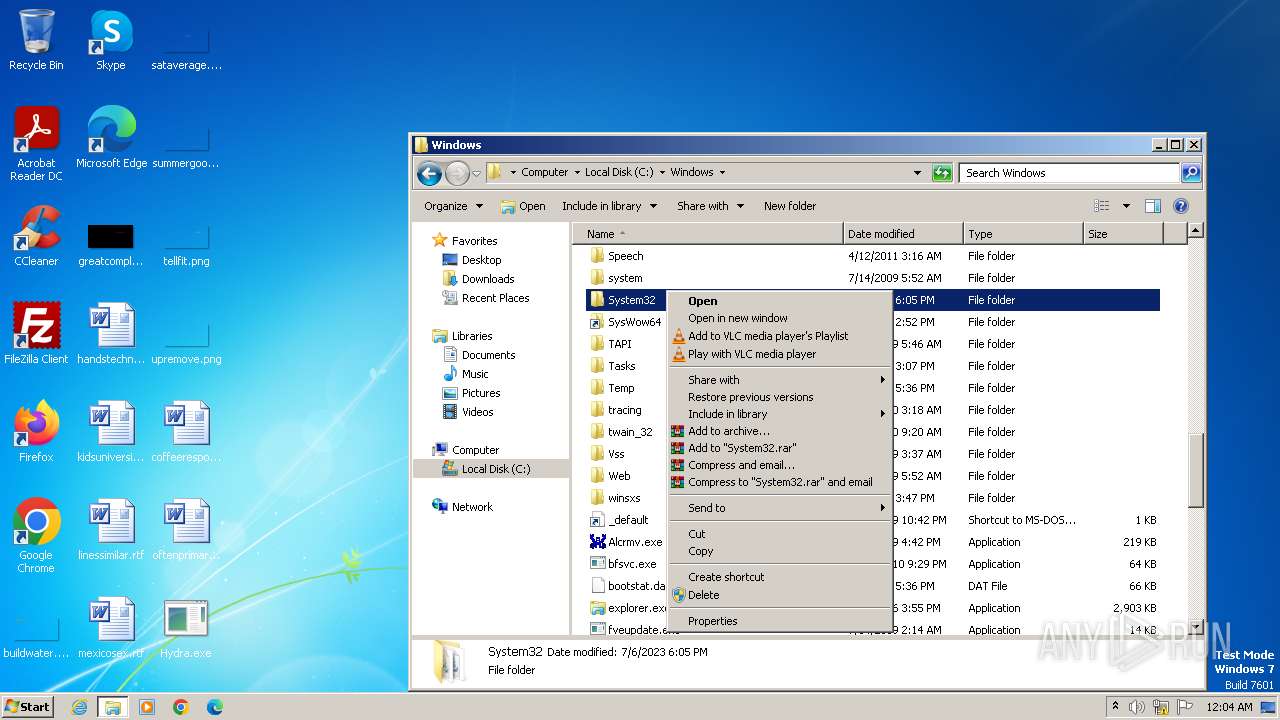
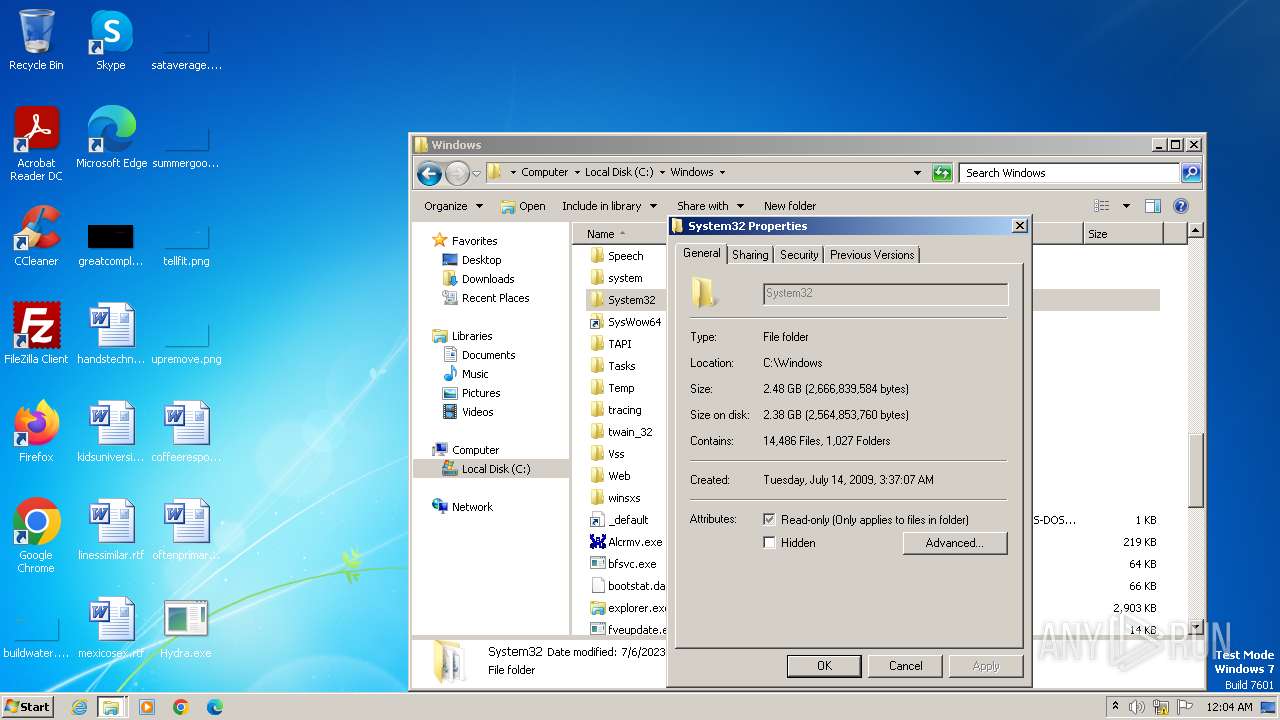
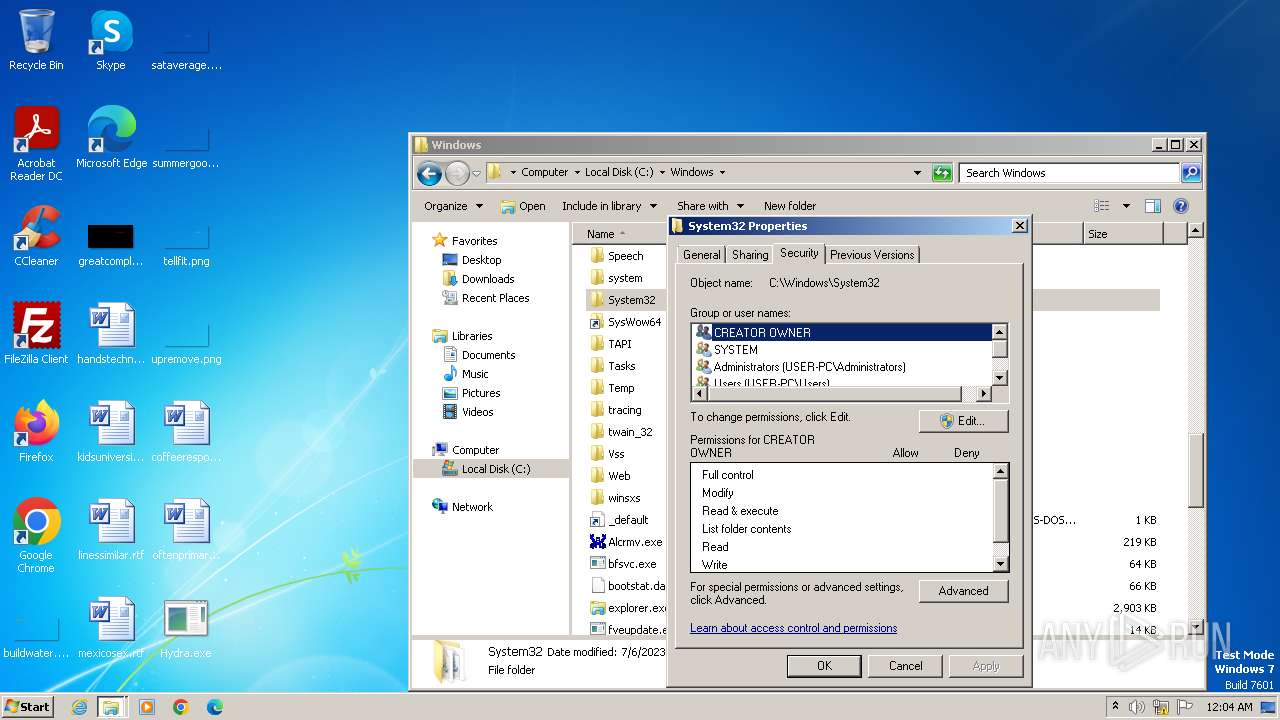
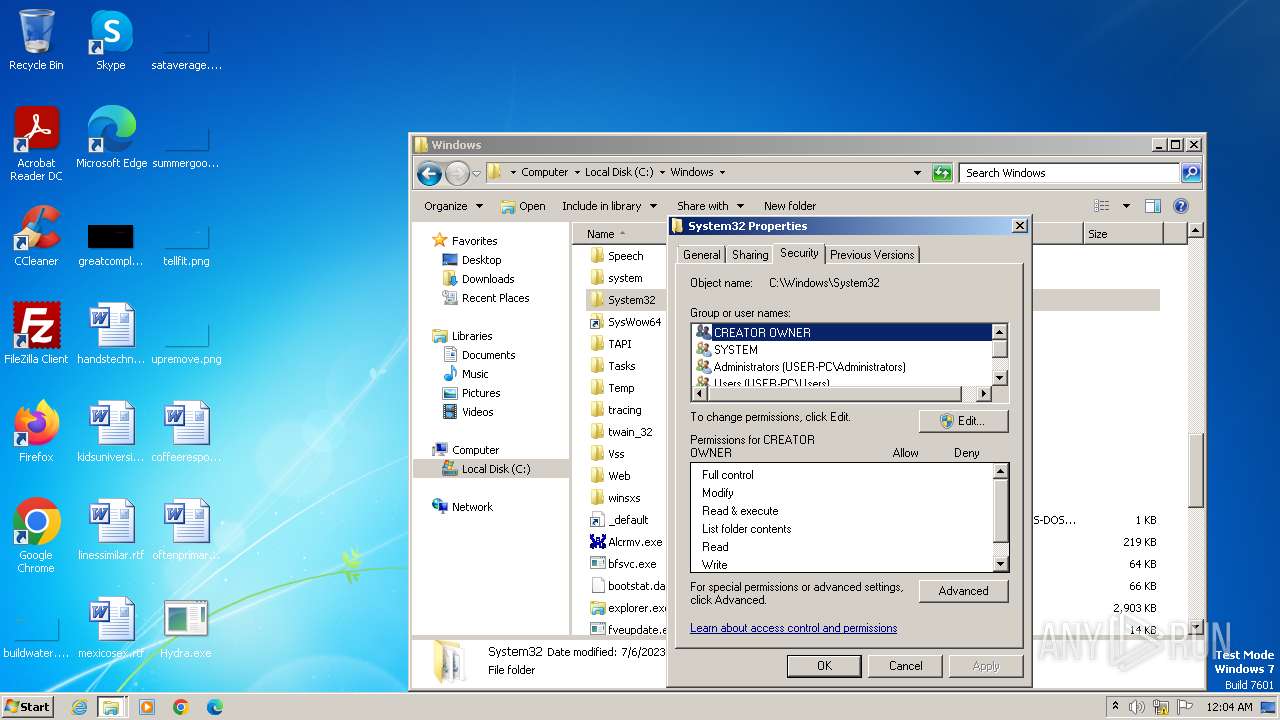
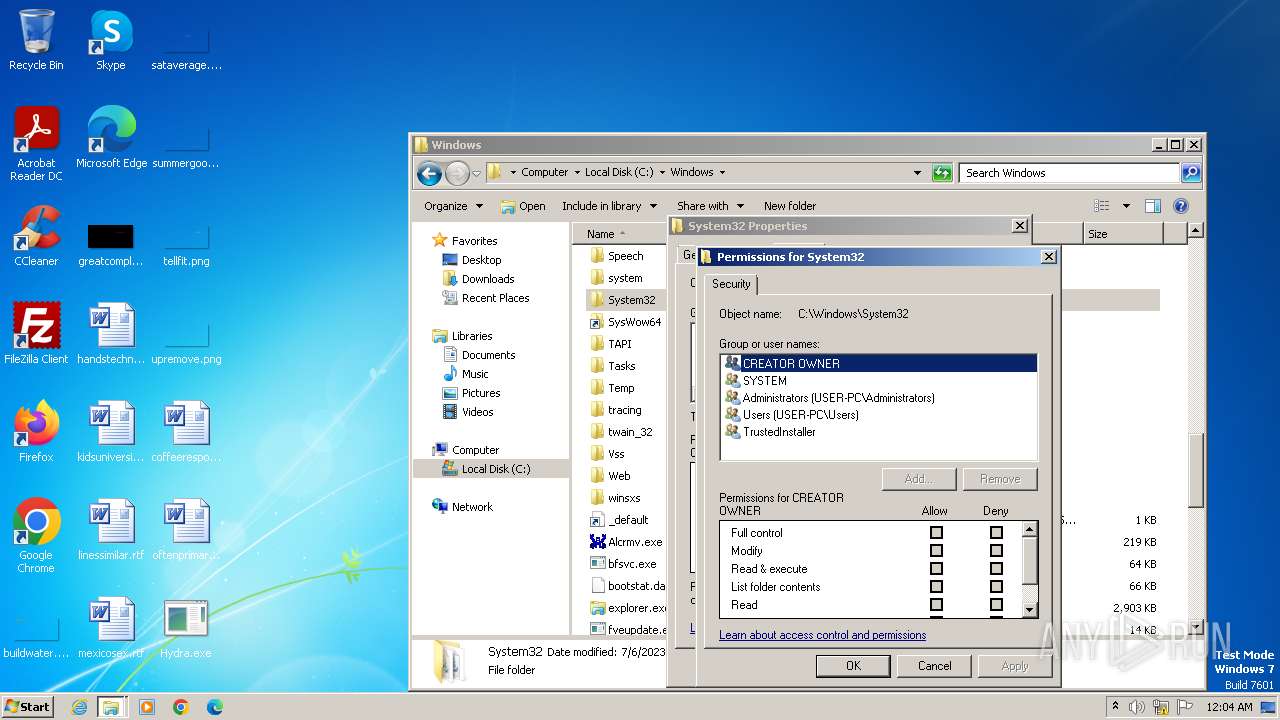
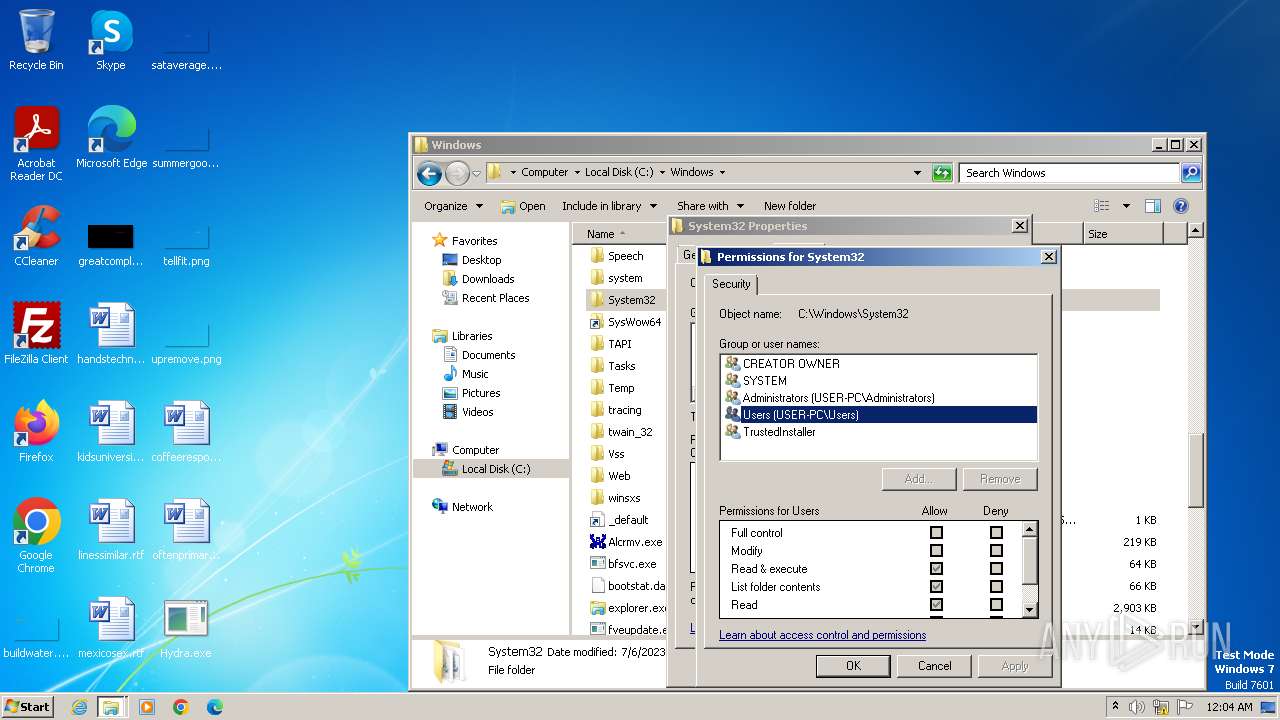
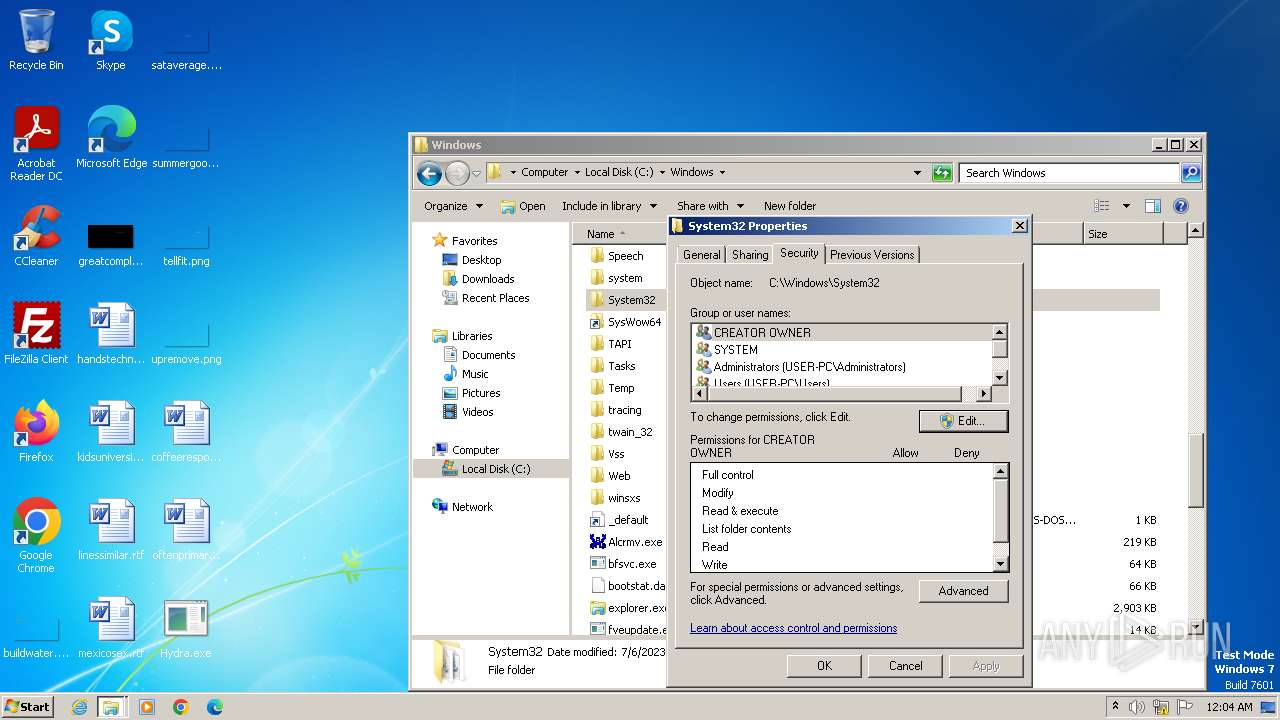
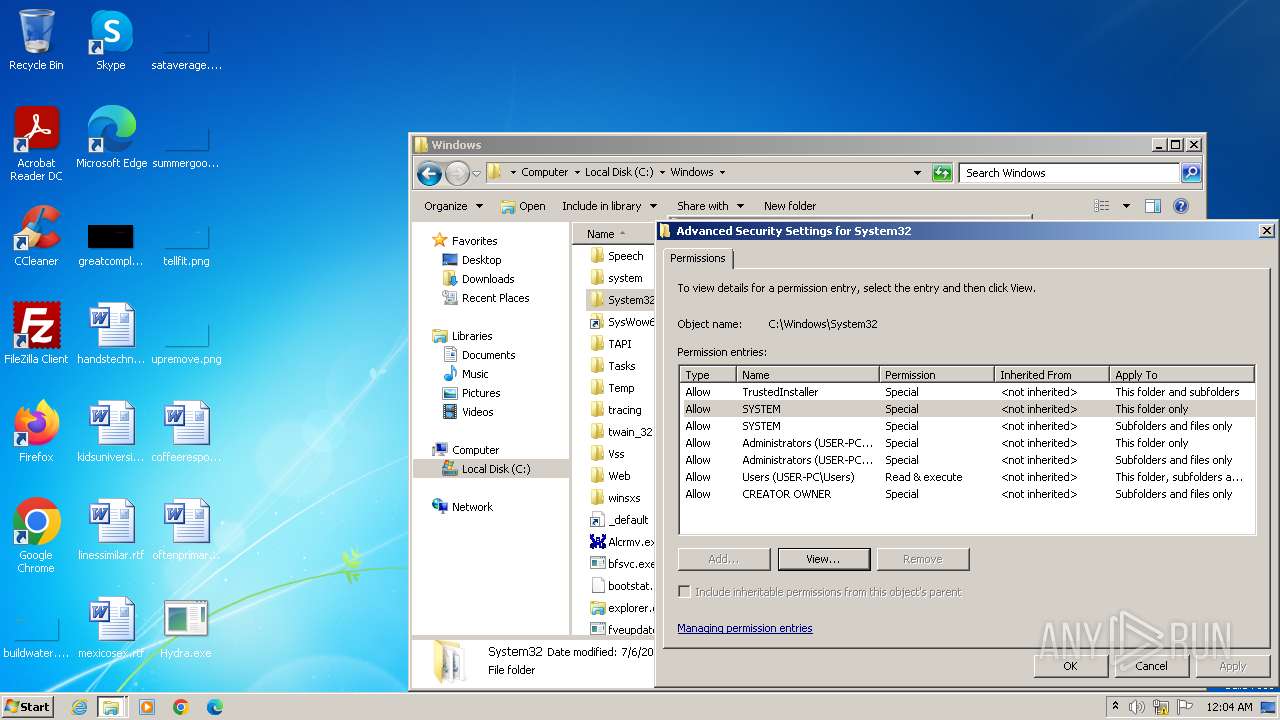
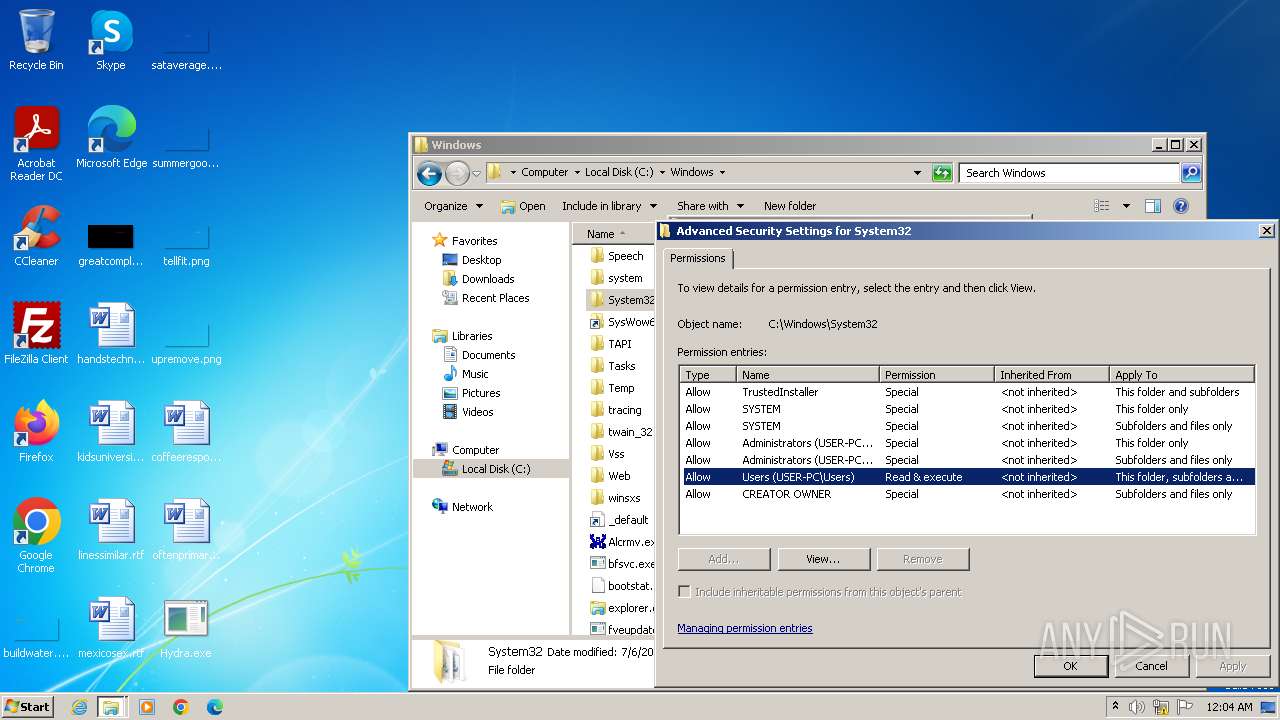
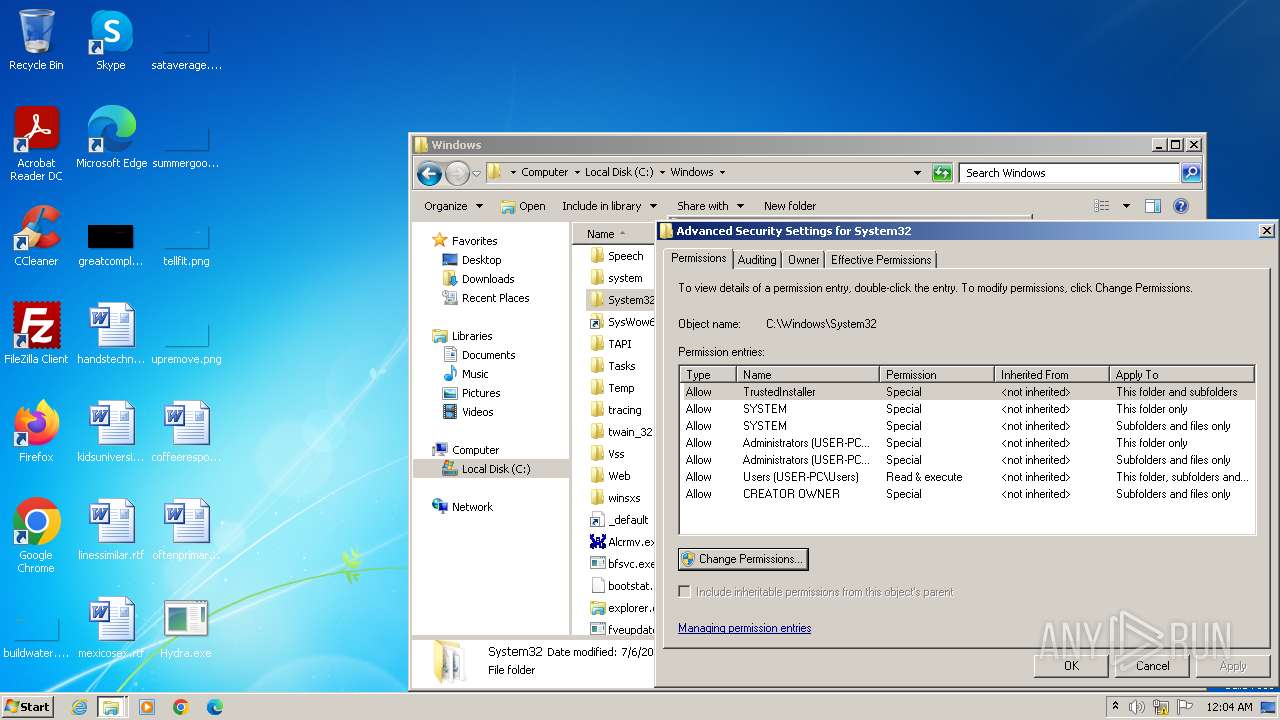
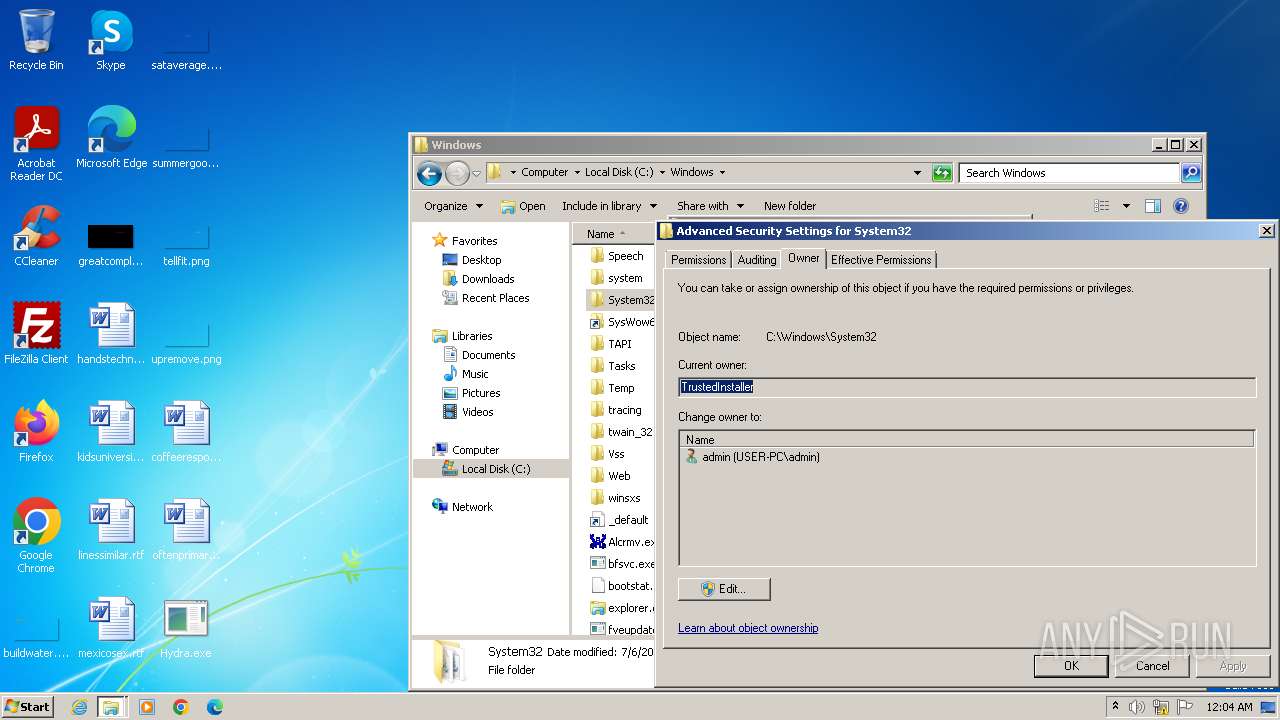
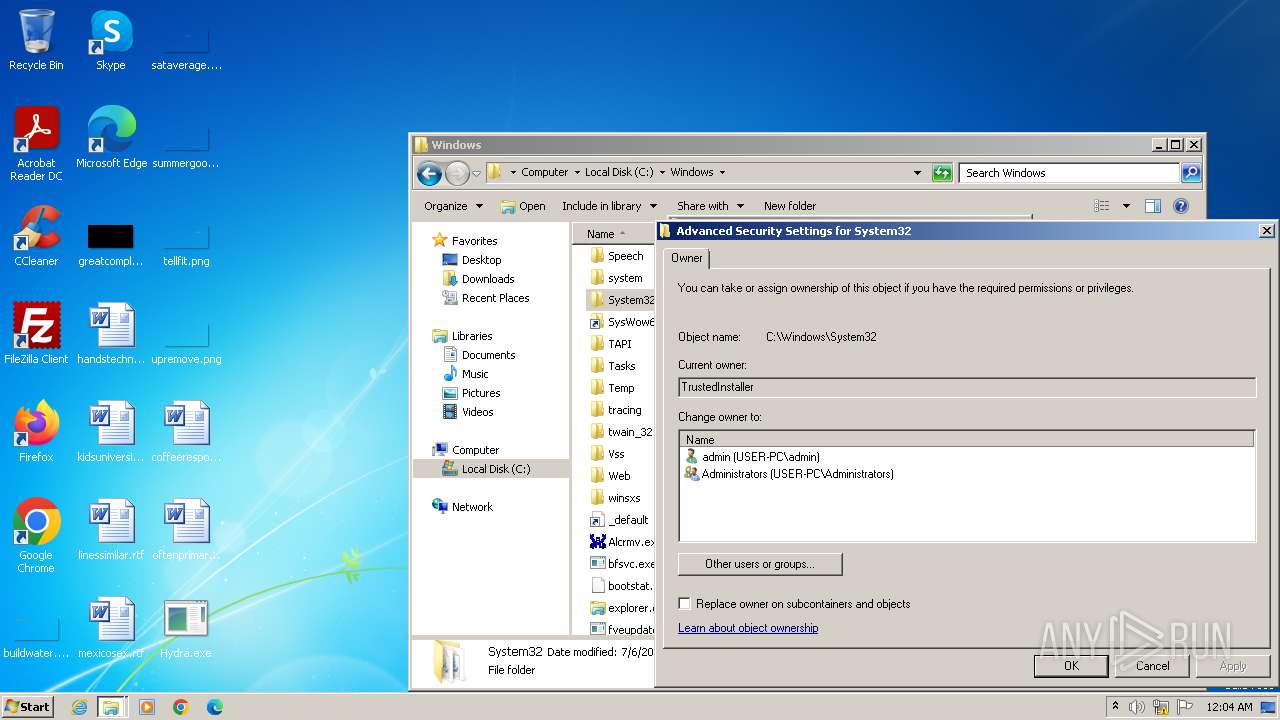
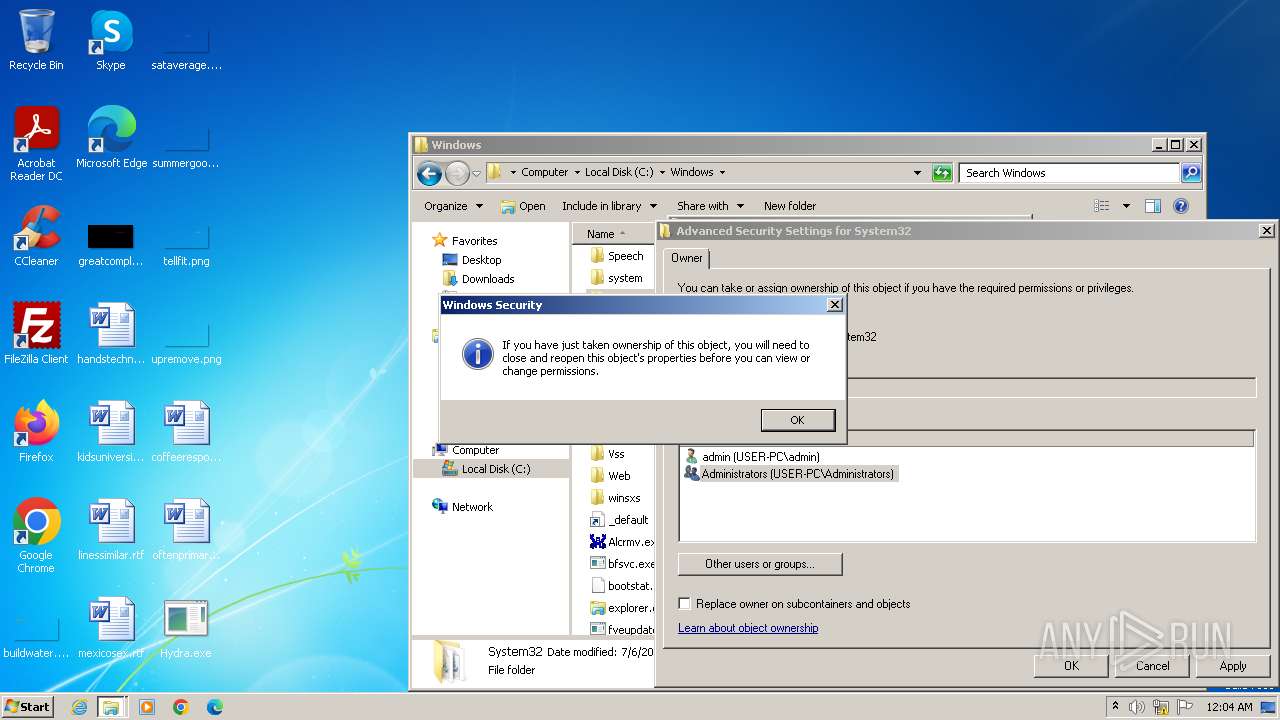
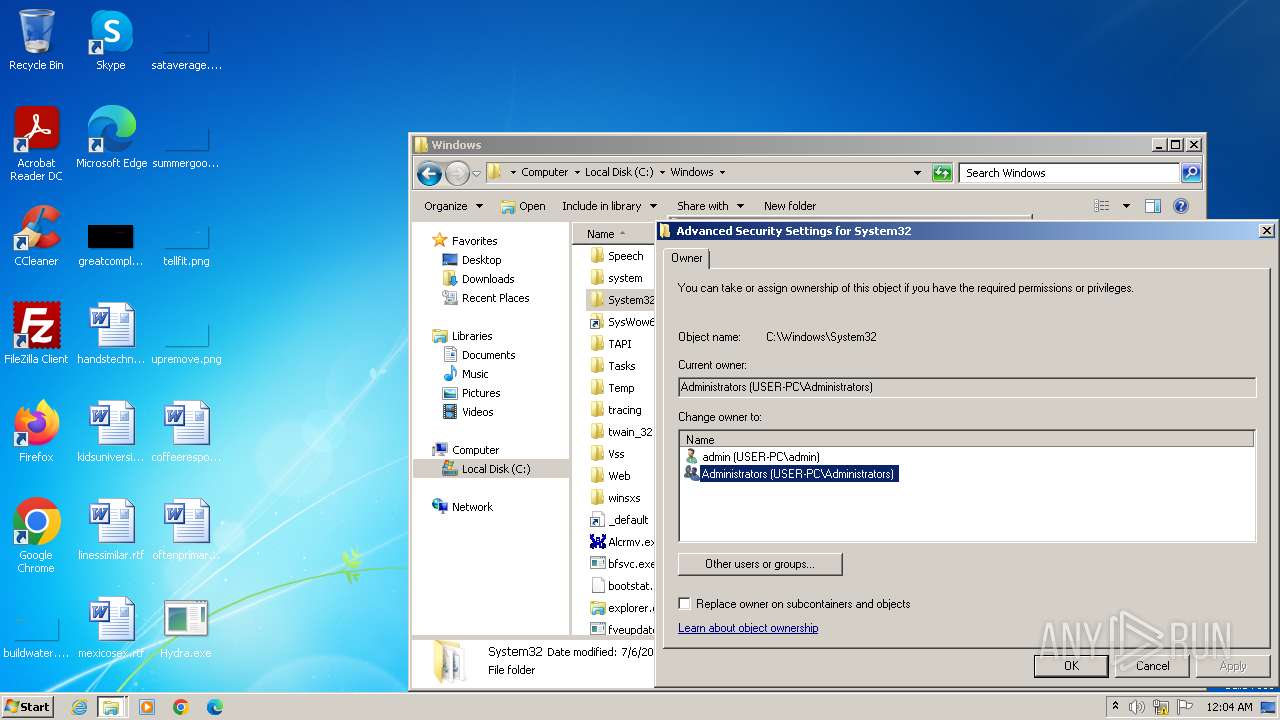
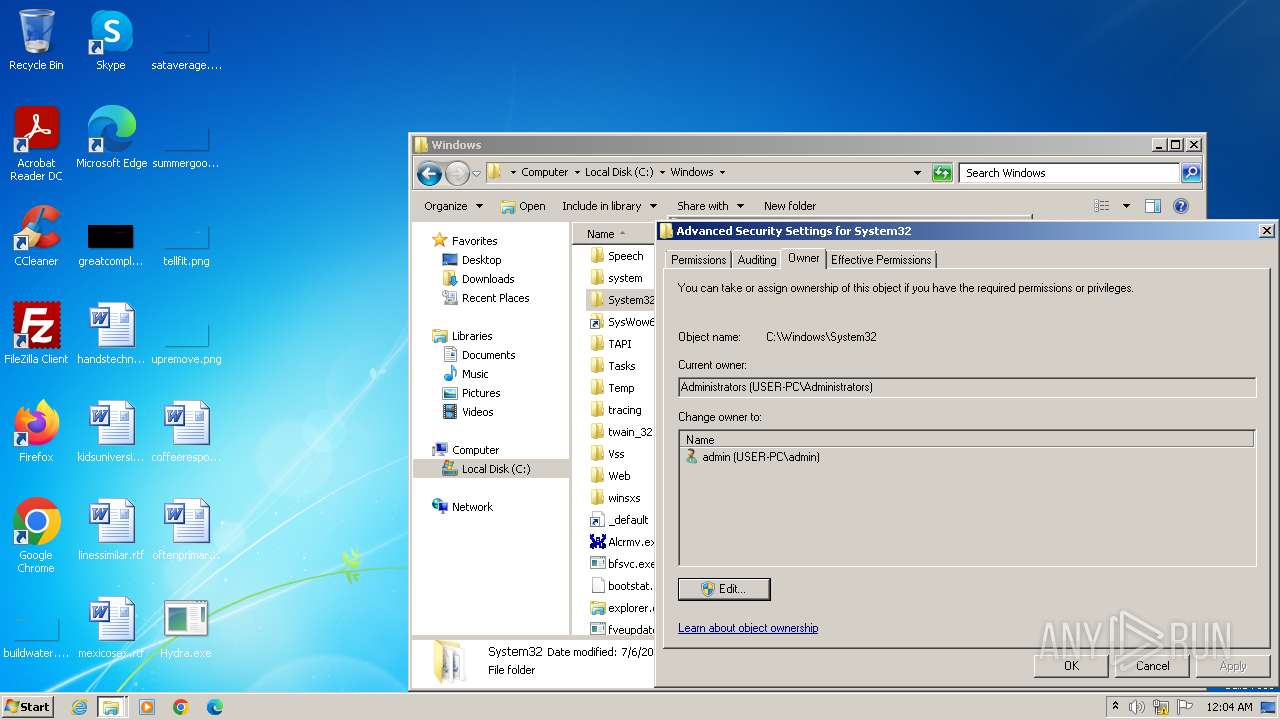
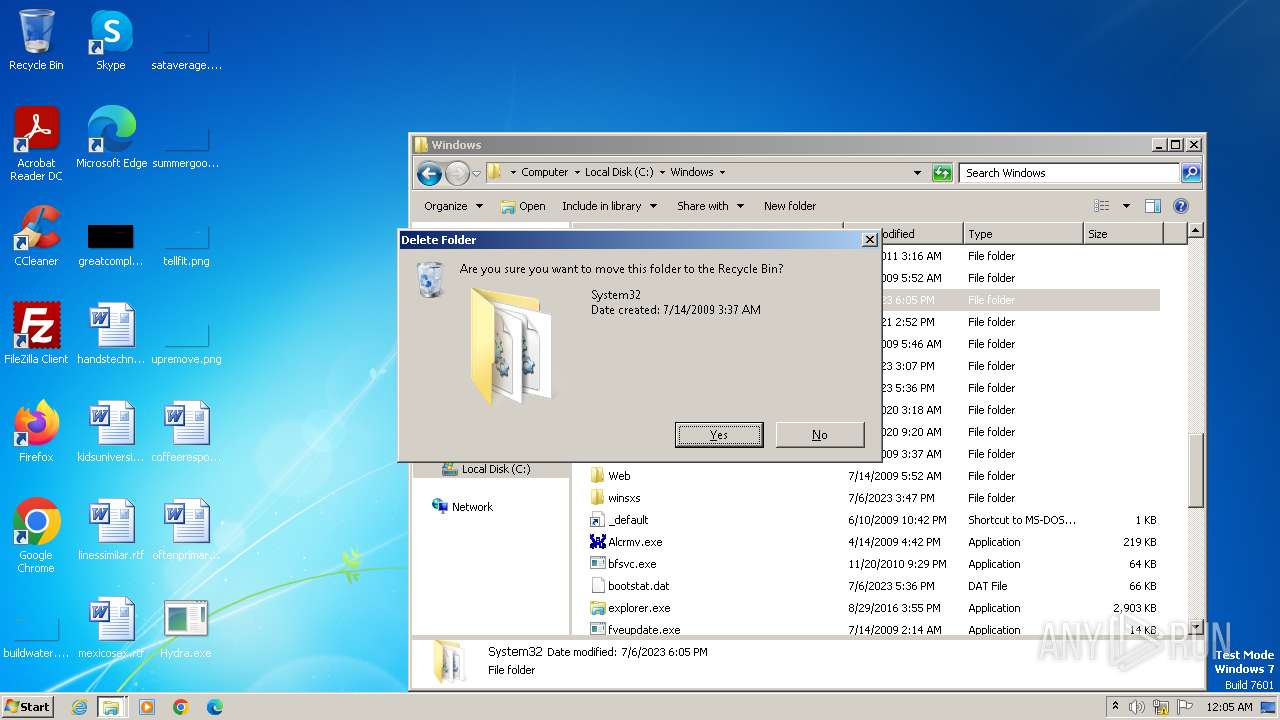
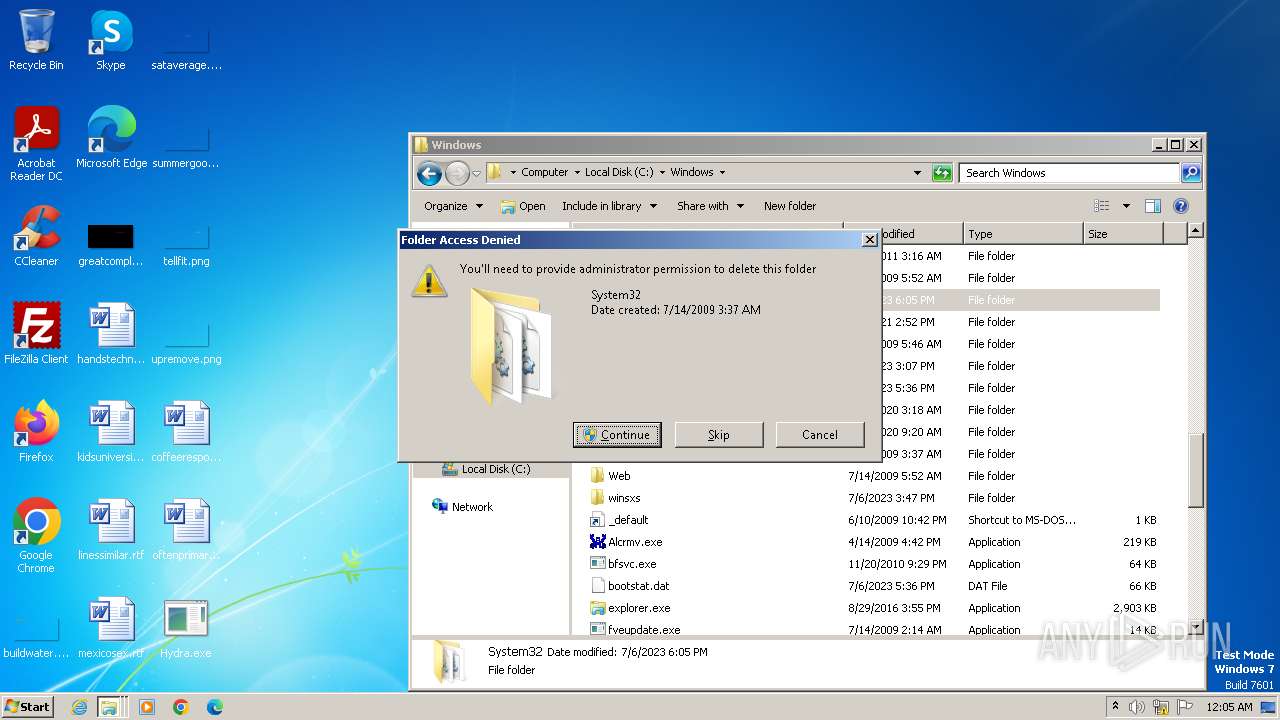
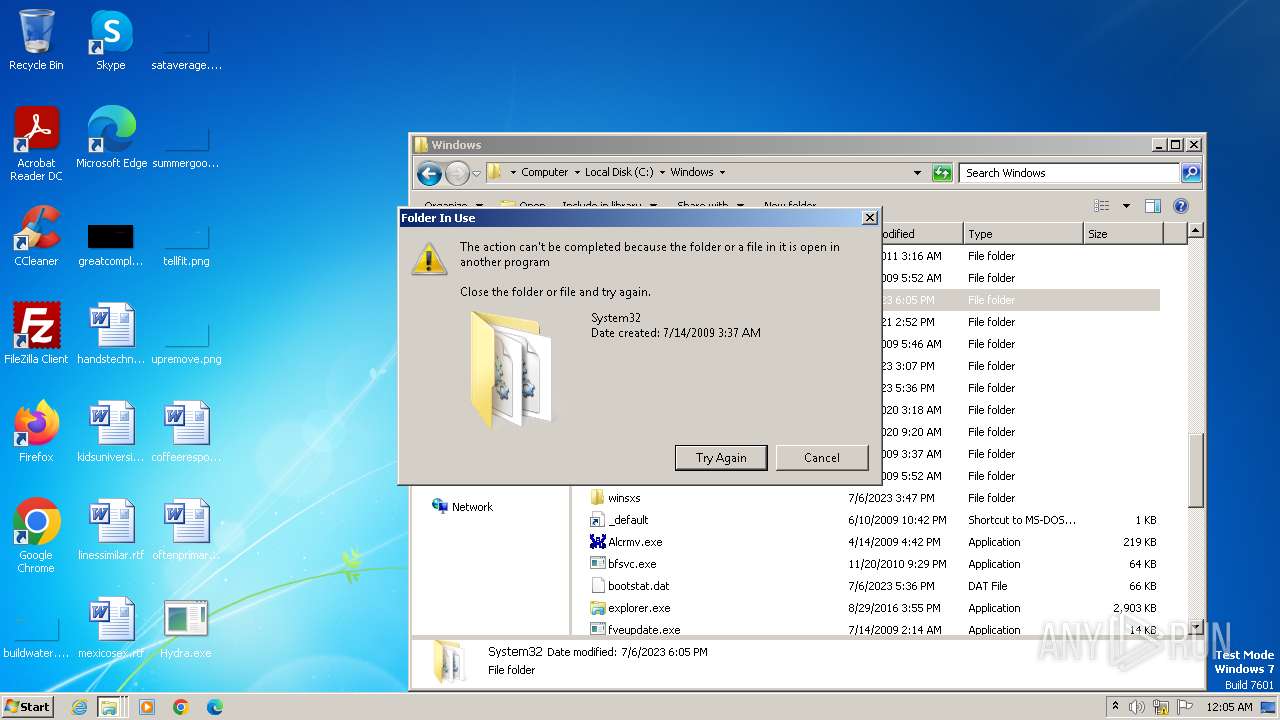
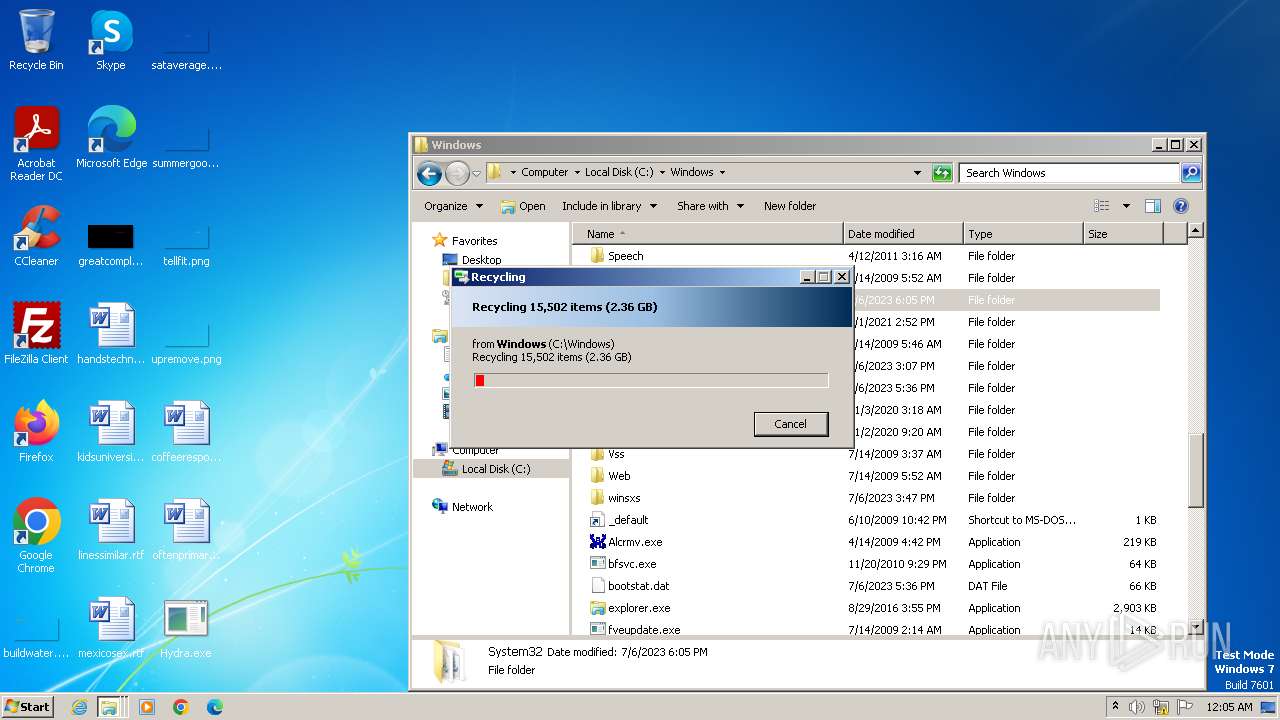
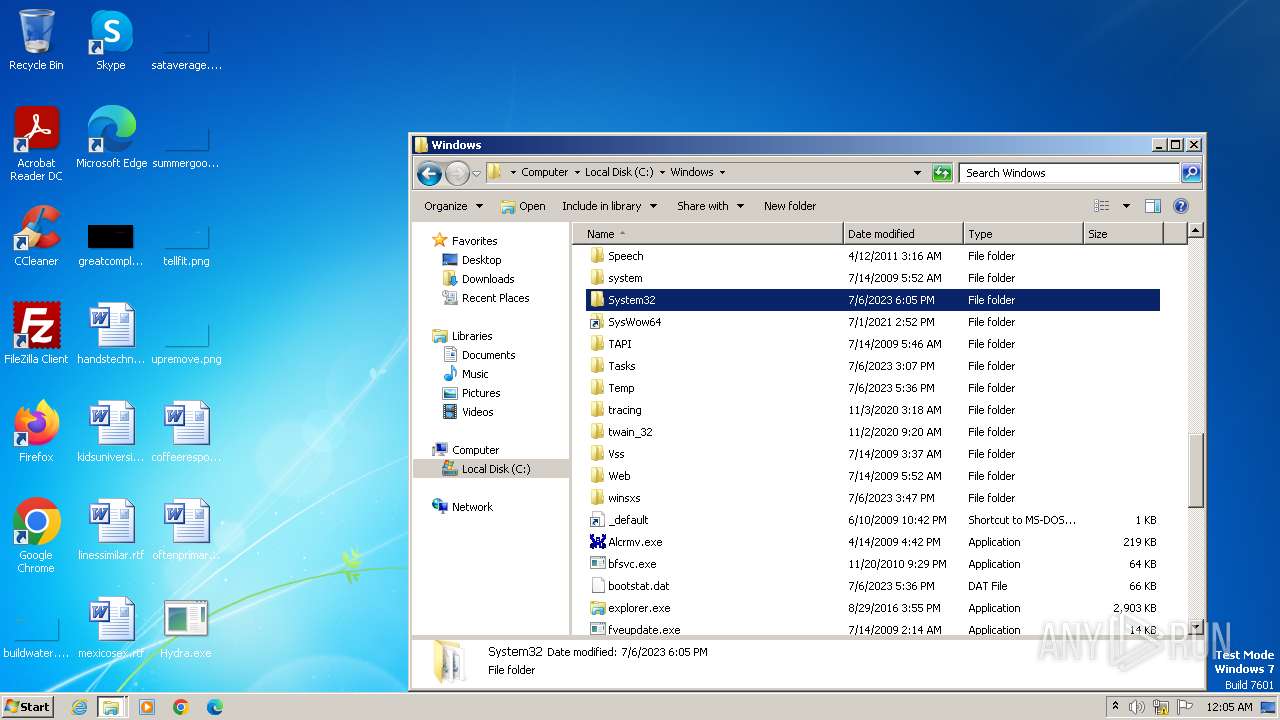
| download: | /giabao4498/Hydra-Virus/blob/master/Hydra.exe |
| Full analysis: | https://app.any.run/tasks/dfe2274c-05a1-4451-a886-213d534b68aa |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2023, 00:02:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/json |
| File info: | JSON data |
| MD5: | 89583A969C822039374090BF064D7846 |
| SHA1: | 04C98DF0DA1B6291CADB423F1BAC7C098D8F11C9 |
| SHA256: | C61DB13EA6E20137AF16052156D928C6BBE9DF08CDE55C58B94DD4B71458366F |
| SSDEEP: | 96:yMZFGvIIVk+qL7rb9p2y1e1vTeYn1hydEI0:lZFGvII6j9p2yO1Q90 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes via Task Scheduler
- sipnotify.exe (PID: 1452)
- ctfmon.exe (PID: 1496)
Reads the Internet Settings
- sipnotify.exe (PID: 1452)
Reads settings of System Certificates
- sipnotify.exe (PID: 1452)
INFO
Manual execution by a user
- explorer.exe (PID: 2424)
- IMEKLMG.EXE (PID: 1696)
- IMEKLMG.EXE (PID: 1940)
- wmpnscfg.exe (PID: 2308)
- wmpnscfg.exe (PID: 2380)
- SearchFilterHost.exe (PID: 2484)
Checks supported languages
- IMEKLMG.EXE (PID: 1940)
- IMEKLMG.EXE (PID: 1696)
- wmpnscfg.exe (PID: 2308)
- wmpnscfg.exe (PID: 2380)
Reads the computer name
- IMEKLMG.EXE (PID: 1940)
- IMEKLMG.EXE (PID: 1696)
- wmpnscfg.exe (PID: 2308)
- wmpnscfg.exe (PID: 2380)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 1940)
- IMEKLMG.EXE (PID: 1696)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1452)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2308)
- wmpnscfg.exe (PID: 2380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
JSON
| PayloadAllShortcutsEnabled: | - |
|---|---|
| PayloadBlobCsv: | null |
| PayloadBlobCsvError: | null |
| PayloadBlobDependabotInfoConfigFilePath: | null |
| PayloadBlobDependabotInfoConfigurationNoticeDismissed: | null |
| PayloadBlobDependabotInfoCurrentUserCanAdminRepo: | - |
| PayloadBlobDependabotInfoDismissConfigurationNoticePath: | /settings/dismiss-notice/dependabot_configuration_notice |
| PayloadBlobDependabotInfoNetworkDependabotPath: | /giabao4498/Hydra-Virus/network/updates |
| PayloadBlobDependabotInfoRepoAlertsPath: | /giabao4498/Hydra-Virus/security/dependabot |
| PayloadBlobDependabotInfoRepoOwnerIsOrg: | - |
| PayloadBlobDependabotInfoRepoSecurityAndAnalysisPath: | /giabao4498/Hydra-Virus/settings/security_analysis |
| PayloadBlobDependabotInfoShowConfigurationBanner: | - |
| PayloadBlobDiscussionTemplate: | null |
| PayloadBlobDisplayName: | Hydra.exe |
| PayloadBlobDisplayUrl: | https://github.com/giabao4498/Hydra-Virus/blob/master/Hydra.exe?raw=true |
| PayloadBlobHeaderInfoBlobSize: | 127 KB |
| PayloadBlobHeaderInfoDeleteInfoDeleteTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoEditInfoEditTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoGhDesktopPath: | https://desktop.github.com |
| PayloadBlobHeaderInfoGitLfsPath: | null |
| PayloadBlobHeaderInfoIsCSV: | - |
| PayloadBlobHeaderInfoIsRichtext: | - |
| PayloadBlobHeaderInfoLineInfoTruncatedLoc: | null |
| PayloadBlobHeaderInfoLineInfoTruncatedSloc: | null |
| PayloadBlobHeaderInfoMode: | file |
| PayloadBlobHeaderInfoOnBranch: | |
| PayloadBlobHeaderInfoShortPath: | 251898a |
| PayloadBlobHeaderInfoSiteNavLoginPath: | /login?return_to=https%3A%2F%2Fgithub.com%2Fgiabao4498%2FHydra-Virus%2Fblob%2Fmaster%2FHydra.exe |
| PayloadBlobHeaderInfoToc: | null |
| PayloadBlobImage: | - |
| PayloadBlobIsCodeownersFile: | null |
| PayloadBlobIsPlain: | - |
| PayloadBlobIsValidLegacyIssueTemplate: | - |
| PayloadBlobIssueTemplate: | null |
| PayloadBlobIssueTemplateHelpUrl: | https://docs.github.com/articles/about-issue-and-pull-request-templates |
| PayloadBlobLanguage: | null |
| PayloadBlobLanguageID: | null |
| PayloadBlobLarge: | - |
| PayloadBlobLoggedIn: | - |
| PayloadBlobNewDiscussionPath: | /giabao4498/Hydra-Virus/discussions/new |
| PayloadBlobNewIssuePath: | /giabao4498/Hydra-Virus/issues/new |
| PayloadBlobPlanSupportInfoRepoIsFork: | null |
| PayloadBlobPlanSupportInfoRepoOwnedByCurrentUser: | null |
| PayloadBlobPlanSupportInfoRequestFullPath: | /giabao4498/Hydra-Virus/blob/master/Hydra.exe |
| PayloadBlobPlanSupportInfoShowFreeOrgGatedFeatureMessage: | null |
| PayloadBlobPlanSupportInfoShowPlanSupportBanner: | null |
| PayloadBlobPlanSupportInfoUpgradeDataAttributes: | null |
| PayloadBlobPlanSupportInfoUpgradePath: | null |
| PayloadBlobPublishBannersInfoDismissActionNoticePath: | /settings/dismiss-notice/publish_action_from_dockerfile |
| PayloadBlobPublishBannersInfoDismissStackNoticePath: | /settings/dismiss-notice/publish_stack_from_file |
| PayloadBlobPublishBannersInfoReleasePath: | /giabao4498/Hydra-Virus/releases/new?marketplace=true |
| PayloadBlobPublishBannersInfoShowPublishActionBanner: | - |
| PayloadBlobPublishBannersInfoShowPublishStackBanner: | - |
| PayloadBlobRawBlobUrl: | https://github.com/giabao4498/Hydra-Virus/raw/master/Hydra.exe |
| PayloadBlobRawLines: | null |
| PayloadBlobRenderImageOrRaw: | |
| PayloadBlobRenderedFileInfo: | null |
| PayloadBlobRichText: | null |
| PayloadBlobShortPath: | null |
| PayloadBlobStylingDirectives: | null |
| PayloadBlobSymbols: | null |
| PayloadBlobTabSize: | 8 |
| PayloadBlobTopBannersInfoActionsOnboardingTip: | null |
| PayloadBlobTopBannersInfoCitationHelpUrl: | https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/creating-a-repository-on-github/about-citation-files |
| PayloadBlobTopBannersInfoGlobalPreferredFundingPath: | null |
| PayloadBlobTopBannersInfoOverridingGlobalFundingFile: | - |
| PayloadBlobTopBannersInfoRepoName: | Hydra-Virus |
| PayloadBlobTopBannersInfoRepoOwner: | giabao4498 |
| PayloadBlobTopBannersInfoShowDependabotConfigurationBanner: | - |
| PayloadBlobTopBannersInfoShowInvalidCitationWarning: | - |
| PayloadBlobTruncated: | - |
| PayloadBlobViewable: | - |
| PayloadBlobWorkflowRedirectUrl: | null |
| PayloadCopilotAccessAllowed: | - |
| PayloadCopilotInfo: | null |
| PayloadCsrf_tokensgiabao4498Hydra-VirusbranchesPost: | F1iorKtejSdW6RWQAKsa0PvyqvGKCcAQpqyGTfEGiyEJMsDMo5cgi6o3XdrPT9bRGBBJF-cYozOQCi3e7_paUg |
| PayloadCsrf_tokensrepospreferencesPost: | DG8mCubT8ugtnbjF8ryT6iBP3-sHXfjOcQw6XNo8GFAUJh5vNP7wrtTS057rNG8xXwM9lL5I4oX3OCnhiDAWDQ |
| PayloadCurrentUser: | null |
| PayloadFileTreeItemsContentType: |
|
| PayloadFileTreeItemsName: |
|
| PayloadFileTreeItemsPath: |
|
| PayloadFileTreeTotalCount: | 13 |
| PayloadFileTreeProcessingTime: | 2.4316440000000004 |
| PayloadPath: | Hydra.exe |
| PayloadReducedMotionEnabled: | null |
| PayloadRefInfoCanEdit: | - |
| PayloadRefInfoCurrentOid: | 7698248514f3c49dd99e03386755186d484ee215 |
| PayloadRefInfoListCacheKey: | v0:1568639498.0 |
| PayloadRefInfoName: | master |
| PayloadRefInfoRefType: | branch |
| PayloadRepoCreatedAt: | 2019-09-16T13:11:36.000Z |
| PayloadRepoCurrentUserCanPush: | - |
| PayloadRepoDefaultBranch: | master |
| PayloadRepoId: | 208803131 |
| PayloadRepoIsEmpty: | - |
| PayloadRepoIsFork: | - |
| PayloadRepoIsOrgOwned: | - |
| PayloadRepoName: | Hydra-Virus |
| PayloadRepoOwnerAvatar: | https://avatars.githubusercontent.com/u/26693113?v=4 |
| PayloadRepoOwnerLogin: | giabao4498 |
| PayloadRepoPrivate: | - |
| PayloadRepoPublic: | |
| PayloadSymbolsExpanded: | - |
| PayloadTreeExpanded: | |
| Title: | Hydra-Virus/Hydra.exe at master · giabao4498/Hydra-Virus |
Total processes
112
Monitored processes
16
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1496 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1940 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2164 | C:\Windows\system32\DllHost.exe /Processid:{1F2E5C40-9550-11CE-99D2-00AA006E086C} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2424 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10001_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10001 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
4 051
Read events
4 020
Write events
14
Delete events
17
Modification events
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: C85E140DA1B5BFA785A61C0ECDB0EC43DC6AAAB1430FDB8DDB7BC144A83D3739 | |||
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Windows\System32 | |||
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 24650DFFAAAFD2DCE855F5E30B0BE50CCF079EC8FF43C7DC6971DCCE53E4308E | |||
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 000C000019B8E0EF8E2CDA01 | |||
| (PID) Process: | (3072) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1940) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEJP\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (1696) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEKR\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (1452) sipnotify.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2380) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{B8ECC31C-9278-4C55-A213-F19A3B41AC3E}\{3C0E7A6F-02FA-470C-944A-B80812D5444E} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2464 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFD40.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:E8A970BA6CE386EED9A5E724F26212A6 | SHA256:7E06107D585D8FC7870998F3856DCC3E35800AA97E4406AAB83BC8444B6CBDE3 | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 2464 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFD51.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 1452 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\en-us.html | html | |
MD5:9752942B57692148B9F614CF4C119A36 | SHA256:E31B834DD53FA6815F396FC09C726636ABF98F3367F0CF1590EF5EB3801C75D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | sipnotify.exe | HEAD | 200 | 23.210.119.212:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133468131677340000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1116 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1452 | sipnotify.exe | 23.210.119.212:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
2540 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |