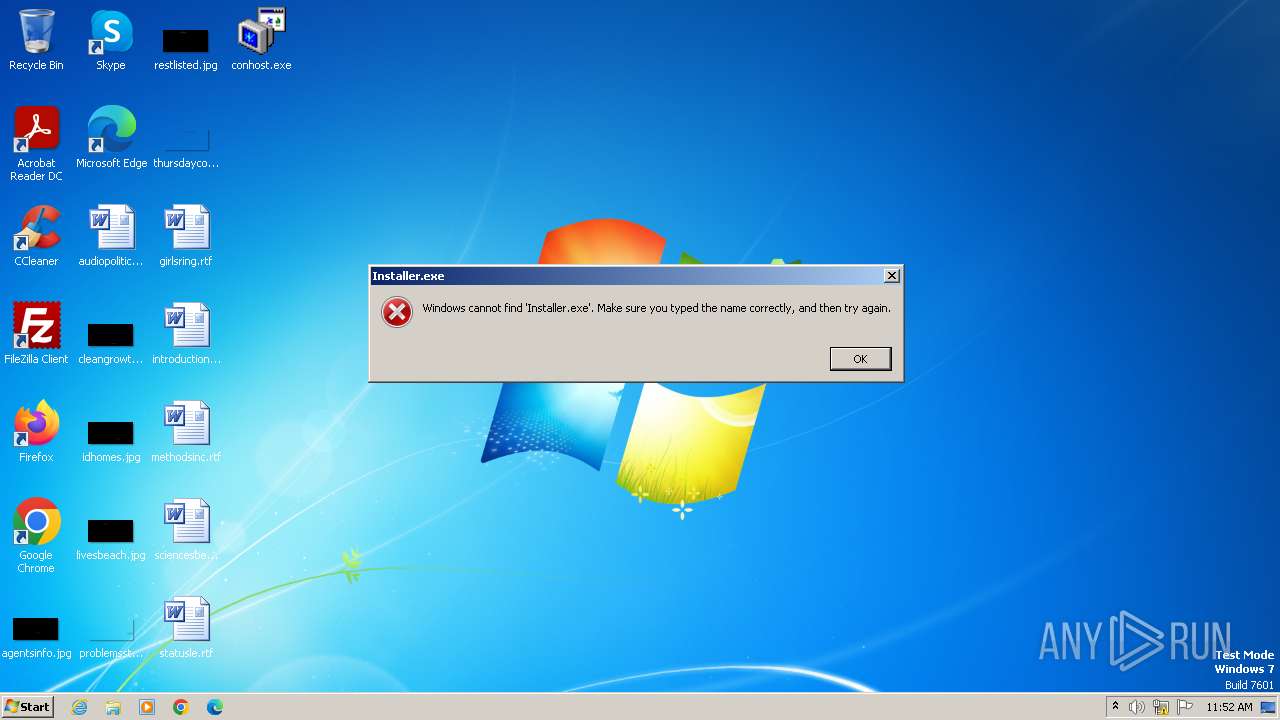
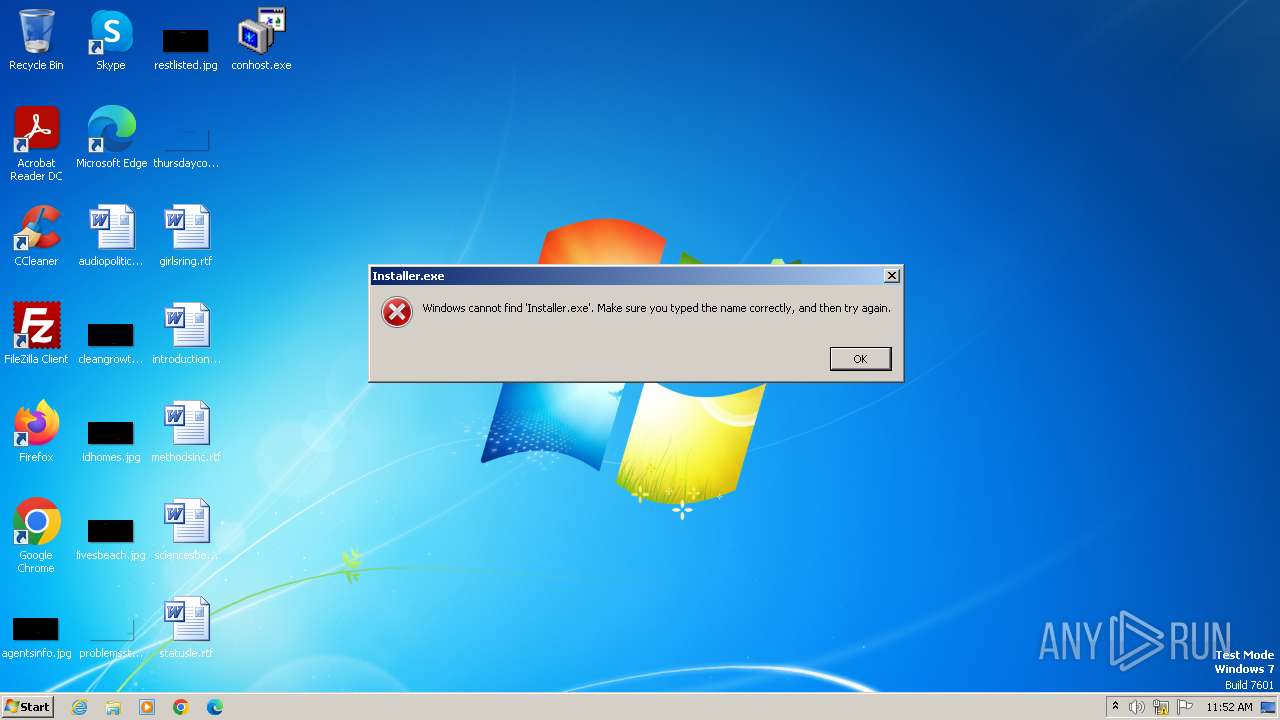
| download: | /conhost.exe |
| Full analysis: | https://app.any.run/tasks/a65500f7-acbf-4c7a-b971-b7f275593bf8 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2023, 11:52:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 202BAC6533237A8985A1B9DF5DAC9E59 |
| SHA1: | 05EFDA4FEF1A771DCC06BB6EE21A71D3082C54E1 |
| SHA256: | C6176FA396F754207C5CAF2C6ED26B55312B17720E889055CDE7D90AE84CF40D |
| SSDEEP: | 98304:+bCQfsZarRX45nbxrUkGBtn+QALa1nXITT4cK+L7WjUPmjiLZteG2/oERYBD3x1C:A24IBZkn |
MALICIOUS
Drops the executable file immediately after the start
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3680)
- cmd.exe (PID: 3308)
Reads the Internet Settings
- cmd.exe (PID: 3680)
- cmd.exe (PID: 3308)
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
Executing commands from a ".bat" file
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
INFO
Reads the computer name
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
Checks supported languages
- conhost.exe (PID: 3384)
- mode.com (PID: 3140)
- mode.com (PID: 3888)
- conhost.exe (PID: 3556)
Manual execution by a user
- explorer.exe (PID: 3940)
- conhost.exe (PID: 3556)
Create files in a temporary directory
- conhost.exe (PID: 3384)
- conhost.exe (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:05:28 11:05:18+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 102400 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1945f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.11.0.0 |
| ProductVersionNumber: | 6.11.0.7 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Alexander Roshalov |
| LegalCopyright: | Copyright © Alexander Roshalov 1993-2022 |
| LegalTrademarks: | i6i7ju56ytgrft423t |
| ProductName: | WinRAR |
| PrivateBuild: | i67juyhtgerft34t34 |
| Comments: | k786jutyhrtgj756h4tgrku6jyhrtgerjyhrtgerfwc |
| FileVersion: | 6.11.0.0 |
| SpecialBuild: | k68ju7yh5rtgsdgfsdgderfwe |
| OriginalFileName: | Uninstall.exe |
| FileDescription: | Uninstall WinRAR |
| InternalName: | Uninstall WinRAR |
| ProductVersion: | 6.11.0.7 |
| Created: | 7z SFX Constructor v4.6.0.0 (http://usbtor.ru/viewtopic.php?t=798) |
| Builder: | ahileeeeeess 15:22:00 07/11/2023 |
Total processes
49
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | mode 65,10 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\main\main.bat" /S" | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3384 | "C:\Users\admin\Desktop\conhost.exe" | C:\Users\admin\Desktop\conhost.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshalov Integrity Level: MEDIUM Description: Uninstall WinRAR Exit code: 0 Version: 6.11.0.0 Modules
| |||||||||||||||
| 3540 | attrib +H "Installer.exe" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\Desktop\conhost.exe" | C:\Users\admin\Desktop\conhost.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshalov Integrity Level: HIGH Description: Uninstall WinRAR Exit code: 0 Version: 6.11.0.0 Modules
| |||||||||||||||
| 3680 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\main\main.bat" /S" | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3880 | attrib +H "Installer.exe" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3888 | mode 65,10 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3940 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 706
Read events
1 690
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3384) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3384) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3384) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3384) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3556) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3556) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3556) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3556) conhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
6
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\main.bat | text | |
MD5:5FCFDBCA8322E4696CEBA685A02B20E3 | SHA256:6B49585D8657733B19EC3E1FD8BE6CA90814ACD3FBC83C114B3F8566617EBCC6 | |||
| 3384 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\7z.dll | executable | |
MD5:72491C7B87A7C2DD350B727444F13BB4 | SHA256:34AD9BB80FE8BF28171E671228EB5B64A55CAA388C31CB8C0DF77C0136735891 | |||
| 3384 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\KillDuplicate.cmd | text | |
MD5:68CECDF24AA2FD011ECE466F00EF8450 | SHA256:64929489DC8A0D66EA95113D4E676368EDB576EA85D23564D53346B21C202770 | |||
| 3384 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\7z.exe | executable | |
MD5:619F7135621B50FD1900FF24AADE1524 | SHA256:344F076BB1211CB02ECA9E5ED2C0CE59BCF74CCBC749EC611538FA14ECB9AAD2 | |||
| 3384 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\file.bin | compressed | |
MD5:D6F940342C7B677A42C605BD1C2B22E4 | SHA256:FE4D8482247B7C337DDDF2B7B651A102AED2D3666B5ADAA4BD710C2E84A0E0F6 | |||
| 3308 | cmd.exe | C:\Users\admin\AppData\Local\Temp\main\file.bin | compressed | |
MD5:D6F940342C7B677A42C605BD1C2B22E4 | SHA256:FE4D8482247B7C337DDDF2B7B651A102AED2D3666B5ADAA4BD710C2E84A0E0F6 | |||
| 3556 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\main.bat | text | |
MD5:5FCFDBCA8322E4696CEBA685A02B20E3 | SHA256:6B49585D8657733B19EC3E1FD8BE6CA90814ACD3FBC83C114B3F8566617EBCC6 | |||
| 3556 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\file.bin | compressed | |
MD5:D6F940342C7B677A42C605BD1C2B22E4 | SHA256:FE4D8482247B7C337DDDF2B7B651A102AED2D3666B5ADAA4BD710C2E84A0E0F6 | |||
| 3308 | cmd.exe | C:\Users\admin\AppData\Local\Temp\main\file.zip | compressed | |
MD5:D6F940342C7B677A42C605BD1C2B22E4 | SHA256:FE4D8482247B7C337DDDF2B7B651A102AED2D3666B5ADAA4BD710C2E84A0E0F6 | |||
| 3556 | conhost.exe | C:\Users\admin\AppData\Local\Temp\main\KillDuplicate.cmd | text | |
MD5:68CECDF24AA2FD011ECE466F00EF8450 | SHA256:64929489DC8A0D66EA95113D4E676368EDB576EA85D23564D53346B21C202770 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |