| File name: | WRL GAMEPAD FOR PS3-PC.exe |
| Full analysis: | https://app.any.run/tasks/039c8d2a-946c-4881-91c2-e6d8b14e05aa |
| Verdict: | Malicious activity |
| Analysis date: | August 15, 2020, 16:27:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B276F72ADF2FEF8DD76C8D1F1C51C40A |
| SHA1: | 229CC1442DD3AEC5C7C437DC0841B64AAA1AEAE6 |
| SHA256: | C6097DA5317EFD8393CE40ACFADFF58561B80F35179C8F0DE6C2834D83862561 |
| SSDEEP: | 49152:johTR5c9CsOZSGz9mdTiLPaAU8Tnma2ohTR5c9CsO0t:8THc9l61z9mdyajmn93THc9lD |
MALICIOUS
Loads dropped or rewritten executable
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
SUSPICIOUS
Executable content was dropped or overwritten
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
Executed via COM
- DllHost.exe (PID: 2616)
Creates a software uninstall entry
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
Searches for installed software
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
Creates files in the user directory
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
Creates files in the program directory
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
Creates COM task schedule object
- WRL GAMEPAD FOR PS3-PC.exe (PID: 1776)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ax | | | DirectShow filter (40.7) |
|---|---|---|
| .exe | | | InstallShield setup (8.6) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (6.3) |
| .exe | | | Win64 Executable (generic) (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:05:24 18:57:31+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 282624 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x22a29 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.0.0.49974 |
| ProductVersionNumber: | 12.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Macrovision Corporation |
| FileDescription: | Setup.exe |
| FileVersion: | 12.0.49974 |
| InternalName: | Setup |
| OriginalFileName: | Setup.exe |
| LegalCopyright: | Copyright (C) 2006 Macrovision Corporation |
| ProductName: | InstallShield |
| ProductVersion: | 12 |
| OLESelfRegister: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-May-2006 16:57:31 |
| Detected languages: |
|
| CompanyName: | Macrovision Corporation |
| FileDescription: | Setup.exe |
| FileVersion: | 12.0.49974 |
| InternalName: | Setup |
| OriginalFilename: | Setup.exe |
| LegalCopyright: | Copyright (C) 2006 Macrovision Corporation |
| ProductName: | InstallShield |
| ProductVersion: | 12.0 |
| OLESelfRegister: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 24-May-2006 16:57:31 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00044952 | 0x00045000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.56528 |
.rdata | 0x00046000 | 0x00005A80 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.36508 |
.data | 0x0004C000 | 0x0000742C | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.4136 |
.rsrc | 0x00054000 | 0x0001B410 | 0x0001C000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.39315 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.02975 | 897 | UNKNOWN | Turkish - Turkey | RT_MANIFEST |
2 | 6.39652 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.4963 | 764 | UNKNOWN | Serbian - Serbia (Cyrillic) | RT_STRING |
4 | 3.5139 | 1728 | UNKNOWN | Serbian - Serbia (Cyrillic) | RT_STRING |
100 | 2.64576 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
108 | 2.34615 | 66 | UNKNOWN | UNKNOWN | RT_DIALOG |
113 | 2.86715 | 486 | UNKNOWN | UNKNOWN | RT_DIALOG |
116 | 6.40312 | 148 | UNKNOWN | English - United States | PUBLICKEY |
118 | 2.75963 | 610 | UNKNOWN | UNKNOWN | RT_DIALOG |
119 | 2.90117 | 222 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
LZ32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
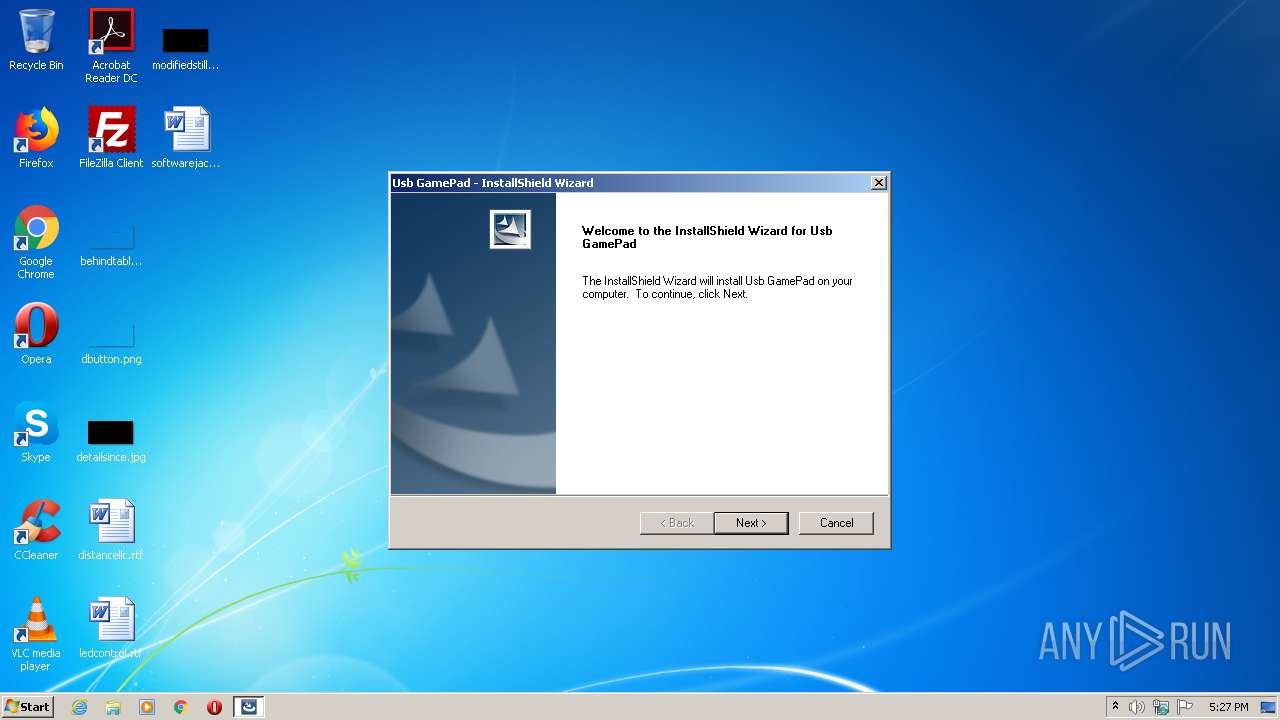
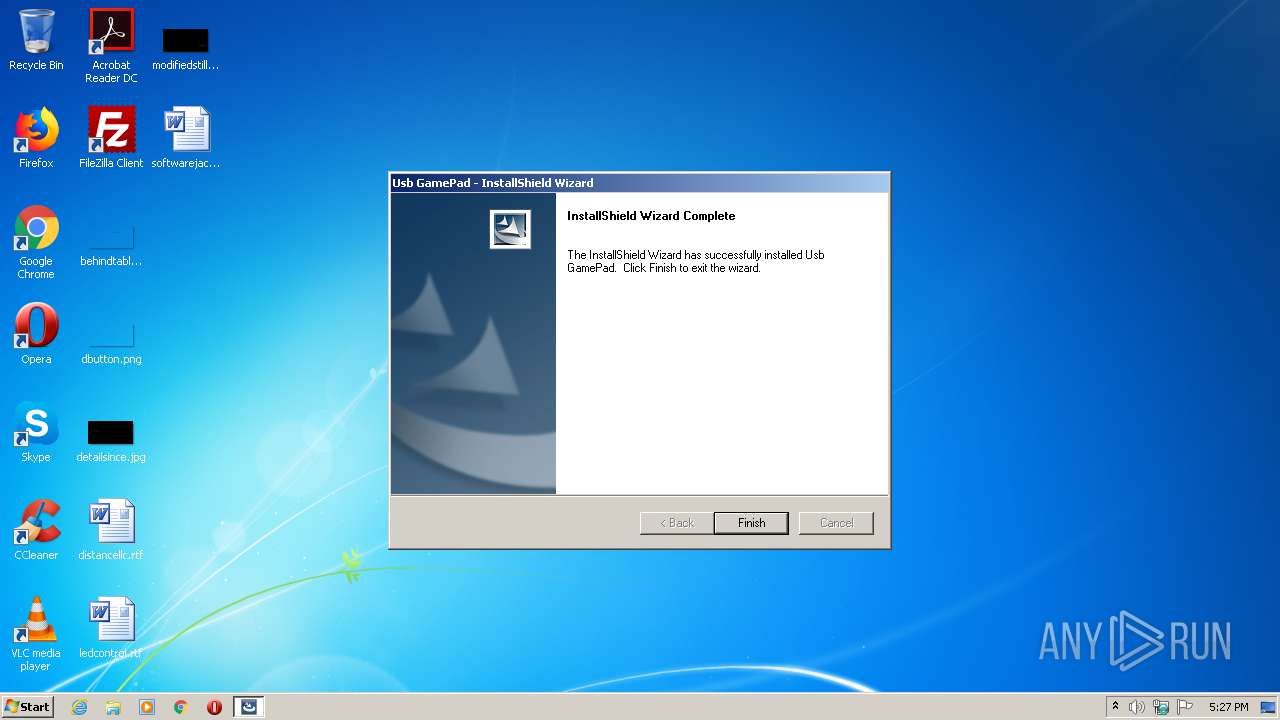
| 1776 | "C:\Users\admin\AppData\Local\Temp\WRL GAMEPAD FOR PS3-PC.exe" | C:\Users\admin\AppData\Local\Temp\WRL GAMEPAD FOR PS3-PC.exe | explorer.exe | ||||||||||||
User: admin Company: Macrovision Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 12.0.49974 Modules
| |||||||||||||||
| 2616 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2680 | "C:\Users\admin\AppData\Local\Temp\WRL GAMEPAD FOR PS3-PC.exe" | C:\Users\admin\AppData\Local\Temp\WRL GAMEPAD FOR PS3-PC.exe | — | explorer.exe | |||||||||||
User: admin Company: Macrovision Corporation Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 12.0.49974 Modules
| |||||||||||||||
Total events
351
Read events
141
Write events
210
Delete events
0
Modification events
| (PID) Process: | (2616) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000DCBC80012173D601380A0000B40B0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2616) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 42 | |||
| (PID) Process: | (2616) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000908185012173D601380A0000B40B0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2616) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000EAE387012173D601380A0000CC0E0000E8030000010000000000000000000000569884862D84154E9BBD21BB83F4680F0000000000000000 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000E23458012173D601F0060000B0060000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000E23458012173D601F0060000B0060000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 41 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 400000000000000096F95C012173D601F0060000B0060000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000F05B5F012173D601F00600003C0E0000E8030000010000000000000000000000B211D14650ECD24587E55C4D490D5C9A0000000000000000 | |||
| (PID) Process: | (1776) WRL GAMEPAD FOR PS3-PC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000001AD174012173D601F00600003C0E0000E8030000000000000000000000000000B211D14650ECD24587E55C4D490D5C9A0000000000000000 | |||
Executable files
14
Suspicious files
13
Text files
25
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\setud69.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\liced69.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\cored79.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\dotnd79.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\Fontd88.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\DIFxd88.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\Strid88.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\isrtd98.rra | — | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{761CD2E4-96D2-4792-BA0A-408D3CFB085E}\Disk1\data1.cab | compressed | |
MD5:— | SHA256:— | |||
| 1776 | WRL GAMEPAD FOR PS3-PC.exe | C:\Users\admin\AppData\Local\Temp\{8409A90C-5B1D-4F84-B2AB-E42894139B07}\{DEC7CD2E-2BB5-40C3-9592-078F64677E6C}\defad98.rra | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report