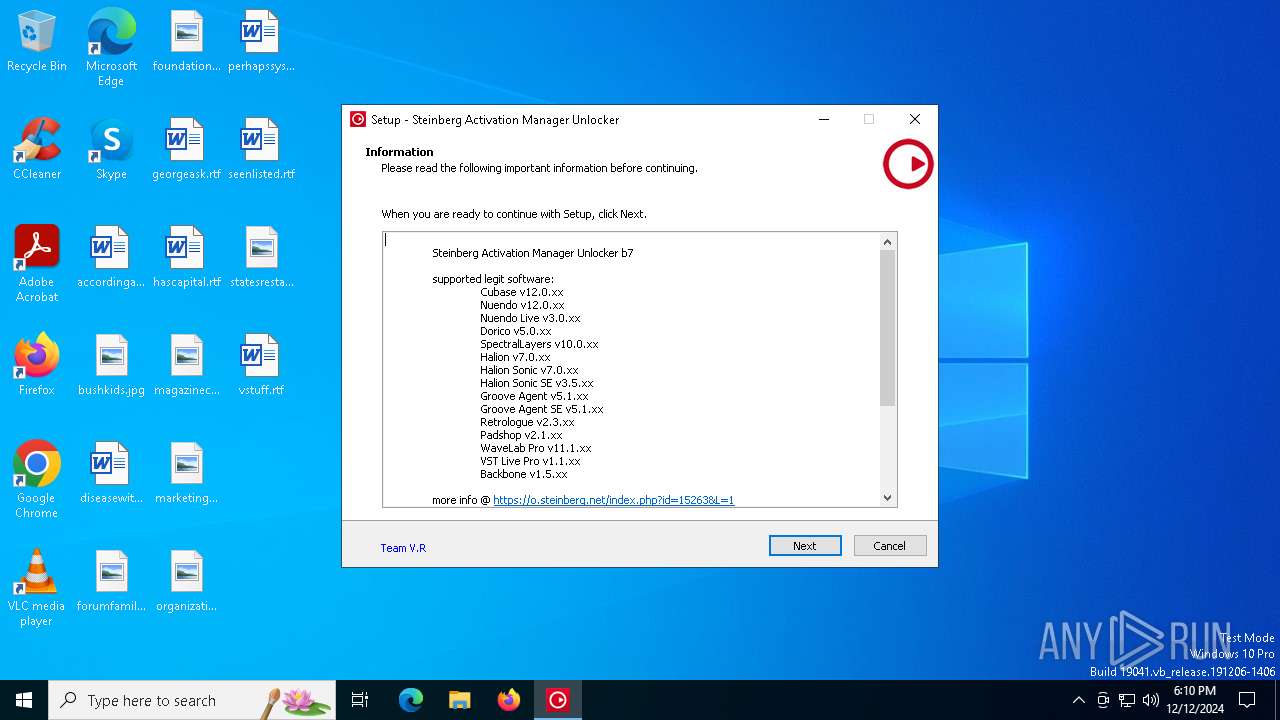
| File name: | Activation Manager Unlocker b7.exe |
| Full analysis: | https://app.any.run/tasks/d7ffd363-21f0-4373-8026-bcabce4aa391 |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2024, 18:10:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | CD185BC66A39A26C8E3CB39E5C6F0FC9 |
| SHA1: | CE080C0F1E689E301520677E2E4D11470EACD98C |
| SHA256: | C5C92160DD15279364CC98979043660DF30037E33EB0DBF6DBB107CC46BB5DD8 |
| SSDEEP: | 98304:i+cD4dnwCY11nWRpqpeFMWVFVLxr1gqX/f9dR2sSUkLqADATZRiZ4+vBpXr9amMZ:mx37K |
MALICIOUS
No malicious indicators.SUSPICIOUS
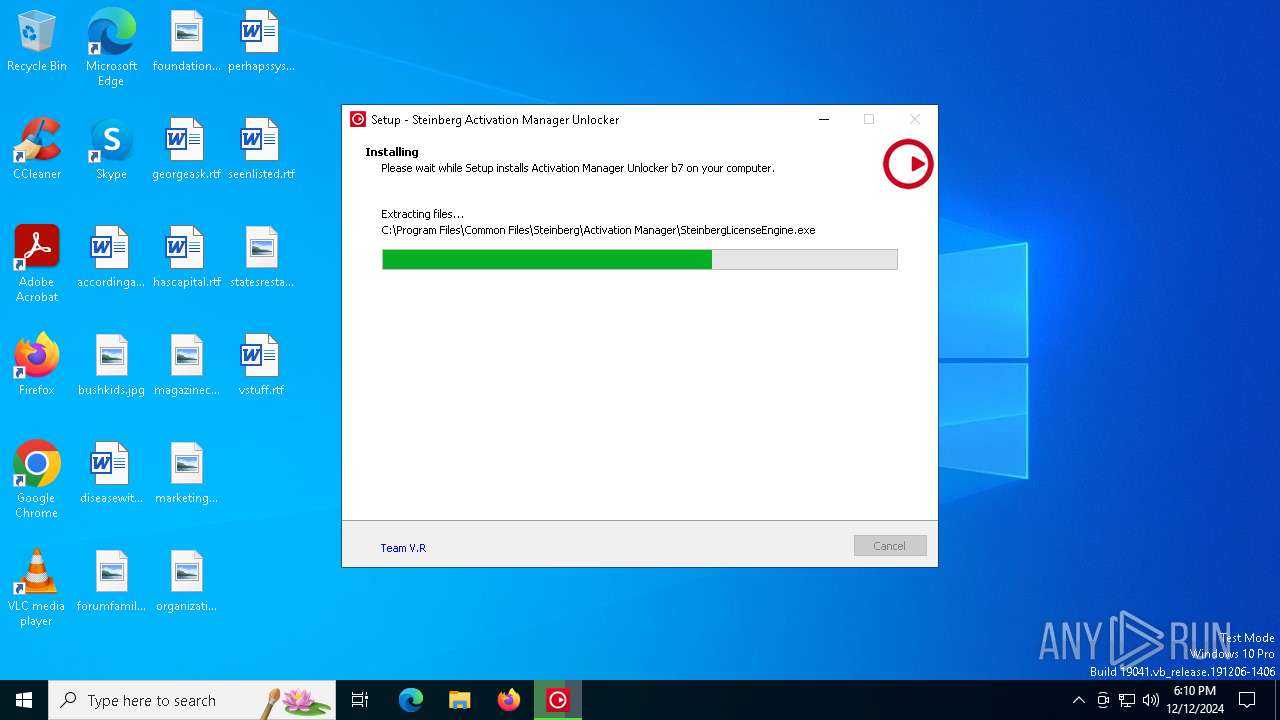
Executable content was dropped or overwritten
- Activation Manager Unlocker b7.exe (PID: 6332)
- Activation Manager Unlocker b7.tmp (PID: 6368)
Reads the Windows owner or organization settings
- Activation Manager Unlocker b7.tmp (PID: 6368)
Starts a Microsoft application from unusual location
- certmgr.exe (PID: 6428)
- makecert.exe (PID: 6540)
- certmgr.exe (PID: 6652)
- signtool.exe (PID: 6864)
- signtool.exe (PID: 6724)
Process drops legitimate windows executable
- Activation Manager Unlocker b7.tmp (PID: 6368)
Adds/modifies Windows certificates
- makecert.exe (PID: 6540)
- signtool.exe (PID: 6724)
- certmgr.exe (PID: 6652)
INFO
Checks supported languages
- Activation Manager Unlocker b7.exe (PID: 6332)
- Activation Manager Unlocker b7.tmp (PID: 6368)
- certmgr.exe (PID: 6428)
- makecert.exe (PID: 6540)
- certmgr.exe (PID: 6652)
- signtool.exe (PID: 6724)
- SearchApp.exe (PID: 5064)
- signtool.exe (PID: 6864)
Create files in a temporary directory
- Activation Manager Unlocker b7.exe (PID: 6332)
- Activation Manager Unlocker b7.tmp (PID: 6368)
- makecert.exe (PID: 6540)
Reads the computer name
- Activation Manager Unlocker b7.tmp (PID: 6368)
- makecert.exe (PID: 6540)
- signtool.exe (PID: 6724)
- signtool.exe (PID: 6864)
The sample compiled with english language support
- Activation Manager Unlocker b7.tmp (PID: 6368)
Creates files or folders in the user directory
- makecert.exe (PID: 6540)
Reads the machine GUID from the registry
- makecert.exe (PID: 6540)
- signtool.exe (PID: 6864)
- SearchApp.exe (PID: 5064)
- signtool.exe (PID: 6724)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Reads the software policy settings
- signtool.exe (PID: 6724)
- SearchApp.exe (PID: 5064)
- signtool.exe (PID: 6864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 441856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.40.1045 |
| ProductVersionNumber: | 1.4.40.1045 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Steinberg |
| FileDescription: | Steinberg Activation Manager Unlocker |
| FileVersion: | 1.4.40.1045 |
| LegalCopyright: | Team V.R private build |
| OriginalFileName: | |
| ProductName: | Steinberg Activation Manager Unlocker |
| ProductVersion: | 1.4.40.1045 |
Total processes
140
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1616 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | "C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe" | C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe | — | explorer.exe | |||||||||||
User: admin Company: Steinberg Integrity Level: MEDIUM Description: Steinberg Activation Manager Unlocker Exit code: 3221226540 Version: 1.4.40.1045 Modules
| |||||||||||||||
| 6332 | "C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe" | C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe | explorer.exe | ||||||||||||
User: admin Company: Steinberg Integrity Level: HIGH Description: Steinberg Activation Manager Unlocker Exit code: 0 Version: 1.4.40.1045 Modules
| |||||||||||||||
| 6368 | "C:\Users\admin\AppData\Local\Temp\is-DBPCJ.tmp\Activation Manager Unlocker b7.tmp" /SL5="$90224,3239068,1184768,C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe" | C:\Users\admin\AppData\Local\Temp\is-DBPCJ.tmp\Activation Manager Unlocker b7.tmp | Activation Manager Unlocker b7.exe | ||||||||||||
User: admin Company: Steinberg Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6428 | "C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\certmgr.exe" /del /all /s PrivateCertStore | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\certmgr.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.19041.685 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\makecert.exe" -r -a SHA256 -eku "1.3.6.1.5.5.7.3.3,1.3.6.1.4.1.311.10.3.13" -n CN="Steinberg Media Technologies GmbH" -pe -ss PrivateCertStore SMTG.cer | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\makecert.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM MakeCert Exit code: 0 Version: 10.0.18362.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | makecert.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6652 | "C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\certmgr.exe" -add C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\SMTG.cer -s -r localMachine ROOT | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\certmgr.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.19041.685 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 644
Read events
10 597
Write events
40
Delete events
7
Modification events
| (PID) Process: | (6540) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates |
| Operation: | delete value | Name: | CA60A09238BE9380F0251C2B1B845E27A4BF136F |
Value: | |||
| (PID) Process: | (6540) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates\CA60A09238BE9380F0251C2B1B845E27A4BF136F |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000CA60A09238BE9380F0251C2B1B845E27A4BF136F20000000010000006A030000308203663082024EA00302010202104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3234313231323138313032355A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100D78E3EF1784290E2FEBE1257B637180211E44B374CC1486D3256A1144AB80CE237AE1DFEFABF137F3696BC2F445F6E326FA2388101D7C3BC95D725BE9E3A2D8FA7FBB584DADB73261A5514A8478ACE114ED6A5EE7118EAF944914042B47C1F4F2B70F898C7BF0154ADBE44310436D7A620A1CF01BF017A14B1812DF1112058E77C4512EDDB4C40281CE190E209E36922A002DCD798C0D57018499D6472DAAB0B994C946FA091C6BBDBD9873D3AE14CA780563990A9E510135ECE9F3EF4C47DDCA72F92F668EA85EA200FA8BE9750900CDAC89E0F79BBF7F9211EB547B31ED369F92EBE8BD25B45D68C06FB037D76EA2A547CE6031C1AABB20B366BF329E21EB10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010110F42C23A90B9599FCCC2ED4352CE97A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624882104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B050003820101006E1023C7DEB2DE54FD635639D5EE06F9EDD9D1DC27775772AFB256A919CA5DAA248DA1B8734504FDC662344AA7901906C994E35E2486B3774355AC0080FF08702F8E9ED5D55208C1CC8DB1AA30DC0F4F6757813950DADC8E5CEF8BB333DCB3C7805B6ED76F28F74DA49BF12DECEB21F403138544DF7E6BF130893D89C12775AC45239DDDC5137A7682D4F2B1B1C16CF521CAB1E57D9A5106CBB29614A1D80B11C2A690D8AE3689E95FBBF26ACF48946F8B089BA0A974AC03C1F6EAD614FAB0B32EF53A963CF05969C98779F6040117EC3EEB3D37E71C59687D7C8977091AB1B921533A2C48B893E2A1982081110CEB0674BFEED30AD812F7809FDF0430F97437 | |||
| (PID) Process: | (6540) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates\CA60A09238BE9380F0251C2B1B845E27A4BF136F |
| Operation: | write | Name: | Blob |
Value: 0200000001000000BC0000001C0000006C0000000100000000000000000000000000000002000000320033003600640038006400650061002D0064003000330038002D0034006300620063002D0061006200630062002D0062006400370063003700330031006100630064006500660000000000000000004D006900630072006F0073006F006600740020005300740072006F006E0067002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072000000030000000100000014000000CA60A09238BE9380F0251C2B1B845E27A4BF136F20000000010000006A030000308203663082024EA00302010202104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3234313231323138313032355A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100D78E3EF1784290E2FEBE1257B637180211E44B374CC1486D3256A1144AB80CE237AE1DFEFABF137F3696BC2F445F6E326FA2388101D7C3BC95D725BE9E3A2D8FA7FBB584DADB73261A5514A8478ACE114ED6A5EE7118EAF944914042B47C1F4F2B70F898C7BF0154ADBE44310436D7A620A1CF01BF017A14B1812DF1112058E77C4512EDDB4C40281CE190E209E36922A002DCD798C0D57018499D6472DAAB0B994C946FA091C6BBDBD9873D3AE14CA780563990A9E510135ECE9F3EF4C47DDCA72F92F668EA85EA200FA8BE9750900CDAC89E0F79BBF7F9211EB547B31ED369F92EBE8BD25B45D68C06FB037D76EA2A547CE6031C1AABB20B366BF329E21EB10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010110F42C23A90B9599FCCC2ED4352CE97A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624882104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B050003820101006E1023C7DEB2DE54FD635639D5EE06F9EDD9D1DC27775772AFB256A919CA5DAA248DA1B8734504FDC662344AA7901906C994E35E2486B3774355AC0080FF08702F8E9ED5D55208C1CC8DB1AA30DC0F4F6757813950DADC8E5CEF8BB333DCB3C7805B6ED76F28F74DA49BF12DECEB21F403138544DF7E6BF130893D89C12775AC45239DDDC5137A7682D4F2B1B1C16CF521CAB1E57D9A5106CBB29614A1D80B11C2A690D8AE3689E95FBBF26ACF48946F8B089BA0A974AC03C1F6EAD614FAB0B32EF53A963CF05969C98779F6040117EC3EEB3D37E71C59687D7C8977091AB1B921533A2C48B893E2A1982081110CEB0674BFEED30AD812F7809FDF0430F97437 | |||
| (PID) Process: | (6724) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | CA60A09238BE9380F0251C2B1B845E27A4BF136F |
Value: | |||
| (PID) Process: | (6724) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\CA60A09238BE9380F0251C2B1B845E27A4BF136F |
| Operation: | write | Name: | Blob |
Value: 0F0000000100000020000000E773C435607F73E65EB2C7F880A38406FE2866A8DB7A1F120B68EEBDA2E4A729030000000100000014000000CA60A09238BE9380F0251C2B1B845E27A4BF136F20000000010000006A030000308203663082024EA00302010202104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3234313231323138313032355A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100D78E3EF1784290E2FEBE1257B637180211E44B374CC1486D3256A1144AB80CE237AE1DFEFABF137F3696BC2F445F6E326FA2388101D7C3BC95D725BE9E3A2D8FA7FBB584DADB73261A5514A8478ACE114ED6A5EE7118EAF944914042B47C1F4F2B70F898C7BF0154ADBE44310436D7A620A1CF01BF017A14B1812DF1112058E77C4512EDDB4C40281CE190E209E36922A002DCD798C0D57018499D6472DAAB0B994C946FA091C6BBDBD9873D3AE14CA780563990A9E510135ECE9F3EF4C47DDCA72F92F668EA85EA200FA8BE9750900CDAC89E0F79BBF7F9211EB547B31ED369F92EBE8BD25B45D68C06FB037D76EA2A547CE6031C1AABB20B366BF329E21EB10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010110F42C23A90B9599FCCC2ED4352CE97A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624882104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B050003820101006E1023C7DEB2DE54FD635639D5EE06F9EDD9D1DC27775772AFB256A919CA5DAA248DA1B8734504FDC662344AA7901906C994E35E2486B3774355AC0080FF08702F8E9ED5D55208C1CC8DB1AA30DC0F4F6757813950DADC8E5CEF8BB333DCB3C7805B6ED76F28F74DA49BF12DECEB21F403138544DF7E6BF130893D89C12775AC45239DDDC5137A7682D4F2B1B1C16CF521CAB1E57D9A5106CBB29614A1D80B11C2A690D8AE3689E95FBBF26ACF48946F8B089BA0A974AC03C1F6EAD614FAB0B32EF53A963CF05969C98779F6040117EC3EEB3D37E71C59687D7C8977091AB1B921533A2C48B893E2A1982081110CEB0674BFEED30AD812F7809FDF0430F97437 | |||
| (PID) Process: | (6652) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | CA60A09238BE9380F0251C2B1B845E27A4BF136F |
Value: | |||
| (PID) Process: | (6652) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\CA60A09238BE9380F0251C2B1B845E27A4BF136F |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000CA60A09238BE9380F0251C2B1B845E27A4BF136F20000000010000006A030000308203663082024EA00302010202104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3234313231323138313032355A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100D78E3EF1784290E2FEBE1257B637180211E44B374CC1486D3256A1144AB80CE237AE1DFEFABF137F3696BC2F445F6E326FA2388101D7C3BC95D725BE9E3A2D8FA7FBB584DADB73261A5514A8478ACE114ED6A5EE7118EAF944914042B47C1F4F2B70F898C7BF0154ADBE44310436D7A620A1CF01BF017A14B1812DF1112058E77C4512EDDB4C40281CE190E209E36922A002DCD798C0D57018499D6472DAAB0B994C946FA091C6BBDBD9873D3AE14CA780563990A9E510135ECE9F3EF4C47DDCA72F92F668EA85EA200FA8BE9750900CDAC89E0F79BBF7F9211EB547B31ED369F92EBE8BD25B45D68C06FB037D76EA2A547CE6031C1AABB20B366BF329E21EB10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010110F42C23A90B9599FCCC2ED4352CE97A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624882104CDC728E8C649EBD48BAE3AD83C86342300D06092A864886F70D01010B050003820101006E1023C7DEB2DE54FD635639D5EE06F9EDD9D1DC27775772AFB256A919CA5DAA248DA1B8734504FDC662344AA7901906C994E35E2486B3774355AC0080FF08702F8E9ED5D55208C1CC8DB1AA30DC0F4F6757813950DADC8E5CEF8BB333DCB3C7805B6ED76F28F74DA49BF12DECEB21F403138544DF7E6BF130893D89C12775AC45239DDDC5137A7682D4F2B1B1C16CF521CAB1E57D9A5106CBB29614A1D80B11C2A690D8AE3689E95FBBF26ACF48946F8B089BA0A974AC03C1F6EAD614FAB0B32EF53A963CF05969C98779F6040117EC3EEB3D37E71C59687D7C8977091AB1B921533A2C48B893E2A1982081110CEB0674BFEED30AD812F7809FDF0430F97437 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | delete value | Name: | JumpListChangedAppIds |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 1497 | |||
Executable files
13
Suspicious files
13
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6332 | Activation Manager Unlocker b7.exe | C:\Users\admin\AppData\Local\Temp\is-DBPCJ.tmp\Activation Manager Unlocker b7.tmp | executable | |
MD5:3E69F3E1E17D3E74745D5B793DDFA70C | SHA256:EB501987C8027D4841BE7EA908BC2245D1DF03BA981A59868586D6605D6C9D4E | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133785006303504867.txt~RF138b3c.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\is-GA7L3.tmp | executable | |
MD5:8AC6FFB0ABC20398BBD8F3C7C0519609 | SHA256:68040976EA73A1C4A14E40FEDBCB886EDB7AE97B006B9540C74C0F0D313DC78B | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\tmp.zip | compressed | |
MD5:38C1D0C698223371D30B39348FD1DC84 | SHA256:C28DBA2339936FF43DE23C7A95EF43640B43B0C841FDF015D512AEC9D58BBBD5 | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\certmgr.exe | executable | |
MD5:8AC6FFB0ABC20398BBD8F3C7C0519609 | SHA256:68040976EA73A1C4A14E40FEDBCB886EDB7AE97B006B9540C74C0F0D313DC78B | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133785006303504867.txt.~tmp | ini | |
MD5:39FEA118E9A443749C833A616160B40F | SHA256:32F96CF504EF57CA43A9E9886A741DE0DD6AA7DDAEBC78DAAC2D3B041C2C5B53 | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\is-89JMR.tmp | compressed | |
MD5:38C1D0C698223371D30B39348FD1DC84 | SHA256:C28DBA2339936FF43DE23C7A95EF43640B43B0C841FDF015D512AEC9D58BBBD5 | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\is-UEC94.tmp | executable | |
MD5:8A90E91A512DBF56D0D8D87B9A673E53 | SHA256:A36F5E81CE208137ACC8FA9C00547C020FA10F044583002CCD23799B7F64078E | |||
| 6368 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-LTD4J.tmp\is-210QB.tmp | executable | |
MD5:934B19D32E1DC15D4CC2B8DEE12DE758 | SHA256:D184933B6917FAF559BD250C7F2D47D1BC9BBA98442AA0F4B48D4371357C81DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
38
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5856 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6032 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5856 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5856 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
wac-ring.msedge.net |
| unknown |