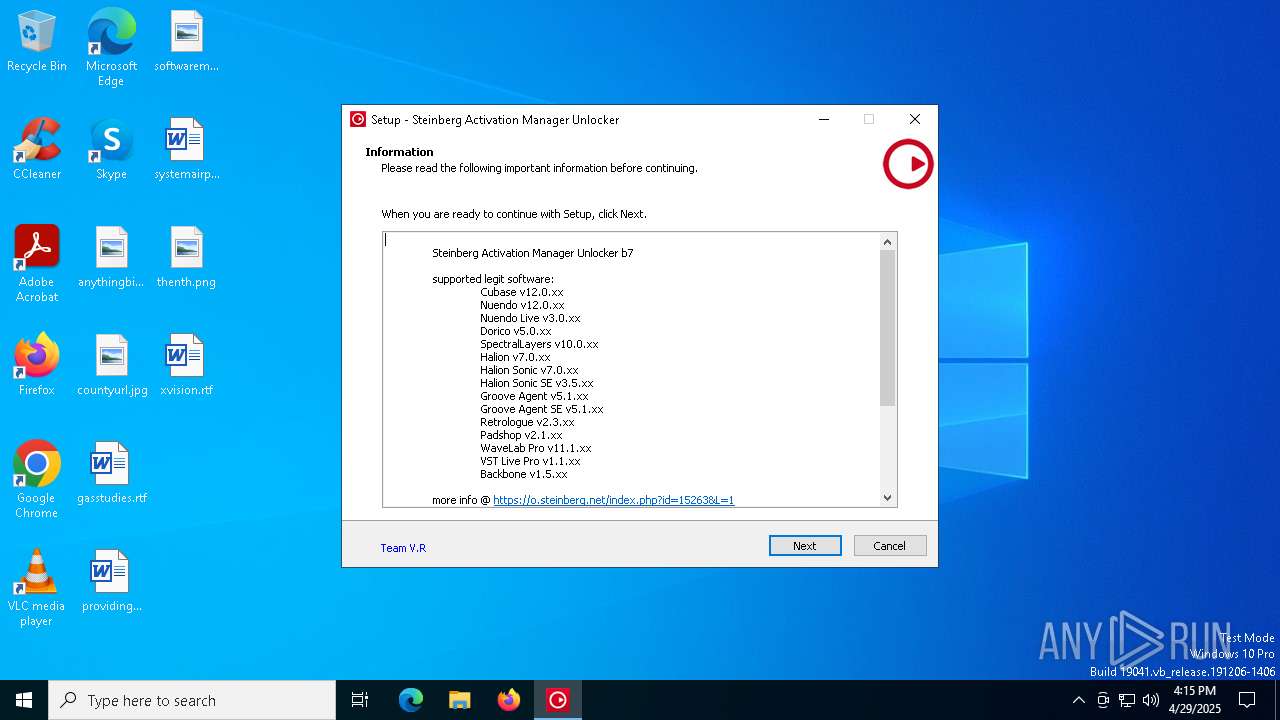
| File name: | Activation Manager Unlocker b7.exe |
| Full analysis: | https://app.any.run/tasks/4f870c15-d4f9-48b9-bb68-7b9e86406b39 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 16:15:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | CD185BC66A39A26C8E3CB39E5C6F0FC9 |
| SHA1: | CE080C0F1E689E301520677E2E4D11470EACD98C |
| SHA256: | C5C92160DD15279364CC98979043660DF30037E33EB0DBF6DBB107CC46BB5DD8 |
| SSDEEP: | 98304:i+cD4dnwCY11nWRpqpeFMWVFVLxr1gqX/f9dR2sSUkLqADATZRiZ4+vBpXr9amMZ:mx37K |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- Activation Manager Unlocker b7.tmp (PID: 5556)
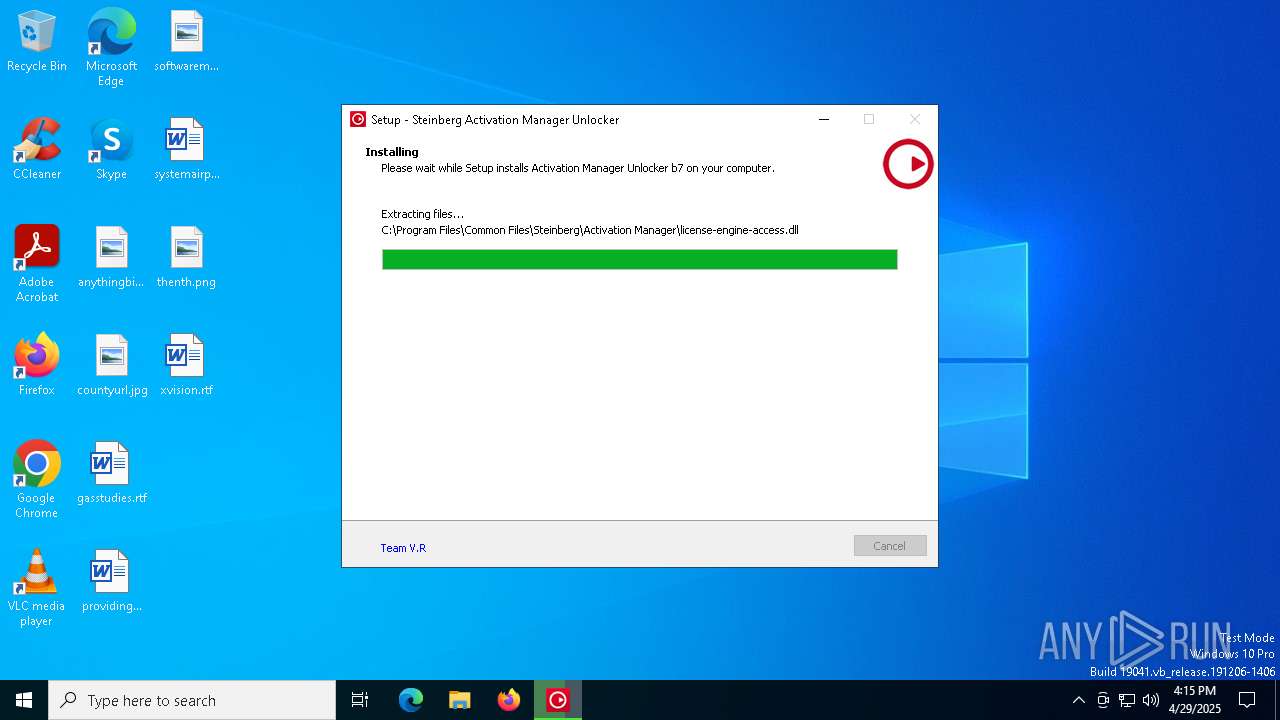
Executable content was dropped or overwritten
- Activation Manager Unlocker b7.exe (PID: 1628)
- Activation Manager Unlocker b7.tmp (PID: 5556)
Process drops legitimate windows executable
- Activation Manager Unlocker b7.tmp (PID: 5556)
Starts a Microsoft application from unusual location
- certmgr.exe (PID: 4920)
- makecert.exe (PID: 4408)
- certmgr.exe (PID: 5608)
- signtool.exe (PID: 732)
- signtool.exe (PID: 3100)
Adds/modifies Windows certificates
- makecert.exe (PID: 4408)
- certmgr.exe (PID: 5608)
- signtool.exe (PID: 3100)
INFO
Checks supported languages
- Activation Manager Unlocker b7.exe (PID: 1628)
- Activation Manager Unlocker b7.tmp (PID: 5556)
- certmgr.exe (PID: 4920)
- makecert.exe (PID: 4408)
- certmgr.exe (PID: 5608)
- signtool.exe (PID: 3100)
- signtool.exe (PID: 732)
Create files in a temporary directory
- Activation Manager Unlocker b7.exe (PID: 1628)
- Activation Manager Unlocker b7.tmp (PID: 5556)
- makecert.exe (PID: 4408)
Reads the computer name
- Activation Manager Unlocker b7.tmp (PID: 5556)
- makecert.exe (PID: 4408)
- signtool.exe (PID: 3100)
- signtool.exe (PID: 732)
Creates files in the program directory
- Activation Manager Unlocker b7.tmp (PID: 5556)
The sample compiled with english language support
- Activation Manager Unlocker b7.tmp (PID: 5556)
Reads the machine GUID from the registry
- makecert.exe (PID: 4408)
- signtool.exe (PID: 732)
- signtool.exe (PID: 3100)
Creates files or folders in the user directory
- makecert.exe (PID: 4408)
Reads the software policy settings
- signtool.exe (PID: 3100)
- signtool.exe (PID: 732)
Detects InnoSetup installer (YARA)
- Activation Manager Unlocker b7.tmp (PID: 5556)
- Activation Manager Unlocker b7.exe (PID: 1628)
Compiled with Borland Delphi (YARA)
- Activation Manager Unlocker b7.tmp (PID: 5556)
- Activation Manager Unlocker b7.exe (PID: 1628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 441856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.40.1045 |
| ProductVersionNumber: | 1.4.40.1045 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Steinberg |
| FileDescription: | Steinberg Activation Manager Unlocker |
| FileVersion: | 1.4.40.1045 |
| LegalCopyright: | Team V.R private build |
| OriginalFileName: | |
| ProductName: | Steinberg Activation Manager Unlocker |
| ProductVersion: | 1.4.40.1045 |
Total processes
143
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\signtool.exe" sign /fd SHA256 /v /s PrivateCertStore /a /n "Steinberg Media Technologies GmbH" "C:\Program Files\Common Files\Steinberg\Activation Manager\SteinbergLicenseEngine.exe" | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\signtool.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Authenticode(R) - signing and verifying tool Exit code: 0 Version: 4.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | signtool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe" | C:\Users\admin\AppData\Local\Temp\Activation Manager Unlocker b7.exe | explorer.exe | ||||||||||||
User: admin Company: Steinberg Integrity Level: HIGH Description: Steinberg Activation Manager Unlocker Exit code: 0 Version: 1.4.40.1045 Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\signtool.exe" sign /fd SHA256 /v /s PrivateCertStore /a /n "Steinberg Media Technologies GmbH" "C:\Program Files\Common Files\Steinberg\Activation Manager\license-engine-access.dll" | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\signtool.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Authenticode(R) - signing and verifying tool Exit code: 0 Version: 4.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | "C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\makecert.exe" -r -a SHA256 -eku "1.3.6.1.5.5.7.3.3,1.3.6.1.4.1.311.10.3.13" -n CN="Steinberg Media Technologies GmbH" -pe -ss PrivateCertStore SMTG.cer | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\makecert.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM MakeCert Exit code: 0 Version: 10.0.18362.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\certmgr.exe" /del /all /s PrivateCertStore | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\certmgr.exe | — | Activation Manager Unlocker b7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 10.0.19041.685 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 119
Read events
8 111
Write events
4
Delete events
4
Modification events
| (PID) Process: | (4408) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates |
| Operation: | delete value | Name: | 1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
Value: | |||
| (PID) Process: | (4408) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates\1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000001B35CCE8DC27590B10A9C72085EFBADEE10F3AB720000000010000006A030000308203663082024EA0030201020210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3235303432393136313533305A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100BFF6D7B71F48C90884019E9630A282CF7D891930EA0C42A0E4DE950DEF1156023547FC61F21470E41954AD48FEB918782E00BF6167C15608E89FFA99477B2B180A16047E632B43AF178C247AA4F7F0EFC7AE09F2D8B7C7B0857C9939437BE2408A084D4EDF6EC500AD76BDCC44281E139310A79D5DE79A72E68EFD965BE226F11710E0CDD784BF410182143A6643A88E760F965ABFF7B324A1F26D2FCA5606FBB5E5A401EB96CF00140BA3129C5CB7730C0CE0E43AF4D91B240F4F2D29CCB24B45C615FE6985CCBC119820CEB9DD630A6D147BDC3CFD48E298F109E00F7C19163F3DDC4A5CE8FBB5EFA570AE2B8E3A25CE7C017DB17CF164A77BC78EFA7E7BC10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010EE347769A768E7026578F9836CBDDEE5A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D62488210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500038201010030DD22A36658B8BAE3DC923DBE56E7D1DEAC8E7369F55E192DCFB2E1B0393423559F03283A90BCE7463CE5C9C8C3C99F39AA07A95E13DD9F48A2E7707A1FF930E7D9D1E718023A90BE6875DAAC6F9820F4659EB271ACCBC82518E2ABD1020C3D5E3648F04E9CC44FD23E6373ACD1EA41EA1E35252823B80F3C393E301422441BB67F5B204D9C5D1DFBE8D507FA145DCD9DF06B08E3C811B39FFB0599FF4BC759771347C7D375E0F620ECB9B4CF14ECB852651CEE734694E1FBB245CFBD365A17152BEDB5E227A15155BCDB38B3F2D16ABF36EFEEC3E022710B511224B8D0EC4E0BCD8F5169FD3E849E7EF91DC1B87CF203EA3CDF90725C2D85EAFA184782C6D7 | |||
| (PID) Process: | (4408) makecert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\SystemCertificates\PrivateCertStore\Certificates\1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
| Operation: | write | Name: | Blob |
Value: 0200000001000000BC0000001C0000006C0000000100000000000000000000000000000002000000340032003400370065003000610063002D0031003000330037002D0034003500390037002D0061003500630062002D0062006400330032006200650062003400300032006100610000000000000000004D006900630072006F0073006F006600740020005300740072006F006E0067002000430072007900700074006F0067007200610070006800690063002000500072006F007600690064006500720000000300000001000000140000001B35CCE8DC27590B10A9C72085EFBADEE10F3AB720000000010000006A030000308203663082024EA0030201020210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3235303432393136313533305A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100BFF6D7B71F48C90884019E9630A282CF7D891930EA0C42A0E4DE950DEF1156023547FC61F21470E41954AD48FEB918782E00BF6167C15608E89FFA99477B2B180A16047E632B43AF178C247AA4F7F0EFC7AE09F2D8B7C7B0857C9939437BE2408A084D4EDF6EC500AD76BDCC44281E139310A79D5DE79A72E68EFD965BE226F11710E0CDD784BF410182143A6643A88E760F965ABFF7B324A1F26D2FCA5606FBB5E5A401EB96CF00140BA3129C5CB7730C0CE0E43AF4D91B240F4F2D29CCB24B45C615FE6985CCBC119820CEB9DD630A6D147BDC3CFD48E298F109E00F7C19163F3DDC4A5CE8FBB5EFA570AE2B8E3A25CE7C017DB17CF164A77BC78EFA7E7BC10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010EE347769A768E7026578F9836CBDDEE5A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D62488210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500038201010030DD22A36658B8BAE3DC923DBE56E7D1DEAC8E7369F55E192DCFB2E1B0393423559F03283A90BCE7463CE5C9C8C3C99F39AA07A95E13DD9F48A2E7707A1FF930E7D9D1E718023A90BE6875DAAC6F9820F4659EB271ACCBC82518E2ABD1020C3D5E3648F04E9CC44FD23E6373ACD1EA41EA1E35252823B80F3C393E301422441BB67F5B204D9C5D1DFBE8D507FA145DCD9DF06B08E3C811B39FFB0599FF4BC759771347C7D375E0F620ECB9B4CF14ECB852651CEE734694E1FBB245CFBD365A17152BEDB5E227A15155BCDB38B3F2D16ABF36EFEEC3E022710B511224B8D0EC4E0BCD8F5169FD3E849E7EF91DC1B87CF203EA3CDF90725C2D85EAFA184782C6D7 | |||
| (PID) Process: | (5608) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
Value: | |||
| (PID) Process: | (5608) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000001B35CCE8DC27590B10A9C72085EFBADEE10F3AB720000000010000006A030000308203663082024EA0030201020210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3235303432393136313533305A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100BFF6D7B71F48C90884019E9630A282CF7D891930EA0C42A0E4DE950DEF1156023547FC61F21470E41954AD48FEB918782E00BF6167C15608E89FFA99477B2B180A16047E632B43AF178C247AA4F7F0EFC7AE09F2D8B7C7B0857C9939437BE2408A084D4EDF6EC500AD76BDCC44281E139310A79D5DE79A72E68EFD965BE226F11710E0CDD784BF410182143A6643A88E760F965ABFF7B324A1F26D2FCA5606FBB5E5A401EB96CF00140BA3129C5CB7730C0CE0E43AF4D91B240F4F2D29CCB24B45C615FE6985CCBC119820CEB9DD630A6D147BDC3CFD48E298F109E00F7C19163F3DDC4A5CE8FBB5EFA570AE2B8E3A25CE7C017DB17CF164A77BC78EFA7E7BC10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010EE347769A768E7026578F9836CBDDEE5A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D62488210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500038201010030DD22A36658B8BAE3DC923DBE56E7D1DEAC8E7369F55E192DCFB2E1B0393423559F03283A90BCE7463CE5C9C8C3C99F39AA07A95E13DD9F48A2E7707A1FF930E7D9D1E718023A90BE6875DAAC6F9820F4659EB271ACCBC82518E2ABD1020C3D5E3648F04E9CC44FD23E6373ACD1EA41EA1E35252823B80F3C393E301422441BB67F5B204D9C5D1DFBE8D507FA145DCD9DF06B08E3C811B39FFB0599FF4BC759771347C7D375E0F620ECB9B4CF14ECB852651CEE734694E1FBB245CFBD365A17152BEDB5E227A15155BCDB38B3F2D16ABF36EFEEC3E022710B511224B8D0EC4E0BCD8F5169FD3E849E7EF91DC1B87CF203EA3CDF90725C2D85EAFA184782C6D7 | |||
| (PID) Process: | (3100) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
Value: | |||
| (PID) Process: | (3100) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\1B35CCE8DC27590B10A9C72085EFBADEE10F3AB7 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000002000000010BFDBC4AAA8AD6F544DA52A8DC426D87958B65778BBB977BF6000320879B49A0300000001000000140000001B35CCE8DC27590B10A9C72085EFBADEE10F3AB720000000010000006A030000308203663082024EA0030201020210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D6248301E170D3235303432393136313533305A170D3339313233313233353935395A302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D624830820122300D06092A864886F70D01010105000382010F003082010A0282010100BFF6D7B71F48C90884019E9630A282CF7D891930EA0C42A0E4DE950DEF1156023547FC61F21470E41954AD48FEB918782E00BF6167C15608E89FFA99477B2B180A16047E632B43AF178C247AA4F7F0EFC7AE09F2D8B7C7B0857C9939437BE2408A084D4EDF6EC500AD76BDCC44281E139310A79D5DE79A72E68EFD965BE226F11710E0CDD784BF410182143A6643A88E760F965ABFF7B324A1F26D2FCA5606FBB5E5A401EB96CF00140BA3129C5CB7730C0CE0E43AF4D91B240F4F2D29CCB24B45C615FE6985CCBC119820CEB9DD630A6D147BDC3CFD48E298F109E00F7C19163F3DDC4A5CE8FBB5EFA570AE2B8E3A25CE7C017DB17CF164A77BC78EFA7E7BC10203010001A38183308180301F0603551D250418301606082B06010505070303060A2B0601040182370A030D305D0603551D01045630548010EE347769A768E7026578F9836CBDDEE5A12E302C312A302806035504031321537465696E62657267204D6564696120546563686E6F6C6F6769657320476D62488210A7E4EE08496D98AB4C9E32F1F9BBDCBD300D06092A864886F70D01010B0500038201010030DD22A36658B8BAE3DC923DBE56E7D1DEAC8E7369F55E192DCFB2E1B0393423559F03283A90BCE7463CE5C9C8C3C99F39AA07A95E13DD9F48A2E7707A1FF930E7D9D1E718023A90BE6875DAAC6F9820F4659EB271ACCBC82518E2ABD1020C3D5E3648F04E9CC44FD23E6373ACD1EA41EA1E35252823B80F3C393E301422441BB67F5B204D9C5D1DFBE8D507FA145DCD9DF06B08E3C811B39FFB0599FF4BC759771347C7D375E0F620ECB9B4CF14ECB852651CEE734694E1FBB245CFBD365A17152BEDB5E227A15155BCDB38B3F2D16ABF36EFEEC3E022710B511224B8D0EC4E0BCD8F5169FD3E849E7EF91DC1B87CF203EA3CDF90725C2D85EAFA184782C6D7 | |||
Executable files
13
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\makecert.exe | executable | |
MD5:934B19D32E1DC15D4CC2B8DEE12DE758 | SHA256:D184933B6917FAF559BD250C7F2D47D1BC9BBA98442AA0F4B48D4371357C81DD | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\tmp.zip | compressed | |
MD5:38C1D0C698223371D30B39348FD1DC84 | SHA256:C28DBA2339936FF43DE23C7A95EF43640B43B0C841FDF015D512AEC9D58BBBD5 | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\is-4AF7E.tmp | executable | |
MD5:934B19D32E1DC15D4CC2B8DEE12DE758 | SHA256:D184933B6917FAF559BD250C7F2D47D1BC9BBA98442AA0F4B48D4371357C81DD | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\certmgr.exe | executable | |
MD5:8AC6FFB0ABC20398BBD8F3C7C0519609 | SHA256:68040976EA73A1C4A14E40FEDBCB886EDB7AE97B006B9540C74C0F0D313DC78B | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\is-THBIT.tmp | compressed | |
MD5:38C1D0C698223371D30B39348FD1DC84 | SHA256:C28DBA2339936FF43DE23C7A95EF43640B43B0C841FDF015D512AEC9D58BBBD5 | |||
| 4408 | makecert.exe | C:\Users\admin\AppData\Local\Temp\is-BVHUL.tmp\SMTG.cer | binary | |
MD5:219EA3E6264FF88CDB81BDFFDFCB80A2 | SHA256:352FEDC8122FF8E0047BA3D300B666DC2140FD0B076EC6540F80B12CD22A1AF6 | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Program Files\Common Files\Steinberg\Activation Manager\license-engine-access.dll | executable | |
MD5:E095A701FBA2AB9CA337BD70DE5CEAAD | SHA256:74F0FF345930C7DC6A0EAF2113E9FF2E29596D19628F549C2D7726501DE51081 | |||
| 5556 | Activation Manager Unlocker b7.tmp | C:\Program Files\Common Files\Steinberg\Activation Manager\SteinbergLicenseEngine.exe | executable | |
MD5:4839B82C060AE8240AF6CCBD7261B6B5 | SHA256:7A3F47B4DCFE5025498911A03FA62D2F81F7ADAE700F32AF3D25EA359AC06CDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |