| File name: | Windows 7,XP, Vista Activator.exe |
| Full analysis: | https://app.any.run/tasks/db9cb826-efc0-4ed3-9819-98ed319441fa |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2024, 12:44:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C0827BFDFA8A4E9E52A098584569F8F8 |
| SHA1: | 71691BFA130C1F97F7C639C77CEFEC453BC2DB52 |
| SHA256: | C5B2AD888403A5BB05FCAA02363477594EEE07693F7BFB6B7615773EE72EC33F |
| SSDEEP: | 98304:p3lMudgBXcer3Yio4WvoIOhM1SCkt7Y39T8u60HGsl2SZ85RRfh9Nwkk9jzqt101:1mxnX8d |
MALICIOUS
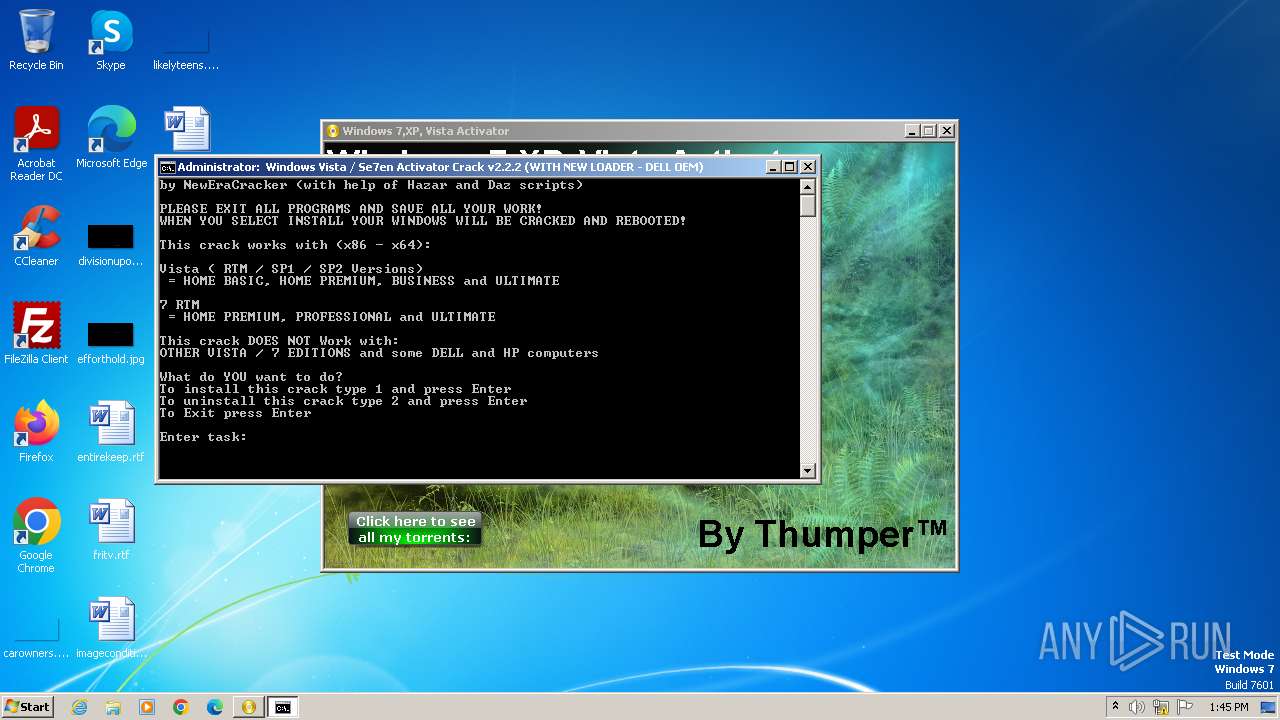
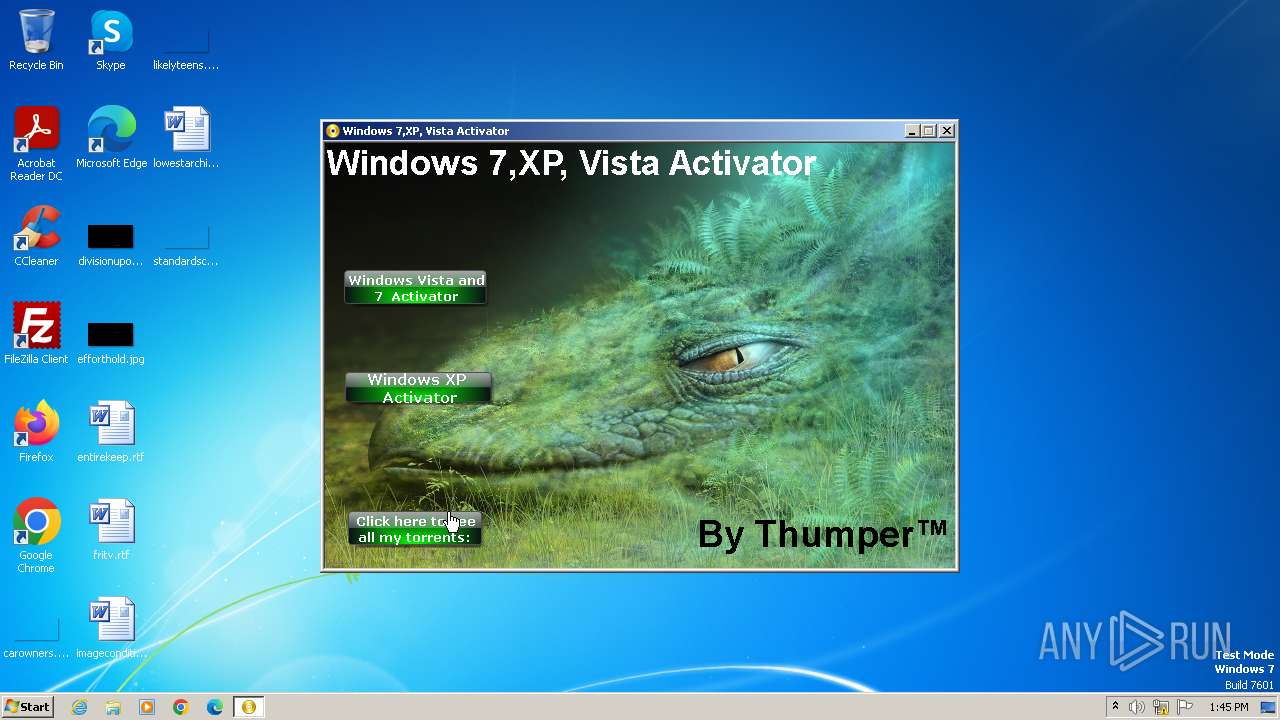
Drops the executable file immediately after the start
- Windows 7,XP, Vista Activator.exe (PID: 3976)
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
SUSPICIOUS
Reads security settings of Internet Explorer
- autorun.exe (PID: 3992)
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
Executable content was dropped or overwritten
- Windows 7,XP, Vista Activator.exe (PID: 3976)
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
Reads the Internet Settings
- autorun.exe (PID: 3992)
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
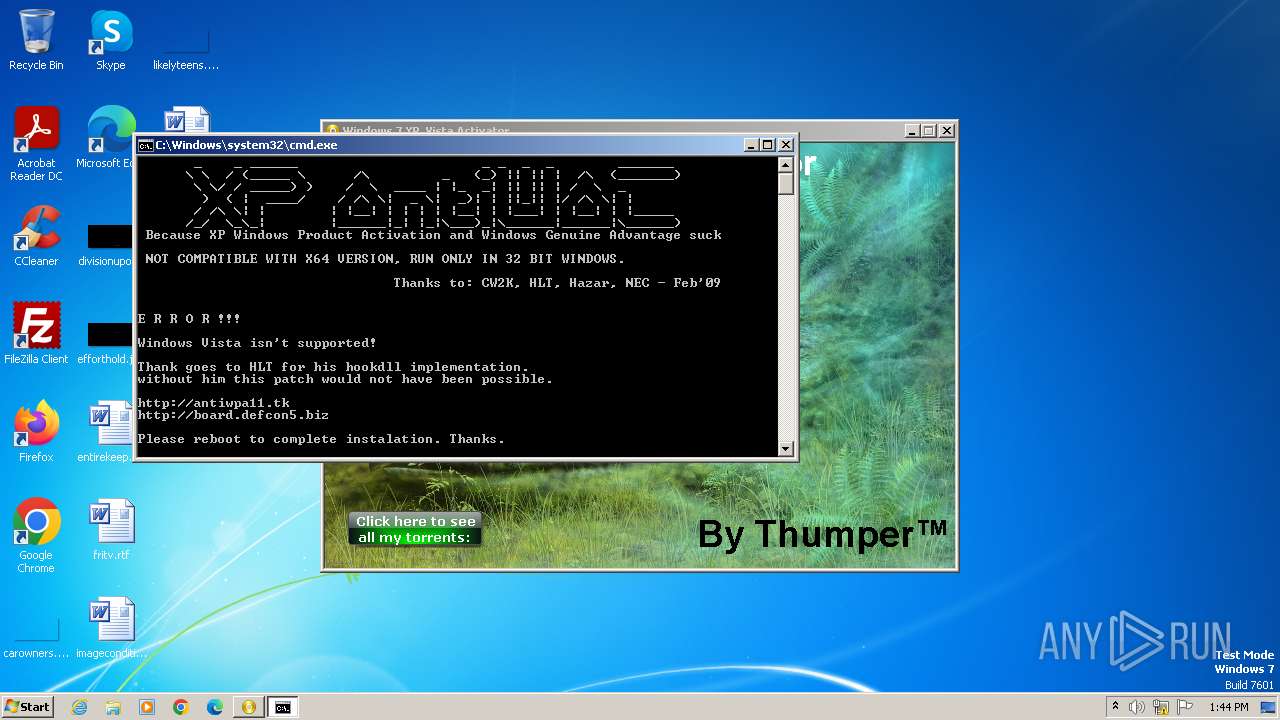
Starts CMD.EXE for commands execution
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
Executing commands from ".cmd" file
- nec-XPact.exe (PID: 1772)
Process drops legitimate windows executable
- Vis7act.exe (PID: 2052)
Executing commands from a ".bat" file
- Vis7act.exe (PID: 2052)
INFO
Create files in a temporary directory
- Windows 7,XP, Vista Activator.exe (PID: 3976)
- nec-XPact.exe (PID: 1772)
- Vis7act.exe (PID: 2052)
Checks supported languages
- Windows 7,XP, Vista Activator.exe (PID: 3976)
- autorun.exe (PID: 3992)
- nec-XPact.exe (PID: 1772)
- wmpnscfg.exe (PID: 2384)
- Vis7act.exe (PID: 2052)
Reads the computer name
- autorun.exe (PID: 3992)
- nec-XPact.exe (PID: 1772)
- wmpnscfg.exe (PID: 2384)
- Vis7act.exe (PID: 2052)
Application launched itself
- msedge.exe (PID: 1640)
Manual execution by a user
- wmpnscfg.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:10:28 13:09:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 192512 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x173a6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.5.1004.0 |
| ProductVersionNumber: | 7.5.1004.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Created with AutoPlay Media Studio |
| CompanyName: | - |
| FileDescription: | AutoPlay Application |
| FileVersion: | 7.5.1004.0 |
| InternalName: | ams_launch |
| LegalCopyright: | Runtime Engine Copyright © 2008 Indigo Rose Corporation (www.indigorose.com) |
| LegalTrademarks: | AutoPlay Media Studio is a Trademark of Indigo Rose Corporation |
| OriginalFileName: | ams_launch.exe |
| PrivateBuild: | - |
| ProductName: | AutoPlay Media Studio Launcher |
| ProductVersion: | 7.5.1004.0 |
| SpecialBuild: | - |
Total processes
63
Monitored processes
23
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\nec-XPact.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\nec-XPact.exe | — | autorun.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2232 --field-trial-handle=1316,i,13813796971458550348,15159359821924521690,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1476 --field-trial-handle=1316,i,13813796971458550348,15159359821924521690,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Vis7act.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Vis7act.exe | — | autorun.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1580 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\XPAntiWAT.cmd" " | C:\Windows\System32\cmd.exe | — | nec-XPact.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
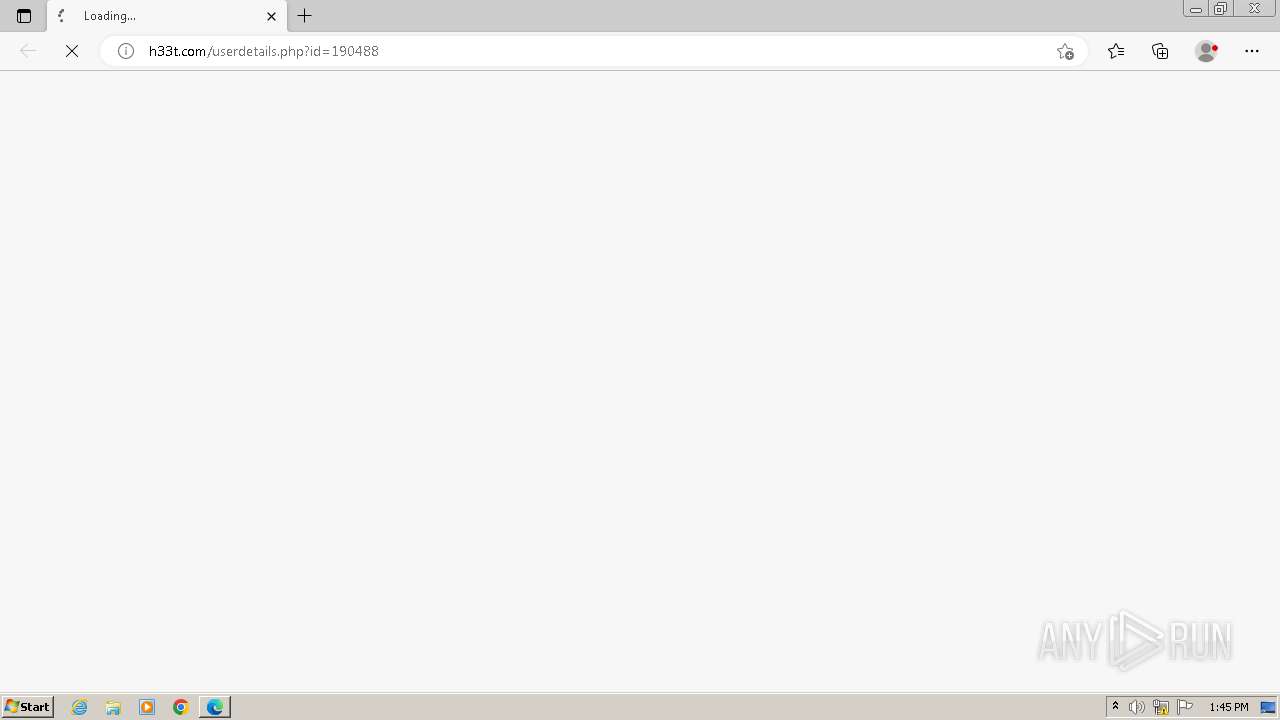
| 1640 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://h33t.com/userdetails.php?id=190488 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | autorun.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1772 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\nec-XPact.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\nec-XPact.exe | autorun.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Vis7act.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Docs\Vis7act.exe | autorun.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2092 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX1\setup.bat" " | C:\Windows\System32\cmd.exe | — | Vis7act.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2264 --field-trial-handle=1316,i,13813796971458550348,15159359821924521690,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
10 728
Read events
10 665
Write events
57
Delete events
6
Modification events
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3992) autorun.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1772) nec-XPact.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1772) nec-XPact.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1772) nec-XPact.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1772) nec-XPact.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2052) Vis7act.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2052) Vis7act.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
8
Suspicious files
68
Text files
48
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | Windows 7,XP, Vista Activator.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\Best techno 2009.mp3 | binary | |
MD5:FD59B27B2DC0AAA525565AD1BFCFD656 | SHA256:2669CD5D3FACA72999CDBF3923DBA54D5C40BD3EA8A5F5EE6D67653978376A25 | |||
| 3976 | Windows 7,XP, Vista Activator.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Buttons\Green.btn | compressed | |
MD5:7080014182EB394217C3D725CB70B3D6 | SHA256:C3186BE9B4016CBBA99DF3D74E2C88B366CB75BB7AC335DC5F0794D2E1950FC8 | |||
| 3976 | Windows 7,XP, Vista Activator.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\Click1.ogg | ogg | |
MD5:93270C4FA492E4E4EDEE872A2B961DDE | SHA256:25D49CBBD65D48AD462455F1143F73EE997DF8F747E7D2213DAAB18E321C028B | |||
| 3976 | Windows 7,XP, Vista Activator.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\High1.ogg | ogg | |
MD5:FC2A595F574B1EAD82A6DCF06492C985 | SHA256:EE9A4903A8DF90EFF4C5B65A8073E564A3581CF73772A72EB82396E69932E769 | |||
| 2052 | Vis7act.exe | C:\Users\admin\AppData\Local\Temp\RarSFX1\bootinst.exe | executable | |
MD5:70C5F6F69CDC6C5B8240622CF7D90380 | SHA256:D7ABA1FA037041412052BFDC0127D44BD63597BF01151058D3EDF585186387BE | |||
| 1772 | nec-XPact.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\genuine.reg | text | |
MD5:849D6CCFAA04151414C73E012CD89F50 | SHA256:76E90999A564568205FA30C19DA957F6BC2B7099ED96563D65B5F9C8014445A2 | |||
| 1772 | nec-XPact.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\XPAntiWAT.cmd | text | |
MD5:C1D9CE6EBF3F7EF5936CC8985720147A | SHA256:CE758AC3542D3F9F8660AB9960DFC1D066F0DC4CF3B4142EBAE81F33141FE90E | |||
| 1772 | nec-XPact.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\oobe.hiv | binary | |
MD5:2EEB8C3C06FE94BEABBC6F42C2A0CB2D | SHA256:0B2AC64B9BC7C73411B237A35625C437C3C1C10B71777D843D68A4CB45AC6053 | |||
| 2052 | Vis7act.exe | C:\Users\admin\AppData\Local\Temp\RarSFX1\setup.bat | text | |
MD5:F51C5D2A43415E12BA65C6825FDC8BE4 | SHA256:8EDDFBF44CEC2C4094086765913650A8A66A42D8FC180CBF1E0F093CB07C35A6 | |||
| 2052 | Vis7act.exe | C:\Users\admin\AppData\Local\Temp\RarSFX1\editioncheck.exe | executable | |
MD5:FC6C8BDFCD8C669DB525CABD1E1F9A3B | SHA256:B4835583E1B887C5432ADB0052D0A5FA6524F51E2EA4E676571838AC5BFE7613 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
15
DNS requests
12
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2508 | msedge.exe | 49.13.77.253:80 | h33t.com | Hetzner Online GmbH | DE | unknown |
1640 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2508 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2508 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2508 | msedge.exe | 2.19.193.138:443 | www.bing.com | Akamai International B.V. | TR | unknown |
2508 | msedge.exe | 88.221.88.50:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
h33t.com |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |