| download: | index.html |
| Full analysis: | https://app.any.run/tasks/c20af069-f002-4117-9f32-a70eda6b862b |
| Verdict: | No threats detected |
| Analysis date: | May 21, 2018, 21:49:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 4035D8059778B3C2D74CA8EE2DE5C978 |
| SHA1: | 385C1151D263A620537EB654410DE3EA5D942D8F |
| SHA256: | C5B233E53FFE51A6BBBDB39EA1B459B019593DA0A0F683AB2CCF3D4D0D68EAB8 |
| SSDEEP: | 6144:n3swSDouEQgC4AO5ZzsYxNVqvDC4zJhohZpwH36sjaEIggtGTK2rt9tefo:8iuiK9tEo |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
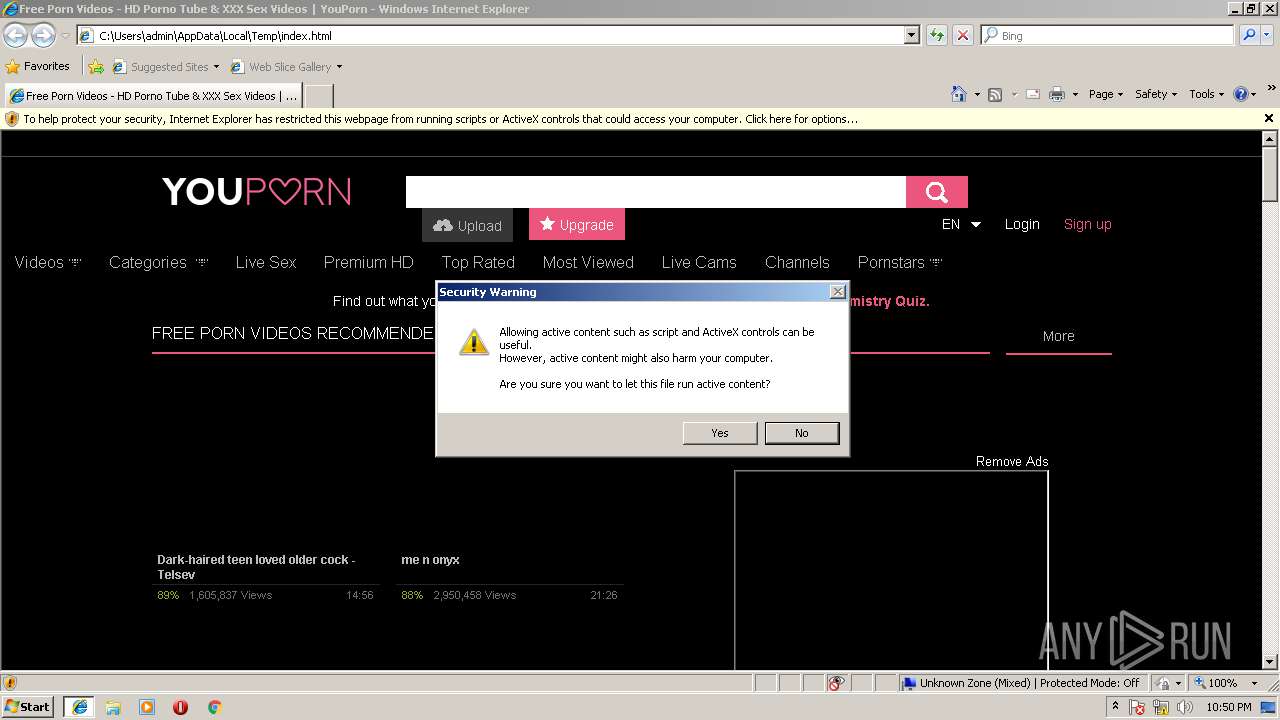
Changes internet zones settings
- iexplore.exe (PID: 3268)
Reads internet explorer settings
- iexplore.exe (PID: 3820)
Creates files in the user directory
- iexplore.exe (PID: 3820)
Dropped object may contain URL's
- iexplore.exe (PID: 3268)
- iexplore.exe (PID: 3820)
Reads settings of System Certificates
- iexplore.exe (PID: 3820)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3820)
Reads Internet Cache Settings
- iexplore.exe (PID: 3820)
Changes settings of System certificates
- iexplore.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .aiml | | | Artificial Intelligence Markup Language (48.3) |
|---|---|---|
| .htm/html | | | HyperText Markup Language with DOCTYPE (41.6) |
| .html | | | HyperText Markup Language (9.9) |
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|---|
| formatDetection: | telephone=no |
| mobileWebAppCapable: | yes |
| applicationName: | YouPorn |
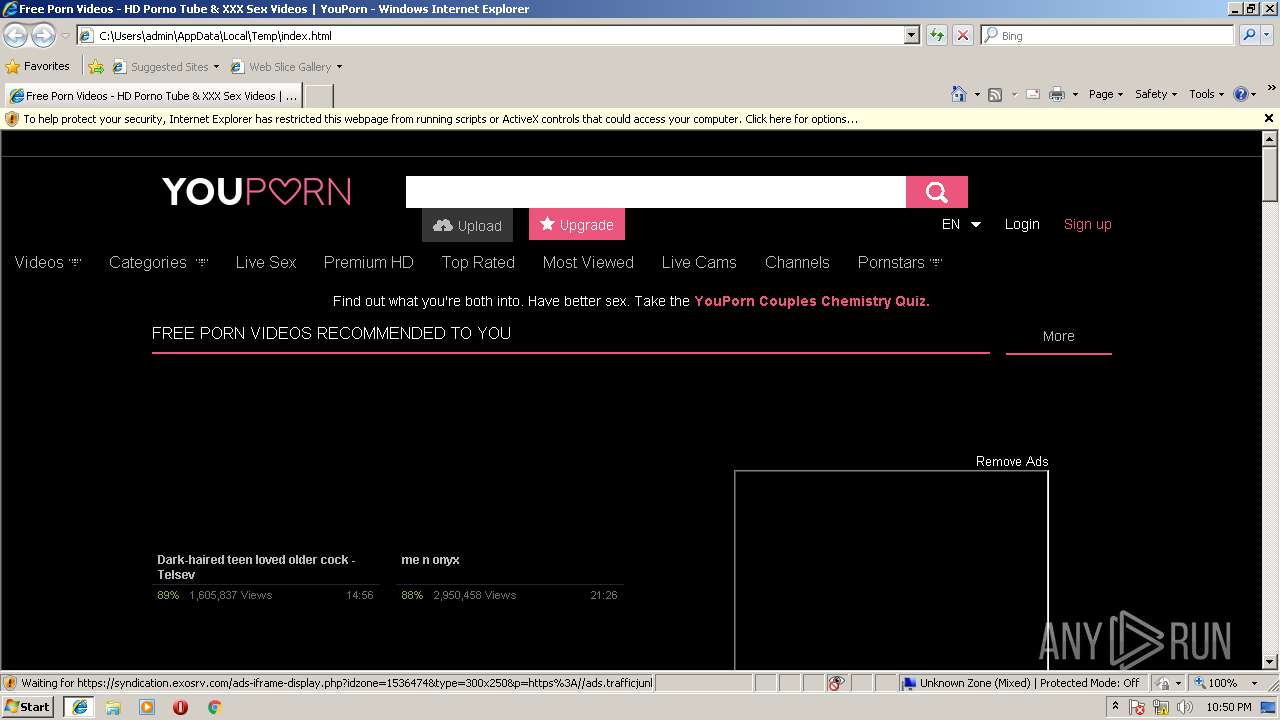
| Description: | YouPorn is your home for free XXX porn videos. Sit back and watch all of the unlimited, high quality HD porn your heart desires. Enjoy the hottest porno movies from just about any category you can imagine. Discover the sexiest naked pornstars and amateurs on Earth, only on the world's favorite sex tube - YouPorn! |
| yandexVerification: | 742d9a1367ba840b |
| Rating: | RTA-5042-1996-1400-1577-RTA |
| msapplicationSquare70x70logo: | https://fs.ypncdn.com/cb/bundles/youpornwebfront/images/windowsTiles/70x70_YP_Tile.png?v=08b503f4259b95e650da612e47378ae9be0f096a |
| msapplicationSquare150x150logo: | https://fs.ypncdn.com/cb/bundles/youpornwebfront/images/windowsTiles/150x150_YP_Tile.png?v=08b503f4259b95e650da612e47378ae9be0f096a |
| msapplicationWide310x150logo: | https://fs.ypncdn.com/cb/bundles/youpornwebfront/images/windowsTiles/310x150_YP_Tile.png?v=08b503f4259b95e650da612e47378ae9be0f096a |
| msapplicationSquare310x310logo: | https://fs.ypncdn.com/cb/bundles/youpornwebfront/images/windowsTiles/310x310_YP_Tile.png?v=08b503f4259b95e650da612e47378ae9be0f096a |
| msapplicationTileColor: | #232323 |
| Title: | Free Porn Videos - HD Porno Tube & XXX Sex Videos | YouPorn |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3268 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3820 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3268 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
420
Read events
331
Write events
84
Delete events
5
Modification events
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006B000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {F4DECD57-5D40-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (3268) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E207050001001500150032001500D301 | |||
Executable files
0
Suspicious files
4
Text files
93
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3268 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3268 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BCPS3ZPQ\f50dd17[1].css | text | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\f5a162e[1].css | text | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\3704da4[1].js | text | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\ads[1].htm | — | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\OP5DQHUV\yp[1].eot | eot | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\OP5DQHUV\3232805[1].js | text | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BCPS3ZPQ\l_youporn_black[1].png | image | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\09985c3[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
97
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3820 | iexplore.exe | GET | 304 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
3820 | iexplore.exe | GET | 200 | 185.75.252.204:80 | http://ht.youporn.com/js/ht.js?site_id=5 | NL | text | 1.78 Kb | unknown |
3820 | iexplore.exe | GET | 200 | 192.35.177.64:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | US | cat | 893 b | shared |
3268 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3268 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3820 | iexplore.exe | 66.254.122.102:443 | fs.ypncdn.com | Reflected Networks, Inc. | US | suspicious |
3820 | iexplore.exe | 94.199.253.32:443 | ads2.contentabc.com | Viking Host B.V. | NL | unknown |
3820 | iexplore.exe | 205.185.216.42:443 | ads.exosrv.com | Highwinds Network Group, Inc. | US | whitelisted |
3820 | iexplore.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3820 | iexplore.exe | 192.35.177.64:80 | apps.identrust.com | IdenTrust | US | malicious |
3820 | iexplore.exe | 95.211.229.245:443 | syndication.exosrv.com | LeaseWeb Netherlands B.V. | NL | suspicious |
4 | System | 216.58.205.238:445 | www.google-analytics.com | Google Inc. | US | whitelisted |
3820 | iexplore.exe | 205.185.216.10:443 | ads.exosrv.com | Highwinds Network Group, Inc. | US | whitelisted |
4 | System | 216.58.205.238:139 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
fs.ypncdn.com |
| suspicious |
cdn1d-static-shared.phncdn.com |
| whitelisted |
media.trafficjunky.net |
| whitelisted |
ads.trafficjunky.net |
| whitelisted |
ads2.contentabc.com |
| whitelisted |
hw-cdn.trafficjunky.net |
| whitelisted |
ads.exosrv.com |
| whitelisted |
apps.identrust.com |
| shared |
vz-cdn.contentabc.com |
| unknown |