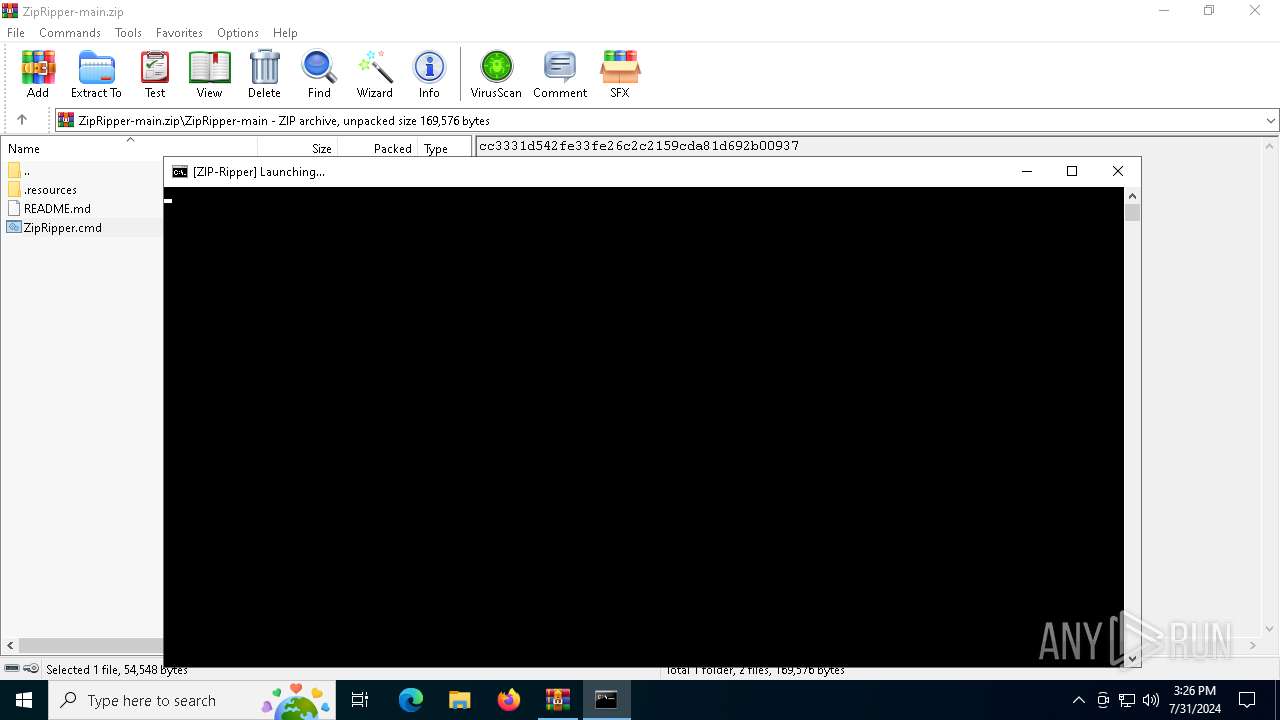
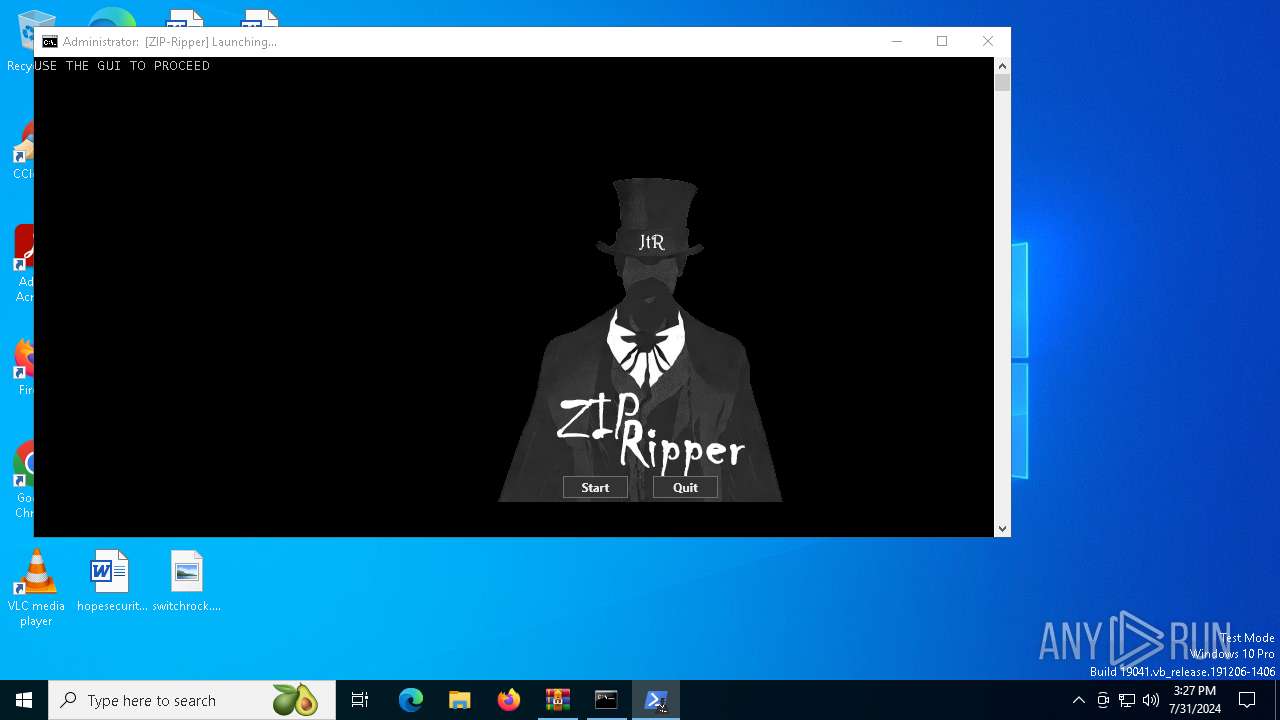
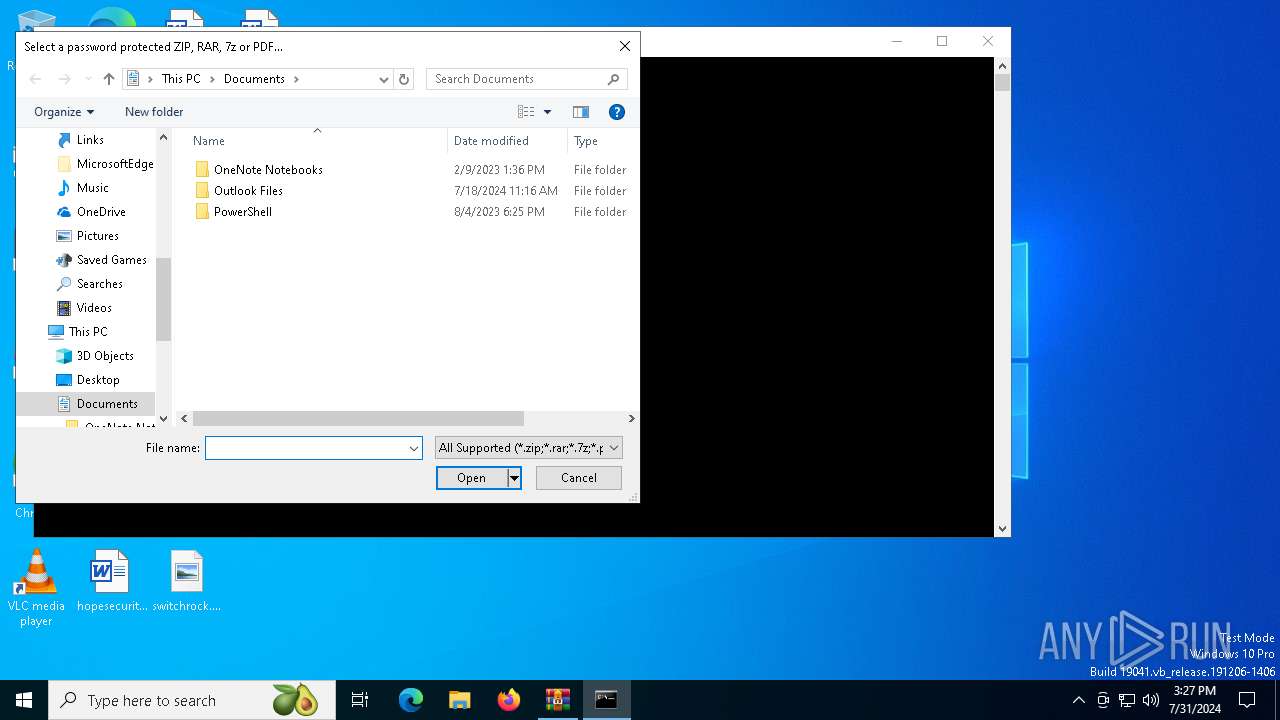
| File name: | ZipRipper-main.zip |
| Full analysis: | https://app.any.run/tasks/a38f1483-ca8a-45bc-aceb-1a949d432750 |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2024, 15:26:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | A52BDC111E25A173CF25451D11F37C9C |
| SHA1: | 142EB64A91EF7006DE03D527BFDA2EFC5FC09201 |
| SHA256: | C5ABCE7E8038C0AE9A9E4634861ADCEEA954104F68DA42EFE21455DCA0870A23 |
| SSDEEP: | 3072:bhHTZ1GL2jTMP+WfxeW+XbA9H4Lkb5WWlkKS4Pqp:1zZ1GK3M+WfxeW+XafZJ98 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6356)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6624)
- WinRAR.exe (PID: 6356)
- cmd.exe (PID: 6280)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3272)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 5028)
- cmd.exe (PID: 5292)
- cmd.exe (PID: 5992)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6624)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 5292)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6624)
- cmd.exe (PID: 6280)
Get information on the list of running processes
- cmd.exe (PID: 6624)
- cmd.exe (PID: 6280)
Application launched itself
- cmd.exe (PID: 6624)
- cmd.exe (PID: 6280)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6808)
- cmd.exe (PID: 3272)
- cmd.exe (PID: 6280)
- cmd.exe (PID: 5292)
- cmd.exe (PID: 5992)
- cmd.exe (PID: 5028)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 6356)
- cmd.exe (PID: 6624)
Hides command output
- cmd.exe (PID: 6152)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 5292)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 5796)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6280)
Executable content was dropped or overwritten
- csc.exe (PID: 6492)
Kill processes via PowerShell
- powershell.exe (PID: 6212)
- powershell.exe (PID: 6560)
- powershell.exe (PID: 6544)
Probably download files using WebClient
- cmd.exe (PID: 6280)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6544)
INFO
Disables trace logs
- powershell.exe (PID: 6824)
- powershell.exe (PID: 2720)
- powershell.exe (PID: 6544)
Checks proxy server information
- powershell.exe (PID: 6824)
- powershell.exe (PID: 2720)
- powershell.exe (PID: 6544)
Creates files in the program directory
- cmd.exe (PID: 6624)
- cmd.exe (PID: 7064)
- powershell.exe (PID: 6544)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5796)
Create files in a temporary directory
- cvtres.exe (PID: 6496)
- csc.exe (PID: 6492)
Checks supported languages
- csc.exe (PID: 6492)
- cvtres.exe (PID: 6496)
Reads the machine GUID from the registry
- csc.exe (PID: 6492)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:06:25 20:25:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ZipRipper-main/ |
Total processes
166
Monitored processes
34
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | FINDSTR /I /C:"ZIP-Ripper" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1608 | REG ADD HKCU\Software\classes\.ZipRipper\shell\runas\command /f /ve /d "CMD /x /d /r SET \"f0=1\"&CALL \"%2\" %3" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | findstr "." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2720 | POWERSHELL -nop -c "$ProgressPreference='SilentlyContinue';irm http://www.msftncsi.com/ncsi.txt;$ProgressPreference='Continue'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3272 | C:\WINDOWS\system32\cmd.exe /c POWERSHELL -nop -c "$ProgressPreference='SilentlyContinue';irm http://www.msftncsi.com/ncsi.txt;$ProgressPreference='Continue'" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5028 | C:\WINDOWS\system32\cmd.exe /c POWERSHELL -nop -c "Add-Type -AssemblyName PresentationFramework, System.Drawing, System.Windows.Forms, WindowsFormsIntegration;function wlist(){Switch($showL){0{$D.Visibility="""Visible""";$R.Visibility="""Visible""";$C.Visibility="""Visible""";$global:showL="""1"""}1{$D.Visibility="""Collapsed""";$R.Visibility="""Collapsed""";$C.Visibility="""Collapsed""";$global:showL="""0"""}}};[xml]$xaml='<Window xmlns="""http://schemas.microsoft.com/winfx/2006/xaml/presentation""" xmlns:x="""http://schemas.microsoft.com/winfx/2006/xaml""" WindowStartupLocation="""CenterScreen""" WindowStyle="""None""" Background="""Transparent""" AllowsTransparency="""True""" Width="""285""" Height="""324"""><Window.Resources><ControlTemplate x:Key="""nM""" TargetType="""Button"""><Border Background="""{TemplateBinding Background}""" BorderBrush="""{TemplateBinding BorderBrush}""" BorderThickness="""{TemplateBinding BorderThickness}"""><ContentPresenter HorizontalAlignment="""{TemplateBinding HorizontalContentAlignment}""" VerticalAlignment="""{TemplateBinding VerticalContentAlignment}"""/></Border><ControlTemplate.Triggers><Trigger Property="""IsEnabled""" Value="""False"""><Setter Property="""Background""" Value="""{x:Static SystemColors.ControlLightBrush}"""/><Setter Property="""Foreground""" Value="""{x:Static SystemColors.GrayTextBrush}"""/></Trigger></ControlTemplate.Triggers></ControlTemplate></Window.Resources><Grid><Grid.RowDefinitions><RowDefinition Height="""298"""/><RowDefinition Height="""*"""/></Grid.RowDefinitions><Grid.Background><ImageBrush ImageSource="""C:\ProgramData\zipripper.png"""/></Grid.Background><Grid.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation Storyboard.TargetProperty="""Background.Opacity""" From="""0""" To="""1""" Duration="""0:0:1"""/></Storyboard></BeginStoryboard></EventTrigger></Grid.Triggers><Canvas Grid.Row="""0"""><Button x:Name="""Offline""" Canvas.Left="""141""" Canvas.Top="""56""" Height="""16""" Width="""26""" ToolTip="""Create [zr-offline.txt]""" Template="""{StaticResource nM}"""/><Button x:Name="""Cleanup""" Canvas.Left="""138""" Canvas.Top="""154""" Height="""20""" Width="""20""" ToolTip="""Clear Resume Cache""" Template="""{StaticResource nM}"""/><Button Name="""List""" Canvas.Left="""143""" Canvas.Top="""116""" Height="""10""" Width="""15""" ToolTip="""Select Wordlist""" Template="""{StaticResource nM}""" Opacity="""0"""></Button><Button Name="""Default""" Canvas.Left="""123""" Canvas.Top="""130""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Default</Button><Button Name="""WL""" Canvas.Left="""123""" Canvas.Top="""147""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Cyclone</Button><Button Name="""Custom""" Canvas.Left="""123""" Canvas.Top="""164""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Custom</Button></Canvas><Canvas Grid.Row="""1"""><Button x:Name="""Start""" Height="""22""" Width="""65""" Content="""Start""" ToolTip="""Click to Begin...""" Template="""{StaticResource nM}"""><Button.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation From="""40""" To="""65""" Duration="""0:0:1""" Storyboard.TargetProperty="""(Canvas.Left)""" AutoReverse="""False"""/><DoubleAnimation Storyboard.TargetProperty="""Opacity""" From="""0""" To="""1""" Duration="""0:0:2"""/></Storyboard></BeginStoryboard></EventTrigger></Button.Triggers></Button></Canvas><Canvas Grid.Row="""1"""><Button x:Name="""Quit""" Height="""22""" Width="""65""" Content="""Quit""" ToolTip="""Click to Exit""" Template="""{StaticResource nM}"""><Button.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation From="""40""" To="""65""" Duration="""0:0:1""" Storyboard.TargetProperty="""(Canvas.Right)""" AutoReverse="""False"""/><DoubleAnimation Storyboard.TargetProperty="""Opacity""" From="""0""" To="""1""" Duration="""0:0:2"""/></Storyboard></BeginStoryboard></EventTrigger></Button.Triggers></Button></Canvas></Grid><Window.TaskbarItemInfo><TaskbarItemInfo/></Window.TaskbarItemInfo></Window>';$reader=(New-Object System.Xml.XmlNodeReader $xaml);$window=[Windows.Markup.XamlReader]::Load($reader);$window.Title='ZipRipper';$bitmap=New-Object System.Windows.Media.Imaging.BitmapImage;$bitmap='C:\ProgramData\zipripper.png';$window.Icon=$bitmap;$window.TaskbarItemInfo.Overlay=$bitmap;$window.TaskbarItemInfo.Description=$window.Title;$window.Add_Closing({[System.Windows.Forms.Application]::Exit();Stop-Process $pid});$L=$Window.FindName("""List""");$D=$Window.FindName("""Default""");$R=$Window.FindName("""WL""");$C=$Window.FindName("""Custom""");$L.Add_Click({wlist});$D.Add_MouseEnter({$D.Background="""#eeeeee""";$D.Foreground="""#333333"""});$D.Add_MouseLeave({$D.Background="""#333333""";$D.Foreground="""#eeeeee"""});$D.Add_Click({$global:list="""0""";wlist});$R.Add_MouseEnter({$R.Background="""#eeeeee""";$R.Foreground="""#333333"""});$R.Add_MouseLeave({$R.Background="""#333333""";$R.Foreground="""#eeeeee"""});$R.Add_Click({$global:list="""1""";wlist});$C.Add_MouseEnter({$C.Background="""#eeeeee""";$C.Foreground="""#333333"""});$C.Add_MouseLeave({$C.Background="""#333333""";$C.Foreground="""#eeeeee"""});$C.Add_Click({$global:list="""2""";wlist});$b=$Window.FindName("""Start""");$b.Background = """#333333""";$b.Foreground="""#eeeeee""";$b.FontSize="""12""";$b.FontWeight="""Bold""";$b.Add_MouseEnter({$b.Background="""#eeeeee""";$b.Foreground="""#333333"""});$b.Add_MouseLeave({$b.Background="""#333333""";$b.Foreground="""#eeeeee"""});$b.Add_Click({write-host """Start,$list""";Exit});$b2=$Window.FindName("""Quit""");$b2.Background="""#333333""";$b2.Foreground="""#eeeeee""";$b2.FontSize="""12""";$b2.FontWeight="""Bold""";$b2.Add_MouseEnter({$b2.Background="""#eeeeee""";$b2.Foreground="""#333333"""});$b2.Add_MouseLeave({$b2.Background="""#333333""";$b2.Foreground="""#eeeeee"""});$b2.Add_Click({write-host 'Quit';Exit});$b3=$Window.FindName("""Offline""");$b3.Opacity="""0""";$b3.Add_Click({$b3m=New-Object -ComObject Wscript.Shell;$b3a=$b3m.Popup('Create [zr-offline.txt] for Offline Mode?',0,'Offline Mode Builder',0x1);if($b3a -eq 1){write-host 'Offline';Exit}});$b4=$Window.FindName("""Cleanup""");$b4.Opacity="""0""";$b4.Add_Click({$b4m=New-Object -ComObject Wscript.Shell;$b4a=$b4m.Popup("""Cleanup ALL resume data?""",0,'Clear InProgress Jobs',0x1);if($b4a -eq 1){if(Test-Path -Path 'C:\Users\admin\AppData\Roaming\ZR-InProgress'){Remove-Item 'C:\Users\admin\AppData\Roaming\ZR-InProgress' -Recurse -force -ErrorAction SilentlyContinue;$b4m2=New-Object -ComObject Wscript.Shell;$b4m2.Popup("""ALL Jobs Cleared""",0,'Clear InProgress Jobs',0x0)} else {$b4m3=New-Object -ComObject Wscript.Shell;$b4m3.Popup('There are no jobs to clear',0,'Clear InProgress Jobs',0x0)}}});$list="""0""";$showL="""0""";$window.add_MouseLeftButtonDown({if($showL -eq 1){wlist};$window.DragMove()});$window.Show();$appContext=New-Object System.Windows.Forms.ApplicationContext;[void][System.Windows.Forms.Application]::Run($appContext)" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5052 | POWERSHELL -nop -c "$w=Add-Type -Name WAPI -PassThru -MemberDefinition '[DllImport("""user32.dll""")]public static extern void SetProcessDPIAware();[DllImport("""shcore.dll""")]public static extern void SetProcessDpiAwareness(int value);[DllImport("""kernel32.dll""")]public static extern IntPtr GetConsoleWindow();[DllImport("""user32.dll""")]public static extern void GetWindowRect(IntPtr hwnd,int[] rect);[DllImport("""user32.dll""")]public static extern void GetClientRect(IntPtr hwnd, int[] rect);[DllImport("""user32.dll""")]public static extern void GetMonitorInfoW(IntPtr hMonitor, int[] lpmi);[DllImport("""user32.dll""")]public static extern IntPtr MonitorFromWindow(IntPtr hwnd, int dwFlags);[DllImport("""user32.dll""")]public static extern int SetWindowPos(IntPtr hwnd,IntPtr hwndAfterZ,int x,int y,int w,int h,int flags);';$PROCESS_PER_MONITOR_DPI_AWARE=2;try{$w::SetProcessDpiAwareness($PROCESS_PER_MONITOR_DPI_AWARE)}catch{$w::SetProcessDPIAware()}$hwnd=$w::GetConsoleWindow();$moninf=[int[]]::new(10);$moninf[0]=40;$MONITOR_DEFAULTTONEAREST=2;$w::GetMonitorInfoW($w::MonitorFromWindow($hwnd, $MONITOR_DEFAULTTONEAREST), $moninf);$monwidth=$moninf[7]-$moninf[5];$monheight=$moninf[8]-$moninf[6];$wrect=[int[]]::new(4);$w::GetWindowRect($hwnd, $wrect);$winwidth=$wrect[2]-$wrect[0];$winheight=$wrect[3]-$wrect[1];$x=[int][math]::Round($moninf[5]+$monwidth/2-$winwidth/2);$y=[int][math]::Round($moninf[6]+$monheight/2-$winheight/2);$SWP_NOSIZE=0x0001;$SWP_NOZORDER=0x0004;exit [int]($w::SetWindowPos($hwnd,[IntPtr]::Zero,$x,$y,0,0,$SWP_NOSIZE -bOr $SWP_NOZORDER) -eq 0)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | TASKLIST /V /NH /FI "imagename eq cmd.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5292 | C:\WINDOWS\system32\cmd.exe /c WMIC path Win32_VideoController get Name | findstr "." | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5292 | C:\WINDOWS\system32\cmd.exe /c POWERSHELL -nop -c "Add-Type -AssemblyName PresentationFramework, System.Drawing, System.Windows.Forms, WindowsFormsIntegration;function wlist(){Switch($showL){0{$D.Visibility="""Visible""";$R.Visibility="""Visible""";$C.Visibility="""Visible""";$global:showL="""1"""}1{$D.Visibility="""Collapsed""";$R.Visibility="""Collapsed""";$C.Visibility="""Collapsed""";$global:showL="""0"""}}};[xml]$xaml='<Window xmlns="""http://schemas.microsoft.com/winfx/2006/xaml/presentation""" xmlns:x="""http://schemas.microsoft.com/winfx/2006/xaml""" WindowStartupLocation="""CenterScreen""" WindowStyle="""None""" Background="""Transparent""" AllowsTransparency="""True""" Width="""285""" Height="""324"""><Window.Resources><ControlTemplate x:Key="""nM""" TargetType="""Button"""><Border Background="""{TemplateBinding Background}""" BorderBrush="""{TemplateBinding BorderBrush}""" BorderThickness="""{TemplateBinding BorderThickness}"""><ContentPresenter HorizontalAlignment="""{TemplateBinding HorizontalContentAlignment}""" VerticalAlignment="""{TemplateBinding VerticalContentAlignment}"""/></Border><ControlTemplate.Triggers><Trigger Property="""IsEnabled""" Value="""False"""><Setter Property="""Background""" Value="""{x:Static SystemColors.ControlLightBrush}"""/><Setter Property="""Foreground""" Value="""{x:Static SystemColors.GrayTextBrush}"""/></Trigger></ControlTemplate.Triggers></ControlTemplate></Window.Resources><Grid><Grid.RowDefinitions><RowDefinition Height="""298"""/><RowDefinition Height="""*"""/></Grid.RowDefinitions><Grid.Background><ImageBrush ImageSource="""C:\ProgramData\zipripper.png"""/></Grid.Background><Grid.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation Storyboard.TargetProperty="""Background.Opacity""" From="""0""" To="""1""" Duration="""0:0:1"""/></Storyboard></BeginStoryboard></EventTrigger></Grid.Triggers><Canvas Grid.Row="""0"""><Button x:Name="""Offline""" Canvas.Left="""141""" Canvas.Top="""56""" Height="""16""" Width="""26""" ToolTip="""Create [zr-offline.txt]""" Template="""{StaticResource nM}"""/><Button x:Name="""Cleanup""" Canvas.Left="""138""" Canvas.Top="""154""" Height="""20""" Width="""20""" ToolTip="""Clear Resume Cache""" Template="""{StaticResource nM}"""/><Button Name="""List""" Canvas.Left="""143""" Canvas.Top="""116""" Height="""10""" Width="""15""" ToolTip="""Select Wordlist""" Template="""{StaticResource nM}""" Opacity="""0"""></Button><Button Name="""Default""" Canvas.Left="""123""" Canvas.Top="""130""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Default</Button><Button Name="""WL""" Canvas.Left="""123""" Canvas.Top="""147""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Cyclone</Button><Button Name="""Custom""" Canvas.Left="""123""" Canvas.Top="""164""" FontSize="""11""" Foreground="""#eeeeee""" Background="""#333333""" Height="""18""" Width="""55""" Visibility="""Collapsed""" HorizontalContentAlignment="""Left""" Template="""{StaticResource nM}""" Opacity="""0.9""">Custom</Button></Canvas><Canvas Grid.Row="""1"""><Button x:Name="""Start""" Height="""22""" Width="""65""" Content="""Start""" ToolTip="""Click to Begin...""" Template="""{StaticResource nM}"""><Button.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation From="""40""" To="""65""" Duration="""0:0:1""" Storyboard.TargetProperty="""(Canvas.Left)""" AutoReverse="""False"""/><DoubleAnimation Storyboard.TargetProperty="""Opacity""" From="""0""" To="""1""" Duration="""0:0:2"""/></Storyboard></BeginStoryboard></EventTrigger></Button.Triggers></Button></Canvas><Canvas Grid.Row="""1"""><Button x:Name="""Quit""" Height="""22""" Width="""65""" Content="""Quit""" ToolTip="""Click to Exit""" Template="""{StaticResource nM}"""><Button.Triggers><EventTrigger RoutedEvent="""Loaded"""><BeginStoryboard><Storyboard><DoubleAnimation From="""40""" To="""65""" Duration="""0:0:1""" Storyboard.TargetProperty="""(Canvas.Right)""" AutoReverse="""False"""/><DoubleAnimation Storyboard.TargetProperty="""Opacity""" From="""0""" To="""1""" Duration="""0:0:2"""/></Storyboard></BeginStoryboard></EventTrigger></Button.Triggers></Button></Canvas></Grid><Window.TaskbarItemInfo><TaskbarItemInfo/></Window.TaskbarItemInfo></Window>';$reader=(New-Object System.Xml.XmlNodeReader $xaml);$window=[Windows.Markup.XamlReader]::Load($reader);$window.Title='ZipRipper';$bitmap=New-Object System.Windows.Media.Imaging.BitmapImage;$bitmap='C:\ProgramData\zipripper.png';$window.Icon=$bitmap;$window.TaskbarItemInfo.Overlay=$bitmap;$window.TaskbarItemInfo.Description=$window.Title;$window.Add_Closing({[System.Windows.Forms.Application]::Exit();Stop-Process $pid});$L=$Window.FindName("""List""");$D=$Window.FindName("""Default""");$R=$Window.FindName("""WL""");$C=$Window.FindName("""Custom""");$L.Add_Click({wlist});$D.Add_MouseEnter({$D.Background="""#eeeeee""";$D.Foreground="""#333333"""});$D.Add_MouseLeave({$D.Background="""#333333""";$D.Foreground="""#eeeeee"""});$D.Add_Click({$global:list="""0""";wlist});$R.Add_MouseEnter({$R.Background="""#eeeeee""";$R.Foreground="""#333333"""});$R.Add_MouseLeave({$R.Background="""#333333""";$R.Foreground="""#eeeeee"""});$R.Add_Click({$global:list="""1""";wlist});$C.Add_MouseEnter({$C.Background="""#eeeeee""";$C.Foreground="""#333333"""});$C.Add_MouseLeave({$C.Background="""#333333""";$C.Foreground="""#eeeeee"""});$C.Add_Click({$global:list="""2""";wlist});$b=$Window.FindName("""Start""");$b.Background = """#333333""";$b.Foreground="""#eeeeee""";$b.FontSize="""12""";$b.FontWeight="""Bold""";$b.Add_MouseEnter({$b.Background="""#eeeeee""";$b.Foreground="""#333333"""});$b.Add_MouseLeave({$b.Background="""#333333""";$b.Foreground="""#eeeeee"""});$b.Add_Click({write-host """Start,$list""";Exit});$b2=$Window.FindName("""Quit""");$b2.Background="""#333333""";$b2.Foreground="""#eeeeee""";$b2.FontSize="""12""";$b2.FontWeight="""Bold""";$b2.Add_MouseEnter({$b2.Background="""#eeeeee""";$b2.Foreground="""#333333"""});$b2.Add_MouseLeave({$b2.Background="""#333333""";$b2.Foreground="""#eeeeee"""});$b2.Add_Click({write-host 'Quit';Exit});$b3=$Window.FindName("""Offline""");$b3.Opacity="""0""";$b3.Add_Click({$b3m=New-Object -ComObject Wscript.Shell;$b3a=$b3m.Popup('Create [zr-offline.txt] for Offline Mode?',0,'Offline Mode Builder',0x1);if($b3a -eq 1){write-host 'Offline';Exit}});$b4=$Window.FindName("""Cleanup""");$b4.Opacity="""0""";$b4.Add_Click({$b4m=New-Object -ComObject Wscript.Shell;$b4a=$b4m.Popup("""Cleanup ALL resume data?""",0,'Clear InProgress Jobs',0x1);if($b4a -eq 1){if(Test-Path -Path 'C:\Users\admin\AppData\Roaming\ZR-InProgress'){Remove-Item 'C:\Users\admin\AppData\Roaming\ZR-InProgress' -Recurse -force -ErrorAction SilentlyContinue;$b4m2=New-Object -ComObject Wscript.Shell;$b4m2.Popup("""ALL Jobs Cleared""",0,'Clear InProgress Jobs',0x0)} else {$b4m3=New-Object -ComObject Wscript.Shell;$b4m3.Popup('There are no jobs to clear',0,'Clear InProgress Jobs',0x0)}}});$list="""0""";$showL="""0""";$window.add_MouseLeftButtonDown({if($showL -eq 1){wlist};$window.DragMove()});$window.Show();$appContext=New-Object System.Windows.Forms.ApplicationContext;[void][System.Windows.Forms.Application]::Run($appContext)" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 336
Read events
33 295
Write events
41
Delete events
0
Modification events
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ZipRipper-main.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6003 |
Value: Windows Command Script | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
1
Text files
21
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6356.41460\ZipRipper.cmd | text | |
MD5:3D2999161A65CEA9D646A724A5FAD979 | SHA256:ADBB6CDF1DA0FD8696B66C9372182D5F2D1D90E89197BF480CE3532D909F0CD7 | |||
| 5052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ugy3wfgk.o4z.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_20e0ol55.ss1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6624 | cmd.exe | C:\ProgramData\ZipRipper.cmd | text | |
MD5:3D2999161A65CEA9D646A724A5FAD979 | SHA256:ADBB6CDF1DA0FD8696B66C9372182D5F2D1D90E89197BF480CE3532D909F0CD7 | |||
| 6824 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:F403E6990BFED1D42C240721899F9E05 | SHA256:— | |||
| 7064 | cmd.exe | C:\ProgramData\launcher.ZipRipper | text | |
MD5:2CCBA1F2476697B81B96866CA4A9E1D5 | SHA256:— | |||
| 6212 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3je4s5az.t0j.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6496 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES8180.tmp | o | |
MD5:0113EB5EA14D1F9077270EF38FA2271E | SHA256:— | |||
| 5052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jeyi4yhi\jeyi4yhi.cmdline | text | |
MD5:03D028B4755FADA5BA5897E0CD8FF669 | SHA256:— | |||
| 2720 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tineizlq.hmo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
19
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6824 | powershell.exe | GET | 200 | 88.221.110.147:80 | http://www.msftncsi.com/ncsi.txt | unknown | — | — | whitelisted |
2720 | powershell.exe | GET | 200 | 88.221.110.147:80 | http://www.msftncsi.com/ncsi.txt | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3160 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6692 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6032 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5116 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1120 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6824 | powershell.exe | 88.221.110.147:80 | www.msftncsi.com | Akamai International B.V. | DE | unknown |
2720 | powershell.exe | 88.221.110.147:80 | www.msftncsi.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.msftncsi.com |
| whitelisted |
www.bing.com |
| unknown |
ocsp.digicert.com |
| unknown |
client.wns.windows.com |
| unknown |
login.live.com |
| unknown |
th.bing.com |
| unknown |
raw.githubusercontent.com |
| unknown |
fd.api.iris.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6824 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2720 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |